Hello everybody!!
First of all, excuse me that I have not posted anything, I carry many things at once and between work, studies, various projects, trips and I have two things that I want to post and I have almost finished, I do not have time, even for myself.
But well, today I bring you something light. Some time ago I received a rather striking email, I had never received anything like that and the truth, it amazed me as the scammers are so careful. This is why, I would like to talk about this topic, and being connected has many dangers, including phishing.
Most of you will know what phishing is, but in case someone doesn’t know it, phishing is a method by which they try to extract all kinds of confidential information fraudulently from the victim (any of us), mainly bank account data. Phishing is nothing more than a type of social engineering, in which they impersonate an identity (a real person or entity) to make the victim believe it is trustworthy and sting in the hook. Phishers (those who do phishing) primarily use email or some type of instant messaging.
Although many people think that the danger is phishing, they are wrong, the danger is always present and can manifest itself in many ways, including phishing. Although there are many other ways, such as smishing, that instead of email use SMS on mobile, or vishing, with phone calls. All of them are variants and belong to the Social Engineering group.
After that, I make a special mention to all types of social engineering, something that very few people give importance, and given the times, and that will get worse, it is very necessary to inform people of all the dangers which entails being connected. I would like to comment on all of them here, but it would be too long. Whenever I can I give advice, and that is always always always, doubt at all costs to give information, be it passwords, credit cards or some type of information so lightly. Because remember, the principle that underpins social engineering is that in any system, users are the weak link.
Continuing with the phishing issue, this is the email I received:

As you can see, it is from Amazon, or rather, it seems to be from Amazon.
To anyone who is not very well placed in this line, he will think, oh my God, they will close my account, how? Why? It cannot be! And click on the button.
This could happen, but remembering the first thing I said, always always always doubt at all costs giving information. With this in mind you should start to doubt, “Are there really problems with my account? Amazon has never asked me anything. Is it really Amazon?”
t’s normal, we can have doubts, and this is where I would like to comment on some “tricks” to know if it’s really fake or not.
If in this case we click on the “Update now” link. The following page will open in the browser.

When you open it you say, it is apparently Amazon, with the typical login, same appearance, same image, all the same, but … If we look at the URL we can verify that it is not Amazon.com, no matter how much green lock there is, it is NOT Amazon.
But in addition, with this it isn’t enough, because in this case I have been lucky and the browser shows me the domain part of URL, I mean, the real page, but other browsers may not be like this and show the prepared URL that cybercriminals have created, that just have enough characters to show this prepared part of URL and hide the real part of URL. And when I say enough characters, I mean the necessary characters that only goes into the width, in this case, the mobile.

Scammers are interested in showing the subdomain, and with some luck the real domain is not seen. Many times if the victim sees the word “Amazon” doesn’t give it more importance and fall into the trap.
But there is more, if we return to the email, we can see more information about who sent it to us.

If we click on customer-service@amazon.com which seems to be the email of the person who sent it to us, we will see the real information of the issuer and just below it appears the real email from where it was sent.
These are the main “tricks” to which I referred, very careful with the URL, but above all, special attention to email sender. If we pass this barrier, we will hardly be able to realize it later, we must have our eyes wide open!
Let’s keep going; At this point, and knowing that it is phishing, I have placed a fully invented username and password, and as I expected, the page has advanced and it has shown me the following. Of course, they don’t have the database, they can’t contrast something!
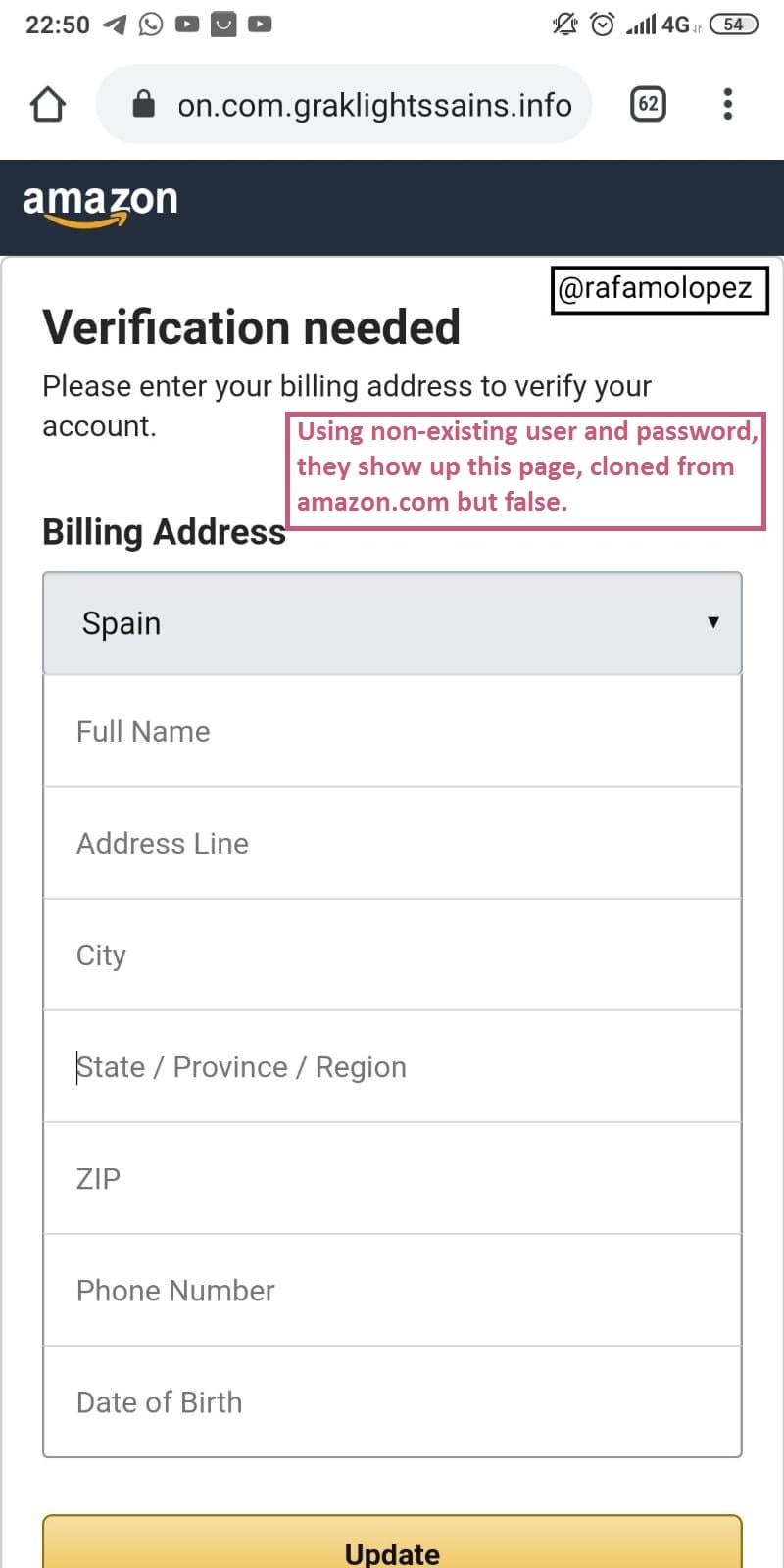
The page looks very real, it looks a lot like Amazon’s styles. Here they ask for any type of information, even the brand of your underwear! So placing a random text, we go to the next page.
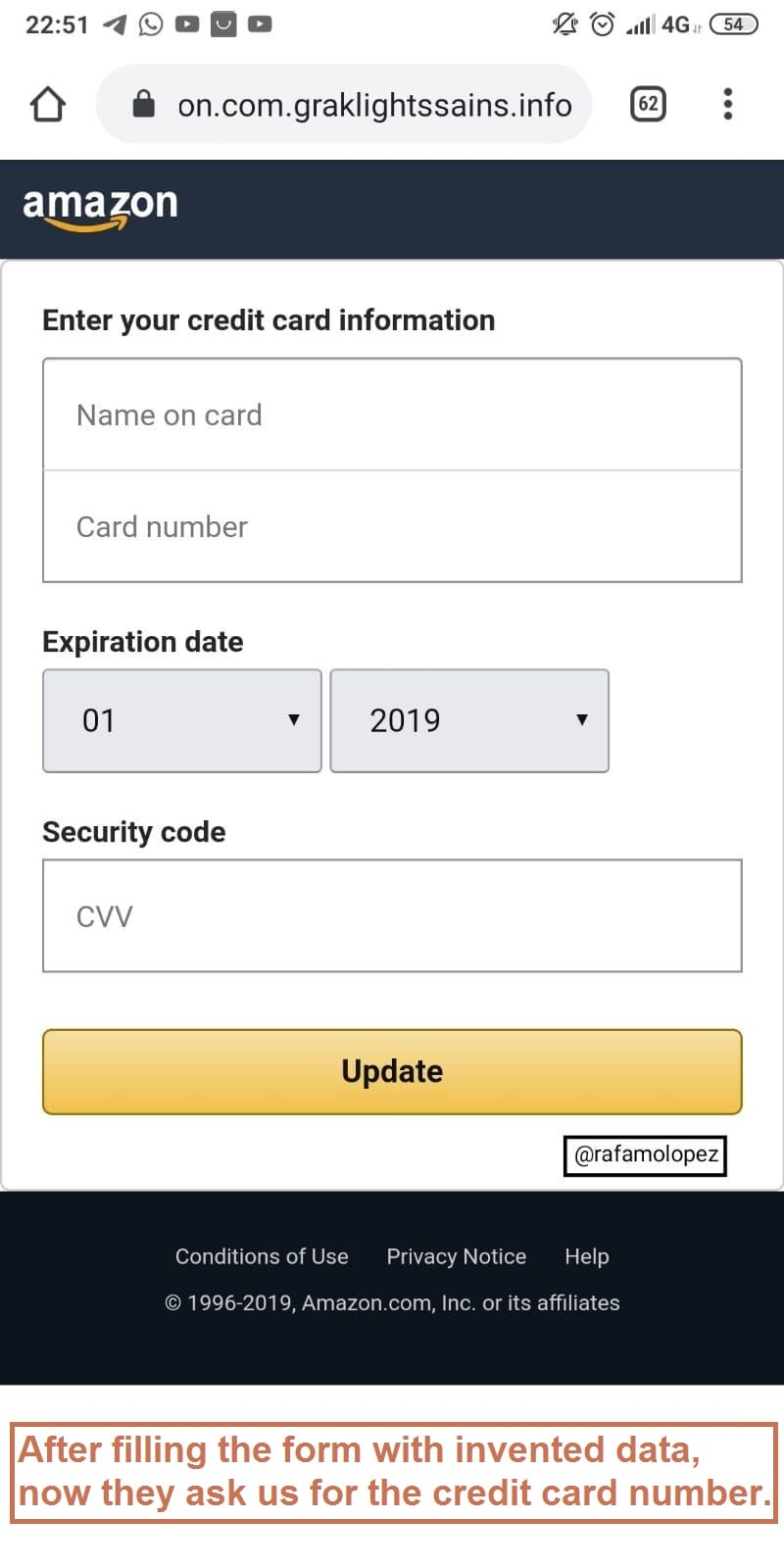
As expected, they will ask for the credit card number. Although at this point, something got my attention, they have a credit card checker! They check the credit card number before you can go to the next page. I had to search an online generator of virtual credit cards to pass the checker. They took it very seriously!

Now they ask us for a front and back credit card photo.
By placing them, it takes us to:
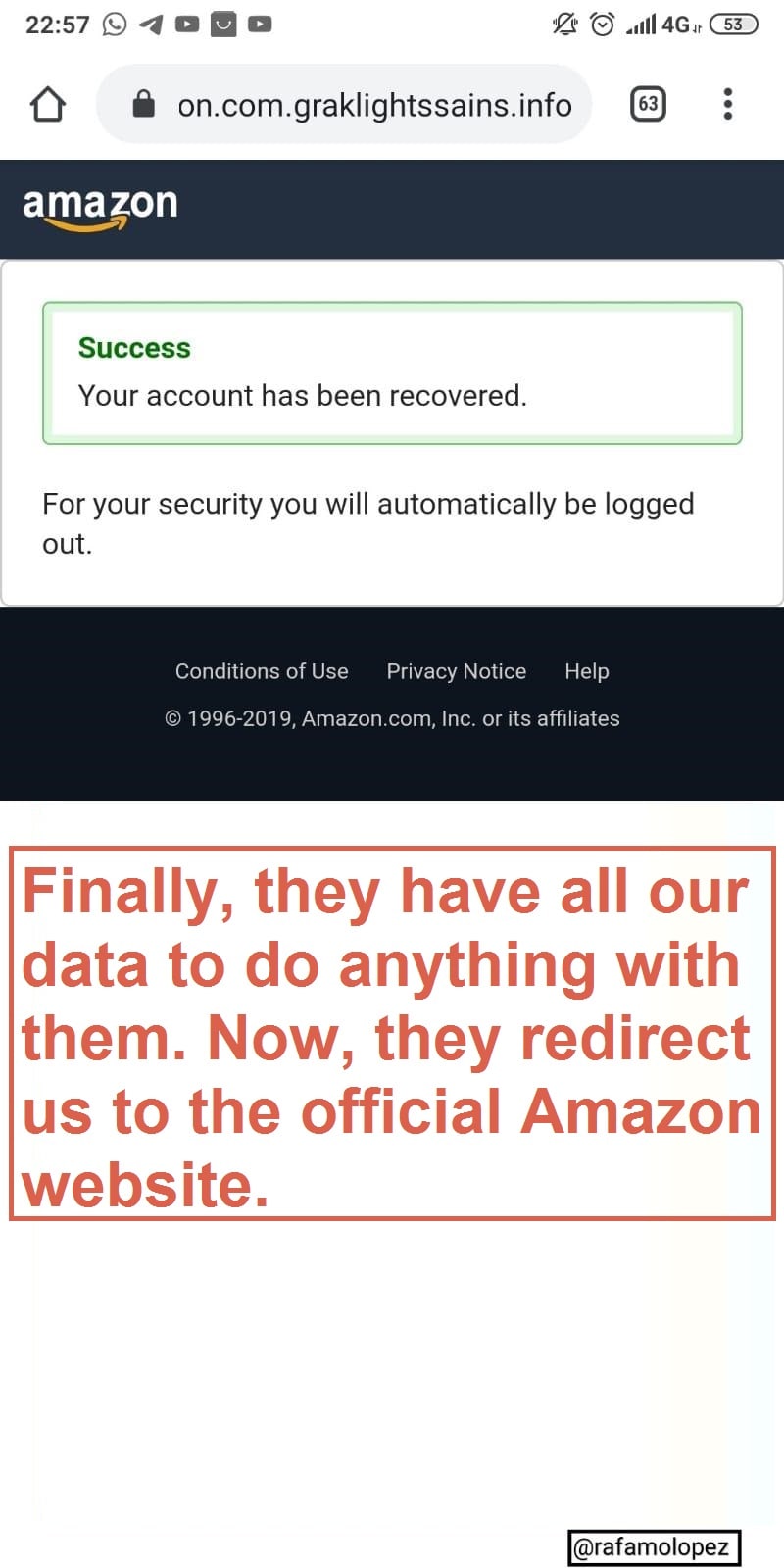
We have verified our account, apparently, everything is OK, and now it will redirect us to the official Amazon webpage, and thus you can enter your username and password, and see that Amazon has not deleted anything.

And here the phishing ends, the victim in a few days will see movements in his credit card, password changes, Amazon orders to other places and someone with bad luck in a few months or years could find some type of complaint of any scam or illegality, for having used cybercriminals their data on illegal pages.
I hope I explained clearly and that you liked it. Remember, always always always, doubt at all costs to give information, be it passwords, credit cards or some kind of information so lightly.
See you in the next post! 😉
Happy Hacking!
Author: Rafael Moreno López.

buy 10 mg prednisone: https://prednisone1st.store/# cost of prednisone tablets
prednisone 4mg tab: http://prednisone1st.store/# 50mg prednisone tablet
medication canadian pharmacy buy drugs from canada
amoxicillin discount: order amoxicillin no prescription amoxicillin 200 mg tablet
propecia without insurance propecia cheap
where can i get generic mobic without insurance: where can i buy cheap mobic without dr prescription – cost of cheap mobic for sale
Actual trends of drug.
generic amoxicillin cost buy amoxicillin online mexico – amoxicillin 500 mg online
Everything about medicine.
buying cheap propecia without prescription cost of generic propecia online
canada drug pharmacy canadian pharmacy 24
medicine erectile dysfunction: drugs for ed – erection pills online
order generic mobic tablets: where to buy cheap mobic without a prescription – can you get cheap mobic price
cheap propecia tablets buying propecia without rx
canada pharmacy online canadian pharmacies that deliver to the us
canadian mail order pharmacy canadian pharmacy
canadian pharmacy checker pharmacy canadian superstore
trustworthy canadian pharmacy: legal canadian pharmacy online – my canadian pharmacy
http://certifiedcanadapharm.store/# canadapharmacyonline
online pharmacy india: cheapest online pharmacy india – india pharmacy
https://mexpharmacy.sbs/# mexican border pharmacies shipping to usa
mexican drugstore online: mexican online pharmacies prescription drugs – best online pharmacies in mexico
http://indiamedicine.world/# indian pharmacies safe
mexico drug stores pharmacies: buying from online mexican pharmacy – pharmacies in mexico that ship to usa
http://certifiedcanadapharm.store/# canadian drugs
medicine in mexico pharmacies: mexican pharmaceuticals online – mexican mail order pharmacies
http://certifiedcanadapharm.store/# canadian drug
http://gabapentin.pro/# gabapentin buy
brand neurontin 100 mg canada: buying neurontin online – neurontin capsules 100mg
https://stromectolonline.pro/# ivermectin cream 5%
zithromax 500 mg lowest price online: zithromax online usa no prescription – zithromax cost australia
http://gabapentin.pro/# neurontin 50mg cost
buy cheap neurontin: neurontin buy from canada – neurontin generic south africa
п»їpaxlovid: buy paxlovid online – paxlovid for sale
https://antibiotic.guru/# cheapest antibiotics
Paxlovid over the counter: paxlovid pharmacy – paxlovid for sale
https://lipitor.pro/# lipitor 4 mg
https://ciprofloxacin.ink/# cipro
canadian pharmacy online maple leaf pharmacy in canada trustworthy canadian pharmacy
https://certifiedcanadapills.pro/# legal to buy prescription drugs from canada
pharmacy wholesalers canada canadian drug pharmacy www canadianonlinepharmacy
buying prescription drugs in mexico online: best online pharmacies in mexico – pharmacies in mexico that ship to usa
indian pharmacy paypal: india pharmacy mail order – indian pharmacies safe
pharmacies in mexico that ship to usa: buying prescription drugs in mexico – mexican border pharmacies shipping to usa
http://edapotheke.store/# versandapotheke
acheter sildenafil 100mg sans ordonnance
buying prescription drugs in mexico: mexican drugstore online – mexican pharmaceuticals online
side effect for zoloft
purple pharmacy mexico price list: buying prescription drugs in mexico online – reputable mexican pharmacies online
купить бетон
indian pharmacies safe: top 10 online pharmacy in india – online pharmacy india
best rated canadian pharmacy: canadian pharmacies compare – canadian pharmacy checker
canadian neighbor pharmacy: buying from canadian pharmacies – prescription drugs canada buy online
antibiotics doxycycline buy doxycycline online how much is doxycycline 100mg
http://azithromycinotc.store/# zithromax 500 mg for sale
Some are medicines that help people when doctors prescribe. doxycycline buy online us: buy doxycycline over the counter – doxycycline buy canada 100mg
All trends of medicament. http://azithromycinotc.store/# buy cheap zithromax online
ed pills cheap ED pills online erectile dysfunction drug
The widest range of international brands under one roof. http://azithromycinotc.store/# zithromax online usa no prescription
A beacon of international trust and reliability. https://azithromycinotc.store/# zithromax azithromycin
I’m always impressed with their efficient system. http://indianpharmacy.life/# buy medicines online in india
Their international collaborations benefit patients immensely. https://canadapharmacy.cheap/# drugs from canada
mexico drug stores pharmacies and mexico pharmacy price list – pharmacies in mexico that ship to usa
http://canadapharmacy24.pro/# canadian pharmacy 365
http://indiapharmacy24.pro/# indian pharmacy
http://indiapharmacy24.pro/# п»їlegitimate online pharmacies india
https://plavix.guru/# Cost of Plavix on Medicare
can you buy cheap mobic without a prescription: buy mobic – how to get cheap mobic prices
ivermectin medication: minocycline for uti – ivermectin goodrx
https://kamagra.icu/# п»їkamagra
https://cialis.foundation/# Tadalafil price
http://cialis.foundation/# Tadalafil Tablet
Buy Tadalafil 10mg Tadalafil price Cialis 20mg price
https://cialis.foundation/# Cialis 20mg price in USA
cialis for sale cheapest cialis Cialis without a doctor prescription
buy cialis pill cheapest cialis Generic Tadalafil 20mg price
https://kamagra.icu/# Kamagra tablets
https://kamagra.icu/# sildenafil oral jelly 100mg kamagra
Cialis without a doctor prescription Generic Cialis price Generic Tadalafil 20mg price
http://kamagra.icu/# Kamagra tablets
Tadalafil Tablet Buy Tadalafil 10mg cialis for sale
купить бетон
консультации юриста бесплатно для всех вопросов о законодательстве|юридическая помощь без оплаты на любые темы
бесплатная юридическая поддержка для частных лиц и организаций по разнообразным вопросам юриспруденции от опытных юристов|Получи бесплатное консультирование от опытных юристов по любым проблемам
Консультации юристов бесплатно: оспорьте незаконные действия соседей
нужна юридическая помощь бесплатно http://www.konsultaciya-yurista-499.ru/.
Бесплатная помощь юриста
сколько стоит адвокат по уголовным делам в москве lawyer-uslugi.ru.
Получите бесплатную юридическую консультацию по телефону способ получить Экономьте лишних трат на юридические услуги с помощью бесплатной консультации
Как защитить собственные права без затрат на юридические услуги?
Свободная юридическая консультация 24/7 под рукой
Куда обратиться бесплатную юридическую помощь?
Узнавайте свои юридические вопросы экономно с бесплатной консультацией
Ищете консультацию? Получите бесплатную юридическую помощь прямо сейчас
Сберегите свои права с бесплатной юридической консультацией
Что делать в сложной юридической ситуации? Получите бесплатную консультацию и решите проблему
Полное пояснение правового вопроса с помощью квалифицированных юристов
Как защитить свою правоту? Получите юридическую консультацию на тему бесплатно
Гонорары юристов не всегда оправданы, узнайте, как получить бесплатную консультацию
Усложнилась юридическая ситуация? Получите бесплатную юридическую поддержку
Советы юридических экспертов вам доступны бесплатно
Как защитить документы без юриста? Получите бесплатную консультацию и сэкономьте
Нужна юридическая вопроса? Получите бесплатную консультацию от Профессионалов
Безопасно получите бесплатную юридическую консультацию онлайн с помощью бесплатной юридической консультации
Нужна комплексная юридическая помощь? Получите бесплатную консультацию
Доступная юридическая консультация по целому ряду вопросов
Не откладывайте – получите бесплатную помощь от лучших юристов
Арбитражный юрист с опытом защиты интересов клиентов
отзыв арбитражный адвокат https://www.advocate-uslugi.ru/.
Качественная консультация по наследству от эксперта
сколько стоит адвокат по наследству http://www.nasledstvennyye-dela-v-moskve.ru/.
https://amoxil.icu/# generic amoxicillin 500mg
can i buy cheap clomid for sale how to buy cheap clomid no prescription – cost of clomid prices
http://amoxil.icu/# amoxicillin 500mg capsule
buying clomid tablets where to get cheap clomid – can i buy clomid without rx
https://amoxil.icu/# amoxicillin 250 mg price in india
can i get generic clomid price: can i purchase generic clomid – cost generic clomid
https://ciprofloxacin.life/# buy generic ciprofloxacin
https://ciprofloxacin.life/# where can i buy cipro online
prednisone prescription for sale: where can i buy prednisone – buy prednisone from canada
prednisone 20mg tab price: purchase prednisone – prednisone online australia
московские юристы консультация бесплатная https://konsultaciya-yurista5.ru.
https://zithromaxbestprice.icu/# zithromax tablets for sale
https://cytotec.icu/# cytotec abortion pill
who should take tamoxifen: tamoxifen breast cancer – tamoxifen endometriosis
buy cytotec online: buy cytotec over the counter – buy cytotec pills
buy doxycycline online 270 tabs: order doxycycline 100mg without prescription – doxycycline hyc
buy 20mg lisinopril: prinivil coupon – over the counter lisinopril
zithromax 500 mg lowest price pharmacy online: zithromax prescription in canada – generic zithromax over the counter
can you buy zithromax over the counter in australia: cheap zithromax pills – generic zithromax medicine
buy cytotec: buy cytotec over the counter – buy cytotec in usa
buy doxycycline without prescription uk: doxycycline 50 mg – doxycycline hyclate
https://cytotec.icu/# Misoprostol 200 mg buy online
mexico drug stores pharmacies: Mexico pharmacy online – mexico pharmacies prescription drugs mexicopharm.com
indian pharmacy paypal India Post sending medicines to USA buy prescription drugs from india indiapharm.llc
best india pharmacy: India pharmacy of the world – buy prescription drugs from india indiapharm.llc
http://mexicopharm.com/# buying from online mexican pharmacy mexicopharm.com
medication from mexico pharmacy Purple Pharmacy online ordering mexican mail order pharmacies mexicopharm.com
Автоюристы – ваша надежда на справедливость в автомобильных спорах
автоюрист оплата по результату http://avtoyurist-moskva1.ru/.
canadian pharmacy no scripts: canada pharmacy online – pharmacy com canada canadapharm.life
buy prescription drugs from india: Online medicine order – indianpharmacy com indiapharm.llc
reputable canadian pharmacy: Canada pharmacy online – canadian pharmacy oxycodone canadapharm.life
reliable canadian pharmacy reviews Canadian pharmacy best prices canadian pharmacy price checker canadapharm.life
best canadian pharmacy online: Canadian pharmacy best prices – buying drugs from canada canadapharm.life
maple leaf pharmacy in canada: Canada pharmacy online – canadian pharmacy ltd canadapharm.life
buy sildenafil 20 mg: sildenafil without a doctor prescription Canada – cheap sildenafil 100
cheap sildenafil citrate Buy generic 100mg Sildenafil online sildenafil prescription cost
tadalafil 20 mg best price: tadalafil online canada – tadalafil 22 mg
ed pills that work: erectile dysfunction drug – best ed pills
buy kamagra online usa cheap kamagra buy kamagra online usa
tadalafil online 10mg: Tadalafil 20mg price in Canada – buy tadalafil over the counter
sildenafil 150 mg: Cheapest Sildenafil online – sildenafil 50 mg mexico
Vardenafil price: Levitra best price – Levitra 20 mg for sale
non prescription ed drugs: erection pills over the counter – what is the best ed pill
http://edpillsdelivery.pro/# erectile dysfunction pills
tadalafil 10mg generic tadalafil without prescription generic tadalafil without prescription
http://tadalafildelivery.pro/# tadalafil generic us
Levitra 20 mg for sale: Buy generic Levitra online – Levitra 10 mg buy online
http://stromectol.guru/# ivermectin pills human
paxlovid buy Buy Paxlovid privately paxlovid price
https://prednisone.auction/# prednisone best prices
Paxlovid over the counter paxlovid pharmacy paxlovid india
how to get cheap clomid without rx: where buy cheap clomid without insurance – get cheap clomid without insurance
https://amoxil.guru/# amoxicillin 500mg without prescription
cheap prednisone online: buy prednisone from canada – prednisone 20mg capsule
https://furosemide.pro/# lasix 100mg
zithromax pill: cheapest azithromycin – zithromax 500mg
get generic propecia without a prescription: Best place to buy propecia – cost of propecia tablets
buy cytotec over the counter Buy Abortion Pills Online cytotec abortion pill
http://finasteride.men/# generic propecia without a prescription
Abortion pills online: buy cytotec online – cytotec buy online usa
cytotec pills buy online: buy cytotec online – п»їcytotec pills online
https://azithromycin.store/# zithromax without prescription
buy zithromax canada: zithromax best price – zithromax 500 mg lowest price online
https://furosemide.pro/# furosemide 40mg
lisinopril pill 5 mg: buy lisinopril online – cost of lisinopril 20 mg
lisinopril tablets: High Blood Pressure – lisinopril 10mg
lisinopril generic drug: over the counter lisinopril – prinivil 5mg tablet
http://misoprostol.shop/# Cytotec 200mcg price
lisinopril 12.5 tablet: over the counter lisinopril – lisinopril 40 mg prices
http://azithromycin.store/# zithromax 500mg
zithromax for sale 500 mg: buy zithromax over the counter – zithromax online usa
buy zithromax online cheap: buy zithromax z-pak online – zithromax azithromycin
lisinopril 5 mg tabs: cheapest lisinopril – price lisinopril 20 mg
http://azithromycin.store/# zithromax online paypal
2 prinivil: over the counter lisinopril – where to buy lisinopril online
http://finasteride.men/# cost generic propecia prices
https://lisinopril.fun/# lisinopril 80
acquistare farmaci senza ricetta: Avanafil farmaco – farmacie online autorizzate elenco
farmacia online migliore: cialis generico consegna 48 ore – farmacie on line spedizione gratuita
https://kamagraitalia.shop/# farmacie online autorizzate elenco
farmacia online: kamagra oral jelly consegna 24 ore – farmacie online autorizzate elenco
https://farmaciaitalia.store/# farmacie online affidabili
acquisto farmaci con ricetta: kamagra oral jelly consegna 24 ore – acquistare farmaci senza ricetta
farmacia online miglior prezzo: avanafil prezzo in farmacia – farmacia online senza ricetta
farmacia online piГ№ conveniente: dove acquistare cialis online sicuro – farmaci senza ricetta elenco
farmacia online piГ№ conveniente: avanafil prezzo in farmacia – farmacie on line spedizione gratuita
http://farmaciaitalia.store/# farmacia online migliore
acquisto farmaci con ricetta: kamagra gel – comprare farmaci online con ricetta
https://tadalafilitalia.pro/# migliori farmacie online 2023
farmacia online miglior prezzo: avanafil prezzo in farmacia – acquisto farmaci con ricetta
https://sildenafilitalia.men/# viagra naturale in farmacia senza ricetta
viagra originale recensioni: viagra prezzo – pillole per erezione immediata
https://farmaciaitalia.store/# farmacia online migliore
farmacia online senza ricetta: avanafil prezzo in farmacia – farmacie online autorizzate elenco
viagra generico sandoz: sildenafil 100mg prezzo – miglior sito dove acquistare viagra
farmacia online kamagra farmacia online
http://avanafilitalia.online/# farmacie online sicure
http://indiapharm.life/# buy prescription drugs from india
pharmacy website india: india pharmacy mail order – online shopping pharmacy india
https://indiapharm.life/# reputable indian pharmacies
canadian discount pharmacy buy prescription drugs from canada cheap global pharmacy canada
pharmacy website india: india pharmacy – indian pharmacy
medication canadian pharmacy: canadian pharmacy cheap – canadian pharmacy online
http://canadapharm.shop/# canadian pharmacy
buy prescription drugs from india: buy prescription drugs from india – Online medicine order
https://canadapharm.shop/# buy prescription drugs from canada cheap
mexican mail order pharmacies: medication from mexico pharmacy – medicine in mexico pharmacies
canadian pharmacy meds: canada pharmacy world – canadian pharmacy in canada
canadian pharmacy online ship to usa: buy drugs from canada – canada pharmacy online legit
mexico drug stores pharmacies: purple pharmacy mexico price list – buying from online mexican pharmacy
mexican border pharmacies shipping to usa mexican rx online buying prescription drugs in mexico
http://indiapharm.life/# indian pharmacy paypal
online pharmacy canada: canadian pharmacy online store – medication canadian pharmacy
http://indiapharm.life/# reputable indian online pharmacy
pharmacies in mexico that ship to usa: mexico drug stores pharmacies – п»їbest mexican online pharmacies
online pharmacy canada: pharmacies in canada that ship to the us – best rated canadian pharmacy
https://canadapharm.shop/# reddit canadian pharmacy
pharmacies in mexico that ship to usa: purple pharmacy mexico price list – reputable mexican pharmacies online
https://mexicanpharm.store/# mexico pharmacies prescription drugs
mexican rx online: mexican pharmaceuticals online – mexican border pharmacies shipping to usa
my canadian pharmacy reviews: canada drugs online reviews – certified canadian international pharmacy
mexico pharmacies prescription drugs mexican online pharmacies prescription drugs mexican pharmaceuticals online
https://indiapharm.life/# indian pharmacy online
best online pharmacies in mexico: mexican border pharmacies shipping to usa – mexican online pharmacies prescription drugs
online canadian pharmacy review: pharmacy rx world canada – legitimate canadian pharmacy online
https://canadapharm.shop/# is canadian pharmacy legit
indian pharmacies safe: online shopping pharmacy india – cheapest online pharmacy india
https://mexicanpharm.store/# medicine in mexico pharmacies
india pharmacy mail order: buy medicines online in india – reputable indian online pharmacy
Online medicine order: best india pharmacy – india pharmacy mail order
http://indiapharm.life/# india online pharmacy
top 10 online pharmacy in india indian pharmacy online pharmacy india
http://nolvadex.pro/# where to get nolvadex
http://clomidpharm.shop/# can i get cheap clomid now
nolvadex 10mg: tamoxifen for breast cancer prevention – nolvadex steroids
https://clomidpharm.shop/# can i buy clomid online
buy cytotec: cytotec pills online – cytotec online
http://clomidpharm.shop/# get generic clomid without dr prescription
generic zithromax 500mg india: zithromax over the counter canada – can i buy zithromax over the counter in canada
https://prednisonepharm.store/# prednisone brand name
buy prednisone online uk: prednisone 20 mg without prescription – prednisone 2.5 mg tab
prednisone 50 mg buy prednisone 20mg online without prescription prednisone without prescription.net
https://clomidpharm.shop/# order generic clomid without insurance
buy misoprostol over the counter: buy cytotec pills – order cytotec online
https://zithromaxpharm.online/# zithromax over the counter uk
cytotec pills online: Abortion pills online – buy cytotec online
https://zithromaxpharm.online/# zithromax z-pak
http://edwithoutdoctorprescription.store/# non prescription ed drugs
https://edwithoutdoctorprescription.store/# viagra without a doctor prescription walmart
order drugs online: canada prescription – overseas pharmacies
http://reputablepharmacies.online/# canadian pharmacy drugstore
legitimate mexican pharmacy online: canadian online pharmacy – online pharmacies canada reviews
http://edpills.bid/# online ed pills
real viagra without a doctor prescription: ed meds online without doctor prescription – prescription drugs
http://edwithoutdoctorprescription.store/# prescription drugs online without doctor
https://edwithoutdoctorprescription.store/# 100mg viagra without a doctor prescription
prescription drugs without doctor approval: legal to buy prescription drugs without prescription – buy prescription drugs online without
buy prescription drugs without doctor: real viagra without a doctor prescription – best ed pills non prescription
http://edpills.bid/# mens ed pills
prescriptions canada: good online mexican pharmacy – canadian pharmacy canada
http://edpills.bid/# new ed drugs
https://reputablepharmacies.online/# canadian pharmacy world reviews
cialis without a doctor’s prescription: viagra without a doctor prescription – prescription without a doctor’s prescription
https://edwithoutdoctorprescription.store/# prescription meds without the prescriptions
buy prescription drugs without doctor: viagra without doctor prescription amazon – 100mg viagra without a doctor prescription
http://canadianpharmacy.pro/# legitimate canadian mail order pharmacy canadianpharmacy.pro
buying prescription drugs in mexico online: Medicines Mexico – best online pharmacies in mexico mexicanpharmacy.win
http://canadianpharmacy.pro/# canadian pharmacy king reviews canadianpharmacy.pro
canadian pharmacy shop
mexican pharmacy Mexico pharmacy mexican border pharmacies shipping to usa mexicanpharmacy.win
https://indianpharmacy.shop/# best online pharmacy india indianpharmacy.shop
legitimate canadian pharmacy online: pharmacy rx world canada – canadian pharmacy scam canadianpharmacy.pro
medication from mexico pharmacy online mexican pharmacy buying prescription drugs in mexico online mexicanpharmacy.win
http://canadianpharmacy.pro/# canadian world pharmacy canadianpharmacy.pro
п»їbest mexican online pharmacies mexico drug stores pharmacies mexican mail order pharmacies mexicanpharmacy.win
http://canadianpharmacy.pro/# canadian pharmacy ratings canadianpharmacy.pro
canadian prescription drug prices
http://canadianpharmacy.pro/# canadian drugs canadianpharmacy.pro
best online pharmacies in mexico Mexico pharmacy mexican online pharmacies prescription drugs mexicanpharmacy.win
http://indianpharmacy.shop/# india pharmacy mail order
cheapest online pharmacy india
http://indianpharmacy.shop/# online pharmacy india
indian pharmacy paypal
https://canadianpharmacy.pro/# certified canadian international pharmacy canadianpharmacy.pro
https://indianpharmacy.shop/# indianpharmacy com indianpharmacy.shop
buy medicines online in india indian pharmacy online pharmacy india indianpharmacy.shop
https://indianpharmacy.shop/# india online pharmacy indianpharmacy.shop
http://canadianpharmacy.pro/# canadian pharmacy ratings canadianpharmacy.pro
Online medicine home delivery
online canadian pharmacy canadian world pharmacy canadian pharmacy 365 canadianpharmacy.pro
http://mexicanpharmacy.win/# mexican border pharmacies shipping to usa mexicanpharmacy.win
ed meds online without doctor prescription
http://mexicanpharmacy.win/# mexican drugstore online mexicanpharmacy.win
top online pharmacy india
https://canadianpharmacy.pro/# buy prescription drugs from canada cheap canadianpharmacy.pro
https://canadianpharmacy.pro/# ordering drugs from canada canadianpharmacy.pro
legal to buy prescription drugs from canada canadapharmacyonline com canadian pharmacy 365 canadianpharmacy.pro
http://mexicanpharmacy.win/# buying prescription drugs in mexico mexicanpharmacy.win
п»їlegitimate online pharmacies india
https://mexicanpharmacy.win/# pharmacies in mexico that ship to usa mexicanpharmacy.win
http://mexicanpharmacy.win/# medication from mexico pharmacy mexicanpharmacy.win
canadian online drugstore Canada Pharmacy global pharmacy canada canadianpharmacy.pro
http://mexicanpharmacy.win/# mexican rx online mexicanpharmacy.win
canadianpharmacymeds com Cheapest drug prices Canada canada drug pharmacy canadianpharmacy.pro
https://mexicanpharmacy.win/# mexican pharmacy mexicanpharmacy.win
best online pharmacy india
http://mexicanpharmacy.win/# best mexican online pharmacies mexicanpharmacy.win
https://mexicanpharmacy.win/# medication from mexico pharmacy mexicanpharmacy.win
pharmacy online canada
top 10 online pharmacy in india indian pharmacy to usa online pharmacy india indianpharmacy.shop
https://mexicanpharmacy.win/# mexican mail order pharmacies mexicanpharmacy.win
india online pharmacy
http://mexicanpharmacy.win/# mexico pharmacy mexicanpharmacy.win
Pharmacie en ligne pas cher Acheter Cialis 20 mg pas cher acheter medicament a l etranger sans ordonnance
http://acheterkamagra.pro/# Pharmacie en ligne France
acheter medicament a l etranger sans ordonnance
Pharmacie en ligne livraison 24h: acheterkamagra.pro – Pharmacie en ligne fiable
http://viagrasansordonnance.pro/# Meilleur Viagra sans ordonnance 24h
Pharmacie en ligne fiable: Pharmacies en ligne certifiees – Pharmacie en ligne sans ordonnance
https://pharmadoc.pro/# Acheter médicaments sans ordonnance sur internet
Acheter Sildenafil 100mg sans ordonnance Acheter du Viagra sans ordonnance Viagra vente libre allemagne
Pharmacie en ligne fiable: kamagra 100mg prix – Pharmacie en ligne livraison rapide
https://pharmadoc.pro/# pharmacie ouverte
Pharmacie en ligne livraison rapide
https://levitrasansordonnance.pro/# pharmacie ouverte 24/24
Prix du Viagra 100mg en France viagrasansordonnance.pro Viagra femme sans ordonnance 24h
acheter mГ©dicaments Г l’Г©tranger: Pharmacie en ligne France – Pharmacie en ligne livraison gratuite
https://cialissansordonnance.shop/# Acheter médicaments sans ordonnance sur internet
Pharmacie en ligne livraison rapide: kamagra livraison 24h – Pharmacie en ligne fiable
http://acheterkamagra.pro/# pharmacie ouverte 24/24
Pharmacie en ligne livraison rapide Medicaments en ligne livres en 24h Pharmacie en ligne sans ordonnance
https://pharmadoc.pro/# Pharmacie en ligne livraison gratuite
acheter mГ©dicaments Г l’Г©tranger levitra generique prix en pharmacie acheter mГ©dicaments Г l’Г©tranger
http://levitrasansordonnance.pro/# Pharmacie en ligne pas cher
Pharmacie en ligne livraison rapide
iv prednisone prednisone 1 tablet prednisone sale
https://amoxicillin.bid/# buy amoxicillin without prescription
ivermectin 10 ml: ivermectin iv – ivermectin 3 mg dose
ivermectin 9mg stromectol 3 mg tablet price stromectol price uk
ivermectin purchase: ivermectin 1mg – stromectol over the counter
https://amoxicillin.bid/# can i buy amoxicillin over the counter in australia
online prednisone 50mg prednisone tablet fast shipping prednisone
zithromax 250mg: zithromax over the counter – where can i buy zithromax in canada
http://clomiphene.icu/# where to buy generic clomid pills
zithromax price canada how to get zithromax online zithromax 250 mg tablet price
http://azithromycin.bid/# zithromax buy online
amoxicillin 1000 mg capsule: can i buy amoxicillin over the counter in australia – how to get amoxicillin
https://amoxicillin.bid/# price of amoxicillin without insurance
amoxicillin cephalexin generic for amoxicillin buying amoxicillin online
https://prednisonetablets.shop/# prednisone prices
azithromycin zithromax: buy zithromax without presc – cheap zithromax pills
http://ivermectin.store/# ivermectin uk coronavirus
buy prednisone online india 1250 mg prednisone prednisone 20mg price in india
generic prednisone tablets: how much is prednisone 10 mg – cortisol prednisone
https://ivermectin.store/# stromectol in canada
prednisone best price: prednisone where can i buy – prednisone nz
non prescription prednisone 20mg prednisone 60 mg price prednisone 50 mg coupon
https://clomiphene.icu/# cost cheap clomid online
https://ivermectin.store/# ivermectin stromectol
over the counter prednisone cream: prednisone 10 mg daily – prednisone 10mg tablet price
mexico pharmacy medicine in mexico pharmacies mexican border pharmacies shipping to usa mexicanpharm.shop
canadian pharmacies compare: Certified Online Pharmacy Canada – best rated canadian pharmacy canadianpharm.store
http://indianpharm.store/# buy medicines online in india indianpharm.store
cheapest online pharmacy india order medicine from india to usa indian pharmacy indianpharm.store
mexican pharmacy: mexico drug stores pharmacies – mexico drug stores pharmacies mexicanpharm.shop
https://canadianpharm.store/# canada cloud pharmacy canadianpharm.store
pet meds without vet prescription canada Canadian International Pharmacy best mail order pharmacy canada canadianpharm.store
best india pharmacy: Indian pharmacy to USA – reputable indian online pharmacy indianpharm.store
http://indianpharm.store/# cheapest online pharmacy india indianpharm.store
buying from online mexican pharmacy: mexican drugstore online – buying prescription drugs in mexico online mexicanpharm.shop
https://canadianpharm.store/# canadian pharmacy india canadianpharm.store
mexican drugstore online: mexican rx online – pharmacies in mexico that ship to usa mexicanpharm.shop
http://mexicanpharm.shop/# pharmacies in mexico that ship to usa mexicanpharm.shop
best canadian pharmacy online: online canadian pharmacy – best canadian online pharmacy reviews canadianpharm.store
http://indianpharm.store/# reputable indian pharmacies indianpharm.store
77 canadian pharmacy Canadian Pharmacy canadian pharmacies canadianpharm.store
maple leaf pharmacy in canada: Canadian International Pharmacy – canadian discount pharmacy canadianpharm.store
canadian drug stores: Canada Pharmacy online – precription drugs from canada canadianpharm.store
https://mexicanpharm.shop/# mexican border pharmacies shipping to usa mexicanpharm.shop
canadian pharmacy near me Canada Pharmacy online canadian pharmacy online canadianpharm.store
online pharmacy india: Indian pharmacy to USA – online shopping pharmacy india indianpharm.store
https://canadianpharm.store/# best rated canadian pharmacy canadianpharm.store
https://indianpharm.store/# indian pharmacy indianpharm.store
canadian drug prices: canadianpharmacy com – legit canadian pharmacy online canadianpharm.store
best rated canadian pharmacy Certified Online Pharmacy Canada onlinecanadianpharmacy 24 canadianpharm.store
http://canadianpharm.store/# canadian pharmacy in canada canadianpharm.store
It’s very unreliable, engages in deception scam site
indian pharmacies safe india online pharmacy buy prescription drugs from india
Настоящий официальный канал 1Win зеркало
https://certifiedpharmacymexico.pro/# best mexican online pharmacies
india pharmacy mail order: top 10 pharmacies in india – best online pharmacy india
mexico drug stores pharmacies purple pharmacy mexico price list pharmacies in mexico that ship to usa
herbal ed treatment: medication for ed dysfunction – men’s ed pills
https://canadianinternationalpharmacy.pro/# canada pharmacy 24h
Рекомендую официальный телеграм канал на 1Win вход
purple pharmacy mexico price list medication from mexico pharmacy mexico pharmacies prescription drugs
http://medicinefromindia.store/# indianpharmacy com
impotence pills buy ed pills ed pills gnc
https://canadianinternationalpharmacy.pro/# legal to buy prescription drugs from canada
medication from mexico pharmacy mexican drugstore online mexican border pharmacies shipping to usa
http://medicinefromindia.store/# online shopping pharmacy india
canadian family pharmacy canada rx pharmacy best canadian online pharmacy reviews
http://canadianinternationalpharmacy.pro/# certified canadian international pharmacy
reputable indian pharmacies indian pharmacy paypal mail order pharmacy india
http://medicinefromindia.store/# Online medicine order
rate canadian pharmacies canadian pharmacy review pharmacy canadian superstore
http://certifiedpharmacymexico.pro/# mexican pharmacy
http://edpill.cheap/# non prescription ed drugs
http://edpill.cheap/# compare ed drugs
http://edpill.cheap/# best erectile dysfunction pills
new treatments for ed pills erectile dysfunction best over the counter ed pills
https://edpill.cheap/# ed remedies
reputable indian online pharmacy mail order pharmacy india indianpharmacy com
https://medicinefromindia.store/# cheapest online pharmacy india
world pharmacy india top 10 pharmacies in india world pharmacy india
https://medicinefromindia.store/# reputable indian pharmacies
http://edwithoutdoctorprescription.pro/# buy prescription drugs without doctor
best mail order pharmacy canada canadian drug pharmacy canadianpharmacymeds com
http://edpill.cheap/# cheap ed drugs
canadian pharmacy king online canadian pharmacy review best canadian online pharmacy
https://canadianinternationalpharmacy.pro/# cross border pharmacy canada
http://medicinefromindia.store/# indian pharmacy paypal
best male ed pills erectile dysfunction medicines otc ed pills
https://edpill.cheap/# herbal ed treatment
canadian pharmacy king safe canadian pharmacy safe online pharmacies in canada
http://canadianinternationalpharmacy.pro/# global pharmacy canada
pharmacies in mexico that ship to usa purple pharmacy mexico price list mexican online pharmacies prescription drugs
mexico drug stores pharmacies purple pharmacy mexico price list buying from online mexican pharmacy
purple pharmacy mexico price list buying prescription drugs in mexico mexico drug stores pharmacies
reputable mexican pharmacies online buying from online mexican pharmacy mexican mail order pharmacies
purple pharmacy mexico price list purple pharmacy mexico price list mexican mail order pharmacies
pharmacies in mexico that ship to usa reputable mexican pharmacies online mexico drug stores pharmacies
mexican pharmaceuticals online mexican border pharmacies shipping to usa medication from mexico pharmacy
mexico pharmacy pharmacies in mexico that ship to usa medicine in mexico pharmacies
mexico pharmacies prescription drugs medicine in mexico pharmacies reputable mexican pharmacies online
best online pharmacies in mexico buying prescription drugs in mexico online mexican mail order pharmacies
mexican mail order pharmacies buying prescription drugs in mexico online п»їbest mexican online pharmacies
purple pharmacy mexico price list mexican online pharmacies prescription drugs pharmacies in mexico that ship to usa
mexico pharmacies prescription drugs buying from online mexican pharmacy mexico drug stores pharmacies
mexico drug stores pharmacies mexican drugstore online mexican pharmaceuticals online
mexican drugstore online mexico drug stores pharmacies mexican mail order pharmacies
reputable mexican pharmacies online mexican drugstore online pharmacies in mexico that ship to usa
mexico pharmacies prescription drugs mexico drug stores pharmacies purple pharmacy mexico price list
mexico drug stores pharmacies mexican drugstore online purple pharmacy mexico price list
medicine in mexico pharmacies mexico drug stores pharmacies medication from mexico pharmacy
buying prescription drugs in mexico online purple pharmacy mexico price list mexico drug stores pharmacies
mexican drugstore online best mexican online pharmacies reputable mexican pharmacies online
pharmacies in mexico that ship to usa mexico pharmacies prescription drugs mexico pharmacies prescription drugs
mexican pharmacy medication from mexico pharmacy pharmacies in mexico that ship to usa
mexico pharmacies prescription drugs mexican drugstore online mexico pharmacy
mexico pharmacies prescription drugs mexican rx online reputable mexican pharmacies online
mexican online pharmacies prescription drugs buying prescription drugs in mexico best online pharmacies in mexico
medicine in mexico pharmacies mexican pharmaceuticals online mexican pharmacy
mexico drug stores pharmacies best mexican online pharmacies medication from mexico pharmacy
https://mexicanph.com/# mexican border pharmacies shipping to usa
mexico drug stores pharmacies
best mexican online pharmacies mexican rx online mexican drugstore online
best online pharmacies in mexico pharmacies in mexico that ship to usa mexican rx online
mexico pharmacy mexican mail order pharmacies mexican pharmacy
best online pharmacies in mexico mexico pharmacy buying prescription drugs in mexico
mexican border pharmacies shipping to usa mexican border pharmacies shipping to usa mexican rx online
medicine in mexico pharmacies reputable mexican pharmacies online best online pharmacies in mexico
http://mexicanph.shop/# buying prescription drugs in mexico online
pharmacies in mexico that ship to usa
medicine in mexico pharmacies mexican drugstore online buying prescription drugs in mexico online
best online pharmacies in mexico purple pharmacy mexico price list mexican pharmacy
buying from online mexican pharmacy mexican drugstore online mexican online pharmacies prescription drugs
mexican online pharmacies prescription drugs mexican drugstore online mexican online pharmacies prescription drugs
п»їbest mexican online pharmacies mexican mail order pharmacies mexican pharmacy
mexican rx online mexico pharmacies prescription drugs mexico pharmacies prescription drugs
reputable mexican pharmacies online mexican pharmacy mexican drugstore online
mexico drug stores pharmacies mexico drug stores pharmacies reputable mexican pharmacies online
reputable mexican pharmacies online mexican drugstore online mexican border pharmacies shipping to usa
mexican rx online buying prescription drugs in mexico online mexico drug stores pharmacies
best online pharmacies in mexico best online pharmacies in mexico mexican pharmaceuticals online
mexican border pharmacies shipping to usa mexican rx online mexico pharmacies prescription drugs
mexico pharmacies prescription drugs mexican drugstore online pharmacies in mexico that ship to usa
mexican mail order pharmacies mexican pharmaceuticals online mexican rx online
http://lisinopril.top/# lisinopril 12.5 mg
ivermectin 3mg: ivermectin 3mg – ivermectin 6
https://stromectol.fun/# generic ivermectin
http://stromectol.fun/# stromectol cvs
amoxicillin medicine over the counter: amoxicillin buy canada – amoxicillin without prescription
http://furosemide.guru/# furosemide 40mg
amoxicillin online pharmacy: where can i buy amoxicillin online – amoxicillin 875 mg tablet
http://amoxil.cheap/# order amoxicillin 500mg
https://amoxil.cheap/# where to buy amoxicillin over the counter
https://lisinopril.top/# lisinopril 10mg online
stromectol price: stromectol 3 mg – ivermectin tablets uk
https://furosemide.guru/# lasix furosemide
can i order lisinopril online: prinivil drug cost – lisinopril 40 mg canada
http://stromectol.fun/# п»їwhere to buy stromectol online
lasix 20 mg: Over The Counter Lasix – lasix online
http://amoxil.cheap/# amoxicillin azithromycin
amoxicillin order online no prescription: where can i get amoxicillin – amoxicillin 500mg price
http://amoxil.cheap/# prescription for amoxicillin
prednisone brand name us: buy prednisone nz – apo prednisone
http://lisinopril.top/# zestril 5 mg prices
lasix online: lasix furosemide – lasix for sale
http://furosemide.guru/# lasix dosage
lasix 100mg: Buy Lasix No Prescription – lasix 20 mg
http://buyprednisone.store/# can i buy prednisone online without a prescription
can you buy amoxicillin over the counter in canada: amoxicillin 30 capsules price – amoxicillin 500mg no prescription
https://stromectol.fun/# ivermectin 500ml
average cost of prednisone 20 mg: 100 mg prednisone daily – order prednisone 10mg
https://furosemide.guru/# lasix tablet
https://furosemide.guru/# lasix furosemide 40 mg
https://amoxil.cheap/# order amoxicillin online uk
https://furosemide.guru/# generic lasix
lasix tablet: Buy Lasix – lasix
prednisone price: prednisone 5 50mg tablet price – 20mg prednisone
https://buyprednisone.store/# prednisone 5 mg brand name
https://stromectol.fun/# ivermectin 400 mg brands
ivermectin 2mg: stromectol 3 mg dosage – ivermectin 8 mg
https://lisinopril.top/# zestoretic 25
furosemida: Buy Lasix No Prescription – lasix for sale
http://lisinopril.top/# cost for generic lisinopril
http://amoxil.cheap/# amoxicillin 500
http://amoxil.cheap/# cost of amoxicillin prescription
prednisone 20 mg generic: prednisone 2.5 mg tab – prednisone 5mg daily
https://lisinopril.top/# buy lisinopril online canada
ivermectin 1%: ivermectin 3mg tablets – ivermectin lotion for lice
https://furosemide.guru/# lasix 100 mg tablet
https://lisinopril.top/# zestril lisinopril
prednisone 300mg: prednisone coupon – prednisone tabs 20 mg
http://stromectol.fun/# stromectol cream
http://furosemide.guru/# lasix 100mg
prednisone pills cost: 5 prednisone in mexico – order prednisone on line
amoxicillin 500mg buy online canada: order amoxicillin online uk – amoxicillin 500 mg cost
https://lisinopril.top/# lisinopril 419
http://buyprednisone.store/# where can i buy prednisone online without a prescription
lasix online: lasix – lasix dosage
Your insights into the tactics used by cybercriminals to deceive users and gain unauthorized access to sensitive information were incredibly valuable.
Online medicine home delivery reputable indian online pharmacy reputable indian online pharmacy
http://indianph.xyz/# india online pharmacy
best online pharmacy india
http://indianph.com/# best india pharmacy
http://indianph.com/# best india pharmacy
mail order pharmacy india
https://indianph.xyz/# top online pharmacy india
indian pharmacy paypal
http://indianph.xyz/# best online pharmacy india
reputable indian pharmacies
https://indianph.xyz/# legitimate online pharmacies india
best online pharmacy india
http://indianph.com/# indianpharmacy com
pharmacy website india
https://indianph.xyz/# buy medicines online in india
buy prescription drugs from india
how to buy doxycycline online: buy doxycycline online 270 tabs – doxycycline 100mg capsules
http://cytotec24.shop/# buy cytotec online
https://nolvadex.guru/# low dose tamoxifen
buy cytotec pills: order cytotec online – cytotec pills buy online
https://cytotec24.com/# buy cytotec pills online cheap
doxycycline generic: buy doxycycline without prescription – order doxycycline
http://diflucan.pro/# diflucan cost canada
https://diflucan.pro/# diflucan 150 tab
buy ciprofloxacin over the counter: buy cipro – ciprofloxacin generic
http://diflucan.pro/# how much is a diflucan pill
ciprofloxacin order online: cipro online no prescription in the usa – cipro pharmacy
diflucan generic cost: diflucan 150 mg canada – diflucan 200
sweeti fox: Sweetie Fox filmleri – sweety fox
lana rhodes: lana rhodes – lana rhoades
lana rhoades: lana rhoades filmleri – lana rhoades modeli
Sweetie Fox filmleri: Sweetie Fox video – Sweetie Fox modeli
Angela White: Angela White izle – Angela White izle
eva elfie izle: eva elfie – eva elfie izle
?????? ????: abella danger izle – Abella Danger
http://abelladanger.online/# abella danger izle
eva elfie izle: eva elfie modeli – eva elfie
https://evaelfie.pro/# eva elfie
http://lanarhoades.fun/# lana rhoades
swetie fox: Sweetie Fox – Sweetie Fox
http://angelawhite.pro/# Angela White
lana rhoades filmleri: lana rhoades – lana rhoades video
http://abelladanger.online/# abella danger video
Angela White izle: ?????? ???? – Angela White
http://lanarhoades.fun/# lana rhoades filmleri
http://angelawhite.pro/# Angela White
Sweetie Fox modeli: Sweetie Fox video – sweeti fox
Sweetie Fox izle: Sweetie Fox filmleri – Sweetie Fox izle
http://sweetiefox.online/# sweeti fox
https://miamalkova.life/# mia malkova videos
lana rhoades unleashed: lana rhoades full video – lana rhoades unleashed
https://miamalkova.life/# mia malkova new video
http://sweetiefox.pro/# sweetie fox cosplay
http://evaelfie.site/# eva elfie hd
sweetie fox full video: sweetie fox – sweetie fox full
http://evaelfie.site/# eva elfie hd
fox sweetie: fox sweetie – sweetie fox cosplay
https://lanarhoades.pro/# lana rhoades solo
fox sweetie: fox sweetie – fox sweetie
mia malkova new video: mia malkova only fans – mia malkova latest
https://lanarhoades.pro/# lana rhoades boyfriend
https://sweetiefox.pro/# sweetie fox video
lana rhoades videos: lana rhoades pics – lana rhoades unleashed
https://lanarhoades.pro/# lana rhoades full video
sweetie fox new: sweetie fox full video – sweetie fox new
eva elfie videos: eva elfie hot – eva elfie new video
https://lanarhoades.pro/# lana rhoades pics
https://sweetiefox.pro/# sweetie fox video
lana rhoades solo: lana rhoades pics – lana rhoades videos
mia malkova videos: mia malkova girl – mia malkova movie
https://sweetiefox.pro/# sweetie fox video
https://sweetiefox.pro/# sweetie fox new
http://jogodeaposta.fun/# aplicativo de aposta
aviator oyna slot: aviator sinyal hilesi – aviator hilesi
https://aviatorghana.pro/# aviator bet
aviator bet: aviator ghana – aviator sportybet ghana
aviator game: aviator betano – jogar aviator Brasil
http://aviatormalawi.online/# aviator betting game
aviator sportybet ghana: aviator game bet – aviator ghana
http://aviatorjogar.online/# aviator jogar
pin-up casino entrar: pin up aviator – pin-up cassino
https://jogodeaposta.fun/# aviator jogo de aposta
aviator oyna: aviator oyunu – aviator oyunu
aviator login: aviator game – aviator game online
aviator bahis: aviator oyna – aviator bahis
estrela bet aviator: aviator jogar – aviator jogo
aviator: aviator betting game – aviator betting game
zithromax for sale us: zithromax with alcohol buy cheap generic zithromax
aviator jogar: aviator jogo – jogar aviator online
pin up bet: cassino pin up – pin up bet
can you buy zithromax over the counter – https://azithromycin.pro/zithromax-non-prescription.html buy zithromax online fast shipping
zithromax 250 price: zithromax warnings zithromax generic price
pin up bet: pin-up casino entrar – pin-up
zithromax 500mg price: zithromax generic cost – purchase zithromax z-pak
mexican drugstore online: Mexico pharmacy online – mexican border pharmacies shipping to usa mexicanpharm.shop
purple pharmacy mexico price list: Mexico pharmacy price list – mexican border pharmacies shipping to usa mexicanpharm.shop
https://indianpharm24.com/# indian pharmacy online indianpharm.store
https://indianpharm24.com/# world pharmacy india indianpharm.store
https://mexicanpharm24.shop/# purple pharmacy mexico price list mexicanpharm.shop
world pharmacy india: Generic Medicine India to USA – india pharmacy indianpharm.store
http://mexicanpharm24.com/# best mexican online pharmacies mexicanpharm.shop
https://indianpharm24.shop/# indianpharmacy com indianpharm.store
http://mexicanpharm24.shop/# buying prescription drugs in mexico mexicanpharm.shop
mexico pharmacy: order online from a Mexican pharmacy – mexican online pharmacies prescription drugs mexicanpharm.shop
https://indianpharm24.shop/# online shopping pharmacy india indianpharm.store
http://mexicanpharm24.com/# pharmacies in mexico that ship to usa mexicanpharm.shop
http://canadianpharmlk.com/# canadian 24 hour pharmacy canadianpharm.store
http://indianpharm24.com/# buy medicines online in india indianpharm.store
https://amoxilst.pro/# buy amoxicillin canada
http://clomidst.pro/# can i order generic clomid tablets
https://prednisonest.pro/# no prescription online prednisone
http://amoxilst.pro/# order amoxicillin 500mg
https://prednisonest.pro/# prednisone pills cost
https://prednisonest.pro/# prednisone pharmacy prices
http://edpills.guru/# ed online pharmacy
https://edpills.guru/# order ed meds online
http://edpills.guru/# ed meds on line
http://pharmnoprescription.pro/# no prescription online pharmacy
http://pharmnoprescription.pro/# online pharmacy no prescription needed
https://pharmnoprescription.pro/# online pharmacy canada no prescription
Discover the pinnacle of companionship with our elite Allahabad Call Girls. We offer unparalleled satisfaction and indulgence through our carefully curated selection of companions. With a commitment to excellence and discretion, we guarantee unforgettable experiences for those seeking the best in companionship and pleasure
Experience the epitome of companionship with our prestigious MG Road Escorts We provide unmatched satisfaction and luxury with our handpicked selection of companions. Committed to excellence and discretion, we assure unforgettable experiences for those seeking the ultimate in companionship and pleasure
http://canadianpharm.guru/# pharmacies in canada that ship to the us
https://pharmacynoprescription.pro/# buying prescription drugs online without a prescription
https://pharmacynoprescription.pro/# online pharmacy reviews no prescription
https://indianpharm.shop/# online shopping pharmacy india
http://pharmacynoprescription.pro/# buy prescription drugs without a prescription
http://canadianpharm.guru/# canadian pharmacy checker
https://mexicanpharm.online/# mexican pharmaceuticals online
https://canadianpharm.guru/# canadian pharmacy 365
https://pharmacynoprescription.pro/# canadian prescription prices
https://pharmacynoprescription.pro/# online pharmacy with prescription
http://indianpharm.shop/# world pharmacy india
https://pharmacynoprescription.pro/# overseas online pharmacy-no prescription
https://indianpharm.shop/# indian pharmacies safe
http://pharmacynoprescription.pro/# canadian prescription drugstore review
aviator oyunu 20 tl: aviator bahis – aviator oyunu 50 tl
pin-up casino giris: pin up giris – pin-up giris
pragmatic play gates of olympus: gates of olympus slot – gates of olympus demo turkce oyna
gates of olympus taktik: gates of olympus oyna demo – gates of olympus demo turkce
aviator oyna: aviator hile – aviator oyna 20 tl
gates of olympus 1000 demo: gates of olympus nas?l para kazanilir – gates of olympus max win
sweet bonanza bahis: sweet bonanza oyna – sweet bonanza 90 tl
guvenilir slot siteleri: en iyi slot siteleri 2024 – en cok kazandiran slot siteleri
casino slot siteleri: oyun siteleri slot – yeni slot siteleri
aviator oyunu 10 tl: aviator hilesi ucretsiz – aviator hile
http://gatesofolympus.auction/# gates of olympus demo
buy prescription drugs from india: Generic Medicine India to USA – indian pharmacy paypal
canadian pharmacy meds: Prescription Drugs from Canada – canadian valley pharmacy
legitimate canadian pharmacies: pills now even cheaper – canadian world pharmacy
canadian pharmacy meds review: Prescription Drugs from Canada – canadian online drugs
cheap canadian pharmacy online: Licensed Canadian Pharmacy – canadian pharmacy service
http://kamagraiq.com/# super kamagra
https://tadalafiliq.shop/# Buy Tadalafil 20mg
http://tadalafiliq.shop/# Cialis without a doctor prescription
https://tadalafiliq.com/# buy cialis pill
https://tadalafiliq.com/# Generic Cialis price
http://sildenafiliq.com/# Generic Viagra online
http://mexicanpharmgrx.com/# buying prescription drugs in mexico
https://canadianpharmgrx.xyz/# canada pharmacy 24h
http://mexicanpharmgrx.shop/# mexican mail order pharmacies
http://indianpharmgrx.com/# top 10 online pharmacy in india
https://canadianpharmgrx.com/# best mail order pharmacy canada
http://canadianpharmgrx.xyz/# best canadian pharmacy
http://mexicanpharmgrx.shop/# reputable mexican pharmacies online
doxy 200: doxycycline hyclate 100 mg cap – doxycycline medication
tamoxifen and weight loss: tamoxifen cancer – tamoxifen side effects forum
cytotec online: cytotec buy online usa – Abortion pills online
Abortion pills online: Abortion pills online – Misoprostol 200 mg buy online
doxycycline 100mg online: doxycycline monohydrate – order doxycycline 100mg without prescription
buy doxycycline online uk: doxycycline prices – 200 mg doxycycline
fluconazole diflucan: price of diflucan in south africa – how much is diflucan over the counter
azithromycin amoxicillin: where can i buy amoxicillin over the counter uk – antibiotic amoxicillin
get generic clomid tablets: can you buy clomid – where can i get clomid now
where to get clomid prices: how to get cheap clomid pills – how to buy clomid without prescription
zithromax prescription in canada: where to buy zithromax in canada – azithromycin zithromax
200 mg prednisone daily: 1 mg prednisone daily – buying prednisone mexico
amoxicillin 500mg no prescription: how to buy amoxycillin – purchase amoxicillin online
how can i get generic clomid: cost generic clomid without a prescription – can you get cheap clomid online
http://onlinepharmacyworld.shop/# canadian pharmacy no prescription needed
https://edpill.top/# buy ed pills
https://edpill.top/# ed medicine online
https://medicationnoprescription.pro/# meds no prescription
https://onlinepharmacyworld.shop/# prescription drugs from canada
http://onlinepharmacyworld.shop/# cheapest pharmacy to fill prescriptions without insurance
casino tr?c tuy?n vi?t nam: dánh bài tr?c tuy?n – game c? b?c online uy tín
Great job! Your attention to detail really shines through in this work.
stellar data recovery activation key
https://health-lists.com/story17912359/pin-up-um-dos-maiores-casinos-online-internacionais
Thanks for sharing your thoughts. I really appreciate your efforts and I am waiting for your further write ups thank you once again.
mystroycenter.ru/page/14В
moysamogon.ru/comment-page-30/В
fabnews.ru/forum/showthread.php?p=76998В
fat-girls.ru/page/10В
azat.on.kg/blogs/451/%D0%A1%D0%BA%D0%BE%D0%BB%D1%8C%D0%BA%D0%BE-%D1%81%D1%82%D0%BE%D0%B8%D1%82-%D1%81%D0%B5%D0%B9%D1%87%D0%B0%D1%81-%D0%BA%D0%B0%D1%87%D0%B5%D1%81%D1%82%D0%B2%D0%B5%D0%BD%D0%BD%D1%8B%D0%B9-%D0%B4%D0%B8%D0%BF%D0%BB%D0%BE%D0%BCВ