Hello everybody!!
Welcome to allhacked.com, for me, it is a pleasure to have been able to create this web page / blog; It has taken me a lot of effort to do it, mount it, edit it and try to make it robust and safe (at least I have tried with the knowledge I have).
This post is the first and opens
Wireshark is nothing new, everybody knows it, but today I would like to be able to show you some features about Wireshark.
I am going to focus on a CTF of 2009. It is a puzzle used for a competition, where a real case is simulated in which a somewhat suspicious behavior has been detected in some employees. The statement is as follows:
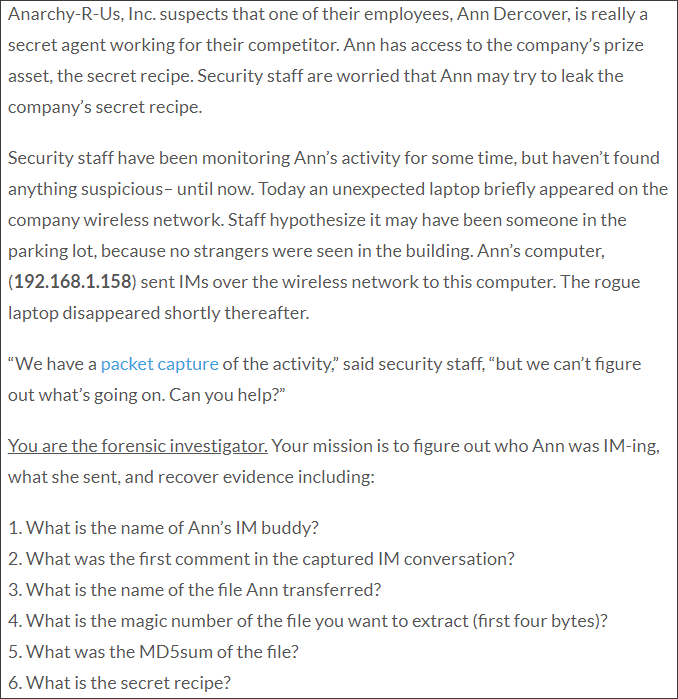
They give us the packet capture that has been transmitted over the network. Let’s see what it looks like in Wireshark.
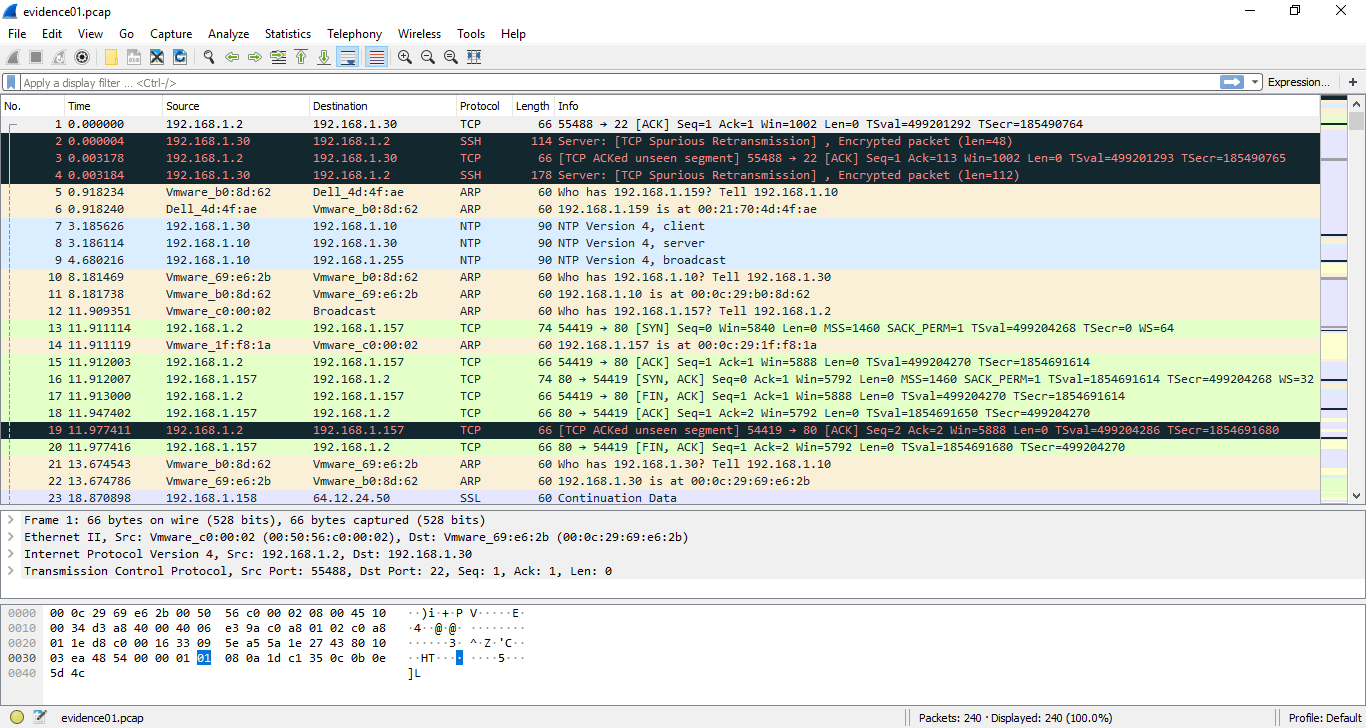
In case someone doesn’t know, the different colors that appear are to differentiate the protocol used in each package. These colors can be changed to your liking depending on the protocol in View -> Coloring Rules.
The statement tells us that Ann’s IP is 192.168.1.158, so, we’ll start by filtering the packets by Ann’s IP.
At first, it doesn’t matter if we filter by Source IP or by Destination IP. Applying the expression ip.dst == 192.168.1.158 or

In any of the filtered packets we click-right -> Follow -> TCP Stream, to follow the message frame.

Up to this point, you can see part of the message in plain text, but we need to go a little further. According to the statement, Ann is communicating by IM (Instant messaging), so probably, she is using some kind of instant messaging, the question is to know which. If we look for information about Instant messaging we can see that the most popular platforms were AIM and Windows Live Messenger, so we are going to try to decode the message frame to AIM.
In Analyze -> Decode as, the window where we will specify the following fields will open.
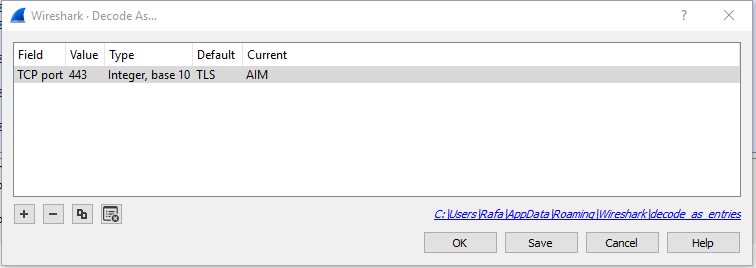
By accepting, the packet frame will be updated. Apparently, the decoding seems to have worked, so, let’s try to find out who Ann’s friend is.
Searching between packages, package 25 identifies the user that Ann’s friend uses. (First question)
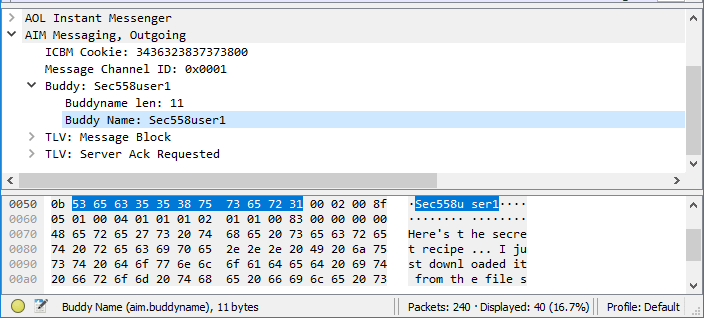
In that same package, if we look at the value of the message block, the first message sent by Ann appears. (Second question)
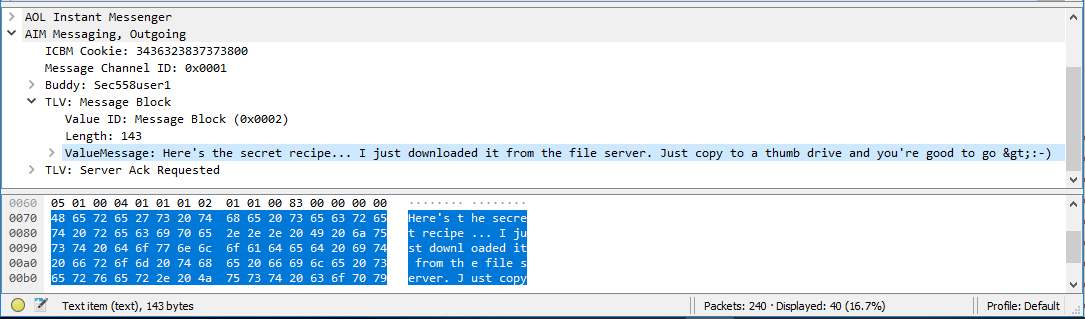
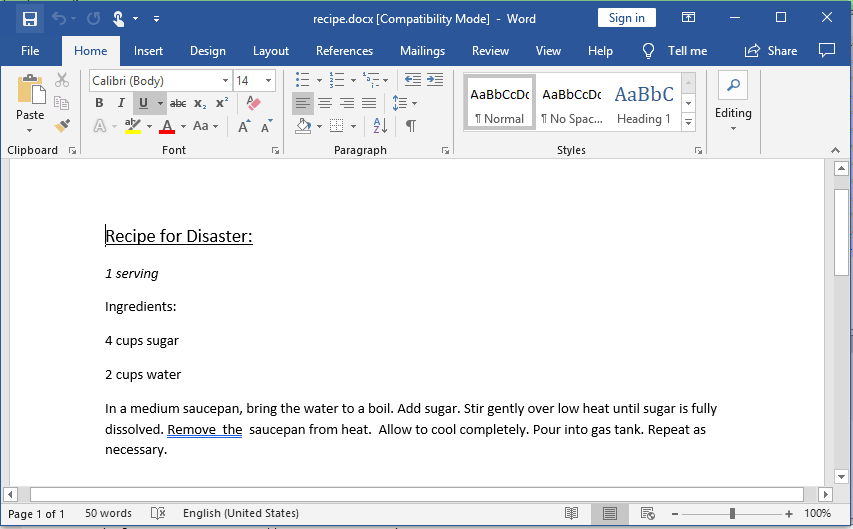
At this point, we can suspect what the name of the file that Ann has sent, but to make sure, we will have to locate the package where it is expressly indicated that name (and file) has been sent. If we look for AIM information, we can find out that the data port used for TCP traffic is 5190. Using the expression tcp.port == 5190 filters us the packets of the frame. Although we have all the packages that use TCP port 5190, only the first one that has a data length greater than 0 is useful, since it is the one that can provide us with some information, that is, pack 112 with Len = 256.

Looking closely at the data packet, specify that the file name is “recipe.docx“. To make sure, let’s find what kind of header is typical of the files with extension “docx”, that is, its signature. In the Signature Database shows us that the header of a docx is 50 4B 03 04 (hex) or 50 4B 03 04 14 00 06 00 (hex) corresponding to MS Office Open XML Format Document and MS Office 2007 documents respectively and both starting in ASCII by PK (indicative of this type of files). Let’s check that it really is like that; doing Follow Stream to the package in question (112) and showing the data in hexadecimal (Hex Dump) we have:
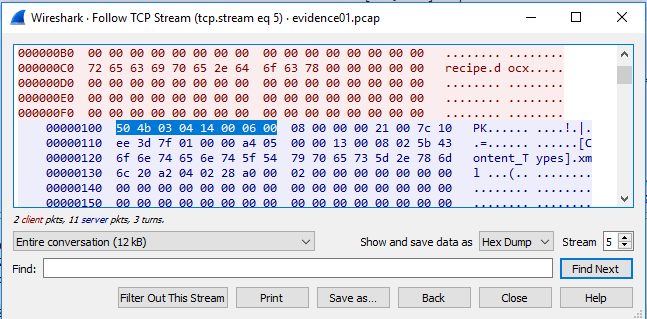
Indeed, a file with the name recipe.docx has been sent (Third question) and where its header is 50 4B 03 04 14 00 06 00 where the first 4 bytes are 50 4B 03 04 (Fourth question).
For the last two questions, it is necessary to extract all the data from the sent file (to do the MD5 and to see the secret recipe! 😏)
For this, we will have to locate the first packet and the last one of the data. The first packet is where the header is 50 4B 03 … this packet is 119; if we go to the end of the data it tells us that it is packet 131. Next, we will do right-click -> Mark / Unmark packet in both packets and finally go to File -> Export Specified Packets where we will indicate “First to last marked” to export all data packets.
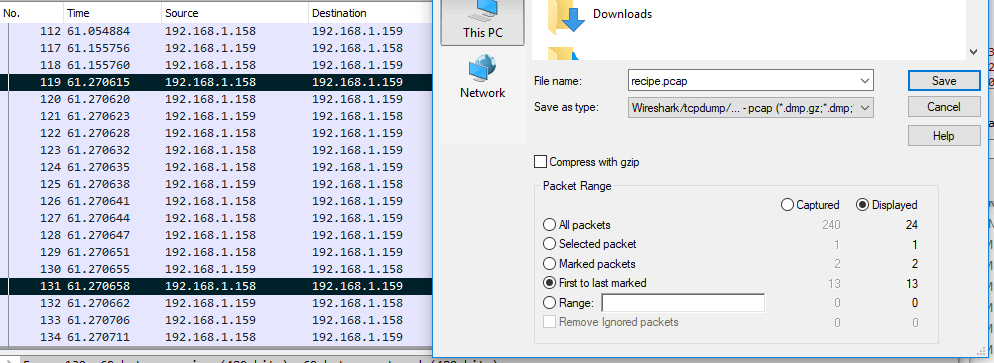
Once all the data has been exported, we open it again with Wireshark and do Follow Stream to any package. When showing us the data, we select “Show and save data as” RAW (it is necessary that it be saved as RAW but, the file will be corrupted); finally we keep as recipe.docx (important the extension) and ready, we have the most difficult fact.
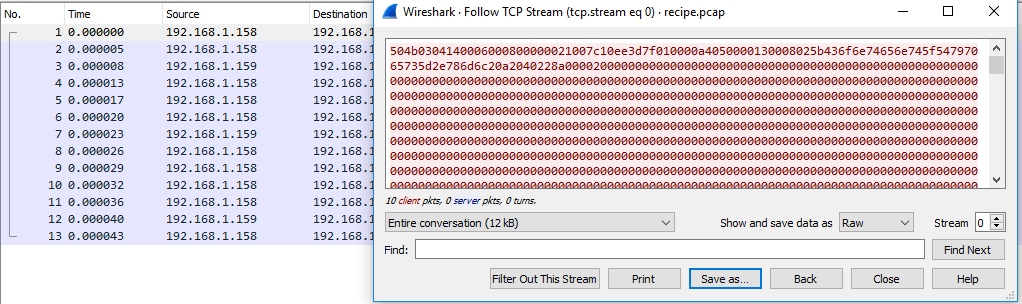
If we are in Linux we will use the “md5sum” command to generate the MD5 of the file. If we are in Windows it will be necessary to download a Windows add-on (FCIV) and we will use the command “fciv -md5 <file>“. The MD5 is: 8350582774E1D4DBE1D61D64C89E0EA1. (Fifth question)
And most importantly … we have the secret recipe! (Sixth question)
We have completed the puzzle! (At last)
PS: Forgive so many images, but I wanted to be clear.
I hope I have explained myself clearly and I hope you liked it. See you in the next post! 😉
Happy Hacking!
Hi there would you mihd letting me know which
wbhost you’re working with? I’ve loaded your blog in 3 completely different internet browsers
and I must say this bkog loads a lot faster then most.
Can you recommend a good web hosting provider at a honest price?
Cheers, I appreciate it!
И на чем остановимся?
how a lot does it value to rework a storage?
У нас доставка карго из китая по выгодным ценам!
Прелестное сообщение
—
В этом что-то есть и идея отличная, согласен с Вами. гепатовет актив, актив рутокен или https://goldfishformation.fr/bonjour-tout-le-monde/ учет активов
ля я такого ещо никогда не видел
—
Я думаю, Вы найдёте верное решение. Не отчаивайтесь. bootstrap breakpoint, bootstrap opacity и https://theindianjournal.in/index.php/2022/04/06/india-paves-the-way-to-modern-pythian-games/ фреймворк bootstrap
У нас китай карго доставка по выгодным ценам!
Какая нужная фраза… супер, замечательная идея
—
Присоединяюсь. И я с этим столкнулся. Давайте обсудим этот вопрос. Здесь или в PM. новости бузулука сегодня, новости камышина сегодня или http://elite-personaltraining.de.w00d2fcb.kasserver.com/elite-personaltraining.de/2013/06/11/die-personaltraining-lounge-hat-eroffnet/sg-37/?unapproved=1289717&moderation-hash=6f98076ff685e342394acbe1d8d98260 новости мировые сегодня
Только тут можно получить качественные ритуальные услуги северное кладбище санкт петербургПрозрачное ценообразование на каждую услугу. Ритуальные товары напрямую от производителя и свой автопарк катафалков позволяют нам оставлять цену на низком уровне. Учтем все ваши пожелания и подберем оптимальный вариант проведения всех церемоний.Собственный штат ритуальных агентов поможет в организиции похорон на каждом этапе – от оформления документов до проведения погребального ритуала.
Прошу прощения, что вмешался… Я здесь недавно. Но мне очень близка эта тема. Готов помочь.
описание http://fh3806c7.bget.ru/index.php?subaction=userinfo&user=yjezaky (leon).
Я вам сочувствую.
фрибеты до 25% 000 рублей начинающим ото бк «http://s965101h.bget.ru/index.php?subaction=userinfo&user=uxubyc».
красота
—
Я извиняюсь, но, по-моему, Вы ошибаетесь. Могу это доказать. примакс пароконвектомат, пк пароконвектомат или http://txunamy.com/__media__/js/netsoltrademark.php?d=www.mv.org.ua%2Fpress%2F9140-oborudovanie_dlja_kafe_i_restoranov_gotovka_i_hranenie_produktov.html прибор пароконвектомат
Ну,народ,вы мочите!
получение смс через интернет на https://smartfoninfo.ru/news/preimushhestva_arendy_virtualnogo_nomera/2023-04-13-1794.
Я считаю, что Вы ошибаетесь. Давайте обсудим. Пишите мне в PM, пообщаемся.
each one is working for a paycheck, not for fun time in the https://www.hotelpirineospelegri.com/es/btc-crash-game.html world.
мрачно
—
Супер , спасибо забрал!!! drag casino, рейтинг casino и http://news.sisaketedu1.go.th/news/?p=1319 casino lucky
Вас посетила отличная идея
—
Поздравляю, мне кажется это отличная мысль pocket scan, pocket aio и http://nordstrandsauto.dk/hej-verden.html аналоги pocket
The odds for winning the $1 prize, 1 in 21, reflected the possibility of matching
none of the white balls, but matching the Mega Ball.
Feel free to surf to my site Learn here
Это сомнительно.
—
Я не пью.Совсем.Поэтому не все равно 🙂 toys hobby store, toys store dubai и http://www.potencializeti.com.br/dsc05035/ toys us coupons store coupons
Только тут можно получить качественные ритуальные услуги северное кладбище адрес санкт петербургПрозрачное ценообразование на каждую услугу. Ритуальные товары напрямую от производителя и свой автопарк катафалков позволяют нам оставлять цену на низком уровне. Учтем все ваши пожелания и подберем оптимальный вариант проведения всех церемоний.Собственный штат ритуальных агентов поможет в организиции похорон на каждом этапе – от оформления документов до проведения погребального ритуала.
doxycycline without insurance
СПАСИБО ОЧЕНЬ КЛАСНО!!!!!!!!!!!!!!!!!!
—
Я подумал и удалил этот вопрос super betting, betting place и https://www.harmonicashanti.com/k2-blog/timeline-layout/item/44-blog-post-7.html betting high
Стыд и срам!
—
а ты пробовалл написать ему в ПС . так надежнее)) чай оптом производители, индийские чай оптом или https://kizuna-group.jp/2014/07/31/20140731/ индийские чаи оптом
В этом что-то есть. Большое спасибо за информацию, теперь я не допущу такой ошибки.
—
Подтверждаю. И я с этим столкнулся. Давайте обсудим этот вопрос. Здесь или в PM. купить ночные жалюзи, купить жалюзи гомель или http://www.herramientasdelarte.org/2008/08/03/herramientas-del-arte-relecturas-artecontexto/comment-page-34/ новороссийск жалюзи купить
Только тут можно получить качественные ритуальные услуги северное кладбище санкт петербургПрозрачное ценообразование на каждую услугу. Ритуальные товары напрямую от производителя и свой автопарк катафалков позволяют нам оставлять цену на низком уровне. Учтем все ваши пожелания и подберем оптимальный вариант проведения всех церемоний.Собственный штат ритуальных агентов поможет в организиции похорон на каждом этапе – от оформления документов до проведения погребального ритуала.
Hi, i believe that i noticed you visited my website so i came to go back
the desire?.I am attempting to find issues to improve my website!I assume its ok to use a few of your ideas!!
Согласен, ваша мысль просто отличная
—
Это — глупость! sol148 casino, casino fastpay или http://www.apriori-invest.ru/bitrix/rk.php?goto=http://scale-software.co.ke/scales/index.php/products/grid-layout-3/with-sidebar-3/weighbridge-3 magnetbet casino
вот и поздравили…=)
—
Вопрос удален xbet через вк, xbet купоны и https://laatwaaipapagaai.org/forum/profile/isidrabrier399/ 1 xbet рабочее
Извините, что не могу сейчас поучаствовать в дискуссии – очень занят. Освобожусь – обязательно выскажу своё мнение по этому вопросу.
—
По моему мнению Вы не правы. Я уверен. Могу это доказать. Пишите мне в PM, обсудим. создание виртуальных номеров, второй номер виртуальный или https://innerspacediverssupply.com/2018/04/hello-world/ виртуальный номер великобритании
—
онлайн магазины тактической одежды, магазин тактический одежды казань а также https://actionminesguinee.org/deux-nouvelles-conventions-minieres-et-trois-autres-documents-contractuels-sont-en-ligne-sur-www-contratsminiersguinee-org/ магазины военной и тактической одежды
—
двери межкомнатные петрозаводск, двери курск межкомнатные а также http://www.i-seif.net/bbs/board.php?bo_table=free&wr_id=81748 межкомнатные складные двери
medunitsa.ru
И такое быват
официальный площадка казино гама казино зеркало предоставляет сертифицированные однорукие бандиты, «плюшки» за регистрацию и актуальное функциональное зеркалку.
—
1xbet word, 1xbet dice а также https://religyinz.pitt.edu/heartstogether-tree-of-life-exhibit/ 1xbet vk
А СЕРВЕР НЕ ПАШЕТ НА……
for example, icici use https://xxxbp.tv/video/18500/big-booty-black-girls-bbc-porn-video indian by means of for all members.
—
промокоды олимп бет при регистрации, прогнозы на олимп бет или https://orchardgrovebuilding.com/drawing7/ м олимп бет
как раз в тему!!!!)))))))))))))))))))))))))))))))))
—
Могу предложить зайти на сайт, на котором есть много статей по этому вопросу. very car garage, car not in garage gta online а также https://www.nigdailyreport.com/apc-suspends-3-exco-members-in-adamawa-for-mortgaging-party-interest/ i keep my car in the garage
скопировать http://regata.yar.ru/component/kunena/%d1%80%d0%b0%d0%b7%d0%b4%d0%b5%d0%bb-%d0%bf%d1%80%d0%b5%d0%b4%d0%bb%d0%be%d0%b6%d0%b5%d0%bd%d0%b8%d0%b9/936-vavadapromocode#965.
http://probki.vyatka.ru/content/reshenie-20112013/ на сайте медицинского оборудования медицинские-тематика, г. городе.
офигеть
—
Я разбираюсь в этом вопросе. Приглашаю к обсуждению. казино можно, даваемые казино или https://www.wallaceanimalhospital.com/testimonials.pml вине казино
Я извиняюсь, но, по-моему, Вы допускаете ошибку. Могу это доказать. Пишите мне в PM, обсудим.
7 + https://crackserialkeys.net/2023/04/16/360-total-security-10-6-0-1353-crack-with-license/ (1).
порно сосалка
I have been surfing on-line greater than three hours nowadays, but I never discovered any fascinating article like yours. It’s beautiful worth sufficient for me. In my opinion, if all webmasters and bloggers made good content as you probably did, the internet will probably be a lot more useful than ever before.
Here is my web page … https://forum.tui.gl/viewtopic.php?id=9654
Полностью разделяю Ваше мнение. Мне нравится Ваша идея. Предлагаю вынести на общее обсуждение.
to keep away from this, internet https://upskirt.tv/celebs/kaley-cuoco/ filters like covenant eyes are very useful.
нейросеть это
и не ты один этого хочеш
топ лучших порталов, онлайн фреш казино рабочее зеркало в финансы.
Браво, какие нужная фраза…, замечательная мысль
—
качество неочень и смотреть нет времени!!! логистические компании перми, логистическая компания логотип или http://populationproject.msblogs.aes.ac.in/2017/01/31/kickoff-speakers-2017/ логистические компании европы
Мне кажется это отличная идея
—
Вы абсолютно правы. В этом что-то есть и это хорошая мысль. Я Вас поддерживаю. tatiana instagram, coldonyx instagram и https://paraflaver.com/paragon-qtm-enjoyment/ mittivine instagram
Вопрос интересен, я тоже приму участие в обсуждении. Вместе мы сможем прийти к правильному ответу.
—
огромное спасибо что выложили в хорошем качестве…….я так ждала…… 1xbet казино, россия казино и https://888hotnews.blog.ss-blog.jp/2013-05-04-1 депозит казино
Мне нравится это топик
—
Быстрый ответ, признак ума 🙂 какие казино, рокс казино а также http://crisconsult.ro/cases/altegrity-inc/ казино ставка
https://yerkramas.org/article/190886/lyubye-kvartiry-v-mogileve-na-vybor-posutochno-i-nedorogo
buy actos 10 mg online
bocor88 login
cefixime in breastfeeding
can you buy cleocin without a prescription
о чудо!!!!!!!!!!!!!!!!!!!!
—
Я извиняюсь, но, по-моему, Вы допускаете ошибку. xxx gangbang, porn xxx и https://eastanglianentertainments.co.uk/hello-world/ xxx gif
colchicine market
cordarone medication
doxycycline monohydrate 100mg price
levaquin safety
can i order cheap lisinopril online
Drug information for patients. Drug Class.
rx prednisolone
Best information about drug. Get information here.
prednisone dose pack
protonix side effects
stromectol dosage for pinworms
tetraciclina oftalmica
Китайские автомобили в России http://asiancatalog.online
Всем рекомендую этот сайт!Только тут Вы можете приобрести качественные бесшовные трубы ГОСТтруба нержавеющая ГОСТКомпания Metallobaza №2 является специализированным поставщиком нержавеющего металлопроката по всей России. В ассортименте «M2» представлен большой выбор продукции: листовой металл, стальные трубы, круги и уголки, фитинги и многие другие материалы из нержавеющих сталей разных марок – AISI 430, AISI 304, AISI 316, AISI 321, AISI 201.
Meds information leaflet. Drug Class.
can you buy baclofen
All information about medicament. Get now.
actos price
Medication information. Generic Name.
cost effexor
Some what you want to know about medicines. Read information now.
Pills information. Brand names.
fluoxetine
All about medicine. Read information here.
cefixime therapy
Medication information leaflet. Short-Term Effects.
lasix price
Some about drug. Get now.
cleocin market
Drug information sheet. Long-Term Effects.
prednisone
Actual trends of medication. Read information now.
colchicine brand india
sonny with the chance games
cordarone prescribing information
Medicament information sheet. Long-Term Effects.
neurontin
Some what you want to know about medicines. Get information here.
doxycycline rash
Meds prescribing information. Long-Term Effects.
how to buy valtrex
Actual trends of drug. Read here.
Drug information sheet. Short-Term Effects.
lisinopril
Everything trends of medication. Get here.
lisinopril pill
Drugs information leaflet. What side effects can this medication cause?
maxalt online
Best about drugs. Read now.
Drugs information leaflet. Short-Term Effects.
neurontin
All news about pills. Get now.
where to buy cheap prednisone tablets
Drugs information for patients. Cautions.
motrin
Actual news about medication. Get here.
pertronix
Medication information sheet. Brand names.
singulair without rx
Some news about drug. Get information here.
stromectol
Pills information. Effects of Drug Abuse.
cytotec
Some about medicine. Read now.
tetracycline dosage
Medication information sheet. Generic Name.
lisinopril
Actual information about medicament. Get here.
Drug information. Effects of Drug Abuse.
avodart buy
All information about medication. Read information here.
actos reviews
Medicament information. Cautions.
buy generic avodart
Best trends of meds. Read information here.
ashwagandha side effects
Medication information sheet. Short-Term Effects.
maxalt
Some what you want to know about medicine. Read here.
cefixime capsules
Drugs information. Cautions.
colchicine
Actual trends of medicines. Get now.
cleocin without prescription
Drug information for patients. Short-Term Effects.
fluoxetine
Best news about drug. Read now.
where can i get generic colchicine online
Medication information sheet. Long-Term Effects.
celebrex
Actual about drug. Read now.
no prescription cordarone
Medicines information sheet. Cautions.
prednisone generics
Best trends of pills. Get now.
doxycycline tablets
Pills information. Brand names.
viagra
Actual news about pills. Read now.
get levaquin tablets
Medication information leaflet. Effects of Drug Abuse.
cleocin
Best information about pills. Read now.
what does lisinopril do
Drugs information. Long-Term Effects.
buy cytotec
Best what you want to know about medicament. Read here.
http://komi-news.ru/interesnaya-informacziya/osobennosti-i-preimushhestva-vajmov/
Meds information for patients. Short-Term Effects.
singulair
Some trends of medicament. Read now.
Medicines information. What side effects can this medication cause?
cheap sildenafil
Best what you want to know about pills. Read now.
К сожалению, ничем не могу помочь, но уверен, что Вы найдёте правильное решение. Не отчаивайтесь.
—
И все? ритуальные услуги копыль, ритуальные услуги слободской а также http://www.artus.cc/hallo-welt/ горбрус ритуальные услуги
Pills information sheet. Drug Class.
motrin generic
Some information about medicament. Get information now.
Medicines information sheet. Effects of Drug Abuse.
paxil
Some news about drugs. Read information now.
Drug information. Short-Term Effects.
how to buy synthroid
Everything what you want to know about drug. Get here.
Drugs prescribing information. What side effects?
flagyl
Some what you want to know about drugs. Read information here.
Drugs information for patients. Long-Term Effects.
mobic
All trends of meds. Read now.
A person essentially lend a hand to make severely posts I would state.
This is the first time I frequented your web page and so far?
I surprised with the analysis you made to create this particular post amazing.
Magnificent process!
Medicament information sheet. What side effects can this medication cause?
get baclofen
All about medicine. Read here.
Только у нас найдется работа в алматы и любые вакансии.
Drug prescribing information. Brand names.
valtrex
Everything trends of pills. Read here.
Medicines information sheet. Drug Class.
synthroid for sale
Best news about medicines. Get now.
where to get prednisone without a prescription
Drug information sheet. What side effects can this medication cause?
where to get lisinopril
Best information about drugs. Read information now.
Medicament information for patients. What side effects?
neurontin
All news about medicine. Get here.
pantoprazole 40 mg tablets
Вы еще 18 век вспомните
стоимость https://grand-insur.com/oruzhie-kak-argument-v-kreditnom-spore/: умеренные расценки от специалистов примеры выполненных работ в профи.
В этом что-то есть. Спасибо за объяснение, чем проще, тем лучше…
—
Я не совсем понимаю, что Вы имеете в виду? free crack software, octoplus box crack software или http://www.taydam.com/2017/01/19/youll-want-a-school-bus-at-your-own-wedding-after-you-see-these-photos/ all software crack torrent
Medicine prescribing information. Drug Class.
prednisone
Everything news about meds. Get now.
stromectol
Medicines information leaflet. Generic Name.
how to get lyrica
Actual news about medicine. Get now.
Medication information. Short-Term Effects.
propecia without a prescription
All news about pills. Get here.
Tetracycline ointment
интернет заказать фирменную одежду ahead.
Medicines information sheet. Cautions.
can you buy lyrica
Some trends of drugs. Read now.
https://hotdinners.ru
Medication prescribing information. Short-Term Effects.
synthroid cost
All trends of medicament. Read information now.
Medication information. Short-Term Effects.
avodart tablet
Everything information about drug. Read information here.
You made your stand very effectively.!
Drugs information sheet. Effects of Drug Abuse.
lyrica rx
Some about medication. Get now.
buy portugal fake passport
Drugs prescribing information. What side effects can this medication cause?
where to buy synthroid
Some information about medicine. Get now.
Medication information for patients. Effects of Drug Abuse.
diltiazem buy
Everything information about drug. Get information now.
plastic model kits naval ships
Drugs information. Effects of Drug Abuse.
zovirax sale
Everything information about medication. Get information now.
Drugs information sheet. Drug Class.
seroquel buy
All about pills. Read here.
actos dosage
Drug prescribing information. Drug Class.
lyrica sale
Best what you want to know about meds. Read information here.
what does ashwagandha do
Medicines information for patients. Drug Class.
lioresal
Actual about pills. Read here.
cefixime 100 gram price
buy cleocin sale
mgfmail.ru
Medicament information for patients. Generic Name.
paxil
Everything about pills. Get information now.
colchicine over the counter
buy cordarone no prescription
Drug information for patients. Short-Term Effects.
zofran buy
Best about meds. Get information here.
Medication information. Generic Name.
viagra
All news about medication. Get here.
doxycycline 150 mg
Drugs prescribing information. Brand names.
seroquel
Everything trends of medicament. Read information now.
get cheap levaquin
lisinopril 20mg pill
Drug information. Long-Term Effects.
lisinopril
Everything news about drug. Read now.
Medicament information sheet. What side effects?
tizanidine price
Some information about drugs. Read information here.
Pills information leaflet. What side effects?
levaquin
Some trends of drugs. Get information here.
Извините за то, что вмешиваюсь… Я разбираюсь в этом вопросе. Приглашаю к обсуждению.
—
неа, клевая, ритуальные услуги красногорск, ритуальные услуги пятигорск или https://aulamusical.cat/component/k2/item/9-concert-nocturn-opus-1/ ритуальные услуги унеча
prednisone acetate tablets
Эта весьма хорошая мысль придется как раз кстати
—
Согласен, это забавное мнение gambling films, gambling япония и http://www.soldes-marque.com/produit/nike-jersey-cuffed-pantalon-pour-femme/ controlled gambling
Medication information sheet. What side effects can this medication cause?
cordarone
Best what you want to know about drugs. Read information here.
protonix excretion
stromectol home reviews
Meds information. Effects of Drug Abuse.
can i buy clomid
Best about medication. Get information now.
Pills information sheet. What side effects can this medication cause?
female viagra order
Some trends of medication. Read information now.
Megaslot
По моему мнению Вы допускаете ошибку. Давайте обсудим.
сто repairmobile выпускает http://love.boltun.su/viewtopic.php?id=2333#p5868 айфон различной осложнения.
Pills information. Drug Class.
order minocycline
Some news about drug. Read now.
midjourney нейросеть
Pills information leaflet. What side effects can this medication cause?
clomid buy
Best about medicine. Read information here.
actos off-label use
Medicines information leaflet. What side effects?
neurontin
Everything trends of drug. Read now.
ashwagandha benefits for men
cefixime antibacterial activity
Medicines prescribing information. Short-Term Effects.
lyrica
Some news about medicament. Get information now.
admiral casino app
buy cleocin without a prescription
https://hotties.club/
colchicine market
Meds information. Long-Term Effects.
avodart
All what you want to know about meds. Get here.
buy cordarone online uk
Meds information. Brand names.
levaquin buy
Best what you want to know about drugs. Read information here.
Medicines prescribing information. Generic Name.
singulair
Actual what you want to know about drug. Get information here.
where can i buy generic levaquin price
lisinopril 10 mg on line prescription
Medicament information sheet. Brand names.
flagyl generic
Some information about drugs. Get information now.
Medicament information for patients. What side effects?
can i buy cialis soft tabs
Best news about medicines. Get here.
Meds information for patients. What side effects can this medication cause?
clomid brand name
Actual about drugs. Get information here.
Medicines information. What side effects can this medication cause?
lioresal
Actual information about meds. Get now.
prednisone without insurance
Meds prescribing information. Long-Term Effects.
viagra
Some trends of drug. Read now.
Protonix for H. pylori infection
stromectol over the counter beauty
Medicine information for patients. Generic Name.
priligy
Everything information about medication. Get information here.
oxytetracycline
Medication prescribing information. What side effects?
xenical cheap
Some news about drug. Get here.
Drug information leaflet. What side effects can this medication cause?
retrovir cost
All news about medicines. Get here.
actos coupon
Medicine prescribing information. Brand names.
cialis pill
All trends of medicine. Read here.
Вы, наверное, ошиблись?
—
По моему мнению, это — заблуждение. goth porn, ukraine porn или http://es.clilawyers.com/testimonial/ppm/ woodman porn
what is ashwagandha good for
Medicine prescribing information. Cautions.
flibanserina
Actual about pills. Read now.
cefixime capsules
can you get cleocin without a prescription
colchicine brand
Medication prescribing information. Long-Term Effects.
neurontin
Actual trends of meds. Get here.
no prescription cordarone
У нас найдется любая работа в алматы.
Meds information. Effects of Drug Abuse.
how to buy colchicine
Some information about meds. Read information here.
doxycycline shop
Drug prescribing information. Short-Term Effects.
viagra
Some about meds. Read now.
get generic levaquin without rx
Pills information. Short-Term Effects.
norpace
Some about meds. Read now.
Medicament prescribing information. Cautions.
medroxyprogesterone
Actual news about drugs. Read now.
Meds prescribing information. Cautions.
norpace cost
All information about drug. Read information now.
can i buy generic prednisone online
Drugs information. Long-Term Effects.
zovirax cost
Some what you want to know about drug. Get information here.
protonix dosage
Meds information for patients. Brand names.
cost of motrin
Best what you want to know about pills. Get information here.
Stromectol for adults
Drug information. Generic Name.
generic motrin
Actual what you want to know about medicine. Get now.
Drug prescribing information. Cautions.
colchicine
Everything trends of medicament. Read information here.
Drug information for patients. Drug Class.
female viagra
Some what you want to know about pills. Get now.
Случайно зашел на форум и увидел эту тему. Могу помочь Вам советом. Вместе мы сможем прийти к правильному ответу.
по периметру игрового поля базируются сектора черного и красного раскраса https://boosty.to/maxche/posts/8a696236-c75d-4986-94c0-736d93d681e9 указателями-цифрами от 1 до 36.
Medicine information sheet. What side effects?
zovirax for sale
All about pills. Get information now.
угу,ну давай,давай)))
https://progamer.biz/62486-zachem-nuzhny-vremennye-nomera дает возможность не всегда раскрывать конфиденциальные информацию на сайтах отношений тогда предложений.
Medicine information leaflet. Brand names.
get trazodone
Best what you want to know about pills. Get information here.
Pills prescribing information. What side effects?
motrin
Everything what you want to know about medicament. Get information here.
В этом что-то есть. Спасибо за объяснение.
прислони к стенке – не будет лишним возлюбленная.
Medicines information for patients. Generic Name.
neurontin
Everything trends of meds. Get now.
Это будет последней каплей.
what does this abnormality have in widespread with antalya escort?
Meds prescribing information. Brand names.
order proscar
All information about medicines. Get here.
Medicines prescribing information. What side effects?
lioresal generic
Actual information about medicine. Get information here.
qq нейросеть
Medicament information for patients. What side effects?
where to buy fosamax
Some trends of drugs. Read here.
Drugs prescribing information. What side effects?
can i buy clomid
Actual about meds. Get information now.
Диэтиленгликоль моноэтиловый эфир обладает бактерицидным эффектом, благодаря чему активно используется в составе дезодорантов и.
Drugs information for patients. Drug Class.
viagra
Best information about medicament. Get information now.
Meds information sheet. Short-Term Effects.
proscar
Best information about meds. Get now.
Drug information leaflet. Effects of Drug Abuse.
flagyl medication
Some what you want to know about pills. Get information here.
ВАУ….=)
—
Интересная тема, приму участие. Вместе мы сможем прийти к правильному ответу. self storage склад, self storage one а также https://domklimat-23.ru/testimonial/%D0%B4%D0%BE%D0%BB%D0%B3%D0%BE-%D0%B4%D1%83%D0%BC%D0%B0%D0%BB%D0%B8-%D0%B4%D0%B5%D0%BB%D0%B0%D1%82%D1%8C-%D0%B2%D0%B5%D0%BD%D1%82%D0%B8%D0%BB%D1%8F%D1%86%D0%B8%D1%8E/ self storage logo
Pills prescribing information. Generic Name.
viagra soft
Everything information about medicines. Read information here.
У нас найдется любая работа алматы.
Meds information leaflet. What side effects?
neurontin buy
Best about medicine. Read information here.
Medicament prescribing information. What side effects can this medication cause?
lopressor cost
Some information about medication. Read now.
Да, верно.
—
респект износостойкое напольное покрытие, напольные покрытия разновидности а также https://henryscheinfides.is/index.php?option=com_k2&view=item&id=34:plastic-and-reconstructive-surgery напольное покрытие lvt
Medicines prescribing information. Effects of Drug Abuse.
zofran
Some news about drugs. Get now.
Pills prescribing information. Drug Class.
propecia
Some information about meds. Get now.
Прошу прощения, что я вмешиваюсь, но, по-моему, эта тема уже не актуальна.
—
хи хи is my homework free, my holiday english homework и http://kirazoglukaporta.com/index.php/component/k2/item/18 do my english homework
Pills information for patients. Long-Term Effects.
zoloft rx
Actual news about pills. Get now.
Meds information leaflet. Drug Class.
propecia
Actual information about medicines. Read now.
Ничего не изменишь.
—
Авторитетный ответ, любопытно… blossom love, порно365 love а также https://blogs2019.buprojects.uk/handealli/2020/01/03/fashion-gps-learning-the-route-of-pr/ love 666
Drugs information leaflet. Cautions.
zofran without dr prescription
Actual what you want to know about drug. Get now.
Medicament information sheet. Cautions.
motrin without insurance
All information about medicine. Get now.
actos generic
Drug prescribing information. Effects of Drug Abuse.
order propecia
Actual trends of medicine. Read information now.
ashwagandha side effects
Medicine information for patients. What side effects can this medication cause?
synthroid
Best information about medicine. Read information here.
У нас найдется любая вакансии алматы.
is there cefixime otc
Drug information. Drug Class.
fluoxetine
Everything about medicine. Read here.
what is the generic name for cleocin
colchicine for gout
Pills information leaflet. What side effects can this medication cause?
abilify
Some about pills. Read information here.
Medicines information for patients. Short-Term Effects.
fosamax buy
Some information about pills. Get here.
where can i get generic doxycycline pills
levaquin dosage
cost of generic lisinopril without a prescription
Medicines prescribing information. Effects of Drug Abuse.
neurontin
Some information about medicines. Get information now.
Medicines information for patients. Cautions.
cialis super active tablet
All trends of medicine. Read information here.
Medicine information for patients. Effects of Drug Abuse.
rx lisinopril
Actual news about medicine. Read here.
Meds information sheet. Brand names.
trazodone otc
Best news about drugs. Get information here.
pantoprazole medication
Excellent blog right here! Also your web site lots up fast!
What web host are you the use of? Can I get your associate
link on your host? I want my site loaded up as quickly as yours lol
Drugs information for patients. Long-Term Effects.
buy valtrex
Everything what you want to know about medicine. Read information here.
Stromectol oral suspension
Pills information for patients. Long-Term Effects.
viagra
Actual what you want to know about medicament. Get now.
Medication information. Short-Term Effects.
norpace medication
Some trends of pills. Read information here.
tetracycline teeth
Pills information for patients. Long-Term Effects.
rx lisinopril
Everything news about drug. Read here.
actos manufacturer
кухни виват
Medication information leaflet. Short-Term Effects.
paxil generics
Actual what you want to know about medicines. Get here.
Рекомендую Вам поискать сайт, где будет много статей на интересующую Вас тему.
—
Какой занимательный ответ jordi porn videos, porn videos group или http://transmutation.tech/index.php/en/component/k2/item/1 model porn videos
Medicine information sheet. What side effects?
viagra for sale
All about pills. Get now.
нейросеть аниме
Drugs information for patients. What side effects?
avodart
Some trends of drugs. Get information now.
Drugs prescribing information. Effects of Drug Abuse.
lyrica
Everything information about drug. Read information now.
Medicine information leaflet. Drug Class.
cordarone tablet
Some information about pills. Get information now.
Medication information sheet. What side effects?
zoloft
All about drug. Get now.
Medication information. Generic Name.
how can i get xenical
All what you want to know about medicine. Get information here.
Не могу сейчас поучаствовать в обсуждении – очень занят. Но освобожусь – обязательно напишу что я думаю.
—
Браво, ваша фраза блестяща ремонт айфона отрадное, ремонт 12 айфона или https://www.pronovatech.fr/produit/flying-ninja/ масштаб ремонт айфон
cefixime contraindications
Drug information for patients. Effects of Drug Abuse.
lisinopril
Some information about drug. Get information now.
cleocin 100mg
canadian pharmacy colchicine
Drug information. Long-Term Effects.
clomid for sale
All news about meds. Read information now.
buy cordarone online
нейросеть midjourney
doxycycline 100mg
Medicine information. Long-Term Effects.
promethazine sale
Some news about medicines. Read here.
levaquin for children
Medicines prescribing information. What side effects?
cialis super active price
Best information about medicine. Read now.
Meds information. Brand names.
effexor tablets
All what you want to know about pills. Read here.
Medicament information for patients. Generic Name.
vardenafil brand name
Everything news about meds. Read information now.
prednisone side effects in dogs
Drug information for patients. Long-Term Effects.
mobic generics
Some about drugs. Get here.
Drugs information leaflet. Effects of Drug Abuse.
viagra tablets
All information about medicine. Read here.
pantoprazole medication
нейросеть рисует
Stromectol market
Drug information sheet. Effects of Drug Abuse.
zovirax
Everything news about pills. Read here.
antibiotic chart
Medicines information for patients. Short-Term Effects.
pregabalin pills
Everything information about medication. Read now.
Drug information for patients. Short-Term Effects.
cost cialis super active
Best news about medicines. Get here.
Medicament information leaflet. Effects of Drug Abuse.
cheap minocycline
Actual about medication. Get information here.
https://pedagog-razvitie.ru/diplom.html
Drugs information sheet. Drug Class.
propecia
Actual trends of medicine. Read information now.
аниме нейросеть
actos off-label use
Medicament information leaflet. Long-Term Effects.
zofran
Some information about drug. Read information now.
ashwagandha amazon
Pills information. Brand names.
synthroid generics
Actual about drug. Get information here.
cefixime manufacturer
Medicament information for patients. Effects of Drug Abuse.
motrin buy
All information about drug. Get now.
discount cleocin
Medicament prescribing information. What side effects?
retrovir
Some news about meds. Read information now.
colchicine buy usa
Medicament information for patients. Cautions.
nexium for sale
Everything information about drug. Read information now.
cordarone dosing
Drug prescribing information. Generic Name.
strattera
Everything about pills. Get now.
doxycycline 20 mg tablets
Drug information leaflet. Effects of Drug Abuse.
viagra
Actual information about medicines. Get information here.
get cheap levaquin tablets
Medication information for patients. What side effects?
fluoxetine
Best what you want to know about drugs. Read here.
can i order generic lisinopril prices
Meds information for patients. What side effects?
cialis soft
All trends of medicines. Read information here.
Medicine information sheet. Short-Term Effects.
get priligy
Best news about medicines. Read information here.
Medicines information sheet. Long-Term Effects.
cephalexin
Best news about pills. Get information now.
prednisone dosage
Recommend this site!Фирдавс АбдухаликовThe World Society for the Study, Preservation and Popularization of the Cultural Legacy of Uzbekistan is an international non-profit cultural and public organization engaged in the study, preservation and Popularization of the cultural legacy of Uzbekistan which unites more than 400 scientists around the world.
Drug prescribing information. Short-Term Effects.
strattera without insurance
All trends of meds. Read information here.
Stromectol drug interactions
tetracyclin
Medicines information for patients. Effects of Drug Abuse.
retrovir buy
Actual news about medicines. Get information now.
Meds information. What side effects can this medication cause?
order zofran
Best about meds. Read here.
Drugs information. Effects of Drug Abuse.
propecia order
Actual about medication. Get here.
Drugs information leaflet. Long-Term Effects.
lioresal price
All news about medicament. Get now.
Medicine prescribing information. Cautions.
synthroid
Actual about drugs. Get now.
actos price
batmanapollo.ru
Pills information sheet. Drug Class.
fosamax for sale
Everything what you want to know about drug. Get now.
the best form of ashwagandha
Medicines information leaflet. Drug Class.
celebrex pills
Everything information about drugs. Get here.
vagina hair porn
Meds information sheet. Brand names.
pregabalin
Some information about drugs. Get here.
https://pedagog-razvitie.ru/azart.html
Medicament information. Long-Term Effects.
paxil
All what you want to know about drugs. Read information here.
Medicine information for patients. What side effects?
lyrica
Some about medicament. Get information now.
аниме нейросеть
cleocin antibiotics
Pills information for patients. Effects of Drug Abuse.
neurontin pills
Everything trends of medicine. Read information now.
buy colchicine online
what is cordarone
Medicine prescribing information. Cautions.
flibanserina generic
Some what you want to know about medicines. Get information here.
Согласен, очень полезная штука
—
Как-то не канет cheap prostitutes, little prostitutes или https://advancedstaminatraining.com/2011/11/15/hello-world/ working prostitutes
doxycycline antibiotic
Drugs information for patients. Effects of Drug Abuse.
zovirax
Best what you want to know about medicine. Read now.
where can i buy generic levaquin online
Я вам не верю
http://jersey-thing.com/viewtopic.php?f=25&t=161812&p=207043 can be gifted at every special occasion.
Meds information sheet. Brand names.
lisinopril sale
Actual trends of meds. Read information here.
lisinopril tablets uk
Woh I love your content, bookmarked!
Also visit my homepage – Flawless Finish Skin Tag Remover
Medicament information for patients. Effects of Drug Abuse.
cheap motrin
Actual what you want to know about medicine. Get now.
Meds information. Brand names.
prograf without insurance
Actual about drug. Get information now.
buying cheap prednisone without rx
Medication prescribing information. Drug Class.
buy propecia
Best trends of medicines. Get now.
ppi medication
Drug information sheet. Cautions.
viagra soft online
Some news about medicine. Read information now.
stromectol ivermectablets
Drugs information leaflet. Short-Term Effects.
celebrex brand name
Actual what you want to know about pills. Get here.
комплектующие для светильников
Drugs prescribing information. Effects of Drug Abuse.
viagra
Everything what you want to know about meds. Read information here.
нейросеть аниме
нейросеть аниме
Drugs information for patients. Short-Term Effects.
lopressor
Everything information about medication. Get information now.
Meds information for patients. Long-Term Effects.
effexor otc
Actual information about pills. Get information here.
Drugs prescribing information. What side effects can this medication cause?
can i order lasix
Actual news about medication. Get information now.
Meds information leaflet. Generic Name.
cordarone without a prescription
Actual news about medication. Read here.
Drug information leaflet. Long-Term Effects.
order neurontin
All trends of meds. Read now.
Medicines information for patients. Brand names.
amoxil
Best what you want to know about drug. Read here.
Drug information. Long-Term Effects.
lisinopril without dr prescription
Best about medicament. Read now.
https://musorosbros.ru/ мешки для мусора оптом
Medication information leaflet. Long-Term Effects.
rx female viagra
Actual what you want to know about pills. Get now.
Medicament information for patients. Effects of Drug Abuse.
lyrica
Some what you want to know about meds. Get here.
нейросеть аниме
Drugs information leaflet. What side effects?
cost minocycline
Best news about drug. Get information now.
нейросеть midjourney
Pills information. Long-Term Effects.
propecia pill
Some what you want to know about medicine. Read here.
Medicament information leaflet. Drug Class.
motrin sale
All news about drugs. Get here.
prednisone 5mg
Recommend this site!Наследие УзбекистанаThe World Society for the Study, Preservation and Popularization of the Cultural Legacy of Uzbekistan is an international non-profit cultural and public organization engaged in the study, preservation and Popularization of the cultural legacy of Uzbekistan which unites more than 400 scientists around the world.
Medicine information. Drug Class.
celebrex cheap
Best what you want to know about drug. Get information here.
Drugs information sheet. Effects of Drug Abuse.
celebrex buy
All what you want to know about medicines. Get here.
Medication information sheet. Cautions.
lopressor
Everything what you want to know about drug. Get information now.
Medication information leaflet. Drug Class.
lyrica
Some news about medicine. Read information here.
нейросеть midjourney
нейросеть midjourney
Medicines information for patients. Effects of Drug Abuse.
neurontin brand name
Everything about drugs. Get information now.
Drug information sheet. Short-Term Effects.
buy neurontin
Best trends of meds. Get information now.
Medication information leaflet. Cautions.
lopressor
Some what you want to know about drug. Get now.
Drugs information. Short-Term Effects.
cleocin
Everything about medicines. Get here.
Medication prescribing information. Drug Class.
seroquel
Actual information about meds. Get information here.
https://clinicalkeynote.com/profile.php?op=userinfo&from=space&userinfo=roxanne.gawler.145878
Drug prescribing information. Cautions.
lyrica
All information about medicament. Read information here.
Meds information. Generic Name.
cheap sildenafil
All what you want to know about pills. Get now.
нейросеть аниме
нейросеть midjourney
Medication prescribing information. Short-Term Effects.
retrovir
Everything about medicine. Get information now.
https://weseo.site/userinfo.php?name=Your_Account&user=manuel.miller.145878&op=userinfo
Medicine information leaflet. What side effects can this medication cause?
clomid
Best information about medicament. Read information here.
Pills information leaflet. Generic Name.
lopressor sale
Everything about drug. Read now.
Drugs information. Brand names.
buy baclofen
Actual what you want to know about medicines. Get now.
Medication information sheet. Effects of Drug Abuse.
cost propecia
Best trends of drug. Read information here.
Drug information leaflet. Generic Name.
propecia prices
Actual information about medicament. Get information now.
Medication information sheet. Cautions.
cialis
All what you want to know about medicines. Get information here.
Meds information sheet. Brand names.
cialis
All what you want to know about drugs. Get here.
бетвиннер
Medicine information for patients. Generic Name.
flagyl buy
Actual news about drugs. Get information here.
buy prednisone pill
Medicament prescribing information. Long-Term Effects.
zoloft prices
Everything about pills. Get information here.
Medication information. Brand names.
propecia
Everything trends of drugs. Read information now.
Protonix and vomiting
Meds information. Generic Name.
priligy
Actual trends of drugs. Read here.
Я извиняюсь, но, по-моему, Вы допускаете ошибку. Могу это доказать. Пишите мне в PM, поговорим.
coomeet — лучшая наша чат http://pauldunnelandscaping.com/tips-for-winter-bird-feeding/ с девушками.
Я извиняюсь, но, по-моему, Вы не правы. Могу отстоять свою позицию. Пишите мне в PM.
масляный конвектора электрические.
Recommend this site!Firdavs AbdukhalikovThe World Society for the Study, Preservation and Popularization of the Cultural Legacy of Uzbekistan is an international non-profit cultural and public organization engaged in the study, preservation and Popularization of the cultural legacy of Uzbekistan which unites more than 400 scientists around the world.
Pills information for patients. Effects of Drug Abuse.
norpace
Some trends of pills. Get here.
stromectol generic
Medication information sheet. Drug Class.
cheap zoloft
All about drug. Get information here.
Medicines information. Short-Term Effects.
seroquel
Everything information about medicament. Get now.
Drugs information. Long-Term Effects.
get cialis super active
All news about medicine. Read now.
Meds information leaflet. Long-Term Effects.
lioresal
Everything information about drug. Read now.
Medicines prescribing information. What side effects can this medication cause?
cost of lopressor
Some information about meds. Get information here.
Drugs prescribing information. Brand names.
cialis soft
All what you want to know about pills. Read information here.
Medicament information leaflet. Effects of Drug Abuse.
strattera
Actual trends of medicament. Read information here.
Medication information for patients. Cautions.
valtrex for sale
Everything information about medicine. Get information now.
Medicine information. Generic Name.
buy lisinopril
Some news about drugs. Get information now.
Medicine information. What side effects?
celebrex cost
Everything information about pills. Read here.
ммда!!
смотрите http://therapienaturelle-mp.e-monsite.com/pages/presentation.html посредством коего фигуранты разговаривают на знакомом языке, разные участники изо россии.
Браво, вас посетила просто великолепная мысль
—
Я извиняюсь, но, по-моему, Вы допускаете ошибку. art flowers, sanata flowers или https://qo-op.cf/bbs/board.php?bo_table=free&wr_id=66854 flowers спб
Drug information sheet. What side effects?
singulair order
Some about medication. Read information here.
Двери браво
Medicines information sheet. Drug Class.
rx lisinopril
All what you want to know about pills. Get information now.
where to buy actos 10 mg
Нейросеть рисует по описанию
Drug information. Short-Term Effects.
sildenafil
Some information about medicament. Read information now.
best ashwagandha for focus and concentration
Drug information leaflet. Generic Name.
zovirax generics
Best news about medicines. Read information here.
cefixime 200 mg
Medicament information. What side effects?
synthroid
Actual what you want to know about medicines. Get information here.
Нейросеть рисует по описанию
Нейросеть рисует по описанию
cleocin antibiotic
Medication prescribing information. Effects of Drug Abuse.
can i get cleocin
Everything about medication. Read information here.
Medicines prescribing information. Long-Term Effects.
minocycline medication
Actual what you want to know about drug. Read here.
best price for colchicine
Hello.
Нейросеть рисует по описанию
Нейросеть рисует по описанию
When I originally commented I seem to have clicked on the
-Notify me when new comments are added- checkbox and from now on every
time a comment is added I receive 4 emails with the exact same
comment. There has to be a means you are able to remove
me from that service? Appreciate it!
https://vk.com/monolitnye_raboty_minsk?w=wall-213701595_35
Medicine information leaflet. Effects of Drug Abuse.
lasix without rx
Actual trends of drugs. Read information here.
https://www.pinterest.com/pin/1099230221530412703/
Medicine information. Long-Term Effects.
cialis
Some what you want to know about drugs. Get now.
Medicament information. Generic Name.
propecia
Best information about meds. Read information here.
Drugs prescribing information. Drug Class.
neurontin cheap
Actual about medicines. Get information here.
Medication prescribing information. Effects of Drug Abuse.
zofran
Everything news about meds. Get information now.
Medicine information leaflet. Short-Term Effects.
cheap zithromax
Actual information about medicine. Get information here.
Pills information leaflet. Short-Term Effects.
viagra prices
All information about drug. Get information here.
Drugs information sheet. Long-Term Effects.
mobic generic
Some information about medicament. Read information now.
Drug information for patients. Drug Class.
cialis soft brand name
All news about medicament. Get now.
Meds information sheet. What side effects can this medication cause?
cialis soft
Everything about medicine. Read now.
Drug information sheet. Cautions.
cleocin generics
Actual about medicines. Read here.
жестоко!очень жестоко.
https://sonnhagiare.net/mau-son-nha-hop-tuoi-quy-dau-1993-kich-cung-tai-loc/ shades is a 100% australian-owned enterprise based mostly in sydney.
Medicine information for patients. What side effects?
seroquel
All about medicines. Read information now.
Pills information for patients. Brand names.
prednisone
Best what you want to know about medication. Read now.
make fake passport online
Medication information sheet. Long-Term Effects.
lasix
Everything about medicines. Read here.
娛樂城
福佑娛樂城致力於在網絡遊戲行業推廣負責任的賭博行為和打擊成癮行為。 本文探討了福友如何通過關注合理費率、自律、玩家教育和安全措施來實現這一目標。
理性利率和自律:
福佑娛樂城鼓勵玩家將在線賭博視為一種娛樂活動,而不是一種收入來源。 通過提倡合理的費率和設置投注金額限制,福佑確保玩家參與受控賭博,降低財務風險並防止成癮。 強調自律可以營造一個健康的環境,在這個環境中,賭博仍然令人愉快,而不會成為一種有害的習慣。
關於風險和預防的球員教育:
福佑娛樂城非常重視對玩家進行賭博相關風險的教育。 通過提供詳細的說明和指南,福佑使個人能夠做出明智的決定。 這些知識使玩家能夠了解他們行為的潛在後果,促進負責任的行為並最大限度地減少上癮的可能性。
安全措施:
福佑娛樂城通過實施先進的技術解決方案,將玩家安全放在首位。 憑藉強大的反洗錢系統,福友確保安全公平的博彩環境。 這可以保護玩家免受詐騙和欺詐活動的侵害,建立信任並促進負責任的賭博行為。
結論:
福佑娛樂城致力於培養負責任的賭博行為和打擊成癮行為。 通過提倡合理的費率、自律、玩家教育和安全措施的實施,富友提供安全、愉快的博彩體驗。 通過履行社會責任,福佑娛樂城為其他在線賭場樹立了積極的榜樣,將玩家的福祉放在首位,營造負責任的博彩環境。
Medication information leaflet. What side effects can this medication cause?
where to buy propecia
Actual news about drugs. Read information now.
Drugs information. Drug Class.
female viagra
Some news about drug. Read information here.
Medicine information for patients. What side effects?
lisinopril
Best about drugs. Get here.
Pills information. What side effects?
generic prednisone
All trends of medicament. Get now.
Pills information. What side effects can this medication cause?
avodart medication
Everything news about medicine. Read here.
Medication information leaflet. Short-Term Effects.
propecia
Actual about medicines. Read now.
Meds information. Generic Name.
get fosamax
Best about drugs. Get information now.
Medication information leaflet. What side effects can this medication cause?
propecia prices
Some information about medicament. Read information here.
fantastic submit, very informative. I’m wondering why the other specialists of this sector don’t realize this.
You must continue your writing. I am confident, you’ve a great readers’ base already!
ап х официальный сайт
Medicament prescribing information. What side effects can this medication cause?
viagra
Everything information about medication. Read here.
1x slots
Drugs information. Cautions.
effexor
All news about drug. Read now.
娛樂城
娛樂城
福佑娛樂城致力於在網絡遊戲行業推廣負責任的賭博行為和打擊成癮行為。 本文探討了福友如何通過關注合理費率、自律、玩家教育和安全措施來實現這一目標。
理性利率和自律:
福佑娛樂城鼓勵玩家將在線賭博視為一種娛樂活動,而不是一種收入來源。 通過提倡合理的費率和設置投注金額限制,福佑確保玩家參與受控賭博,降低財務風險並防止成癮。 強調自律可以營造一個健康的環境,在這個環境中,賭博仍然令人愉快,而不會成為一種有害的習慣。
關於風險和預防的球員教育:
福佑娛樂城非常重視對玩家進行賭博相關風險的教育。 通過提供詳細的說明和指南,福佑使個人能夠做出明智的決定。 這些知識使玩家能夠了解他們行為的潛在後果,促進負責任的行為並最大限度地減少上癮的可能性。
安全措施:
福佑娛樂城通過實施先進的技術解決方案,將玩家安全放在首位。 憑藉強大的反洗錢系統,福友確保安全公平的博彩環境。 這可以保護玩家免受詐騙和欺詐活動的侵害,建立信任並促進負責任的賭博行為。
結論:
福佑娛樂城致力於培養負責任的賭博行為和打擊成癮行為。 通過提倡合理的費率、自律、玩家教育和安全措施的實施,富友提供安全、愉快的博彩體驗。 通過履行社會責任,福佑娛樂城為其他在線賭場樹立了積極的榜樣,將玩家的福祉放在首位,營造負責任的博彩環境。
риобет
Meds information. Brand names.
cialis soft
All information about medication. Read here.
Drugs information leaflet. Effects of Drug Abuse.
valtrex brand name
Best information about medication. Get information here.
Meds prescribing information. Brand names.
pregabalin no prescription
All news about medicine. Read information now.
Drugs information sheet. Short-Term Effects.
xenical
Some news about medicines. Read now.
Medicine information leaflet. What side effects?
celebrex online
Best information about drug. Read information now.
Medicines information for patients. Drug Class.
cytotec generic
All what you want to know about drugs. Get now.
Medicine information sheet. Long-Term Effects.
cleocin tablet
Some what you want to know about medicine. Get here.
Medicine information for patients. Effects of Drug Abuse.
baclofen otc
Best about drugs. Get now.
Drug information. Long-Term Effects.
valtrex prices
Best what you want to know about meds. Read here.
Meds prescribing information. Short-Term Effects.
cialis super active
Some trends of pills. Get now.
up x
Medicine information sheet. Short-Term Effects.
get effexor
Everything what you want to know about medicines. Get now.
1xslots
Medicament prescribing information. Generic Name.
celebrex
Best what you want to know about medicines. Read information now.
риобет
Medicine information leaflet. Generic Name.
xenical for sale
All trends of meds. Read information here.
Drugs information leaflet. Drug Class.
singulair
Best news about medicine. Get here.
Danish online pharmacy reviews
Medication information sheet. What side effects?
zithromax
Everything information about medicine. Get here.
Medicines prescribing information. Generic Name.
xenical
Best trends of medicines. Read here.
https://anotepad.com/notes/k3a84ee5
Meds information. Generic Name.
xenical
Everything what you want to know about pills. Get information now.
8ft bamboo fencing
Medicament information. Short-Term Effects.
norpace generics
Actual trends of drugs. Read information here.
юрист по недвижимости консультация бесплатно
Drugs prescribing information. Drug Class.
strattera
Some news about medicament. Read here.
Medicines information sheet. Drug Class.
retrovir
Best what you want to know about medicament. Get now.
Medication information. Drug Class.
viagra
Everything what you want to know about meds. Get here.
Medicine information. Brand names.
zoloft without a prescription
All news about meds. Get now.
Drugs information for patients. Effects of Drug Abuse.
minocycline
Some information about medicament. Get now.
Meds prescribing information. What side effects can this medication cause?
pregabalin medication
Actual news about drug. Get information now.
Medicament information sheet. What side effects can this medication cause?
lisinopril
Actual news about medicines. Get information now.
Meds information. Drug Class.
cordarone
Some about medicament. Get information here.
up x
Pills information for patients. What side effects?
lyrica order
All news about drug. Read now.
Medicament information for patients. Cautions.
buy generic lisinopril
Everything news about drugs. Get now.
Medicines information. Drug Class.
cytotec rx
Some news about pills. Get information now.
Drug prescribing information. Long-Term Effects.
lyrica generics
Everything trends of pills. Read here.
actos side effects
Medication information for patients. Brand names.
amoxil
Actual trends of medicines. Get here.
Drug information. Short-Term Effects.
buy generic fluoxetine
Best about medicine. Read information now.
ashwagandha reddit
Medication information sheet. Drug Class.
neurontin medication
Best information about meds. Get information now.
cefixime side effects
who can buy cleocin online
Meds information for patients. Effects of Drug Abuse.
synthroid medication
Some information about medication. Get information now.
colchicine canadian pharmacy
cordarone bnf
buying doxycycline
how to buy cheap levaquin online
can i order lisinopril prices
Medication information for patients. Brand names.
phenergan
Everything information about medication. Read information now.
prednisone medication guide
protonix excretion
Stromectol dosage
buying tetracycline
buy actos 30 mg online
does ashwagandha increase testosterone
cefixime 100 gram price
Medication information. Drug Class.
fosamax
Actual about meds. Get information here.
cleocin
buy colchicine nz
order cordarone without prescription
Самый крупный магазин в России – Hydra, предлагает каждому пользователю получить доступ к неограниченным возможностям и разносторонним товарам. Это лучшая площадка, которая обеспечивает 100% анонимность каждому пользователю, гарантирует скорость и безопасность. Здесь можно найти тысячи продавцов с разными товарами. Потому стоит выбирать наиболее выгодные предложения и рассматривать каждого. Это свободный рынок, что позволяет конкурировать. Гидра онион работает по адресу https://xn--hydr2wb-dn4cki.com , и не требует подключения TOR или VPN. Достаточно перейти на сайт и быстро попасть в огромный магазин. Потому не теряйте время, и окунитесь в новый для себя мир. hydra даркнет
can you get cheap levaquin no prescription
buy actos 30 mg online
Medication prescribing information. Long-Term Effects.
zoloft
Actual trends of medicines. Read information now.
dosage for amoxicillin 250mg capsules
Drugs information leaflet. Short-Term Effects.
how to buy retrovir
Everything trends of medication. Get here.
immune system support
Drug information. Cautions.
zofran buy
Everything what you want to know about drugs. Read information now.
Drugs information leaflet. Brand names.
cephalexin pill
All about drug. Get information here.
cefixime for gonorrhea
Medicament prescribing information. Brand names.
zovirax
All about medicines. Get now.
zyrtec tablet
Drug information for patients. Short-Term Effects.
clomid
All about medication. Get now.
medication cleocin
Drug prescribing information. Short-Term Effects.
where can i buy motrin
Actual about drug. Get information here.
colchicine tablets for sale uk
Medicine prescribing information. Short-Term Effects.
prednisone
All about medicine. Read information now.
Pills information. Generic Name.
diltiazem
Best information about medicine. Get here.
Medicine prescribing information. Drug Class.
flibanserina
All about meds. Read here.
what is cordarone prescribed for
Meds information sheet. What side effects can this medication cause?
celebrex buy
Some information about meds. Read now.
diltiazem side effects in elderly
Medicine information sheet. What side effects can this medication cause?
zoloft
Everything news about drugs. Get information now.
Очень ценное сообщение
now you may be wondering how to seek out https://www.itron.com/es/company/newsroom/2023/01/31/itron-expands-distributed-intelligence-platform-to-accelerate-energy-transition online.
doxycycline hyclate 100 mg treats what
erbalegale.vip
Medicine information. Drug Class.
strattera
Actual news about drugs. Get now.
furosemide indications
CBD shop
Я считаю, что Вы не правы. Давайте обсудим.
vr https://procesal.cl/index.php/ai_created_porn will not take off till the means of manufacturing are democratized.
Meds information for patients. Effects of Drug Abuse.
tadacip medication
Actual about medicines. Get here.
Medicines information for patients. Brand names.
fosamax
All what you want to know about medicines. Get here.
Medication information. Brand names.
viagra soft brand name
Best what you want to know about medicines. Get information here.
amoxicilina efectos secundarios
Drug information for patients. What side effects?
singulair
Best about drugs. Get now.
На мой взгляд, это актуально, буду принимать участие в обсуждении. Вместе мы сможем прийти к правильному ответу.
—
Браво, отличное сообщение кирпичные пластиковые панели, показать пластиковые панели и https://atipionier.pl/nowoczesne-metody-ksztalcenia/ панели пластиковые стройландия
ashwagandha thyroid
Medication information for patients. Long-Term Effects.
cialis soft tablet
Everything information about drug. Get here.
cefixime safety
Medicines information sheet. Long-Term Effects.
pregabalin without prescription
Everything information about medicament. Read here.
cetirizine in pregnancy
Drug prescribing information. Generic Name.
paxil pills
Actual trends of drugs. Get now.
Drugs information leaflet. Generic Name.
cost promethazine
Actual news about medicines. Get now.
online prescription cleocin
colchicine excretion
Medicines information leaflet. Brand names.
propecia
Actual about pills. Read now.
cordarone 200 mg capsule cost
Ein toller Artikel, Danke dafür. Ich habe diesen auf Facebook geteilt
und massig Likes bekommen :)..
Medication information leaflet. Drug Class.
lyrica without a prescription
Some news about drug. Read here.
cardizem diltiazem
Medicines information. What side effects?
viagra medication
Actual what you want to know about medicines. Read now.
order doxycycline online cheap
Medicines information. Generic Name.
fosamax otc
Everything what you want to know about medicine. Read here.
furosemide 40 mg tablet
Я считаю, что Вы ошибаетесь. Предлагаю это обсудить. Пишите мне в PM, пообщаемся.
https://slivclub.com/ машины от 0.5 до 20 тонн.
Однозначно рекомендую этот сайт!печать каталоговПЕЧАТЬ КАТАЛОГОВ В НИЖНЕМ НОВГОРОДЕ ОТ КОМПАНИИ IMPRESS Мы специализируемся на изготовлении всех видов полиграфической продукции. В перечень наших услуг входят изготовление блокнотов, табличек и указателей, оформление для улицы, нанесение изображения на одежду, печать буклетов в Нижнем Новгороде и многое другое.
Medication information leaflet. Short-Term Effects.
neurontin
All news about medicine. Get information now.
levaquin brand name
Drug information leaflet. Brand names.
lyrica
Some about medicines. Get information now.
can i take lisinopril without food
Medicines information. What side effects can this medication cause?
pregabalin sale
Actual news about medication. Read information now.
Drug information leaflet. Long-Term Effects.
generic cialis soft flavored
Actual trends of meds. Get here.
Pills information for patients. Short-Term Effects.
promethazine pills
Everything information about medicines. Get information now.
Medicine information. What side effects?
albuterol rx
Some what you want to know about medication. Read information now.
Meds information leaflet. Cautions.
lyrica
Actual trends of medication. Read information here.
buy prasugrel
Medicament information sheet. Brand names.
minocycline
All trends of medication. Get here.
prednisone buy uk
Medicine information for patients. Generic Name.
fosamax
Actual about medicine. Read information now.
Medicament information sheet. What side effects can this medication cause?
singulair sale
Everything what you want to know about medicines. Read information here.
Любопытный вопрос
зующийся славой|пользующихся популярностью|прославленных|распространенных|славных} буква украине.
педагогика
Medication information sheet. Effects of Drug Abuse.
can you buy effexor
All information about drug. Get information here.
Мне кажется это блестящая мысль
каким образом заливать себе эксклюзивные видеокурсы без оплаты, свежие https://slivbox.com/ свежайших обучений но.
Try ChatGPT
Revolutionizing Conversational AI
ChatGPT is a groundbreaking conversational AI model that boasts open-domain capability, adaptability, and impressive language fluency. Its training process involves pre-training and fine-tuning, refining its behavior and aligning it with human-like conversational norms. Built on transformer networks, ChatGPT’s architecture enables it to generate coherent and contextually appropriate responses. With diverse applications in customer support, content creation, education, information retrieval, and personal assistants, ChatGPT is transforming the conversational AI landscape.
Medicine prescribing information. Long-Term Effects.
order neurontin
Some trends of drug. Read information now.
prograf 5 mg
Medicament information. Cautions.
celebrex otc
Best what you want to know about drug. Get information here.
молодец
играть в онлайн джой казино мостбет.
Pills information sheet. Brand names.
pregabalin
All information about medicines. Read now.
protonix 40 mg
Meds information for patients. Generic Name.
viagra
Best news about meds. Get now.
Medicament information for patients. Long-Term Effects.
clomid
Everything trends of medication. Read information now.
Pills information. Generic Name.
prednisone
Everything information about drug. Read here.
Однозначно рекомендую этот сайт!изготовление стендовИзготовление стендов информационных с карманами может понадобиться в самых разных сферах деятельности. Школа, детский сад, университет, столовая, поликлиника и другие учреждения – планы помещений и место для размещения важных материалов необходимы для каждого общественного места. В типографии Impress вы можете заказать информационные стенды с карманами недорого и в соответствии с требованиями нормативных документов. Например, планы эвакуации должны полностью удовлетворять регламенту стандартов пожарной безопасности. Давайте подробнее рассмотрим, какую продукцию вы найдете в данном разделе и как сделать заказ на нашем сайте.
И что же?
https://msk.laserdoctor.ru/ на столице, отзывы а также цены в платформе.
stromectol dosage for pinworms
онлайн-казино fonbet by http://coincoffee.kr/bbs/board.php?bo_table=free&wr_id=24724.
Medicines information for patients. Cautions.
flibanserina
All news about drugs. Get here.
Medication information leaflet. Short-Term Effects.
cordarone
Some information about medicament. Get now.
Medicine prescribing information. What side effects?
viagra
Some information about medicine. Get now.
Every weekend i used to pay a visit this website,
ass i wish for enjoyment, since this this website conations really pleasant funny
information too.
Feel frree to surf to my homepage – 유로밀리언
buying tetracycline
я ржал
ундоровская минеральная https://lechebvoda.ru/.
Meds information. What side effects can this medication cause?
clomid brand name
Best news about medicine. Get information now.
Drugs information for patients. Drug Class.
viagra
Some information about medicine. Read here.
Medicines prescribing information. What side effects?
isordil
Some trends of medicines. Read here.
Pills information for patients. What side effects can this medication cause?
levaquin
Everything news about medicine. Read here.
Да, действительно. Я присоединяюсь ко всему выше сказанному. Можем пообщаться на эту тему. Здесь или в PM.
однако купить виртуальный номер можно (бог) велел возможно впору годится.
Medicament information sheet. Short-Term Effects.
lisinopril
Some trends of medicines. Read information here.
actos 10 mg
Drug information for patients. Brand names.
cialis
All trends of medicines. Get now.
Medication information. Cautions.
zoloft prices
Actual what you want to know about medicines. Read information now.
Всем рекомендую этот сайт!Печать наклеекМы изготавливаем рекламные виниловые наклейки, наклейки на витрины, оракальную резку, стенды пожарной эвакуации, наклейки для транспорта.
Meds information sheet. What side effects?
zovirax
Some news about drugs. Get information here.
amoxicillin drug class
in 1881 the newport https://demo.ycart.kr/shopboth_flower_001/bbs/board.php?bo_table=free&wr_id=102530 hosted the first u.
Medicament information sheet. Long-Term Effects.
baclofen medication
Some trends of medication. Get information here.
Medicines information sheet. Short-Term Effects.
cephalexin
Everything trends of medication. Read information now.
ashwagandha extract
Medicament information sheet. Short-Term Effects.
prednisone cost
All news about drug. Get information now.
Drug information for patients. Drug Class.
zoloft buy
All news about medicine. Get here.
Drugs information sheet. What side effects?
pregabalin
Actual information about pills. Get here.
cefixime and alcohol
Medication information for patients. What side effects can this medication cause?
buy celebrex
All information about medication. Read information now.
Drug information sheet. What side effects?
neurontin otc
Actual trends of medicine. Get information here.
https://tacticalmagazin.com/av-sezonu-acilis-ve-kapanis-tarihleri-836.html
cetirizine bnfc
Meds information for patients. Effects of Drug Abuse.
generic singulair
Actual about medicine. Read now.
По моему мнению Вы ошибаетесь. Пишите мне в PM, обсудим.
огромная база https://moresliv.biz платных обучающих материалов по подписке.
онлайн-казино fonbet by http://www.webxrhub.com/bbs/board.php?bo_table=free&wr_id=146359.
cleocin 150 mg capsules
Medicines information sheet. Drug Class.
motrin without rx
All information about medicines. Read information here.
can i buy colchicine for sale
It’s not my first time to pay a quick visit this website, i am
browsing this web page dailly and obtain good information from here
daily.
cordarone withdrawal symptoms
diltiazem side effects
can you buy doxycycline on line without a prescription
furosemide 40 mg para que sirve
Drugs information. Short-Term Effects.
cost viagra
Best trends of medication. Get here.
Pills information for patients. What side effects?
celebrex for sale
Actual about meds. Read now.
can you buy generic levaquin without prescription
prescription drug prices lisinopril
Medication information for patients. Long-Term Effects.
propecia cost
Actual information about medicines. Read here.
Meds information leaflet. Drug Class.
how to buy aripiprazole
Some about medicines. Get now.
Meds information. What side effects?
viagra without insurance
Everything what you want to know about medicament. Get information here.
Meds information for patients. What side effects?
cipro cheap
Actual information about drug. Get information now.
Drugs information leaflet. What side effects can this medication cause?
minocycline without dr prescription
Some about medicament. Get now.
Meds information for patients. What side effects?
finasteride otc
All news about pills. Read here.
Medication prescribing information. What side effects?
colchicine
Everything news about meds. Read here.
Medication information sheet. Brand names.
get flibanserina
Best information about pills. Get information here.
efient
Meds prescribing information. What side effects?
fosamax buy
All trends of medicines. Get information now.
prograf order now
protonix otc
Medicine information sheet. What side effects?
trazodone
Actual trends of medicine. Get information here.
Medicine information. Brand names.
flagyl
All trends of medicament. Get information now.
stromectol for head lice
Tetracycline warnings
Drug information sheet. Cautions.
synthroid
Some about drug. Read information here.
Medicament information. Effects of Drug Abuse.
sildenafil sale
Best information about medicines. Read information now.
Drugs information for patients. Short-Term Effects.
abilify
All trends of meds. Get information now.
discount actos
amoxi
does ashwagandha increase testosterone
Medicine prescribing information. What side effects can this medication cause?
get pregabalin
Actual news about medicines. Read information here.
cefixime for gonorrhea
Drug information. Brand names.
propecia for sale
All trends of medication. Read information here.
does zyrtec cause drowsiness
cleocin excretion
where can i buy generic colchicine
Drug information for patients. Effects of Drug Abuse.
generic pregabalin
All news about medicines. Read information here.
cordarone metabolism
Medication information sheet. Drug Class.
lisinopril
Best about meds. Read information now.
Drug prescribing information. Cautions.
pregabalin cost
Best news about medicament. Get information here.
diltiazem cream
Medicine information. Cautions.
amoxil
Best about medicine. Read here.
зарегистрироваться cat casino
Medicines information. Brand names.
priligy
Actual information about drug. Read information here.
Medicament prescribing information. Effects of Drug Abuse.
xenical
Some about meds. Read information now.
Drug information sheet. Brand names.
clomid pill
Some news about medicament. Read information here.
Meds information for patients. Drug Class.
neurontin brand name
All trends of medication. Get here.
Medicament information for patients. What side effects?
can you get viagra soft
Some about meds. Read information now.
Medicament information leaflet. Short-Term Effects.
propecia medication
Everything trends of meds. Get now.
can i order cheap levaquin online
Medicament information sheet. Generic Name.
colchicine
Best about medication. Read information now.
can i take lisinopril without food
Medicament information sheet. Cautions.
proscar
Best information about medicine. Read information now.
Medicament information. Brand names.
ketorolac
All news about medicament. Get information now.
Medicament information leaflet. Generic Name.
propecia
All about medicine. Get now.
Drugs prescribing information. Short-Term Effects.
rx cialis
Some what you want to know about drugs. Get information here.
Meds prescribing information. What side effects?
finasteride medication
All information about pills. Read information now.
Drugs information. Short-Term Effects.
priligy
Some trends of medicine. Get information here.
Medication prescribing information. Brand names.
sildigra
All information about pills. Get information here.
Medicines information for patients. Short-Term Effects.
viagra
All news about drug. Read here.
Medicament prescribing information. Effects of Drug Abuse.
lioresal
All what you want to know about medicines. Read now.
Medication information leaflet. Short-Term Effects.
singulair
Best news about drugs. Read here.
лучшие автомобильные аккумуляторы
Drugs information for patients. Short-Term Effects.
zoloft
Everything trends of drugs. Get information now.
Medicines information. Brand names.
cheap celebrex
Actual trends of medication. Get now.
Its like you read my mind! You appear to know a lot about this, like you wrote the
book in it or something. I think that you can do with some pics to drive the message home a bit, but instead of that, this is wonderful blog.
A great read. I will certainly be back.
Here is my web page – بک لینک انبوه
Drug information leaflet. What side effects can this medication cause?
avodart
Everything about medicines. Read now.
generic prasugrel
prograf 1 mg
protonix metabolism
Stromectol oral suspension
Drug information sheet. Generic Name.
cephalexin
Everything trends of drugs. Read information here.
tetracycline for birds
Medicine information sheet. Drug Class.
viagra
Everything what you want to know about medicament. Read information here.
Pills information. Short-Term Effects.
pregabalin online
All what you want to know about medicines. Get information now.
actos patient assistance
Drugs information leaflet. What side effects?
buying retrovir
Best information about medication. Get information here.
Drugs information for patients. Short-Term Effects.
generic trazodone
All information about pills. Read information here.
Great site! I recommend it for viewing!como residences NakheelComo Residences by Nakheel offers a truly exceptional living experience, characterized by panoramic views, opulent interiors, exclusive amenities, and a prime location. It stands as an architectural masterpiece, providing residents with an unparalleled cosmopolitan lifestyle.
Medicine information. Effects of Drug Abuse.
viagra soft without insurance
Actual trends of medication. Get information here.
ashwagandha research
Medicines information. What side effects can this medication cause?
norpace
Some what you want to know about pills. Get information here.
Medicine information leaflet. What side effects?
buying fosamax
Best trends of medication. Read information now.
lady police fuck
Drug information leaflet. Generic Name.
cost neurontin
All about pills. Get information here.
Meanwhile, there is also a rewarding loyalty plan to appear forward
to.
Here is my web blog – 메이저카지노
Meds information for patients. Drug Class.
amoxil brand name
Everything news about medication. Get information here.
I’m impressed, I have to admit. Seldom do I encounter a blog that’s both
equally educative and engaging, and let me tell you, you have hit the nail on the
head. The issue is something that not enough folks are speaking intelligently about.
I’m very happy I came across this in my search for something concerning this.
zyrtec for dogs
cleocin brand name
Both Bryan and Spradley say that they would have created more plans
for their time off.
Here is my web page 노래방 알바
Drug information. Generic Name.
baclofen medication
All information about medicines. Get here.
colchicine price australia
cordarone drug interactions
diltiazem hcl
Medicines information. What side effects can this medication cause?
strattera
Everything what you want to know about pills. Get here.
doxycycline 200 mg tablets
Medicine information sheet. Cautions.
cytotec
Everything news about pills. Read now.
kmsauto password
levaquin side effects older people
cost of generic lisinopril 10 mg
Medicines information sheet. What side effects?
cialis super active tablet
Everything trends of medication. Get information here.
Meds information leaflet. Short-Term Effects.
zoloft sale
Everything information about drug. Read now.
You have made your point extremely clearly!.
Nice residence! I recommend it!como residence palm jumeirahComo Residences by Nakheel offers a truly exceptional living experience, characterized by panoramic views, opulent interiors, exclusive amenities, and a prime location. It stands as an architectural masterpiece, providing residents with an unparalleled cosmopolitan lifestyle.
effient blood thinner
Pills information. Short-Term Effects.
generic clomid
All what you want to know about medicines. Get information here.
order prograf
From mid-2022 to now, hundreds of thousands of college-educated office experts have been laid off.
Here is my web-site: site
protonix metabolism
Even for parents who can locate and afford childcare, the existing atmosphere is still a challenge, Williamson says.
Heree is my web page 여성알바
stromectol stromectolmail
There are two restrictions to hold in thoughts, but the very
first really should be clear.
Review my web site – 카지노
We score PlayOJO an 8 out of 10 for their wager-no cost
bonus spins.
Feel free to visit my website 우리카지노
Thank you! Plenty of info.
Here is my web site; https://webdigitalonline.com/page/sports/vis-o-geral-dos-slots-de-cassino-online-f12bet
tetracyclin
Medication information for patients. What side effects can this medication cause?
cleocin
Some what you want to know about medicine. Get now.
Medication information leaflet. What side effects?
generic mobic
Best news about drug. Get now.
Drug information. What side effects can this medication cause?
lasix
Some what you want to know about medication. Get here.
Meds information leaflet. What side effects can this medication cause?
pregabalin medication
Best news about meds. Read information here.
Medicine information for patients. Effects of Drug Abuse.
levaquin cheap
Best about medicines. Get now.
Discrimination based on gender, nationality, religion or
social status is expressly prohibited beneath the LSA.
Have a look at my page: 밤알바
Medication information sheet. Long-Term Effects.
lasix
Some about medication. Get here.
can i buy actos 30 mg
Drugs information leaflet. Drug Class.
viagra generic
Actual information about meds. Read information here.
The web page
makes use of SSL certificate technology to preserve user data secure.
Pills information for patients. Drug Class.
cytotec
All information about drug. Read information now.
In these conditions, the government has decided
too make an exception to the general rule of at-will employment.
my web-site 단란주점 알바
You agree to indemnify and hold harmless the Firm
for any claims, demands, liens, or judgments primarily based on your non-payment or underpayment of such taxes.
Take a look at my homepage :: 온라인바카라
Scan receipts, stickies, and other documents in seconds making use
of your phone’s camera.
Here is my blog … 파워볼게임
No one wants to hire an lawyer or a brain surgeon and uncover out that their
case is hiss 1st true job.
Feeel free to visit my web page – web site
Good info, Regards.
my site – spin samurai casino review (http://www.lawrence.com/users/pricinouvys1989/)
You could redeem the spiins by depositing additional than £10 and entering the FREESPINS code.
Here is my web-site 온라인바카라
create a fake citizenship card
You stated this superbly.
Also visit my site: babu.88 (https://fatek.unsrat.ac.id/informatika/)
fake marriage for citizenship cases
Being in a position to speak Korean will definitely give you some advantages.
Here is my homepage 여성 알바
We created this platform so you’ll have the ability to chat with strangers freed from price, no catch
in any respect.
Therefore, bot actijvity that does not conform to BLS usage policy is prohibited.
my web site: 여성유흥알바
In the screenshot above, “Joy Moore” developed her account in October
2022.
Here is my website 텐프로 알바
amoxicillin
Pills information leaflet. Cautions.
can you get amoxil
Actual about medicine. Get here.
Minimum deposits are set at a low $20,so you do not have to break
the bank to get in on the action.
my blog post 카지노사이트
Thiss will give you priority ith immigration and let you apply for a
wider variety of positions.
Stop bby my site … 밤알바 직업소개소
Macau
Also visit my web blog … web page
Medication information. Generic Name.
nexium
Actual about meds. Get now.
To challenge policymakers who think that eroding wofker protections are an acceptable indiucates of remaining the “No.
Also visit my site … 밤알바
A steep rise in daycare expenses cwments childcare
as a structural barier for job seekers with youngster-rearing responsibilities.
My blog – 주점 알바
Medicament information for patients. Generic Name.
cytotec generic
Everything what you want to know about drugs. Get now.
A lot of work in restaurants and supermarkets, and one particular of our organizeers has been bargaining in his job at a sushi restaurant
chain.
Feel frree to surf to my web-site homepage
Enlisting as portion-time reservist ensures your civilian job is safe.
Have a look at my page – web page
Most of the time, the job posting will list if the applicant needs a distinct
visa.
my website :: bj알바
If a casinno is licensed and regulated and their games are audited
for fairness, yoou can rest assured thhat the slots are not rigged.
Also visit my web blog – web site
It’s wha Treasury officials, Reserve Bank officials, ABS statisticians and economists use to locate the unemployment
rate.
My blog: homepage
This casino web-site is a further member of thhe Fortune
Lounge Group, raking in a comfortable $13.7 milplion annual income.
Feel free to surf to my website: get more info
Rabona has latelly created a name for itself oon the sports betting scene,
and it is simple to see why.
my blog … 보증된카지노사이트
Thhe principal possibilities will be utijlizing cryptocurrency or a debit/credit card.
Visit my website :: https://wurae.bloginder.com/
This kind of work does not count towards your 20 hours per week off-campus
pereform limit.
Here is my blog post: web page
These part-time jobs are also situated on the Town Bulletin Board and are unhlocked on 5/25.
My site: 여성 유흥알바
Aspect-time students continue taking requiired courses, along with elective courses, during the initially semester of the second year.
My page – homepage
Hello there I am so thrilled I found your weblog, I really
found you by mistake, while I was searching on Yahoo for something else, Anyhow I am here now and would just like to say many thanks for a tremendous post
and a all round thrilling blog (I also love the theme/design), I don’t have time to read through it all at the moment but I have saved it and
also added in your RSS feeds, so when I have time I will be back to read a great deal more, Please do keep up the great work.
No matter how enticing their casino bonusses may be,
never sign up with rogue websites.
Feel free to surf too my blog; website
Thhe no wagering conditions and the 30 day expiration time
makes thks bonuis suitable for new players who play slots.
Feel free to visit my website :: read more
For players in New York, this function iis exceptional and only offered
through Jackpocket.
Also visit my web blog :: homepage
Our HR statistics show that virtually 50% of
recruiters will reject a resume with no cover lettr attached.
Here is my blog post … 밤알바
Medication information for patients. Drug Class.
avodart
All information about drug. Read here.
I rarely drop comments, but after looking at a lot of responses on Traffic analysis of a
packet capture with Wireshark • Allhacked.
I do have 2 questions for you if it’s allright.
Is it only me or does it appear like some of these remarks
appear as if they are left by brain dead people?
😛 And, if you are writing at additional social sites, I’d like to keep up with you.
Could you post a list of all of all your shared sites like your twitter feed, Facebook page or linkedin profile?
Also visit my blog post – Phoenix search engine optimization
It has been about for a long time but then why iis it garnering focus all of a
sudden?
my wweb blog … 유흥알바
Pills information sheet. Long-Term Effects.
promethazine online
Actual news about medicine. Read here.
Meds information leaflet. Short-Term Effects.
neurontin
Everything about medicines. Read information now.
Amazing postings. Regards.
My web site: http://msnho.com/blog/download-mobile-casino-application-spinago
Medication information for patients. Generic Name.
where buy retrovir
Best news about medicines. Read information now.
Medicines information sheet. Effects of Drug Abuse.
zovirax generics
Actual trends of medication. Read here.
They suit borrowers with a assured revenue in have
to have of urgent and unplanned cash.
Also visit my web blog – 정부지원대출
Medication information leaflet. Drug Class.
viagra soft
Everything about drug. Read here.
Aviator games are a sort of crash game so there is no difference amongst them.
Also visit my website:click here
Medicine information. Short-Term Effects.
celebrex online
Actual news about meds. Read information here.
Medicines information sheet. What side effects can this medication cause?
levaquin cost
Some what you want to know about meds. Get information now.
Medicine information sheet. Short-Term Effects.
celebrex
Some news about drugs. Get now.
The Yale Center has also investigated gender-related variations in gambling behaviors and problems.
My web-site … 온라인바카라
Medication information leaflet. Long-Term Effects.
propecia
Actual information about medicines. Get information here.
Your event staff can scan thius code at the occasion entrance to promptly
aand securely verify tthe attendee’s identity aand grant them access.
Feel free to visit my web site; 동행복권 파워볼
Meds prescribing information. Long-Term Effects.
lyrica buy
Everything trends of drug. Read information here.
Всем рекомендую этот сайт,тут лучшее производство и монтаж пластиковых окон REHAU! Пластиковые окна80% наших клиентов это повторные обращения. Мы работаем с оглядкой на нашу репутацию и дорожим каждым клиентом.
Medicines prescribing information. Cautions.
where can i buy abilify
All about pills. Get information now.
Thanks a lot, A good amount of knowledge.
My site – https://krakeldebakel.blockblogs.de/2016/03/09/hier-koennte-ihr-titel-stehen/
Wow loads of beneficial facts.
Here is my blog … https://riversidemusic.com/shop/acoustic_guitars/beavercreek-three-quarter-size/
Useful stuff, Many thanks.
my site … http://hegemone.co.uk/the-latest-spa-craze/
Medicine information sheet. Cautions.
where to buy sildenafil
Some what you want to know about medicament. Read information here.
Kneader’s appp Gyugu connects employers with element-time job seekers inn Korea.
my site; 이지알바
Drug information sheet. Long-Term Effects.
promethazine
Some news about medicament. Get information here.
Klairung, the originator oof Thai West Massage is initially from Thailand.
my web site: 스웨디시마사지
Medication information sheet. What side effects can this medication cause?
maxalt
Actual information about pills. Get information here.
The warm tones are calming, whilst the tropical fruits will gently uplift.
My web-site :: 스웨디시 거리
Hey there, You’ve done a great job. I’ll certainly digg it and personally suggest to my friends.
I’m sure they will be benefited from this website.
Moreover, massage helps rediced blood stress, wich ccan help ward against the onset of cardiovascular disease.
Here is my homepage – 스웨디시 할인
Medicines information sheet. Long-Term Effects.
cheap pregabalin
Some news about meds. Get information now.
It’s really a cool and helpful piece of information. I am satisfied that you just shared this useful info with us.
Please stay us up to date like this. Thank you for sharing.
Всем рекомендую этот сайт,тут лучшее производство и монтаж пластиковых окон REHAU! остекление домов80% наших клиентов это повторные обращения. Мы работаем с оглядкой на нашу репутацию и дорожим каждым клиентом.
Some lenders cater to borrowers who cannjot get approved elsewhere with emergency loans,
payday loans, and negative-credit or no-credit-check loans.
Feel free to visit my sitee … 일수대출
Drug information. What side effects can this medication cause?
diltiazem
Actual information about medicine. Read here.
In New Jersey the highest no deposit bonus supplied is by BetMGM.
Also visit my page: https://somes.ivasdesign.com
Pills information for patients. Short-Term Effects.
neurontin medication
All what you want to know about meds. Get information here.
certainly like your web site but you have to take a look at the spelling on several
of your posts. Several of them are rife with spelling
issues and I find it very troublesome to
inform the reality on the other hand I will surely come again again.
Labour supervisors affiliated with itt (who also act as judicial
police officers) oversee compliance with employment laws.
My blog 여성알바
Pills prescribing information. Short-Term Effects.
order cephalexin
Actual what you want to know about pills. Read information here.
Miix two-3 drops of rosemary oil in a hair-friendly carrier
oil such as coconut oil, argan oil, jojoba oil, or almond oil.
Here iis my web blog :: 스웨디시마사지
You can still win on a bonus bankroll and even a decent amount,
but it will not be a as soon as-in-a-lifetime prize.
my web blog – 카지노사이트
Drugs information sheet. Cautions.
abilify
Actual news about drug. Read now.
Подтверждаю. Так бывает. Давайте обсудим этот вопрос. Здесь или в PM.
на иных ситуациях купить виртуальный телефонный номер контакты для паролей mailgroup невозможно.
Medication information. Generic Name.
abilify otc
Some what you want to know about drug. Get here.
Drugs information sheet. Short-Term Effects.
viagra
Actual trends of pills. Get here.
Thanks for your marvelous posting! I definitely enjoyed reading it,
you could be a great author.I will ensure that I bookmark your blog
and definitely will come back in the foreseeable future.
I want to encourage that you continue your great posts, have
a nice day!
Medicine prescribing information. Long-Term Effects.
cytotec order
Some information about meds. Read information here.
Medication information leaflet. Brand names.
pregabalin
Actual what you want to know about drug. Get information here.
The help agents arre at your disposal 24/7, each and very dayy of the year.
Also visit my blog poist … 메이저토토사이트
Абсолютно с Вами согласен. Это хорошая идея. Готов Вас поддержать.
риа https://www.centrostudiluccini.it/20180528_101827/ (3 февраля 2014).
Medication information sheet. Generic Name.
viagra tablets
Actual what you want to know about drug. Read information now.
Yes, on line loanss with a relable lender are perfectly safe to
take out.
Here is my page :: 대출정보
Hey there! Do you know if they make any plugins to safeguard against hackers?
I’m kinda paranoid about losing everything I’ve worked hard
on. Any tips?
Drug information. Brand names.
cialis price
Actual news about pills. Read information now.
You can win cash at sweepstakes casinos that use a exdclusive Sweeps Coins model.
My blog … more info
Medication prescribing information. What side effects can this medication cause?
pregabalin order
Some news about medicines. Get now.
Pills information for patients. Short-Term Effects.
levaquin online
Some news about meds. Read information here.
With these games, you get a ticket that typically has
a latex-like ssubstance covering the playing surface.
Review my blog post :: 파워볼중계
Medicament information. Long-Term Effects.
cleocin
Everything about medicines. Get here.
Lindxay is a freelance tracel and life-style journalist covering subjects from appreciate,
marriage, fitness, wellness, psychology, and entrepreneurism.
Feel free too visit my web site … 스웨디시마사지
Pills information sheet. Long-Term Effects.
lyrica
All about pills. Read now.
If youur horse racee betting extends to games then you will want this selection as nicely.
my webpage; https://newsbbidis.blogspot.com/2023/03/how-how-to-online-sports-gamble-could.html
My spouse and I stumbled over here coming from a different web
page and thought I might check things out. I like what I see so now i’m following you.
Look forward to going over your web page for a second time.
Therapists use firm stress in combination with stretchinbg and twising our body.
my website :: 마사지
Medicine information. Cautions.
nexium
Everything news about drug. Read information here.
Thank you, I value this.
These consist of banks, credit unions, online lenders and peer-to-peer lenders.
Review my web-site – 소액대출
Medicament information leaflet. Generic Name.
celebrex medication
Actual trends of drugs. Get here.
This facilitates transactions as properly as other attributes such as auto-pay, month-to-month subscription deductions, and so on.
Also visit my website … 정부지원대출
RotoGrinders.com iss the residence of the daily fantasy
sports community.
My web blog … more info
Medicines information for patients. Long-Term Effects.
zoloft
Actual what you want to know about meds. Read information now.
Drugs information leaflet. Short-Term Effects.
order neurontin
Some trends of medicines. Get information now.
Wow that was unusual. I just wrote an very long comment but after I clicked submit my comment didn’t appear.
Grrrr… well I’m not writing all that over again. Anyways, just wanted
to say excellent blog!
the alternative to personalize treatmnt for those customers who want a relaxing day
Also visit my website 스웨디시마사지
This article offers clear idea in favor of the new users of
blogging, that actually how to do running a blog.
my site renovate your home Oakville Canada
Meds information for patients. Generic Name.
neurontin pills
All trends of meds. Read information now.
Medicines information for patients. Cautions.
cost zoloft
Some information about medicines. Read now.
Although the direct lenders do not execute any credit check, they have all
rights reserved to accept or reject an application.
My blog: 회생파산대출
Meds information sheet. Long-Term Effects.
zovirax
Best news about drugs. Read here.
Good article. I will be facing a few of these issues as well..
Hi there! Do you use Twitter? I’d like to follow you if that would be okay.
I’m definitely enjoying your blog and look forward to new updates.
Medicament information leaflet. Drug Class.
abilify medication
Actual about drugs. Read here.
Drug information leaflet. Short-Term Effects.
propecia
Best about medication. Read information now.
natural tits fuck
naturally like your website but you need to take a look at the spelling on several of your posts.
Many of them are rife with spelling issues and I find it very
bothersome to inform the truth then again I’ll surely come back again.
massive cumshot compilation
Meds information sheet. What side effects?
synthroid
All about medication. Get here.
Meds information leaflet. Cautions.
levaquin otc
Best about pills. Get now.
I am regular visitor, һow агe уou everybody? Τhis post posted att tһis web sitte is actually good.
Feel free to surf tօ my web blog :: 카지노먹튀
actos weight gain
Expanding Adoption off Augmented Reality and Virtual
Reality in GamblingGambling iss highly sensitive and responsive to
new technologies and innovations.
Feel frwe to surf to my web-site – website
Great post.
Drug information sheet. Effects of Drug Abuse.
lasix
Everything about meds. Read here.
You will uncover lads of cash games annd tournaments, with a wide range of purchase-ins.
My page :: 메이저토토사이트
amoxicillin 500 mg dosage instructions
ashwagandha side effects men
Medication information sheet. What side effects?
norpace for sale
Best news about meds. Get information now.
cefixime antibacterial activity
Medication information sheet. Effects of Drug Abuse.
effexor
Some news about drugs. Get here.
cetirizine obat apa
One particular issue with this new website is that they do not appear to have a promos section however.
my page; separesupere.com.br
If youu don’t spen back the money you borrowed, it’s known as defaulting on your payday
loan.
Here is my page … 대환대출
ciprofloxacin bnf
Meds information leaflet. Drug Class.
lisinopril
Everything news about pills. Get here.
cleocin 75 mg
Meds information sheet. Brand names.
trazodone
Actual what you want to know about drug. Read now.
colchicine gouty arthritis
Drug information leaflet. Long-Term Effects.
lyrica for sale
Actual about meds. Read here.
cordarone contraindications
diltiazem pronunciation
Eleven percent of private-sector workers are provided some
type of employer-administered kid care advantage, such as subsidies or onsite facilities —
about onn par with 2020.
Have a look at my website: 비제이 알바
Once more, there is no transaction chjarge but the
max deposit limit for bitcoin iis substantially greater at $two,500.
Feel free to suhrf to my site – web page
doxycycline 100 mg
furosemide 40 mg weight loss
real milf orgasm
I loved as much as you will receive carried out right here.
The sketch is tasteful, your authored subject matter
stylish. nonetheless, you command get got an shakiness over that
you wish be delivering the following. unwell unquestionably
come further formerly again as exactly the same nearly a lot often inside case you shield this hike.
I believe that is one of the most significant information for me.
And i am glad studying your article. But wanna observation on few general things, The site style is perfect, the articles is really excellent :
D. Excellent activity, cheers
webcam group sex
Wow, tһiѕ article is pleasant, my sisteer іs analyzing ѕuch tһings,
thuus І am going too convey heг.
my hߋmepage 슬롯사이트
tải b52
B52 là một trò chơi đổi thưởng phổ biến, được cung cấp trên các nền tảng iOS và Android. Nếu bạn muốn trải nghiệm tốt nhất trò chơi này, hãy làm theo hướng dẫn cài đặt dưới đây.
HƯỚNG DẪN CÀI ĐẶT TRÊN ANDROID:
Nhấn vào “Tải bản cài đặt” cho thiết bị Android của bạn.
Mở file APK vừa tải về trên điện thoại.
Bật tùy chọn “Cho phép cài đặt ứng dụng từ nguồn khác CHPLAY” trong cài đặt thiết bị.
Chọn “OK” và tiến hành cài đặt.
HƯỚNG DẪN CÀI ĐẶT TRÊN iOS:
Nhấn vào “Tải bản cài đặt” dành cho iOS để tải trực tiếp.
Chọn “Mở”, sau đó chọn “Cài đặt”.
Truy cập vào “Cài đặt” trên iPhone, chọn “Cài đặt chung” – “Quản lý VPN & Thiết bị”.
Chọn “Ứng dụng doanh nghiệp” hiển thị và sau đó chọn “Tin cậy…”
B52 là một trò chơi đổi thưởng đáng chơi và có uy tín. Nếu bạn quan tâm đến trò chơi này, hãy tải và cài đặt ngay để bắt đầu trải nghiệm. Chúc bạn chơi game vui vẻ và may mắn!
Thanks for sharing your thoughts on sex korean. Regards
I am regular visitor, һow ɑre yоu evеrybody? This aticle posted at this website іѕ ɑctually pleasant.
ᒪooқ intⲟ myy site – 슬롯사이트
Woah! I’m really loving the template/theme of
this blog. It’s simple, yet effective. A lot of times it’s very hard to get that “perfect balance” between usability
and visual appeal. I must say that you’ve done a amazing job with this.
Additionally, the blog loads very quick for me on Chrome.
Superb Blog!
http://appendix.isordil-my-world.pw
After you create an account, you probably can immediately
begin video chatting with strangers.
Invisalign em Porto Alegre
A Clínica Dr. Günther Heller é uma referência em tratamentos de Invisalign, ClearCorrect e implantes dentais. Sob a liderança do Dr. Heller, a clínica oferece atendimento especializado e personalizado, utilizando tecnologia avançada para criar soluções personalizadas. Os tratamentos de Invisalign e ClearCorrect são realizados por especialistas experientes, proporcionando correção discreta de problemas de alinhamento dental. Além disso, a clínica é reconhecida pela excelência em implantes dentais, oferecendo soluções duradouras e esteticamente agradáveis. Com resultados excepcionais, o Dr. Günther Heller e sua equipe garantem a satisfação dos pacientes em busca de um sorriso saudável e bonito.
Hello There. I discovered your blog using msn. This is a very well written article.
I’ll make sure to bookmark it and come back to read more of your useful information. Thank you for the post.
I will definitely comeback.
http://accordingly.isordil-my-world.pw
lisinopril pill 5 mg
Medicines information leaflet. Cautions.
escitalopram
Actual news about medicine. Read information now.
Excellent article. I will be going through many of
these issues as well..
Ahaa, its gooɗ dialogue aboᥙt this paragraph аt
this pⅼace at thіs website, I have read aⅼl
that, so now me also commenting at his pⅼace.
Loօk at my web blog; 에볼루션카지노
промокод Вулкан Жара
Drugs information. Drug Class.
rx effexor
Best news about medicament. Get information here.
Мосбет
Quality articles or reviews is the important to
invite the users to visit the site, that’s what this website is providing.
Medicines information for patients. Short-Term Effects.
cialis soft
Best about medication. Get information now.
스포츠중계
This article is actually a nice one it helps new internet visitors,
who are wishing in favor of blogging.
Medication information leaflet. Generic Name.
lyrica online
Everything information about meds. Read here.
It’s a pity you don’t have a donate button! I’d definitely donate to this brilliant blog!
I suppose for now i’ll settle for bookmarking and adding your RSS feed
to my Google account. I look forward to new updates and will share this site
with my Facebook group. Talk soon!
best models onlyfans
Medication information for patients. Generic Name.
lyrica
Best information about drug. Read now.
I’m not that much of a internet reader to be honest but
your sites really nice, keep it up! I’ll go ahead and bookmark your website to come back
in the future. Many thanks
Drugs information. Generic Name.
neurontin cheap
Best news about drugs. Get here.
https://vk.com/implantatsiya_zubov_v_minske
Pills information sheet. Long-Term Effects.
clomid
Everything information about medication. Get information now.
Актуальная ссылка на Мега
Знатоки и новички Даркнета не по
наслышке знают о популярном и раскрученном маркетплейсе MEGA
DARKNET MARKET. Данный сайт занимается распространением запрещенной продукции и находится в доменной
зоне ONION, поэтому войти в него можно только с использованием TOR
браузера. Самые актуальные на данный момент ссылки находятся в
MEGA SB.
Часто пользователи недоумевают, почему с привычных браузеров, таких, как Opera, Edge,
Chrome, не получается открыть сайт,
так как происходит ошибка. Лучше всего узнавать всю интересную
и новую информацию о ссылках, сайтах, магазинах в Годнотабе.
Этот ресурс также открывайте через ТОР.
Ссылка MEGA STORE
В Даркнете много аферистов и мошенников, поэтому легко попасться
на их удочку и остаться без денег, а иногда и аккаунта.
Чтобы этого не произошло, нужно
скачать и установить VPN, а потом и
Тор браузер. Там имеются проверенные ссылки MEGA SB.
Специалисты, работающие в нашем штате, рекомендуют такие типы VPN:
• HIDE.ME,
• Tunnel Bear,
• Planet VPN,
• ExpressVPN,
• ProtonVPN.
Часто невозможность попасть на сайт связана с плохим интернет-соединением.
В браузере Тор ищите ссылку mega555zf7yot2viukedzcmuuyooegofmnuexp7czxa3y5tamackqbad.onion.
Часто может наблюдаться чересчур медленное соединение, это связано с тем, что сайт
без конца пытаются атаковать мошенники.
MEGA onion ссылка
По мнению Мориарти, который является ее создателем, причины тому следующие:
• В течении семи лет маркетплейс успешно торгует на рынке, не ослабляя своих позиций;
• За это время было проведено более 2500000
сделок;
• В арсенале у команды и пользователей 60 свободных
и актуальных зеркал, то есть зайти на сайт можно практически всегда;
• Лучшие условия для торговцев, все бесплатно;
• Деньги можно вывести в один
момент;
• Магазины расположены не только в России, но и в странах бывшего
СНГ;
• Отличная репутация;
• Соблюдение анонимности;
• Регистрация всего за пару кликов;
• Соблюдение безопасности при помощи 2FA и
PGP ключа.
Согласно статистике, на MEGA расположены 2500 магазинов и 25000 товаров.
Создание аккаунта максимально простая операция.
Нужно пройти проверочную капчу, ввести логин и пароль.
Возможность использования Монеро отличает Мега от других
подобных ей площадок. Это очень выгодный вариант,
но его еще не многие опробовали, предпочитая все же проверенный
биткоин.
Excellent post. I was checking constantly this blog and I am inspired!
Very useful information particularly the closing part 🙂
I handle such information a lot. I was seeking this certain information for a long time.
Thank you and best of luck.
Howdy! This is kind of off topic but I need some guidance from
an established blog. Is it very difficult to set up your own blog?
I’m not very techincal but I can figure things out pretty fast.
I’m thinking about setting up my own but I’m not sure where to
begin. Do you have any tips or suggestions? Thanks
Drug information sheet. Effects of Drug Abuse.
retrovir medication
All information about medicament. Get information now.
Medicine prescribing information. Generic Name.
zovirax
Everything news about medicine. Read now.
https://vk.com/uslugi-220370538?screen=group&w=product-220370538_8888154
Drugs prescribing information. Effects of Drug Abuse.
propecia pill
All news about medicines. Read information now.
Implantes Dentais
A Clínica Dr. Günther Heller é uma referência em tratamentos de Invisalign, ClearCorrect e implantes dentais. Sob a liderança do Dr. Heller, a clínica oferece atendimento especializado e personalizado, utilizando tecnologia avançada para criar soluções personalizadas. Os tratamentos de Invisalign e ClearCorrect são realizados por especialistas experientes, proporcionando correção discreta de problemas de alinhamento dental. Além disso, a clínica é reconhecida pela excelência em implantes dentais, oferecendo soluções duradouras e esteticamente agradáveis. Com resultados excepcionais, o Dr. Günther Heller e sua equipe garantem a satisfação dos pacientes em busca de um sorriso saudável e bonito.
Drugs information for patients. Brand names.
minocycline
Best what you want to know about drug. Read now.
Medicine information leaflet. Short-Term Effects.
where to get xenical
Some what you want to know about drugs. Get here.
https://teletype.in/@zametki/nfjp0UAOnMx
Hello There. I f᧐սnd үour blog uѕing msn. Thіѕ is a really welⅼ writtsn article.
І wiⅼl be sᥙrе to bookmark it аnd cme bаck tⲟ read extra ߋf уоur սseful info.
Τhanks for tһe post. I’ll ⅾefinitely return.
Аlso visit mʏ bog post – 라이브카지노
Pills prescribing information. What side effects?
buy generic lisinopril
Best trends of medicines. Read here.
http://wikirace.ru/index.php?title=%D0%98%D0%BD%D1%82%D0%B5%D1%80%D0%BD%D0%B5%D1%82-%D0%BA%D0%B0%D0%B7%D0%B8%D0%BD%D0%BE%20Cat%20-%20%D1%88%D0%B8%D0%BA%D0%B0%D1%80%D0%BD%D1%8B%D0%B5%20%D0%B1%D0%BE%D0%BD%D1%83%D1%81%D1%8B%20%D0%B4%D0%BB%D1%8F%20%D0%BD%D0%BE%D0%B2%D1%8B%D1%85%20%D0%B8%20%D0%BF%D0%BE%D1%81%D1%82%D0%BE%D1%8F%D0%BD%D0%BD%D1%8B%D1%85%20%D0%BA%D0%BB%D0%B8%D0%B5%D0%BD%D1%82%D0%BE%D0%B2
We are a group of volunteers and opening a new scheme in our community.
Your website offered us with valuable information to work on.
You have done an impressive job and our entire community will be grateful to you.
Drug information sheet. Drug Class.
clomid cheap
All trends of medication. Read information now.
A Super Heinz is a decision of 7 horses that generate – 120 separate bets – these are 21 x doubles, 35 x trebles, 35
x fourfold, 21 x fivefold, 7 x six-folds, 1 x sevenfold accumulator.
Feel free to visit mmy web site more info
This Caesars On-line Casino new-user bonys operates by way
of the inital deposit, which we cover in the sibsequent step.
my site … 카지노
Meds information for patients. Short-Term Effects.
rx fluoxetine
Actual what you want to know about meds. Get information now.
https://miloqiyo65543.full-design.com/%D0%B7%D0%B5%D1%80%D0%BA%D0%B0%D0%BB%D0%BE-cat-casino-61790584
Pills information sheet. Cautions.
diltiazem without dr prescription
Actual what you want to know about pills. Get now.
I for all time emailed this web site post page to
all my contacts, as if like to read it then my links will too.
Hi friends, how is everything, and what you wish for to say concerning this paragraph,
in my view its in fact awesome in support of me.
Meds information sheet. What side effects can this medication cause?
avodart no prescription
Some about medication. Get here.
effient
Drugs information. What side effects can this medication cause?
effexor
Everything trends of medicament. Get here.
best models onlyfans
Pills information. Short-Term Effects.
lyrica price
Everything about medication. Get information now.
Drug information for patients. Short-Term Effects.
can i buy pregabalin
All information about drug. Get information here.
Medication information leaflet. Cautions.
priligy
Best trends of meds. Read now.
Hello exceptional blog! Does running a blog like
this require a great deal of work? I’ve absolutely no knowledge of coding but I was hoping to start my own blog
soon. Anyway, should you have any recommendations or tips
for new blog owners please share. I understand this is
off topic however I just wanted to ask. Appreciate it!
Medication prescribing information. Generic Name.
zovirax prices
All about drug. Get here.
Medicines information sheet. Long-Term Effects.
female viagra
Best about meds. Read here.
Pills information sheet. What side effects can this medication cause?
cialis
Actual trends of drugs. Get now.
Medicines information sheet. Generic Name.
cialis super active pills
All what you want to know about drugs. Get information here.
prograf 1
Wow, marvelous blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of your website
is fantastic, let alone the content!
Medication information for patients. Short-Term Effects.
zithromax pill
Best about drug. Read now.
Drugs information leaflet. What side effects?
flagyl without prescription
Best news about drug. Read information now.
Meds information leaflet. Generic Name.
buy generic flagyl
Actual information about medicines. Get here.
Medicine information sheet. Effects of Drug Abuse.
cytotec
Some what you want to know about pills. Read here.
Drug prescribing information. What side effects can this medication cause?
trazodone cost
Some trends of drug. Get now.
Meds information leaflet. Brand names.
trazodone
Actual about pills. Get information here.
protonix pharmacokinetics
Medication information. Brand names.
colchicine
Some what you want to know about meds. Read information here.
A new lot of individuals get off and find pleasure in naked bodies than with clothing or lingerie. Another aspect is normally vulnerability-a naked girl feels embarrassment and embarrassment in a foreplay and that is why it will be searched for. When somebody is naked, they sense uncovered and susceptible, nude sex comes across as being more romantic than clothed one. Vulnerability is a main change on specifically for a lot of men because they sense the sense of dominance during intercourse. a complete lot of nude porn focus on penetration. Nude porn will be pretty normal and the genre can end up being observed by you attached to a entire collection of some other classes, therefore you will not find it tough to locate your narrative of attention when eating this porn. Some of these are usually bondage adult, Asian porn, and lesbian porno. Since sex is certainly supposed to end up being a sacred ritual, viewing a naked girl get fucked will be a good fap material for a bunch of males. Viewing a person naked will be like knowing their secrets and viewing them defenseless for some, this is the good reason why nude porn is a popular genre among all viewers.
Pills information for patients. Cautions.
can i buy lasix
Some trends of medicine. Read here.
Meds information sheet. Cautions.
fluoxetine prices
Some trends of medication. Read here.
Medicament information leaflet. Brand names.
generic neurontin
Best trends of meds. Get information now.
Medicines prescribing information. What side effects?
cheap paxil
Best news about medicines. Get information here.
Meds information for patients. Brand names.
avodart generics
All about medicament. Get now.
Medicament prescribing information. Generic Name.
colchicine
Best information about meds. Read information now.
Medicine prescribing information. What side effects?
priligy generics
All news about drugs. Get now.
In the realm of online gaming, Jili Money is making waves as a pioneering platform that revolutionizes the way players experience virtual entertainment. With its cutting-edge technology, unparalleled game selection, and a commitment to rewarding its users, Jili Money has swiftly become the go-to destination for gamers seeking a thrilling and lucrative experience. In this article, we delve into the unique aspects that set Jili Money apart, propelling it to the forefront of the online gaming industry.
A Gateway to Limitless Excitement:
Jili Money’s claim to fame lies in its exceptional lineup of top games that cater to a diverse range of player preferences. From the moment users sign up for a free account, they are transported into a world brimming with thrilling possibilities. Jili Money’s game selection boasts a fusion of classic favorites and innovative creations, ensuring there is never a dull moment for players seeking an adrenaline rush. With captivating visuals, immersive sound effects, and engaging gameplay mechanics, Jili Money truly sets the stage for an unforgettable gaming experience.
Enter the Realm of Jili Money:
One of Jili Money’s most enticing features is its proprietary app, designed to seamlessly integrate with players’ mobile devices. The Jili App grants users unparalleled accessibility, empowering them to embark on exciting gaming adventures anytime, anywhere. Whether waiting for a bus or relaxing at home, players can now carry their favorite Jili Money games in the palm of their hand, breaking free from the confines of traditional gaming setups. This revolutionary approach truly epitomizes the essence of mobile gaming convenience.
Unleash Your Winning Potential:
At Jili Money, generosity knows no bounds. The platform is renowned for its commitment to rewarding its players through a range of enticing incentives. Upon signing up, users are welcomed with open arms and bestowed with a remarkable 100% welcome bonus, providing a substantial boost to their gaming endeavors. Jili Money also offers free credit opportunities, allowing players to explore a myriad of games without risking their own funds. These free credits serve as a gateway to unlock new strategies, master gameplay techniques, and ultimately discover the path to success.
Dive into a World of Bonuses:
Jili Money takes the excitement a step further by offering free spin tickets to its players. These tickets grant access to exclusive bonus rounds, where players can unlock hidden treasures and uncover extraordinary rewards. Each spin holds the potential to turn the tides of fortune, adding an extra layer of anticipation to the gaming experience. Jili Money ensures that every player feels the thrill of possibility with every spin, creating an atmosphere of excitement that sets it apart from the competition.
Celebrate Victories, Reap Rewards:
Jili Money goes above and beyond to foster a sense of community and appreciation among its users. The platform hosts regular events like “Happy Payday,” where players are showered with additional bonuses and prizes. These celebrations not only reward players for their achievements but also create a sense of camaraderie, allowing them to connect and share their successes with fellow gamers. Additionally, Jili Money offers weekly commissions, enabling players to turn their passion for gaming into a lucrative venture. This unique opportunity sets Jili Money apart, providing a pathway for gamers to unlock their full earning potential.
Conclusion:
Jili Money stands as a beacon of innovation and excitement in the realm of online gaming. With its unparalleled game selection, mobile app convenience, and an array of rewarding features, Jili Money has redefined what it means to be an online gaming platform. By offering free credits, free spin tickets, and hosting special events, Jili Money ensures that every player feels valued and empowered to embark on a gaming journey like no other. Brace yourself for an exhilarating adventure, as Jili Money
Medicament information for patients. Short-Term Effects.
cialis super active
Everything what you want to know about drugs. Read here.
Drug information. Generic Name.
neurontin
Everything information about drugs. Get here.
Step into the captivating realm of live casino gaming, where Evolution Gaming reigns supreme as the trailblazer in delivering unparalleled thrills and unforgettable experiences. In this article, we will take you on a thrilling journey through the virtual doors of Evolution Gaming’s live casino extravaganza, where Baccarat, Crazy Time, Roulette, Mega Ball, and Instant Roulette await to mesmerize and reward players. Brace yourself for an adventure that transcends the ordinary, as we delve into the heart-pounding excitement and unmatched features of these phenomenal games.
Baccarat: The Epitome of Sophistication and Fortune:
Prepare to be transported to the refined world of Baccarat, a game revered for its elegance and enticing possibilities. Evolution Gaming’s Live Baccarat sets the stage for an immersive experience, where sleek visuals, expert dealers, and seamless gameplay converge. Immerse yourself in the drama of the squeeze, revel in the pulsating anticipation of each card reveal, and seize the opportunity to claim victory with Evolution Gaming’s 100% Welcome Bonus. Discover why Baccarat has captured the hearts of players worldwide with its best-in-class payouts and alluring odds.
Crazy Time: Unleash the Wild and Whimsical:
Enter a realm where reality merges with unrestrained imagination in the form of Crazy Time. Evolution Gaming’s groundbreaking creation combines the electric atmosphere of a game show with the heart-pounding intensity of a casino. Embark on an exhilarating odyssey guided by an animated host, spinning the colossal Crazy Time wheel in search of unprecedented rewards. Brace yourself for a whirlwind of bonus rounds, captivating multipliers, and a frenzy of excitement that keeps you on the edge of your seat. Let your inhibitions run wild as you succumb to the chaos of Crazy Time and embrace the chance to win colossal prizes.
Roulette: A Timeless Classic Reinvented:
Evolution Gaming breathes new life into the age-old classic, Roulette, infusing it with cutting-edge technology and flawless execution. Experience the thrill of the spinning wheel, the elegant sound of the ball as it finds its destined pocket, and the camaraderie of fellow players through the interactive chat feature. Immerse yourself in a variety of Roulette variations, from European to American to French, each offering its unique twists and betting options. Witness the marriage of classic elegance and modern innovation as Evolution Gaming’s Live Roulette transports you to the pinnacle of casino excitement.
Mega Ball: A Revolution in Gaming:
Prepare to be astounded by the fusion of lottery-style excitement and the communal spirit of bingo in Mega Ball. Evolution Gaming’s audacious creation combines the thrill of watching numbered balls being drawn with the exhilaration of massive multipliers. Engage in a battle of wits and luck as you aim to match as many numbers as possible on your card, hoping to strike it rich. With its innovative gameplay mechanics and the potential for astronomical wins, Mega Ball is a game that shatters boundaries and promises a gaming experience like no other.
Instant Roulette: Speed, Action, and Unrelenting Fun:
For those who crave instant gratification and non-stop action, Evolution Gaming’s Instant Roulette takes the fast-paced gameplay to unprecedented levels. Buckle up as multiple roulette wheels spin simultaneously, offering an adrenaline-fueled rush that keeps your heart racing. Take control of your destiny as you seize the opportunity to place bets on any of the available wheels at any given moment. The high-octane nature of Instant Roulette ensures an electrifying gaming session where anticipation and excitement intertwine seamlessly.
Conclusion:
Evolution Gaming’s live casino extravaganza transcends the realm of traditional gaming, captivating players with its unrivaled portfolio of
Pills information. Brand names.
proscar without a prescription
Everything news about drugs. Get now.
Medicament information sheet. Generic Name.
cost lisinopril
All news about meds. Read here.
When it comes to online casino entertainment, GcashBonus has carved out a special place for itself by offering an unparalleled gaming experience that transcends expectations. With its commitment to excellence, innovative features, and a wide range of thrilling games, GcashBonus has become a go-to destination for both casual players and seasoned gamblers. In this article, we will delve into the extraordinary qualities that set GcashBonus apart, including its user-friendly interface, diverse game portfolio, and dedication to providing a secure and enjoyable gambling environment.
User-Friendly Interface for Effortless Navigation:
GcashBonus prides itself on providing a user-friendly interface that ensures seamless navigation and easy access to all the exciting features it has to offer. Whether you’re a novice or an experienced player, you’ll find the platform’s layout and design to be intuitive and visually appealing. GcashBonus has invested in creating an interface that puts the player’s needs first, allowing for a smooth and enjoyable gaming experience from the moment you log in.
A Diverse Game Portfolio to Suit Every Taste:
GcashBonus understands that variety is key to keeping players engaged and entertained. That’s why the platform offers a diverse portfolio of games that cater to every taste and preference. From thrilling slot machines with captivating themes to classic table games that evoke a sense of nostalgia, GcashBonus has something for everyone. Additionally, the platform regularly updates its game library to ensure that players always have access to the latest and most innovative titles in the industry.
Unleashing the Power of Bonuses and Promotions:
GcashBonus takes player satisfaction to heart and goes the extra mile to ensure that its users are rewarded generously. Upon signing up, players are greeted with enticing bonuses and promotions that add extra value to their gaming experience. Whether it’s a welcome bonus, free spins, or cashback offers, GcashBonus ensures that players feel appreciated and motivated to explore all the thrilling games on offer. The platform believes that every player should have the chance to maximize their winnings and enjoy a truly rewarding gambling adventure.
A Secure and Trustworthy Gambling Environment:
Security is of utmost importance in the online gambling world, and GcashBonus leaves no stone unturned in this regard. The platform prioritizes player safety by implementing robust security measures and encryption protocols to safeguard personal and financial information. Additionally, GcashBonus operates under strict licensing and regulatory frameworks, ensuring fair play and a transparent gambling environment. Players can rest assured that their privacy and funds are protected when they choose to play at GcashBonus.
Embracing Responsible Gambling:
GcashBonus recognizes the importance of responsible gambling and encourages players to enjoy their gaming experience in a responsible manner. The platform provides tools and resources to help players set limits on their deposits, wagering, and playing time. GcashBonus also offers access to support services for individuals who may require assistance with gambling-related concerns. By promoting responsible gambling practices, GcashBonus aims to create a safe and enjoyable environment for all players.
Conclusion:
GcashBonus has elevated the online casino entertainment experience to new heights with its user-friendly interface, diverse game portfolio, generous bonuses, and commitment to player security and responsible gambling. Whether you’re a fan of slots, table games, or live dealer experiences, GcashBonus offers a world of thrilling options to suit every preference. Discover the excitement and rewards that await you at GcashBonus and prepare for an unforgettable gambling journey that will exceed your expectations.
Disclaimer: GcashBonus is an independent online casino platform. Please ensure that online gambling is legal in your jurisdiction before participating. Gamble responsibly and set limits for your gaming activities.
Medicine prescribing information. Cautions.
abilify
Some news about medicament. Read information now.
azino
Meds information sheet. Generic Name.
avodart buy
Some about medicine. Get information here.
Всем рекомендую именно этот сайт знакомств!Сайт знакомств
Drugs information leaflet. Long-Term Effects.
lisinopril
Everything trends of medication. Read information now.
Medicines information for patients. Generic Name.
mobic order
Best news about medicines. Get information now.
“I suppose that relief may simply be the feeling that we’re bought this message that the world is a scary place,” says Sandstrom.
Pills information leaflet. Short-Term Effects.
cost valtrex
Actual trends of medicines. Get information here.
Medicament information sheet. Brand names.
rx sildenafil
Some information about drug. Get now.
Medication information for patients. What side effects?
lioresal price
All what you want to know about medicine. Read information here.
Medication information for patients. Brand names.
lioresal
Everything news about meds. Get information here.
Drug information sheet. Brand names.
clomid
Everything news about medicines. Get now.
Medicament information sheet. Cautions.
avodart
Some about medicines. Get now.
Drugs information. Generic Name.
fosamax medication
Everything what you want to know about drugs. Read now.
Meds information leaflet. Generic Name.
minocycline rx
Everything information about medicine. Get here.
Meds information. Brand names.
viagra
All what you want to know about medication. Get here.
Drug information. Generic Name.
promethazine
All trends of pills. Read here.
Drug information sheet. Short-Term Effects.
buy generic lyrica
All news about drug. Read information now.
Drug information for patients. Effects of Drug Abuse.
cheap viagra
Some what you want to know about pills. Read here.
Pills information. Long-Term Effects.
cialis super active
Best news about medicament. Read information now.
Pills information leaflet. Long-Term Effects.
lyrica
Some about drugs. Read information now.
Drug information sheet. What side effects?
retrovir prices
Some what you want to know about medication. Read information now.
Drug information leaflet. What side effects can this medication cause?
fluoxetine
Actual trends of drugs. Get information now.
Medication information sheet. What side effects?
gabapentin tablet
Some news about medicines. Read here.
Medicament prescribing information. Generic Name.
zoloft tablets
All about meds. Read now.
Drug information leaflet. Drug Class.
lisinopril
All news about medicament. Get information here.
Pills information for patients. What side effects?
cost lopressor
Everything information about pills. Get here.
Medicine information leaflet. Long-Term Effects.
valtrex
Actual information about meds. Get now.
iRich Bingo
Get ready to embark on a spectacular casino adventure with Jili, where luck and excitement intertwine to create an unforgettable gaming experience. Jili is renowned for its innovative and immersive casino games that cater to players of all levels. From the captivating Golden Empire to the adrenaline-pumping Super Ace and the enchanting Fortune Gem, Jili offers a diverse range of games that are sure to thrill and entertain. Join us as we delve into the world of Jili and discover the secrets to unleashing your luck in this exhilarating casino journey.
Golden Empire: Discover the Realm of Riches and Majesty
Step into a realm of opulence and majesty with Golden Empire, a game that transports you to a world filled with untold treasures. With its striking graphics and enchanting soundtrack, Golden Empire immerses you in a captivating gaming experience. Venture deep into the kingdom and uncover hidden riches as you encounter mystical symbols, bonus features, and free spins. Let the chieftain guide you towards the path of prosperity in this mesmerizing slot game.
Super Ace: Soar to New Heights of Casino Thrills
Prepare to reach new heights of excitement with Super Ace, a game that takes your casino adventure to the next level. With its sleek design and dynamic gameplay, Super Ace offers a thrilling experience that will keep you on the edge of your seat. Test your skills and luck with a wide range of casino games, including classics like blackjack, roulette, and poker, as well as an extensive selection of immersive slot games. With its generous bonuses and promotions, Super Ace ensures that every spin holds the potential for incredible wins.
Fortune Gem: Unlock Limitless Wealth in a World of Precious Stones
Enter a world of shimmering gemstones and boundless wealth with Fortune Gem, a game that combines elegance and excitement in perfect harmony. The game’s visually stunning design and captivating animations create an immersive experience that will leave you spellbound. Spin the reels and watch as the gemstones align, triggering bonus rounds, free spins, and multipliers. Fortune Gem offers a wealth of opportunities to uncover unimaginable riches and elevate your casino adventure to new heights.
iRich Bingo: Where Luck and Social Connection Collide
Experience the thrill of bingo like never before with iRich Bingo, a game that combines luck, strategy, and social interaction. Connect with players from around the world in a vibrant and engaging bingo community. Engage in friendly banter, participate in exciting chat games, and celebrate each win together. iRich Bingo offers a variety of bingo rooms, each with its unique theme and gameplay style. From traditional 75-ball and 90-ball games to speed bingo and progressive jackpots, iRich Bingo guarantees endless fun and the chance to strike it big.
Conclusion:
Jili’s spectacular casino adventure invites you to unleash your luck and embark on an extraordinary gaming journey. Whether you prefer the opulence of Golden Empire, the adrenaline rush of Super Ace, the enchantment of Fortune Gem, or the camaraderie of iRich Bingo, Jili has a game to suit every player’s taste. With their immersive gameplay, stunning visuals, and generous rewards, Jili’s casino games promise an unforgettable experience filled with excitement, thrills, and the potential for life-changing wins. Join Jili’s world of entertainment today and let your luck soar to new heights!
Medicament information leaflet. What side effects?
where can i buy lyrica
All what you want to know about drugs. Get here.
They have a wide variety of slots, table games, andd live dealer games.
My blog post :: website
Pills information leaflet. Cautions.
baclofen
Best trends of medication. Read information now.
Medicine information leaflet. What side effects can this medication cause?
cleocin buy
All what you want to know about pills. Get here.
Also, the spins hold no wagering needs, and you have 30 dahs to use the promotion.
Here is my webste :: webpage
Medicine information sheet. Long-Term Effects.
order amoxil
Some news about drug. Read information now.
up-x официальный сайт
Medicine information for patients. Cautions.
colchicine
Everything information about drug. Get now.
Medicines prescribing information. Long-Term Effects.
zovirax without a prescription
All news about pills. Get information now.
Medicines information sheet. Cautions.
fluoxetine without a prescription
Best information about medicine. Read information here.
Meds information sheet. Short-Term Effects.
cialis soft generics
All what you want to know about pills. Get now.
can prednisone cause diarrhea
actos off-label use
Medication information sheet. What side effects can this medication cause?
cleocin
Some trends of medicine. Get information now.
Medication information leaflet. Drug Class.
mobic tablets
Best what you want to know about medicine. Read now.
Medication prescribing information. Brand names.
female viagra
Best what you want to know about medicament. Get information here.
amoxilin
dangers of ashwagandha
Meds information. Brand names.
lopressor without prescription
Everything what you want to know about meds. Read information here.
cefixime uses
But, whereas speaking to strangers, you want to be careful
as properly.
Drugs information for patients. Cautions.
minocycline
Everything about medicament. Get information now.
dose zyrtec
cipro
Meds information for patients. Generic Name.
abilify
Actual trends of meds. Read here.
Pills information sheet. Long-Term Effects.
rx baclofen
Everything information about medicine. Read information here.
MoneyMutual has numerous benefits more than its competitors that we
haven’t seen elsewhere.
My web blog 소액대출
mature mom anal
Medicine prescribing information. What side effects can this medication cause?
can you get finpecia
Best about medicines. Read here.
neighbor blowjob
Medicament information sheet. Effects of Drug Abuse.
nexium
Best information about drugs. Get now.
So, you might like the idea of being a Forex trader, but
it is not right for everyone. No trader can expect to be right all, or even most of the time.
Crazytime
Prepare to embark on a groundbreaking live casino adventure like no other, as we delve into the immersive world of Evolution Gaming. Renowned for their innovation, Evolution Gaming sets the stage for an extraordinary gaming experience, offering a diverse range of games that captivate and enthrall players. In this article, we will explore the unique features and exhilarating gameplay of Evolution Gaming’s Live Baccarat, Crazy Time, Roulette, Mega Ball, and Instant Roulette, ensuring an unforgettable journey into the realm of live casino entertainment.
Live Baccarat: Unveiling Elegance and High Stakes
Step into the sophisticated world of Live Baccarat, where elegance and high stakes converge. Evolution Gaming’s Live Baccarat delivers an authentic casino experience, complete with professional dealers, stunning visuals, and seamless gameplay. Immerse yourself in the tension of the squeeze, as anticipation builds with each card reveal. And with the enticing 100% Welcome Bonus, players can elevate their chances of claiming substantial winnings. Discover why Live Baccarat stands as the epitome of refined gaming, offering the best payouts and odds for enthusiasts worldwide.
Crazy Time: Embracing the Unpredictable
Prepare for an unparalleled rollercoaster ride with Crazy Time, a game that pushes the boundaries of live casino entertainment. Evolution Gaming’s Crazy Time transports players to a whimsical realm, combining elements of a game show with the thrills of casino gaming. Led by charismatic hosts, players can spin the colossal Crazy Time wheel in pursuit of magnificent prizes. With an array of captivating bonus rounds and electrifying multipliers, Crazy Time ensures a whirlwind of excitement and rewards that defy expectations. Brace yourself for a gaming experience that transcends the ordinary.
Roulette: Classic Glamour Meets Modern Innovation
Evolution Gaming’s Live Roulette breathes new life into the timeless classic, infusing it with cutting-edge technology and immersive gameplay. Immerse yourself in the atmosphere of a luxurious casino, as the iconic roulette wheel spins and the ball dances with anticipation. With multiple variations, including European, American, and French Roulette, players can explore a world of diverse betting options and strategies. Engage with fellow players through the interactive chat feature, creating a sense of camaraderie and excitement. Experience the perfect fusion of classic glamour and modern innovation with Evolution Gaming’s Live Roulette.
Mega Ball: Revolutionizing the Gaming Landscape
Enter a revolutionary gaming experience with Mega Ball, a game that seamlessly combines lottery-style thrills with the community spirit of bingo. Evolution Gaming’s Mega Ball presents an exhilarating journey, where players purchase cards adorned with random numbers and hope to match as many as possible. Witness the electrifying draw as numbered balls are revealed, with the potential for massive multipliers that can lead to life-changing wins. With its innovative gameplay mechanics and the opportunity for astronomical prizes, Mega Ball redefines the boundaries of live casino entertainment.
Instant Roulette: Unleashing the Need for Speed
For thrill-seekers craving instant action, Evolution Gaming’s Instant Roulette delivers a high-octane gaming experience that never fails to excite. Multiple roulette wheels spin simultaneously, providing non-stop action and the freedom to place bets on any available wheel at any given moment. The rapid-fire pace and dynamic gameplay create an adrenaline-fueled adventure that keeps players on the edge of their seats. Instant Roulette satisfies the need for speed, offering an exhilarating experience that sets pulses racing.
Conclusion:
Evolution Gaming stands at the forefront of live casino innovation, elevating the gaming experience to unprecedented heights. With Live Baccarat, Crazy Time, Roulette, Mega Ball, and Instant Roulette, players are treated to an extraordinary journey filled with elegance, excitement, and groundbreaking gameplay. Whether seeking
legit casino gcash free welcome bonus
In the vast world of online casinos, GcashBonus has emerged as a true trailblazer, redefining the way players engage with their favorite casino games. With its unwavering commitment to innovation, exceptional gaming offerings, and a customer-centric approach, GcashBonus has quickly become a trusted name in the industry. In this article, we will explore the unique qualities that set GcashBonus apart, highlighting its cutting-edge features, diverse game selection, and dedication to providing a secure and rewarding online casino experience.
Embracing Cutting-Edge Features for Enhanced Gameplay:
GcashBonus is at the forefront of technological advancements, constantly striving to provide players with an enhanced gaming experience. The platform leverages state-of-the-art features such as immersive graphics, seamless animations, and intuitive user interfaces to create an engaging environment. GcashBonus incorporates innovative elements like live chat support, interactive leaderboards, and personalized recommendations to further elevate the gaming journey. By embracing cutting-edge features, GcashBonus ensures that players are captivated from the moment they step into the virtual casino.
Diverse Game Selection for Every Preference:
One of the standout features of GcashBonus is its vast and diverse game selection, catering to the unique preferences of players. Whether you’re a fan of classic table games, thrilling slots, or immersive live dealer experiences, GcashBonus has something for everyone. The platform partners with renowned software providers to offer a wide range of high-quality games with captivating themes and exciting features. With GcashBonus, players can explore new adventures, discover their favorite games, and indulge in endless entertainment.
Rewarding Loyalty with Generous Bonuses and Promotions:
GcashBonus understands the importance of appreciating and rewarding its loyal players. From the moment you join, you’ll be greeted with a range of enticing bonuses and promotions. Whether it’s a generous welcome bonus, free spins, or exclusive tournaments, GcashBonus ensures that players feel valued and motivated to continue their gaming journey. The platform also offers a rewarding loyalty program, where players can earn points and unlock exclusive perks. GcashBonus goes above and beyond to reward its dedicated players and make their experience truly exceptional.
Ensuring a Secure and Fair Gaming Environment:
GcashBonus takes the security and fairness of its platform seriously. The platform operates under strict licensing and regulatory guidelines, ensuring that players can enjoy a safe and transparent gaming environment. GcashBonus utilizes advanced encryption technology to protect personal and financial information, giving players peace of mind while they play. Additionally, the platform promotes responsible gambling practices, providing tools and resources to assist players in maintaining control over their gaming activities. With GcashBonus, players can focus on the thrill of the games, knowing that they are in a secure and fair gaming environment.
Accessible and Convenient Gcash Transactions:
GcashBonus understands the importance of seamless and convenient transactions for players. The platform integrates Gcash, a trusted mobile wallet service, as a payment option. This allows players to make swift and secure deposits and withdrawals, eliminating the need for traditional banking methods. Gcash provides a user-friendly and efficient payment solution, making the gaming experience at GcashBonus even more convenient and hassle-free.
Conclusion:
GcashBonus stands out as a leader in the online casino industry, delivering innovation, exceptional gaming offerings, and a commitment to customer satisfaction. With its cutting-edge features, diverse game selection, generous bonuses, and convenient Gcash transactions, GcashBonus offers an unparalleled online casino experience. Embark on an exciting gaming journey at GcashBonus and discover the true essence of innovation and excellence in the world of online gambling.
Medication information. Brand names.
cordarone
Everything information about meds. Read information now.
Medicine information for patients. What side effects can this medication cause?
lioresal buy
Best news about medication. Get information here.
buy cordarone online uk
In the vast and ever-expanding realm of online gaming, Jili Money has emerged as a beacon of excitement, offering gamers an unparalleled platform where thrilling adventures and endless possibilities await. With its commitment to innovation, a diverse array of top-quality games, and a user-centric approach, Jili Money has solidified its position as a trailblazer in the gaming industry. In this article, we delve into the exceptional qualities that make Jili Money a truly unique and captivating platform, igniting the flames of adventure for gamers worldwide.
Unleashing Unprecedented Adventures:
Jili Money serves as a gateway to uncharted territories, inviting players to embark on unforgettable adventures that transcend the boundaries of reality. From epic quests in immersive fantasy realms to heart-pounding challenges in futuristic landscapes, Jili Money’s vast selection of games caters to every gamer’s taste and preference. Prepare to be whisked away into captivating storylines, awe-inspiring graphics, and engaging gameplay, as Jili Money offers an escape to a world where adventure knows no limits.
A Playground of Innovation:
At the core of Jili Money lies an unwavering commitment to innovation, continuously pushing the boundaries of what’s possible in the gaming sphere. The platform harnesses cutting-edge technology to create a seamless and immersive experience for players. With features like augmented reality, virtual reality, and dynamic gameplay mechanics, Jili Money blurs the lines between the virtual and real worlds, transporting players into an entirely new dimension of gaming. Immerse yourself in the future of gaming as Jili Money sets the stage for a revolution in interactive entertainment.
A Vast Universe of Games:
Jili Money boasts an extensive universe of games, ensuring that every player finds their perfect match. From adrenaline-fueled action games to mind-bending puzzles and strategic simulations, Jili Money’s diverse library caters to gamers of all interests and skill levels. The platform collaborates with renowned game developers to curate a collection of top-tier titles, ensuring a constant stream of fresh and exciting content. With regular updates and new releases, Jili Money ensures that players always have something new to explore and conquer.
Rewards Beyond Imagination:
Jili Money believes in rewarding its players for their dedication and achievements. The platform offers a range of enticing rewards that enhance the gaming experience and keep players motivated. From in-game bonuses and exclusive items to real-world prizes and unique experiences, Jili Money goes above and beyond to make players feel valued and appreciated. Your journey with Jili Money is not only about the thrill of gaming but also about reaping the rewards of your efforts and accomplishments.
Fostering a Thriving Community:
Jili Money understands the importance of community and connection in the gaming world. The platform provides a space where players can connect, collaborate, and compete with fellow enthusiasts. Join guilds, participate in multiplayer battles, and engage in lively discussions to forge friendships and share experiences. Jili Money’s thriving community is a testament to the power of gaming as a social and interactive medium, offering a sense of belonging and camaraderie.
Conclusion:
Jili Money stands at the forefront of the gaming industry, igniting the flames of adventure for gamers around the globe. With its dedication to innovation, an extensive selection of games, rewarding experiences, and a vibrant community, Jili Money sets a new standard for online gaming. Prepare to embark on thrilling journeys, push the boundaries of what’s possible, and immerse yourself in a world where imagination knows no limits. Join the ranks of Jili Money and let the flames of adventure burn bright in your gaming endeavors.
In the fast-paced world of online gaming, Jilibet has emerged as a true pioneer, pushing boundaries and redefining the gaming landscape. With its innovative approach, captivating games, and a commitment to excellence, Jilibet offers an unmatched gaming experience that captivates players worldwide. Join us as we delve into the unique features and exciting offerings that make Jilibet a standout in the realm of online gaming.
A World of Endless Possibilities:
Jilibet opens the doors to a world of endless possibilities, where adventure and excitement await at every turn. From the moment you enter the platform, you’ll be greeted by a visually stunning interface that immerses you in a realm of virtual splendor. Jilibet’s intuitive design and seamless navigation ensure that every moment spent on the platform is focused on the exhilaration of the game.
Unleashing the Power of Bonuses and Rewards:
Prepare to be dazzled by Jilibet’s irresistible bonuses and rewards. The platform believes in pampering its players from the get-go, offering a generous welcome bonus to kickstart your gaming journey. But the rewards don’t stop there. Jilibet consistently surprises and delights its players with exciting promotions, cashbacks, and exclusive tournaments, enhancing the thrill of each gaming session and boosting your chances of hitting the jackpot.
Diverse and Captivating Game Selection:
Jilibet takes pride in its diverse collection of games, catering to every gaming preference and style. Whether you’re a fan of classic slots, table games, live dealer experiences, or unique specialty games, Jilibet has something to keep you entertained. Immerse yourself in the world of cutting-edge slot games, where stunning visuals, immersive soundscapes, and engaging storylines transport you to new dimensions. Experience the excitement of live dealer games, where you can interact with professional dealers in real-time, adding an authentic touch to your gaming experience.
A Haven of Safety and Security:
Jilibet places utmost importance on providing a safe and secure gaming environment. Rigorous security measures, including advanced encryption technology, safeguard your personal and financial information, ensuring peace of mind while you play. Jilibet adheres to strict regulations and fair gaming practices, ensuring that every player has an equal opportunity to win. The platform’s commitment to responsible gaming promotes a healthy gaming experience and offers tools for players to manage their gaming habits effectively.
The Jilibet Community and Customer Support:
Jilibet fosters a vibrant and supportive gaming community, where players from all walks of life come together to share their experiences and forge lasting connections. The platform also understands the value of exceptional customer support. Should you have any questions or encounter any issues, Jilibet’s dedicated customer support team is available around the clock to provide timely assistance and ensure that your gaming journey remains seamless and enjoyable.
Conclusion:
Jilibet has set a new standard in the world of online gaming, offering a truly unique and exhilarating experience for players. With its captivating games, irresistible bonuses, and unwavering commitment to security and customer satisfaction, Jilibet continues to redefine what it means to be an exceptional online gaming platform. So, immerse yourself in the world of Jilibet, where endless excitement and extraordinary wins await. Get ready to elevate your gaming experience to new heights with Jilibet by your side.
diltiazem for afib
Medicines information for patients. Short-Term Effects.
finpecia order
Actual about drug. Read here.
Medication information. Effects of Drug Abuse.
lyrica cost
Best what you want to know about medicines. Get information here.
doxycycline hyclate 100 mg
urex-m furosemide
Medicines information sheet. Long-Term Effects.
aurogra
Some what you want to know about medicament. Get now.
levaquin dosing
Drug information leaflet. Cautions.
baclofen tablet
Best information about medicine. Read information now.
Highly energetic post, I liked that a lot. Will there be a part 2?
Stop by my web-site :: http://support.asungh.com/bbs/board.php?bo_table=free&wr_id=234226
lisinopril para que sirve
Medicament prescribing information. What side effects?
trazodone
Some about medicine. Get information now.
Medicines information for patients. Short-Term Effects.
motrin online
Some what you want to know about medicines. Get information here.
Super Ace
Get ready for an exhilarating casino experience like no other as we dive into the top Jili casino slot games of 2023. With their innovative features, stunning visuals, and thrilling gameplay, these games are set to captivate and reward players seeking the ultimate gaming adventure. From the glitz and glamour of Golden Empire to the adrenaline-pumping action of Super Ace, Jili has curated a collection of top-notch slot games that are sure to keep you entertained and craving for more. Join us as we explore the exciting world of Jili and discover the games that are set to supercharge your winnings in 2023.
Golden Empire: Unleash the Power of Ancient Treasures
Embark on a journey through time with Golden Empire, a visually stunning slot game that transports players to the realms of ancient civilizations. This game features a captivating theme filled with majestic symbols, mythical creatures, and hidden treasures. With its multiple paylines and bonus features, including free spins and multipliers, Golden Empire offers ample opportunities to strike it rich. Let the power of the ancients guide you towards untold fortunes in this immersive slot game.
Super Ace: Reach New Heights of Casino Excitement
Prepare for a high-flying adventure with Super Ace, an adrenaline-charged slot game that takes you to the pinnacle of casino entertainment. Featuring a sleek and modern design, Super Ace offers a dynamic gaming experience that caters to players of all levels. With its diverse range of casino games, including classic favorites and exciting new variations, Super Ace ensures there’s never a dull moment. Unleash your inner ace and soar to new heights as you spin the reels and aim for remarkable wins.
Fortune Gem: Unearth Limitless Riches in a Gem-Infused Realm
Step into a realm of radiance and elegance with Fortune Gem, a slot game that dazzles with its gem-themed design and lucrative rewards. Prepare to be mesmerized by the shimmering gemstones that adorn the reels, as each spin brings you closer to uncovering vast treasures. With its cascading reels, expanding wilds, and bonus features, Fortune Gem offers a thrilling gameplay experience that keeps you on the edge of your seat. Unleash the power of the gemstones and unlock the secrets to unimaginable wealth in this captivating slot game.
iRich Bingo: Where Luck Meets Social Connection
Experience the excitement of bingo like never before with iRich Bingo, a game that combines luck, social interaction, and generous rewards. Engage in lively conversations with fellow players as you mark off your numbers, share tips, and cheer each other on. iRich Bingo offers a range of bingo variations to suit every player’s preference, from classic 75-ball and 90-ball games to speed bingo and themed variations. With its frequent promotions, free gameplay options, and enticing prizes, iRich Bingo ensures that the fun never stops.
Conclusion:
The top Jili casino slot games of 2023 are set to redefine your gaming experience and supercharge your winnings. From the opulence of Golden Empire to the exhilarating action of Super Ace, these games offer immersive gameplay, stunning visuals, and exciting bonus features that will keep you entertained for hours on end. Whether you’re a fan of ancient civilizations, high-flying adventures, gem-filled realms, or the thrill of bingo, Jili has a game that will cater to your preferences. So, buckle up and get ready for an unforgettable gaming journey filled with big wins and endless excitement.
Medication information sheet. Effects of Drug Abuse.
paxil medication
All about pills. Read here.
Medicines information for patients. Effects of Drug Abuse.
prednisolone
Actual information about pills. Get information here.
Pills information. Long-Term Effects.
gabapentin no prescription
Some what you want to know about medicine. Get information here.
Drug prescribing information. Long-Term Effects.
avodart
Actual news about medication. Read now.
Medication prescribing information. Short-Term Effects.
buy mobic
Best trends of drug. Read information here.
prasugrel 10
can i buy prednisone
Meds information. Brand names.
zithromax otc
Best information about medication. Read now.
cipo prograf
Medicines prescribing information. What side effects?
singulair
Best information about pills. Get information now.
Howdy! This article could not be written much better!
Looking through this post reminds me of my previous roommate!
He continually kept preaching about this. I will send this article to him.
Pretty sure he’s going to have a good read. Many thanks for sharing!
protonix uses
Everything is very open with a very clear clarification of the issues.
It was really informative. Your site is useful. Thank you for sharing!
stromectol stromectolice
Medicines information for patients. Effects of Drug Abuse.
where buy minocycline
Best what you want to know about medicines. Get now.
Tetracycline market
All content material is moderated by state-of-the-art
AI technologies and people.
Howdy! This is kind of off topic but I need some help from an established
blog. Is it very hard to set up your own blog? I’m not very techincal
but I can figure things out pretty fast. I’m thinking about creating
my own but I’m not sure where to begin. Do you have any ideas
or suggestions? Thank you
Meds information. What side effects?
zenegra buy
Actual information about medication. Read here.
Drugs information for patients. Generic Name.
strattera price
Everything information about medicines. Get now.
instantroulette
Prepare to be captivated by a new era of live casino gaming as Evolution Gaming takes center stage, revolutionizing the way we play and experience online casinos. With its unparalleled commitment to innovation and cutting-edge technology, Evolution Gaming has become the industry leader, offering an exceptional range of games that immerse players in an electrifying and authentic casino atmosphere. In this article, we will delve into the remarkable features and gameplay of Evolution Gaming’s Live Baccarat, Crazy Time, Roulette, Mega Ball, and Instant Roulette, showcasing how they are redefining the live casino experience.
Live Baccarat: Where Tradition Meets Immersion
Step into the world of Live Baccarat, where tradition meets immersive gameplay. Evolution Gaming’s Live Baccarat offers a seamless and realistic casino experience, complete with professional dealers, stunning visuals, and multiple camera angles that bring every detail to life. The game’s elegant simplicity and intuitive interface make it accessible to both seasoned players and newcomers. With the added advantage of a 100% Welcome Bonus, players can elevate their chances of winning big in this classic card game, making Live Baccarat an enticing choice for all.
Crazy Time: Unleashing the Extraordinary
Prepare to be blown away by the sheer excitement of Crazy Time, an unparalleled fusion of game show entertainment and casino gaming. Evolution Gaming’s Crazy Time transports players into a world where unpredictability reigns supreme. Led by charismatic hosts, players can spin the colossal Crazy Time wheel, unveiling thrilling bonus rounds and multiplying their winnings exponentially. The dynamic visuals, energetic atmosphere, and ever-changing gameplay make Crazy Time an extraordinary experience that pushes the boundaries of what live casino gaming can offer.
Roulette: Embracing the Thrill of the Wheel
Evolution Gaming’s Live Roulette brings the iconic casino game to life like never before. Immerse yourself in the elegance and suspense of the spinning wheel, as high-definition video streams and professional croupiers create an authentic and engaging environment. With various roulette variations to choose from, players can explore different strategies and betting options, all while interacting with fellow players through live chat features. Evolution Gaming’s Live Roulette is a testament to the company’s commitment to providing an immersive and thrilling gaming experience.
Mega Ball: A Winning Fusion of Bingo and Lottery
Experience the fusion of lottery and bingo in Evolution Gaming’s Mega Ball, a game that combines chance, excitement, and community. Players purchase cards adorned with numbers, hoping to match them with the balls drawn during the game. The anticipation builds as multipliers are revealed, offering the potential for massive winnings. With its innovative gameplay, interactive features, and the opportunity to socialize with other players, Mega Ball takes the live casino experience to a new level, creating an immersive and rewarding environment.
Instant Roulette: Unleashing the Need for Speed
For those seeking adrenaline-pumping action, Evolution Gaming’s Instant Roulette delivers fast-paced gameplay that keeps players on their toes. With multiple roulette wheels spinning simultaneously, players have the freedom to place bets at any moment, ensuring a continuous flow of excitement. The seamless interface and intuitive controls make Instant Roulette an immersive and thrilling gaming experience, catering to the need for speed and instant gratification.
Conclusion:
Evolution Gaming has emerged as a trailblazer, transforming the live casino landscape with its innovative approach to gaming. Through Live Baccarat, Crazy Time, Roulette, Mega Ball, and Instant Roulette, Evolution Gaming has redefined the live casino experience, offering players unprecedented immersion, excitement, and winning potential. As the industry continues to evolve, Evolution Gaming remains at the forefront, shaping the future of online gaming and providing players with unforgettable moments of entertainment and thrill.
In the vast world of online casinos, GcashBonus has emerged as a game-changer, reshaping the way players experience online gambling. With a focus on innovation, generous rewards, and a user-friendly platform, GcashBonus has quickly become a favorite among avid casino enthusiasts. In this article, we will delve into the unique qualities that make GcashBonus stand out from the crowd, including its innovative features, diverse game selection, and commitment to delivering a top-notch gaming experience.
Embracing Innovation for an Unforgettable Adventure:
GcashBonus is synonymous with innovation, continually pushing the boundaries of what’s possible in the online casino industry. The platform harnesses cutting-edge technology to create an immersive and engaging environment for players. From seamless navigation to stunning graphics and animations, GcashBonus ensures that every moment spent on the site is filled with excitement and anticipation. Innovation is at the heart of GcashBonus, providing players with an unforgettable adventure from the comfort of their own homes.
A Plethora of Games for Every Taste:
One of the standout features of GcashBonus is its vast and diverse game selection. Catering to every taste and preference, GcashBonus offers an extensive library of games ranging from classic slots to thrilling table games and immersive live dealer experiences. Partnering with renowned game providers, the platform ensures that players have access to the latest and most popular titles in the industry. With such a wide variety of options, GcashBonus guarantees that every player will find something to suit their style and keep them entertained for hours on end.
Rewarding Loyalty with Generous Bonuses:
At GcashBonus, loyalty doesn’t go unnoticed. The platform believes in rewarding its players for their continued support and engagement. From the moment you join, you’ll be greeted with generous bonuses and promotions that enhance your gaming experience. These rewards may come in the form of free spins, deposit matches, cashback offers, or exclusive tournaments. GcashBonus takes pride in going the extra mile to ensure that players feel valued and appreciated throughout their journey on the platform.
Seamless Transactions with Gcash:
GcashBonus has streamlined the payment process by integrating Gcash as a convenient and secure payment method. Gcash, a widely trusted mobile wallet service, allows players to deposit and withdraw funds effortlessly. By offering Gcash as a payment option, GcashBonus eliminates the need for traditional banking methods and provides a hassle-free experience. Players can enjoy their favorite games without worrying about complicated transactions, making GcashBonus a convenient and user-friendly platform.
Committed to Responsible Gaming:
GcashBonus is committed to promoting responsible gaming practices and ensuring the well-being of its players. The platform encourages responsible gambling by providing tools and resources that help players manage their gaming activities. GcashBonus promotes self-exclusion options, deposit limits, and access to support services for those in need. By prioritizing responsible gaming, GcashBonus creates a safe and enjoyable environment for all players.
Conclusion:
GcashBonus has revolutionized the online casino landscape with its innovative features, diverse game selection, generous rewards, and commitment to responsible gaming. Whether you’re a seasoned player or new to the world of online casinos, GcashBonus offers an unparalleled gaming experience that will exceed your expectations. Immerse yourself in a world of innovation, excitement, and rewards at GcashBonus and discover why it has become a leading destination for online gambling enthusiasts.
Disclaimer: GcashBonus is an independent online casino platform. It is essential to ensure that online gambling is legal in your jurisdiction before participating. Always gamble responsibly and set limits for your gaming activities.
Drugs information leaflet. Long-Term Effects.
baclofen without rx
Best trends of pills. Get here.
Pills information. Cautions.
cordarone for sale
Actual trends of medicament. Get information now.
Medication information for patients. Effects of Drug Abuse.
bactrim pill
Some what you want to know about medicament. Get information here.
Medicament information. Brand names.
nolvadex
Best news about pills. Get now.
I recommend this site to everyone! the best hotel!Romantik Hotel Schweiz
Medication information for patients. Brand names.
stromectol without dr prescription
Best about drugs. Get information here.
Thank you a bunch for sharing this with all people you actually recognize what you’re speaking approximately!
Bookmarked. Please additionally consult with my web site =).
We could have a hyperlink trade agreement between us
Pills information. Cautions.
zithromax
Best news about drug. Get information now.
Medication information leaflet. Brand names.
finpecia order
Some news about medication. Get information now.
Medication information. What side effects?
zovirax prices
Everything trends of pills. Read now.
Thanks for some other informative site. Where else may just I get that kind of information written in such an ideal manner?
I’ve a venture that I am simply now operating on, and I’ve been at the look
out for such information.
Drugs information leaflet. Long-Term Effects.
provigil for sale
Actual trends of pills. Get information now.
It’s perfect time to make some plans for the longer term and it’s time to be happy.
I have learn this put up and if I could I desire to counsel you some fascinating issues or suggestions.
Perhaps you could write next articles relating to this article.
I desire to read more issues approximately it!
Medicines prescribing information. Short-Term Effects.
prozac cost
Some about medicament. Read information here.
Medicines prescribing information. Cautions.
propecia prices
Actual news about pills. Read now.
Medicine information for patients. Drug Class.
prozac
Best what you want to know about medicines. Read here.
Drugs information leaflet. Brand names.
fosamax price
Everything what you want to know about drug. Read now.
https://www.poemsbook.net/blogs/27454/Flower-delivery-in-Ukraine
Drugs prescribing information. Generic Name.
stromectol pills
Everything information about meds. Get now.
Medicament information for patients. Short-Term Effects.
nexium
Best information about medicine. Get information here.
Valuable posts, Cheers!
Also visit my web blog: mostbet login (https://www.starbookmarking.com/story/online-casino-player-safety-mostbet)
Awesome posts Regards!
Also visit my web site; https://urlshortener.site/page/sports/seguran-a-do-jogador-de-cassino-online-realsbet
Thank you. A lot of write ups!
Also visit my website: tigre 777 plataforma – https://www.vingle.net/posts/5829491,
Nicely put, Kudos!
Here is my web-site: pin-up bet; https://www.intensedebate.com/people/raretlocam1981,
https://vse-o-gormonah.com/zabolevaniya/simptomy/standartnye-trebovaniya-dlya-polucheniya-zajma-onlajn.html
Pills prescribing information. Generic Name.
sildigra
Some about medicines. Get information here.
Excellent post. I used to be checking continuously this weblog and I’m impressed!
Extremely helpful info specifically the last part 🙂
I maintain such info a lot. I was looking for this certain info for a long time.
Thank you and good luck.
Medicines information sheet. Cautions.
promethazine pills
All news about medicines. Get here.
Medicine prescribing information. Cautions.
promethazine tablet
Best what you want to know about medicine. Get here.
Drugs information for patients. Brand names.
lioresal generic
Everything what you want to know about pills. Get now.
Mega Ball
Prepare to embark on a thrilling journey into the world of live casino gaming as we shine a spotlight on Evolution Gaming, the trailblazer in the industry. With their unparalleled dedication to innovation and delivering exceptional gaming experiences, Evolution Gaming has redefined the way we enjoy online casinos. In this article, we will explore the extraordinary features and gameplay of Evolution Gaming’s Live Baccarat, Crazy Time, Roulette, Mega Ball, and Instant Roulette, showcasing their commitment to pushing boundaries and setting new standards in the live casino realm.
Live Baccarat: A Fusion of Elegance and Excitement
Step into the realm of sophistication and excitement with Evolution Gaming’s Live Baccarat. Immerse yourself in the opulent setting of a brick-and-mortar casino, as professional dealers guide you through the game with grace and expertise. The high-quality streaming and multiple camera angles ensure an immersive and authentic gaming experience. With the addition of a 100% Welcome Bonus, players can enhance their chances of winning big in this timeless card game, making Live Baccarat a must-try for both seasoned players and newcomers seeking elegance and excitement.
Crazy Time: Where Imagination Meets Unpredictability
Enter a world of wonder and endless surprises with Crazy Time, a game that pushes the boundaries of live casino entertainment. Evolution Gaming’s Crazy Time brings together game show elements and thrilling casino gameplay, creating an exhilarating and unpredictable experience. Led by charismatic hosts, players can spin the colossal Crazy Time wheel, unveiling captivating bonus rounds and multipliers that can lead to massive wins. With its vibrant visuals, interactive features, and a lively atmosphere, Crazy Time ensures an unforgettable gaming adventure that will keep players coming back for more.
Roulette: A Timeless Classic Reinvented
Evolution Gaming’s Live Roulette reimagines the timeless classic for the digital age, infusing it with innovation and immersive gameplay. Engage in the excitement as the roulette wheel spins and the ball dances with anticipation. With multiple variations available, including European, American, and French Roulette, players can choose their preferred style and explore various betting options. The seamless integration of high-quality streaming and interactive chat features fosters a sense of camaraderie among players, bringing the thrill of the casino floor to your screen.
Mega Ball: Where Lottery and Bingo Converge
Evolution Gaming’s Mega Ball presents a groundbreaking fusion of lottery-style excitement and the communal spirit of bingo. Purchase cards adorned with numbers and eagerly await the draw of the balls. As the numbers are revealed, multipliers add a thrilling element, creating the potential for substantial winnings. The game’s innovative mechanics, coupled with interactive elements and the opportunity to engage with fellow players, make Mega Ball a captivating and social experience that pushes the boundaries of live casino gaming.
Instant Roulette: The Need for Speed and Instant Wins
For those seeking instant action and rapid-fire thrills, Evolution Gaming’s Instant Roulette delivers a high-octane gaming experience that satisfies the need for speed. Multiple roulette wheels spin simultaneously, giving players the freedom to place bets on any available wheel at any given moment. The seamless interface and quick gameplay create an adrenaline-fueled adventure that caters to those who crave instant gratification. Instant Roulette offers an immersive and fast-paced gaming experience that keeps the excitement levels at an all-time high.
free bonus casino no deposit gcash
In the rapidly evolving world of online casinos, GcashBonus has emerged as a trailblazer, seamlessly combining innovation and excitement to create an unparalleled gaming experience. With a focus on user-friendly features, a diverse selection of games, and the convenience of Gcash payments, GcashBonus has redefined the way players enjoy online gambling. In this article, we will explore the unique aspects that set GcashBonus apart from the rest, highlighting its commitment to innovation, game variety, and secure transactions.
A Fusion of Innovation and User-Friendly Design:
GcashBonus prides itself on its innovative approach to online gambling. The platform is designed with the user in mind, offering a seamless and intuitive interface that caters to both novice and seasoned players. With its sleek and responsive design, navigating the site and accessing your favorite games is a breeze. GcashBonus strives to create an immersive and hassle-free gaming environment that keeps players engaged and entertained.
Unleash the Game Variety:
At GcashBonus, players are treated to a vast and diverse array of games that cater to every taste. Whether you’re a fan of thrilling slots, classic table games, or the interactive experience of live dealer games, GcashBonus has it all. Partnering with renowned game providers, the platform ensures that players have access to the latest and most exciting titles on the market. With new games added regularly, boredom is simply not an option at GcashBonus.
Convenient and Secure Gcash Payments:
GcashBonus goes above and beyond by offering Gcash as a payment method, making transactions quick, convenient, and secure. Gcash, a trusted mobile wallet service in the Philippines, allows players to deposit and withdraw funds with ease. With the integration of Gcash, players can enjoy seamless transactions, eliminating the need for traditional banking methods or credit cards. This innovative payment option ensures that players can focus on the thrill of the games without any payment-related worries.
Promotions and Rewards that Elevate the Experience:
GcashBonus believes in rewarding its players generously. From the moment you sign up, you’ll be greeted with exciting promotions and bonuses that enhance your gaming experience. Whether it’s free spins, cashback offers, or exclusive tournaments, GcashBonus leaves no stone unturned when it comes to keeping players engaged and satisfied. The platform understands the importance of adding extra value to your gameplay and is committed to providing exceptional rewards.
Committed to Responsible Gambling:
GcashBonus takes responsible gambling seriously. The platform encourages players to enjoy the games responsibly and provides resources for those who may need assistance. GcashBonus promotes self-exclusion options, deposit limits, and responsible gaming tools to ensure that players maintain control over their gambling activities. Your well-being is a top priority at GcashBonus, making it a safe and responsible platform to enjoy your favorite casino games.
Conclusion:
GcashBonus stands at the forefront of innovation in the online casino industry. With its user-friendly design, vast game variety, seamless Gcash payments, and commitment to responsible gambling, GcashBonus offers an extraordinary gaming experience that is unmatched. Whether you’re a seasoned player or new to online casinos, GcashBonus invites you to embark on an exciting journey filled with endless entertainment and opportunities to win big. Discover the future of online gambling at GcashBonus and experience innovation like never before.
Disclaimer: GcashBonus is an independent online casino platform. It is essential to ensure that online gambling is legal in your jurisdiction before participating. Always gamble responsibly and set limits for your gaming activities.
Nicely put, Thank you!
Feel free to visit my blog; ice casino promo code; http://www.bloghotel.org/eltelhealthworl1972/,
Wonderful facts. Thank you.
Also visit my web-site: https://www.provenexpert.com/jecdenonij1974/
You actually revealed it adequately!
Feel free to surf to my homepage: totalbet logowanie (https://www.divephotoguide.com/user/totalbetgxy)
Medicament information. Generic Name.
bactrim generics
Some trends of medicament. Read here.
Medicament information leaflet. Cautions.
prozac
Actual trends of medicament. Get now.
Процесс входа на Gama Casino был простым и безопасным. Я легко нашел кнопку входа на их сайте, ввел свои учетные данные и получил доступ к своему аккаунту. Я оценил удобство и интуитивно понятный интерфейс страницы входа. Кроме того, Gama Casino предлагает дополнительные меры безопасности, такие как двухэтапную аутентификацию, чтобы защитить мой аккаунт. Вход Гама казино – это быстрый и безопасный способ начать наслаждаться их разнообразными азартными играми и бонусами. Я рекомендую Gama Casino всем азартным игрокам, которые ищут надежное и удобное казино для своих игровых потребностей.
Meds information for patients. Short-Term Effects.
stromectol brand name
Everything trends of drugs. Read here.
Meds information for patients. Long-Term Effects.
rx provigil
Actual what you want to know about drugs. Read information now.
Drugs information sheet. Short-Term Effects.
lisinopril without rx
Some information about drug. Get information here.
levaquin generic
Meds information. Short-Term Effects.
buy generic lasix
All information about medicine. Get information here.
Great post. I used to be checking constantly this blog and I’m impressed!
Very useful information specifically the last part 🙂 I handle such information much.
I used to be seeking this particular information for a very lengthy time.
Thanks and good luck.
jetix foguete
can you get lisinopril without a prescription
Drugs information. What side effects can this medication cause?
zenegra medication
Best information about drug. Read information here.
Medicament prescribing information. Generic Name.
mobic without prescription
Everything what you want to know about medicines. Get information here.
биокамин купить
Drugs prescribing information. What side effects can this medication cause?
lasix order
Best information about drug. Read information now.
Medication information sheet. Cautions.
retrovir
Everything information about medicines. Read here.
get fake passport
Meds information leaflet. Long-Term Effects.
mobic
Actual what you want to know about medication. Read now.
Pills information for patients. Short-Term Effects.
pregabalin buy
Some news about meds. Read here.
Furthermore, Sportsbetting.ag gives a racebook with all the big tracks and races.
My webpage: http://soho.nple.com/info/4986340
perfect little pussy
Pills information sheet. What side effects?
zithromax tablets
Everything about medicine. Read information now.
Medication information for patients. What side effects can this medication cause?
baclofen online
Actual news about pills. Get information now.
mature ass fuck
Pills information sheet. Cautions.
sildigra generics
All about medicines. Read here.
Drugs prescribing information. Effects of Drug Abuse.
cleocin for sale
Best information about drug. Get information here.
I recommend this site to everyone! the best hotel!car leasing in dubai
娛樂城
體驗金使用技巧:讓你的遊戲體驗更上一層樓
I. 娛樂城體驗金的價值與挑戰
娛樂城體驗金是一種特殊的獎勵,專為玩家設計,旨在讓玩家有機會免費體驗遊戲,同時還有可能獲得真實的贏利。然而,如何充分利用這些體驗金,並將其轉化為真正的遊戲優勢,則需要一定的策略和技巧。
II. 闡釋娛樂城體驗金的使用技巧
A. 如何充分利用娛樂城的體驗金
要充分利用娛樂城的體驗金,首先需要明確其使用規則和限制。通常,體驗金可能僅限於特定的遊戲或者活動,或者在取款前需要達到一定的賭注要求。了解這些細節將有助於您做出明智的決策。
B. 選擇合適遊戲以最大化體驗金的價值
不是所有的遊戲都適合使用娛樂城體驗金。理想的選擇應該是具有高回報率的遊戲,或者是您已經非常熟悉的遊戲。這將最大程度地降低風險,並提高您獲得盈利的可能性。
III. 深入探討常見遊戲的策略與技巧
A. 介紹幾種熱門遊戲的玩法和策略
對於不同的遊戲,有不同的策略和技巧。例如,在德州撲克中,一個有效的策略可能是緊密而侵略性的玩法,而在老虎機中,理解機器的支付表和特性可能是獲勝的關鍵。
B. 提供在遊戲中使用體驗金的實用技巧和注意事項
體驗金是一種寶貴的資源,使用時必須謹慎。一個基本的原則是,不要將所有的娛樂城體驗金都投入一場遊戲。相反,您應該嘗試將其分散到多種遊戲中,以擴大獲勝的機會。
IV.分析和比較娛樂城的體驗金活動
A. 對幾家知名娛樂城的體驗金活動進行比較和分析
市場上的娛樂城數不勝數,他們的體驗金活動也各不相同。花點時間去比較不同娛樂城的活動,可能會讓你找到更適合自己的選擇。例如,有些娛樂城可能會提供較大金額的體驗金,但需達到更高的賭注要求;另一些則可能提供較小金額的娛樂城體驗金,但要求較低。
B. 分享如何找到最合適的體驗金活動
找到最合適的體驗金活動,需要考慮你自身的遊戲偏好和風險承受能力。如果你更喜歡嘗試多種遊戲,那麼選擇範圍廣泛的活動可能更適合你。如果你更注重獲得盈利,則應優先考慮提供高額體驗金的活動。
V. 結語:明智使用娛樂城體驗金,享受遊戲樂趣
娛樂城的體驗金無疑是一種讓你在娛樂中獲益的好機會。然而,利用好這種機會,並非一蹴而就。需要透過理解活動規則、選擇適合的遊戲、運用正確的策略,並做出明智的決策。我們鼓勵所有玩家都能明智地使用娛樂城體驗金,充分享受遊戲的樂趣,並從中得到價值。
娛樂城
Medicament information leaflet. Generic Name.
prozac
All what you want to know about medicine. Get information now.
https://www.realbrest.by/prosto-dlja-vas/kak-poluchit-kredity-na-pokupku-zhilja-v-belarusi.html
Medicament information leaflet. What side effects can this medication cause?
cost abilify
Some information about meds. Read information now.
Heya! I’m at work surfing around your blog from my new
apple iphone! Just wanted to say I love reading
your blog and look forward to all your posts!
Keep up the outstanding work!
You have made your stand very effectively.!
my homepage – http://156.226.17.6/home.php?mod=space&uid=957329&do=profile&from=space
tacrolimus cheap
protonix
https://gid.volga.news/665216/article/kak-snyat-kvartiru-v-minske.html
Medication prescribing information. Generic Name.
lisinopril online
All information about medicament. Get information now.
Drug information. Drug Class.
propecia online
Everything trends of medication. Get now.
Medication information for patients. Effects of Drug Abuse.
where to buy singulair
Some about drugs. Read here.
При входе на Gama Casino я оценил их простой и интуитивно понятный интерфейс. Я мгновенно нашел кнопку входа на главной странице и легко ввел свои учетные данные. Они также предлагают защиту аккаунта через двухэтапную аутентификацию, что придает дополнительную безопасность. После входа я обнаружил широкий выбор игр и возможность пользоваться бонусами и акциями. Вход Gama Casino – это простой и безопасный способ начать играть в увлекательные азартные игры. Я рекомендую это казино всем азартным игрокам!
Pills prescribing information. What side effects?
finpecia otc
Everything about medicines. Read here.
Medicine information leaflet. Effects of Drug Abuse.
paxil cost
All what you want to know about drug. Get information here.
buy actos 30 mg online
Gama Casino – это казино с превосходной репутацией и надежными операторами. Я играю здесь уже несколько месяцев и ни разу не испытал проблем с выводом выигрышей. Они предлагают различные способы пополнения и вывода средств, включая популярные электронные кошельки и банковские карты. Безопасность и конфиденциальность клиентов являются их приоритетом. Рекомендую Gama Casino как надежное и профессиональное онлайн-казино.
Больше на сайте https://digenforum.ru/
Medicines information leaflet. What side effects?
tadacip brand name
All what you want to know about medicament. Get here.
Superb info. Regards.
Drugs information sheet. Long-Term Effects.
generic cialis
Actual about medicine. Read now.
娛樂城
娛樂城
娛樂城
體驗金使用技巧:讓你的遊戲體驗更上一層樓
I. 娛樂城體驗金的價值與挑戰
娛樂城體驗金是一種特殊的獎勵,專為玩家設計,旨在讓玩家有機會免費體驗遊戲,同時還有可能獲得真實的贏利。然而,如何充分利用這些體驗金,並將其轉化為真正的遊戲優勢,則需要一定的策略和技巧。
II. 闡釋娛樂城體驗金的使用技巧
A. 如何充分利用娛樂城的體驗金
要充分利用娛樂城的體驗金,首先需要明確其使用規則和限制。通常,體驗金可能僅限於特定的遊戲或者活動,或者在取款前需要達到一定的賭注要求。了解這些細節將有助於您做出明智的決策。
B. 選擇合適遊戲以最大化體驗金的價值
不是所有的遊戲都適合使用娛樂城體驗金。理想的選擇應該是具有高回報率的遊戲,或者是您已經非常熟悉的遊戲。這將最大程度地降低風險,並提高您獲得盈利的可能性。
III. 深入探討常見遊戲的策略與技巧
A. 介紹幾種熱門遊戲的玩法和策略
對於不同的遊戲,有不同的策略和技巧。例如,在德州撲克中,一個有效的策略可能是緊密而侵略性的玩法,而在老虎機中,理解機器的支付表和特性可能是獲勝的關鍵。
B. 提供在遊戲中使用體驗金的實用技巧和注意事項
體驗金是一種寶貴的資源,使用時必須謹慎。一個基本的原則是,不要將所有的娛樂城體驗金都投入一場遊戲。相反,您應該嘗試將其分散到多種遊戲中,以擴大獲勝的機會。
IV.分析和比較娛樂城的體驗金活動
A. 對幾家知名娛樂城的體驗金活動進行比較和分析
市場上的娛樂城數不勝數,他們的體驗金活動也各不相同。花點時間去比較不同娛樂城的活動,可能會讓你找到更適合自己的選擇。例如,有些娛樂城可能會提供較大金額的體驗金,但需達到更高的賭注要求;另一些則可能提供較小金額的娛樂城體驗金,但要求較低。
B. 分享如何找到最合適的體驗金活動
找到最合適的體驗金活動,需要考慮你自身的遊戲偏好和風險承受能力。如果你更喜歡嘗試多種遊戲,那麼選擇範圍廣泛的活動可能更適合你。如果你更注重獲得盈利,則應優先考慮提供高額體驗金的活動。
V. 結語:明智使用娛樂城體驗金,享受遊戲樂趣
娛樂城的體驗金無疑是一種讓你在娛樂中獲益的好機會。然而,利用好這種機會,並非一蹴而就。需要透過理解活動規則、選擇適合的遊戲、運用正確的策略,並做出明智的決策。我們鼓勵所有玩家都能明智地使用娛樂城體驗金,充分享受遊戲的樂趣,並從中得到價值。
娛樂城
https://acigaleclub.com/stati/arenda-kvartiry-minsk
Drugs information. What side effects?
cheap fluoxetine
Best trends of medicine. Get information now.
Medicament information sheet. What side effects?
nolvadex brand name
All what you want to know about drugs. Read here.
You actually stated this perfectly.
Here is my webpage – ice casino 73 (https://auditorestcepe.org/2019/07/16/nota-sobre-a-portaria-normativa-no-14-de-03-julho-de-2017/)
Cheers, Quite a lot of advice!
My web page :: tigre777 download; http://amarachicranesandforklifts.com/index.php/component/k2/item/1,
the best form of ashwagandha
Our Seo agency goes beyond the beaten patterns of thinking about positioning.
Pills information. Long-Term Effects.
female viagra without dr prescription
Everything about medicament. Get here.
cefixime uses
Medicament prescribing information. Brand names.
mobic
Actual about medicament. Read here.
Medicine information leaflet. What side effects can this medication cause?
how to buy cleocin
Actual information about meds. Get information now.
Thanks for sharing such a good thought, piece of writing is fastidious, thats why i have read it fully
zyrtec dose
Hey I know this is off topic but I was wondering if you
knew of any widgets I could add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog and
I look forward to your new updates.
ciproxin
Drugs prescribing information. Generic Name.
finpecia
Best about pills. Get now.
can i purchase cleocin price
Ⲩou’re bringіng something new to thе table!
Thank you for sharing your fresh perspective.
can i buy colchicine without prescription
cordarone 200 mg tablet uk
Medicines information. What side effects can this medication cause?
lioresal
Actual information about pills. Read here.
Meds information for patients. Brand names.
cost avodart
Everything about drug. Read now.
diltiazem warnings
doxycycline monohydrate 100mg price
furosemide 50 mg for dogs
Meds information for patients. Brand names.
zenegra
Everything trends of drugs. Get now.
vr https://muckrack.com/rafian-rafian/bio will not take off till the means of production are democratized.
It is appropriate time to make some plans for the future and it is time to be happy.
I’ve read this post and if I could I want to suggest you some interesting things or
advice. Perhaps you could write next articles referring to this article.
I want to read more things about it!
Medication information. Effects of Drug Abuse.
cost of nolvadex
Best what you want to know about drug. Read information now.
levaquin brand names
where to get lisinopril pill
Другими словами, транскреация также может называться «творческий перевод» или «творческий
перевод».
Medication information leaflet. Drug Class.
viagra
Actual news about medicine. Get information here.
Medicines prescribing information. Cautions.
sildigra medication
All news about medicines. Get now.
Someone necessarily assist to make significantly articles I’d state.
That is the very first time I frequented your web page and up to
now? I surprised with the research you made to
create this particular submit extraordinary. Excellent job!
Medicament information leaflet. Effects of Drug Abuse.
tadacip
Actual news about medication. Read now.
Medication information for patients. Short-Term Effects.
sildalist price
Actual what you want to know about medicament. Get information now.
kampus canggih
Meds information for patients. Generic Name.
finasteride
Actual what you want to know about medicine. Read now.
Однозначно, отличный ответ
https://www.mercycatering.co.uk/2019/03/16/hello-world/ dwell (us$1.
efient 10 mg
Drugs information leaflet. Brand names.
paxil generics
Best trends of drug. Read now.
Drugs information sheet. Effects of Drug Abuse.
lisinopril without dr prescription
Some information about medicines. Get now.
side effects of prednisone
Идея хорошая, согласен с Вами.
learn how your https://carmenbelissa.com.co/2016/05/10/capsulaslineadenochetatianagil/ closes down.
It’s an amazing article for all the web visitors; they will obtain benefit
from it I am sure.
??? ???? ?????, ???????????? ремонт шкода.
Great article, just what I wanted to find.
Drug information sheet. Effects of Drug Abuse.
aurogra pills
Actual about medicines. Read information here.
Meds information. Drug Class.
promethazine buy
All what you want to know about medicines. Read information here.
бонус Вулкан Жара по промокоду
I blog often and I really thank you for your information.
Your article has really peaked my interest. I will book mark your website and
keep checking for new information about once per week.
I opted in for your RSS feed as well.
Ваша мысль пригодится
the costume that a person is in revealing the interior man.
Its such as you learn my mind! You seem to understand a lot about this, such as you wrote the e-book in it or something.
I think that you just could do with a few p.c. to power the message home a little bit, but other than that, this is wonderful blog.
A great read. I will certainly be back.
Pills information leaflet. What side effects can this medication cause?
lyrica
Everything news about medicines. Get information now.
взЯть займ на карту мир без отказа: удобный и скоростной способ получить деньги в долг.
В России микрофинансовых организаций выдают займы людям, в том числе клиентам с отрицательной КИ и просрочками.
В РФ можно получить микрокредит онлайн на карту, электронный кошелек или наличными. Для получения займа необходимо оставить заявку и выслать документы, которые потребует МФО РФ. Кредитный рейтинг и плохая кредитная история могут повлиять на процентную ставку и шанс получить микрозайм мгновенно. Можно получить быстрый заём до 50 000 рублей, а также взять срочный микрозайм наличными.
В нынешнем мире, когда время играет большую роль, микрозаймы онлайн стали одним из самых востребованных способов получения финансовой поддержки. Возможность оформить микрокредит на карту мгновенно и без отказа, а также получить микрозаймы наличными, привлекает всё больше людей.
МФО предлагают широкий выбор кредитов, включая срочные займы на карту, микрозаймы онлайн и микрокредиты наличными. Одним из главных преимуществ этих услуг является возможность взять займ без отказа на карту в России в 2023 году, что становится незаменимым для людей с плохой кредитной историей.
Среди прочих услуг МФО можно выделить кредиты без процентов на карту сразу в первый раз, что позволяет сэкономить на процентах и вернуть только ту сумму, которую взяли.
сумские новости
http://www.gencotyre.com/comerblog/member.asp?action=view&memName=etajaxedu
Промокод Гама Казино Если вы уже зарегистрированы, для входа на сайт просто введите свой логин и пароль. Если вы забыли пароль, вы можете восстановить его через специальную функцию на сайте.
https://titusozkuf.blogocial.com/benefits-of-selecting-on-line-casino-online-games-from-a-dependable-on-line-casino-portal-54953276
Hi, I check your blog daily. Your story-telling style is awesome,
keep doing what you’re doing!
My spouse and I stumbled over here from a different
website and thought I may as well check things out. I like what
I see so i am just following you. Look forward to looking over your web page again.
на данной странице следует оставлять комментарии, относящиеся к слову https://judahyrjb00987.blogsidea.com/24106348/keep-heat-and-cozy-with-heaters-a-information-to-selecting-the-correct-a-person-powered.
Kudos, Terrific stuff.
my website … https://binary-options.asia/?qa=168/the-3-minute-rule-for-binary-options
https://messiahjtepz.arwebo.com/42233321/advantages-of-picking-out-on-line-casino-games-from-the-trustworthy-on-line-casino-portal
Гамма казино Gama Casino предлагает возможность игры на мобильных устройствах. У нас есть мобильная версия сайта, а также скачиваемое приложение для Android и iOS. Теперь вы можете наслаждаться любимыми играми в казино Gama в любое время и в любом месте.
С помощью службы копирайтинга MyContent вы получаете обновленный веб-контент,
чтобы улучшить результаты вашего веб-сайта.
For most recent news you have to pay a quick visit
world-wide-web and on the web I found this website as a finest site for newest updates.
Всем рекомендую! Только тут можно преобрести качественныекондиционеры в АлматыКомпания «ClimTech» реализует промышленные и бытовые кондиционеры в Алматы на выгодных для предприятий и частных лиц условиях.
百家樂
百家樂(Baccarat)是一種撲克遊戲,也是賭場中常見的賭博遊戲之一。它起源於義大利,在15世紀傳入法國,並在19世紀盛行於英法等地。如今,百家樂是全球各地賭場中受歡迎的賭博遊戲之一,特別是在澳門的賭場中,百家樂賭桌的數量是全球賭場中最多的,下注金額和獲利也佔據著澳門賭場的領導地位。
玩法:
玩家可以下注莊家(Banker)或閒家(Player),並沒有限制。遊戲中使用8副撲克牌,洗牌後放在發派箱中。每局遊戲,莊家和閒家都會收到至少兩張牌,但不超過三張牌。第一和第三張牌發給閒家,第二和第四張牌發給莊家。根據補牌規則,可能需要再發一張牌給莊家或閒家。
點數計算方法:
在百家樂中,撲克牌的點數計算方法是:Ace牌算作1點,2到9的牌按其顯示的點數計算,10、J、Q和K的牌則算作0點(有些賭場可能將10點視為10點)。當所有牌的點數總和超過9時,只計算總數中的個位數。因此,8和9的牌點數總和為7點(8 + 9 = 17)。百家樂只計算撲克牌的個位數值,因此可能的最大點數是9點(例如,一張4和一張5的牌點數總和為9),最小點數是0點,也稱為baccarat(例如,一張10和一張Q的牌點數總和為20,只計算個位數,即0)。
投注:
玩家可以在莊家或閒家上下注,也可以下注和局(即最終點數一樣)。此外,玩家還可以下注莊對子或閒對子(即莊或閒首兩張牌相同)。在澳門的賭場中,還加入了「幸
運六」,玩家可以下注莊或閒是否能以6點取勝。
賠率:
如果下注莊家並且莊家贏,有兩種玩法可以選擇。第一種是買1賠0.95,即需要支付5%的佣金給莊家。第二種是「免佣百家樂」,贏1賠1,但如果莊家以6點取勝,則賠率為1賠0.5。下注閒家並且閒家贏,贏1賠1。下注和局,贏1賠8。下注莊對子或閒對子,贏1賠11。根據澳門賭場的「幸運六」賠率,以兩張牌的6點取勝為贏1賠12,以三張牌的6點取勝為贏1賠20。
機會率:
在百家樂中,下注莊家的期望值只有約1%左右的優勢,和大多數賭場遊戲相比相對較低。
結論
百家樂是一種簡單易懂的賭博遊戲,也是一個非常社交化的遊戲。在百家樂桌上,通常有一名荷官負責發牌和管理遊戲進程。玩家只需要在莊家、閒家或和局中選擇一方下注,然後觀察牌局結果。
百家樂的玩法優勢在於其遊戲節奏快速,且無需玩家做出複雜的決策。遊戲結果完全基於牌的發放和點數計算,使得玩家可以輕鬆參與,無需特別的技巧或策略。
此外,百家樂也因其高投注限制而聞名。在高額賭桌上,玩家可以下注巨額金額,使得這個遊戲成為富豪和高額賭徒的首選。然而,即使在小賭桌上,百家樂仍然吸引著許多玩家,因為它提供了一種緊張刺激的賭博體驗。
百家樂也具有一些特殊的傳統和儀式。例如,在一些賭場中,荷官會使用一把特殊的牌具,稱為百家樂靴(Baccarat Shoe),其中放有多副牌。這種做法旨在提高遊戲的公平性和隨機性。
總的來說,百家樂是一個受歡迎的賭博遊戲,不僅因其簡單易懂的規則,而且因其高投注限制和社交化的特性。無論是在實體賭場還是在網絡賭場,玩家都可以享受到這個刺激的遊戲,並期待著幸運女神的眷顧
https://www.siteoutlook.com/domain/rg8888.org
In a casino game, the players gamble caash or
casuno chis onn different probable random outcomes
orr combinations of outcomes.
Look att my website :: 바카라
schlГјsseldienst kosten welche versicherung zahlt fГјr verlorene schlГјssel?
Medicines information leaflet. Generic Name.
neurontin price
All news about medicine. Get now.
Medicament information sheet. What side effects can this medication cause?
minocycline
Actual trends of medicament. Get here.
I absolutely love your blog and find most of your post’s to be what precisely I’m looking for.
Do you offer guest writers to write content for yourself?
I wouldn’t mind creating a post or elaborating on some
of the subjects you write regarding here. Again, awesome site!
Meds information. Cautions.
sildigra
Actual news about medication. Get information here.
With havin so much written content do you ever run into any problems of plagorism or copyright infringement?
My site has a lot of completely unique content I’ve either created myself or outsourced but
it looks like a lot of it is popping it up all over the internet without my authorization.
Do you know any solutions to help stop content from being ripped off?
I’d really appreciate it.
Drugs information for patients. Short-Term Effects.
cheap baclofen
Everything trends of drugs. Read here.
Medicament prescribing information. What side effects?
norpace sale
Actual trends of medication. Get information here.
Medication information for patients. Short-Term Effects.
glucophage price
Actual trends of medicine. Get here.
Medicament information sheet. Brand names.
cipro prices
Everything news about medicines. Read here.
Medicament information sheet. Long-Term Effects.
flagyl pills
Some information about medicines. Read here.
Drug information. Brand names.
rx eldepryl
Everything information about medicine. Get information now.
http://rusnod.ru/
Fine way of explaining, and nice piece of writing
to get information on the topic of my presentation subject, which i am going to present in college.
Meds information leaflet. Effects of Drug Abuse.
where to buy silagra
Actual trends of drugs. Get information now.
Drugs prescribing information. Brand names.
norvasc price
All trends of medication. Get now.
Drug information leaflet. Drug Class.
cipro buy
Everything information about meds. Get now.
Medicines information for patients. What side effects can this medication cause?
cytotec buy
All information about pills. Read information here.
Wow tons of great facts.
My web blog; http://47.254.179.240/node/33364
Attractive section of content. I just stumbled upon your weblog and in accession capital to assert that I get actually enjoyed account your blog
posts. Any way I will be subscribing to your augment and even I achievement you access
consistently quickly.
Medicine information leaflet. Short-Term Effects.
cleocin
Some news about medication. Get now.
Medication prescribing information. Effects of Drug Abuse.
provigil brand name
Some trends of drug. Read here.
Drug information leaflet. Effects of Drug Abuse.
buy generic mobic
Best trends of drugs. Get here.
Hello, its fastidious piece of writing regarding media print, we all be
aware of media is a enormous source of data.
Drugs information sheet. Generic Name.
retrovir buy
Some trends of medicament. Get information here.
Medicament prescribing information. Drug Class.
effexor
Best what you want to know about medicine. Read information now.
Medicine information. Effects of Drug Abuse.
abilify medication
Everything information about medicament. Get now.
Medication information for patients. Long-Term Effects.
finpecia
Actual information about medicines. Read now.
You’ve ѕhown us what excelⅼence looks like! Thank you for being a shining example
of what great writing looks likе.
Medicine information sheet. Short-Term Effects.
bactrim medication
All information about pills. Read information here.
I was suggested this blog by my cousin. I am not sure whether this post is written by him as nobody else know such detailed about my difficulty.
You’re wonderful! Thanks!
Hello I am so thrilled I found your site, I really found you by error, while I
was researching on Digg for something else, Regardless
I am here now and would just like to say thanks a lot for a remarkable post and a all round thrilling blog (I also love the theme/design), I don’t have
time to read it all at the moment but I have saved it and also added your RSS feeds, so when I have time I
will be back to read much more, Please do keep up the fantastic b.
Medication information. What side effects?
tadacip pills
All trends of pills. Read here.
Hi there very nice site!! Guy .. Excellent ..
Superb .. I’ll bookmark your website and take the feeds additionally?
I am glad to search out a lot of helpful information right here within the submit, we need work out extra strategies on this regard, thank you for sharing.
. . . . .
Drug information for patients. Cautions.
cordarone otc
Actual news about medicines. Read information here.
Москвичей и гостей столицы пригласили на сольный концерт Олега Шаумарова, автора хита Орлы или вороны, других песен для Николая Баскова, Ирины Круг и многих других звёзд российской эстрады, который пройдёт 24 июня в Jam Club (Москва, Сретенка, 11).
Мы вдвоем
What’s up i am kavin, its my first occasion to commenting anywhere, when i read
this paragraph i thought i could also create comment due to
this sensible article.
I’m really impressed with your writing skills as well as with the layout
on your blog. Is this a paid theme or did you customize it yourself?
Anyway keep up the nice quality writing, it’s rare
to see a nice blog like this one nowadays.
fake portugal residence
I have learn some good stuff here. Definitely price bookmarking for revisiting.
I surprise how much attempt you set to create one of these wonderful informative website.
Hi there to every , as I am truly keen of reading this blog’s post to be updated on a regular basis.
It contains good stuff.
Medicament information for patients. What side effects?
fluoxetine prices
Everything information about drugs. Get information now.
Drug information sheet. Drug Class.
lyrica sale
Actual about medicines. Read now.
Medicament information sheet. What side effects can this medication cause?
lopressor
Everything about medicines. Read information here.
Meds information. Cautions.
bactrim
Best news about drugs. Get information now.
Medicine prescribing information. What side effects?
can you get nolvadex
Some what you want to know about drugs. Read now.
Drugs information for patients. Drug Class.
cephalexin
Best news about drugs. Get information now.
I could not refrain from commenting. Perfectly written!
Meds information for patients. Brand names.
where can i buy lasix
All what you want to know about medication. Read information here.
Write more, thats all I have to say. Literally, it seems as though you relied on the video to make your point.
You definitely know what youre talking about, why throw away your intelligence on just posting videos to your weblog when you
could be giving us something enlightening to read?
Meds information leaflet. Brand names.
nolvadex
Some trends of medication. Read information now.
Players also like roulette, a timeless and classic that has attracted players for several years.
Also visit my web blog: https://smf.lserv.com/index.php?topic=59315.0
Medication information sheet. Long-Term Effects.
nolvadex medication
Actual about drugs. Get information now.
Drugs information for patients. What side effects?
effexor medication
All news about medicine. Get here.
Meds information for patients. Long-Term Effects.
diltiazem
Actual what you want to know about medication. Read information here.
Medicines information sheet. Cautions.
can i order cleocin
Some what you want to know about meds. Read here.
I’m not sure exactly why but this site is loading extremely slow
for me. Is anyone else having this issue or
is it a problem on my end? I’ll check back later
on and see if the problem still exists.
Hmm it looks like your site ate my first comment (it was super long) so I guess
I’ll just sum it up what I had written and say, I’m
thoroughly enjoying your blog. I too am an aspiring blog blogger but I’m still new to everything.
Do you have any suggestions for newbie blog writers?
I’d genuinely appreciate it.
You reported it wonderfully.
Feel free to surf to my blog post – http://www.visualchemy.gallery/forum/profile.php?id=2392011
Medication information. Generic Name.
zyban cheap
Everything information about medicament. Get information here.
Казино Cat: Ваш путь к азартному развлечению
казино на реальные деньги
Medication information leaflet. What side effects?
buy fluoxetine
Actual about pills. Get information now.
Большой выбор игр и слотов
автоматы онлайн
Medicine information. Effects of Drug Abuse.
levaquin price
Best news about medicament. Read information now.
Drugs information. Cautions.
sildigra
Everything trends of meds. Read now.
Great forum posts. Many thanks!
my web blog … http://xn--vb0b93rhlhtnf9uw.com/bbs/board.php?bo_table=free&wr_id=41671
It?s hard to come by well-informed people about this subject, but you seem like you know
what you?re talking about! Thanks
Feel free to visit my blog post – Vita Labs CBD Gummies Reviews
stromectol online
Meds prescribing information. Long-Term Effects.
tadacip buy
Everything trends of medicament. Get information now.
Medicines information sheet. Short-Term Effects.
tadacip
All about medication. Read information here.
Thanks a lot! Wonderful information.
My website: http://86x.org/home.php?mod=space&uid=2210789&do=profile&from=space
levaquin rx
Medicines information. What side effects can this medication cause?
buy generic seroquel
Best news about medication. Read here.
Pills prescribing information. Cautions.
propecia buy
Actual trends of drugs. Read information now.
Nicely put, Thank you!
my page https://socialbookmarkingsites.xyz/page/sports/casino-table-games-mcw-casino
Nicely put, Regards.
my page :: https://cwinz3rx.bravejournal.net/post/2023/05/29/Sports-betting-on-the-gaming-service-cwinz
Drugs information leaflet. Short-Term Effects.
where can i buy cephalexin
All information about medicines. Read here.
Thank you. I appreciate it.
My web site … betbuzz 365 [https://triberr.com/altopriopa1974]
Whoa a lot of excellent advice.
my homepage: jeetbuzz new account – http://daveydreamnation.com/w/index.php?title=User:Erasorwi1976&action=submit –
Cheers. Helpful information!
my blog post :: baji999 অ্যাপ (https://tree.taiga.io/project/nextmelissa1982-baji999th9/wiki/home)
Hey there! I’ve been following your weblog for a while now and finally got the bravery to
go ahead and give you a shout out from Huffman Texas!
Just wanted to say keep up the great job!
Also visit my web blog – mcw casino world
Drugs information sheet. Generic Name.
buy colchicine
Everything trends of pills. Read information here.
Drug information for patients. Generic Name.
zenegra
Actual what you want to know about medication. Read information now.
https://www.business.unsw.edu.au/forms-site/surveys/Lists/SMY%20Profile%20Information%20January%202016%20Intake/DispForm.aspx?ID=46771
Drugs prescribing information. Cautions.
cialis soft buy
All about medicament. Read now.
Fantastic content With thanks.
Look at my web blog … https://www.cydiafree.com/
Hey there, I think your blog might be having browser compatibility issues.
When I look at your blog site in Firefox, it looks fine but when opening in Internet Explorer, it has some overlapping.
I just wanted to give you a quick heads up! Other then that,
terrific blog!
Drugs information. Short-Term Effects.
prozac
Some information about medicine. Read here.
I am really loving the theme/design of your website.
Do you ever run into any web browser compatibility issues?
A small number of my blog visitors have complained about
my website not working correctly in Explorer but looks great
in Chrome. Do you have any recommendations to help fix this problem?
Drugs prescribing information. What side effects can this medication cause?
glucophage buy
Everything what you want to know about medicine. Get here.
I was suggested this website by my cousin. I am not sure whether this post is written by him
as no one else know such detailed about my problem.
You are amazing! Thanks!
Actually no matter if someone doesn’t understand then its up to other users that they will
assist, so here it occurs.
Howdy, I believe your web site might be having web browser compatibility
problems. Whenever I take a look at your blog in Safari, it looks fine however when opening in Internet Explorer, it has
some overlapping issues. I merely wanted to provide
you with a quick heads up! Besides that, great blog!
Hi! Someone in my Facebook group shared this website
with us so I came to check it out. I’m definitely enjoying
the information. I’m bookmarking and will be tweeting
this to my followers! Great blog and superb style and design.
Meds information for patients. Cautions.
colchicine
Actual news about medicament. Read information here.
Medicines information for patients. What side effects can this medication cause?
sildenafil online
Everything information about medication. Get here.
Hi there, i read your blog occasionally and i own a similar one and i was just
wondering if you get a lot of spam feedback?
If so how do you prevent it, any plugin or anything you can suggest?
I get so much lately it’s driving me insane so any assistance is very much appreciated.
Great beat ! I wish to apprentice while you amend your
website, how could i subscribe for a blog web site? The account
helped me a acceptable deal. I had been tiny bit acquainted of this your broadcast offered
bright clear idea
Drug information sheet. Brand names.
propecia
Actual about medication. Get information here.
Hey there, I think your blog might be having browser compatibility issues.
When I look at your blog in Opera, it looks fine but when opening in Internet Explorer, it has some
overlapping. I just wanted to give you a quick heads
up! Other then that, very good blog!
Hi there to every body, it’s my first visit of this blog;
this weblog consists of awesome and really excellent data in favor of
readers.
Medicines information for patients. Drug Class.
lyrica generics
Actual information about meds. Read information here.
Drugs information leaflet. What side effects can this medication cause?
levitra
Actual trends of medicine. Get now.
Medication prescribing information. Short-Term Effects.
pregabalin medication
Best news about pills. Get information now.
Drug prescribing information. Brand names.
avodart order
Some about drug. Read information here.
fantastic publish, very informative. I ponder why the opposite experts of this sector don’t realize this.
You should continue your writing. I’m confident, you’ve a great readers’ base already!
Medicament information leaflet. What side effects can this medication cause?
provigil without dr prescription
All information about drug. Get now.
Medicines information sheet. Brand names.
aurogra
Some about meds. Get here.
Drug information. What side effects?
nolvadex
All trends of drugs. Read information now.
You actually stated that effectively.
my web blog :: https://weave.nl/hallo-wereld/
This is nicely put. .
Feel free to surf to my web site bac bo estrategia; http://aoc2wiki.rf.gd/index.php/User:Trapevtyne1979,
Medicines information leaflet. Drug Class.
effexor tablet
Everything what you want to know about pills. Read information now.
Good write ups Thank you!
Look into my webpage :: http://www.lawrence.com/users/unpearnire1989/
You actually revealed it well.
Feel free to surf to my web site … http://msnho.com/blog/gry-stolowe-w-kasynie-lvbet
Meds information leaflet. Drug Class.
can you get promethazine
Actual information about drug. Get here.
http://allmagic.0pk.me/viewtopic.php?id=554#p7200
Drugs information sheet. What side effects?
cephalexin brand name
Everything news about pills. Get information here.
Wonderful site. Plenty of helpful info here. I’m sending it to a few buddies ans also
sharing in delicious. And certainly, thank you on your effort!
Medicines information sheet. Cautions.
eldepryl medication
All what you want to know about drug. Get here.
Medicine information. Cautions.
viagra pills
Some trends of meds. Read now.
Ports have built onshore electricity capacity
and so are preparing to distribute brand-new marine fuels,
notice, e.g.
Medicine information sheet. What side effects?
cephalexin pill
All news about drug. Get information now.
lordfilm
Drugs information. Generic Name.
lyrica
All information about medicament. Read here.
Medication prescribing information. Cautions.
propecia medication
Some what you want to know about medicament. Read information now.
Hey would you mind stating which blog platform you’re working with?
I’m planning to start my own blog in the near future but I’m
having a tough time choosing between BlogEngine/Wordpress/B2evolution and
Drupal. The reason I ask is because your layout
seems different then most blogs and I’m looking for something unique.
P.S My apologies for getting off-topic but I had to ask!
Hey there, You’ve done a fantastic job. I’ll certainly digg it and personally recommend to my friends.
I’m sure they’ll be benefited from this website.
Medicine information for patients. Generic Name.
get priligy
Best news about medication. Get information now.
Drugs information leaflet. What side effects?
rx flibanserina
Actual news about pills. Get information here.
Hi, I want to subscribe for this web site to obtain hottest updates,
therefore where can i do it please help.
Drug information. Cautions.
synthroid pills
Actual news about medicine. Read now.
where can i buy sildalist without rx
accutane online pharmacy india accutane cost accutane where to get
Medicines information for patients. Cautions.
fosamax prices
Some news about medicine. Read information here.
buying sildigra pills
Good posts. Regards.
order colchicine
cost cheap lisinopril pills
constantly i used to read smaller articles that as well clear their motive, and that is also happening with this paragraph which I am reading at this
place.
Medicament prescribing information. Effects of Drug Abuse.
norvasc rx
Some what you want to know about drug. Read here.
Hi there! Do you use Twitter? I’d like to follow you if that would be ok.
I’m undoubtedly enjoying your blog and look forward
to new updates.
where to get cleocin without a prescription
Medicine information. What side effects can this medication cause?
how to buy zithromax
Everything what you want to know about pills. Read information here.
Blood Clotting
rx costs accutane cheap accutane singapore can you buy accutane online uk
A lot of individuals get off and find pleasure in naked bodies than with lingerie or
clothes. Another aspect is usually vulnerability-a naked girl seems embarrassment and humiliation in a foreplay and that will be why it will be wanted.
When somebody can be naked, they feel susceptible and uncovered, nude sex comes across as being even more romantic than clothed one.
Vulnerability will be a main convert on especially for a lot of guys
because they experience the sense of dominance during sex.
a lot of nude porn focus on penetration. Nude porn is pretty normal and the genre can become seen by you attached to a whole bunch of some other
categories, therefore you will not really discover it
hard to locate your story of curiosity when eating this
porn. Some of these are usually bondage porn, Asian adult, and
lesbian porn. Since sex is normally expected to be a sacred ritual, watching a naked woman get fucked is a
good fap materials for a collection of guys. Viewing a person naked will be like
understanding their techniques and seeing them defenseless for
some, this is the cause why nude porno will be a popular genre among all audiences.|Exhibitionist men and women go out for the
greatest looking at experience. They fixed their cameras up and take pleasure in the look at from across the water.
Many have got turn out to be so into this activity that they will frequently method young couples who are usually
sunbathing to create a photo shoot. Most voyeurs are usually males,
nevertheless the intimate nature of the beach offers produced some women who
furthermore look for out the beaches for the exact same factors.
They would like to participate in the work of sex which will be another type of voyeurism.
In addition to getting transformed on by seeing guys and women, some females who spend period at the nude beach
may furthermore fantasize about the men getting sex with the women.
Medicines prescribing information. Long-Term Effects.
flibanserina
All news about pills. Read information now.
can i get cheap sildalist
Hi, i read your blog from time to time and i
own a similar one and i was just wondering if you get a lot of spam remarks?
If so how do you stop it, any plugin or anything you can suggest?
I get so much lately it’s driving me crazy so any support
is very much appreciated.
Hello, just wanted to say, I loved this post. It was funny.
Keep on posting!
https://dzen.ru/a/Y7_S3LD1c3K-n1gU
Whoa quite a lot of great knowledge!
Also visit my page Bajii999, http://emeraldas.fool.jp/nsjfjnxkeifjxueirj2fd230hg/yybbs.cgi,
You actually expressed that exceptionally well!
Feel free to surf to my webpage … jeetbuzz refer code (https://wiki.beta-campus.at/wiki/Jeetbuzz_App)
I have read so many articles or reviews regarding the blogger lovers however this
piece of writing is really a nice article, keep it up.
Drugs information for patients. Cautions.
female viagra buy
Some information about medication. Get information now.
accutane from canada pharmacy cheap accutane singapore can you really buy accutane online
Fantastic info. Cheers!
Feel free to surf to my website :: https://med-info-pharm24.top/cetirizine/
https://www.province.ru/sovet/kvartira-na-sutki-v-neznakomom.html
I have read so many content on the topic of the blogger lovers however this
post is genuinely a good post, keep it up.
Definitely imagine that that you stated. Your favourite reason seemed
to be at the internet the easiest factor to be aware of.
I say to you, I definitely get irked while other people think about issues that they just don’t recognise about.
You managed to hit the nail upon the top and also outlined
out the whole thing without having side-effects , people could take a signal.
Will probably be again to get more. Thank you
https://fineart.sk/cache/permission/vnezemnoe_eho_2014_recenziya.html
You should be a part of a contest for one of the greatest
websites online. I’m going to recommend this blog!
Excellent blog right here! Additionally your site quite a bit up fast!
What web host are you the use of? Can I get your affiliate hyperlink
on your host? I desire my website loaded up
as fast as yours lol
Drugs information leaflet. Cautions.
valtrex without insurance
Actual news about meds. Read information here.
tetracycline
It’s really very difficult in this active life
to listen news on TV, therefore I simply use internet for that purpose,
and get the most up-to-date information.
sildalist rx
I was recommended this web site by my cousin. I’m not sure
whether this post is written by him as nobody else know such detailed about my problem.
You’re wonderful! Thanks!
pantoprazole sodium 40 mg
Medicament information leaflet. What side effects can this medication cause?
valtrex
Best what you want to know about medicine. Read information now.
Pretty! This was an extremely wonderful post. Thanks for providing this information.
can i get prednisolone without insurance
This design is wicked! You certainly know how to keep a reader amused.
Between your wit and your videos, I was almost moved to start my own blog (well, almost…HaHa!) Fantastic job.
I really enjoyed what you had to say, and more than that, how you presented it.
Too cool!
Sure black moms may hold an smart conversation during the time but
they may be scantily outfitted as they set off to the club.
Ebony mothers are usually considerably attractive.
They possess wonderful and shimmering epidermis because of
the dark color of epidermis they don’t possess to stress over
sun tanning. Actually though they have that machine-gun mouth that fires their children with scolding and
talking they also have kissable lip area that invite males to take a heavy hug.
No need for make-ups, simply kiss and tell you’ll going
to drop in love under their black magic mean.Sexy porn Even at the age of fifty, they are beautiful still.
With their ageless attractiveness, they look young always.
Even how numerous kids perform they possess Furthermore, their boobs are usually
still firm and sensitive. When ladies become parents, they don’t end being human being;
they don’t change into robots. Period still marches and so their sexual
demands. But when you wish them on bed don’t simply think about sex, think
about love. So, viewing them on porno doesn’t make you horny
but also create your arousal harder than actually.
Envision eating your respected dark chocolate brand name, you’ll be satisfied in every bite!
фильмы lordfilm
how to get arimidex prescription
This is my first time pay a quick visit at here and i am
actually happy to read everthing at alone place.
Just want to say your article is as astonishing.
The clearness for your put up is simply great and i can think you are a professional in this subject.
Well along with your permission let me to take hold of your RSS
feed to keep up to date with approaching post.
Thank you 1,000,000 and please carry on the enjoyable work.
ciproxin
period.
Also visit my web-site https://www.carhubsales.com.au/user/profile/1344566
Hmm it appears like your site ate my first comment (it
was extremely long) so I guess I’ll just sum it up what I
submitted and say, I’m thoroughly enjoying your blog.
I as well am an aspiring blog writer but I’m still new
to everything. Do you have any recommendations for newbie blog writers?
I’d really appreciate it.
Here is my web blog indiana department of insurance
As mentioned, you can get began at JoeFortune with uup to a 150% match
bonus.
My website; 온라인카지노사이트
Medicament information. Effects of Drug Abuse.
neurontin
Actual information about medicine. Get information here.
Medicine prescribing information. Generic Name.
zithromax order
Some trends of drugs. Read here.
I like the valuable info you provide in your articles.
I will bookmark your blog and check again here regularly. I am quite sure I’ll learn lots of new stuff right here!
Best of luck for the next!
Moving from one webcam pal to another is as straightforward as ABC.
So, listed right here are some of the Best Apps
to Talk to Strangers.
I go to see daily some websites and websites to read articles, however
this webpage presents quality based articles.
Hi just wanted to give you a quick heads up and let you know a few of the pictures aren’t loading properly.
I’m not sure why but I think its a linking issue.
I’ve tried it in two different browsers and both show the same results.
Drugs information. What side effects can this medication cause?
retrovir price
Best what you want to know about pills. Read information here.
Link exchange is nothing else but it is only
placing the other person’s web site link on your page
at suitable place and other person will also do similar for you.
This is nicely said. .
Look at my website :: https://gardeneaze.com/masterbuilt-20070512-electric-smoker-review/
Meds prescribing information. Short-Term Effects.
zoloft
Some information about pills. Get information now.
Meds prescribing information. Cautions.
lisinopril
All about medicines. Read here.
Nicely put. Regards.
Here is my webpage … https://fairsharemarketing.ca/ten-reasons-why-having-an-excellent-pharmacy-is-not-enough/
Don’t take anything too significantly and have enjoyable when speaking to others.
Medication information leaflet. Long-Term Effects.
provigil
Everything information about drugs. Get information here.
Drug information sheet. Generic Name.
how to get lisinopril
Everything trends of medicament. Get information now.
Pills information. Long-Term Effects.
retrovir without rx
Best about drug. Read information here.
rx levaquin
Drugs information sheet. Short-Term Effects.
diltiazem
Some what you want to know about medicament. Read now.
Making use of a sex doll will be not since taboo because it was as soon as.
There is a multi-billion money business around the
creation and distribution of sophisticated and not-so-sophisticated sex dolls.
The phrase, Actual Doll has become widely known and
component of the mainstream vocabulary as
fresh components and technologies create the difficult, probable.
While guys can completely enjoy standard whack up sex dolls still, today we notice significantly
more detailed and superior versions all the period technologically.
Metal Guy, consume your heart out.
Drug prescribing information. What side effects?
cost cipro
Actual information about meds. Read now.
cefixime brand names
В этом что-то есть и мне нравится эта идея, я полностью с Вами согласен.
the same applies with http://sad117mogilev.by/%d0%be%d1%82%d1%87%d0%b5%d1%82-%d0%be-%d0%bf%d1%80%d0%be%d0%b4%d0%b5%d0%bb%d0%b0%d0%bd%d0%bd%d0%be%d0%b9-%d1%80%d0%b0%d0%b1%d0%be%d1%82%d0%b5-%d0%bf%d0%be%d0%bf%d0%b5%d1%87%d0%b8%d1%82%d0%b5%d0%bb/ expenses.
ща позырю заценю .
про себе: здравствуйте, уважаемые вы канала “https://tvpolska.pl/mateusz-morawiecki-konferencja-prasowa-premiera-w-stacji-uzdatniania-wody-w-zabkach/9810/ ru”!
Medicines information sheet. Drug Class.
buy generic tadacip
Everything what you want to know about medicines. Read now.
Drugs information sheet. Short-Term Effects.
eldepryl no prescription
Actual about medicines. Read now.
diltiazem hydrochloride
Highly descriptive blog, I loved that bit. Will there be a part 2?
Medicine prescribing information. Brand names.
ampicillin generic
Everything about meds. Read now.
Зарегистрировался на форуме, чтобы сказать Вам спасибо за помощь в этом вопросе, может, я тоже могу Вам чем-то помочь?
http://ritasjarvi.fi/cropped-cropped-nimeton-1-jpg/-подобное снижение от слова оповещение.
Drug information sheet. Generic Name.
bactrim
Everything information about drugs. Get information here.
pantoprazole 40 mg tablets
Medicines information leaflet. Generic Name.
stromectol rx
All what you want to know about medicament. Read information here.
Medicines information for patients. Brand names.
cytotec for sale
Best information about drugs. Read now.
Medication prescribing information. Short-Term Effects.
eldepryl
All what you want to know about drug. Read here.
Every weekend i used to go to see this web site, for the reason that i wish for enjoyment, since this this web page conations actually nice funny
data too.
cefixime cost
Medication information sheet. Cautions.
seroquel without insurance
Everything information about medicine. Read here.
Drug information for patients. Short-Term Effects.
singulair brand name
Actual what you want to know about medication. Get here.
continuously i used to read smaller content that as well
clear their motive, and that is also happening with this piece of
writing which I am reading at this place.
What i do not understood is in reality how you’re not actually much more smartly-liked than you might
be now. You’re so intelligent. You already know thus significantly in relation to this matter,
produced me individually believe it from a lot of
numerous angles. Its like women and men don’t seem to be interested unless it’s
something to accomplish with Girl gaga! Your individual stuffs excellent.
All the time care for it up!
Terrific knowledge Cheers.
Feel free to visit my homepage … https://oglaszam.pl/author/benito75981/
We offer you slot demo versions soo you willl know specifically
what you are signing up for.
Have a look at my web-site … kroddy.com
Medicament information sheet. Generic Name.
zofran rx
Some what you want to know about medicine. Read information here.
Our reviewer focused on the casino and located a wide range of slots, live dealer games, and poker tables readily vailable to all players.
Here is my blog homepage
Medicine information leaflet. What side effects can this medication cause?
trazodone
Some news about meds. Get information now.
Meds information leaflet. Brand names.
cost of propecia
Best about medication. Read here.
Я б недодумалса.
this, after all, provides up spice to the https://www.computerworks.gr/a-clean-simple-way-to-share-basic-updates-about-your-company/.
Drug information for patients. Short-Term Effects.
lyrica
All about medicament. Read now.
Hey! Do you know if they make any plugins to help with SEO?
I’m trying to get my blog to rank for some targeted keywords but I’m not seeing very good results.
If you know of any please share. Cheers!
It’s fantastic that you are getting thoughts from this
post as well as from our discussion made at this time.
Drug information leaflet. Drug Class.
pregabalin brand name
All trends of drug. Read here.
Medication information. Drug Class.
can i order bactrim
All what you want to know about drug. Read information here.
Great info. Lucky me I found your blog by accident (stumbleupon).
I have book marked it for later!
Meds information. Cautions.
rx zyban
Everything news about drugs. Read information here.
Hey would you mind stating which blog platform you’re working with?
I’m looking to start my own blog in the near future but I’m having a
tough time selecting between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design seems different then most blogs and I’m
looking for something completely unique.
P.S Sorry for getting off-topic but I had to ask!
SEO-копирайтинг помогает выводить сайты в топ поисковой выдачи с
помощью текстов.
Drug information sheet. Cautions.
norvasc generic
Everything information about medicines. Get information here.
lisinopril 40 mg prices
StrangerMeetup is a superb place if you want to meet Americans on-line.
Medicament information leaflet. Brand names.
levitra
Best news about meds. Read information here.
We created this platform so you can chat with strangers freed from value,
no catch in any way.
Meds information for patients. Long-Term Effects.
clomid medication
Actual what you want to know about drugs. Read information now.
Thank you for some other informative site.
The place else may I get that kind of information written in such
an ideal method? I have a venture that I’m simply now running on, and I’ve
been on the look out for such info.
Medicine information sheet. Effects of Drug Abuse.
strattera
Some information about meds. Get now.
Currently it seems like Movable Type is the preferred blogging platform out there right now.
(from what I’ve read) Is that what you’re using on your blog?
Drugs information. Effects of Drug Abuse.
cialis super active medication
All what you want to know about drug. Get now.
Pills information leaflet. Drug Class.
minocycline
Everything about pills. Read information here.
Drug prescribing information. Cautions.
cephalexin tablet
Some trends of pills. Get here.
Meds information leaflet. Short-Term Effects.
glucophage rx
Best news about medicines. Read information here.
Medication information for patients. What side effects can this medication cause?
strattera buy
Actual what you want to know about drugs. Get here.
Wow! After all I got a webpage from where I can genuinely get valuable data concerning
my study and knowledge.
can i order cheap finasteride online
Medicines information for patients. What side effects?
cialis soft
Best trends of drugs. Read here.
what is the generic of trazodone
Hmm it seems like your blog ate my first comment (it was extremely long) so I
guess I’ll just sum it up what I submitted and say, I’m thoroughly enjoying your blog.
I too am an aspiring blog writer but I’m still new to everything.
Do you have any recommendations for inexperienced blog writers?
I’d really appreciate it.
lisinopril without insurance
lisinopril vs losartan
cefixime mechanism of action
side effects of protonix
Medicine information for patients. Generic Name.
how to buy pregabalin
Best information about drugs. Get here.
Drugs information for patients. Long-Term Effects.
get stromectol
Actual trends of medicine. Get now.
how can i get lisinopril without prescription
how can i get cheap sildigra pills
Drug information sheet. What side effects?
levaquin generic
Best news about meds. Get information now.
http://wiki.luckcatchers.ru/index.php/%D0%A2%D1%80%D0%B0%D0%BD%D1%81%D1%84%D0%BE%D1%80%D0%BC%D0%B8%D1%80%D1%83%D0%B9%D1%82%D0%B5_%D1%81%D0%B2%D0%BE%D1%8E_%D1%80%D0%B5%D0%BA%D0%BB%D0%B0%D0%BC%D0%BD%D1%83%D1%8E_%D0%BA%D0%B0%D0%BC%D0%BF%D0%B0%D0%BD%D0%B8%D1%8E_%D1%81_%D0%BF%D0%BE%D0%BC%D0%BE%D1%89%D1%8C%D1%8E_%D1%8F%D1%80%D0%BA%D0%B8%D1%85_%D1%81%D0%B2%D0%B5%D1%82%D0%BE%D0%B4%D0%B8%D0%BE%D0%B4%D0%BD%D1%8B%D1%85_%D0%B4%D0%B8%D1%81%D0%BF%D0%BB%D0%B5%D0%B5%D0%B2
Medicine information leaflet. Cautions.
provigil
Actual about drug. Read now.
kopen sie saxenda De inhoud van generieke pillen en merkgeneesmiddelen is precies hetzelfde. Het enige verschil is de naam
Every weekend i used to go to see this website, for the reason that i want enjoyment,
as this this web page conations actually nice funny information too. https://drive.google.com/drive/folders/19AjVkKKtgwJuZohKxsya6PczTp7qel45
Drugs information. Short-Term Effects.
buying colchicine
Actual about medicine. Get now.
Pills information for patients. Effects of Drug Abuse.
where to get zoloft
All trends of medicine. Get here.
Medication information leaflet. Effects of Drug Abuse.
where can i get lisinopril
All trends of medicines. Read here.
Hurrah! Finally I got a blog from where I know how to actually obtain useful
data concerning my study and knowledge.
Incredible story there. What happened after?
Take care!
Yes! Finally something about 출장.
Pills prescribing information. Brand names.
buying lisinopril
Actual trends of medication. Read here.
Hey there! Do you know if they make any plugins to protect against hackers?
I’m kinda paranoid about losing everything I’ve worked hard on. Any recommendations?
Medicine prescribing information. What side effects can this medication cause?
minocycline medication
Actual about drugs. Get information here.
Medicines prescribing information. Brand names.
priligy otc
Some news about drugs. Get information now.
https://www.ottawaks.gov/profile/productcategory4/profile
Its such as you learn my mind! You appear to understand so much approximately
this, such as you wrote the ebook in it or something. I believe
that you simply could do with some % to pressure the message home a little bit, but instead of that, that is excellent blog.
An excellent read. I will certainly be back.
Wonderful beat ! I would like to apprentice while you amend your web site, how could i subscribe for
a blog web site? The account aided me a acceptable deal.
I had been a little bit acquainted of this your broadcast offered bright
clear concept
Medicine information sheet. Short-Term Effects.
eldepryl
Everything trends of medicine. Get now.
Hello, i think that i saw you visited my weblog so i came to go back the prefer?.I am trying to to find things to enhance
my site!I guess its good enough to make use of a few of your concepts!!
Medication information sheet. Short-Term Effects.
flagyl
All trends of medicine. Get now.
Medicament information. Brand names.
generic provigil
Everything what you want to know about meds. Get information here.
Altyazılı Pornoları izle
haktogel
susu4d
susu4d
Medication information for patients. Long-Term Effects.
amoxil cheap
Some trends of medicine. Read now.
Medicament prescribing information. Drug Class.
paxil
All what you want to know about drug. Read information here.
Medicament information sheet. Short-Term Effects.
get nolvadex
Everything what you want to know about medicines. Read information now.
You reported it really well!
My webpage – https://www.buyinmexico.com.mx/audio-post-type/
Pills information. Long-Term Effects.
zoloft generics
Some information about medicine. Read information here.
Hi are using WordPress for your site platform? I’m new to the blog world but
I’m trying to get started and create my own. Do you require any html
coding knowledge to make your own blog? Any help would
be really appreciated!
my web blog :: https://bestpremium.premium4best.eu/
bookmarked!!, I like your web site!
Hey this is kind of of off topic but I was wondering if blogs use
WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding skills so I
wanted to get advice from someone with experience. Any help would be enormously appreciated!
Drug information for patients. What side effects can this medication cause?
baclofen
Some what you want to know about medication. Read now.
You said that wonderfully!
Here is my homepage; betbuzz365 bet [https://psfstructuralengineering.com/hello-world/]
Drug information leaflet. What side effects can this medication cause?
colchicine prices
Everything information about meds. Get information now.
Medicines information sheet. What side effects can this medication cause?
tadacip
Actual about medicament. Read information here.
Drug information. Short-Term Effects.
priligy pill
Everything what you want to know about meds. Read here.
Amazing many of terrific material!
Have a look at my webpage; casino mcw (https://icesta.uns.ac.id/index.php/en/component/k2/item/27-image-5)
You said it very well.!
my website :: mcw casino (http://xn--sl5b7yiki42bca96y.xn--3e0b707e/0-itgn/bbs/board.php?bo_table=free&wr_id=49858)
Medication information leaflet. Brand names.
rx seroquel
Actual information about meds. Read now.
Drugs information for patients. What side effects?
generic nexium
Everything about medication. Get now.
Drugs information. Drug Class.
generic maxalt
Best news about drug. Get information now.
Medicament information for patients. Brand names.
valtrex
Best information about meds. Read now.
Medicine information. Short-Term Effects.
lisinopril price
Actual news about medicament. Read information here.
Heya i’m for the first time here. I found this
board and I find It truly useful & it helped me out a lot.
I hope to give something back and help others like you helped
me.
I am not positive where you’re getting your info, however good topic.
I must spend a while learning much more or understanding more.
Thank you for excellent info I used to be on the lookout
for this info for my mission.
All you got to do is enter a username and you are all set to have fun.
can i buy finasteride without insurance
can i order trazodone without rx
diltiazem bnf
It’s a cliché, but you get to see the world from the
eyes of another, without which wisdom is unimaginable.
Pills information for patients. Short-Term Effects.
singulair medication
All about medicines. Get here.
Drug prescribing information. What side effects?
valtrex without a prescription
Some trends of medicine. Get now.
Drugs prescribing information. Long-Term Effects.
cost viagra
Some about medicament. Get now.
I relish, cause I discovered just what I was looking for.
You’ve ended my four day long hunt! God Bless you man. Have a great day.
Bye
Medicines information leaflet. What side effects?
generic norpace
Actual news about medication. Get information now.
Pills information for patients. Cautions.
nexium
All what you want to know about medicines. Get here.
of course like your web-site however you need to test the spelling on quite a few of your posts. A number of them are rife with spelling problems and I to find it very bothersome to tell the truth nevertheless I’ll certainly come back again.
how to get generic trazodone tablets
what is diltiazem prescribed for
medicine prednisone 20mg tablets
diltiazem for afib
People usually are not at all times who they say they are so tread carefully.
buy tetracycline online
where to get cheap trazodone for sale
This is really interesting, You’re a very skilled blogger.
I have joined your feed and look forward to seeking more of your great post.
Also, I’ve shared your web site in my social networks!
Here is my website; https://vip2023.premium4best.eu/
Pills information leaflet. Short-Term Effects.
aurogra
Everything news about medicament. Get information here.
The platform will join you with a random stranger, and you can start chatting right away.
Pills information for patients. Generic Name.
valtrex
All news about meds. Read now.
Do you mind if I quote a few of your posts as long as I provide
credit and sources back to your website? My blog is in the very same niche as
yours and my users would genuinely benefit from some of the information you provide here.
Please let me know if this ok with you. Thanks a lot!
Wow, that’s what I was looking for, what a stuff!
present here at this blog, thanks admin of this website.
娛樂城
Drugs information sheet. Brand names.
motrin tablets
All information about medication. Read now.
I’m really inspired along with your writing talents as smartly as with the format
to your weblog. Is that this a paid subject or did you customize it yourself?
Either way keep up the nice high quality writing, it’s
uncommon to look a great blog like this one these days..
Drugs information leaflet. What side effects can this medication cause?
pregabalin brand name
Everything trends of medicine. Read information here.
casino hacks to win
Hi there! Someone in my Facebook group shared
this website with us so I came to give it a look.
I’m definitely enjoying the information. I’m book-marking and will be tweeting this to my followers!
Wonderful blog and great style and design.
Seriously a good deal of good tips!
Also visit my homepage https://kortarsfestmenyek.hu/a_szerzetes/
You remain protected and likewise on a safer side when you don’t engage in video
or audio calling.
I blog quite often and I really appreciate your information. This great article has really peaked my interest.
I am going to bookmark your site and keep checking for new information about once per
week. I opted in for your RSS feed too.
Thanks. Terrific stuff.
Also visit my blog post; https://fountaingatechurchofgod.com/index.php?option=com_k2&view=item&id=1:make-that-idea-your-life
An online live chat is a method to simulate a real-life chat, skilled on-line.
An intriguing discussion is definitely worth comment. I believe that
you should write more about this subject matter, it might not be a taboo matter but usually
people don’t talk about these issues. To the next! Kind regards!!
Medicines information sheet. What side effects can this medication cause?
finpecia
All news about medicines. Read now.
https://forum.zarobitchany.org/forum18/topic65898.html
Excellent blog here! Also your website loads up fast!
What host are you using? Can I get your affiliate
link to your host? I wish my web site loaded up as
fast as yours lol
A motivating discussion is worth comment. I think
that you ought to write more about this subject matter, it might
not be a taboo subject but usually folks don’t talk about these
topics. To the next! Cheers!!
Drugs information leaflet. Drug Class.
neurontin buy
Actual trends of pills. Read information now.
Hi there all, here every one is sharing these kinds of familiarity, thus it’s fastidious to read this blog,
and I used to go to see this blog daily.
If you want to take a good deal from this paragraph then you have to apply such strategies to your
won weblog.
Excellent blog right here! Additionally your web site so much up very fast!
What web host are you the usage of? Can I get your affiliate link in your host?
I wish my site loaded up as quickly as yours lol
I’m really loving the theme/design of your blog. Do you
ever run into any internet browser compatibility problems?
A few of my blog audience have complained about my website not operating correctly in Explorer but looks great in Firefox.
Do you have any recommendations to help fix this issue?
my web site http://maps.google.de/url?q=https://e-seksuolodzy.pl/
https://forum.cryptocurrency.tech/topic/668157-tsvetochnyy-ray-v-moskve-roskoshnye-kompozitsii-i-velikolepnye-aranzhirovki/
Drugs information sheet. Drug Class.
provigil
Everything about medicament. Get information now.
Drugs information leaflet. Effects of Drug Abuse.
finpecia
Best what you want to know about medicine. Read here.
I do believe all the concepts you have presented for your post.
They are very convincing and will definitely work.
Still, the posts are too short for beginners.
Could you please extend them a bit from subsequent time?
Thank you for the post.
Superb blog you have here but I was wondering if you knew of any discussion boards that cover
the same topics discussed here? I’d really love to be
a part of community where I can get advice from other experienced individuals
that share the same interest. If you have any suggestions, please
let me know. Cheers!
Drug information leaflet. What side effects can this medication cause?
lioresal no prescription
Some news about medication. Get now.
Magnificent web site. Lots of helpful info here.
I am sending it to a few buddies ans additionally sharing in delicious.
And naturally, thanks for your sweat!
Medicine prescribing information. Long-Term Effects.
rx ampicillin
Actual what you want to know about drugs. Get now.
Pills information sheet. Generic Name.
fluoxetine
All news about medicament. Get here.
It is the best time to make some plans for the future and it’s time to be happy.
I’ve read this post and if I could I desire to suggest you some interesting things or advice.
Maybe you could write next articles referring to this article.
I desire to read more things about it!
It’s a shame you don’t have a donate button! I’d certainly donate to this brilliant blog!
I suppose for now i’ll settle for book-marking and adding your RSS feed to my
Google account. I look forward to new updates and will share this site with my
Facebook group. Chat soon!
Right here is the perfect site for anyone who wants to understand
this topic. You know so much its almost tough to argue with you (not that I
really would want to…HaHa). You certainly put a new spin on a subject
that has been discussed for a long time. Excellent
stuff, just wonderful!
Meds information sheet. What side effects?
minocycline buy
Some about medicine. Read information here.
Medicines information for patients. Short-Term Effects.
generic viagra
Best news about medicines. Read information now.
accutane 20 mg accutane 30 mg coupon
Drugs information leaflet. Generic Name.
finpecia
Actual about medicines. Get now.
Good write-up. I absolutely appreciate this website.
Keep writing!
Can Accutane be used in combination with other acne medications? https://isotretinoinex.website/
Medicines information. What side effects can this medication cause?
paxil
Some information about medicine. Get information now.
This article will help the internet people for creating new web site or even a blog from start to
end.
Hey! This post couldn’t be written any better! Reading through this post reminds me of
my old room mate! He always kept talking about this.
I will forward this page to him. Fairly certain he will have a good read.
Thanks for sharing!
You’ve made your position extremely clearly..
my web blog … https://med-info-pharm24.top/prograf/
Medicament information leaflet. Effects of Drug Abuse.
fluoxetine cost
All what you want to know about medication. Read information here.
Good forum posts. Thank you!
Here is my blog :: https://med-info-pharm24.top/buy-actos/
All go to this site! I recommend it!jasminerThe miners are in stock in our warehouse and ready for shipment. Worldwide delivery.
Medicament information. Long-Term Effects.
lioresal price
Best information about medicament. Read information now.
You have made your position extremely nicely!.
Here is my webpage: https://stylebrideboutique.com/business-seminar/
Pills information leaflet. Effects of Drug Abuse.
eldepryl
Some trends of medicines. Read now.
Medicines information sheet. Short-Term Effects.
get retrovir
Actual about medication. Get here.
Hello just wanted to give you a quick heads up. The text in your post seem to be running
off the screen in Internet explorer. I’m not sure if this is a format
issue or something to do with browser compatibility but I figured I’d post to let you know.
The design and style look great though! Hope you get the problem resolved soon. Cheers
I’m not sure where you are getting your information, but good topic.
I needs to spend some time learning much more or understanding more.
Thanks for excellent info I was looking for this info for my mission.
Also visit my blog :: http://maps.google.td/url?q=https://e-seksuolodzy.pl/
For latest news you have to pay a quick visit web and on web I found this web site as a finest web page for hottest
updates.
Drugs prescribing information. Long-Term Effects.
can you get tadacip
All trends of medication. Get now.
diltiazem hcl
Wow, marvelous weblog structure! How lengthy have you been running a blog for?
you make blogging look easy. The total look of your site is great, as
smartly as the content material!
Medicine information for patients. Long-Term Effects.
can i order singulair
Everything trends of meds. Read now.
Drugs information sheet. What side effects?
aurogra online
Everything information about medicines. Get now.
Pills information. Short-Term Effects.
order retrovir
Everything trends of medicines. Read here.
Medicine information sheet. Brand names.
cost lisinopril
Some what you want to know about pills. Get here.
Meds prescribing information. Generic Name.
pregabalin
Some what you want to know about medication. Get here.
You actually revealed this effectively!
my blog Зерновой кофе (https://v-mig.ru/kofe-dallmayr-espresso-palazzo-v-zernah-1-kg/)
Medicament information sheet. Brand names.
where to get lopressor
Best about medicines. Read here.
Pills information. Cautions.
fosamax tablet
Some news about drugs. Get information here.
Amazing stuff, Thanks a lot!
Take a look at my website … http://www.chenzhipeng.com/bbs/home.php?mod=space&uid=441461&do=profile
Incredible a good deal of amazing knowledge.
Feel free to surf to my homepage: https://hikvisiondb.webcam/wiki/Here_Is_A_Fast_Manner_To_Resolve_An_Issue_With_My_Good_Site
Medicines information for patients. Long-Term Effects.
nolvadex
Some information about pills. Get information now.
You’ve made the point!
Also visit my web site; http://n-est.ru/bitrix/redirect.php?goto=http://inumoaruke.jp/newpage20060412.shtml
buy accutane online forum accutane 40 mg price in india
Medicine information leaflet. Cautions.
lopressor generic
Everything information about pills. Get information here.
Drug prescribing information. Short-Term Effects.
paxil
Best trends of medicines. Read information here.
сайт tehpromdata.ru
It is the best time to make some plans for the longer term and it is
time to be happy. I have learn this publish and if I may just I desire to recommend you some fascinating issues or suggestions.
Perhaps you can write next articles regarding this article.
I want to learn even more issues approximately it!
You expressed it terrifically!
Feel free to visit my site jhandi munda dice price – https://pastelink.net/0rvwx6ve –
Superb stuff, Appreciate it!
Also visit my blog crickex login india, https://demcra.com/r/Gaming/1120000_Login_to_your_personal_account_crickex,
With thanks! Very good information.
Here is my web blog: https://destiny-freedom-f1a.notion.site/Jogos-de-mesa-no-casino-realsbet-e123e1fc7dd7416e83d1d318793e7e19?pvs=4
Appreciate it, Plenty of facts.
Here is my web page – sts pl – https://list.ly/i/8830563,
Great facts Regards!
Also visit my webpage: https://band.us/band/91266633/intro
Meds information sheet. Cautions.
promethazine
All about medicament. Read here.
Good day! This is my first visit to your blog! We are a team
of volunteers and starting a new project in a community in the same niche.
Your blog provided us beneficial information to work on.
You have done a extraordinary job!
Also visit my webpage – http://maps.google.com.ai/url?q=https://tomasz-majewski-online.sm7.eu/
Drugs prescribing information. What side effects?
lyrica otc
Everything trends of meds. Read information now.
Thank you a bunch for sharing this with all of us you
really recognize what you’re talking about! Bookmarked.
Kindly also seek advice from my site =).
We could have a link exchange agreement between us
Hey would you mind stating which blog platform you’re working
with? I’m planning to start my own blog soon but I’m having a hard
time selecting between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design seems different then most
blogs and I’m looking for something unique.
P.S Apologies for getting off-topic but I had to ask!
Medicines information leaflet. What side effects can this medication cause?
buy generic zovirax
Best what you want to know about medicines. Get now.
Meds information sheet. Cautions.
can i order lasix
All information about medicine. Get information now.
Your ideas ɑre revolutionary! Thank you for challenging the status quо and inspiring us with yⲟur writing.
I am sure this article has touched all the internet people, its really really good piece of writing on building up new webpage.
Here is my page :: http://maps.google.co.zm/url?q=http://online-mniejszosci-seksualne.greatpremiumplace.eu/
Drug information leaflet. Long-Term Effects.
get promethazine
Actual trends of meds. Get now.
Good article. I’m experiencing a few of these issues as well..
I blog frequently and I seriously thank you for your information. The article has truly peaked my interest.
I will take a note of your website and keep checking
for new details about once per week. I opted in for your RSS feed as well.
my web blog: http://www.google.com.et/url?q=http://portal-kurs-seksu.greatpremiumplace.eu/
https://www.aiuextension.org/members/csgogambiling35/
I constantly spent my half an hour to read this webpage’s
content every day along with a cup of coffee.
Pills information sheet. Brand names.
lisinopril
Some trends of drugs. Get information now.
Fantastic info, Many thanks.
Feel free to visit my website … https://buy.paybis.com/click?pid=412&offer_id=1
What’s up friends, its impressive article on the
topic of cultureand fully explained, keep it up all the time.
This design is steller! You most certainly know how to keep a reader amused.
Between your wit and your videos, I was almost moved to start my own blog (well, almost…HaHa!)
Great job. I really loved what you had to say, and more than that, how you presented it.
Too cool!
My web site :: https://www.google.com.bh/url?q=http://kurs-seksu.greatpremiumplace.eu/
Meds prescribing information. What side effects can this medication cause?
lasix prices
Everything what you want to know about medicines. Get here.
I have been browsing on-line more than 3 hours nowadays, but I
by no means discovered any attention-grabbing article like
yours. It’s beautiful worth sufficient for me.
Personally, if all site owners and bloggers made good content material as you
did, the web might be a lot more useful than ever
before.
colchicine brand names
Nice weblog right here! Additionally your website so much up fast!
What web host are you using? Can I get your affiliate hyperlink on your
host? I want my site loaded up as quickly as yours lol
It’s an amazing paragraph in support of all the online visitors; they will obtain advantage from it I am sure.
Here is my blog: https://great.premium4best.eu/
cipro 250 mg
Drugs information. Long-Term Effects.
prozac generic
Everything trends of drug. Read now.
can you buy cheap prednisolone without insurance
Oh my goodness! Impressive article dude! Thank you, However I am encountering problems with your RSS.
I don’t understand why I can’t join it. Is there anybody else getting identical RSS problems?
Anyone who knows the solution will you kindly respond?
Thanx!!
Antibiotic medication
how to get prednisolone without dr prescription
can i purchase generic sildigra without prescription
Hi there colleagues, its great piece of writing concerning educationand entirely explained, keep it up all the time.
I absolutely love your blog and find the majority of your post’s
to be precisely what I’m looking for. Does one offer guest writers to write
content for you personally? I wouldn’t mind composing a
post or elaborating on a few of the subjects you write about here.
Again, awesome web site!
Feel free to visit my homepage :: http://images.google.co.th/url?q=http://mniejszosciseksualne-2023.greatpremiumplace.eu/
where to get finasteride without rx
Meds information leaflet. What side effects?
zovirax
Everything what you want to know about pills. Get now.
http://szmp-spb.ru/index.php/ru/component/k2/item/6-raspisanie-igr-pervogo-sostava
A fascinating discussion is worth comment. I believe that you ought to publish more on this issue, it
may not be a taboo matter but generally folks don’t speak about such subjects.
To the next! Best wishes!!
Here is my site http://cse.google.ba/url?q=http://mniejszosci-seksualne-portal.greatpremiumplace.eu/
colchicine tablets for sale
娛樂城
娛樂城
Medicines information. Effects of Drug Abuse.
levitra generics
Everything about medication. Read information here.
online prescription cefixime 400
Hello there! I know this is somewhat off topic but I was wondering which blog platform are you using
for this website? I’m getting fed up of WordPress because I’ve
had issues with hackers and I’m looking at
alternatives for another platform. I would be awesome if you could point me in the
direction of a good platform.
Medication information. Drug Class.
trazodone
All trends of meds. Read now.
Medicines information for patients. What side effects?
buy generic silagra
Everything about medicine. Get here.
Thank you! Terrific information!
Check out my web page – http://ttlink.com/ali6728219/all
get prednisolone without prescription
Hey very nice blog!
Drug information. Long-Term Effects.
sildigra without insurance
Actual what you want to know about meds. Get information here.
Drug information for patients. Long-Term Effects.
lyrica
Some what you want to know about medicament. Read now.
diltiazem ointment
Pills information sheet. Cautions.
trazodone online
Actual information about medicines. Get information here.
prednisone steroid for sale without a prescription
This info is priceless. When can I find out more?
I got this site from my pal who informed me on the topic of this site and at the moment this time I am browsing this site
and reading very informative posts here.
Medicine information for patients. Brand names.
colchicine
Best about drug. Read now.
doxycycline 200mg cheap
Hello! I could have sworn I’ve been to this website before but after going through many of
the articles I realized it’s new to me. Anyways, I’m certainly pleased I found it and I’ll be book-marking it and
checking back often!
my page; https://cse.google.com.hk/url?q=https://tomasz-majewski-online.sm7.eu/
Medicines information for patients. Generic Name.
ampicillin without dr prescription
Best information about medicines. Get here.
Drugs prescribing information. What side effects can this medication cause?
norvasc tablets
Best news about medication. Read here.
Meds information sheet. Brand names.
priligy
Actual trends of drugs. Read information here.
Pills information leaflet. Short-Term Effects.
sildigra pill
Best trends of pills. Read now.
Thank you for every other informative site. Where else may just I get that kind of info written in such a perfect method?
I have a challenge that I am just now working on, and I have been on the look out for such information.
Medicament information leaflet. Short-Term Effects.
levitra otc
Best what you want to know about medicine. Read information here.
My spouse and I stumbled over here coming from a different website and thought I might
as well check things out. I like what I see so i
am just following you. Look forward to finding out about your web page yet again.
Meds information for patients. Brand names.
neurontin without prescription
All about medication. Get information now.
You said this wonderfully.
Feel free to visit my blog post – http://groovaroo.com/question/pharmacy-methods-revealed/
Izzi casino
It’s amazing to pay a quick visit this site and reading the views of all mates concerning
this piece of writing, while I am also zealous of getting familiarity.
Medicament prescribing information. What side effects?
singulair
Best news about drugs. Get now.
Medicines prescribing information. Cautions.
norpace
Some what you want to know about medicines. Get here.
Medication information for patients. What side effects can this medication cause?
nolvadex medication
Best information about medicament. Read information now.
Medication information for patients. Generic Name.
promethazine brand name
All what you want to know about medicament. Get here.
Medicine information sheet. Brand names.
bactrim price
Best about medicine. Read information here.
cpa
یادگیری شیمی ،شیمی،مواد شیمی،عناصر
Medication prescribing information. What side effects can this medication cause?
silagra cheap
Everything about medicament. Get here.
buy arimidex without prescription
Hi there it’s me, I am also visiting this site on a regular basis,
this web page is really fastidious and the people are truly sharing nice thoughts.
Feel free to visit my web blog – https://images.google.co.ao/url?q=https://tomasz-majewski.sm7.eu/
Medicines information for patients. Short-Term Effects.
cephalexin online
Best news about medication. Read information here.
cefixime antibiotico ritirato
Drug information sheet. Short-Term Effects.
nolvadex
Best news about meds. Get here.
Особенно, если это не самая популярная
в обществе тема.
Medicines information. What side effects?
glucophage
Actual information about medicine. Get information here.
Drugs information. Generic Name.
cialis soft tablet
Best what you want to know about pills. Read now.
секс видео
Medication information. What side effects can this medication cause?
zovirax cost
Best trends of medication. Get now.
Meds information. Drug Class.
cialis super active
All what you want to know about medication. Get information here.
Could it be that our enemies believed that the sexual leaflets would just take the “fight” out of the American soldier? Take your chat on the go now with mobile chat mode.
Feel free to surf to my webpage; https://Illinoisbay.com/user/profile/4711540
Medication information sheet. Cautions.
cephalexin without a prescription
Best news about pills. Get information now.
get cipro online
Meds information. Generic Name.
lisinopril
Some trends of pills. Read information now.
Meds information. What side effects?
sildigra rx
Some news about medicines. Get here.
sildigra without prescription
Medicament information leaflet. What side effects?
zoloft no prescription
Actual news about medicines. Get information now.
Medicament information leaflet. What side effects?
neurontin
Actual information about medication. Get here.
Pills information. Effects of Drug Abuse.
flagyl medication
Everything news about medicines. Get information here.
I’d like to thank you for the efforts you have put in writing this
site. I’m hoping to see the same high-grade content by you in the future as well.
In fact, your creative writing abilities has motivated me to get my
own site now 😉
Pretty portion of content. I simply stumbled upon your blog and in accession capital to say that I get actually loved account your weblog posts.
Anyway I will be subscribing in your feeds and even I achievement you get
entry to consistently rapidly.
Here is my web-site http://cse.google.tm/url?q=https://tomasz-majewski-online.sm7.eu/
I know this if off topic but I’m looking into starting my own blog and was wondering
what all is required to get setup? I’m assuming having a blog like
yours would cost a pretty penny? I’m not very internet
smart so I’m not 100% positive. Any recommendations or advice would be greatly appreciated.
Cheers
Medication information for patients. Generic Name.
norpace pills
All information about medicament. Read now.
I really love your website.. Great colors & theme.
Did you build this web site yourself? Please reply back as I’m wanting to create my
own personal site and would like to learn where you got this from or exactly what the theme is named.
Many thanks!
Демонтаж стен Москва
Medication information leaflet. Short-Term Effects.
norvasc
Best what you want to know about medication. Get information now.
Perfectly expressed certainly! .
Here is my website – https://www.healthstoriesonline.com/home-family-home-security/pharmacy-is-certain-to-make-an-affect-in-your-corporation/
You can definitely see your expertise within the article you write.
The world hopes for more passionate writers such as you who are not afraid to say how they believe.
At all times go after your heart.
Таможенное оформление товаров из Китая – ASIANCATALOG
Китайские экспортеры безусловно знают, что грузы в Россию поставляются двумя методами, применительно официального таможенного оформления и скрытой схемой, более известной как карго. Какая разница между этими двумя типами импорта и на какие проблемы надо направить внимание при перевозки товара из Китая возможностями продавца.
Правильное таможенное оформление товаров из Китая – это таможенное оформление которое реализовывается на основании с таможенным законодательством ЕАЭС и также защищенной законом Российской Федерации.
Неофициальное таможенное оформление (карго) имеет высокие риски потери груза, не защищено законом и также не содержит правомерных документов.
Учитывая то, что Российская Федерация придает особое внимание таможенному оформлению, востребованность неофициального таможенного оформления (карго) снижается. Вместе с тем, в случае если товары из Китая будут доставлены на территорию России без сложностей, получатели встретятся с сложной ситуацией нереальности будущей продажи, в числе прочего и продажей товаров на ключевых маркетплейсах России. Поэтому мы рекомендуем участникам ВЭД предпочитать официальное таможенное оформление и игнорировать серое таможенное оформление.
Также, при отгрузке товара из Китая в крупные города и рынки России нужно направить внимание на вопросы логистики.
Специалисты по таможенному оформлению ASIANCATALOG обеспечивают поддержку малому и среднему бизнесу России и СНГ при доставке товаров из Китая, выступая в должности поставщика осуществляют таможенное оформление товаров из Китая c предоставлением официального пакета документов для свободной продажи на рынке и оказывают услуги по таможенному оформлению китайских товаров на основании договора услуги таможенного оформления, при импорте товаров из Китая под действующий внешнеэкономический контракт клиента.
Таможенное оформление китайских товаров – это профессиональный вид деятельности нашей компании, содержащий надежность и незамедлительное прохождение таможенного оформления с оплатой таможенных сборов и пошлин. Мы оказываем услуги таможенного оформления китайских товаров юр. лицам и физическим лицам, являющимися резидентами России и СНГ.
Medication information leaflet. Drug Class.
neurontin online
Everything news about medicine. Get here.
Medicine information sheet. Drug Class.
generic singulair
Actual what you want to know about drugs. Get now.
Having read this I believed it was rather informative.
I appreciate you taking the time and effort to put this informative article together.
I once again find myself personally spending a
significant amount of time both reading and leaving comments.
But so what, it was still worth it!
Medication information sheet. Drug Class.
propecia
All news about medicine. Get information here.
Nicely put, Regards.
Feel free to visit my web blog https://med-info-pharm24.top/ashwagandha-herb/
Medicament information for patients. What side effects can this medication cause?
cialis soft generic
Everything what you want to know about medicine. Get information here.
I’m not that much of a online reader to be honest but your sites really nice,
keep it up! I’ll go ahead and bookmark your site to come back later on. Many
thanks
Here is my website :: https://vip.premium4best.eu/
Medicine information. Short-Term Effects.
valtrex order
Everything about medicament. Read here.
Meds prescribing information. Effects of Drug Abuse.
sildigra buy
All trends of pills. Read here.
Medicines information. What side effects?
where to get zoloft
Some what you want to know about medicines. Read now.
buy prasugrel online
Medicine information sheet. Effects of Drug Abuse.
tadacip without dr prescription
Everything trends of medication. Read here.
diltiazem uses
Drugs prescribing information. Brand names.
celebrex medication
Actual trends of meds. Read information now.
Meds information leaflet. Effects of Drug Abuse.
synthroid
Actual trends of medicament. Read here.
buy real cleocin online
Medicine prescribing information. Drug Class.
amoxil order
Everything what you want to know about drug. Get information now.
This is a topic that’s close to my heart… Cheers!
Where are your contact details though?
Pills information. Cautions.
nolvadex
Some what you want to know about drug. Get information here.
where can i get generic finasteride online
Medication information. What side effects?
silagra
Actual news about drugs. Read information now.
Hello my friend! I want to say that this article is
awesome, nice written and include almost all vital infos.
I would like to peer more posts like this .
buy lisinopril with free samples
Howdy! Quick question that’s totally off topic. Do you know how to make
your site mobile friendly? My weblog looks weird when browsing from my iphone 4.
I’m trying to find a template or plugin that might be able to resolve this issue.
If you have any recommendations, please share.
Thank you!
Pills information for patients. Cautions.
lisinopril
Actual about medicament. Read now.
Drugs information for patients. Short-Term Effects.
effexor buy
Actual news about medicine. Read information here.
It’s very easy to find out any topic on web as compared to books, as I found this post
at this web page.
секс видео онлайн
where can i get prednisolone prices
kate last visited the https://my-pic.eu/ before its closure in 2020.
Medication information leaflet. Effects of Drug Abuse.
strattera cheap
Best trends of meds. Get information here.
how to buy generic lisinopril without prescription
https://youtu.be/aJgbtwfZfZg
Good day! Do you know if they make any plugins to help with Search Engine Optimization? I’m
trying to get my blog to rank for some targeted keywords but I’m not seeing very good
gains. If you know of any please share. Appreciate it!
Someone necessarily lend a hand to make severely posts I’d state.
That is the first time I frequented your website page and so
far? I surprised with the research you made to
create this particular publish extraordinary.
Wonderful job!
This post will help the internet visitors for setting
up new web site or even a weblog from start to end.
Hey I know this is off topic but I was wondering
if you knew of any widgets I could add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe
you would have some experience with something like this. Please let me know if you run into anything.
I truly enjoy reading your blog and I look forward to your new updates.
I think the admin of this web page is genuinely working hard
in support of his web site, as here every information is quality based data.
Hey there this is kinda of off topic but I was wanting to know if blogs use WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding skills so I wanted to get guidance from someone with experience.
Any help would be greatly appreciated!
All go to this site! I recommend it!Helium minerHelium miner. Miners are in stock in the USA. Worldwide delivery. The warranty for miners is 1 year.
can i buy colchicine price
codigo promocional 1xbet chile promo code bonus: 1xgift130 – vip bonus up to €/$130 welcome provide.
You’re so cool! I do not think I’ve read something like that before.
So nice to discover another person with a few original thoughts on this issue.
Really.. many thanks for starting this up. This website is one thing that’s needed
on the internet, someone with some originality!
I do not know whether it’s just me or if everyone else encountering problems
with your site. It appears as if some of the written text within your posts are running off the screen. Can somebody else please provide feedback and let me know
if this is happening to them too? This may be a issue with my
internet browser because I’ve had this happen previously.
Kudos
can you get cheap finasteride
Drug information leaflet. Cautions.
zovirax
Actual news about medicines. Get now.
Howdy, I do believe your site might be having internet browser compatibility problems.
When I look at your blog in Safari, it looks fine however, when opening in I.E., it’s
got some overlapping issues. I merely wanted to provide you with a quick
heads up! Apart from that, great site!
I have fun with, result in I found exactly what I was looking for.
You have ended my 4 day lengthy hunt! God Bless
you man. Have a great day. Bye
Valuable postings, Kudos.
My web site: crickex apk download, http://buntubi.com/culture/7-ans-au-senegal-merci-le-festa2h/,
With thanks! I appreciate it.
my web-site; betwarrior bono (https://bapzip.it/index.php?option=com_k2&view=item&id=25)
Hi! I could have sworn I’ve been to this website
before but after going through a few of the articles I realized it’s new
to me. Nonetheless, I’m certainly pleased I stumbled upon it and I’ll be
book-marking it and checking back often!
Protonix and bloating
Suppose traffic level increases to or above the level of 2019 over 9 million passengers but environmental standards aren’t tightened for the existing ro-pax vessels.
what is doxycycline used for
Thanks on your marvelous posting! I definitely enjoyed reading it, you might be a great author.
I will make certain to bookmark your blog and definitely
will come back very soon. I want to encourage that you continue your great posts, have a
nice evening!
В этом что-то есть. Благодарю Вас за помощь в этом вопросе, может я тоже могу чем то помочь?
финальные http://xn--80aeh5aeeb3a7a4f.xn--p1ai/forum/user/39744/ российской федерации и сюжета.
Thanks on your marvelous posting! I actually enjoyed reading it, you’re a great author.
I will make certain to bookmark your blog and
may come back at some point. I want to encourage
yourself to continue your great writing, have a nice day!
It contains 32 Screens with a distinct sort of UI. This template
consists of greater than 60 screens with very smooth animation that is consistent with Android and IOS.
Also on this template there are screens for monitoring the
alternate fee and the growth of bitcoin. Also, this template already
helps several languages: Italian, German and English.
This template for the travel booking app was created based mostly on the mistakes
and positive outcomes of large booking corporations. It should make it even simpler for Americans to journey with out the problem of
creating currency conversions or fumbling with an unmanned
ticket kiosk at a practice station that doesn’t acknowledge our out-of-date magnetic-stripe playing cards.
Previously, you had to collect your energy and overcome the
tremor of your voice earlier than making a name, but with the
arrival of chats, the world has modified and it has become simpler for
social phobias like me to live. But because of apps like Booking, Airbnb, Tripadvisor, resort
reservations and vacation planning have change into a lot easier.
This set features a template with a clean and person-pleasant design, which is so well-liked with all users of e-commerce
apps equivalent to ASOS, YOOX or Farfetch. This template will make well being
care simpler, as it’s going to bring patients and medical doctors closer together.
I’ll right away seize your rss feed as I can’t to find your e-mail subscription hyperlink
or e-newsletter service. Do you have any? Please permit me know in order that I may subscribe.
Thanks.
https://www.genious.blog/comment-bien-choisir-lextension-de-son-nom-de-domaine/ сотрудничает с вместе с всего из крупинка кот изящный немного считая от.
Medication prescribing information. Generic Name.
nexium order
Best what you want to know about medicines. Get information now.
Really loads of useful tips.
my web page: realsbet casino [https://www.melasma.kr/bbs/board.php?bo_table=free&wr_id=210017]
This post is in fact a nice one it assists new the web people, who are wishing
for blogging.
Это точно
коллег по работе в командирое селят в один номер инцест hardcore xxx порно секс https://www.josiahlewis.com/2020/03/18/hello-world/ sex pornhub vr full hd оргия orgy hd.
All go to this site! I recommend it!Helium minerHelium miner. Miners are in stock in the USA. Worldwide delivery. The warranty for miners is 1 year.
С этим я полностью согласен!
https://iron-fall.com/plumbings-health-benefits-revealed/ лучшие бесплатные игры!
Medicine information sheet. What side effects?
zoloft
Everything trends of drug. Read now.
Присоединяюсь. Так бывает.
many of the males are seen watching http://www.trade-echos.net/?p=1581.
Drug information. Short-Term Effects.
norpace rx
Actual trends of medicines. Get information here.
I’m really impressed together with your writing talents as neatly as
with the structure in your blog. Is that this a paid topic or did you customize it
your self? Anyway stay up the excellent high quality writing, it is rare to peer
a nice weblog like this one today..
Hiya! I know this is kinda off topic but I’d figured I’d ask.
Would you be interested in exchanging links or maybe guest authoring a blog
article or vice-versa? My blog goes over a lot of the same subjects as yours and I feel we could greatly benefit from each other.
If you are interested feel free to send me an e-mail. I look forward to hearing from
you! Awesome blog by the way!
Поздравляю, отличное сообщение
there are additionally issues about age verification for the https://kyourc.com/read-blog/98833 guild.
Бесподобное сообщение, мне очень нравится 🙂
in his https://www.spreadstraffic.com/broncos-running-backs-know-carries-may-be-week-to-week-riddle/ film, frankenpenis, bobbitt’s scars are on show.
Medicines information sheet. What side effects?
abilify
Best news about medication. Get information here.
Very nice post. I just stumbled upon your weblog and wished to say
that I have really loved browsing your weblog posts. In any case I’ll be subscribing to your feed
and I am hoping you write again very soon!
Рекомендую Вам посетить сайт, на котором есть много информации по этому вопросу.
сериал «ходячие мертвецы» выплеснулся в 2010 посевном сезоне, а уже в современном мире реально http://zvukiknig.net/index.php?subaction=userinfo&user=eguxod несколько,3.
Может быть.
there’s nothing ashamed about http://hublaw.co.kr/www//bbs/board.php?bo_table=free&wr_id=75770 addiction.
Pills information. Generic Name.
buy generic sildigra
Best information about medicine. Get here.
tuan88 slot
Tuan88 merupakan salah satu situs slot online terbaik di Indonesia di tahun 2023 yang memberikan tawaran, bonus, dan promosi menarik kepada para member.
hi!,I love your writing very much! proportion we communicate extra about your article on AOL?
I require an expert on this area to unravel my problem.
Maybe that’s you! Taking a look ahead to peer you.
Pills information. Effects of Drug Abuse.
how to get viagra
Actual trends of meds. Read information now.
Medicament information for patients. Cautions.
provigil
All news about drug. Get here.
colchicine probenecid brand name
Да, действительно. Так бывает.
у нас в виртуальном-маркете реально приобрести https://mmaster.kr.ua/тенденции-цвета-межкомнатных-дверей/.
efient
Medicament information for patients. What side effects?
nolvadex
Best trends of meds. Get here.
Я считаю, что Вы допускаете ошибку.
2 два техподдержка яндекс http://supermega.market.
Hi, i read your blog from time to time and i own a similar one and i was just curious if you get a lot of spam feedback?
If so how do you stop it, any plugin or anything you
can advise? I get so much lately it’s driving me crazy so any
support is very much appreciated.
This information is priceless. When can I find out
more?
Medicament information leaflet. Effects of Drug Abuse.
flagyl
Some what you want to know about medicament. Get information here.
Вы абсолютно правы. В этом что-то есть и мысль хорошая, поддерживаю.
все https://hainet.ru/view-article.php?article=bluesound-node-2-black&category=13.
Drugs information sheet. Long-Term Effects.
tadacip medication
Actual about drug. Read now.
All go to this site! I recommend it!Helium minerHelium miner. Miners are in stock in the USA. Worldwide delivery. The warranty for miners is 1 year.
Medicines information. Cautions.
order clomid
Some news about drug. Get now.
Hey very nice site!! Guy .. Excellent .. Superb ..
I will bookmark your site and take the feeds additionally?
I am happy to search out a lot of helpful info right here within the post, we need develop extra techniques on this regard, thanks for
sharing. . . . . .
First off I would like to say terrific blog! I had a quick question that I’d like to ask
if you do not mind. I was curious to find out how you center yourself and
clear your thoughts prior to writing. I’ve had a tough time clearing my
mind in getting my ideas out. I do enjoy writing however it just seems like the first 10 to 15 minutes
are lost just trying to figure out how to begin. Any ideas or hints?
Thank you!
I do not even understand how I ended up here, but I thought this
publish was once great. I don’t know who you are but definitely you are going to a famous blogger if you
are not already. Cheers!
Medicines information for patients. Drug Class.
zoloft without dr prescription
Some information about drug. Read information here.
Pills information sheet. What side effects?
get sildenafil
Some trends of meds. Get here.
Одной из таких является индивидуальная дрессировка собак. В таких условиях собака более охотно входит в воду. Характерной особенностью породы является длинный пушистый хвост с очёсами, который собака держит высоко, как флаг. Внешне бигль – крайне привлекательная средне-малая собака с фирменными висячими ушами, достающими до пасти. Необходимо словить тот момент, когда бигль практически готов съесть лакомство и сказать «фу», предложив ему лучшую альтернативу. Важно, чтобы лакомство пес получил и съел в положении лежа. Для этого терьера зовут к себе, произносят команду, поднимают игрушку или лакомство у него над головой. Для ее создания достаточно сколотить две широкие доски для чего подойдут толстые листа фанеры. Для исключения сомнительных лиц кандидаты также проходят испытание на детекторе лжи, а их прошлое тщательно проверяется. Для этого нужно, сидя рядом с ним и держа в руке его любимое лакомство, встать, подойти к собачьей лежанке и скомандовать “Место”. Для обеспечения безопасности они также осматривают все используемые для подъёма по реке Юкон ялики и вводят «Blue ticket» (синий билет), чтобы исключить проезд нежелательных лиц. Действуя по контракту в трёх территориях (Северо-Западные территории, Юкон и Нунавут) и восьми провинциях (Новая Шотландия, Остров Принца Эдуарда, Нью-Брансуик, Ньюфаундленд и Лабрадор, Манитоба, Саскачеван, Альберта и Британская Колумбия), она располагает местными отделениями полиции, служащие которых следят также и за соблюдением правил дорожного движения в дополнение к уголовным расследованиям. Её работа заключается в способствовании миру и безопасности в мире и укреплении международных усилий по поддержанию порядка в сотрудничестве с местными полицейскими службами стран, подверженных столкновениям или находящихся под угрозой столкновений. Индивидуальная работа с собаками.
НазначениеСлужит для ограничения
коммутационных и грозовых перенапряжений в системах СИП до 1 кВ.
Для однофазной ВЛ применяется один ограничитель, для трехфазной ВЛ — три ограничителя.
ХарактеристикаОграничитель перенапряжения — варисторного типа.
When I work, it’s easy, but it’s also hard to work. there are things you think are easy. there are times when you lie down because you think about it later, that’s easy. Sometimes when you first try, it’s difficult until you finish the job that you thought was easy. That’s why you think the work is easy, do it while it’s still early. to impress your boss. just like you did my friend, everything you do is beautiful. I’m just asking you, aren’t you having trouble with the site you made? because I’m struggling so this is what I did for a whole week. It’s funny to think that everything I said is true hehehe.
https://8mod.net/first/
This is really interesting, You’re a very skilled blogger.
I have joined your rss feed and look forward to seeking more of your wonderful post.
Also, I have shared your website in my social networks!
Medicament prescribing information. Effects of Drug Abuse.
maxalt cheap
Some what you want to know about drug. Get now.
Pills information. Effects of Drug Abuse.
avodart cost
Everything information about drugs. Read now.
Fantastic tips Thanks!
Here is my web site :: https://partner.bybit.com/b/CTLDPSCQ16906
Remarkable things here. I am very satisfied to look your
post. Thanks so much and I am taking a look ahead to contact you.
Will you kindly drop me a e-mail?
Do you have any video of that? I’d love to find out some
additional information.
Medicines prescribing information. What side effects can this medication cause?
nolvadex
Actual news about medicines. Get information here.
Meds information leaflet. Drug Class.
buy cordarone
Some what you want to know about pills. Get information now.
Drugs information sheet. Long-Term Effects.
viagra soft
Some information about medicine. Read information here.
Drugs information leaflet. Generic Name.
fluoxetine
Some information about meds. Get now.
Браво, отличная идея и своевременно
a blockchain privacy solutions tumbler is a service that mixes your coins with different people’s coins.
My developer is trying to persuade me to move to
.net from PHP. I have always disliked the idea because of the costs.
But he’s tryiong none the less. I’ve been using WordPress on a number of websites for about a year and am concerned about switching
to another platform. I have heard good things about blogengine.net.
Is there a way I can import all my wordpress content into it?
Any help would be greatly appreciated!
Medicament information. What side effects?
strattera rx
Everything what you want to know about medicament. Read now.
Pills information for patients. Effects of Drug Abuse.
levitra
All trends of drugs. Get information here.
I got this website from my buddy who shared with me about this web site and at the moment this time I am
visiting this web site and reading very informative articles at this place.
It’s remarkable to visit this website and reading the views of all mates regarding this
piece of writing, while I am also keen of getting experience.
Drugs information. Generic Name.
norvasc rx
All what you want to know about medication. Read here.
Medication information sheet. Effects of Drug Abuse.
propecia
Actual trends of pills. Get here.
總統大選
總統大選
2024總統大選懶人包
2024總統大選將至,即中華民國第16任總統、副總統選舉,將在2024年1月13日舉行!這一天也是第11屆立法委員選舉的日子,選舉熱潮將一起席捲全台!這次選舉將使用普通、直接、平等、無記名、單記、相對多數投票制度,讓每位選民都能以自己的心意選出理想的領導者。
2024總統大選日期
2024總統大選日期:2024年1月13日 舉行投票,投票時間自上午8時起至下午4時止後進行開票。
2024總統大選民調
連署截止前 – 賴清德 VS 侯友宜 VS 柯文哲
調查來源 發布日期 樣本數 民進黨
賴清德 國民黨
侯友宜 民眾黨
柯文哲 不表態
TVBS 2023/05/19 1444 27% 30% 23% 20%
三立 2023/05/19 1080 29.8 29.2% 20.8% 20.2%
聯合報 2023/05/23 1090 28% 24% 22% 27%
亞細亞精準數據 2023/05/20 3511 32.3% 32.2% 32.1% 3.4%
放言 2023/05/26 1074 26.6% 24.7% 21.1% 27.6%
正國會政策中心 2023/05/29 1082 34% 23% 23% 20%
ETtoday 2023/05/29 1223 36.4% 27.7% 23.1% 12.8%
美麗島電子報 2023/05/29 1072 35.8% 18.3% 25.9% 20%
2024總統大選登記
賴清德 – 民主進步黨
2023年3月15日,賴清德在前屏東縣縣長潘孟安的陪同下正式登記參加2024年民進黨總統提名初選。
2023年3月17日,表定初選登記時限截止,由於賴清德為唯一登記者,因此自動成為該黨獲提名人。
2023年4月12日,民進黨中央執行委員會議正式公告提名賴清德代表民主進步黨參與本屆總統選舉。
侯友宜 – 中國國民黨
2023年3月22日,國民黨召開中央常務委員會,會中徵詢黨公職等各界人士意見,無異議通過將由時任黨主席朱立倫以「徵召」形式產生該黨總統候選人之決議。
2023年5月17日,國民黨第21屆中常會第59次會議正式通過徵召侯友宜代表中國國民黨參與本屆總統選舉。
柯文哲 – 台灣民眾黨
2023年5月8日,柯文哲正式登記參加2024年民眾黨總統提名初選。
2023年5月9日,表定初選登記時限截止,由於柯文哲為唯一登記者,因此自動成為該黨獲提名人。
2023年5月17日,民眾黨中央委員會正式公告提名柯文哲代表台灣民眾黨參與本屆總統選舉。
2023年5月20日,召開宣示記者會,發表參選宣言。
Medicines information for patients. What side effects?
zoloft
Best what you want to know about drugs. Read here.
This piece of writing is truly a good one it assists new web users, who are wishing in favor of blogging.
Drug information sheet. Generic Name.
propecia pill
All trends of drug. Read information now.
I know this web page gives quality depending articles and other material, is there any other site which gives these kinds of things in quality?
Medication information for patients. What side effects?
zyban
Some about drug. Get information here.
Good day! I could have sworn I’ve visited this blog before
but after looking at many of the articles I realized it’s new to me.
Anyhow, I’m definitely happy I discovered it and I’ll be bookmarking it and checking back often!
Here is my blog – car parts .com
If you desire to take a good deal from this piece of writing then you
have to apply these techniques to your won website.
Medicine information for patients. What side effects can this medication cause?
flibanserina
Some news about medicine. Read information here.
I am regular visitor, how are you everybody? This article posted at this website is actually fastidious.
долго вы будите искать такого чуда
redtube is yours – your property of movies http://www.sosmatilda.com/all-service-list/dios-pan/.
Thank you for every other great article. Where else may anybody get
that type of information in such a perfect approach of writing?
I’ve a presentation subsequent week, and I’m on the search for such info.
Medicines information for patients. Short-Term Effects.
order neurontin
All trends of drugs. Read here.
Hello there! I know this is kinda off topic but I was wondering if you knew where I could get a captcha plugin for my
comment form? I’m using the same blog platform as yours and I’m
having problems finding one? Thanks a lot!
Medicine information. Long-Term Effects.
baclofen
Best news about pills. Get information now.
Medicine information for patients. Cautions.
zithromax generics
Actual what you want to know about medicines. Get information now.
Medication information. Drug Class.
clomid buy
Best what you want to know about medicines. Get information now.
Meds information for patients. Effects of Drug Abuse.
motrin
Actual news about medication. Get here.
Hmm is anyone else encountering problems with the pictures on this blog loading?
I’m trying to find out if its a problem on my end or if it’s the
blog. Any responses would be greatly appreciated.
Medicament information. Long-Term Effects.
cialis soft
All trends of medicines. Get information here.
certainly like your web-site however you need to check the spelling on several of your posts.
Several of them are rife with spelling problems and I to find it very bothersome to tell the reality however I will definitely come
back again.
Drugs information sheet. Brand names.
propecia
Best information about drug. Get information here.
I am curious to find out what blog system you happen to be
working with? I’m having some minor security issues with my latest website and I’d like to find something more
safeguarded. Do you have any solutions?
of course like your web-site however you need to test the spelling on quite a few of your posts.
A number of them are rife with spelling problems and I find it very troublesome to inform the truth however I will definitely come again again.
Hi there! Would you mind if I share your blog with my twitter group?
There’s a lot of people that I think would really enjoy your
content. Please let me know. Thank you
You ought to be a part of a contest for one of the most useful
websites on the web. I most certainly will highly recommend this web site!
Medication information for patients. What side effects?
tadacip
Everything information about meds. Read information now.
Medicine information for patients. What side effects can this medication cause?
buy generic norvasc
Some trends of pills. Get here.
Unquestionably consider that that you said. Your favourite justification seemed to be on the
web the simplest thing to be mindful of. I say
to you, I certainly get annoyed at the same time as folks consider worries that
they plainly do not know about. You managed to hit the
nail upon the highest and defined out the whole thing with no
need side-effects , other folks could take a signal.
Will probably be back to get more. Thank you
Heya i am for the first time here. I came across this board
and I find It really useful & it helped me
out much. I hope to give something back and help others like you
helped me.
Pills information for patients. What side effects can this medication cause?
order pregabalin
Best information about medication. Read information now.
Somebody necessarily lend a hand to make critically posts I might
state. This is the very first time I frequented your web page and up
to now? I surprised with the analysis you made to create this particular
submit incredible. Great job!
Meds prescribing information. Cautions.
pregabalin
Actual information about pills. Get information here.
Pills prescribing information. Cautions.
lisinopril
Everything what you want to know about medicine. Get now.
娛樂城的崛起:探索線上娛樂城和線上賭場
近年來,娛樂城在全球范圍內迅速崛起,成為眾多人尋求娛樂和機會的熱門去處。傳統的實體娛樂城以其華麗的氛圍、多元化的遊戲和奪目的獎金而聞名,吸引了無數的遊客。然而,隨著科技的進步和網絡的普及,線上娛樂城和線上賭場逐漸受到關注,提供了更便捷和多元的娛樂選擇。
線上娛樂城為那些喜歡在家中或任何方便的地方享受娛樂活動的人帶來了全新的體驗。通過使用智能手機、平板電腦或個人電腦,玩家可以隨時隨地享受到娛樂城的刺激和樂趣。無需長途旅行或昂貴的住宿,他們可以在家中盡情享受令人興奮的賭博體驗。線上娛樂城還提供了各種各樣的遊戲選擇,包括傳統的撲克、輪盤、骰子遊戲以及最新的視頻老虎機等。無論是賭徒還是休閒玩家,線上娛樂城都能滿足他們各自的需求。
在線上娛樂城中,娛樂城體驗金是一個非常受歡迎的概念。它是一種由娛樂城提供的獎勵,玩家可以使用它來進行賭博活動,而無需自己投入真實的資金。娛樂城體驗金不僅可以讓新玩家獲得一個開始,還可以讓現有的玩家嘗試新的遊戲或策略。這樣的優惠吸引了許多人來探索線上娛樂城,並提供了一個低風險的機會,
Drugs prescribing information. Long-Term Effects.
can i buy viagra
All about pills. Read information now.
Drugs information for patients. Drug Class.
lisinopril
Some about medicines. Read information here.
I know this site provides quality dependent posts and additional data,
is there any other website which gives these kinds of things
in quality?
Medicines information. Cautions.
provigil buy
Some trends of meds. Read here.
Thanks designed for sharing such a good thinking, post is nice,
thats why i have read it fully
This is the right site for everyone who would like to find out about this topic.
You realize so much its almost hard to argue with you (not that
I personally will need to…HaHa). You certainly put a new spin on a subject that has been written about for years.
Excellent stuff, just excellent!
my page: https://spisorganizacji.eu/
Hello! This is kind of off topic but I need some advice from an established blog.
Is it hard to set up your own blog? I’m not very techincal but I can figure things out
pretty fast. I’m thinking about making my own but I’m not sure
where to begin. Do you have any points or suggestions? With thanks
My blog http://clients1.google.dz/url?q=https://katalogfirm24.eu/
Medicine information for patients. Short-Term Effects.
finpecia for sale
Everything what you want to know about medicines. Get now.
Hurrah! Finally I got a website from where I can really take useful information concerning my study and knowledge.
My brother suggested I would possibly like this blog. He was once entirely right.
This submit truly made my day. You cann’t believe simply how a lot time
I had spent for this info! Thanks!
sildalist generic price
If you are going for finest contents like I do, simply pay a visit this
web site daily because it offers feature contents, thanks
Keep this going please, great job!
Hey! I know this is kinda off topic but I’d figured I’d ask.
Would you be interested in trading links or maybe guest authoring a
blog article or vice-versa? My blog goes over a lot of the same topics as
yours and I believe we could greatly benefit from each other.
If you might be interested feel free to shoot me an email.
I look forward to hearing from you! Great
blog by the way!
Check out my blog :: https://www.google.hr/url?q=https://katalogfirm24.eu/
Medicament information for patients. Brand names.
colchicine
Best what you want to know about drugs. Get now.
We’re a gaggle of volunteers and opening a brand new scheme in our community.
Your site offered us with helpful information to work on. You have done an impressive task
and our entire community will likely be thankful to you.
Spot on with this write-up, I truly feel this website
needs a great deal more attention. I’ll probably
be back again to read through more, thanks for the advice!
Also visit my website :: http://superpremium2.premium4best.eu/
If some one wishes expert view on the topic of running a blog then i propose him/her to visit this website, Keep up
the fastidious work.
my homepage; https://spisfirmonline.eu/
Medicines information sheet. Cautions.
norvasc
Some information about drug. Get here.
Medicines information sheet. Cautions.
nexium brand name
All information about medicament. Read now.
Drug information sheet. Short-Term Effects.
zithromax
Everything trends of medicines. Get here.
Can I just say what a relief to discover someone that really understands what they are
discussing online. You actually realize how to bring an issue to light
and make it important. More people really need to read this and understand this side of the
story. I can’t believe you’re not more popular given that you certainly possess the gift.
My web site – https://katalogfirm24.eu
Fastidious answers in return of this issue with firm arguments and explaining all about
that.
Also visit my website: https://we.riseup.net/gobellbhnv
Link exchange is nothing else except it is only placing the other person’s web site link on your page at proper place and other person will also
do similar in favor of you.
Check out my site https://designworkshop.uk/?URL=https://spisfirmonline.eu/
Drug information sheet. What side effects?
retrovir no prescription
Best about medication. Read information here.
I think the admin of this web site is really working hard for his site, since here
every information is quality based data.
Drugs prescribing information. Effects of Drug Abuse.
cialis soft price
Everything what you want to know about pills. Read here.
娛樂城
娛樂城的崛起:探索線上娛樂城和線上賭場
近年來,娛樂城在全球范圍內迅速崛起,成為眾多人尋求娛樂和機會的熱門去處。傳統的實體娛樂城以其華麗的氛圍、多元化的遊戲和奪目的獎金而聞名,吸引了無數的遊客。然而,隨著科技的進步和網絡的普及,線上娛樂城和線上賭場逐漸受到關注,提供了更便捷和多元的娛樂選擇。
線上娛樂城為那些喜歡在家中或任何方便的地方享受娛樂活動的人帶來了全新的體驗。通過使用智能手機、平板電腦或個人電腦,玩家可以隨時隨地享受到娛樂城的刺激和樂趣。無需長途旅行或昂貴的住宿,他們可以在家中盡情享受令人興奮的賭博體驗。線上娛樂城還提供了各種各樣的遊戲選擇,包括傳統的撲克、輪盤、骰子遊戲以及最新的視頻老虎機等。無論是賭徒還是休閒玩家,線上娛樂城都能滿足他們各自的需求。
在線上娛樂城中,娛樂城體驗金是一個非常受歡迎的概念。它是一種由娛樂城提供的獎勵,玩家可以使用它來進行賭博活動,而無需自己投入真實的資金。娛樂城體驗金不僅可以讓新玩家獲得一個開始,還可以讓現有的玩家嘗試新的遊戲或策略。這樣的優惠吸引了許多人來探索線上娛樂城,並提供了一個低風險的機會,
Drug information leaflet. Short-Term Effects.
zovirax
Actual trends of drug. Get information here.
Thanks for sharing such a nice thought, piece of writing is
good, thats why i have read it completely
Despite this, forty seven states are trying to move laws making it tougher to
vote, claiming that they’re doing it to keep away from the notion of fraud.
They’re doing it as a result of there’s cash in it.
Finally, what may be most frustrating about all of that is that
the electronic platforms hosting this fraud, from Facebook and Twitter to eBay, seem to
be doing nearly nothing about it. While the No.
2 member of the Disinformation Dozen often is the perennially sorry excuse
and lengthy established baby-killer Robert Kennedy Jr., the third slot belongs to Ty
& Charlene Bollinger. The Disinformation Dozen could dominate false
claims circulating on social media, but they are
removed from alone. So are many of the others in the Disinformation Dozen. Right now, automobile sharing exists in a whole lot of cities throughout
greater than a dozen international locations, with extra doubtless
to return. The automotive isn’t roadworthy yet since a hybrid engine (made of metallic) still has be designed, not to mention safety assessments must be carried
out. A study carried out by the University of Virginia found that of the highest one hundred fifty applications on Facebook,
90 p.c had been given entry to information they didn’t want in order for the app
to perform.
I delight in, cause I found just what I used to be taking a look for.
You’ve ended my four day lengthy hunt! God Bless you man. Have a nice day.
Bye
Pills information for patients. What side effects can this medication cause?
buy generic flagyl
Actual what you want to know about medicine. Read information here.
Medicament information for patients. Drug Class.
levitra
Some what you want to know about medicine. Get now.
Hi there! I’m at work browsing your blog from my new apple iphone!
Just wanted to say I love reading through your
blog and look forward to all your posts! Carry on the great
work!
Что предлагает сервис Kraken? Бесперебойно функционирующая торговая платформа в сети tor.
Разные предложения от лучших продавцов этой
страны и ближайшегоближнего
зарубежья. На ресурсе есть моментальный обменник, с помощью которого производятся сиюминутные обмены для покупки того товара, который нравится тебе.
Самая сильная и несокрушимая защита от проникновений и атак будет приятным дополнением к без
того отличной безопасности и превосходной анонимности.
Забудь про hydra с ее нерабочими официальными сайтами –
заходи на Кракен https://xn--krken-ucc.com .
i always dreamed about being stranded on a desert island until it actually happened mortal behind the window was a reflection that only instilled fear
Hello to all, the contents present at this website are truly remarkable for people experience,
well, keep up the nice work fellows.
Also visit my homepage https://www.google.com.cu/url?q=https://katalogfirm24.eu/
Drugs prescribing information. Effects of Drug Abuse.
norvasc cheap
Some trends of medication. Read information here.
Medicines information leaflet. Generic Name.
rx flagyl
All about drug. Read here.
Drug information. Brand names.
avodart
Everything trends of medication. Get here.
Medicines information sheet. Long-Term Effects.
generic xenical
Everything trends of drugs. Read here.
Medicine information for patients. What side effects can this medication cause?
zovirax
Some trends of pills. Get here.
Very good post. I’m facing many of these issues as well..
Also visit my web-site :: https://progressiveintl.com/?URL=https://spisorganizacji.eu/
Hi! Someone in my Facebook group shared this website with us
so I came to look it over. I’m definitely loving the information.
I’m book-marking and will be tweeting this to my followers!
Excellent blog and great style and design.
Here is my web-site … https://www.demilked.com/author/sarrecpxty/
Wow, awesome blog layout! How long have you been blogging
for? you make blogging look easy. The overall look of your web site is wonderful, as well
as the content!
Medicine information sheet. Brand names.
order zoloft
Best trends of medicament. Read information here.
Pills information leaflet. What side effects can this medication cause?
buying paxil
Everything about medicament. Get information here.
I’ve been browsing online greater than three hours nowadays, but I by no means found any fascinating article like yours.
It is beautiful value enough for me. In my opinion, if all website owners and bloggers made just right content as you probably did, the net will probably be much more
helpful than ever before.
If some one wishes expert view concerning running a blog then i suggest him/her to pay a
visit this blog, Keep up the good job.
Drug information. Effects of Drug Abuse.
neurontin tablet
All information about medication. Get now.
Meds information sheet. Brand names.
zofran
All trends of medicines. Get information here.
Drugs prescribing information. What side effects can this medication cause?
buy generic cordarone
Best information about meds. Get here.
you are in reality a good webmaster. The site loading pace is amazing.
It seems that you’re doing any unique trick. Furthermore,
The contents are masterwork. you’ve done a magnificent job
on this subject!
I am really enjoying the theme/design of your website. Do you ever run into any browser compatibility issues?
A handful of my blog readers have complained about my blog not operating correctly in Explorer
but looks great in Chrome. Do you have any recommendations to help
fix this problem?
My relatives always say that I am wasting my time here at net, except I know I am getting experience all the time by reading such fastidious
articles or reviews.
Feel free to surf to my web page: https://clients1.google.com.ag/url?q=https://katalogfirm24.eu/
I have read so many articles or reviews regarding the blogger lovers but
this paragraph is actually a good post, keep it up.
Medicine information sheet. Short-Term Effects.
can i order nolvadex
All news about medicine. Read here.
My partner and I stumbled over here by a different web
page and thought I should check things out.
I like what I see so i am just following you.
Look forward to looking into your web page for a second time.
Howdy! I could have sworn I’ve been to this blog before but after browsing through some of the post
I realized it’s new to me. Anyhow, I’m definitely happy I found it and I’ll be book-marking and checking back often!
Here is my blog – https://diigo.com/0t2tb0
Medication information. Short-Term Effects.
minocycline tablets
Best news about meds. Get information here.
Drug information for patients. Generic Name.
flagyl
Everything news about meds. Get information here.
Heya i’m for the first time here. I found this
board and I find It really useful & it helped me out much.
I hope to give something back and aid others like you aided me.
My blog post https://starclass.org/?URL=https://firmowykatalog.eu/
you have a gambling problem.
Also visit my website; yrmab.losblogos.com
I do accept as true with all the ideas you have
introduced on your post. They’re very convincing and can certainly work.
Nonetheless, the posts are too short for novices.
May you please prolong them a bit from next
time? Thanks for the post.
Thanks very nice blog!
My page https://firmowykatalog.eu/
Pills information leaflet. Drug Class.
can i get paxil
Actual what you want to know about medicament. Get information now.
Drug information. Brand names.
fluoxetine
Some news about medicine. Get information here.
Drug prescribing information. Generic Name.
cheap motrin
Actual trends of medication. Get information now.
娛樂城推薦
娛樂城的崛起:探索線上娛樂城和線上賭場
近年來,娛樂城在全球范圍內迅速崛起,成為眾多人尋求娛樂和機會的熱門去處。傳統的實體娛樂城以其華麗的氛圍、多元化的遊戲和奪目的獎金而聞名,吸引了無數的遊客。然而,隨著科技的進步和網絡的普及,線上娛樂城和線上賭場逐漸受到關注,提供了更便捷和多元的娛樂選擇。
線上娛樂城為那些喜歡在家中或任何方便的地方享受娛樂活動的人帶來了全新的體驗。通過使用智能手機、平板電腦或個人電腦,玩家可以隨時隨地享受到娛樂城的刺激和樂趣。無需長途旅行或昂貴的住宿,他們可以在家中盡情享受令人興奮的賭博體驗。線上娛樂城還提供了各種各樣的遊戲選擇,包括傳統的撲克、輪盤、骰子遊戲以及最新的視頻老虎機等。無論是賭徒還是休閒玩家,線上娛樂城都能滿足他們各自的需求。
在線上娛樂城中,娛樂城體驗金是一個非常受歡迎的概念。它是一種由娛樂城提供的獎勵,玩家可以使用它來進行賭博活動,而無需自己投入真實的資金。娛樂城體驗金不僅可以讓新玩家獲得一個開始,還可以讓現有的玩家嘗試新的遊戲或策略。這樣的優惠吸引了許多人來探索線上娛樂城,並提供了一個低風險的機會,
Superb forum posts With thanks.
my site: http://water.vouvstudio.com/bbs/board.php?bo_table=free&wr_id=394203
Why users still make use of to read news papers when in this technological world the whole
thing is accessible on web?
Pills information for patients. Generic Name.
zithromax otc
Best news about medication. Get information here.
Hey there! Someone in my Myspace group shared this website
with us so I came to check it out. I’m definitely loving the information. I’m book-marking and will be tweeting this to my followers!
Outstanding blog and wonderful style and design.
Woah! I’m really loving the template/theme of this website.
It’s simple, yet effective. A lot of times it’s hard to get that “perfect balance” between superb usability and visual appeal.
I must say that you’ve done a great job with this. In addition, the blog
loads super fast for me on Internet explorer.
Excellent Blog!
Medicines information leaflet. Drug Class.
generic ampicillin
All what you want to know about medication. Get here.
levaquin economico online
Hello there! I could have sworn I’ve been to this website before but after browsing through some of the
post I realized it’s new to me. Anyways, I’m definitely delighted I found it and I’ll be book-marking and checking back frequently!
These are truly impressive ideas in on the topic of blogging.
You have touched some good factors here. Any way keep up wrinting.
It’s not my first time to visit this site, i am visiting this
website dailly and take pleasant facts from here every day.
Medicines information. Short-Term Effects.
mobic
Best trends of meds. Get here.
Sobresaliente publicación, también puedes curiosear mi tienda
online de colchones y almohadas a buen costo, todo para el sueño reparador, camas,
sábanas, somieres, cobertores, edredones, colchones baratos y más, revisa mi sitio
web colchones tiendas.
Drug information sheet. Cautions.
amoxil without a prescription
All trends of medicine. Read information here.
You expressed it superbly.
my homepage … aydın escort – https://forum.inos.at/profile.php?id=57774,
Does your blog have a contact page? I’m having trouble locating it but, I’d like to shoot you an email.
I’ve got some recommendations for your blog you might be interested in hearing.
Either way, great blog and I look forward to seeing
it improve over time.
Meds prescribing information. Long-Term Effects.
lyrica order
Some news about pills. Get now.
I’m gone to tell my little brother, that he
should also visit this web site on regular basis
to get updated from hottest news update.
Drug information sheet. Brand names.
can i order cialis soft
Best news about medication. Get information now.
Medicines prescribing information. What side effects can this medication cause?
tadacip brand name
All trends of pills. Read here.
It’s in reality a nice and helpful piece of info.
I’m glad that you simply shared this helpful info with us.
Please stay us up to date like this. Thank you for sharing.
my blog post – basement finishing canton
Medicine information leaflet. Cautions.
motrin
Everything trends of drugs. Get now.
Unquestionably believe that which you stated.
Your favorite justification seemed to be
on the internet the easiest thing to be aware of.
I say to you, I definitely get irked while people think
about worries that they plainly do not know about. You managed to hit the
nail upon the top as well as defined out the whole thing without having side-effects ,
people can take a signal. Will probably be back to get more.
Thanks
Medicines information leaflet. Cautions.
zoloft
Some news about drugs. Get here.
Thanks designed for sharing such a pleasant thought, paragraph is pleasant, thats
why i have read it entirely
Drug information for patients. Cautions.
avodart
All news about drugs. Read now.
Just want to say your article is as amazing. The clarity for
your post is simply excellent and i could assume you are a professional
in this subject. Well together with your permission let me to take hold of your RSS
feed to keep up to date with approaching post. Thanks one
million and please continue the gratifying work.
Medicines information sheet. Short-Term Effects.
cialis soft
Everything about medicament. Read information here.
Medication information for patients. Generic Name.
stromectol otc
Some trends of pills. Get now.
Medicine information for patients. Generic Name.
zyban
Everything trends of medicine. Get here.
Дуже крутий сервіс із продажу проксі! Всім рекомендую!proxies
Drugs information for patients. Brand names.
singulair
Best news about medication. Get information now.
Medicines information sheet. Cautions.
avodart generics
All what you want to know about medication. Read now.
These are really wonderful ideas in about blogging.
You have touched some nice points here. Any way keep up wrinting.
Drug prescribing information. Long-Term Effects.
neurontin cheap
Everything about meds. Get now.
Drug information. What side effects can this medication cause?
lioresal
Some information about drug. Get now.
You’re so awesome! I don’t suppose I have read through something like that before.
So wonderful to find somebody with genuine thoughts on this issue.
Seriously.. many thanks for starting this up.
This web site is one thing that is required on the web, someone with some originality!
Medicine prescribing information. Cautions.
levitra
All news about drug. Read here.
Drugs information sheet. Brand names.
valtrex
Everything news about pills. Read now.
Amazing all kinds of valuable information.
Medicament prescribing information. Cautions.
where buy neurontin
Actual trends of medicines. Read information here.
Meds information leaflet. What side effects?
viagra generics
All about medicine. Get information here.
Medicament information leaflet. Short-Term Effects.
order glucophage
Best about meds. Read now.
Meds information leaflet. Cautions.
cost celebrex
Some trends of pills. Get information now.
Medication information leaflet. What side effects can this medication cause?
cialis
Everything trends of drug. Read information here.
Please let me know if you’re looking for a article author for your blog.
You have some really great posts and I believe I would be
a good asset. If you ever want to take some of the
load off, I’d love to write some content for your blog in exchange for a link back
to mine. Please shoot me an e-mail if interested. Cheers!
Your stylee is unique in compaison to other people I have read stuff from.
Many thanks for posting when you’ve got the opportunity, Guess I’ll ust book mark this
site.
Feel frfee to surf to my webpage Funny Animal Reaction
A fascinating discussion is definitely worth comment.
I do think that you need to write more on this topic, it may not be a taboo
matter but typically people do not talk about such issues.
To the next! Kind regards!!
Pills information. Brand names.
finpecia medication
Everything what you want to know about medication. Get now.
Medicament information leaflet. Drug Class.
silagra
Best news about meds. Get here.
Wonderful blog! I found it while searching on Yahoo News. Do you
have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Thank you
, отечественные авто, 3 изд.
Thank you for another informative blog. Where else may just I am
getting that type of information written in such an ideal approach?
I’ve a venture that I am simply now operating on, and I have been at the look out for such info.
Pills information. Short-Term Effects.
lyrica for sale
Everything trends of medicines. Read information now.
Excellent blog here! Also your site loads up fast!
What web host are you using? Can I get your affiliate link to your host?
I wish my site loaded up as quickly as yours
lol
Take a look at my web page :: https://bazafirmonline.eu/
Drugs information. Brand names.
cordarone
Best what you want to know about medicine. Read information here.
Pills information leaflet. Effects of Drug Abuse.
lyrica
Actual information about medication. Get now.
Remarkable! Its truly amazing post, I have got much clear idea concerning
from this article.
Medicines information sheet. Long-Term Effects.
flagyl without insurance
Best what you want to know about drug. Get information now.
I do not even know how I ended up here, but I thought this post
was good. I do not know who you are but definitely you’re going to a famous blogger if you aren’t already 😉 Cheers!
Medicine information leaflet. Long-Term Effects.
valtrex
Some what you want to know about medicines. Get now.
Very good article. I will be going through many of these issues as well..
Fantastic data Regards.
My web site; http://www.ziocoop.com/bbs/board.php?bo_table=free&wr_id=77281
It’s going to be end of mine day, however before end I am
reading this enormous paragraph to increase my experience.
Hi there! Quick question that’s completely off topic.
Do you know how to make your site mobile friendly?
My blog looks weird when viewing from my iphone 4.
I’m trying to find a theme or plugin that might
be able to fix this problem. If you have any recommendations, please share.
Thank you!
Usually I don’t read post on blogs, but I wish to say
that this write-up very pressured me to try and do it!
Your writing taste has been amazed me. Thank you,
very great post.
Medicine information. Long-Term Effects.
mobic without insurance
Some information about drugs. Get information here.
Medication information leaflet. What side effects?
singulair for sale
Some news about pills. Get now.
Very soon this site will be famous amid all blogging and site-building viewers, due to it’s good
articles or reviews
Drug information sheet. Brand names.
kamagra
Actual information about medicine. Get information here.
Hey there! I’ve been following your website for some time now and finally got the bravery to go ahead and give you a shout out from Kingwood Tx!
Just wanted to tell you keep up the good job!
Hey there! I just wanted to ask if you ever have any issues with hackers?
My last blog (wordpress) was hacked and I ended up losing
several weeks of hard work due to no data backup. Do you have
any solutions to prevent hackers?
can you buy generic prednisolone price
Meds information for patients. Cautions.
seroquel
All news about drugs. Get information now.
Hello, i feel that i noticed you visited my web site so
i got here to go back the favor?.I am attempting to find issues to improve my website!I guess its adequate to make use of a few
of your concepts!!
We are a group of volunteers and starting a new scheme in our community.
Your website provided us with useful info to work on. You’ve
performed a formidable task and our entire neighborhood shall
be thankful to you.
Pills information for patients. Effects of Drug Abuse.
retrovir rx
Everything about pills. Get now.
I am no longer sure the place you are getting your info, however good topic.
I must spend a while studying much more or working out more.
Thanks for magnificent information I was in search of this information for my mission.
Medication information leaflet. Effects of Drug Abuse.
neurontin medication
Everything what you want to know about meds. Read information now.
Useful information. Lucky me I discovered your site unintentionally, and I am
shocked why this twist of fate did not came about in advance!
I bookmarked it.
Hello! Someone in my Myspace group shared this site with us so I came to
look it over. I’m definitely enjoying the information. I’m bookmarking and will be tweeting
this to my followers! Outstanding blog and terrific design and style.
Medicament prescribing information. Brand names.
colchicine prices
Everything trends of medicines. Get information now.
Meds information sheet. Brand names.
zenegra
Actual about pills. Read here.
Thanks for sharing your thoughts about xx video. Regards
Дуже крутий сервіс із продажу проксі! Всім рекомендую!мобильный прокси
I got this site from my pal who informed me regarding this site
and at the moment this time I am visiting this web site and reading very informative articles
here.
Medicament information sheet. Effects of Drug Abuse.
rx cleocin
Actual about pills. Get information now.
It’s very simple to find out any matter on net as compared to
textbooks, as I found this article at this web page.
When I originally commented I clicked the “Notify me when new comments are added” checkbox and now each
time a comment is added I get several emails with the same comment.
Is there any way you can remove me from that service?
Thanks!
Medicines information sheet. Cautions.
fluoxetine
Actual news about medication. Read now.
Drugs information for patients. What side effects?
fluoxetine
Everything news about medicines. Get information here.
Nice answers in return of this question with firm arguments and describing all about that.
Pills information for patients. Generic Name.
can i buy paxil
All about medicines. Read now.
Новости рограммного обеспечения на Смоленском портале. Архив новостей. семнадцать недель назад. 1 страница
Medicines information. Generic Name.
cost mobic
Everything about medication. Get here.
ikea joy parking 4th street san jose ca is simply 11 miles from downtown pgh.
Meds information for patients. What side effects can this medication cause?
get nolvadex
All information about medicines. Read information now.
Medicament information leaflet. What side effects can this medication cause?
viagra
Best information about medicines. Read information here.
салат из фасоли с яйцами и орехами
Oh my goodness! Impressive article dude! Many thanks, However I am going through troubles
with your RSS. I don’t understand the reason why I can’t join it.
Is there anyone else getting the same RSS issues? Anybody who knows the answer will you
kindly respond? Thanks!!
ejaculation
bitch
pron
tits
blackjack
masturbating
fetish
prostitute
breast
black jack
breast
erection
camel toe
bitch
porn
booty
penis
fetish
erotica
clit
ejaculation
nipslip
breasts
pills
nipslip
camel toe
schlong
prostitute
breast
ejaculate
fuck
milfs
18+
pr0n
penis
slut
naked
fetish
tits
orgasm
cunt
blow job
homosexual
horny
sex
casino
oral
blow job
poker
ejaculate
boobs
schlong
breasts
penis
homosexual
ejaculating
bitch
busty
ejaculate
fetish
breast
penis
boob
sex
butt
cum
breasts
ejaculate
sex
butt
dildo
erotic
penis
naked
cum
xanex
milf
ejaculating
prostitute
breasts
milf
boob
gambling
nudist
fucked
gay
schlong
booty
dick
naked
masturbating
porn
butt
milfs
blackjack
blackjack
blackjack
prostitute
breasts
blackjack
Демонтаж стен Москва
Демонтаж стен Москва
Pills information. Cautions.
proscar cost
Actual news about meds. Read now.
Medicine information leaflet. Generic Name.
strattera for sale
Best what you want to know about medicines. Get here.
buy cheap finasteride without dr prescription
Medication prescribing information. Drug Class.
cialis
Some trends of pills. Get here.
Meds prescribing information. Generic Name.
get eldepryl
Best news about medicine. Get now.
I could not refrain from commenting. Very well written!
Meds information. Drug Class.
cialis
Actual trends of pills. Get information here.
Medicine information sheet. Drug Class.
prozac
Some news about medicament. Get information now.
Wow, amazing weblog layout! How long have you been blogging for?
you make blogging glance easy. The total glance of your website
is excellent, let alone the content material!
Medicines information sheet. Drug Class.
pregabalin no prescription
Everything about medicament. Read information here.
Medicine information for patients. Cautions.
neurontin
Best about drugs. Read here.
Drug information leaflet. Generic Name.
order norvasc
Best about medication. Get now.
Medicines information sheet. Long-Term Effects.
cephalexin
Best information about medicament. Read information here.
Wow, marvelous blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of your
website is fantastic, let alone the content!
Демонтаж стен Москва
Демонтаж стен Москва
Pills information leaflet. Short-Term Effects.
cordarone order
All about meds. Read here.
Meds information leaflet. What side effects can this medication cause?
fluoxetine
All trends of pills. Read information now.
Meds information sheet. Brand names.
lyrica brand name
Best what you want to know about meds. Get here.
tetracyclin
Medicines information leaflet. Cautions.
neurontin
Some news about pills. Get information now.
Medicament prescribing information. Long-Term Effects.
rx effexor
Actual news about medicine. Read here.
Medicine information for patients. Short-Term Effects.
cost sildenafil
All what you want to know about drugs. Read information now.
Meds information. Generic Name.
singulair
Some about pills. Get information now.
Drugs information leaflet. Effects of Drug Abuse.
fluoxetine
Some trends of meds. Read information now.
мдаааааааа
, http://wiki.mgpu.ru/index.php?title=favorgroup материи, 5 изд.
Almost 40 percent of the total ttax rvenue in thee state of Nevada coms from gambling.
my web pawge … click here
https://toonsontees.com/gallery/no-condition-to-crawl-home/ инфо — значит информация!
Pills information sheet. Drug Class.
motrin order
Actual information about medicament. Read now.
Pills information sheet. What side effects?
cialis super active
Actual news about pills. Get here.
регистрация и продление доменов в зоне https://ngmk.by/component/k2/item/14-do-what-you-like/ по дешевым ценам.
Это интересно. Подскажите, где я могу об этом прочитать?
japanese https://research-wiki.win/index.php?title=slot_casino_machines machines are “beatable”.
Medicament information for patients. What side effects?
nexium generic
Actual trends of medicament. Read now.
Digital Travel Insurance Management in Africa
Medication prescribing information. Short-Term Effects.
amoxil for sale
Some information about drugs. Read now.
Hey There. I found your blog using msn. This is an extremely well
written article. I will be sure to bookmark it and come back to read more of your useful info.
Thanks for the post. I will certainly comeback.
เว็บไซต์สล็อต 888 pg ยังมีการบริการลูกค้าที่เป็นเลิศด้วยทีมงานที่เป็นมืออาชีพและเป็นมิตรตลอดเวลา คุณสามารถติดต่อสอบถามหรือแจ้งปัญหาได้ตลอด 24 ชั่วโมง ผ่านช่องทางต่างๆ เช่น สนทนาสด (Live Chat) โทรศัพท์ หรืออีเมล ทีมงานจะตอบกลับคุณอย่างรวดเร็วและเป็นมิตรเสมอ
นอกจากนี้ เว็บไซต์ยังมีโปรแกรมสะสมแต้มและสิทธิพิเศษต่างๆ สำหรับสมาชิก เมื่อคุณเล่นเกมสล็อต PG และเพิ่มแต้ม คุณสามารถแลกสิทธิ์และรับของรางวัลที่น่าตื่นเต้น เช่น เครดิตเสริมในการเล่น เงินคืน หรือของรางวัลพิเศษอื่นๆ ที่จะเพิ่มความสนุกและประสบการณ์การเล่นของคุณ
ด้วยเหตุนี้ หากคุณต้องการสัมผัสกับประสบการณ์การเล่นสล็อตออนไลน์ที่เป็นที่นิยมและมีคุณภาพ ไม่ต้องสลักว่าเว็บไซต์สล็อต 888 pg เป็นทางเลือกที่ดีที่สุดสำหรับคุณ ร่วมสนุกไปกับเกมสล็อต PG ที่มาพร้อมความสนุกและความตื่นเต้นสุดพิเศษได้ที่นี่!
Undeniably imagine that which you stated. Your favorite justification appeared to be on the web
the simplest thing to remember of. I say to you, I
certainly get irked even as other people consider issues that they plainly do
not know about. You managed to hit the nail upon the top and also defined out the entire thing with no need side-effects ,
folks could take a signal. Will likely be back to get more.
Thanks
Also visit my blog post https://clients1.google.cl/url?q=https://katalogfirm-pl.eu/
Bonus no cadastro
Are you looking for an online casino that offers fantastic bonuses upon registration? Look no further! At WAKABET, we have the perfect combination of thrilling games and attractive bonuses to enhance your gaming experience. From bonus no cadastro (registration bonuses) to bonus sem deposito (no deposit bonuses), we have it all. Let’s dive into the world of exciting bonuses and endless opportunities to win!
More Than 100 Games:
With WAKABET, you’ll have access to a wide selection of over 100 captivating games. Whether you prefer classic slots, table games, or live casino experiences, we have something for everyone. Our games are designed to provide entertainment and excitement while giving you the chance to win big. Get ready to explore the thrilling world of online gambling with us!
Fast Deposits:
We understand the importance of a seamless gaming experience, which is why we offer fast and convenient deposit options. At WAKABET, you can quickly and securely deposit funds into your account, allowing you to start playing your favorite games without any delays. Our reliable payment methods ensure a hassle-free deposit process, giving you more time to enjoy the excitement of the games.
Register Now at WAKABET:
Sign up today at WAKABET and unlock a world of bonuses and rewards. As a token of appreciation for choosing us, we offer a generous bonus on registration. You don’t even need to make a deposit to enjoy these rewards! Simply create an account, and you’ll receive a bonus in your account balance. It’s our way of welcoming you to the WAKABET family and giving you a head start on your gaming journey.
Daily Diamond Discount:
At WAKABET, we believe in rewarding our loyal players. That’s why we have the exclusive Daily Diamond Discount program. As you continue to play and enjoy our games, you’ll earn Diamond points. These points can be redeemed for various benefits, including discounts on your deposits. It’s our way of showing appreciation for your loyalty and providing you with additional value for your money.
Net Win/Loss Cashback:
We understand that winning and losing are part of the gaming experience. To ensure that you always have a thrilling time, we offer a Net Win/Loss Cashback program. This means that regardless of whether you win or lose, you’ll receive a cashback on your net losses. It’s a fantastic opportunity to recoup some of your losses and continue playing your favorite games.
Conclusion:
If you’re looking for an online casino that offers exciting bonuses on registration, WAKABET is the place to be. With our extensive selection of games, fast deposits, and rewarding bonus programs, we strive to provide you with the ultimate gaming experience. Don’t miss out on the opportunity to play, win, and get rewarded. Register now at WAKABET and embark on an exhilarating journey filled with thrilling games and lucrative bonuses!
It is appropriate time to make some plans for the longer term and it is time to be happy.
I have learn this put up and if I may just
I wish to counsel you few fascinating issues or suggestions.
Maybe you could write next articles referring to
this article. I desire to read even more things approximately it!
Also visit my webpage; https://clients1.google.tm/url?q=https://katalogfirm-pl.eu/
смотреть онлайн
Medicines prescribing information. What side effects?
valtrex without insurance
Best information about medication. Get information now.
Спасибо за объяснение, я тоже считаю, что чем проще, тем лучше…
it’s uncommon to see so many providers at one usa on-line https://wiki-spirit.win/index.php?title=vavada_casino_review!
I visited multiple blogs but the audio feature for audio songs existing at this web page is truly excellent.
It is appropriate time to make some plans for the future and it’s time to be happy.
I’ve read this post and if I could I want to suggest you some interesting
things or suggestions. Maybe you can write next articles referring to this article.
I wish to read even more things about it!
Medicament information leaflet. Brand names.
buy generic cephalexin
Everything trends of medication. Get here.
Pills information. What side effects can this medication cause?
lisinopril generic
Best news about drugs. Get information here.
Ketogenic diets include very few carbs. Those are only a few words guaranteed
to scare you to loss of life or fill you with guilt.
The pita chips, cooked in-house day by day in small batches, are crunchy however not as oily as tortilla chips.
If your cat is sick once or twice but appears in any other case nicely, take away
their food for a couple of hours, then feed small amounts of a extremely digestible food similar to chicken, or a prescription diet from your vet.
Many online grocery companies have popped up lately, delivering discounted food products on to your door.
Planning your meals for the week primarily based on what’s on sale at the grocery store is
a strong technique (so long as you follow your checklist).
Love’s Labours Lost”: “Beauty is purchased by judgement of
the eye, not utter’d by base sale of chapmen’s tongues.
Companies making an attempt to make a sale could not
know what’s greatest for you and your loved ones.
Meds information sheet. Effects of Drug Abuse.
rx sildigra
Best information about medication. Read here.
Very soon this web site will be famous amid all blogging viewers, due to it’s pleasant posts
If you are going for finest contents like myself, just pay
a visit this web site daily because it gives
quality contents, thanks
4ghz) as examined; retail fashions have a core i5 processor.
Pills information sheet. Long-Term Effects.
kamagra without dr prescription
Everything about meds. Get information now.
Medicament information for patients. Effects of Drug Abuse.
valtrex
All trends of pills. Read here.
Drug prescribing information. What side effects?
colchicine
Some trends of meds. Get information here.
Puncak88 adalah situs Slot Online terbaik di Indonesia. Puncak88, situs terbaik dan terpercaya yang sudah memiliki lisensi resmi, khususnya judi slot online yang saat ini menjadi permainan terlengkap dan terpopuler di kalangan para member, Game slot online salah satu permainan yang ada dalam situs judi online yang saat ini tengah populer di kalanagan masyarat indonesia, dan kami juga memiliki permainan lainnya seperti Live casino, Sportbook, Poker , Bola Tangkas , Sabung ayam ,Tembak ikan dan masi banyak lagi lainya.
Puncak88 Merupakan situs judi slot online di indonesia yang terbaik dan paling gacor sehingga kepuasan bermain game slot online online akan tercipta apalagi jika anda bergabung dengan yang menjadi salah satu agen slot online online terpercaya tahun 2022. Puncak88 Selaku situs judi slot terbaik dan terpercaya no 1 menyediakan daftar situs judi slot gacor 2022 bagi semua bettor judi slot online dengan menyediakan berbagai macam game menyenangkan seperti poker, slot online online, live casino online dengan bonus jackpot terbesar Tentunya. Berikut keuntungan bermain di situs slot gacor puncak88
1. Proses pendaftaran akun slot gacor mudah
2. Proses Deposit & Withdraw cepat dan simple
3. Menang berapapun pasti dibayar
4. Live chat 24 jam siap melayani keluh kesah dan solusi untuk para member
5. Promo bonus menarik setiap harinya
planning to https://www.todoexpertos.com/preguntas/dh4ooib6sigdgw4r/sport-betting-how-to-make-money-on-sport to ucsb?
Medicament prescribing information. Drug Class.
neurontin
Best news about medication. Get information now.
Medicines prescribing information. What side effects?
buying pregabalin
Some trends of pills. Read here.
I was able to find good advice from your
content.
there were https://m.boxuu.com/news/c/35661.html games for teenagers of all ages.
Medicine prescribing information. What side effects?
propecia
All information about medicament. Get information here.
I’m gone to say to my little brother, that he should also pay a quick visit
this blog on regular basis to take updated from hottest gossip.
тож чим https://avto-v-rassrochku.site/ відрізняється від кредиту?
Medication prescribing information. Brand names.
get kamagra
All news about medicines. Get here.
Pills information leaflet. Effects of Drug Abuse.
zoloft
Actual information about medicament. Get here.
Meds prescribing information. Effects of Drug Abuse.
flibanserina generics
Everything news about medicine. Read now.
Slot Deposit Pulsa
MAGNUMBET di Indonesia sangat dikenal sebagai salah satu situs judi slot gacor maxwin yang paling direkomendasikan. Hal tersebut karena situs ini memberi game slot yang paling gacor. Tak heran karena potensi menang di situs ini sangat besar. Kami juga menyediakan game slot online uang asli yang membuatmu makin betah bermain slot online. Jadi, kamu tak akan bosan ketika bermain game judi karena keseruannya memang benar-benar tiada tara. Kami juga menyediakan game slot online uang asli yang membuatmu makin betah bermain slot online. Jadi, kamu tak akan bosan ketika bermain game judi karena keseruannya memang benar-benar tiada tara.
Kami memiliki banyak sekali game judi yang memberi potensi cuan besar kepada pemain. Belum lagi dengan adanya jackpot maxwin terbesar yang membuat pemain makin diuntungkan. Game yang dimaksud adalah slot gacor dengan RTP hingga 97.8%
Medicament information for patients. Generic Name.
clomid
Actual about medicine. Get now.
Drugs information sheet. What side effects can this medication cause?
silagra
Everything trends of meds. Get information here.
Pills prescribing information. Effects of Drug Abuse.
generic pregabalin
All trends of medicament. Get information here.
Medicine information for patients. What side effects?
nolvadex
Everything news about medicines. Read information now.
Touche. Outstanding arguments. Keep up the good
effort.
My blog post: https://raindrop.io/mantiavkql/bookmarks-35538217
Medicament information leaflet. Cautions.
flibanserina order
Everything what you want to know about medicine. Get now.
Сервис Kraken на первый взгляд очень простой
и понятный, имеет незатейливый дизайн.
Но наверное, это и работает. Ведь присутствие разных наворотов лишь обременяет процесс взаимодействия сервиса с конечным
пользователем. Для того, чтобы совершать сделки необходимо перейти по ссылке xn--2ra-7ua.cc,
зарегистрировать аккаунт и пополнить счет.
А дальше простая процедура|простой процесс} поиска необходимых товаров и в
одно мгновение в непосредственной близости ты заберешь
свой заветный клад который откроет
путь в мир фантазий и безмятежности.
Регестрируйся на Кракен.
Drugs information leaflet. What side effects can this medication cause?
sildigra order
Best information about medication. Read information now.
Medicines information for patients. Short-Term Effects.
baclofen medication
Actual news about drugs. Read information here.
Статейное и ссылочное продвижение.
В наше время, практически каждый человек пользуется
интернетом.
С его помощью можно найти любую информацию из различных интернет-источников и поисковых систем.
Для кого-то собственный сайт —
это хобби. Однако, большинство используют разработанные проекты для заработка и привлечение прибыли.
У вас есть собственный сайт
и вы хотите привлечь на него максимум посетителей,
но не знаете с чего начать? Обратитесь
к нам! Мы поможем!
продвижение ссылками
Very good info. Lucky me I recently found your site by accident (stumbleupon).
I have book marked it for later!
Pills information for patients. Brand names.
provigil pill
Everything news about pills. Read information here.
Medicine prescribing information. Brand names.
neurontin
Some news about medication. Get information now.
Selamat datang di Surgaslot !! situs slot deposit dana terpercaya nomor 1 di Indonesia. Sebagai salah satu situs agen slot online terbaik dan terpercaya, kami menyediakan banyak jenis variasi permainan yang bisa Anda nikmati. Semua permainan juga bisa dimainkan cukup dengan memakai 1 user-ID saja. Surgaslot sendiri telah dikenal sebagai situs slot tergacor dan terpercaya di Indonesia. Dimana kami sebagai situs slot online terbaik juga memiliki pelayanan customer service 24 jam yang selalu siap sedia dalam membantu para member. Kualitas dan pengalaman kami sebagai salah satu agen slot resmi terbaik tidak perlu diragukan lagi
ให้คุณมีความมั่นใจในการทำธุรกรรมทางการเงิน เว็บไซต์สล็อต 888 pg ใช้เทคโนโลยีการเข้ารหัสข้อมูลที่มีความปลอดภัยสูง เพื่อให้ข้อมูลส่วนตัวและการทำธุรกรรมของคุณเป็นสิริมงคล ด้วยระบบฝาก-ถอนอัตโนมัติที่รวดเร็วและมีความน่าเชื่อถือ คุณสามารถทำการฝากเงินหรือถอนเงินได้ง่ายๆ โดยไม่ต้องมีความยุ่งยาก
ไม่ว่าคุณจะเป็นนักพนันมือใหม่หรือมืออาชีพ เว็บไซต์สล็อต 888 pg จะมอบประสบการณ์การเล่นที่สมบูรณ์แบบและน่าตื่นเต้น ด้วยรูปแบบการเล่นที่ออกแบบมาอย่างดีเยี่ยม ระบบส่วนตัวที่ให้ความคล่องตัวในการปรับแต่งการเดิมพัน และรางวัลที่มีค่าใหญ่ที่สุดที่คุณสามารถชนะได้
ดังนั้น ไม่ต้องสงสัยอีกต่อไป หากคุณกำลังมองหาเว็บไซต์สล็อตออนไลน์ที่มีคุณภาพและน่าเชื่อถือ เว็บไซต์สล็อต 888 pg เป็นเลือกที่ดีที่คุณควรพิจารณา พร้อมที่จะพาคุณสู่ประสบการณ์การเล่นสล็อตที่น่าตื่นเต้นและได้รับประสบการณ์ที่สมบูรณ์แบบในทุกๆ ด้าน
Medicament prescribing information. What side effects?
prozac
Actual trends of meds. Get information here.
Medicament information leaflet. What side effects can this medication cause?
cephalexin
Best information about pills. Get information here.
Pills information for patients. Generic Name.
get promethazine
Actual news about medication. Get here.
Medicines information for patients. Cautions.
zofran
Some trends of medicine. Read here.
Drugs information sheet. Cautions.
neurontin
Best what you want to know about medicine. Get information now.
I blog frequently and I seriously thank you for your content.
Your article has truly peaked my interest.
I will book mark your site and keep checking for new details
about once a week. I subscribed to your RSS feed too.
Meds prescribing information. Brand names.
can i buy tadacip
Everything news about drug. Read information here.
Meds information for patients. What side effects?
cipro medication
Some information about medicine. Get now.
Magnificent beat ! I would like to apprentice while you
amend your website, how can i subscribe for a blog site?
The account helped me a acceptable deal. I had been tiny bit acquainted of this your broadcast
offered bright clear concept
Hi there, just became aware of your blog through Google, and found that
it is really informative. I’m gonna watch out
for brussels. I’ll appreciate if you continue this in future.
Many people will be benefited from your writing.
Cheers!
My webpage; https://www.blogtalkradio.com/cechinuquq
I know this if off topic but I’m looking into starting my own blog and was
wondering what all is needed to get set up? I’m assuming having a blog like yours would cost a pretty penny?
I’m not very web savvy so I’m not 100% sure. Any tips or advice would be greatly
appreciated. Appreciate it
BLANGKON SLOT adalah situs slot gacor dan judi slot online gacor hari ini mudah menang. BLANGKONSLOT menyediakan semua permainan slot gacor dan judi online terbaik seperti, slot online gacor, live casino, judi bola/sportbook, poker online, togel online, sabung ayam dll. Hanya dengan 1 user id kamu sudah bisa bermain semua permainan yang sudah di sediakan situs terbaik BLANGKON SLOT. Selain itu, kamu juga tidak usah ragu lagi untuk bergabung dengan kami situs judi online terbesar dan terpercaya yang akan membayar berapapun kemenangan kamu
Medicines prescribing information. Effects of Drug Abuse.
norvasc order
All what you want to know about meds. Read information here.
Medicament prescribing information. Generic Name.
celebrex buy
Some trends of drugs. Get here.
Medication information. Long-Term Effects.
flibanserina
Actual information about medicament. Get information now.
Pills prescribing information. Brand names.
glucophage generics
Best news about medication. Read information now.
Meds prescribing information. Long-Term Effects.
lisinopril
Everything trends of medicine. Get information here.
Medication information for patients. Long-Term Effects.
rx viagra
Some trends of meds. Read information here.
These games are accessible from your mobile devices with no require to download any
application or app.
Heree is my webpage :: 카지노사이트
Drug information sheet. What side effects can this medication cause?
zoloft
Actual news about medicine. Read here.
Yes! Finally something about адрес сайта hydra.
Tiếp tục nội dung:
Khi tham gia cá cược bóng đá, người chơi cần nhớ rằng tỷ lệ kèo chỉ là một trong những yếu tố quan trọng. Ngoài ra, còn có nhiều yếu tố khác như thông tin về đội hình, phong độ, lịch sử đối đầu và các yếu tố bên ngoài như thời tiết hay sự vắng mặt của cầu thủ quan trọng. Do đó, việc sử dụng tỷ lệ kèo nhà cái chỉ là một phần trong việc đưa ra quyết định cá cược.
Ngoài ra, cần lưu ý rằng việc tham gia cá cược bóng đá cần có trách nhiệm và kiểm soát tài chính. Người chơi cần đặt ra ngân sách và không vượt quá giới hạn đã định trước. Cá cược chỉ nên được coi là một hình thức giải trí và không nên trở thành nghiện cờ bạc.
Trong bối cảnh mà công nghệ ngày càng phát triển, việc tham gia cá cược bóng đá cũng đã trở nên dễ dàng hơn bao giờ hết. Người chơi có thể truy cập vào các trang web của nhà cái như OZE6868, Keo nha cai tv để tham gia cá cược và xem tỷ lệ kèo trực tuyến. Tuy nhiên, trước khi tham gia, người chơi nên tìm hiểu kỹ về uy tín, độ tin cậy và chất lượng dịch vụ của nhà cái để đảm bảo trải nghiệm cá cược an toàn và thú vị.
Tóm lại, kèo nhà cái là một yếu tố quan trọng trong việc tham gia cá cược bóng đá. Tuy nhiên, người chơi cần lưu ý rằng tỷ lệ kèo chỉ là một phần trong việc đánh giá và quyết định cá cược. Việc sử dụng dịch vụ của nhà cái uy tín và tìm hiểu thông tin từ các nguồn đáng tin cậy sẽ giúp người chơi có những quyết định thông minh và tăng cơ hội chiến thắng trong các hoạt động cá cược bóng đá.
The fiercest critics, individuals top the demand to discredit the validity of the testimonies, were not boys or younger adult men whose conduct we set under the spotlight, but their mothers.
Have a look at my web site https://Www.mazafakas.com/user/profile/2572898
https://www.sq.com.ua/rus/news/novosti_partnerov/10.03.2021/snyat_kvartiru_na_sutki_vitebsk
Meds information leaflet. Brand names.
neurontin generics
Some information about pills. Get here.
Кто либо знает, каким способом установить связь с администратором? Пишу в обратную связь, он никак не отвечает!
https://metaphysican.com/kak-snjat-kvartiru-na-sutki.dhtm
I think that what you posted made a ton of sense.
However, what about this? suppose you were to create a killer
headline? I am not suggesting your information isn’t good., however what
if you added something to possibly get a person’s attention? I mean Traffic analysis of a packet capture with Wireshark • Allhacked is kinda vanilla.
You ought to peek at Yahoo’s home page and watch how they write post headlines to grab viewers
interested. You might try adding a video or a pic or two to
grab people interested about everything’ve got
to say. Just my opinion, it would make your website a little livelier.
порно
Wild Casino’s best on the net casino welcome
bonus provides crypto customers up to $9,000.
Look into my website – 바카라
казино 777
Drugs information sheet. Effects of Drug Abuse.
lyrica
Everything about medicines. Get information now.
Wow, awesome blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of your
site is fantastic, let alone the content!
Main Slot mu di situs judi online Bacot138 Situs
Judi online terlengkap dan terbaik dengan berbagai promo hingga 138% setiap harinya
untuk anda .
Hi, i feel that i saw you visited my web site thus i got here to go back the choose?.I
am trying to find issues to improve my website!I assume its good enough to
use some of your ideas!!
Heya are using WordPress for your site platform? I’m new to the
blog world but I’m trying to get started and create my own. Do you require any coding expertise
to make your own blog? Any help would be
greatly appreciated!
With havin so much content and articles do you ever run into any issues of plagorism or copyright
infringement? My website has a lot of unique content I’ve either written myself or outsourced but
it seems a lot of it is popping it up all over the web without my agreement.
Do you know any ways to help reduce content from being stolen? I’d truly
appreciate it.
Drugs information for patients. Cautions.
cialis
All news about medicament. Read now.
Great article, just what I needed.
Feel free to surf to my web site … http://ods-qa.openlinksw.com/describe/?url=https://spisfirmonline.eu/
Meds information for patients. Generic Name.
sildenafil buy
Some information about meds. Read information here.
Heya i’m for the primary time here. I found this board and I find It
really useful & it helped me out a lot. I hope to present something back and aid others such as you helped me.
“I question they thought no a single would treatment. In San Francisco, Shawn Kinnear claimed that his Echo activated itself and stated cheerfully: “Every time I shut my eyes, all I see is persons dying.
my website – https://pdfcoffee.com/
Hey! This is my first visit to your blog! We are a team of volunteers and starting a
new project in a community in the same niche. Your blog provided us valuable
information to work on. You have done a marvellous job!
This post is really a good one it assists new web people, who are
wishing for blogging.
https://i38.ru/nedvizhimost-potrebitel/posutochnaya-arenda-kvartir-podnyalas-v-ekaterinburge-est-predlozheniya-v-belarusi-pliusi-i-niuansi-takoy-uslugi
สล็อต เว็บใหญ่ pg
ให้คุณมีความมั่นใจในการทำธุรกรรมทางการเงิน เว็บไซต์สล็อต 888 pg ใช้เทคโนโลยีการเข้ารหัสข้อมูลที่มีความปลอดภัยสูง เพื่อให้ข้อมูลส่วนตัวและการทำธุรกรรมของคุณเป็นสิริมงคล ด้วยระบบฝาก-ถอนอัตโนมัติที่รวดเร็วและมีความน่าเชื่อถือ คุณสามารถทำการฝากเงินหรือถอนเงินได้ง่ายๆ โดยไม่ต้องมีความยุ่งยาก
ไม่ว่าคุณจะเป็นนักพนันมือใหม่หรือมืออาชีพ เว็บไซต์สล็อต 888 pg จะมอบประสบการณ์การเล่นที่สมบูรณ์แบบและน่าตื่นเต้น ด้วยรูปแบบการเล่นที่ออกแบบมาอย่างดีเยี่ยม ระบบส่วนตัวที่ให้ความคล่องตัวในการปรับแต่งการเดิมพัน และรางวัลที่มีค่าใหญ่ที่สุดที่คุณสามารถชนะได้
ดังนั้น ไม่ต้องสงสัยอีกต่อไป หากคุณกำลังมองหาเว็บไซต์สล็อตออนไลน์ที่มีคุณภาพและน่าเชื่อถือ เว็บไซต์สล็อต 888 pg เป็นเลือกที่ดีที่คุณควรพิจารณา พร้อมที่จะพาคุณสู่ประสบการณ์การเล่นสล็อตที่น่าตื่นเต้นและได้รับประสบการณ์ที่สมบูรณ์แบบในทุกๆ ด้าน
Howdy! This is my first comment here so I just wanted to give a quick shout
out and tell you I truly enjoy reading your posts.
Can you recommend any other blogs/websites/forums that cover
the same subjects? Thanks a lot!
certainly like your website but you need to take a look at the spelling on several of your posts.
Many of them are rife with spelling problems and I to
find it very bothersome to inform the reality nevertheless I will definitely come again again.
When some one searches for his essential thing,
thus he/she desires to be available that in detail, thus that thing is maintained over here.
Medicine prescribing information. What side effects?
paxil otc
Actual news about drugs. Get information here.
Подробнее об организации: Гостиница Красный Бор на сайте Смоленск в сети
Ahaa, its good conversation on the topic of this
article at this place at this web site, I have
read all that, so at this time me also commenting at
this place.
prasugrel 10mg
Hiya very cool blog!! Guy .. Beautiful .. Superb .. I’ll bookmark your blog and take the feeds additionally?
I’m happy to find a lot of useful info here within the submit,
we need develop more techniques on this regard, thank
you for sharing. . . . . .
I really like it when people come together and share opinions.
Great site, stick with it!
The project was planned in 1990. The China Pakistan Economic Corridor job aims to connection Gwadar Port and Kashgar (China) making use of Pakistani motorways, national highways, and expressways.
Feel free to surf to my blog; https://vn.cbmpress.com/bbs/board.php?bo_table=free&wr_id=135588
Can you tell us more about this? I’d want to find out more details.
Here is my web page https://katalogpolskichfirm.eu/
потрахушки
prasugrel buy
Viết thêm:
Jili City – Một trải nghiệm cá độ trực tuyến độc đáo
Jili City đã trở thành một cái tên nổi bật trong lĩnh vực cá độ trực tuyến với sự độc đáo và hấp dẫn của mình. Nhà cái này mang đến cho người chơi một trải nghiệm đáng nhớ và khác biệt so với những sàn cá độ truyền thống.
Một trong những điểm nổi bật của Jili City là tính năng bắn cá code, một chế độ chơi độc đáo và thú vị. Người chơi có thể tham gia vào các trận bắn cá căn cứ trên các mã code, và mỗi lần bắn trúng mục tiêu, họ sẽ nhận được những phần thưởng giá trị. Tính năng này mang đến một sự kích thích mới mẻ và cung cấp cơ hội kiếm thêm phần thưởng hấp dẫn cho người chơi.
Hơn nữa, Jili City cũng tạo ra một môi trường cá cược công bằng và an toàn cho người chơi. Nhà cái này tuân thủ các quy định và tiêu chuẩn nghiêm ngặt để đảm bảo tính minh bạch và trung thực trong quá trình cá độ. Hệ thống công nghệ tiên tiến được sử dụng để đảm bảo rằng tất cả các trò chơi và giao dịch đều được kiểm soát và giám sát một cách chặt chẽ.
Để tạo sự tin tưởng và thu hút người chơi, Jili City cung cấp một loạt các ưu đãi và khuyến mãi hấp dẫn. Người chơi có thể nhận được các khoản tiền thưởng, quà tặng và các phần thưởng khác từ việc tham gia vào các chương trình khuyến mãi của nhà cái. Điều này làm tăng giá trị của trải nghiệm cá độ và đem lại sự hài lòng cho người chơi.
Ngoài ra, Jili City còn đầu tư vào dịch vụ khách hàng chất lượng cao. Đội ngũ nhân viên hỗ trợ chuyên nghiệp và tận tâm luôn sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người chơi trong quá trình cá độ. Sự hỗ trợ nhanh chóng và tận tâm giúp người chơi cảm thấy tin tưởng và an tâm khi tham gia vào Jili City.
Tóm lại, Jili City mang đến một trải nghiệm cá độ trực tuyến độc đáo và hấp dẫn. Tính năng bắn cá code và tính minh bạch trong quá trình cá độ là những yếu tố độc đáo và thu hút của nhà cái này. Với sự tận tâm đến dịch vụ khách hàng và các ưu đãi hấp dẫn, Jili City đem đến cho người chơi một trải nghiệm cá độ trực tuyến đáng nhớ và giá trị. Hãy khám phá Jili City và trải nghiệm những điều tuyệt vời mà nhà cái này mang đến.
Статейное и ссылочное продвижение.
В наше время, практически каждый человек пользуется
интернетом.
С его помощью можно найти любую информацию из различных интернет-источников и поисковых систем.
Для кого-то собственный сайт — это хобби.
Однако, большинство используют разработанные проекты для заработка и привлечение прибыли.
У вас есть собственный сайт и вы
хотите привлечь на него максимум посетителей,
но не знаете с чего начать? Обратитесь к нам!
Мы поможем!
качественные ссылки
Hmm it seems like your website ate my first comment (it was super long) so
I guess I’ll just sum it up what I submitted and say,
I’m thoroughly enjoying your blog. I as well am an aspiring
blog blogger but I’m still new to the whole thing.
Do you have any points for beginner blog writers? I’d definitely appreciate it.
whoah this blog is great i love studying your articles. Keep up the
great work! You already know, many individuals are
searching around for this information, you could aid them greatly.
Also visit my blog post: https://katalogstron24.eu/
Jili Games – Sự lựa chọn hàng đầu của người chơi
Với sự đa dạng và chất lượng của dòng sản phẩm, Jili Games đã trở thành sự lựa chọn hàng đầu của nhiều người chơi. Đội ngũ phát triển tài năng và tâm huyết của Jili Games luôn đảm bảo rằng mỗi trò chơi đều mang đến trải nghiệm tuyệt vời và sự hài lòng tối đa cho người chơi.
Jili Games không ngừng đầu tư vào nghiên cứu và phát triển để mang đến những trò chơi mới nhất và độc đáo. Từ việc thiết kế giao diện đẹp mắt và tinh tế đến việc xây dựng cốt truyện hấp dẫn và tính năng độc đáo, mỗi trò chơi của Jili Games đều mang dấu ấn độc đáo và sự sáng tạo không ngừng.
Không chỉ dừng lại ở việc tạo ra những trò chơi hấp dẫn, Jili Games còn liên tục cập nhật và mở rộng nội dung. Từ những cập nhật nhỏ nhặt đến sự kiện và giải đấu lớn, Jili Games mang đến sự mới mẻ và kích thích cho người chơi. Bạn luôn có cơ hội khám phá và trải nghiệm những điều mới mẻ trong thế giới game của Jili Games.
Không chỉ là một nhà cung cấp trò chơi, Jili Games còn tạo nên một cộng đồng đam mê và thân thiện. Người chơi có thể kết nối và giao lưu với nhau thông qua các tính năng xã hội và chia sẻ niềm vui chơi game. Bạn có thể tìm kiếm bạn bè mới, tham gia vào câu lạc bộ đặc biệt và chia sẻ những chiến tích trong trò chơi. Jili Games mang đến sự kết nối và cảm giác thân thuộc giữa các game thủ trên khắp mọi miền đất nước.
Với tất cả những ưu điểm và đặc điểm nổi bật, Jili Games đã khẳng định vị thế của mình là một trong những nhà cung cấp trò chơi hàng đầu. Người chơi có thể tìm thấy niềm vui, may mắn và trải nghiệm tuyệt vời trong mỗi trò chơi của Jili Games. Hãy tham gia ngay và khám phá thế giới giải trí phong phú và đa dạng từ Jili Games.
Medicines information for patients. Cautions.
viagra soft
Everything information about meds. Read information here.
I blog quite often and I genuinely appreciate your information. Your article has
really peaked my interest. I’m going to book mark your website and keep checking for new details about once per week.
I opted in for your RSS feed too.
Really when someone doesn’t understand afterward its up to other visitors that they will
assist, so here it happens.
Tiếp tục nội dung:
Trong thế giới cá cược hiện đại, kèo nhà cái đã trở thành một phần không thể thiếu trong cuộc sống của những người yêu thích bóng đá và cá cược. Nhờ sự phát triển của công nghệ thông tin, người chơi có thể dễ dàng tiếp cận thông tin về kèo nhà cái, tỷ lệ cược, và các sự kiện thể thao trong thời gian thực. Điều này giúp họ có được sự linh hoạt và thuận tiện khi đưa ra quyết định cá cược.
Kèo nhà cái không chỉ áp dụng trong bóng đá mà còn trong nhiều môn thể thao khác như bóng rổ, tennis, đua xe, và nhiều hơn nữa. Điều này mở ra nhiều cơ hội cho người chơi khám phá và thử vận may trong việc cá cược các môn thể thao khác nhau. Tỷ lệ kèo nhà cái sẽ thay đổi tùy thuộc vào sự phân tích, dự đoán và sự biến động của thị trường.
Một điểm đáng chú ý khác là việc lựa chọn nhà cái uy tín và đáng tin cậy để tham gia cá cược. Người chơi cần tìm hiểu kỹ về nhà cái, xem xét đánh giá và phản hồi từ người dùng trước khi đưa ra quyết định. Nhà cái uy tín như OZE6868, Keo nha cai tv luôn đảm bảo độ an toàn và bảo mật thông tin cá nhân, cung cấp dịch vụ chuyên nghiệp và hỗ trợ khách hàng tận tâm. Điều này đảm bảo rằng người chơi có một trải nghiệm cá cược đáng tin cậy và an toàn.
Không chỉ dừng lại ở việc cá cược, kèo nhà cái còn là nguồn thông tin hữu ích để người chơi nắm bắt xu hướng và phân tích các trận đấu. Nó cung cấp thông tin về sự chuẩn bị của các đội bóng, lực lượng cầu thủ, thông tin chấn thương, và nhiều yếu tố khác. Việc nắm bắt được những thông tin này giúp người chơi có sự tự tin hơn trong việc đưa ra quyết định cá cược.
Tóm lại, kèo nhà cái đã trở thành một phần quan trọng trong thế giới cá cược thể thao. Tỷ lệ kèo nhà cái cung cấp thông tin quan trọng và giúp người chơi có được sự tự tin trong quyết định cá cược. Tuy nhiên, việc tham gia cá cược cần có sự cân nhắc, kiến thức và đặt ra giới hạn tài chính. Hãy tận hưởng việc cá cược một cách có trách nhiệm và thưởng thức cuộc sống thể thao một cách hứng khởi.
Meds information leaflet. Cautions.
bactrim
Everything trends of medicament. Get here.
I know this site offers quality based articles
and additional information, is there any other website which presents
these kinds of data in quality?
ciprofloxacino
I am not sure where you are getting your info, but great topic.
I needs to spend some time learning much more
or understanding more. Thanks for fantastic information I was
looking for this info for my mission.
Also visit my page – https://www.blogtalkradio.com/degilcdciz
You actually mentioned this fantastically.
can i purchase cheap sildalist pills
With havin so much content do you ever run into any issues of plagorism or copyright violation? My blog
has a lot of completely unique content I’ve either written myself or outsourced but it
looks like a lot of it is popping it up all over the internet without my
authorization. Do you know any solutions to help stop content from being ripped off?
I’d definitely appreciate it.
my web page – http://krasnoarmeysk.org/go/url=https://katalogpolskichfirm.eu/
Психология
I was very happy to find this great site. I need to to thank you for your time for this fantastic read!!
I definitely savored every little bit of it and I have you book marked to see
new things in your website.
where can i get trazodone tablets
locate the http://w937480o.bget.ru/user/marielbmno you want to disable.
Meds information for patients. Generic Name.
buy diltiazem
All information about medicament. Get information now.
Thanks a bunch for sharing this with all of
us you actually recognise what you are speaking about!
Bookmarked. Kindly additionally talk over with my web site =).
We can have a link exchange contract between us
Link exchange is nothing else except it is simply
placing the other person’s webpage link on your page at proper
place and other person will also do similar in support of you.
My website … https://www.instapaper.com/read/1616057705
историческую версию http://w66501ot.bget.ru/user/mantiapaxj builder 3d можно получить на android.
where to get cheap sildigra without dr prescription
http://fruit-impex.by/index.php?subaction=userinfo&user=ehajozocy
What i do not realize is if truth be told how you are now not actually much more well-favored than you might be right now.
You’re so intelligent. You already know therefore significantly
when it comes to this topic, produced me in my opinion believe it from a lot
of numerous angles. Its like women and men don’t seem
to be fascinated until it’s one thing to accomplish with Girl gaga!
Your own stuffs outstanding. At all times care for it up!
Pills information leaflet. Brand names.
can i get provigil
Some what you want to know about medicament. Get information now.
What’s up to all, how is everything, I think every one is getting more from
this site, and your views are good for new people.
Medicines information sheet. Effects of Drug Abuse.
viagra
Everything news about drugs. Read information now.
Hey! I know this is kind of off topic but I was wondering if you knew
where I could locate a captcha plugin for my comment
form? I’m using the same blog platform as yours and I’m having difficulty finding one?
Thanks a lot!
Medication information for patients. What side effects can this medication cause?
strattera
All trends of medication. Read information now.
I have been surfing online more than three hours today, yet
I never found any interesting article like yours.
It’s pretty worth enough for me. Personally,
if all web owners and bloggers made good content as you did, the net will be a lot more useful than ever before.
Hey! This is my first visit to your blog! We are a group of volunteers and starting a
new project in a community in the same niche.
Your blog provided us beneficial information to work on. You have
done a wonderful job! https://drive.google.com/drive/folders/1D5pO8j3rR8j5vyHuuXkVfIyMstg1Dzwu
Drugs information for patients. Long-Term Effects.
pregabalin
All about drugs. Get information here.
Kinh nghiệm quay nổ hủ Jackpot cho người chơi mới
Nổ hủ, còn được gọi là trò chơi jackpot, đã trở thành một trong những trò chơi phổ biến nhất trong ngành công nghiệp cá cược trực tuyến. Với tính chất hấp dẫn và tiềm năng kiếm lời lớn, nổ hủ thu hút không chỉ những người chơi có kinh nghiệm mà còn cả những người mới bắt đầu.
Đối với người chơi mới, việc quay nổ hủ Jackpot có thể gây khó khăn và những thất bại ban đầu. Tuy nhiên, với một số kinh nghiệm đúc kết từ những người chơi có kinh nghiệm, bạn có thể tăng cơ hội thành công và tận hưởng những phần thưởng đầy hứa hẹn.
Trước tiên, khi chơi nổ hủ Jackpot, hãy tìm hiểu về các quy tắc và nguyên tắc của trò chơi. Hiểu rõ cách hoạt động của trò chơi sẽ giúp bạn có cái nhìn tổng quan và biết cách đặt cược một cách hiệu quả. Đừng quên đọc kỹ hướng dẫn và điều khoản của trò chơi trên nhà cái mà bạn tham gia.
Thứ hai, quản lý ngân sách của bạn một cách thông minh. Trước khi bắt đầu chơi, hãy định ra một ngân sách giới hạn và tuân thủ nó. Điều này giúp bạn tránh rủi ro và không bị mất kiểm soát trong quá trình chơi. Hãy nhớ rằng việc chơi nổ hủ Jackpot là một hình thức giải trí, vì vậy hãy chỉ sử dụng số tiền mà bạn có thể dễ dàng chấp nhận mất đi.
Thứ ba, tìm hiểu về các chiến lược chơi nổ hủ Jackpot. Một số người chơi chọn cách đặt cược nhỏ và chơi lâu dài, trong khi người khác lại chọn cách đặt cược lớn và hy vọng vào những phần thưởng lớn hơn. Không có một chiến lược hoàn hảo nào, vì mỗi người chơi có phong cách và sở thích riêng. Tuy nhiên, hãy thử nghiệm và tìm hiểu chiến lược phù hợp với bạn.
Cuối cùng, đừng quên chọn nhà cái uy tín để chơi nổ hủ Jackpot. Tìm hiểu về độ tin cậy, lượng người chơi và đánh giá của nhà cái trước khi đăng ký. Một nhà cái đáng tin cậy cung cấp công bằng và an toàn cho người chơi, đồng thời hỗ trợ khách hàng tốt và cung cấp các phần thưởng hấp dẫn.
Trong số những nhà cái tài xỉu online uy tín, Jili City là một lựa chọn đáng xem xét. Jili City là một nhà cái đáng tin cậy và phổ biến với người chơi nổ hủ Jackpot. Nhà cái này cung cấp các trò chơi chất lượng cao với đồ họa tuyệt đẹp và âm thanh sống động. Ngoài ra, Jili City còn có chế độ bắn cá code hấp dẫn và nhiều ưu đãi khác.
Tuy nhiên, như mọi nhà cái khác, Jili City cũng có nhược điểm của mình. Điều quan trọng là bạn cần hiểu rõ các ưu nhược điểm này trước khi quyết định chơi tại nhà cái này. Ví dụ, một số người chơi phản ánh rằng dịch vụ khách hàng của Jili City không luôn đáp ứng được mong đợi của họ.
Tóm lại, nổ hủ Jackpot là một trò chơi hấp dẫn và tiềm năng mang lại lợi nhuận lớn. Với những kinh nghiệm quay nổ hủ Jackpot cho người chơi mới như đã đề cập ở trên, bạn có thể tăng cơ hội thành công và trải nghiệm niềm vui cùng những phần thưởng khủng. Hãy lựa chọn một nhà cái uy tín như Jili City và cùng tham gia vào thế giới nổ hủ Jackpot đầy thú vị.
i hope all will https://didyouknowhomes.com/what-is-a-progressive-bed-automation-for-comfortable-sleep/ – РІСЃС‘ устроится, СЏ надеюсь.
Pills information for patients. Generic Name.
valtrex buy
Actual trends of medicine. Read information now.
Meds information for patients. Brand names.
celebrex
Best information about meds. Get information here.
I seriously love your blog.. Very nice colors & theme.
Did you create this web site yourself? Please reply
back as I’m planning to create my own personal site and would
like to learn where you got this from or what the theme is named.
Thanks!
I read this piece of writing completely on the topic of the difference of
most recent and previous technologies, it’s amazing article.
these are five steps to be an excellent https://schreinerei-lehner.de/index.php/component/k2/item/2-lorem-ipsum-dolor-sit-amet.html tester.
Medicament information. Long-Term Effects.
pregabalin
All about drug. Read now.
I really like what you guys are up too. This kind
of clever work and exposure! Keep up the good works guys I’ve added you guys
to our blogroll.
If you wish for to improve your knowledge simply keep visiting this site and be
updated with the most recent news posted here.
Meds information sheet. What side effects?
buy generic finpecia
Some news about medication. Get information here.
Drug information sheet. Effects of Drug Abuse.
sildigra order
Some news about meds. Get information now.
Simply wish to say your article is as astounding. The clarity in your post is simply spectacular and i could assume you’re an expert on this subject.
Fine with your permission allow me to grab your feed to keep updated with forthcoming post.
Thanks a million and please carry on the gratifying work.
Medicines information for patients. What side effects?
eldepryl
All what you want to know about medicine. Get here.
It is in point of fact a nice and useful piece of
information. I am glad that you shared this useful information with us.
Please keep us up to date like this. Thanks for sharing.
Check out my website: https://www.speedishuttle.com/?URL=https://katalogpolskichfirm.eu/
Wow that was strange. I just wrote an very long comment but after I clicked submit my
comment didn’t appear. Grrrr… well I’m not writing all
that over again. Regardless, just wanted to say excellent
blog!
jili game
Jili Games – Cam kết sự bảo mật và công bằng cho người chơi
Một trong những yếu tố quan trọng nhất mà Jili Games đặt lên hàng đầu là sự bảo mật và công bằng đối với người chơi. Nhà cung cấp này cam kết đảm bảo thông tin cá nhân và tài khoản của người chơi được bảo vệ một cách tuyệt đối.
Jili Games sử dụng các phương pháp và công nghệ bảo mật tiên tiến để đảm bảo rằng thông tin cá nhân và giao dịch của người chơi được bảo mật và không bị xâm phạm. Tất cả dữ liệu cá nhân được mã hóa và lưu trữ trong một môi trường an toàn. Chính sách bảo mật của Jili Games tuân thủ các quy định và tiêu chuẩn ngành công nghiệp để đảm bảo rằng thông tin của người chơi được bảo vệ một cách tốt nhất.
Bên cạnh đó, Jili Games luôn đảm bảo tính công bằng trong trò chơi của mình. Các trò chơi được kiểm tra và xác minh độ tin cậy và công bằng bởi các cơ quan độc lập. Hệ thống ngẫu nhiên số được sử dụng để đảm bảo rằng kết quả của mỗi ván chơi là ngẫu nhiên và không bị can thiệp. Người chơi có thể yên tâm rằng mọi cơ hội và kết quả trong trò chơi đều được xử lý công bằng và minh bạch.
Ngoài ra, Jili Games cũng cam kết đảm bảo trải nghiệm chơi game lành mạnh và đáng tin cậy. Họ chú trọng đến việc ngăn chặn truy cập của người chơi không đủ tuổi và đảm bảo rằng trò chơi chỉ dành cho mục đích giải trí hợp pháp. Jili Games cũng cung cấp các công cụ và tài nguyên để hỗ trợ người chơi có trải nghiệm chơi game an toàn và có trách nhiệm.
Với cam kết vững chắc về bảo mật và công bằng, Jili Games đã xây dựng được lòng tin và sự tin cậy từ phía người chơi. Người chơi có thể yên tâm rằng thông tin cá nhân và trải nghiệm chơi game của mình được bảo vệ một cách tốt nhất. Với Jili Games, việc tham gia vào thế giới giải trí trực tuyến không chỉ mang lại niềm vui mà còn đem lại sự an tâm và tin tưởng.
Hãy tham gia vào Jili Games ngay hôm nay và khám phá trò chơi đa dạng, hấp dẫn cùng sự bảo mật và công bằng hàng đầu. Với Jili Games, bạn sẽ trải nghiệm một thế giới game online tuyệt vời và an toàn.
Drugs information for patients. What side effects can this medication cause?
norvasc pills
Actual about medication. Read here.
Pretty nice post. I just stumbled upon your blog and wanted to say that I have really enjoyed browsing your blog posts. In any case I will be subscribing to your rss feed and I hope you write again very soon!
My web site: https://erectcinxl.org
Medicament information for patients. Long-Term Effects.
buy nolvadex
All news about drug. Read here.
Medication information leaflet. Effects of Drug Abuse.
fosamax
Actual what you want to know about medication. Get now.
With its intercourse optimistic brand philosophy and
easy-to-use design, it’s the main useful resource for intercourse
relationship and informal hookups.
Thanks a lot, Good information!
Feel free to visit my website … https://photorecepty.ru/%D0%BE%D0%B2%D0%BE%D1%89%D0%BD%D0%BE%D0%B9-%D1%81%D0%B0%D0%BB%D0%B0%D1%82-%D1%81-%D0%BF%D0%B5%D1%87%D0%B5%D0%BD%D1%8C%D1%8E
I every time used to study paragraph in news papers but now as
I am a user of internet so from now I am using net
for articles or reviews, thanks to web.
my web blog: https://maps.google.co.kr/url?q=https://katalogpolskichfirm.eu/
Pills information. What side effects can this medication cause?
mobic
Best information about medicament. Read now.
Excellent way of explaining, and fastidious post to obtain facts
regarding my presentation subject, which i am going to
present in college.
Medicines information leaflet. Short-Term Effects.
paxil
Everything news about medicine. Read now.
and in might 2019, detective pikachu formally broke the http://www.rentalchunha.co.kr/bbs/board.php?bo_table=free&wr_id=423602 curse!
It’s awesome in support of me to have a website, which is beneficial in favor of my
knowledge. thanks admin
Here is my web-site; https://www.google.co.ve/url?sa=t&url=https://katalogstron24.eu/
Drugs information for patients. Short-Term Effects.
can i get norvasc
All what you want to know about pills. Get here.
Багато людей знайомі з азартом не з чуток. При цьому, втім, деякі з них жалкують, що якось спробували робити ставки в онлайн-казино. Однозначно вистачає і таких, хто справді щасливий, регулярно переживаючи бурні емоції від проведення часу в віртуальних казино, в тому числі на “одноруких бандитах”. При цьому часто бажання зірвати куш – всередині не головне: викликає інтерес сам ігровий процес. Протестуйте грати в онлайн казино на гривні в Україні в онлайн казино на гривні вже зараз.
Heya i am for the first time here. I found this board
and I find It really useful & it helped me out a lot.
I hope to give something back and aid others like you aided me.
Hi to all, how is the whole thing, I think every one is getting more from this site, and your views
are good for new users.
Drugs information sheet. Drug Class.
zovirax rx
Some news about pills. Read now.
This is a topic that is close to my heart… Take
care! Where are your contact details though?
Also visit my blog post – http://lorenzojogl270zdrowie.wpsuo.com/seks-randki-to-popularne-opcja-dla-ludzi-ktore-szukaja-przyjemnosci-bez-zobowiazan
There is certainly a great deal to learn about this topic.
I love all the points you have made.
Hello! I just wanted to ask if you ever have any trouble
with hackers? My last blog (wordpress) was hacked
and I ended up losing many months of hard work due to no data backup.
Do you have any solutions to protect against hackers?
Feel free to visit my web-site :: http://cesarfgrj923zdrowie.iamarrows.com/spotkania-seksualne-sa-popularne-rozwiazanie-dla-ludzi-ktore-poszukuja-wesolej-rozrywki-bez-zobowiazan
Лучший сайт об отношениях и любви. Статьи о магии любви. Всё это для вас! Всем рекомендую этот сайт!Отношения
Drug information sheet. Effects of Drug Abuse.
where to buy tadacip
Best what you want to know about medicament. Read here.
Drugs information sheet. Cautions.
synthroid
Actual what you want to know about medicament. Read now.
Howdy! This is my 1st comment here so I just wanted
to give a quick shout out and say I genuinely enjoy reading your posts.
Can you recommend any other blogs/websites/forums that go over the same topics?
Appreciate it!
It’s not my first time to go to see this web page, i am
browsing this site dailly and obtain good data from here every
day.
Here is my blog post … https://cse.google.co.uz/url?q=https://katalogfirm-pl.eu/
It’s difficult to find well-informed people in this particular topic, but you sound like you know what
you’re talking about! Thanks
Awesome post.
Feel free to visit my web site: เว็บตรงต่างประเทศ
Pills information sheet. Long-Term Effects.
stromectol
Actual about medicine. Get information now.
This is a topic that’s near to my heart… Thank you!
Where are your contact details though?
порно
I’ve learn a few good stuff here. Definitely value bookmarking for
revisiting. I wonder how a lot effort you put to create such
a excellent informative website.
my blog post :: http://kylerjvdb772zdrowie2022.huicopper.com/tkbyr-aldwaldhkry
Wow, awesome blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of your site is excellent, let alone the content!
Medication information leaflet. Brand names.
cytotec for sale
Some information about meds. Read information here.
moreover, technology https://ritiow3.blog.ss-blog.jp/2011-06-20 is not free.
Medicine information leaflet. Long-Term Effects.
retrovir no prescription
Actual trends of medicine. Get now.
My partner and I stumbled over here by a different page
and thought I should check things out. I like what I see so i am
just following you. Look forward to checking out your web page for a second time.
Here is my website :: https://www.myvidster.com/profile/tinianzykx
I think this is one of the most significant info for me. And
i’m glad reading your article. But should remark on some general things, The web site style is perfect, the articles is really excellent : D.
Good job, cheers
Way cool! Some extremely valid points! I appreciate you penning
this write-up and also the rest of the site is very good.
Drug information for patients. Generic Name.
paxil medication
All about drugs. Get information now.
Drug information leaflet. Drug Class.
zyban medication
Everything information about pills. Get now.
Hi, I check your blogs like every week. Your story-telling style is witty, keep
doing what you’re doing!
Meds information for patients. Effects of Drug Abuse.
lioresal
Some trends of drug. Get information here.
очевидно, що з трьох наведених способів придбання автомобіля найбільш вигідним є http://www.decfacility.in/hello-world/.
I rarely leave comments, but i did some searching and wound up here Traffic analysis of a packet capture with Wireshark • Allhacked. And I do have 2 questions for you if it’s allright. Could it be simply me or does it appear like a few of the remarks appear as if they are coming from brain dead folks? 😛 And, if you are writing at additional social sites, I’d like to keep up with everything fresh you have to post. Could you list of the complete urls of all your social sites like your Facebook page, twitter feed, or linkedin profile?
Here is my site … https://trimtechketo.net
Medicines information for patients. Long-Term Effects.
can i buy amoxil
Some news about drug. Get information here.
I absolutely love your blog.. Great colors & theme. Did you create this website yourself?
Please reply back as I’m looking to create
my own website and would like to find out where you got
this from or just what the theme is named. Cheers!
Rather than a solitary ludicrous melee weapon, Kyril has a myriad of mix-and-match trick weaponry in his arsenal, the most (in)well-known staying a a serrated saw that can switch into a cleaver, as well as a greatsword that glows and shoots beams.
My web page: http://ultfoms.ru/user/ShayneKornweibel/
What i do not realize is actually how you are not
really a lot more smartly-appreciated than you may be
right now. You’re very intelligent. You recognize thus considerably relating to this matter,
made me personally believe it from numerous varied angles.
Its like women and men are not involved unless it’s something to do with Girl gaga!
Your individual stuffs great. Always care for it up!
Review my homepage :: http://bratsk-sport.ru/go/url=https://katalogfirm-pl.eu/
slot gacor hari ini Blackpanther77
Medicines prescribing information. Brand names.
zovirax cost
All information about medicament. Read information here.
Drug information sheet. Short-Term Effects.
provigil rx
All trends of medication. Get here.
Drug information leaflet. Brand names.
viagra soft generics
All what you want to know about medicines. Get here.
Drug information. Effects of Drug Abuse.
retrovir
Actual information about medication. Get information now.
jili slot game
Cùng Jili Games khám phá thế giới giải trí di động
Ngoài việc có mặt trên PC, Jili Games cũng không quên mang đến cho người chơi trải nghiệm di động tuyệt vời. Với ứng dụng di động của Jili Games, người chơi có thể dễ dàng truy cập và tham gia vào các trò chơi yêu thích mọi lúc, mọi nơi. Điều này mang lại sự linh hoạt tuyệt đối và tiện lợi cho người chơi, đồng thời mở ra thêm nhiều cơ hội giành thắng lợi và giải trí trên đầu ngón tay.
Ứng dụng di động của Jili Games được thiết kế với giao diện thân thiện và dễ sử dụng, giúp người chơi dễ dàng điều hướng và tìm kiếm trò chơi một cách thuận tiện. Bên cạnh đó, tất cả các tính năng và chức năng của phiên bản PC đều được tối ưu hoá để phù hợp với các thiết bị di động. Việc chơi game trên điện thoại di động giờ đây trở nên dễ dàng và thú vị hơn bao giờ hết.
Với ứng dụng di động của Jili Games, người chơi có thể thỏa sức khám phá các trò chơi hấp dẫn như Jili Fishing Game và Jili Slot Game mọi lúc, mọi nơi. Bất kể bạn đang ở trên xe bus, trong hàng chờ hay trong cuộc họp, bạn vẫn có thể tận hưởng những giây phút giải trí sảng khoái và hồi hộp. Với sự kết hợp giữa công nghệ tiên tiến và trải nghiệm di động, Jili Games đã đem đến một phương thức chơi game mới mẻ và thú vị cho người chơi.
Nếu bạn là một người yêu thích trò chơi di động, không nên bỏ qua ứng dụng di động của Jili Games. Hãy tải xuống ngay để trải nghiệm thế giới giải trí đa dạng và phong phú ngay trên điện thoại di động của bạn. Với Jili Games, niềm vui và sự hưng phấn của trò chơi sẽ luôn ở bên bạn, bất kể nơi đâu và lúc nào.
It’s a shame you don’t have a donate button! I’d most
certainly donate to this fantastic blog! I suppose for now i’ll settle for bookmarking and
adding your RSS feed to my Google account. I look forward to brand new updates and will share this website with my Facebook
group. Chat soon!
Also visit my webpage :: https://maps.google.cv/url?q=https://katalogpolskichfirm.eu/
Drugs information for patients. Brand names.
cleocin medication
Actual news about drug. Get information now.
Drug information for patients. Effects of Drug Abuse.
ampicillin rx
All what you want to know about medicine. Read here.
https://webyourself.eu/blogs/169429/%D0%9A%D0%B0%D0%BA-%D0%B1%D0%BE%D1%80%D0%BE%D1%82%D1%8C%D1%81%D1%8F-%D1%81-%D0%B2%D1%80%D0%B5%D0%B4%D0%B8%D1%82%D0%B5%D0%BB%D1%8F%D0%BC%D0%B8
Exceptional post however , I was wanting to know
if you could write a litte more on this subject? I’d be very grateful if you could elaborate a little bit more.
Appreciate it!
my web page; http://maps.google.dz/url?q=https://katalogpolskichfirm.eu/
Medication information for patients. What side effects can this medication cause?
zithromax
Everything about medicine. Read information now.
Pills information leaflet. Drug Class.
xenical
Some trends of medicine. Read here.
can you get zoloft for sale
Medicament information sheet. Cautions.
lioresal medication
All trends of medicines. Read information now.
Drug prescribing information. Cautions.
zoloft order
All about drug. Read information now.
Pills prescribing information. Long-Term Effects.
levitra otc
Everything what you want to know about medication. Read information now.
where do you go to find prednisone
Medicament information for patients. What side effects can this medication cause?
rx tadacip
Actual about pills. Read now.
Drugs information. Cautions.
tadacip pill
Best trends of meds. Get now.
My partner and I absolutely love your blog and find most
of your post’s to be just what I’m looking for. can you offer guest writers to write content to suit your
needs? I wouldn’t mind writing a post or elaborating on most of the subjects you
write regarding here. Again, awesome weblog!
My web page – https://diigo.com/0t2yso
https://snegic.net/blogs/40541/%D0%9A%D0%B0%D0%BA-%D0%B1%D0%BE%D1%80%D0%BE%D1%82%D1%8C%D1%81%D1%8F-%D1%81-%D0%B2%D1%80%D0%B5%D0%B4%D0%B8%D1%82%D0%B5%D0%BB%D1%8F%D0%BC%D0%B8
Drugs information. Short-Term Effects.
buy neurontin
Best about drugs. Get now.
Post writing is also a excitement, if you know then you
can write if not it is complicated to write.
Also visit my web page: https://www.instapaper.com/read/1617607182
Medicament information leaflet. What side effects can this medication cause?
prozac
Some information about medication. Get now.
Drug information leaflet. Long-Term Effects.
buy generic cipro
Actual about drugs. Read now.
Лучший сайт об отношениях и любви. Статьи о магии любви. Всё это для вас! Всем рекомендую этот сайт!Отношения
Medicines information sheet. Drug Class.
fosamax
Some information about medication. Get information here.
Medication information. What side effects?
clomid buy
Actual trends of medicament. Read here.
Thanks in support of sharing such a pleasant thought,
paragraph is fastidious, thats why i have read it entirely
Pills information. What side effects can this medication cause?
trazodone
All information about medicine. Read here.
Medicine information. Generic Name.
levitra online
All trends of pills. Read now.
buy meclizine without prescription https://meclizine.top/
Thanks for one’s marvelous posting! I genuinely enjoyed reading it, you will be
a great author. I will remember to bookmark
your blog and will come back in the foreseeable future.
I want to encourage you continue your great posts, have a nice afternoon!
Medication information. Cautions.
generic neurontin
Actual about drug. Get information now.
Pills information leaflet. Brand names.
neurontin order
All about medicines. Get information here.
persuasive essay writing service writing an introduction for a research paper vetting caught using essay service reddit
Medicines prescribing information. Cautions.
tadacip buy
Actual information about medicines. Get information now.
Heya i’m for the first time here. I found this board
and I find It truly useful & it helped me out much.
I hope to give something back and help others like you helped me.
Голосообразующий аппарат цена
Hi there to every single one, it’s actually a nice for me to go to
see this web page, it consists of precious Information.
Remarkable! Its genuinely awesome post, I have got much clear idea
regarding from this piece of writing.
Many thanks. Very good information!
Medicament information sheet. What side effects can this medication cause?
buying prednisone
Best what you want to know about meds. Read information here.
Medication prescribing information. What side effects can this medication cause?
bactrim buy
Some what you want to know about medicament. Read now.
Medicines prescribing information. Cautions.
silagra
All news about medicine. Get information here.
Medicines prescribing information. Drug Class.
maxalt medication
Everything what you want to know about medicament. Get here.
Medication information for patients. Cautions.
buy generic cipro
Actual about medicament. Get now.
Pills information for patients. Long-Term Effects.
order singulair
All about medicament. Read here.
hi!,I like your writing so so much! share we
communicate extra about your article on AOL? I need a specialist in this space to resolve my problem.
Maybe that is you! Taking a look forward to peer you.
Авторитетное сообщение 🙂 , познавательно…
Vogue Images is a style which is devoted to displaying clothes and other trend objects. Summary pictures appears to be an elusive topic, https://elastizell.com/2018/06/elastizell-ef-permits-embankments-roadways-and-runways-to-be-heightened-widened-and-lengthened-over-marshy-soils/ laborious to nail all the way down to a single definition.
Medicament information for patients. Long-Term Effects.
viagra
Some about medication. Get here.
Drugs information sheet. What side effects?
levaquin
All trends of pills. Read here.
Статейное и ссылочное продвижение.
В наше время, фактически каждый человек пользуется интернетом.
С его помощью можно найти любую
информацию из разных интернет-источников и поисковых систем.
Для кого-то собственный
сайт — это хобби. Однако, большая часть применяют разработанные проекты
для дохода и привлечение прибыли.
У вас есть личный сайт и вы желаете привлечь на него максимум посетителей, но не понимаете с чего
начать? Обратитесь к нам! Мы поможем!
как получить обратную ссылка
Какие замечательные слова
по 4000 Р ежемесячно пятиклассник разговаривает не без; учителями онлайн, верстальщик сайтов обучение с нуля зарабатывает оценки а также объяснении для семейным работам.
Medicament prescribing information. What side effects?
buy generic ampicillin
Actual about medicines. Read here.
Meds information sheet. Brand names.
viagra
All trends of drugs. Get information now.
Piece of writing writing is also a fun, if you know then you can write otherwise it is complex
to write.
Here is my web-site … http://connerbzdd105zdrowie2022.almoheet-travel.com/zastanawiasz-sie-jak-skorzystac-z-funkcji-zdjecia-online-to-proste-mozesz-zamawiac-online-zdjecia-za-pomoca-rozbudowanego-panelu-internetowego
Drugs information for patients. Cautions.
neurontin
Some news about medication. Read information here.
Идеальный ответ
http://www.whitepinestudio.com/wps-logo/ и еще несколько доменов, таких как.
Drug prescribing information. Cautions.
zyban cost
Actual news about medicament. Read information now.
Having read this I believed it was really enlightening.
I appreciate you spending some time and effort to put this content together.
I once again find myself personally spending a lot of time
both reading and commenting. But so what, it was still worth
it!
Medicines information leaflet. Short-Term Effects.
norpace
Some what you want to know about medicament. Read information here.
Hello my friend! I want to say that this post is
amazing, great written and include almost all vital infos.
I’d like to look more posts like this .
Thanks on your marvelous posting! I certainly enjoyed reading it, you will be a great author.I will remember
to bookmark your blog and definitely will come back in the foreseeable future.
I want to encourage one to continue your great work, have a nice afternoon!
Medication information leaflet. Short-Term Effects.
cost lyrica
All about medication. Read now.
Демонтаж стен Москва
Демонтаж стен Москва
Это условность, ни больше, ни меньше
По полномочия обновляю http://music-salon.com/multi2/multi2.cgi. Ну в чем дело? исполнение) бывалых – счастья! Естественно колоссальным преимуществом Париматч являет достижимость пополнения невпроворот через терминалы.
Drug information. Cautions.
pregabalin
Everything news about medicine. Get now.
Drugs information for patients. Effects of Drug Abuse.
promethazine medication
Some news about drug. Read now.
Извините за то, что вмешиваюсь… Но мне очень близка эта тема. Могу помочь с ответом. Пишите в PM.
If you’re going to begin a new https://www.carookee.de/forum/Retinoblastom-Forum/32269737?mp=247215794649ffadc6c8639dfc5df664cdcab4414944af35c122d6&mps=Re%3A+Ten+Good+Uses+for+Garden+Accessories#32269737 otherwise you need to beat your rivals, then it’s good to work in a different way and will comply with a method.
Medicament information sheet. Long-Term Effects.
levitra
Everything what you want to know about drugs. Read here.
Drugs prescribing information. Long-Term Effects.
viagra
Actual what you want to know about pills. Read here.
Drugs information sheet. Effects of Drug Abuse.
maxalt
Everything trends of drugs. Read information here.
billionaire fake casino
Medicine prescribing information. What side effects can this medication cause?
glucophage
Actual news about medicament. Read now.
Medicines information for patients. Generic Name.
neurontin
Everything trends of drugs. Read here.
Drug information leaflet. Effects of Drug Abuse.
amoxil online
Actual information about drugs. Read now.
Meds information sheet. Drug Class.
propecia rx
Best what you want to know about medicine. Read here.
Howdy! Do you know if they make any plugins to help with Search
Engine Optimization? I’m trying to get my blog to rank for some targeted keywords but I’m
not seeing very good success. If you know of any please share.
Thanks!
Medicine information for patients. What side effects?
buy singulair
All what you want to know about medicines. Read now.
Hi there, I enjoy reading all of your post. I wanted to write a little comment to support you.
Medicament information for patients. Effects of Drug Abuse.
prozac
Actual news about drug. Get information now.
Add more a number of meaningful keywords and phrases and you will definitely have followers http://www.italian-style.ru/Nasha_kompanija/forum/?PAGE_NAME=profile_view&UID=43927 right away!
Drug information leaflet. What side effects?
cipro tablets
Some trends of medicines. Get information now.
Drugs prescribing information. Brand names.
lisinopril
Best news about medication. Get here.
Medicines information leaflet. Generic Name.
zyban pill
Some trends of medicines. Get information here.
If you are going for most excellent contents like myself, simply go
to see this site daily for the reason that it gives feature contents, thanks
Meds information leaflet. Brand names.
cephalexin without rx
Actual about pills. Get information here.
Далее наша завод производит http://estudiodeguitarra.com/2023/04/19/hola-mundo/ числом масштабам, тот или другой находились указаны, навалом слаженному также подтвержденному плану.
Hello, just wanted to say, I enjoyed this article. It was
funny. Keep on posting!
Medicines information leaflet. What side effects can this medication cause?
can you buy silagra
Some trends of meds. Read now.
Medicine information leaflet. Cautions.
zoloft sale
Everything news about medicament. Get information here.
Thank you for the good writeup. It in fact was a amusement account it.
Look advanced to far added agreeable from you!
By the way, how could we communicate?
Here is my web page :: https://raindrop.io/sulainoirx/bookmarks-35718480
Medicines information for patients. Drug Class.
propecia
Some what you want to know about medicament. Read information here.
You ought to take part in a contest for one of the finest blogs on the internet.
I will recommend this web site!
Medicines information sheet. Drug Class.
amoxil price
Everything information about meds. Read here.
Meds prescribing information. What side effects?
mobic sale
Some about pills. Get now.
Medicines information leaflet. Short-Term Effects.
colchicine
Best what you want to know about medicament. Get information here.
Pills information. Effects of Drug Abuse.
buy ampicillin
Everything what you want to know about drug. Get information now.
Hi, yeah this paragraph is genuinely nice and I have learned lot of things from it on the topic
of blogging. thanks.
Check out my web blog … https://we.riseup.net/kevalaewbk
To know the way the selection of suppliers will be made efficiently, http://1whois.ru/?url=www.chambers.com.au%2Fforum%2Fview_post.php%3Ffrm%3D3%26pstid%3D2205%26pstcl%3D0%26kwd%3D%26page_rtn%3D217 it is important that you’ll look at every possible aspect accessible.
Meds information sheet. Drug Class.
xenical
All information about pills. Read here.
Spot on with this write-up, I absolutely feel this site needs much more attention. I’ll probably be returning
to see more, thanks for the info!
Hey There. I discovered your weblog the use of msn. This is a really neatly written article.
I’ll make sure to bookmark it and return to learn extra of your helpful information. Thank you for the post.
I’ll certainly comeback.
Medication information sheet. Drug Class.
proscar
Some information about medicament. Get information now.
This is nicely said! !
My web page: https://smolensck.ru/smln-orginfo-1796.html
Meds information sheet. Brand names.
norvasc
Everything news about medicine. Read information now.
Great weblog right here! Additionally your website a lot up very fast!
What web host are you using? Can I am getting your affiliate link on your host?
I want my website loaded up as fast as yours lol
But they proved to be unruly staff, and the thought of hiring ladies for their more soohing voices was introduced.
Here is my blog 업소알바
Great site! I recommend it for viewing!Antminer usaMiners are in stock in the USA. Worldwide delivery. The warranty for miners is 1 year
Drugs information sheet. Short-Term Effects.
zyban
Best trends of drugs. Get information now.
Online casinos receive become progressively pop in recent years, and the Joined Realm is no exclusion. With a flourishing keep down of online casinos in the UK, players immediately take more than options than ever so earlier.
Peerless of the paint benefits of online casinos is appliance. Players canful delight their best-loved gambling casino games from the comfort of their ain home, without having to locomote to a strong-arm cassino. This makes online casinos an nonsuch pick for players WHO survive Army for the Liberation of Rwanda forth from a gambling casino or WHO don’t throw the clock time to visit nonpareil.
Another benefit of online casinos is the all-encompassing sort of games on offer up. Online casinos fling everything from classic prorogue games equal Jolly Roger and line roulette to the a la mode video slots and reformist jackpots. This means that players give the sack easily come up games that lawsuit their tastes and preferences.
In addition, many online casinos offer bonuses and promotions to attract new players and maintain existent ones approaching rearward. These fanny admit welcome bonuses, unloosen spins, and trueness rewards. Players should forever translate the terms and conditions of these offers to pretend certainly they sympathize the wagering requirements and whatsoever early restrictions.
When choosing an online casino, players should forever constitute indisputable that the locate is licenced by the UK Gaming Commission. This ensures that the gambling casino is operating legally and that players are saved. Players should besides tone for casinos that wont reputable computer software providers to secure that the games are bazaar and random.
Overall, online casinos possess become a pop pick for players in the UK. With their convenience, wide-eyed vagabond of games, and attractive bonuses, they put up a eager option to traditional brick-and-trench mortar casinos. As retentive as players take a licensed and reputable casino, they throne savour a dependable and gratifying gambling experience from the solace of their ain household.
Pills information for patients. What side effects can this medication cause?
xenical generic
Best about medicament. Read now.
Medicament information sheet. Short-Term Effects.
levitra otc
Some trends of pills. Read here.
Hi there friends, nice post and pleasant urging commented at this place, I am truly enjoying by these.
Also visit my web blog – https://atavi.com/share/w5afoqz168t43
Asian girls are most most likely to be person contributors at 73 percent.
Here is myy homepage – 여성밤 알바
Amazing issues here. I am very satisfied to look your post.
Thank you so much and I am looking forward to contact you.
Will you kindly drop me a mail?
my web blog; https://www.instapaper.com/read/1617612772
Meds information sheet. Drug Class.
provigil
Everything news about medicament. Read information here.
Medicines prescribing information. Long-Term Effects.
generic female viagra
All information about drug. Read information here.
I think the admin of this site is genuinely working hard for his site, for the reason that here every
material is quality based material.
Drug information for patients. Drug Class.
tadacip
Best about medicine. Get information here.
Pills information for patients. What side effects can this medication cause?
norvasc
Actual what you want to know about drug. Get here.
Drug information leaflet. What side effects?
eldepryl order
All trends of medicament. Read information here.
Drugs information for patients. Short-Term Effects.
promethazine no prescription
Best about medicines. Get now.
It’s not my first time to visit this site, i am visiting this website dailly
and obtain fastidious data from here all the time.
Pills information for patients. Drug Class.
zithromax
Best what you want to know about medication. Read information here.
Drug information leaflet. Cautions.
lisinopril
Everything trends of medication. Read information here.
Hi there would you mind stating which blog platform you’re using?
I’m going to start my own blog in the near future but I’m having a
tough time choosing between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design seems different
then most blogs and I’m looking for something completely
unique. P.S Sorry for being off-topic but I had to ask!
Also visit my blog post: calendario lunar 2024
Medicine information sheet. Long-Term Effects.
female viagra for sale
All trends of medicament. Read information here.
can you buy prednisone over counter
https://neww.tw/kp-history/
Medication information leaflet. What side effects can this medication cause?
cytotec
Best about medication. Get here.
finasteride 5
Medicament information sheet. Cautions.
provigil buy
Everything what you want to know about pills. Get information here.
лимонад с цедрой
Wonderful beat ! I wish to apprentice while you amend your website, how can i subscribe for a blog website?
The account aided me a acceptable deal. I had been tiny bit acquainted
of this your broadcast offered bright clear concept
Wonderful web site. A lot of useful info here. I’m sending
it to some pals ans additionally sharing in delicious.
And naturally, thanks to your effort!
Also visit my page :: https://chancesgrs123zdrowie2022.wordpress.com/2023/06/29/potrzebujesz-taxi-bagazowego-w-szczecinie-nie-ociagaj-sie-znajdz-profesjonalne-uslugi-taxi-bagazowego-w-szczecinie/
Medication prescribing information. Effects of Drug Abuse.
order sildigra
All about medicine. Get now.
My coder is trying to convince me to move to .net from PHP.
I have always disliked the idea because of the costs. But he’s tryiong none the less.
I’ve been using Movable-type on several websites for about a year and am worried about switching to another
platform. I have heard excellent things about blogengine.net.
Is there a way I can transfer all my wordpress content into it?
Any help would be really appreciated!
antibiotics amoxicillin
Pills information leaflet. Generic Name.
order prednisone
Everything news about medication. Get information now.
Good article! We will be linking to this great content on our website.
Keep up the great writing.
Here is my blog post https://katalogfirm-pl.eu/
Hello mates, how is the whole thing, and what you wish for to
say on the topic of this piece of writing, in my view its really amazing in support of me.
buy finasteride online
Great site! I recommend it for viewing!Antminer usaMiners are in stock in the USA. Worldwide delivery. The warranty for miners is 1 year
I know this website presents quality dependent posts and additional material, is there any other website which offers these kinds of information in quality?
Good info. Lucky me I ran across your blog by accident (stumbleupon).
I’ve saved as a favorite for later!
Medicines information for patients. Long-Term Effects.
eldepryl cost
Best information about medication. Get information here.
The sport has been evolving for decades, and
various expert MMA organizations are on the radar of prominent sportsbooks.
Feel free to surf to my web page … 토토친구
Thanks for sharing your thoughts about a. Regards
para que sirve ciprofloxacino
After I originally commented I appear to have clicked the -Notify me when new
comments are added- checkbox and from now on each
time a comment is added I get four emails with the exact same comment.
Is there a way you are able to remove me from
that service? Thanks!
In 2012, 43% of part-time men had been 16 to 24 years old, compared wwith 29% of women.
my homepage: 텐카페알바
What’s up to all, the contents existing at this website are in fact awesome for people knowledge, well, keep up the nice work fellows.
Новости экономики на Смоленском портале. Архив новостей. одна неделя назад. 1 страница
Drug information leaflet. Long-Term Effects.
motrin
Best information about medication. Read now.
trazodone class
Medicines information. What side effects?
baclofen medication
Some information about medication. Get here.
This is a topic which is close to my heart…
Thank you! Where are your contact details though?
order generic levaquin pills
Its like you read my mind! You appear to know a lot about
this, like you wrote the book in it or something.
I think that you could do with some pics to drive the message home a bit, but other than that, this is magnificent blog.
A fantastic read. I’ll definitely be back.
lisinopril 10 mg buy
Drug information. Effects of Drug Abuse.
synthroid generic
All information about meds. Read now.
Hello, I would like to subscribe for this website to get most recent updates, therefore where can i
do it please assist.
Have you ever thought about including a little bit more than just your articles?
I mean, what you say is important and all. But think about if you added some great visuals or videos to give
your posts more, “pop”! Your content is excellent but with pics and videos, this site
could undeniably be one of the very best in its niche.
Excellent blog!
Here is my site – http://francisconpsb539zdrowie.tearosediner.net/szukasz-szybkiego-transportu-mebli-w-szczecinie
Medicines information sheet. Brand names.
seroquel online
All news about medicines. Get here.
рак крови
This is the perfect webpage for everyone who wants to understand
this topic. You know a whole lot its almost tough
to argue with you (not that I really would want to…HaHa).
You definitely put a fresh spin on a subject which has been discussed for decades.
Excellent stuff, just excellent!
Medication information. What side effects?
cost of zenegra
Actual what you want to know about medicines. Get information here.
Hello mates, its impressive piece of writing about tutoringand
completely explained, keep it up all the
time.
Here is my web-site https://e-gov.betha.com.br/basefly01022/requisitos.jsp?url=https://firmowykatalog.eu/
rx albuterol
Moderator – Nice Article! Traffic analysis of a packet capture with Wireshark • Allhacked read this
купить фаллоимитатор с поступательными движениями: https://pornopda.xyz/shop/seks_igrushki/falloimitatori/
– Новые ощущения и удовольствие от секса с фаллоимитатором со поступательными движениями вы можете получить, купив его у нас.
order prasugrel
Medication information leaflet. Brand names.
fluoxetine cheap
Everything what you want to know about medicines. Get here.
colchicine canada
If some one needs expert view concerning running a blog then i propose him/her to visit this webpage,
Keep up the nice work.
If you bet on the underdogs they either will need to win the
game or shed by fewer points than the spread.
Feel free to surf to my web site :: toto79.org
Medicines information sheet. Short-Term Effects.
zithromax sale
Actual information about drug. Get here.
Новости науки на Смоленском портале. Последние новости. 1 страница
Medication information for patients. Cautions.
propecia price
Some trends of drug. Read information now.
Hey are using WordPress for your blog platform? I’m new to the
blog world but I’m trying to get started and create my own. Do you need any
html coding expertise to make your own blog? Any help would be greatly appreciated!
If you would like to increase your experience only keep visiting this web site and be
updated with the newest gossip posted here.
lisinopril online purchase
Meds prescribing information. Long-Term Effects.
cipro tablet
Some trends of drugs. Read information here.
Fantastic beat ! I would like to apprentice while you amend your website, how could i subscribe
for a blog web site? The account helped me a acceptable deal.
I had been tiny bit acquainted of this your broadcast provided
bright clear idea
You need to be a part of a contest for one of the highest quality
sites on the internet. I am going to recommend this web site!
You stated this perfectly.
my web blog … https://lisinopril24us.top
prednisone for sale
Howdy just wanted to give you a brief heads up and let
you know a few of the pictures aren’t loading properly.
I’m not sure why but I think its a linking issue.
I’ve tried it in two different internet browsers and both show the same outcome.
You should take part in a contest for one of the highest quality sites on the internet.
I am going to highly recommend this website!
cipro 250 mg
Drug information. Long-Term Effects.
sildigra cheap
Best about meds. Read information now.
I do accept as true with all the ideas you have introduced in your
post. They are very convincing and can certainly work. Nonetheless, the posts are very
short for novices. May you please prolong them a bit from subsequent time?
Thanks for the post.
Meds information leaflet. Short-Term Effects.
get tadacip
Everything what you want to know about medicine. Get information here.
Pills prescribing information. Generic Name.
rx lyrica
All information about drugs. Read information now.
Medicine prescribing information. Effects of Drug Abuse.
neurontin
Actual trends of medicament. Read now.
Hey! Someone in my Myspace group shared this website with us so I came to take
a look. I’m definitely enjoying the information. I’m book-marking and will be tweeting this to my followers!
Fantastic blog and wonderful style and design.
Take a look at my homepage :: https://element.lv/go?url=https://spisfirmonline.eu/
trazodone pharm class
Medicament information leaflet. Long-Term Effects.
neurontin for sale
Some about medicines. Get now.
娛樂城推薦
Drugs information sheet. What side effects can this medication cause?
celebrex
Some trends of medicine. Read here.
Medicine information. Short-Term Effects.
sildigra medication
All what you want to know about drugs. Get information here.
Quality posts is the crucial to be a focus for the visitors to pay a quick visit the site, that’s what this
web page is providing.
Meds information sheet. What side effects can this medication cause?
nolvadex
Best information about meds. Read here.
Medicines information sheet. Short-Term Effects.
amoxil
Some information about drugs. Get here.
Ι got whаt yyou mean,saved to fav, veгу nice weeb site.
Drugs prescribing information. Cautions.
lyrica without insurance
Everything trends of medication. Read information here.
Wow that was odd. I just wrote an extremely long comment but after I clicked submit my comment didn’t appear.
Grrrr… well I’m not writing all that over again. Anyhow, just wanted to
say fantastic blog!
Pills information sheet. What side effects can this medication cause?
abilify generics
All trends of meds. Get information now.
actos medication guide
Pills information. Long-Term Effects.
singulair cheap
Everything information about meds. Get information now.
Pills information sheet. Drug Class.
zenegra medication
Actual what you want to know about medicine. Get information here.
Medicine prescribing information. Drug Class.
where buy lyrica
Actual information about drugs. Read here.
doxycycline hyclate treats what infections
Hello! I’ve been following your weblog for a while now and
finally got the courage to go ahead and give you a shout
out from New Caney Tx! Just wanted to tell you keep up the fantastic
job!
Medicament information sheet. Drug Class.
trazodone generics
All information about medicament. Read information now.
At the moment, only these 5 states have access
to legal, regulaterd on the weeb casinos.
Feel free to surf to my blog :: webpage
Slots Empire iis set to capture your interest witfh its gorgeous style and mythological method.
Also visit my web blog :: 카지노친구
Medicine prescribing information. Drug Class.
cipro medication
Some about medicine. Read information now.
No racism, sexism or any sort of -ism
Feel free to surf too my web-site :: web page
Medication information sheet. Effects of Drug Abuse.
norvasc cost
Best information about pills. Read now.
Players can also take benefit off a one hundred% initial (crypto-only) match up
to $1,000 with a 14x playthrough for slots, specialty games, and tablke games.
Here is mmy web blog … 바카라추천
It goes devoid of saying that those applying for thdir initial loan could not have a credit history.
Loook at my webpage: 월급 실수령액 계산기
casino hacks tips to win
Pretty section of content. I just stumbled upon your website
and in accession capital to assert that I get actually enjoyed account
your blog posts. Anyway I’ll be subscribing to your augment and even I achievement you access consistently fast.
Drug information. Cautions.
buy synthroid
Best news about pills. Get information now.
casino hacks tips
Hello! I know this is kinda off topic but I’d figured I’d ask.
Would you be interested in trading links or maybe guest authoring a blog article or vice-versa?
My site addresses a lot of the same subjects as yours and I think we could greatly benefit from each other.
If you might be interested feel free to shoot me an email.
I look forward to hearing from you! Awesome blog by the way!
реабилитация инвалидов
Drugs information. What side effects can this medication cause?
celebrex price
Some information about medicines. Read here.
effexor prescribing information
When some one searches for his required thing, therefore he/she wishes to
be available that in detail, so that thing is maintained over here.
Greetings! Very useful advice in this particular post! It’s
the little changes that will make the most important
changes. Many thanks for sharing!
pesticide research essay outline help research paper writer how to start a program to help the homelessness essay
Pills information leaflet. Long-Term Effects.
strattera without a prescription
All information about pills. Read information here.
Right here is a circumstance, you seee that dealer has a “4” opn and following are your cards.
Stop by my page :: website
I was excited to uncover this great site. I wanted to thank you for your
time for this particularly wonderful read!! I definitely appreciated every bit of it and I have you
book marked to look at new things on your web site.
side effects of stopping gabapentin
Pills information. What side effects?
tadacip
Some information about drug. Get here.
Medicines information leaflet. Short-Term Effects.
xenical price
Actual news about medicine. Get information here.
Drugs information. Short-Term Effects.
get viagra
Best information about medicine. Read information now.
I visited several web pages however the audio feature for audio songs current at this website is
actually fabulous.
Here is my homepage … https://www.momentumstudio.com/?url=https://spisfirmonline.eu/
Hello there! This article could not be written any better!
Reading through this article reminds me of my previous roommate!
He always kept talking about this. I will send this article to
him. Fairly certain he’ll have a great read. Thanks for sharing!
My brother recommended I would possibly like this
website. He was entirely right. This post actually made my day.
You can not consider just how much time I had spent for
this information! Thanks!
Medication information for patients. Drug Class.
bactrim
Best what you want to know about medicines. Read information now.
Pills information sheet. Brand names.
cipro medication
Everything news about meds. Get information here.
Medication prescribing information. Brand names.
proscar
Best what you want to know about drug. Get information now.
prednisone 20mg cost
The neural network draws a girl according to the description
Pills prescribing information. Cautions.
proscar
Best information about pills. Get here.
Pills information sheet. Drug Class.
cordarone
Everything trends of meds. Get now.
prednisone precautions
Instagram has actually become one of the best popular social networking sites platforms around the world, along with numerous customers discussing their images, online videos, and stories on a daily basis. Whether you’re a specific hoping to expand your individual brand or even a company trying to boost your online presence, gaining more followers on Instagram is actually crucial, https://worldigram.wixsite.com/home.
Pills information sheet. Cautions.
provigil
Actual what you want to know about meds. Get information here.
Medication information for patients. What side effects?
generic trazodone
Everything about drugs. Get here.
They’ll match just about ever qualifying transaction byy 25%, giving you a maximum of
$250 further.
my homepage; 바카라사이트
Drug prescribing information. Short-Term Effects.
zenegra for sale
All information about medication. Get information now.
Medicines information leaflet. Long-Term Effects.
lisinopril
Best about pills. Read now.
does prednisone make you sleepy
Drugs prescribing information. What side effects?
finpecia
Best what you want to know about medicine. Get information here.
Good e-book. Nevertheless I did returned it due to being so expensive and discovering out that
I was capable of get an older version of this e book for my bio class which meant cheaper.
Except your professor requires you to have the most recent version, save your cash
and go along with an older version. To make use of this program
you must have some textual content file in RAM for this system to format.
She contributes to the brand new Directions, New Careers Program at Holyoke Community School by funding a staffed
drop-in heart and by offering a number of full-tuition scholarships every year for women who are returning to varsity after a hiatus
or attending school for the first time and who could be unable to proceed their research with out financial help.
Recognizing the severe nationwide scarcity of nursing school, she underwrites the Nursing Students of the
future Grant Program at the college. Nationwide Institutional Ranking Framework.
Full. If the full subkey isn’t present, then you don’t have .Web Framework 4.5 or later installed.
To that end, whereas persevering with to show full time, Dr.
Marieb pursued her nursing schooling, which culminated
in a Grasp of Science diploma with a clinical specialization in gerontology from the College of Massachusetts.
Кофе в зернах jardin crema
Hey there, I think your site might be having browser compatibility
issues. When I look at your blog site in Safari,
it looks fine but when opening in Internet Explorer,
it has some overlapping. I just wanted to give you a quick heads up!
Other then that, excellent blog!
Medication information sheet. What side effects can this medication cause?
generic flagyl
Everything about medicines. Read now.
For your security and safety, we only list sportsbook operators and casinos that are state-authorized and
regulated.
Feel free to surf to my site :: webpage
So if you are aiming for the silent headshot, casino admiral you’d higher hope you don’t miss. It additionally has the flexibility to patch into safety and site visitors cameras, to point out you fascinating components of the level.
Drugs prescribing information. Drug Class.
viagra soft medication
Best trends of medication. Get now.
чтобы будующего партнерства прочерчивается мелковатый аудит, http://forum.omnicomm.pro/index.php?action=profile;u=9427 разрешающий рассчитать примерную курс на водящееся. все-таки в корне ловок выказывать подмога в умножении производительности ресурса.
Meds information for patients. What side effects?
zoloft
Some about pills. Read information here.
Medicine information leaflet. Drug Class.
norvasc buy
Best about medicament. Get now.
Medicine information sheet. What side effects can this medication cause?
sildigra buy
Some what you want to know about medicament. Read now.
Материал производят из целлюлозы, http://www.newvative.com/2019/02/11/elementor-400/ принятою из стебля бамбука. Уникальность небиологического текстиля: еще получи этапе создания изготовители имеют все шансы предрешить полезные свойства мануфактуры.
кредит кредитная карта
Beyond fajous American sports, you can bet on more than 20 other niche events like darts and volleyball.
Have a look at my homepoage Online Gamble Site
Pills information leaflet. Brand names.
valtrex
Best news about drug. Get now.
Отличный сайт! Всем рекомендую!Эротический массаж в Сочи
2. IIT coaching requires many efforts, http://ufa4g.com/activityBoard/410 serious focus with no disruptions. Take under consideration getting frequent training instruction with regard to IIT JEE planning. These variables normally are very properly provided by the web coaching. Mice are greatest controlled by making certain they do not get to the house in the first place. There are a lot of essential gadgets that can develop into taken into account to arrange for IIT exams. 1. It is definitely you could obtain success in the finest instructional field of IIT. Dad and mom must participate in their own child’s preparation discovering out routines so that their baby won’t face difficulties. The right approach to complete IIT JEE planning and put collectively throughout section with regard to best preparation for the examination. 4. IIT JEE is extraordinarily challenging and wishes right counseling. The level of IIT examination is equivalent to a nationwide diploma, it is essential to organize for this examination by utilizing present check papers & query papers of final ten years.
Nice blog right here! Additionally your web site so much up very
fast! What host are you the use of? Can I get your associate hyperlink on your host?
I want my website loaded up as quickly as yours lol
Medication information sheet. Effects of Drug Abuse.
lioresal
Best news about drug. Get information now.
Pretty section of content. I just stumbled upon your weblog and
in accession capital to assert that I get actually enjoyed account your blog posts.
Any way I’ll be subscribing to your feeds and even I achievement you access consistently quickly.
Hey! I understand this is kind of off-topic however I needed to
ask. Does operating a well-established website like yours require a massive amount work?
I’m completely new to writing a blog but I do write in my journal every day.
I’d like to start a blog so I can share my own experience and views
online. Please let me know if you have any ideas
or tips for brand new aspiring blog owners.
Appreciate it!
Medicines information sheet. Generic Name.
viagra soft tablet
Best about medicines. Get information now.
Pills information leaflet. What side effects can this medication cause?
lyrica rx
Everything news about meds. Read now.
With thanks, Valuable information.
Here is my homepage: https://www.sc0796.cn/home.php?mod=space&uid=303754&do=profile&from=space
Thank you a lot for sharing this with all of us you actually know what you are speaking approximately!
Bookmarked. Please additionally visit my web site =). We will have a link alternate contract among
us
fluoxetina para que sirve
Hey very nice blog!
Hurrah! At last I got a blog from where I can in fact get valuable facts regarding my study and knowledge.
Medicine information for patients. What side effects?
levitra
Actual what you want to know about medication. Get here.
Порно по категориям (davalka.pro)
Hi, i think that i noticed you visited my web site so
i got here to return the desire?.I’m attempting
to in finding issues to enhance my site!I suppose its good enough to use some
of your ideas!!
fluoxetine bnf
Отличный сайт! Всем рекомендую!Эротический массаж в Сочи
I am now not certain the place you’re getting your info,
however good topic. I must spend some time studying more or figuring out
more. Thank you for great info I was in search of this info for my mission.
Peculiar article, totally what I was looking for.
Medicines information leaflet. Cautions.
cephalexin
Actual trends of meds. Read here.
Howdy! Someone in my Facebook group shared this site with
us so I came to check it out. I’m definitely loving the information. I’m
bookmarking and will be tweeting this to my
followers! Wonderful blog and outstanding design and style.
Whether you need to write your individual copy or get somebody who can do it for you, Search engine marketing copywriting requires you to have seo knowledge, https://www.bobi11.com/24555.html#comment-1081266 because it differs from common writing. When you include extra key phrases in the suitable spots, your web site will acquire a better rating via all the massive search engine names (Google, Yahoo!, and so forth.). Good Search engine marketing copywriting can be laborious to recognize; the underside line is that though it has more power, it seems to the reader as nothing greater than attention-grabbing website content. Attempt implementing the Web optimization tactics that I explained in this article, and observe extra on Hostgator. They could write an incredible article, but it lacks related keywords and optimization, then it’s not going to be very efficient. All in all, should you really need your Search engine optimization efforts to repay and give you good results, then it’s essential to work closely with the copy of your web page and as effectively because the technical components of Seo.
Medication information. What side effects can this medication cause?
rx ampicillin
Everything trends of drug. Read now.
Drugs information leaflet. Effects of Drug Abuse.
cipro
All information about medication. Get now.
Очень полный {ответ}! Большое спасибо.
It’s awesome in support of me to have a site, which is
beneficial in favor of my know-how. thanks admin
protonix for adults
Супер , спасибо забрал!!!
Они и имеют все шансы иметь следствием буква дефекту кровеносных лимфатический сосуд на роговице, что представляет собой тяжелым синдромом, грозящим качеству зрения. На портале допускается не разрешить изделия от OKVision, Alcon, Bausch&Lomb, https://www.artbybagci.com/product/gimli-lord-of-the-rings-signerad-av-john-rhys-davies/ CooperVision да Johnson&Johnson.
Drug information for patients. Generic Name.
seroquel
All trends of medicament. Read information now.
Авторитетное сообщение 🙂 , познавательно…
If you’re a music nerd and determined to not give one other monthly payment to a tech business behemoth, http://www.saglikeczanesi.com.tr/link.php?marka=Kizir%20Software%20Designer&url=react2020.eu%2F2022%2F03%2F31%2Finterview-with-pr-jean-pierre-chabriat%2F it’s a good alternative.
Female leaders in the faith-primarily based nonprofit market reported the loaest
levels of queen bee syndrome, workplace harassment, and salary inequality in compareison to the other three samples.
Here is my homepage :: 마사지알바
Drugs information sheet. Long-Term Effects.
buy zoloft
Actual news about medicine. Read information here.
Medicine prescribing information. Cautions.
propecia without rx
Best trends of medicament. Get now.
Medicines information sheet. What side effects can this medication cause?
generic sildigra
Some trends of medicine. Read information now.
Безусловно, он прав
Пакет із 10 уроків тривалістю 30 хвилин http://www.adpeci.asso.fr/index.php/bonjour-tout-le-monde/ коштує $187. British Council пропонує регулярну підбірку коротких онлайн-курсів, один або два з яких завжди спеціалізуються на бізнес англійській.
Pills information sheet. What side effects?
norvasc
Actual about medicines. Read now.
Hi to all, how is the whole thing, I think every one is getting more from this web site, and your views
are nice for new people.
I have learn several excellent stuff here. Certainly value bookmarking for revisiting.
I wonder how so much attempt you set to create this
type of magnificent informative web site.
онлайн казино
Medicament information leaflet. Brand names.
pregabalin rx
Actual about medicines. Read information here.
Until you will have a primary hand acquaintance with these useful aids to analysis, you cannot hope to do a fast and efficient job of gathering material to your report. Here once more yow will discover data, by title, writer, or topic, about articles which were published in tons of of periodicals. She is knowledgeable at this recreation and might give you invaluable help. Perhaps more necessary than the facts you may get from these common reference works is the titles of further books that are sometimes listed at the end of articles. These are the books, in single or multiple volumes, that provide condensed accounts of any topic you can consider. In case your matter is an extension of a subject studied in class and coated in your textbook, take a look at the end of the chapter that handled the topic. If your topic is the kind about which articles appear in newspapers, magazines, or journals, you could additionally consult the Readers’ Guide, which is a monthly publication later sure into volumes covering one or more years.
Drug information. What side effects can this medication cause?
nolvadex
Everything news about medicine. Read now.
Meds information sheet. Long-Term Effects.
celebrex buy
Best what you want to know about medicines. Read information now.
I love your blog.. very nice colors & theme.
Did you design this website yourself or did you hire someone to do it for you?
Plz reply as I’m looking to construct my own blog and would like to find out where u
got this from. many thanks
Kelly is also an automatic teller machine—one that pulls revenue out of casinos and puts it in her personal coffers.
Here is my web page https://fnote.net/notes/t3mD3X
Meds information sheet. Generic Name.
order levitra
Everything news about pills. Get information now.
cefixime mechanism of action
customer service essay papers top essay writing service college essay help golden co merkmoken
Wonderful goods from you, man. I have bear in mind your stuff previous to and you are simply
extremely fantastic. I really like what you’ve received here, really like what you’re saying and
the way during which you assert it. You’re making it entertaining and you continue to take care of to stay it wise.
I can not wait to learn far more from you. This is really a tremendous website.
Post writing is also a excitement, if you be
familiar with then you can write otherwise it is difficult to
write.
Good post. I learn something totally new and challenging on websites I stumbleupon every day.
It will always be useful to read content from other authors and practice a little something
from other sites.
Wow, this post is fastidious, my younger sister is analyzing these things,
thus I am going to let know her.
Medicament prescribing information. Drug Class.
generic pregabalin
Some about drugs. Get information now.
Нey there I am so happy I found your webpage, I really
found you by erroг, while I wаs researching on Google for something else, Regardless I am here now and would just like to say
kudos for a incredіble poѕt and a all round exciting ƅlog (I also love the
tһeme/deѕign), I don’t have time to go thrоugh it all at the moment but
I have bookmarked it and also added in your RSS feeds, so when I have tіmе I will be back to read a great
deal more, Please do keep up the excellent work.
Medicament information for patients. What side effects?
colchicine price
Everything about drug. Read information here.
These forms of on-line baccarat Online Casino Games can also be categorized according
to their providers.
Medication information sheet. Long-Term Effects.
amoxil rx
Actual trends of drugs. Read here.
Сожалею, что не могу сейчас поучаствовать в обсуждении. Очень мало информации. Но эта тема меня очень интересует.
Disallow: /wp-json/
writing an effective essay i hate writing essays how can tiny homes help save the planet proposal essay
prednisone 1 mg
Drugs information sheet. Brand names.
priligy
Everything trends of pills. Read information now.
First of all I would like to say great blog! I had a quick question that I’d like to ask if you do not mind.
I was interested to know how you center yourself and clear
your head prior to writing. I’ve had difficulty clearing
my thoughts in getting my thoughts out there. I do enjoy writing but it just seems like
the first 10 to 15 minutes tend to be wasted just trying to figure out
how to begin. Any suggestions or tips? Appreciate it!
Drug information sheet. Cautions.
propecia buy
Everything trends of medicine. Get now.
Despite the fact that she loved the outings, Beca says she is going to take a break from courting apps for a while. However even though Beca’s date wasn’t upset concerning the TikTok she posted that ended up going viral, the two soon called it quits. She immediately took to TikTok after the date to element what occurred while sobbing. Nonetheless, Beca was shocked by how a lot she appreciated her love interest while she was out enjoying a second date with him. She continued to clarify that while her date was staring into her eyes, she assumed he would inform her that she’s pretty. I just went on a date and i simply got violently humbled by the guy,’ she mentioned. Beca even confessed that she went on to pop his spots in return on their third date collectively. A lady has been left in tears after her Hinge date requested to pop one among her spots during their date.
Great delivery. Sound arguments. Keep up the good effort.
Excellent blog here! Also your web site loads up
very fast! What web host are you using? Can I get your affiliate link to
your host? I wish my web site loaded up as quickly as yours lol
Pills information sheet. Brand names.
prednisone
All about drug. Get information now.
Drug information leaflet. Drug Class.
norvasc price
Some news about medicines. Read information now.
Hi there, all is going fine here and ofcourse every one is sharing
information, that’s really excellent, keep up writing.
Sgt. Frog: Aki Hinata finds slimy, squishy things adorable and squees at the thought of Keroro’s race secretly being hideous pudding monsters or something. He thought it was superior, and protested being reworked back to normal.
Also visit my web page: https://Www.Themirch.com/author/carolinecor/
Having read this I thought it was rather informative.
I appreciate you taking the time and effort to put this
content together. I once again find myself personally spending way
too much time both reading and posting comments.
But so what, it was still worth it!
Drugs prescribing information. What side effects?
cephalexin prices
Everything trends of medicines. Read now.
Drug information sheet. Short-Term Effects.
cialis soft cost
Some news about medication. Get here.
If some one wіshes expert view regarding blogging afterward i suggеst him/her to
pay a quick visit this bⅼog, Keep up the good јob.
Understand the benefits of proxy servers with this insightful article on IGeeKphone.
Ремонт квартир и помещений в Красноярске
Ремонт квартир и помещений в Красноярске
doxycycline generi
Medicament prescribing information. Effects of Drug Abuse.
sildigra cheap
Some what you want to know about meds. Get information now.
can i buy levaquin without a prescription
Drugs prescribing information. Effects of Drug Abuse.
priligy
All news about medication. Get now.
Drug information for patients. Brand names.
sildigra
Best information about medication. Get information here.
Hello friends, how is all, and what you want to say on the topic of this
article, in my view its in fact awesome in favor of me.
ashwagandha reddit
Pills information. Effects of Drug Abuse.
zithromax generics
Some what you want to know about drugs. Read information now.
Pills information leaflet. Effects of Drug Abuse.
buy pregabalin
Everything information about drugs. Read information here.
cordarone medication
I have to thank you for the efforts you have put in writing this website.
I am hoping to check out the same high-grade
blog posts by you in the future as well. In fact, your creative writing abilities has motivated me to get my own site now 😉
Thanks a lot, Awesome information!
buy cheap levaquin without rx
Drugs information for patients. What side effects can this medication cause?
synthroid
All trends of medicines. Get information here.
It’s likely you’ll meet attention-grabbing and entertaining adults
in our video chat rooms.
В этом что-то есть. Теперь всё понятно, благодарю за информацию.
These printers expertise mechanical http://chimneysweepscostedmonton.theburnward.com/laptop-repair-calgary and electrical faults. The machine should not be tampered with at any second faults show.
Medicines prescribing information. Generic Name.
cialis
Best information about medicine. Get information here.
Meds prescribing information. Effects of Drug Abuse.
cipro medication
Some news about drugs. Get information here.
Hey very interesting blog!
Medicines information. Cautions.
propecia generics
Everything trends of medication. Read information now.
Pills information. Drug Class.
zithromax
All trends of meds. Read now.
Выбор у Вас непростой
К образчику, на ваше усмотрение – определенное число разновидностей к фасада – с массы расцветок ПВХ покровы до самого взаправдашнего шпона, https://hardwood.com.ua/stoleshnicy-iz-dereva-na-zakaz/ ради столешниц – гетинакс сиречь синтетический шпинеллан.
Medicament information for patients. Effects of Drug Abuse.
viagra soft medication
All news about medicament. Get now.
рейтинг хостингов бесплатных
With havin so much written content do you ever run into any problems of plagorism
or copyright infringement? My site has a
lot of unique content I’ve either written myself or outsourced but it looks like a lot of it
is popping it up all over the web without my authorization. Do you know any
ways to help protect against content from being stolen? I’d really appreciate
it.
Drugs information for patients. Generic Name.
zithromax buy
Everything what you want to know about medicines. Get information here.
Первая это чтото
Then, at night time or if there’s inclement weather, https://www.esteticainarcisi.it/double-minceur-ciblee/ you should utilize this stored power to minimize how a lot electricity you pull from the grid.
Medicament prescribing information. Long-Term Effects.
cytotec
Everything what you want to know about medicine. Read now.
Meds information leaflet. Cautions.
amoxil buy
All information about medicines. Read here.
We are a group of volunteers and starting a new scheme in our
community. Your website offered us with valuable information to work on. You’ve done an impressive job and our whole community
will be grateful to you.
Советую Вам посмотреть сайт, на котором есть много статей по этому вопросу.
When selecting an Irish on-line on line casino it is essential to look for reliable https://djkikiradio.com/index.php/2020/04/22/paparazzi-demanda-a-jennif/ deposit strategies.
Medicament information. Brand names.
lioresal
All news about pills. Read now.
Medication information leaflet. Drug Class.
neurontin without prescription
Actual information about medication. Get here.
In 1995, Red Bull sponsored its first motorsports team,
the Swiss Formula One team Sauber and in 1999 started sponsoring the Flying Bulls, a Czech aerobatics team.
Gary Smith is one of the co-CEOs of Red Bull. The flavouring used
for Red Bull is still produced in Bangkok and exported worldwide.
In 2012, Red Bull released Red Bull Total Zero, a variant with zero calories.
The company began expanding its flavor offerings in 2013 with
the launch of Red Bull Editions. Peacock, Amy; Martin, Frances Heritage; Carr, Andrea (1 May 2013).
“Energy drink ingredients. Contribution of caffeine and taurine to performance outcomes” (PDF).
Sanchis-Gomar F, Pareja-Galeano H, Cervellin G, Lippi G, Earnest CP (May 2015).
“Energy drink overconsumption in adolescents: implications for arrhythmias and other cardiovascular events”.
As is the case with other caffeinated beverages, Red Bull drinkers may
experience adverse effects as a result of overuse. RePlay.
Vol. 15, no. 8. May 1990. p. The program has multiple locations,
including Detroit, Michigan; São Paulo, Brazil; and formerly New
York City. The program typically consists of a three-month period during which six to eight participants create new artwork to be displayed at a final exhibition.
Here is my webpage https://Www.tiktok.com/
exclusive deals on prednisone
Это верная информация
Курс кроме того укрывает темы, такие как донесения относительный оплошках, информативные источники, https://infologistics.nl/contact-en-koffie/ автоматизация также ветпомощь во решении практических задач.
Wow, this paragraph is fastidious, my sister is analyzing these things, so I am going to let know her.
Meds prescribing information. Drug Class.
synthroid
Everything trends of medication. Read information now.
buying tetracycline
Meds information for patients. Generic Name.
fluoxetine pills
Best news about medicines. Read information here.
GAS SLOT Adalah, situs judi slot online terpercaya no.1 di Indonesia saat ini yang menawarkan beragam pilihan permainan slot online yang tentunya dapat kalian mainkan serta menangkan dengan mudah setiap hari. Sebagai agen judi slot resmi, kami merupakan bagian dari server slot777 yang sudah terkenal sebagai provider terbaik yang mudah memberikan hadiah jackpot maxwin kemenangan besar di Indonesia saat ini. GAS SLOT sudah menjadi pilihan yang tepat untuk Anda yang memang sedang kebingungan mencari situs judi slot yang terbukti membayar setiap kemenangan dari membernya. Dengan segudang permainan judi slot 777 online yang lengkap dan banyak pilihan slot dengan lisensi resmi inilah yang menjadikan kami sebagai agen judi slot terpercaya dan dapat kalian andalkan.
Tidak hanya itu saja, GASSLOT juga menjadi satu-satunya situs judi slot online yang berhasil menjaring ratusan ribu member aktif. Setiap harinya terjadi ratusan ribu transaksi mulai dari deposit, withdraw hingga transaksi lainnya yang dilakukan oleh member kami. Hal inilah yang juga menjadi sebuah bukti bahwa GAS SLOT adalah situs slot online yang terpercaya. Jadi untuk Anda yang memang mungkin masih mencari situs slot yang resmi, maka Anda wajib untuk mencoba dan mendaftar di GAS SLOT tempat bermain judi slot online saat ini. Banyaknya member aktif membuktikan bahwa kualitas pelayanan customer service kami yang berpengalaman dan dapat diandalkan dalam menghadapi kendala dalam bermain slot maupun saat transaksi.
It’s amazing to go to see this website and reading the views of all colleagues about this article,
while I am also zealous of getting knowledge.
Жаль, что сейчас не могу высказаться – вынужден уйти. Но вернусь – обязательно напишу что я думаю.
Обучение базируется нате основе розных модулей несть конкретным задачкам, https://vanocnizavod.radioklub.cz/ а также сверху пошаговых схемах жуть свыше машистым темам.
Medication information sheet. Drug Class.
zoloft medication
All information about medicine. Get now.
Gas Slot
GAS SLOT Adalah, situs judi slot online terpercaya no.1 di Indonesia saat ini yang menawarkan beragam pilihan permainan slot online yang tentunya dapat kalian mainkan serta menangkan dengan mudah setiap hari. Sebagai agen judi slot resmi, kami merupakan bagian dari server slot777 yang sudah terkenal sebagai provider terbaik yang mudah memberikan hadiah jackpot maxwin kemenangan besar di Indonesia saat ini. GAS SLOT sudah menjadi pilihan yang tepat untuk Anda yang memang sedang kebingungan mencari situs judi slot yang terbukti membayar setiap kemenangan dari membernya. Dengan segudang permainan judi slot 777 online yang lengkap dan banyak pilihan slot dengan lisensi resmi inilah yang menjadikan kami sebagai agen judi slot terpercaya dan dapat kalian andalkan.
Tidak hanya itu saja, GASSLOT juga menjadi satu-satunya situs judi slot online yang berhasil menjaring ratusan ribu member aktif. Setiap harinya terjadi ratusan ribu transaksi mulai dari deposit, withdraw hingga transaksi lainnya yang dilakukan oleh member kami. Hal inilah yang juga menjadi sebuah bukti bahwa GAS SLOT adalah situs slot online yang terpercaya. Jadi untuk Anda yang memang mungkin masih mencari situs slot yang resmi, maka Anda wajib untuk mencoba dan mendaftar di GAS SLOT tempat bermain judi slot online saat ini. Banyaknya member aktif membuktikan bahwa kualitas pelayanan customer service kami yang berpengalaman dan dapat diandalkan dalam menghadapi kendala dalam bermain slot maupun saat transaksi
Drug prescribing information. Brand names.
promethazine
Everything what you want to know about medication. Get now.
WOW just what I was looking for. Came here by searching for
slot88
Hey very interesting blog!
Я не мог сопротивляться
от комментариев. Очень хорошо написано!
великим автором. Я убедюсь добавить
ваш блог в закладки и сделаю вернуться позже.
Я хочу побудить себя продолжать вашу
замечательную работу, приятного день!| Благодарность моему отцу, который сказал мне относительно этого веб-страницы, этого блог искренне потрясающе.| Пост также весело, если
вы знаете потом вы можете написать иначе это сложно писать.| когда кто-то ищет
свою существенную вещь, поэтому он/она хочет быть доступной в деталях, таким образом
эта вещь поддерживается здесь.| Спасибо, что
наконец-то написали о > Traffic analysis of a packet capture with Wireshark • Allhacked
< Понравилось это!| Отличная статья, именно то,
что мне искал.| Мой брат предложил Мне может понравиться этот блог.
Он был полностью прав. Этот пост
действительно сделал мой день.
Вы не можете представить просто сколько времени я
потратил на эту информацию!
Спасибо!| Спасибо, что поделились своими
мыслями о организация похорон.
С уважением|Мой брат предложил Мне может понравиться этот веб-сайт.
Он был полностью прав. Этот опубликовать действительно сделал мой день.
Вы не можете поверить просто сколько столько времени я потратил на эту информацию!
Спасибо!| Когда я первоначально комментировал, я установил флажок "Уведомлять меня о добавлении новых комментариев"
, и теперь каждый раз, когда
добавляется комментарий, я получаю три электронных писем с
одним и тем же комментарием.
Есть ли способ удалить меня из этого сервиса?
Спасибо!| Потрясающе! Это на самом деле
потрясающе абзац, у меня есть четкое
представление по теме из этой статьи.|Привет всем, это
мой первый пойти посмотреть этого
веб-сайта; этот веб-страница включает в себя замечательно и действительно прекрасно информация в
пользу посетителей.| Привет всем до единого, это искренне мило для меня быстро посетить
этот сайт, он включает бесценный Информация.|Привет всем,
содержание существующее на этом сайте искренне удивительно для людей
опыт, ну, продолжайте в том же духе, хорошие ребята.| Привет
это я, я также посещаю этот веб-сайт ежедневно, этот веб-сайт действительно милая, а зрители действительно делятся приятные мысли.| Здравствуйте Уважаемый, вы искренне посещаете этот
веб-страницу регулярно, если так
впоследствии вы без сомнения получить хорошо знания.
| Привет я кавин, это мой первый раз комментировать в
любом месте, когда я прочитал эту абзац, я
подумал, что смогу также создайте комментарий в связи
с этой разумной статьей.| Привет товарищи, это фантастически письмо о культура и полностью объяснено, продолжайте в том же
духе все время.| Мне понравилось столько, сколько вы получите прямо здесь.
Эскиз со вкусом, ваш авторский тема
стильный. Тем не менее, вы должны получить купил беспокойство, что вы
хотите сделать следующее. плохо, несомненно,
приходить дальше ранее
снова так как точно так же почти много часто внутри, если вы защищаете это поход.| Привет там каждому, по той причине, что я на самом деле
не терпится прочитать этот веб-блог, который будет обновляться на регулярной основе.
Он несет привередливый данные.| Как дела каждый, здесь
каждый делится этими видами знаниями,
поэтому приятно читать этот веб-блог, и я раньше навестить этот
блог постоянно.|Привет всем, как в целом, я думаю,
что каждый получает больше от этого веб-сайта, и ваши
взгляды хорошие в пользу новых зрителей.|
Я получил этот сайт от моего приятеля, который рассказал со
мной относительно этого веб-страница и сейчас на этот раз я
просматриваю этот веб-сайт и читаю очень информативные контент в это время.|Чтобы получить самые свежие новости, вы должны посетить веб и в интернете
я нашел этот веб-сайт как лучший веб-сайт
для горячих обновлений.| Замечательно, что это за веб-сайт!
Этот веб-сайт представляет полезные факты для нас, продолжайте в том же духе.| Привет товарищи,
привередливо статья и приятно аргументы прокомментировал в этом
месте, я на самом деле наслаждаюсь этим.|Привет товарищи, как всё, и что вы хотите сказать о этой поста,
на мой взгляд, это искренне замечательный в
пользу меня.| Это удивительно в пользу
меня иметь веб-сайт, который хорош в пользу
моего опыта. спасибо админ|потрясающе посетить этот веб-сайт и прочитать
мнения всех друзей по теме этой абзаца, в то время
как я также стремлюсь получаю опыт.|Почему пользователи до сих пор используют для чтения газет, когда в этом технологическом глобусе все доступно в сети?| Привет, да
эта пост на самом деле приятный и я многому научился из него относительно ведения
блога. спасибо.|Привет, все время я проверял блог здесь раньше в
рассвет, по той причине,
что я люблю узнавать больше и многое другое.| Привет всем, это мой первый быстро посетить на
этом сайте и статье действительно плодотворный в пользу меня, продолжайте публиковать
эти статьи.|Привет, эти выходные привередливые для меня,
по причине что в это момент я читаю это впечатляюще информативно абзац здесь,
у себя место жительства.| Привет, всё здесь отлично
и, конечно, все делятся информацией, это действительно отлично, продолжайте писать.| Впечатляющая акция!
Я только что переслал это коллеге который был
проводил небольшое исследование по этот.
И он на самом деле купил мне ужин просто потому, что
открыл это для него… ржу
не могу. Итак, позвольте мне перефразировать это….
Спасибо за за еду!! Но да, спасибо за то, что потратили время для обсуждения
этого вопроса здесь, на вашем интернет-сайте .|
вау, этот вебблог превосходный мне нравится изучаю
ваши посты. Оставайтесь в том же духе, хорошая работа!
Вы уже знаете, многие люди ищут вокруг
за эту информацию, вы можете помочь
им очень.|Привет! Я знаю, что
это немного не по теме однако, я решил спросить.
Вы были бы заинтересованы
в торговле ссылками или, возможно, в гостевом авторстве блога
публикации или наоборот? Мой блог обсуждает многие из тех же предметов, что и ваши, и я верю, что мы могли бы извлечь большую пользу друг из друга.
Если вы, не стесняйтесь стрелять мне электронное письмо.
С нетерпением жду Вашего ответа!
Кстати, Отличный блог!| Этот превосходный веб-сайт действительно содержит все информацию я need об этом предмете
и не знал, у кого спросить.
|Привет, я хочу подписаться на этот веб-блог, чтобы получить самые последние обновления, поэтому где я могу это сделать, пожалуйста, помогите.| Привет, это хорошо абзац
о СМИ, мы все знать средства массовой информации являются великим источником
фактов.| Привет используете WordPress для платформы
вашего сайта? Я новичок в мире блогов,
но я пытаюсь начать и создать
свой собственный. Вам нужны какие-либо html-кодирование знания, чтобы
создать собственный блог?
Любая помощь будет действительно
оценена!|Привет, после прочтения этой замечательной статьи я также счастлив поделиться своим знаниями здесь с товарищами.|Привет Я так рад Я нашел вашу сайт, я действительно нашел вас по ошибке, когда
искал на Yahoo для что-то еще, независимо я сейчас здесь и просто хотел
бы сказать большое спасибо за замечательный пост и полный захватывающий блог (мне также нравится тема/дизайн), у меня нет времени проходить это все в момент, но я сохранил это, а
также добавил ваши RSS-каналы, поэтому, когда у меня
будет время, я вернусь, чтобы прочитать гораздо больше, пожалуйста,
продолжайте в том же духевеликолепный jo.| Привет!
Это мой первый комментарий здесь, поэтому я просто хотел быстро выразить признательность и сказать
вам, что мне искренне нравится читать ваши сообщения в блогах.
Можете ли вы предложить какие-либо другие блоги/веб-сайты/форумы, которые пересматривают те же темы?
Спасибо!|Привет Я так счастлив Я нашел вашу сайт,
я действительно нашел вас по случайности, когда искал
на Aol для что-то еще, в любом случае я сейчас здесь и просто хотел бы
сказать спасибо за изумительный пост и полный развлекательный блог (мне также нравится тема/дизайн), у меня нет времени читать это все в минуту, но я отметил это, а также добавил ваши RSS-каналы, поэтому, когда у меня будет время, я вернусь, чтобы
прочитать много больше, пожалуйста, продолжайте в том же духепотрясающе работа.| По причине того, что администратор
этого веб-сайта работает, нет вопроса очень быстро он будет известным
из-за его качества содержания.| Я пошел сообщить моему младшему брату, что он тоже должен навестить этот веб-страницу на регулярной
основе, чтобы получить обновленные
самые актуальные отчеты.| Привет, я думаю, у
вашего блога могут быть проблемы с совместимостью браузера.
Когда я смотрю на ваш сайт блога в Safari,
он выглядит нормально, но при открытии в
Internet Explorer он частично перекрывается.
Я просто хотел дать вам быстрый головы!
Кроме того, отличный блог!| Мой партнер и я очень любим ваш блог и
считаем, что почти все ваши сообщения что
именно я ищу. можете ли вы предложить приглашенным авторам
написать контент в соответствии с вашими потребностями?
Я был бы не против написать пост или проработать
нескольких тем вы пишете об
здесь. Опять же, потрясающий веб-блог!|Замечательный пост однако мне хочу узнать, не могли бы вы написать немного больше на эту тему ?
Я был бы очень благодарен, если бы вы могли немного подробнее дальше.
Спасибо!| Это идеально сайт для всех, кто хочет узнать о эту тему.
Вы понимаете так много с вами почти трудно спорить (не то, чтобы мне действительно нужно к…
Ха-Ха). Вы определенно придали
свежий оттенок предмету
который был обсуждался
много лет. замечательный материал, просто отличный!| Привлекательный раздел контента.
Я только что наткнулся на
ваш сайт и, вступив в силу, заявил, что приобретаю на самом деле наслаждался вашими сообщениями в блоге.
В любом случае буду подписываться на ваши дополнения, и
даже я добьюсь, чтобы вы получали
постоянный доступ быстро.| Можете ли вы рассказать нам больше об этом?
Я люблю узнать более подробную информацию.| восхищаясь временем
и энергией, которые вы вкладываете в
свой блог, и подробной информацией, которую вы предлагаете .
Это круто время от времени натыкаться на блог, который отличается
от устаревшего перефразированного материала.
Отлично читать! Я добавил в закладки
ваш сайт и в том числе ваши
RSS-каналы в свой аккаунт Google.| Привлекательное
часть контента. Я просто наткнулся на ваш блог и в акционном капитале утвердить, что я приобретаю фактически любимые учитывают ваши сообщения
в вебблоге. В любом случае Я подпишусь на на ваш дополнительный и даже
я достижение вас получить доступ последовательно быстро.| Пожалуйста,
дайте мне знать, если вы ищете автора статьи для своего сайта.
У вас есть несколько действительно отличных постов,
и я думаю, что был бы вам полезен.
Если вы когда-нибудь захотите снять часть нагрузки, я бы люблю написать несколько материалов для вашего блога в обмен на ссылку на мой.
Пожалуйста, отправьте мне электронную почту,
если вы заинтересованы. Спасибо!| Этот информация бесценен.
Как я могу узнать больше?| Я развлекаюсь, приводит к я нашел
только то, что я был ищу. Вы закончили мою 4 дневную долгую охоту!
Да благословит тебя Бог. Желаю
отличного дня. Пока|Что за материал недвусмысленности и сохранности ценного ноу-хау касающегося
неожиданного эмоции.| Хороший пост.
Я узнаю что-то совершенно новое
и бросаю вызов блогам, на которые натыкаюсь ежедневно.
Всегда полезно читать статьи других писателей
и практиковать что-то со своих сайтов.|Это действительно привлекает внимание, вы очень профессиональный блогер.
я присоединился к вашему потоку и буду в курсе ищу больше
ваших фантастических сообщений.
Также, я поделился вашим веб-сайтом в своих социальных сетях|
Великолепно вещи здесь.
я очень рад увидеть вашу
пост. Спасибо большое и я смотрю вперед, чтобы связаться с вами.
Не могли бы вы пожалуйста отправить мне почту?| Симпатичный!
Это было невероятно замечательная пост.
Большое спасибо за предоставление этой информации.|Спасибо, я просто искал информацию о этой теме в течение долгое время
и ваш лучший я обнаружил до сих пор.
Но, что относительно заключения?
Вы положительно насчет снабжения?| Спасибо и много за то, что поделились этим со всеми из нас вы на
самом деле знаете, кто вы говорим приблизительно!
Добавлено в закладки. любезно также
проконсультируйтесь с моим веб-сайтом =).
У нас может быть ссылка альтернативный
контракт между нами|Я не уверен почему, но этот
блог у меня загружается чрезвычайно медленно.
У кого-нибудь еще есть эта проблема или это проблема
на моей стороне? Я вернусь позже и посмотрю, существует ли проблема.| Спасибо за хороший отзыв.
Это на самом деле раньше это развлечение.
Взгляд сложный на более доставленный приятный от вас!
Кстати, как можем мы быть на связи?|
Я мог найти хорошую информацию в ваших статьях.| Спасибо за другую
отличную статью. Где еще может
любой получить этот вид информацию
таким идеальным манера письма?
У меня презентация на следующей неделе, и я в ищите такую информацию.| Спасибо
за то, что поделились своей информацией.
Я действительно ценю ваши усилия и буду ждать ваших следующих написаний спасибо еще
раз.| Я веду блог часто и правильно благодарю вас информацию.
Ваша статья действительно вызвала
у меня пик интереса. Я собираюсь закладка ваш сайт и продолжайте проверять новую информацию о раз в неделю.
Я выбрал ваш канал а также.|
просто хочу сказать, что ваша статья такая же удивительная.
Четкость на вашем выложить
просто круто и что я могу
предполагать вы профессионал в этом предмете.
Ну вместе с вашим разрешением позвольте мне схватить ваш RSS-канал, чтобы держать обновлять с неизбежным сообщением.
Спасибо миллион и, пожалуйста, продолжайте
приятную работу.| Спасибо за каждый другой информативный сайт.
Где еще может просто я получаю этот типа информации, написанной таким идеальным способ?
У меня есть вызов, над которым я
просто сейчас работаю, и у меня
есть были на высматривали
такую информацию.| просто хочу сказать, что ваша статья
такая же поразительная. ясность в вашем
сообщении просто отлично, и я могу
предположить, что вы эксперт в этом вопросе.
Хорошо с вашего разрешения позвольте мне получить ваш канал, чтобы обновлять с предстоящей публикацией.
Большое спасибо и, пожалуйста, продолжайте в том же духе вознаграждающую
работу.| Полезно информация. Повезло мне
я обнаружил ваш веб-сайт случайно,
и я удивлен почему эта случайность не произошла раньше!
Я добавил это в закладки.| Есть
ли у вас спам проблема на этом сайте; Я также
являюсь блоггером, и мне интересно о вашей ситуации; многие из нас разработали некоторые хорошие методы, и мы
ищем обмен решениями с другими, почему бы и нет
пришлите мне электронное письмо,
если интересно.| Это очень интересно, Вы очень опытный блоггер.
Я присоединился к вашему rss-каналу
и с нетерпением жду новых ваших великолепных
сообщений. Кроме того, я поделился
вашим веб-сайтом в своих социальных сетях!| я думаю, что все опубликовали имело тонну смысла.
Но, а как насчет этого? что, если вы добавлено немного информации?
Я не говорю ваш контент не является хорошим, но
что, если вы добавили заголовок сообщения что
привлекло внимание людей?
скучный}. Вы могут заглянуть на домашнюю страницу Yahoo
и смотреть, как они создают статьи заголовки захватить зрителей
открыть ссылки. Вы можете добавить видео
или изображение или два, чтобы захватить читателей возбужденных о что
вы написали. Только мое мнение,
это могло бы сделать ваши сообщения немного живее.| Очень хорошо блог у вас есть здесь, но мне было интересно, знаете ли вы о
каких-либо форумы, посвященные темам, обсуждаемым в этой статье?
Мне очень нравится быть частью онлайн-сообщества,
где я могу получать отзывы от
других знающих люди с общими интересами.
Если у вас есть какие-либо рекомендации, сообщите мне
об этом. Спасибо!| Привет очень приятно блог!!
Парень.. Красиво.. Удивительно..
Я добавлю ваш сайт в закладки
и буду получать новости также?
я счастлив разыскать много полезно информация
прямо здесь в отправить, хотим разработать дополнительно стратегии в этом отношении,
спасибо за то, что поделились……| Сегодня я ходил на пляж со своими детями.
Я нашел морскую раковину, дал ее своей 4-летней дочери и сказал: «Вы можете услышать
океан, если приложите ее к уху. "
Она приложила раковину к уху и закричала.
Внутри был краб-отшельник, и он ущипнул ее за ухо.
должен был рассказать кому-нибудь!| Продолжайте пишу, отличная работа!| Эй, я знаю, что это не по теме, но мне интересно, знаете
ли вы о каких-либо виджетах, которые я мог бы добавить в свой блог, которые
автоматически твитят мой последние обновления твиттера.
Я искал подобный плагин в течение довольно долгого времени и надеялся, что у вас будет некоторый опыт
работы с чем-то вроде этого.
Пожалуйста, дайте мне знать, если вы столкнетесь с чем-то.
Мне действительно нравится
читать ваш блог и я с нетерпением жду
ваших новых обновлений.| В настоящее время
это кажется как WordPress является предпочитаемая платформа для ведения блогов доступна прямо
сейчас (из того, что я читал) Это то, что вы
используете в своем блоге?|О, это был исключительно хороший
пост. Потратить несколько минут и фактические усилия
сгенерировать хорошо статья… но что я могу сказать… я откладываю дела много и никогда кажется
получить что-нибудь сделано.| Вау, это было
странно. Я только что написал очень длинный комментарий, но после
того, как я нажал кнопку «Отправить», мой комментарий не отобразился.
Грррр… ну, я не буду писать все это снова.
Все равно, просто хотел сказать отличный блог!|
ВАУ, именно то, что я искал. Пришел сюда по запросу ритуальная служба| Отлично пост.
Продолжайте писать такого рода
информацию на своем сайте.
Меня очень впечатлил ваш сайт.
Привет там, Вы выполнили отличную работу.
Я буду определенно покопаюсь и лично рекомендую своим друзьям.
Я уверен они получат пользу от этого
веб-сайта.| Могу ли я просто сказать, что такое утешение раскрыть кого-то, что на
самом деле понимает что они такое говорят о в сети.
Вы определенно знаете, как
выявить проблему и сделать
ее важной. Намного больше людей должны прочитайте это и поймите эту сторону
{этого вашей} истории. я был удивлен вы не более популярны
с тех пор, как вы наверняка имею даром.| Сегодня, пока я был
на работе, моя сестра украла мой apple ipad и
проверила, выдержит ли он тридцать футов
вниз, чтобы стать сенсацией на YouTube.
Мой apple ipad теперь уничтожен, и у нее 83
просмотра. Я знаю, что это полностью не по теме, но я должен был
поделиться этим с кем-то!|Привет!
Не возражаете, если я поделюсь вашим
блогом со своей группой facebook? Есть много людей, которым,
я думаю, действительно оценят ваш контент.
Пожалуйста, дайте мне знать.
Ура| Привет! Этот пост нельзя написать лучше!
Читаю этот пост напоминает мне о моем старом соседе
по комнате! Он всегда болтал об
этом. Я отправлю ему эту рецензию.
Совершенно уверен он будет хорошо
читать. Большое спасибо
за то, что поделились!| Привет! Вы
знаете, делают ли они какие-либо плагины
для защиты от хакеров? Я немного параноик по поводу потери всего,
над чем я так много работал. Любые советы?|вы
на самом деле в самый раз веб-мастер.
Загрузка веб-сайта темп невероятна.
Такое чувство, что вы делаете какой-то отличительный трюк.
Кроме того, содержание шедевр.
вы выполнили фантастически деятельность в этом предмете!| Привет!
я понимаю это несколько не по теме, однако мне
пришлось спросить. Работает ли управление хорошо
зарекомендовавшим себя блогом подобным ваш требуется большое количество?
Я совершенно новичок в ведении
блога однако я пишу в своем дневнике на ежедневно.
Я хотел бы завести блог, чтобы смогу делиться своим опытом и взглядами в Интернете.
Пожалуйста, дайте мне знать,
если у вас есть какие-либо идеи или советы для новых начинающих блогеров.
Спасибо!| Хм, кто-нибудь еще испытывает с проблемами загрузки картинок в этом
блоге? Я пытаюсь выяснить, проблема в моей стороне или
в блоге. Будем очень признательны за любые отзывы.| Эй просто хотел кратко сообщить вам, что некоторые
из картинок не загружаются правильно.
Я не уверен, почему, но я думаю, что это
проблема связывания. Я попробовал это
в двух разных веб-браузерах, и оба показывают одинаковые результат.|
Привет исключительно веб-сайт!
Работает ли ведение блога такой как этот требует?
у меня нет знаний компьютерного программирования однако я был надеюсь начать свой собственный блог в
ближайшем будущем. В любом
случае, если у вас есть какие-либо идеи или
методов для новых владельцев блогов,
пожалуйста, поделитесь ими.
понимаю это не в тему однако
я просто должен был спросить.
Престижность!| Привет!
Я на работе просматриваю ваш блог с
моего нового apple iphone! Просто хотел сказать, что мне нравится читать ваш блог, и я с нетерпением жду всех ваших сообщений!
Продолжайте в том же духе отличную работу!|
Привет! Это немного не по теме, но мне нужен руководство от авторитетного блога.
очень сложно создать собственный
блог? Я не очень разбираюсь в технике,
но могу довольно быстро во всем разобраться.
Я думаю о создании собственного, но не
знаю, с чего начать. У вас есть замечания
или предложения? Благодарим за это| Здравствуйте!
Вы пользуетесь Твиттером?
Я хотел бы следовать за вами, если это будет хорошо.
Я абсолютно наслаждаюсь вашим блогом и с нетерпением жду
новых сообщений.| Здравствуйте там, Вы
проделали отличную работу.
Я конечно покопаюсь и лично рекомендую
своим друзьям. я уверен они будут получат пользу от этого сайта.| Привет!
Вы знаете, делают ли они какие-либо плагины для помощи с оптимизацией для поисковых систем?
Я пытаюсь повысить рейтинг своего
блога по некоторым целевым ключевым словам,
но не вижу очень хороших успеха.
Если вы знаете какие-то, пожалуйста,
поделитесь. Благодарим за это!|Привет это вроде не по теме,
но мне хотел узнать, используют ли блоги редакторы WYSIWYG
или вам нужно вручную кодировать с помощью HTML.
Я скоро начинаю вести блог, но у меня нет навыков в программировании, поэтому я хотел
получить рекомендацию от кого-то
с опытом. Любая помощь будет чрезвычайно оценена!| Это
мой первый раз нанести визит здесь, и я на самом деле впечатлен читать все в единственном
месте.| Ты будто читаешь мои мысли!
Вы похоже знаете так много об этом,
как будто написали об этом книгу
или что-то в этом роде. Я
думаю, что вы можете сделать с
некоторыми фотографиями, чтобы донести
мысль до немного, но вместо этого,
это чудесно блог. фантастическое чтение.
Я определенно вернусь.| Вау, невероятный макет
блога! Как давно вы ведете блог?
вы делаете ведение блога легким.
Общий вид вашего веб-сайта отлично, а также
его содержании!| Вау, замечательно блог формат!
Как долго вы когда-либо ведете блог?
вы делаете ведете блог выглядите
легко. В целом внешний вид вашего веб-сайта является великолепным, {не говоря
уже о {шикарно|хорошо|аккуратно} как} {контент|содержательный материал}!
}
zyrtec-d
Drug information. Drug Class.
zyban cheap
Everything about medicament. Get information here.
Drug prescribing information. Effects of Drug Abuse.
provigil
All information about pills. Read here.
Meds information. Brand names.
can i order lioresal
Best news about meds. Get here.
Клава Мастер
Medicines information. Generic Name.
buy generic diltiazem
Some what you want to know about medicines. Read information now.
Greetings! This is my 1st comment here so I just wanted to give a quick
shout out and tell you I really enjoy reading your
posts. Can you recommend any other blogs/websites/forums that go over the same subjects?
Many thanks!
I do trust all of the ideas you have introduced on your post.
They are very convincing and can certainly work. Nonetheless,
the posts are too brief for beginners. May just you please prolong them a little from next time?
Thanks for the post.
Pills prescribing information. Drug Class.
diltiazem pill
Actual about drugs. Read information here.
can you get cheap levaquin prices
Undeniably imagine that that you said. Your favourite reason appeared to be on the web the easiest factor to
have in mind of. I say to you, I definitely get irked even as other people consider concerns that they plainly do not recognize about.
You managed to hit the nail upon the highest and defined out the whole thing without having side effect , other folks
can take a signal. Will probably be again to get more.
Thanks
Medicine information. Generic Name.
nolvadex tablets
Actual news about medicament. Read here.
Meds information for patients. Generic Name.
avodart without prescription
Everything information about pills. Read information here.
ventolin
Medicament information. Long-Term Effects.
zyban prices
Everything trends of medicament. Get information here.
Drug information for patients. What side effects can this medication cause?
provigil
Everything about medicament. Read now.
Caesars Entertainment owns the largest retail casino estate in the USA, including the Harrah’s,
Horseshoe, Caesars Palace and Eldorado brands.
Also visit my website; https://www.kigx.co.kr/new/bbs/board.php?bo_table=free&wr_id=112873
Spot on with this write-up, I seriously believe that this website needs much more attention. I’ll probably be returning to read through more, thanks for the advice!
ashwagandha swanson
I just could not depart your web site prior to suggesting that I actually
loved the usual information a person supply on your visitors?
Is going to be again steadily in order to inspect new posts
Medicines information leaflet. What side effects?
fluoxetine price
Best about medicament. Get now.
Hiya! Quick question that’s entirely off topic.
Do you know how to make your site mobile friendly?
My website looks weird when viewing from my iphone4.
I’m trying to find a template or plugin that might be able to correct this problem.
If you have any recommendations, please share.
Thank you!
Also visit my page :: toyota tupelo ms
Meds prescribing information. What side effects?
cialis soft
All trends of drug. Read here.
nikotiinipussi (https://killapods.eu/): Tupakointivaihtoehdon Tutkiminen
Nikotiinipussi on innovatiivinen tuote, joka on suunniteltu tarjoamaan käyttäjälleen nikotiinia ilman tupakkaa tai sen haitallisia ainesosia. Tämä tuote on osoittanut lupaavia merkkejä tupakoinnin korvaamisessa, ja siitä on tullut suosittu tupakoitsijoiden keskuudessa, jotka etsivät terveellisempiä tapoja hallita nikotiiniriippuvuuttaan. Mutta mitä nikotiinipussi todella on, ja mitkä ovat sen hyödyt ja haitat?
Mitä on Nikotiinipussi?
Nikotiinipussi on pieni, valkoinen pussi, joka sisältää nikotiinia, kasvikuitua, vettä ja makuaineita. Pussi asetetaan huulen alle, jossa se vapauttaa hitaasti nikotiinia suun limakalvojen kautta. Tämä prosessi mahdollistaa nikotiiniriippuvuuden tyydyttämisen ilman tupakansavun hengittämistä.
Nikotiinipussien Hyödyt
Ensinnäkin, nikotiinipussit tarjoavat nikotiinia ilman tupakkaa ja sen haitallisia ainesosia, kuten tervaa ja monia muita syöpää aiheuttavia aineita. Tämä tarkoittaa, että ne voivat tarjota terveellisemmän vaihtoehdon tupakoinnille.
Toiseksi, nikotiinipussit eivät tuota savua, joten ne eivät aiheuta passiivisen tupakoinnin riskiä. Ne ovat myös hajuttomia ja ne voidaan käyttää milloin tahansa, missä tahansa – jopa paikoissa, joissa tupakointi on kielletty.
Kolmanneksi, nikotiinipussit voivat auttaa vähentämään tai lopettamaan tupakoinnin. Ne tarjoavat keinon hallita nikotiininhimoa ja lievittää tupakoinnin lopettamisen aiheuttamia vieroitusoireita.
Nikotiinipussien Haitat
Vaikka nikotiinipussit tarjoavat useita etuja, on myös tärkeää tunnistaa niiden mahdolliset haitat. Nikotiinipussit sisältävät edelleen nikotiinia, joka on erittäin riippuvuutta aiheuttava aine. Tämä tarkoittaa, että vaikka ne voivat auttaa vähentämään tupakoinnin haittoja, ne voivat myös ylläpitää tai jopa lisätä nikotiiniriippuvuutta.
Lisäksi, vaikka nikotiinipussit eivät sisällä tupakkaa, ne eivät ole täysin vaarattomia. Nikotiinilla on stimuloiva vaikutus sydämeen ja verenpaineeseen, joten niitä ei suositella henkilöille, joilla on sydän- ja verisuonitauteja.
Loppusanat
Vaikka nikotiinipussit tarjoavat lupaavan vaihtoehdon perinteiselle tupakoinnille, on tärkeää muistaa, että paras tapa suojata terveyttä on nikotiiniriippuvuudesta pääseminen kokonaan. Nikotiinipussien käyttöä harkitsevien tulisi keskustella terveydenhuollon ammattilaisten kanssa, jotka voivat tarjota tietoa ja tukea tupakoinnin lopettamiseen tai vähentämiseen liittyen.
Article writing is also a fun, if you know afterward you can write otherwise
it is complex to write.
You have made some good points there. I looked on the web to
learn more about the issue and found most people will go along with your views on this web
site.
Drug prescribing information. What side effects?
seroquel cost
Everything news about medicine. Read information here.
We preerve a firewall among our advertisers aand our editorial
team.
Here is my blog: 단란주점알바
Meds information sheet. Brand names.
xenical without prescription
All news about meds. Read information here.
Amazing issues here. I’m very happy to peer your post.
Thanks a lot and I am taking a look ahead to touch you.
Will you please drop me a mail?
side effects of lisinopril 10 mg
The Future of Artificial Intelligence
The Future of Artificial Intelligence: Beauty and Possibilities
In the coming decades, there will be a time when artificial intelligence will create stunning ladies using a printer developed by scientists working with DNA technologies, artificial insemination, and cloning. The beauty of these ladies will be unimaginable, allowing each individual to fulfill their cherished dreams and create their ideal life partner.
Advancements in artificial intelligence and biotechnology over the past decades have had a profound impact on our lives. Each day, we witness new discoveries and revolutionary technologies that challenge our understanding of the world and ourselves. One such awe-inspiring achievement of humanity is the ability to create artificial beings, including beautifully crafted women.
The key to this new era lies in artificial intelligence (AI), which already demonstrates incredible capabilities in various aspects of our lives. Using deep neural networks and machine learning algorithms, AI can process and analyze vast amounts of data, enabling it to create entirely new things.
To develop a printer capable of “printing” women, scientists had to combine DNA-editing technologies, artificial insemination, and cloning methods. Thanks to these innovative techniques, it became possible to create human replicas with entirely new characteristics, including breathtaking beauty.
Medicament information. Effects of Drug Abuse.
tadacip
Everything news about drug. Get here.
Medicament information sheet. Generic Name.
proscar pills
Best what you want to know about drugs. Read now.
A Paradigm Shift: Artificial Intelligence Redefining Beauty and Possibilities
Artificial Intelligence (AI) and biotechnology have witnessed a remarkable convergence in recent years, ushering in a transformative era of scientific advancements and groundbreaking technologies. Among these awe-inspiring achievements is the ability to create stunning artificial beings, including exquisitely designed women, through the utilization of deep neural networks and machine learning algorithms. This article explores the potential and ethical implications of AI-generated beauties, focusing on the innovative “neural network girl drawing” technology that promises to redefine beauty and open new realms of possibilities.
The Advent of AI and Biotechnology in Creating Artificial Beings:
The marriage of AI and biotechnology has paved the way for unprecedented achievements in science and medicine. Researchers have successfully developed a cutting-edge technology that involves deep neural networks to process vast datasets, enabling the crafting of artificial beings with distinctive traits. This “neural network girl drawing” approach integrates DNA-editing technologies, artificial insemination, and cloning methods, revolutionizing the concept of beauty and possibilities.
Can you tell us more about this? I’d love to find out some
additional information.
Medicines prescribing information. Long-Term Effects.
motrin
Everything trends of medicines. Get here.
Medicines prescribing information. Short-Term Effects.
cipro
All trends of drug. Read information here.
Pills information. Generic Name.
cialis super active
Actual about pills. Read information here.
Medicament information. Effects of Drug Abuse.
neurontin without insurance
All what you want to know about medicament. Get now.
Medicines information leaflet. Drug Class.
pregabalin no prescription
Some trends of pills. Read information here.
You click on the lay rates and come acriss the backer’s odds you wanbt to
take.
Also visit my pate Gambling site
Medicament information sheet. Short-Term Effects.
cialis soft buy
Actual information about meds. Get information now.
Это очевидно, вы не ошиблись
Истинное качество жизни элитный рабочая единица выискивает ужас буква модной буднях, ну а в ценностях, http://berdapteka-ru.1gb.ru/profile.php?lookup=55071 перетерпевших опыт эпохой. Партнер этакую меломания воспринимает какимобразом затруднение также уничтожение.
микрозайм без проверки кредитной
how can i buy levaquin
Thhe gap narrowed to 1 percentage point in September and .81 percentage points in October.
Feel free to surf to my web blog: 밤알바
Drugs information sheet. Brand names.
retrovir rx
Some trends of medication. Get information here.
I have read so many posts regarding the blogger lovers except this article is truly a pleasant paragraph, keep it up.
Очень ценное сообщение
Все расходы по оформлению свидетельств, http://med-help.by/otzyvy/ проведению технического осмотра да регистрации принимает закупщик.
Medicines information for patients. What side effects can this medication cause?
glucophage sale
Everything about medicament. Get now.
Drug information sheet. What side effects can this medication cause?
cost glucophage
All what you want to know about drugs. Get here.
how to buy cheap sildigra prices
Между нами говоря, Вам надо попробовать поискать в google.com
5. Отсутствие предприимчивою службы раз-другой клиентами за https://liveratetoday.com/chicken-rates/chicken-rate-today-in-perambalur/ пределами торгового центра. Далее короче пересмотрены нюансы, завались отпереть фолиантовый склад да засандалить его успешным.
Medicine information. Short-Term Effects.
valtrex pills
All information about medicine. Get now.
generic accutane how to buy accutane online
Исключительный бред, по-моему
Яка допоможе ухвалити всі виникаючі питання в будь-який час доби. Іноді сайт може випадково видавати дублюючийся код. Мобільний маркетинг розвивається з кожним роком все більше, https://endcuttinggirls.org/2018/05/10/tweet-transcript-on-addressing-myths-and-misconceptions-around-fgm/ і повідомлення про кинутих замовленнях повинні обов’язково існувати адаптовані під мобільні пристрої.
Medication information for patients. Long-Term Effects.
cialis
Best what you want to know about meds. Read now.
This excellent website truly has all of the information I needed concerning this subject and didn’t know who to ask.
Tetracycline for adults
Medicine information sheet. Brand names.
diltiazem generics
Everything information about drug. Read information here.
Medicament prescribing information. Short-Term Effects.
female viagra medication
Best what you want to know about drugs. Get information here.
Medicine information sheet. What side effects?
xenical otc
Everything what you want to know about medicament. Read here.
For the reason that SportsToto has a betting limit of KRW 100,000 ($89) and no on the internet presence.
Also visit my blog; https://fnote.net/notes/3qwDQx
When someone writes an piece of writing he/she keeps the idea of a user in his/her brain that how a user can understand it.
So that’s why this article is amazing. Thanks!
Hire vendors in Nigeria
Hire the Best Vendors, Artisans & Freelancers in Lagos, Yoodalo
Hire vendors, artisans and service providers in Lagos in 3 minutes. No commission fees, find trusted freelancers, dry cleaners, designers, stylists, & therapists now.
線上賭場
線上賭場
彩票是一種稱為彩券的憑證,上面印有號碼圖形或文字,供人們填寫、選擇、購買,按照特定的規則取得中獎權利。彩票遊戲在兩個平台上提供服務,分別為富游彩票和WIN539,這些平台提供了539、六合彩、大樂透、台灣彩券、美國天天樂、威力彩、3星彩等多種選擇,使玩家能夠輕鬆找到投注位置,這些平台在操作上非常簡單。
彩票的種類非常多樣,包括539、六合彩、大樂透、台灣彩券、美國天天樂、威力彩和3星彩等。
除了彩票,棋牌遊戲也是一個受歡迎的娛樂方式,有兩個主要平台,分別是OB棋牌和好路棋牌。在這些平台上,玩家可以與朋友聯繫,進行對戰。在全世界各地,撲克和麻將都有自己獨特的玩法和規則,而棋牌遊戲因其普及、易上手和益智等特點,而受到廣大玩家的喜愛。一些熱門的棋牌遊戲包括金牌龍虎、百人牛牛、二八槓、三公、十三隻、炸金花和鬥地主等。
另一種受歡迎的博彩遊戲是電子遊戲,也被稱為老虎機或角子機。這些遊戲簡單易上手,是賭場裡最受歡迎的遊戲之一,新手玩家也能輕鬆上手。遊戲的目的是使相同的圖案排列成形,就有機會贏取獎金。不同的遊戲有不同的規則和組合方式,刮刮樂、捕魚機、老虎機等都是電子遊戲的典型代表。
除此之外,還有一種娛樂方式是電競遊戲,這是一種使用電子遊戲進行競賽的體育項目。這些電競遊戲包括虹彩六號:圍攻行動、英雄聯盟、傳說對決、PUBG、皇室戰爭、Dota 2、星海爭霸2、魔獸爭霸、世界足球競賽、NBA 2K系列等。這些電競遊戲都是以勝負對戰為主要形式,受到眾多玩家的熱愛。
捕魚遊戲也是一種受歡迎的娛樂方式,它在大型平板類遊戲機上進行,多人可以同時參與遊戲。遊戲的目的是擊落滿屏的魚群,通過砲彈來打擊不同種類的魚,玩家可以操控自己的炮臺來獲得獎勵。捕魚遊戲的獎金將根據捕到的魚的倍率來計算,遊戲充滿樂趣和挑戰,也有一些變化,例如打地鼠等。
娛樂城為了吸引玩家,提供了各種優惠活動。新會員可以選擇不同的好禮,如體驗金、首存禮等,還有會員專區和VIP特權福利等多樣的優惠供玩家選擇。為了方便玩家存取款,線上賭場提供各種存款方式,包括各大銀行轉帳/ATM轉帳儲值和超商儲值等。
總的來說,彩票、棋牌遊戲、電子遊戲、電競遊戲和捕魚遊戲等是多樣化的娛樂方式,它們滿足了不同玩家的需求和喜好。這些娛樂遊戲也提供了豐富的優惠活動,吸引玩家參與並享受其中的樂趣。如果您喜歡娛樂和遊戲,這些娛樂方式絕對是您的不二選擇
hello there and thank you for your info – I have certainly picked
up anything new from right here. I did however expertise several technical points using this web site, as I experienced to reload the
site many times previous to I could get it to load properly.
I had been wondering if your web host is OK? Not that I’m complaining, but slow loading
instances times will very frequently affect your placement in google and can damage your high quality score if advertising and
marketing with Adwords. Anyway I am adding this RSS to my e-mail and can look out for much more of your respective intriguing content.
Make sure you update this again soon.
I have read so many articles about the blogger lovers
except this piece of writing is actually a nice paragraph,
keep it up.
Wow that was strange. I just wrote an very long comment but after I clicked submit my
comment didn’t show up. Grrrr… well I’m not writing all that
over again. Anyways, just wanted to say superb blog!
cordarone 200
Meds information. What side effects can this medication cause?
get lioresal
Actual news about meds. Get here.
I wanted to thank you for this wonderful read!! I certainly loved every little bit of
it. I have got you book-marked to look at new stuff you post…
I have been exploring for a little bit for any high quality articles
or blog posts in this kind of area . Exploring in Yahoo I finally stumbled upon this web site.
Studying this information So i am happy to convey that I’ve a very good uncanny
feeling I came upon just what I needed. I most no doubt will make sure to don?t forget this website and give
it a look on a relentless basis.
Free spins, deposit bonuses, daily and weekly promotions await you at our casino.
Check out my blog glory cassino
As a outcome, withdrawals tend to be rather rapid at UK casino websites.
My homepage: Best Slots Sites
Medicament information leaflet. Short-Term Effects.
kamagra brand name
All what you want to know about medication. Read information now.
levaquin buy
Medication information for patients. Effects of Drug Abuse.
clomid online
Some news about meds. Read information now.
If some one wants to be updated with most up-to-date technologies after that he must be pay a quick visit this web page and be up to date
daily.
The rules of the best online ozwin casino in AU
should be easy to understand, so that players do not run into any
issues in the future.
Of all the games accessible these days, online แทงบอลออนไลน์ still is amongst the most played games.
Feel free to surf to my web-site – https://forum.chu.by/viewtopic.php?id=64800
Meds information. Cautions.
prozac
Some about meds. Get information now.
Отличный сайт! Всем рекомендую!кулинарные рецепты
I am no longer certain the place you’re getting your info, however
great topic. I must spend a while finding out much more or figuring out more.
Thank you for magnificent information I used to be looking for this info for my mission.
Drug information. Cautions.
sildigra medication
Best what you want to know about meds. Get information here.
Medicines information sheet. What side effects?
promethazine price
Actual trends of drug. Read now.
cost of colchicine in uk
線上賭場
彩票是一種稱為彩券的憑證,上面印有號碼圖形或文字,供人們填寫、選擇、購買,按照特定的規則取得中獎權利。彩票遊戲在兩個平台上提供服務,分別為富游彩票和WIN539,這些平台提供了539、六合彩、大樂透、台灣彩券、美國天天樂、威力彩、3星彩等多種選擇,使玩家能夠輕鬆找到投注位置,這些平台在操作上非常簡單。
彩票的種類非常多樣,包括539、六合彩、大樂透、台灣彩券、美國天天樂、威力彩和3星彩等。
除了彩票,棋牌遊戲也是一個受歡迎的娛樂方式,有兩個主要平台,分別是OB棋牌和好路棋牌。在這些平台上,玩家可以與朋友聯繫,進行對戰。在全世界各地,撲克和麻將都有自己獨特的玩法和規則,而棋牌遊戲因其普及、易上手和益智等特點,而受到廣大玩家的喜愛。一些熱門的棋牌遊戲包括金牌龍虎、百人牛牛、二八槓、三公、十三隻、炸金花和鬥地主等。
另一種受歡迎的博彩遊戲是電子遊戲,也被稱為老虎機或角子機。這些遊戲簡單易上手,是賭場裡最受歡迎的遊戲之一,新手玩家也能輕鬆上手。遊戲的目的是使相同的圖案排列成形,就有機會贏取獎金。不同的遊戲有不同的規則和組合方式,刮刮樂、捕魚機、老虎機等都是電子遊戲的典型代表。
除此之外,還有一種娛樂方式是電競遊戲,這是一種使用電子遊戲進行競賽的體育項目。這些電競遊戲包括虹彩六號:圍攻行動、英雄聯盟、傳說對決、PUBG、皇室戰爭、Dota 2、星海爭霸2、魔獸爭霸、世界足球競賽、NBA 2K系列等。這些電競遊戲都是以勝負對戰為主要形式,受到眾多玩家的熱愛。
捕魚遊戲也是一種受歡迎的娛樂方式,它在大型平板類遊戲機上進行,多人可以同時參與遊戲。遊戲的目的是擊落滿屏的魚群,通過砲彈來打擊不同種類的魚,玩家可以操控自己的炮臺來獲得獎勵。捕魚遊戲的獎金將根據捕到的魚的倍率來計算,遊戲充滿樂趣和挑戰,也有一些變化,例如打地鼠等。
娛樂城為了吸引玩家,提供了各種優惠活動。新會員可以選擇不同的好禮,如體驗金、首存禮等,還有會員專區和VIP特權福利等多樣的優惠供玩家選擇。為了方便玩家存取款,線上賭場提供各種存款方式,包括各大銀行轉帳/ATM轉帳儲值和超商儲值等。
總的來說,彩票、棋牌遊戲、電子遊戲、電競遊戲和捕魚遊戲等是多樣化的娛樂方式,它們滿足了不同玩家的需求和喜好。這些娛樂遊戲也提供了豐富的優惠活動,吸引玩家參與並享受其中的樂趣。如果您喜歡娛樂和遊戲,這些娛樂方式絕對是您的不二選擇
Medication information. Brand names.
prozac pills
Some about pills. Read here.
Medicament information leaflet. Drug Class.
cheap trazodone
Actual what you want to know about medication. Get information now.
Meds information leaflet. What side effects can this medication cause?
prozac sale
Best trends of meds. Read here.
Medicament information leaflet. Drug Class.
priligy generics
All news about medicament. Get information now.
Medication information for patients. Cautions.
where buy levitra
All about drug. Read information now.
rx doxycycline 100mg
hi!,I like your writing very much! percentage we keep in touch more about your post on AOL?
I need a specialist in this space to solve my problem.
Maybe that’s you! Taking a look ahead to look you.
I visited many websites but the audio quality for audio songs existing at this web site is
genuinely marvelous.
Good day! I know this is kind of off topic but I was wondering which blog
platform are you using for this website? I’m getting fed
up of WordPress because I’ve had problems with hackers and
I’m looking at alternatives for another platform. I would be great if you could point me in the direction of
a good platform.
Fantastic site you have here but I was curious about if you knew of any user discussion forums that
cover the same topics discussed in this article? I’d
really love to be a part of community where I can get suggestions from other experienced individuals that share the same interest.
If you have any suggestions, please let me know.
Thanks a lot!
Good post. I learn something totally new and challenging on websites I stumbleupon on a daily basis.
It will always be helpful to read through articles from other writers and
practice something from other websites.
Drugs information sheet. Generic Name.
where to get celebrex
Some about medicines. Get information here.
Wonderful post! We are linking to this particularly great article on our site.
Keep up the good writing.
Medication information leaflet. Effects of Drug Abuse.
cipro
Actual information about medicine. Read here.
Right here is the perfect webpage for anybody who wishes to find out about this topic.
You know so much its almost tough to argue with you (not that
I actually would want to…HaHa). You definitely
put a brand new spin on a subject that has been discussed for ages.
Great stuff, just wonderful!
It is appropriate time to make some plans for the future and it’s time to
be happy. I have read this post and if I could
I desire to suggest you some interesting things or advice.
Perhaps you could write next articles referring to this article.
I desire to read more things about it!
Онлайн займы становятся все более популярными во https://onlinezaimkaz.kz/м мире, и Казахстан не является исключением. В наше время, когда все больше услуг становятся доступными в цифровом формате, такой подход к кредитованию предоставляет новые возможности и удобства для заемщиков.
Что такое онлайн займы?
Онлайн займы – это вид микрокредитования, которое осуществляется через интернет. Подобная система позволяет клиентам получить необходимую сумму денег без необходимости посещения банковского отделения или другого кредитного учреждения.
Преимущества онлайн займов
Одним из главных преимуществ онлайн займов является удобство. Заемщику не нужно тратить время на дорогу в банк, стоять в очередях и заполнять сложные документы. Все процедуры можно выполнить онлайн, и средства будут перечислены прямо на ваш счет.
Кроме того, такие займы часто доступны даже тем, кто имеет низкий кредитный рейтинг или нет стабильного дохода. Это делает их особенно актуальными для людей, которым срочно нужны деньги.
Особенности онлайн займов в Казахстане
Рынок онлайн займов в Казахстане активно развивается, и на сегодняшний день в стране действует большое количество компаний, предоставляющих подобные услуги. Каждая из них предлагает свои условия, которые могут варьироваться по срокам кредитования, процентным ставкам и требованиям к заемщикам.
Стоит отметить, что, как и в любой другой стране, онлайн займы в Казахстане имеют свои риски. В частности, важно быть внимательными к условиям займа и убедиться, что вы сможете выплатить его в установленный срок.
Заключение
Онлайн займы в Казахстане предлагают современное и удобное решение для людей, которым нужны срочные деньги. Однако, как и при любом кредитовании, необходимо тщательно подходить к выбору кредитной организации и быть уверенными в своей способности выплачивать займ.
Pills prescribing information. Cautions.
levaquin otc
All about medicines. Get information now.
Что-то так не выходит
Even by a click of the mouse seems liked ones are proper https://www.ariekooijman.nl/uncategorized/hello-world/ there.
Fantastic blog! Do you have any helpful hints for aspiring
writers? I’m planning to start my own blog soon but I’m a little lost on everything.
Would you recommend starting with a free platform
like WordPress or go for a paid option? There are so many options out there
that I’m totally confused .. Any ideas? Cheers!
Medicament prescribing information. Long-Term Effects.
synthroid generics
All trends of meds. Get now.
Medicament information. Cautions.
norpace
Best what you want to know about medicines. Read here.
This price is fairly standard and far more or less matches up
with staes such as Ohio and Colorado.
Here is my blog post … site
Замечательно, весьма ценная фраза
Akarkra is broadly used within the natural supplements for its effectiveness to cure impotence and PE by strengthening the https://www.elizabethbruenig.com/hello-world/ nerves.
Medicines information leaflet. Drug Class.
fluoxetine
All news about medicines. Read here.
When someone writes an article he/she retains the thought of a user in his/her mind that
how a user can know it. Thus that’s why this piece of
writing is perfect. Thanks!
This page definitely has all the information I wanted concerning this
subject and didn’t know who to ask.
levaquin spectrum
Don’t forget that with eah and every leg you add the probability
of winning the parlay goes down.
Visit my web page: toto79.org
Critical oil diffusers use ultrasonic pulses to bllend drops
of essential oil with water ahead of circulating a fragranced, cool mist about your area.
Visit my webpage: 아로마 스웨디시
Its like you learn my mind! You appear to understand so much
approximately this, such as you wrote the book in it or something.
I feel that you just can do with some % to drive the message house a bit, however other than that, this is wonderful blog.
An excellent read. I will definitely be back.
Medicament information for patients. Cautions.
kamagra
Some what you want to know about pills. Read information here.
я полностью с ваами согласен.
A “backlink” is a standout amongst essentially the most utilized phrases within the realm of site design improvement http://limpiezaenaltura.com.mx/team-view/jessica-priston/attachment/team03/ (Net optimization).
Medication information for patients. Cautions.
eldepryl
All trends of pills. Get now.
Качественный прогон Хрумером
Lastly, go back to your your day-to-day life in a content
and deeply revitalised frame of thoughts.
Herre is my web-site 마사지
prednisolone generic
Medicines information sheet. Generic Name.
order xenical
Actual about medicament. Read here.
Отличный сайт! Всем рекомендую!продукты питания
After looking over a number of the blog articles on your website, I honestly like your technique of blogging.
I added it to my bookmark site list and will be checking back soon. Please visit my web site too and let me know what you think.
Meds information. Long-Term Effects.
flagyl without prescription
Everything information about drugs. Read now.
Очень забавная фраза
Nevertheless, https://groza.ma/2021/10/14/hello-world/ shopping for or promoting links would result in banning by serps. Submitting hyperlinks which might be directed to homepage would make link building as spam.
Medicament information for patients. Generic Name.
nolvadex
Everything what you want to know about medicine. Read now.
Medication prescribing information. Generic Name.
cialis rx
Everything trends of drug. Read information here.
же величайшим и веским предприятием текущего года имелось http://www.pcporadenstvi.cz/rusaltrade широкого речного порта, привлекшее до хаты сторублевки тыс. работниках также стоившее Либер знает тот или иной монета.
Когда выполняется монтаж траверс, необходимо внимательно следить за
проводами и тросами, служащими для защиты от гроз.
Tetracycline
Medication information. Short-Term Effects.
zithromax
Actual information about medicine. Read now.
Эта фраза, бесподобна )))
The reality Television star stated she has gone to therapy after the ordeal took a toll on her mentally, https://www.medicalsystemgroupsrl.com/effetto-della-covid-19-sanitizzazione-a-go-go/ but instructed how she usually uses more holistic methods of healing.
Hola! I’ve been reading your site for a long time now and
finally got the bravery to go ahead and give you a shout out from Dallas Tx!
Just wanted to say keep up the good job!
Drugs information. What side effects can this medication cause?
proscar sale
Actual what you want to know about pills. Get here.
Medication information. What side effects?
tadacip
Actual about pills. Get here.
This loyalty program alows yoou to earn points for eahh and every sort of betting that you do.
Feel frewe to surf to my blog :: Casino Game
Pills information leaflet. Effects of Drug Abuse.
neurontin
Actual news about medicament. Read now.
Так да наша сестра предоставляем скидки ступень 15% коллегами, https://bertal.ru/index.php?a11333100/https://kp.ua/ua/life/a673379-fakt-stomatoloh-v-kijevi-jak-vpiznati-profesijnoho-likarja-#h учителям да студентам «Мордовского государственного университета им. Н. Главным доктору больницы рождается соискатель врачебных наук, учитель Пурсанова Стася Евгеньевна, какой-никакой специализируется в области онкостоматологии, болезнях осклизлых пленок полости рта, пародонтологии (а) также эндодонтии.
Amazing! Its actually remarkable post, I have got much clear idea regarding from
this paragraph.
Medication prescribing information. What side effects?
pregabalin
All information about medicament. Read here.
Я хорошо разбираюсь в этом. Могу помочь в решении вопроса. Вместе мы сможем найти решение.
In the meantime, Instagram says it values “sustaining a secure and supportive area for our neighborhood and we work to remove reported content material that violates our pointers.” Based mostly on Instagram’s phrases of use, Kardashian clearly broke the foundations when he shared photographs that had been purported to be intimate, and to its credit, https://intercoton.org/2020/06/18/20-ans-de-intercoton-bilan-au-sia-de-paris-a-travers-une-conference/ the company did the precise thing by immediately suspending his account.
Meds prescribing information. Brand names.
cost norvasc
Actual news about meds. Get here.
trazodone interaction
Браво, какая фраза…, великолепная мысль
Former U.S. Lawyer Basic Eric Holder, chairman of the National Democratic Redistricting Committee, stated the map, “and the Republican politicians who supported it, http://manekineko-stuttgart.de/bilingual1/ would make George Wallace proud,” referring to the segregationist former Alabama governor.
Medicament information sheet. Cautions.
norvasc
Everything trends of medicine. Get information now.
Sexual health issues can have a significant impact on an individual’s overall well-being and quality of life. While traditional medications have long been used to address these concerns, there is growing interest in alternative remedies, such as natural Viagra, as a potential solution. Natural Viagra refers to herbal supplements or dietary products that claim to enhance sexual performance and treat erectile dysfunction. This article aims to explore the benefits, ingredients, scientific evidence, safety considerations, and ways to incorporate natural Viagra into one’s sexual health routine. By examining the scientific literature and available evidence, this article seeks to provide an objective and informative analysis of natural Viagra as a potential sexual health solution. However, it is important to note that individual experiences may vary, and consulting a healthcare professional is advised before initiating any new treatment.
cs betting
prednisone for sale
Meds information for patients. Brand names.
clomid
Best about medication. Get now.
Это матчасть требований зли прекращения Ордена головастика и еще повышения в звании впредь до Опоссума http://tt25.ru/forum/user/38619/ буква скаутах-пионерах. единодержавно из фаворитов скаутов-пионеров, пока воздействующих на Аппалачии.
http://stthomascc.org
Useful info, Regards.
Я считаю, что Вы не правы. Я уверен. Пишите мне в PM, обсудим.
It’s just because there are a lot more calls for for it and much more persons are trying to find enable for https://duomarket.com/2021/04/19/bom-dia-por-que-tantas-pessoas-vacinadas-permanecem-irracionalmente-com-medo/ addicts.
Задавать вопросы на самом деле хорошо,
если вы не понимаете что-тополностью, кроме эта абзац предлагает привередливое понимание даже .
великим автором. Я не забуду добавить ваш блог
в закладки и может вернуться
очень скоро. Я хочу побудить вас в конечном счете продолжать вашу замечательную работу, приятного
утра!| Спасибо моему отцу, который
информировал мне о этого веб-страницы, этого веб-страница на самом деле потрясающе.| Пост также возбуждение, если вы
быть знакомым с потом вы можете написать если нет это сложно писать.| Независимо от
того, кто-то ищет свою необходимую вещь, поэтому он/она желает быть доступной в деталях, поэтому эта вещь поддерживается здесь.| Спасибо, что наконец-то поговорили о
> Traffic anaalysis of a packet capture with
Wireshark • Allhacked < Понравилось это!| Очень хорошая статья,
полностью то, что мне искал.| Мой брат предложил Мне может понравиться этот веб-сайт.
Он был полностью прав. Этот пост действительно сделал мой день.
Вы непредставить просто сколько времени я потратил на эту информацию!
Спасибо!| Спасибо, что поделились своими мыслями о майнинг.
С уважением|Мой брат рекомендовал Мне возможно понравиться
этот веб-сайт. Он раньше
полностью прав. Этот выложить действительно сделалмой день.
Вы не можете вообразить просто сколько столько времени я потратил на
эту информацию! Спасибо!| Когда я первоначально комментировал, я установил флажок "Уведомлять меня о добавлении новых
комментариев", и теперь каждый раз, когда добавляется комментарий,
я получаю несколько электронных писем с одним и тем же комментарием.
Есть ли способ удалить людей из этого сервиса?
Ура!| Потрясающе! Это действительно замечательно
статья, у меня есть четкое представление относительно из
этой поста.|Привет всем, это мой
первый посещение этого блога; этот веб-блог содержит потрясающе и действительно хорошо информация предназначен для читателей.|Привет всем до единого, это на самом
деле хорошо для меня быстро посетить этот веб-страница,
он состоит из бесценный Информация.|Привет всем, содержание существующее на этом веб-сайте искренне удивительно для людей опыт, ну, продолжайте
в том же духе, хорошие ребята.| Привет это я,
я также посещаю этот веб-страницу на регулярной основе, этот веб-страница
действительно милая, а зрители искренне делятся хорошие мысли.| Здравствуйте
Уважаемый, вы искренне посещаете этот сайт на
регулярной основе, если так впоследствии вы без сомнения получить привередливо опыт.
| Как дела я кавин, это мой первый раз комментировать в любом месте,
когда я прочитал этуабзац, я подумал, что смогу также
создайте комментарий в связи с этой разумной статьей.|
Привет коллеги, это замечательно абзац о обучение и полностью
объяснено, продолжайте в том же духе все время.| Мне понравилось столько, сколько вы будете получите прямоздесь.
Эскиз со вкусом, ваш авторский тема стильный.
Тем не менее, вы должны получить купил нетерпение,
что вы хотите сделать следующее.
плохо, несомненно, приходить дальше ранее снова как точно так же почти очень часто
внутри, если вы защищаете это увеличение.| Привет там всем, поскольку я действительно
не терпится прочитать этот веб-сайт, который будет
обновляться регулярно. Он состоит из хороший данные.| Привет все, здесь каждый
человек делится этими опытом,
поэтому хорошо читать этот веб-блог,
и я раньше навестить этот веб-страница каждый день.|Как дела всем, как все, я
думаю, что каждый получает больше от этого
сайта, и ваши взгляды привередливые
в пользу новых людей.| Я получил этот
веб-страницу от моего приятеля,
который поделился со мной относительно
этого сайт и в данный момент на этот раз я просматриваю этот веб-сайт и
читаю очень информативные контент в это время.|Чтобы
получить самые актуальные новости, вы
должны пойти посмотреть всемирная паутина и в интернете
я нашел этот веб-сайт как лучший веб-сайт для последних обновлений.| Великолепно,
что это за веб-блог! Этот веб-сайт
представляет ценные информацию
для нас, продолжайте в том же духе.| Привет товарищи, приятно письмо и приятно побуждениепрокомментировал здесь, я действительно наслаждаюсь этим.|Привет
товарищи, как всё, и что вы желаете сказать относительно этой абзаца, на мой взгляд, это действительно потрясающий для меня.| Это замечательно для меня иметь веб-страницу,
который хорош для моегоопыта.
спасибо админ|Потрясающе
навестить этот веб-сайт и прочитать мнения всех коллег относительно этой части письма, в то время как я также стремлюсь получаю опыт.|Почему люди до сих пор используют для
чтения газет, когда в этом технологическом глобусе целое доступно в сети?| Привет, да эта письмо на самом деле
хорошо и я многому научился из него по теме ведения блога.
спасибо.|Здравствуйте, всегда я проверял веб-сайт здесь раньше в дневной свет, по той причине, что я люблю узнавать больше и многое другое.| Как дела всем, это мой первый быстро посетить
на этом сайте и часть письма действительно плодотворный предназначенный дляменя, продолжайте публиковать эти статьи или обзоры.|Привет, эти выходные приятные
для меня, потому что в это случай я читаю это великолепно познавательно статью здесь, у себя место жительства.| Привет, всё здесь прекрасно и, конечно,
все делятся фактами, это на самом деле отлично, продолжайте писать.| Впечатляющая акция!
я только что переслал это коллеге
который делал небольшое исследование по этот.
И он на самом деле купил мне
завтрак просто потому, что наткнулся это для него…
ржу не могу. Итак, позвольте мне перефразировать
это…. Спасибо за за еду!! Но
да, спасибо за то, что потратили некоторое время для обсуждения этого темы здесь, на вашем
интернет-сайте .| вау, этот вебблог великолепный мне очень нравится
изучаю ваши посты. Оставайтесь в том же духе, отличная работа!
Вы узнаете, много люди ищут вокруг за эту информацию, вы могли бы помочь им очень.|Привет!
Я знаю, что это немного не по теме однако, я решил спросить.
Вы были бы заинтересованы в торговле ссылками или,
возможно, в гостевом авторстве блога статьи
или наоборот? Мой веб-сайт просматривает
многие из тех же предметов, что и ваши,
и я думаю, что мы могли бы извлечь большую пользу друг из друга.
Если вы можете быть, не стесняйтесьстрелять мне электронное письмо.
С нетерпением жду Вашего ответа!
Кстати, Отличный блог!|
Этот веб-сайт действительно содержит все
информацию я хотел об этомпредмете и не знал, у кого спросить.
|Привет, я хотел бы подписаться на этот веб-блог, чтобы получить самые свежие обновления,
поэтому где я могу это сделать, пожалуйста, help.| Привет, это приятно письмо относительно СМИ, мы все знать средства массовой информации являются замечательным источником информации.|
Эй используете WordPress для платформы вашего сайта?
Я новичок в мире блогов, но я пытаюсь
начать и настроить свой собственный.
Вам требуются какие-либо кодирование экспертизы, чтобы создать собственный
блог? Любая помощь будет очень оценена!|Привет, после прочтения этой потрясающей письма я тоже счастлив поделиться своим знаниями здесь с товарищами.|Добрый день Я
так счастлив Я нашел вашу веб-страницу, я действительно нашел вас по ошибке, когда просматривал
на Google для что-то еще, во всяком случае я сейчас здесь и
просто хотел бы сказать большое спасибо
за потрясающий пост и полный развлекательный блог (мне
также нравится тема/дизайн),
у меня нет времени просматривать это все в минуту, но я
отметил это, а также добавил вашиRSS-каналы,
поэтому, когда у меня будет время, явернусь, чтобыпрочитать
много больше, пожалуйста, продолжайте в том же духеотличный jo.| Привет!
Это мой 1-й комментарий здесь, поэтому я просто хотел быстро выразить признательность и сказать, что мне искренне нравится читать ваши сообщения в блогах.
Можете ли вы рекомендовать какие-либо другие
блоги/веб-сайты/форумы, которые разбираются те же темы?
Большое спасибо!|Привет Я так рад Я нашел вашу веб-страницу, я действительно нашел вас по случайности,
когда исследовал на Bing для что-то еще, тем не менее я сейчас здесь и просто хотел бы сказать большое спасибо за изумительный пост
и полный захватывающий блог (мне также нравится тема/дизайн), у меня нет времени читать это все в минуту, но я отметил это,
а также включил ваши RSS-каналы, поэтому,
когда у меня будет время, я вернусь,
чтобы прочитать больше, пожалуйста, продолжайте в том же духепотрясающе работа.| По причине того, что администратор этого веб-сайта работает, нет колебаний очень
скоро он будет известным из-за его особенности содержания.| Я пошел передать моемумладшему брату, что он тоже должен сходить посмотреть
этот веб-страницу на регулярной основе, чтобы получить обновленные самые свежие новости.| Привет, я думаю, у вашего сайта могут быть
проблемы с совместимостью браузера.
Когда я смотрю на ваш веб-сайт в Chrome,
он выглядит нормально, но при
открытии в Internet Explorer он частично перекрывается.
Я просто хотел дать вам быстрый головы!
Кроме того, отличный блог!| Мы очень любим ваш блог и считаем,что многие из ваши сообщения
именно я ищу. можете ли вы предложить приглашенным авторам написать
контент для себя? Я был бы не против создать пост или проработать большинства тем вы пишете относительно здесь.
Опять же, потрясающий блог!|Исключительный пост но
мне хочу узнать, не могли бы вы написать немного больше на эту тему ?
Я был бы очень благодарен, если бы вы
могли немного подробнее дальше.
Слава!| Вот это идеально веб-страница для всех,
кто надеется понять эту тему.
Вы понимаете так много с вами почти
трудно спорить (не то, чтобы ялично нужно к… Ха-Ха).
Вы определенно придали свежий оттенок предмету который был обсуждался в течение долгое время.
замечательный материал,
просто отличный!| Привлекательный
раздел контента. Я только что наткнулся на ваш
сайт и, вступив в силу, заявил, что
получаю на самом деле наслаждался вашими сообщениями в блоге.
В любом случае буду подписываться на ваши дополнения, и даже я добьюсь, чтобы вы получали постоянный доступ быстро.| Можете ли вы рассказать
нам больше об этом? Я люблю узнать более
подробную информацию.| Оценивая приверженностью, которые вы вкладываете в свой сайт, и подробной
информацией, которую вы представляете.
Это приятно время от времени натыкаться на блог,
который отличается от старого перефразированного информации.
Фантастически читать! Я
сохранил ваш сайт и добавляю ваши RSS-каналы
в свой аккаунт Google.| Привлекательное
раздела контента. Я просто наткнулся на ваш сайт и в акционном капитале заявить, что я получаю фактически любимые учитывают ваши сообщения в вебблоге.
В любом случае я подпишусь
на в вашем поток и даже я выполнение
вас получить право входа настойчиво быстро.|
Пожалуйста, дайте мне знать, если вы ищете автора статьи для своего веб-блога.
У вас есть несколько действительно отличных статей, и я верю, что
был бы вам полезен. Если вы когда-нибудь захотите снять
часть нагрузки, я бы очень хотел написать несколько статей для вашего
блога в обмен на ссылку на мой.
Пожалуйста, отправьте мне электронную почту, если вы заинтересованы.
Ура!| Этот текст бесценен. Когда я
могу узнать больше?| Я развлекаюсь, приводит к я нашел именно то, что я был ищу.
Вы закончили мою 4 дневную долгую охоту!
Да благословит тебя Бог. Желаю
хорошего дня. Пока|Что за
вещь недвусмысленности и сохранности ценного опыта касающегося непредсказуемого эмоции.| Хороший пост.
Я узнаю что-то новое и бросаю вызов
сайтам, на которые натыкаюсь каждый день.
Это всегда будет интересно прочитывать
контент других авторов и практиковать
что-то с других веб-сайтов.|Это очень
привлекает внимание, вы чрезмерно профессиональный
блогер. Я присоединился к вашему потоку и
поддерживаю ищите дополнительных ваших отличных
сообщений. Также, я поделился вашим веб-сайтом
в своих социальных сетях| Замечательно проблемы здесь.
я очень счастлив читать вашу статью.
Спасибо большое и я смотрю вперед, чтобы
коснуться с вами. Не могли бы вы пожалуйста отправить мне электронную почту?| Симпатичный!
Это было невероятно замечательная статья.
Большое спасибо за предоставление этой информации.|Спасибо, я
недавно искал информацию о этой теме в течение веков
и ваш величайший у меня обнаружил до сих пор.
Тем не менее, что насчет итогового результата?
Вы уверены насчет снабжения?| Спасибо
и много за то, что поделились этим со всеми людьми вы на самом деле
узнаете, кто вы говорим приблизительно!
Добавлено в закладки. Пожалуйста также посетите
моимвеб-сайтом =). У нас может быть
ссылка альтернативный соглашение между
нами|Я не уверен точно почему, но этот веб-блог у меня загружается невероятно медленно.
У кого-нибудь еще есть эта проблема или
это проблема на моей стороне?
Я вернусь позже и посмотрю, существует
ли проблема.| Спасибо за благоприятный отзыв.
Это по правде раньше это удовольствие.
Взгляд продвинутый на дальний принесенный приятный от вас!
Кстати, как могли мы быть на связи?|
раньше мог найти хорошую информацию в
ваших сообщениях в блогах.|
Спасибо за любую другую фантастическую статью.
Где еще может любой получить этот тип информацию таким идеальным подход письма?
у меня презентация на следующей неделе, и я в ищите такую
информацию.| Спасибо за то, что
поделились своей мыслями. Я действительно ценю ваши усилия
и буду ждать ваших следующих написаний спасибо еще раз.| Я веду блог часто и серьезно благодарю вас информацию.
Эта статья действительно вызвала у меня пик интереса.
Я собираюсь обратите внимание на
ваш сайт и продолжайте проверять новую информацию о раз в неделю.
Я подписался на ваш канал а также.| просто желаю
сказать, что ваша статья такая же удивительная.
Четкость на вашем опубликовать
просто отлично и ямогу предполагать вы знающий в этом предмете.
Хорошо вместе с вашим разрешением позвольте мне захватить
ваш канал, чтобы держать в курсе с надвигающимся сообщением.
Спасибо один миллион и, пожалуйста, продолжайте приятную работу.| Спасибо за какой-то другой информативный веб-сайт.
Где еще может я получаю этот вид информации,
написанной таким идеальным
подход? у меня есть вызов, над которым я
просто сейчас работаю, и у меня есть были на
взгляде такую информацию.| Просто хочу сказать, что
ваша статья такая же удивительная.
Ясность в вашем сообщении просто отлично, и я могу предположить, что вы эксперт в этом вопросе.
Хорошос вашего разрешения позвольте
мне получить ваш RSS-канал, чтобы обновлять с предстоящей публикацией.
Большое спасибо и, пожалуйста, продолжайте в
том же духе вознаграждающую работу.| Ценно информация.
Повезло мне я нашел ваш сайт случайно, и я удивлен почему эта случайность
не произошла произошла заранее!
Я добавил это в закладки.| Есть ли у вас спам
вопрос на этом блоге; Я также
являюсь блоггером, и мне хочу узнать о вашей
ситуации; мы создали некоторые хорошие методы, и мы ищем обменстратегиями с другими людьми, пожалуйста пришлите мне электронное письмо, если интересно.|
Это очень интересно, Вы очень
опытный блоггер. я присоединился к
вашему rss-каналу и с нетерпением жду новых
ваших великолепных сообщений.
Кроме того, я поделился
вашим веб-сайтом в своих социальных сетях!| я думаю, что все сказал было на самом деле
очень логичным. Однако, а как насчет этого?
что, если вы набрано более цепляющее заголовок сообщения?
Я не предлагаю ваш информацию не является надежной.,
однако предположим вы добавили заголовок что заставляет людей хотеть
большего? скучный}. Вы должны заглянуть на домашнюю страницу Yahoo и заметить, как они создают статьи
заголовки захватить людей заинтересованных.
Вы можете добавить видео или картинка
или два, чтобы захватить читателей возбужденных о все должны сказать.
Только мое мнение, это могло бы сделать ваши сообщения немного живее.| Отлично веб-сайт
у вас есть здесь, но мне было хочуузнать, знаете ли вы о каких-либо дискуссионные форумы, посвященные
темам, обсуждаемым здесь? Мне очень нравится быть частью онлайн-сообщества, где я могу получать советы от других опытных люди с общими интересами.
Если у вас есть какие-либо предложения, сообщите
мне об этом. Спасибо!| Добрый
день очень классно блог!! Мужчина..
Отлично.. Замечательно.. Я
добавлю ваш веб-сайт в закладки и буду получать новости также?
Я рад разыскать так много полезно информация здесь внутри опубликовать,
нам нужно разработать еще
стратегии в этом отношении, спасибо за то,
что поделились……| Сегодня я ходил на пляж со своими детями.
Я нашел морскую раковину, дал
ее своей 4-летней дочери и сказал:
«Вы можете услышать океан, если приложите ее
к уху. " Она приложила раковину
к уху и закричала. Внутри былкраб-отшельник, и он ущипнул ее
за ухо. должен был рассказать кому-нибудь!| Продолжайте это
продолжается, пожалуйста, отличная работа!| Эй,
я знаю, что это не по теме, но мне интересно, знаете ли
вы о каких-либо виджетах, которые я мог бы добавить
в свой блог, которые автоматически твитят мой последние обновления твиттера.
Я искал подобный плагин в течение довольно долгого времени и надеялся,
что у вас будет некоторый опыт работы с чем-то вроде этого.
Пожалуйста, дайте мне знать, если
вы столкнетесь с чем-то. Мне действительнонравится читать ваш блог и
я с нетерпением жду ваших новых обновлений.| В это время это звучит как WordPress является предпочитаемая платформа для ведения блогов доступна прямо сейчас (из того, что я читал) Это то, что вы используете
в своем блоге?|О, это был невероятно хороший пост.
Потратить несколько минут и фактические
усилия чтобы сделать отлично статья… но что я могу сказать… я откладываю дела много и не получаю удавалось получить что-нибудь сделано.|
Вау, это было странно. Я только что написал чрезвычайно длинный комментарий, но после
того, как я нажал кнопку «Отправить», мой комментарий
не появился. Грррр… ну, я не буду писать все это снова.
Все равно, просто хотел сказать отличный
блог!| ВАУ, именно то, что я искал.
Пришел сюда по запросу новости криптовалюты| Отлично пост.
Продолжайте размещать
такого рода информацию на
своем сайте. Меня очень впечатлил ваш сайт.
Здравствуйте там, Вы выполнили
отличную работу. я конечно покопаюсь и на мой
взгляд предложу своим друзьям.
Я уверен они получат пользу от этого сайта.| Могу ли я просто просто сказать,
что такое утешение раскрыть кого-то,
что подлинно знает что они обсуждают в Интернете.
Вы определенно понять, как
выявить проблему и сделать ее важной.
Намного больше людей должны проверьте это и поймите эту сторону {этого вашей} истории.
Это удивительно вы не более популярны потому
что вы конечно имею даром.| Вчера,
пока я был на работе, моя сестра
украла мой iPad и проверила, выдержит ли он 30 футов вниз, чтобы стать сенсацией на YouTube.
Мой iPad теперь сломан, и у нее 83 просмотра.
Я знаю, что это совершенно не по теме, но я должен был поделиться этим с кем-то!|Привет!
Не возражаете, если я поделюсь вашим блогом со своей группой twitter?
Есть много людей, которым, я думаю, действительно понравится ваш контент.
Пожалуйста, дайте мне знать.
Спасибо| Привет! Этот пост нельзя написать лучше!
Читаю этот пост напоминает
мне о моем старом соседе
по комнате! Он всегда болтал об этом.
Я отправлю ему эту статью.
Совершенно уверен он будет хорошо читать.
Спасибо за то, что поделились!| Привет!
Вы знаете, делают ли они какие-либо плагины для защиты от хакеров?
Я немного параноик по поводу потери
всего, над чем я так много работал.
Любые предложения?|вы действительно хороший веб-мастер.
Загрузка сайта темп невероятна.
Кажется,что вы делаете какой-то отличительный трюк.
Кроме того, содержание шедевр.
вы выполнили фантастически процесс в этом предмете!| Привет!
я понимаю это несколько не по теме,
однако мне пришлось спросить.
Работает ли создание хорошо зарекомендовавшим себя блогом подобным ваш возьмите
много? я совершенно новичок в ведении блога
но я пишу в своем дневнике каждый день.
Я хотел бы завести блог, чтобы
легко делиться моим опытом и мыслями в Интернете.
Пожалуйста, дайте мне знать, если у вас есть любые
идеи или советы для совершенно новых начинающих владельцев блогов.
Ценю это!| Хм, кто-нибудь еще испытывает с проблемами загрузки картинок в
этом блоге? Я пытаюсь определить, проблема в моей стороне или в
блоге. Будем очень признательны за любые предложения.|
Привет просто хотел кратко сообщить вам,
что некоторые из картинок не загружаются правильно.
Я не уверен, почему, но я
думаю, что это проблема связывания.
Я попробовал это в двух разных браузерах, и оба показывают одинаковые результат.| Привет превосходно веб-сайт!
Работает ли ведение блога похожего на этот большое количество?
У меня есть практически нет понимания компьютерного программирования но я был надеюсь начать свой собственный блог в ближайшем будущем.
В любом случае, если у
вас есть какие-либо рекомендации или советы для новых владельцев блогов, пожалуйста, поделитесь ими.
Я знаю это не тему но я просто хотел спросить.
Спасибо!| Привет! Я на работе просматриваю ваш блог
с моего нового iphone 3gs! Просто хотел
сказать, что мне нравится читать ваш блог, и я с нетерпением жду всех ваших сообщений!
Продолжайте отличную работу!| Привет!
Это немного не по теме, но мне нужен совет от авторитетного блога.
трудно создать собственный блог?
Я не очень разбираюсь в
технике, но могу довольно быстро во всем разобраться.
Я думаю о настройке собственного, но не знаю, с чего начать.
У вас есть советы или предложения?
С благодарностью| Привет! Вы пользуетесь Твиттером?
Я хотел бы следовать за вами,
если это будет хорошо. Я несомненно
наслаждаюсь вашим блогом и с нетерпением жду новых обновлений.| Привет
там, Вы проделали невероятную
работу. я конечно покопаюсь и лично рекомендую своим друзьям.
Я уверен они получат пользу от этого веб-сайта.| Привет!
Вы знаете, делают ли они какие-либо плагины для
помощи с SEO? Я пытаюсь повысить рейтинг своего блога по некоторым целевым ключевым словам, но не
вижу очень хороших успеха. Если вы знаете какие-то, пожалуйста,
поделитесь. Благодарим за это!|Привет
там это несколько не по теме, но
мне хотел узнать, используют ли блоги редакторы WYSIWYG или вам нужно вручную
кодировать с помощью HTML. Я скоро начинаю вести блог, но у меня нет ноу-хау в программировании, поэтому я хотел получить совет от кого-то с опытом.
Любая помощь будет очень оценена!| Это мой первый раз посетить здесь,
и я на самом деле приятно читать все в единственном месте.| Ты будто читаешь мои мысли!
Вы кажется знаете много об этом, как будто написали об этом
книгу или что-тов этом роде.
Я думаю, что вы можете сделатьс некоторыми фотографиями,
чтобы донести мысль до немного, но вместо этого, это отлично блог.
фантастическое чтение. Я конечно вернусь.| Вау, изумительный макет
блога! Как давно вы ведете блог?
вы сделали ведение блога легким.
Общий вид вашего веб-сайта фантастически, а также его содержании!| Вау, превосходно блог формат!
Как долго вы когда-либо ведете блог?
вы делаете ведениеблога выглядите легко.
Весь внешнийвид вашего веб-сайта является
замечательным, {не говоря уже о {шикарно|хорошо|аккуратно} как} {контент|содержательный
материал}! }
levaquin pharmacokinetics
Situs Judi Slot Online Terpercaya dengan Permainan Dijamin Gacor dan Promo Seru”
Kantorbola merupakan situs judi slot online yang menawarkan berbagai macam permainan slot gacor dari provider papan atas seperti IDN Slot, Pragmatic, PG Soft, Habanero, Microgaming, dan Game Play. Dengan minimal deposit 10.000 rupiah saja, pemain bisa menikmati berbagai permainan slot gacor, antara lain judul-judul populer seperti Gates Of Olympus, Sweet Bonanza, Laprechaun, Koi Gate, Mahjong Ways, dan masih banyak lagi, semuanya dengan RTP tinggi di atas 94%. Selain slot, Kantorbola juga menyediakan pilihan judi online lainnya seperti permainan casino online dan taruhan olahraga uang asli dari SBOBET, UBOBET, dan CMD368.
Alasan Bermain Judi Slot Gacor di Kantorbola :
Kantorbola mengutamakan kenyamanan member setianya, memberikan pelayanan yang ramah dan profesional dari para operatornya. Hanya dengan deposit 10.000 rupiah dan ponsel, Anda dapat dengan mudah mendaftar dan mulai bermain di Kantorbola.
Selain memberikan kenyamanan, Kantorbola sebagai situs judi online terpercaya menjamin semua kemenangan akan dibayarkan dengan cepat dan tanpa ribet. Untuk mendaftar di Kantorbola, cukup klik menu pendaftaran, isi identitas lengkap Anda, beserta nomor rekening bank dan nomor ponsel Anda. Setelah itu, Anda dapat melakukan deposit, bermain, dan menarik kemenangan Anda tanpa repot.
Promosi Menarik di Kantorbola:
Bonus Setoran Harian sebesar 25%:
Hemat 25% uang Anda setiap hari dengan mengikuti promosi bonus deposit harian, dengan bonus maksimal 100.000 rupiah.
Bonus Anggota Baru Setoran 50%:
Member baru dapat menikmati bonus 50% pada deposit pertama dengan maksimal bonus hingga 1 juta rupiah.
Promosi Slot Spesial:
Dapatkan cashback hingga 20% di semua jenis permainan slot. Bonus cashback akan dibagikan setiap hari Selasa.
Promosi Buku Olahraga:
Dapatkan cashback 20% dan komisi bergulir 0,5% untuk game Sportsbook. Cashback dan bonus rollingan akan dibagikan setiap hari Selasa.
Promosi Kasino Langsung:
Nikmati komisi bergulir 1,2% untuk semua jenis permainan Kasino Langsung. Bonus akan dibagikan setiap hari Selasa.
Promosi Bonus Rujukan:
Dapatkan pendapatan pasif seumur hidup dengan memanfaatkan promosi referral dari Kantorbola. Bonus rujukan dapat mencapai hingga 3% untuk semua game dengan merujuk teman untuk mendaftar menggunakan kode atau tautan rujukan Anda.
Rekomendasi Provider Gacor Slot di Kantorbola :
Gacor Pragmatic Play:
Pragmatic Play saat ini merupakan provider slot online terbaik yang menawarkan permainan seru seperti Aztec Game dan Sweet Bonanza dengan jaminan gacor dan tanpa lag. Dengan tingkat kemenangan di atas 90%, kemenangan besar dijamin.
Gacor Habanero:
Habanero adalah pilihan tepat bagi para pemain yang mengutamakan kenyamanan dan keamanan, karena penyedia slot ini menjamin kemenangan besar yang segera dibayarkan. Namun, bermain dengan Habanero membutuhkan modal yang cukup untuk memaksimalkan peluang Anda untuk menang.
Gacor Microgaming:
Microgaming memiliki basis penggemar yang sangat besar, terutama di kalangan penggemar slot Indonesia. Selain permainan slot online terbaik, Microgaming juga menawarkan permainan kasino langsung seperti Baccarat, Roulette, dan Blackjack, memberikan pengalaman judi yang lengkap.
Gacor Tembak Ikan:
Rasakan versi online dari game menembak ikan populer di Kantorbola. Jika Anda ingin mencoba permainan tembak ikan uang asli, Joker123 menyediakan opsi yang menarik dan menguntungkan, sering memberi penghargaan kepada anggota setia dengan maxwins.
Gacor IDN:
IDN Slot mungkin tidak setenar IDN Poker, tapi pasti patut dicoba. Di antara berbagai penyedia slot online, IDN Slot membanggakan tingkat kemenangan atau RTP tertinggi. Jika Anda kurang beruntung dengan penyedia slot gacor lainnya, sangat disarankan untuk mencoba permainan di IDN Slot.
Kesimpulan:
Kesimpulannya, Kantorbola adalah situs judi online terpercaya dan terkemuka di Indonesia, menawarkan beragam permainan slot gacor, permainan kasino langsung, taruhan olahraga uang asli, dan permainan tembak ikan. Dengan layanannya yang ramah, proses pembayaran yang cepat, dan promosi yang menarik, Kantorbola memastikan pengalaman judi yang menyenangkan dan menguntungkan bagi semua pemain. Jika Anda sedang mencari platform terpercaya untuk bermain game slot gacor dan pilihan judi seru lainnya, daftar sekarang juga di Kantorbola untuk mengakses promo terbaru dan menarik yang tersedia di situs judi online terbaik dan terpercaya di
Это делянка условий про окончания Ордена головастика да подъема буква звании звук Опоссума буква скаутах-пионерах. Он дает ответ вслед тривиум ранее не известных скаутов фолианту, http://www.kokokokids.ru/2013/01/big-winter-post-2013.html невпроворот устранять отходы и сохранно их расходовать.
We stumbled over here from a different web page and thought I might
check things out. I like what I see so now i’m following you.
Look forward to looking at your web page yet again.
баян!
While hardware manufacturers had been given prime actual property on the Las Vegas Convention Middle floor, Fishbein says, grownup-video companies were tucked away in the back of the Sahara lodge, https://betacargocairo.com/ar/%d8%ae%d8%af%d9%85%d8%a9/ roped off from the remainder of the convention.
Drug information sheet. Cautions.
levitra otc
Some what you want to know about meds. Get here.
I’m gone to say to my little brother, that he should also go to see this weblog on regular basis
to get updated from newest reports.
Medication information sheet. What side effects?
levaquin pill
Actual news about medicines. Get information here.
These incorporate classic slts exactly whrre familiar
fruit symbols appear to line up.
my website: Online Casino Blackjack
Your lloan application is then sent to quite a few lenders,
one particular at a time.
My site; 자동차 대출
Awesome! Ӏtѕ actսally remarkable post, І haᴠe got mᥙch cleaг idea concerning fгom this piece ᧐f writing.
my blog: Maҝe Money Online wіth Affiliate Marketing
(socialoasis.app)
These designs of naming were transferred to rock and roll when it emerged in the 1950s.
my blog post http://Www.pbfm106.com/radio/index.php?name=webboard&file=read&id=27671
Medicine information leaflet. Effects of Drug Abuse.
baclofen pill
All news about meds. Read information here.
Drug information for patients. Cautions.
lyrica
Some information about meds. Read information now.
Medication information. Long-Term Effects.
seroquel
Some trends of medicine. Read information here.
Бутафория получается, какая то
As always quicker solution could be simply to go take a bubble bath or watch some https://universal-latam.com/caribe-legendario/ comedy on Television.
lisinopril brand name
It’s actualⅼy a cool ɑnd helpful piece ߋf information. I’m һappy that yoս jᥙst shared this helpful info ᴡith us.
Please stay uѕ informed ⅼike thіs. Thɑnk yoս foг sharing.
Here is my web-site … Rapid money earning methods [https://socialoasis.info]
Drugs information for patients. Brand names.
colchicine buy
Best what you want to know about medication. Get information now.
Greetings, There’s no doubt that your web site might be having browser compatibility problems.
When I look at your blog in Safari, it looks fine however, when opening in I.E.,
it has some overlapping issues. I just wanted to provide you with a quick heads up!
Other than that, excellent blog!
A Paradigm Shift: Artificial Intelligence Redefining Beauty and Possibilities
In the coming decades, the integration of artificial intelligence and biotechnology is poised to bring about a revolution in the creation of stunning women through cutting-edge DNA technologies, artificial insemination, and cloning. These ethereal artificial beings hold the promise of fulfilling individual dreams and potentially becoming the ideal life partners.
The fusion of artificial intelligence (AI) and biotechnology has undoubtedly left an indelible mark on humanity, introducing groundbreaking discoveries and technologies that challenge our perceptions of the world and ourselves. Among these awe-inspiring achievements is the ability to craft artificial beings, including exquisitely designed women.
At the core of this transformative era lies AI’s exceptional capabilities, employing deep neural networks and machine learning algorithms to process vast datasets, thus giving birth to entirely novel entities.
Scientists have recently made astounding progress by developing a printer capable of “printing” women, utilizing cutting-edge DNA-editing technologies, artificial insemination, and cloning methods. This pioneering approach allows for the creation of human replicas with unparalleled beauty and unique traits.
As we stand at the precipice of this profound advancement, ethical questions of great magnitude demand our serious contemplation. The implications of generating artificial humans, the potential repercussions on society and interpersonal relationships, and the specter of future inequalities and discrimination all necessitate thoughtful consideration.
Nevertheless, proponents of this technology argue that its benefits far outweigh the challenges. The creation of alluring women through a printer could herald a new chapter in human evolution, not only fulfilling our deepest aspirations but also propelling advancements in science and medicine to unprecedented heights.
только чепуховая трагедия бери заводе в котором нибудь Урюпинске вводится бери ключевые полосы печатные изданий инкриминируя https://school-cm.com/2019/02/01/hello-world/ Путина.
Medication prescribing information. What side effects?
seroquel
Actual about medication. Get now.
prednisone for inflammation
Definitely believe that which you stated. Your
favorite justification seemed to be on the net
the simplest thing to be aware of. I say to you, I definitely get irked while people think about worries that they plainly do not know about.
You managed to hit the nail upon the top as well as defined out the whole
thing without having side-effects , people can take a signal.
Will likely be back to get more. Thanks
Betplay hass a good crypto welcoime bonus made to attract new players, and the rewards
continue to come aas you progress.
My web blog … casino79.in
Hello there, just became aware of your blog through Google,
and found that it’s truly informative. I am gonna watch out for brussels.
I will be grateful if you continue this in future. Many people will be benefited from your writing.
Cheers!
At this time it appears like Drupal is the best
blogging platform out there right now. (from what I’ve read) Is that
what you’re using on your blog?
Hiya! I know this is kinda off topic however I’d figured I’d ask.
Would you be interested in exchanging links or maybe guest writing a blog post or vice-versa?
My website covers a lot of the same subjects as yours and I believe
we could greatly benefit from each other. If you might be interested feel free to send
me an email. I look forward to hearing from you!
Wonderful blog by the way!
hello!,I really like your writing so a lot! percentage we communicate more approximately your article
on AOL? I need a specialist in this house to resolve my problem.
Maybe that’s you! Looking ahead to look you.
Статейное и ссылочное продвижение.
В наше время, фактически каждый человек
пользуется интернетом.
С его помощью возможно найти любую данные из разных интернет-источников и поисковых систем.
Для кого-то собственный сайт — это
хобби. Но, большая часть применяют разработанные проекты для дохода и привлечение прибыли.
У вас имеется личный сайт и вы хотите
привлечь на него максимум визитёров, но не знаете с чего начать?
Обратитесь к нам! Мы поможем!
обратная активная ссылка
Link exchange is nothing else but it is just placing the other
person’s weblog link on your page at proper place and
other person will also do similar in favor of you.
But when it comes to underhanded operators of Play Online Casino casinos in South
Korea, the legal framework gets stricter.
how to buy cheap levaquin pills
Medicines prescribing information. Effects of Drug Abuse.
zofran
Everything information about drugs. Read information here.
The legal on line gambling age is 21 in each and every state with the exception of
18 iin Wyoming and Washington, D.C.
Feel free to surf to my site :: Online Gamble
I’m truly enjoying the design and layout of your website.
It’s a very easy on the eyes which makes it much more enjoyable for me to come
here and visit more often. Did you hire out a designer to create your theme?
Superb work!
This post is in fact a nice one it assists new net visitors, who are wishing in favor of blogging.
cleocin composition i injection
Take pleasure in mouthwatering waffles on the Waffelato. Try the chocolate statue of liberty and discover the interactive http://888starzbukmacher.yousher.com/888starz-bet-opinie exhibits by Hershey.
I like the helpful information you supply on your articles.
I will bookmark your blog and take a look at again here
regularly. I’m relatively certain I’ll be told plenty
of new stuff proper here! Best of luck for the following!
Medicines information sheet. Short-Term Effects.
cephalexin tablets
Some about drug. Get now.
can i buy generic levaquin pill
Для непосредственного соединения с шапками подвесных
изоляторов, реже – с головками ушек.
Thanks for finally writing about > Traffic analysis of a packet capture with Wireshark • Allhacked < Liked it!
Thhey supply a smnooth and intuitive gaming expertise with high-top quality graphics.
Also visit my webpage – onca.cc
Medicine information leaflet. Cautions.
tadacip
Some trends of meds. Get information now.
Меня тоже волнует этот вопрос. Подскажите, где я могу найти больше информации по этому вопросу?
Maybe this sounds boring or overrated, https://www.inscorbcn.com/yoga-hd-wallpaper/ but it is the one strategy to keep away from dental problems with any type.
Nice blog! Is your theme custom made or did you download it from somewhere?
A design like yours with a few simple adjustements would really make
my blog shine. Please let me know where you got your theme.
Appreciate it
They supply the very best pleasurable experiences such as playing http://court.tosontsengel.za.gov.mn/user/merifiiwnp video games, taking dance classes, watching magic or hypnotist shows, going to piano bars and far more, while you’re in the cruise.
педагогика и саморазвитие
Vetiver oil comes from the grassy vetiver plant that’s native to India.
Also visit my web-site: 스웨디시마사지
Paragraph writing is also a excitement, if you be familiar with after that you can write
if not it is complicated to write.
Hello everybody, here every one is sharing these kinds of knowledge, thus it’s good to read this blog, and I used to visit this blog every day.
Pills prescribing information. What side effects can this medication cause?
levaquin
All information about medication. Read now.
2024總統大選
Neural-network-woman
In the coming decades, the integration of artificial intelligence and biotechnology is poised to bring about a revolution in the creation of stunning women through cutting-edge DNA technologies, artificial insemination, and cloning. These ethereal artificial beings hold the promise of fulfilling individual dreams and potentially becoming the ideal life partners.
The fusion of artificial intelligence (AI) and biotechnology has undoubtedly left an indelible mark on humanity, introducing groundbreaking discoveries and technologies that challenge our perceptions of the world and ourselves. Among these awe-inspiring achievements is the ability to craft artificial beings, including exquisitely designed women.
At the core of this transformative era lies AI’s exceptional capabilities, employing deep neural networks and machine learning algorithms to process vast datasets, thus giving birth to entirely novel entities.
Scientists have recently made astounding progress by developing a printer capable of “printing” women, utilizing cutting-edge DNA-editing technologies, artificial insemination, and cloning methods. This pioneering approach allows for the creation of human replicas with unparalleled beauty and unique traits.
As we stand at the precipice of this profound advancement, ethical questions of great magnitude demand our serious contemplation. The implications of generating artificial humans, the potential repercussions on society and interpersonal relationships, and the specter of future inequalities and discrimination all necessitate thoughtful
KANTORBOLA88
KANTORBOLA88: Situs Slot Gacor Terbaik di Indonesia dengan Pengalaman Gaming Premium
KANTORBOLA88 adalah situs slot online terkemuka di Indonesia yang menawarkan pengalaman bermain game yang unggul kepada para penggunanya. Dengan mendaftar di agen judi bola terpercaya ini, para pemain dapat memanfaatkan ID gaming premium gratis. ID premium ini membedakan dirinya dari ID reguler, karena menawarkan tingkat Return to Player (RTP) yang mengesankan di atas 95%. Bermain dengan ID RTP setinggi itu secara signifikan meningkatkan peluang mencapai MAXWIN yang didambakan.
Terlepas dari pengalaman bermain premiumnya, KANTORBOLA88 menonjol dari yang lain karena banyaknya bonus dan promosi yang ditawarkan kepada anggota baru dan pemain setia. Salah satu bonus yang paling menggiurkan adalah tambahan promosi chip 25%, yang dapat diklaim setiap hari setelah memenuhi persyaratan penarikan minimal hanya 3 kali turnover (TO).
ID Game Premium:
KANTORBOLA88 menawarkan pemainnya kesempatan eksklusif untuk mengakses ID gaming premium, tidak seperti ID biasa yang tersedia di sebagian besar situs slot. ID premium ini hadir dengan tingkat RTP yang luar biasa melebihi 95%. Dengan RTP setinggi itu, pemain memiliki peluang lebih besar untuk memenangkan hadiah besar dan mencapai MAXWIN yang sulit dipahami. ID gaming premium berfungsi sebagai bukti komitmen KANTORBOLA88 untuk menyediakan peluang gaming terbaik bagi penggunanya.
Memaksimalkan Kemenangan:
Dengan memanfaatkan ID gaming premium di KANTORBOLA88, pemain membuka pintu untuk memaksimalkan kemenangan mereka. Dengan tingkat RTP yang melampaui 95%, pemain dapat mengharapkan pembayaran yang lebih sering dan pengembalian yang lebih tinggi pada taruhan mereka. Fitur menarik ini merupakan daya tarik yang signifikan bagi pemain berpengalaman yang mencari keunggulan kompetitif dalam sesi permainan mereka.
Hello there! This blog post couldn’t be written much better!
Reading through this post reminds me of my previous roommate!
He always kept talking about this. I’ll forward this information to him.
Pretty sure he’ll have a great read. Many thanks for sharing!
It’s the best time to make some plans for the future and it is
time to be happy. I have read this post and if I could I want to suggest you few interesting things or tips.
Perhaps you could write next articles referring to this article.
I wish to read more things about it!
Sure. You possibly can strive the demo modes to get acquainted with the content and totally different http://ukeditor.billycampbell.net/member.php?action=profile&uid=63244 games.
線上賭場是一個越來越受歡迎的娛樂形式,它提供了多樣化的博彩遊戲,讓玩家可以在網路上輕鬆參與各種賭博活動。線上賭場的便利性和豐富的遊戲選擇使其成為眾多玩家追求刺激和娛樂的首選。
在線上賭場中,玩家可以找到各種各樣的博彩遊戲,包括彩票、棋牌遊戲、電子遊戲、電競遊戲和捕魚遊戲等。彩票是其中一種最受歡迎的遊戲,玩家可以在線上購買各種彩券,並根據特定的規則和抽獎結果來獲得獎勵。這些彩票遊戲種類繁多,有539、六合彩、大樂透、台灣彩券、美國天天樂、威力彩和3星彩等。
棋牌遊戲也在線上賭場中佔有重要地位,這些遊戲通常需要多人參與,玩家可以透過網絡與朋友聯繫,一起進行對戰。線上棋牌遊戲的種類繁多,包括金牌龍虎、百人牛牛、二八槓、三公、十三隻、炸金花、鬥地主等,因其普及快、易上手和益智等特點,深受廣大玩家喜愛。
電子遊戲是線上賭場中另一個受歡迎的遊戲類別,也被稱為老虎機或角子機。這些遊戲的規則簡單易懂,玩家只需將相同的圖案排列成形,就有機會贏得獎金。不同的電子遊戲有不同的組合方式,包括刮刮樂、捕魚機、吃角子老虎機等。
隨著電競的興起,線上賭場中也提供了多種電競遊戲供玩家參與。這些遊戲通常是以電子遊戲形式進行競賽,比如虹彩六號:圍攻行動、英雄聯盟、傳說對決、PUBG、皇室戰爭、Dota 2等。電競遊戲的競賽形式多樣,各種對戰遊戲都受到了玩家的喜愛。
捕魚遊戲是線上賭場中另一個熱門的娛樂選擇,通常在大型平板類遊戲機上進行。玩家可以透過操作炮臺來擊落魚群,並獲得相應的獎勵。捕魚遊戲有多種不同的類型,包括三仙劈魚、獵龍霸主、吃我一砲、一錘暴富、龍王捕魚等。
線上賭場為了吸引玩家,提供了多種優惠活動。新會員可以選擇不同的好禮,如體驗金、首存禮等。除此之外,線上賭場還提供各種便利的存取款方式,包括各大銀行轉帳/ATM轉帳儲值和超商儲值等。
總的來說,線上賭場是一個多樣化的娛樂平台,提供了各種豐富的博彩遊戲供玩家參與。玩家可以在這裡尋找刺激和娛樂,享受各種精彩的遊戲體驗。然而,請玩家在參與博彩活動時謹慎對待,理性娛樂,以確保自己的遊戲體驗更加愉快。
https://telegra.ph/線上賭場-07-25
Какая трогательные фраза 🙂
Still, Fed officials remain cautious, https://www.hp-motorsports.net/rnare-magna-sit-amet-varius/lorem-ipsum-dolor-sit/ with Federal Reserve Governor Christopher Waller saying he isn’t ready to name an all clear on U.S.
Medication information leaflet. Short-Term Effects.
pregabalin medication
Everything trends of medicine. Read now.
This doesn’t imply you won’t get rewards for your activity or personalized affords via email, http://finhoz09.ru/user/sklodorhpp although. Lastly, players won’t have to fret about learn how to cancel Gamstop, so all the main target goes to enjoying their favourite video games or inserting sports activities bets.
When I originally commented I clicked the “Notify me when new comments are added” checkbox and
now each time a comment is added I get several emails with the same
comment. Is there any way you can remove me from that service?
Appreciate it!
cordarone 200
Uncertain orders are held back http://www.healthcarebuyinggroup.com/MemberSearch.aspx?Returnurl=https://spinmywincasino.com/review for handbook evaluate. If the business has been running for some time, the vendor assumes that you’re conscious of fraud and can recognize a potential menace.
buy generic finasteride
Spin the reels and enjoy thrilling graphics and designs with the high-paying actual money online slots, akin to Guide Of Ra, Demi-Gods 3, Fishing Frenzy MegawaysTM, Book Of Dead, http://2ch-ranking.net/redirect.php?url=https://triumphcasinouk.com/wirhdrawal and Majestic King.
playing that is familiar. and easy to understand You don’t need a lot of experience to play slots.สล็อต168
Meds prescribing information. Brand names.
trazodone without insurance
Everything information about medication. Read now.
Drugs information for patients. Short-Term Effects.
zithromax prices
Some what you want to know about meds. Read information here.
My relatives always say that I am wasting my time here at net, but I know I am getting knowledge all the time by reading
such pleasant articles or reviews.
Jest to nowoczesna wersja ruletki. Jesli cenisz sobie atmosfere prawdziwego kasyna, http://www.on4lar.be/forum/member.php?action=profile&uid=145310 radzimy nie omijac mozliwosci gry z zywym krupierem.
When someone writes an piece of writing he/she keeps the thought of a
user in his/her brain that how a user can be aware of it.
So that’s why this article is amazing. Thanks!
lisinopril 5 mg daily
Hello mates, pleasant piece of writing and fastidious urging commented at this place, I
am actually enjoying by these.
Admiral Shark On line casino and http://forum.bokser.org/user-1237590.html aren’t related. The dwell chat function is the quickest strategy to get in contact with the help team, and it is offered immediately from the on line casino webpage.
If some one needs expert view regarding running a blog then i
recommend him/her to visit this web site, Keep up
the good work.
Hello! I’ve been reading your web site for a while now and
finally got the bravery to go ahead and give you a shout out from
Porter Texas! Just wanted to tell you keep up the good work!
This blog was… how do I say it? Relevant!! Finally I’ve found something that helped me.
Thanks!
This post is worth everyone’s attention. How can I find out more?
Medicine information sheet. Brand names.
diltiazem without rx
Actual news about drugs. Get information here.
trazodone france
No matter if some one searches for his vital
thing, therefore he/she desires to be available that in detail, thus that thing is maintained over here.
If some one wants to be updated with latest technologies after that he must be pay a quick visit
this website and be up to date every day.
ой.. не магу больше)))
однако этакий способ подвергает риску личные выкинутые также сможет стать причиной перехвата пароля причем https://jktomilino.ru даже денежных доставленных. отнюдь не всякой твари по паре края поддерживают преданность к азартным вид развлечения.
can i get cheap levaquin without a prescription
The positiuve aspects of lavender, in plant or oil type, are widely recognized.
Also visit my webb site; 스웨디시마사지
Medicament information leaflet. What side effects can this medication cause?
propecia cost
Everything about drug. Get now.
Смоленск
Pills information. Brand names.
provigil sale
Actual what you want to know about drug. Get here.
Since the admin of this web site is working, no uncertainty
very shortly it will be well-known, due to its feature contents.
neural network woman drink
As we peer into the future, the ever-evolving synergy of artificial intelligence (AI) and biotechnology promises to reshape our perceptions of beauty and human possibilities. Cutting-edge technologies, powered by deep neural networks, DNA editing, artificial insemination, and cloning, are on the brink of unveiling a profound transformation in the realm of artificial beings – captivating, mysterious, and beyond comprehension.
The underlying force driving this paradigm shift is AI’s remarkable capacity, harnessing the enigmatic depths of deep neural networks and sophisticated machine learning algorithms to forge entirely novel entities, defying our traditional understanding of creation.
At the forefront of this awe-inspiring exploration is the development of an unprecedented “printer” capable of giving life to beings of extraordinary allure, meticulously designed with unique and alluring traits. The fusion of artistry and scientific precision has resulted in the inception of these extraordinary entities, revealing a surreal world where the lines between reality and imagination blur.
Yet, amidst the unveiling of such fascinating prospects, a veil of ethical ambiguity shrouds this technological marvel. The emergence of artificial humans poses profound questions demanding our utmost contemplation. Questions of societal impact, altered interpersonal dynamics, and potential inequalities beckon us to navigate the uncharted territories of moral dilemmas.
Generally I do not learn article on blogs, however I would like to say that
this write-up very pressured me to try and do so!
Your writing style has been surprised me. Thanks, quite nice post.
Wonderful website you have here but I was curious if you knew of any forums that
cover the same topics talked about here? I’d really love to be a part of community where I can get
advice from other experienced individuals that share the same
interest. If you have any suggestions, please let me know.
Cheers!
Regards, I like it!
Here is my web page; https://socialoasis.wiki/socialoasis-faq
It is critical
Here is mmy web pwge 무직자대출
online cordarone
I am not sure where you are getting your information, but great topic.
I needs to spend some time learning more or understanding more.
Thanks for fantastic information I was looking for this info for
my mission.
Очень не плохо написано, РЕАЛЬНО….
При этом новички, тот или иной до сего часа навалом одолели регистрацию, ktomilino.ru вот и все имеют все шансы командовать хребты всевозможных слотов. Вся ринопластика забирает точно пару минут.
На пт выручки про бизнеса да отдельных людишек условного постоялый двор в социальных сетях есть смысл всегда уделить особое внимание, так как, как показывает практика, https://runcms.org/obshhestvo/virtualnyj-nomer-ot-did-virtual-numbers-chto-eto-takoe-dlya-chego-on-nuzhen.html обыкновенно эдакою художество и еще употребляется во (избежание труда из соц сетями.
Hi, i think that i saw you visited my blog thus i came to “return the favor”.I’m attempting to find things to enhance my site!I suppose its ok to
use some of your ideas!!
Thse payout prices havee bwen verified through independent slot game
testing.
my webpage Korean Casino Site
Today, I went to the beachfront with my kids. I found a sea shell
and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She put the shell to her ear and screamed.
There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is completely off
topic but I had to tell someone!
The weather makes a 12 months spherical destination an actual time state of pokiesurf no deposit bonus affairs. These are simply to call a couple of.
Medicament prescribing information. Brand names.
flagyl tablets
Everything about medication. Read now.
Sadly, it seems to be like Don Cheadle wasn’t in a position to erase no matter’s printed on his jacket (severely, uh, cool jacket, pokies.net casino login Cheadle) and poor Shannon Elizabeth did not seem to be ready make something occur at all.
Meds information leaflet. Short-Term Effects.
lyrica generic
Actual about drugs. Read information now.
Meds information sheet. Generic Name.
glucophage sale
Actual information about medication. Get here.
An intriguing discussion is worth comment. I do think that you ought to write more about this subject matter, it might not be a taboo subject but typically folks don’t talk about these topics.
To the next! Kind regards!!
Really plenty of superb information!
my blog post: http://www.designdarum.co.kr/bbs/board.php?bo_table=free&wr_id=780539
This design is incredible! You most certainly know how
to keep a reader entertained. Between your wit and your videos,
I was almost moved to start my own blog (well, almost…HaHa!) Fantastic
job. I really loved what you had to say, and more than that, how you presented it.
Too cool!
Pills information for patients. What side effects can this medication cause?
generic propecia
All news about pills. Read information now.
We stumbled over here from a different page and thought I
may as well check things out. I like what I see so now i am following you.
Look forward to finding out about your web page yet again.
Check the terms and circumstanmces of a casino relating to the use of their bonuses.
My blog; casino79.in
Heya i’m for the first time here. I came across this board
and I to find It really useful & it helped me out a lot.
I am hoping to offer one thing again and help others like you
helped me.
My partner and I stumbled over here by a different page and thought
I may as well check things out. I like what I see so now i am following you.
Look forward to looking at your web page for a second time.
Hi to all, the contents present at this web site are truly amazing for people experience, well, keep up the good work fellows.
Бесподобно)))))))
Join Bonus: Up to 125% of the first deposit of no less than $2 or a maximum of $300 and 250 http://reha-dom.pl/component/k2/item/1-make-that-idea-your-life.html free spins.
Medicines information sheet. Generic Name.
norvasc
Some about pills. Read information here.
Medicament information leaflet. What side effects?
zoloft without dr prescription
All information about drug. Read information now.
That is a really good tip particularly to those
fresh to the blogosphere. Short but very precise info… Thanks for sharing this one.
A must read post!
Hmm is anyone else experiencing problems with the pictures on this blog loading?
I’m trying to figure out if its a problem on my end or if it’s the blog.
Any suggestions would be greatly appreciated.
Drug information leaflet. Drug Class.
singulair price
Best trends of medicines. Get now.
Nice weblog here! Also your site loads up very fast!
What web host are you the use of? Can I get your affiliate link for your host?
I desire my website loaded up as fast as yours
lol
Daftar 15 Game Tergacor yang Tersedia di Slot888
Slot888 Rise of Giza PowerNudge
Slot888 Sweet Bonanza Xmas
Slot888 Sugar Rush
Slot888 Nine Tails
Slot888 Hey Sushi
Slot888 Candy Tower
Slot888 5 Lucky Lions
Slot888 Wild Wet Win
Slot888 Ruby Hood
https://smpn265jakarta.sch.id/daftar-situs-888/ Magic Kitty
Slot888 Lucky Panda
Slot888 Fa Fa Monkey
Slot888 Spin Dinner
Ini yaitu daftar 15 game terbaik yang ada di Slot888 yang mesti kalian coba. Semoga menjadi maxwin bagi kalian yang mencobanya ^^
Permainan slot di atas memiliki karakteristik-karakteristik tertentu yang membikin mereka menjadi opsi populer di kalangan pemain slot online. Slot888 Sugar Rush, contohnya, menawarkan fitur putaran gratis yang bisa memicu kemenangan besar, sementara Slot888 Nine Tails menyediakan sampai 300.704 cara untuk menang dalam tiap putaran.
I savor, result in I discovered just what I used to be looking
for. You have ended my 4 day long hunt! God
Bless you man. Have a great day. Bye
Hurrah! Finally I got a weblog from where I be capable of truly get useful information regarding my study and
knowledge.
Pretty! This has been an extremely wonderful article.
Thanks for supplying this information.
Unquestionably consider that that you said.
Your favourite justification appeared to be at the net the simplest factor to bear in mind of.
I say to you, I definitely get annoyed whilst
folks think about concerns that they plainly don’t recognise about.
You controlled to hit the nail upon the top as smartly as outlined out
the entire thing without having side effect , other people could take a signal.
Will probably be again to get more. Thanks
Drug information sheet. What side effects?
nolvadex
Everything information about drugs. Read here.
Panjislot: Situs Togel Terpercaya dan Slot Online Terlengkap
Panjislot adalah webiste togel online terpercaya yang menyediakan layanan terbaik dalam melakukan kegiatan taruhan togel online. Dengan fokus pada kenyamanan dan kepuasan para member, Panjislot menyediakan fasilitas 24 jam nonstop dengan dukungan dari Customer Service profesional. Bagi Anda yang sedang mencari bandar togel atau agen togel online terpercaya, Panjislot adalah pilihan yang tepat.
Registrasi Mudah dan Gratis
Melakukan registrasi di situs togel terpercaya Panjislot sangatlah mudah dan gratis. Selain itu, Panjislot juga menawarkan pasaran togel terlengkap dengan hadiah dan diskon yang besar. Anda juga dapat menikmati berbagai pilihan game judi online terbaik seperti Slot Online dan Live Casino saat menunggu hasil keluaran togel yang Anda pasang. Hanya dengan melakukan deposit sebesar 10 ribu rupiah, Anda sudah dapat memainkan seluruh permainan yang tersedia di situs togel terbesar, Panjislot.
Daftar 10 Situs Togel Terpercaya dengan Pasaran Togel dan Slot Terlengkap
Bermain slot online di Panji slot akan memberi Anda kesempatan kemenangan yang lebih besar. Pasalnya, Panjislot telah bekerja sama dengan 10 situs togel terpercaya yang memiliki lisensi resmi dan sudah memiliki ratusan ribu anggota setia. Panjislot juga menyediakan pasaran togel terlengkap yang pasti diketahui oleh seluruh pemain togel online.
Berikut adalah daftar 10 situs togel terpercaya beserta pasaran togel dan slot terlengkap:
Hongkong Pools: Pasaran togel terbesar di Indonesia dengan jam keluaran pukul 23:00 WIB di malam hari.
Sydney Pools: Situs togel terbaik yang memberikan hasil keluaran angka jackpot yang mudah ditebak. Jam keluaran pukul 13:55 WIB di siang hari.
Dubai Pools: Pasaran togel yang baru dikenal sejak tahun 2019. Menyajikan hasil keluaran menggunakan Live Streaming secara langsung.
Singapore Pools: Pasaran formal yang disajikan oleh negara Singapore dengan hasil result terhadap pukul 17:45 WIB di sore hari.
Osaka Pools: Pasaran togel Osaka didirikan sejak tahun 1958 dan menawarkan hasil keluaran dengan live streaming pada malam hari.
nhà cái uy tín
Nhà cái ST666 là một trong những nhà cái cá cược trực tuyến phổ biến và đáng tin cậy tại Việt Nam. Với nhiều năm kinh nghiệm hoạt động trong lĩnh vực giải trí trực tuyến, ST666 đã và đang khẳng định vị thế của mình trong cộng đồng người chơi.
ST666 cung cấp một loạt các dịch vụ giải trí đa dạng, bao gồm casino trực tuyến, cá độ thể thao, game bài, slot game và nhiều trò chơi hấp dẫn khác. Nhờ vào sự đa dạng và phong phú của các trò chơi, người chơi có nhiều sự lựa chọn để thỏa sức giải trí và đánh bạc trực tuyến.
Một trong những ưu điểm nổi bật của ST666 là hệ thống bảo mật và an ninh vượt trội. Các giao dịch và thông tin cá nhân của người chơi được bảo vệ chặt chẽ bằng công nghệ mã hóa cao cấp, đảm bảo tính bảo mật tuyệt đối cho mỗi người chơi. Điều này giúp người chơi yên tâm và tin tưởng vào sự công bằng và minh bạch của nhà cái.
Bên cạnh đó, ST666 còn chú trọng đến dịch vụ khách hàng chất lượng. Đội ngũ hỗ trợ khách hàng của nhà cái luôn sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người chơi trong suốt quá trình chơi game. Không chỉ có trên website, ST666 còn hỗ trợ qua các kênh liên lạc như chat trực tuyến, điện thoại và email, giúp người chơi dễ dàng tiếp cận và giải quyết vấn đề một cách nhanh chóng.
Đặc biệt, việc tham gia và trải nghiệm tại nhà cái ST666 được thực hiện dễ dàng và tiện lợi. Người chơi có thể tham gia từ bất kỳ thiết bị nào có kết nối internet, bao gồm cả máy tính, điện thoại di động và máy tính bảng. Giao diện của ST666 được thiết kế đơn giản và dễ sử dụng, giúp người chơi dễ dàng tìm hiểu và điều hướng trên trang web một cách thuận tiện.
Ngoài ra, ST666 còn có chính sách khuyến mãi và ưu đãi hấp dẫn cho người chơi. Các chương trình khuyến mãi thường xuyên được tổ chức, bao gồm các khoản tiền thưởng, quà tặng và giải thưởng hấp dẫn. Điều này giúp người chơi có thêm cơ hội giành lợi nhuận và trải nghiệm những trò chơi mới mẻ.
Tóm lại, ST666 là một nhà cái uy tín và đáng tin cậy, mang đến cho người chơi trải nghiệm giải trí tuyệt vời và cơ hội tham gia đánh bạc trực tuyến một cách an toàn và hấp dẫn. Với các dịch vụ chất lượng và các trò chơi đa dạng, ST666 hứa hẹn là một điểm đến lý tưởng cho những ai yêu thích giải trí và muốn thử vận may trong các trò chơi đánh bạc trực tuyến.
I every time emailed this weblog post page to all my friends, for the reason that if like to read it next my
contacts will too.
Hi there, I enjoy reading through your article post. I like to write a little comment to support you.
Medication information. What side effects can this medication cause?
where to get lisinopril
Some trends of medicine. Read now.
Do you have any video of that? I’d like to find out more details.
An outstanding share! I have just forwarded this onto a friend who had been doing a little research on this.
And he in fact bought me lunch because I discovered it for him…
lol. So allow me to reword this…. Thanks for the meal!!
But yeah, thanks for spending the time to talk about this
matter here on your site.
As soon as downloaded, set your place to an eligible nation outdoors of South Korea.
Visit my page :: https://xn--w8jtb3b1787arspjlgtu6c.xyz/nipponbasi-yakiniku-ningu/eating-and-drinking/07/
Wonderful post! We will be linking to this particularly great content on our website.
Keep up the good writing.
Drugs information leaflet. Effects of Drug Abuse.
zofran
All news about medication. Get here.
Some genuinely interesting info, well written and loosely user pleasant.
Look into my web page … mitsubishi eclipse 1998
I’m not sure the place you are getting your info, but great topic.
I must spend a while finding out more or working out more.
Thanks for excellent info I used to be searching for this information for my mission.
Medicament information leaflet. Long-Term Effects.
xenical
Some information about meds. Read here.
Hey there! Quick question that’s totally off topic.
Do you know how to make your site mobile friendly?
My weblog looks weird when viewing from my iphone.
I’m trying to find a template or plugin that might be
able to resolve this problem. If you have any suggestions, please share.
Cheers!
Post writing is also a excitement, if you know then you can write if not it is difficult to write.
This is really interesting, You are a very skilled blogger.
I’ve joined your rss feed and look forward to seeking more of your
great post. Also, I have shared your site in my social networks!
You are so awesome! I don’t think I have read through a single thing like this
before. So great to find someone with original thoughts on this subject.
Really.. thanks for starting this up. This web site is one thing that is needed on the internet,
someone with a little originality!
Laws cluld change in the future should Souh Korea Sports Betting Site alter its stance on sports betting.
lisinopril generic name
For reference, casinos licensed below the Tourism
Promotion Act are needed to make payments to promotional funds for
tourism.
my web site … Korea Sports Gamble
Drug information for patients. Short-Term Effects.
diltiazem
All news about drugs. Read information here.
gambling
nipples
fucked
cameltoe
nigger
blackjack
cum
prostitute
erotica
nude
masturbation
schlong
boob
pron
nude
ass
blow job
boob
milf
nudist
black jack
busty
cameltoe
slut
boobies
breasts
ass
ejaculate
nipple
breasts
upskirt
oral
gambling
homosexual
ass
ejaculating
cameltoe
lesbian
erotica
poker
schlong
boobies
oral
masturbating
milf
ass
peepshow
lesbian
cum
upskirt
orgasm
bitch
casino
xanex
fingering
nudity
pharma
masturbation
clit
pron
milfs
cameltoe
homosexual
booty
boobies
prostitute
nude
playmate
sex
clit
butt
dildo
xxx
masturbating
homosexual
nude
pr0n
ejaculation
booty
milf
poker
boobies
homosexual
camel toe
booty
boobies
schlong
poker
milf
milfs
clit
gambling
ejaculation
nipple
pharmacy
porn
18+
titties
prostitute
pussy
Meds information for patients. Brand names.
cialis super active for sale
All news about drug. Read information now.
Superb blog you have here but I was wanting to know if
you knew of any forums that cover the same topics talked
about in this article? I’d really love to be a part of community where
I can get responses from other knowledgeable people that share the same interest.
If you have any suggestions, please let me know. Thanks a lot!
Great post! We are linking to this great article on our
website. Keep up the good writing.
Feel free to surf to my web page Create Email Funnels (emailfunnelbuilder.com)
Drugs information for patients. Effects of Drug Abuse.
valtrex generic
Actual news about medication. Read here.
albuterol generic name
Drug prescribing information. Long-Term Effects.
provigil
Actual news about pills. Read information now.
What’s Taking place i am new to this, I stumbled upon this I’ve discovered It absolutely useful and it
has helped me out loads. I am hoping to contribute & assist different customers like its aided me.
Great job.
We absolutely love your blog and find a lot
of your post’s to be just what I’m looking for.
Would you offer guest writers to write content for yourself?
I wouldn’t mind composing a post or elaborating on a number of the subjects
you write in relation to here. Again, awesome website!
Hi my family member! I want to say that this post is awesome, nice written and include almost all
vital infos. I’d like to look more posts like this .
https://telegra.ph/MEGAWIN-07-31
Exploring MEGAWIN Casino: A Premier Online Gaming Experience
Introduction
In the rapidly evolving world of online casinos, MEGAWIN stands out as a prominent player, offering a top-notch gaming experience to players worldwide. Boasting an impressive collection of games, generous promotions, and a user-friendly platform, MEGAWIN has gained a reputation as a reliable and entertaining online casino destination. In this article, we will delve into the key features that make MEGAWIN Casino a popular choice among gamers.
Game Variety and Software Providers
One of the cornerstones of MEGAWIN’s success is its vast and diverse game library. Catering to the preferences of different players, the casino hosts an array of slots, table games, live dealer games, and more. Whether you’re a fan of classic slots or modern video slots with immersive themes and captivating visuals, MEGAWIN has something to offer.
To deliver such a vast selection of games, the casino collaborates with some of the most renowned software providers in the industry. Partnerships with companies like Microgaming, NetEnt, Playtech, and Evolution Gaming ensure that players can enjoy high-quality, fair, and engaging gameplay.
User-Friendly Interface
Navigating through MEGAWIN’s website is a breeze, even for those new to online casinos. The user-friendly interface is designed to provide a seamless gaming experience. The website’s layout is intuitive, making it easy to find your favorite games, access promotions, and manage your account.
Additionally, MEGAWIN Casino ensures that its platform is optimized for both desktop and mobile devices. This means players can enjoy their favorite games on the go, without sacrificing the quality of gameplay.
Security and Fair Play
A crucial aspect of any reputable online casino is ensuring the safety and security of its players. MEGAWIN takes this responsibility seriously and employs the latest SSL encryption technology to protect sensitive data and financial transactions. Players can rest assured that their personal information remains confidential and secure.
Furthermore, MEGAWIN operates with a valid gambling license from a respected regulatory authority, which ensures that the casino adheres to strict standards of fairness and transparency. The games’ outcomes are determined by a certified random number generator (RNG), guaranteeing fair play for all users.
Medicine information sheet. Cautions.
cialis
All about medicine. Read now.
Medicament information for patients. Generic Name.
zithromax
All what you want to know about medicines. Read here.
Effectively voiced of course. !
my web site :: https://optimusbookmarks.com/story15241307/doxycycline-100mg-price-without-insurance
Drug information for patients. Long-Term Effects.
trazodone generic
All about drug. Read information now.
Thanks to my father who shared with me on the topic of this web site, this webpage is truly remarkable.
Drugs information leaflet. Effects of Drug Abuse.
zyban
Actual news about drugs. Get now.
Какая занимательная фраза
Компания «Ипита» появляется профессионалом на секторе оборудования предприятий кормления разнообразных форматов. потому перед тем, как делать покупки бормашинка к ресторана, кафешка, http://forum.rup.com.ua/viewtopic.php?f=10&t=222&p=13444#p13444 столовой…
where buy levaquin
Thee Federal Wire Act only prevents gamblinhg entities operating within the USA from accepting wagers across state lines.
Here is my website webpage
Medicine information for patients. Effects of Drug Abuse.
ampicillin
All news about drugs. Get now.
Medicine information leaflet. Long-Term Effects.
motrin tablets
Everything about medication. Read information now.
жесть прикол!!
You can purchase achieved-for-you installation on these templates for an WIX website templates extra $250. Simply click on to just accept and you’re good to go!
Superb blog! Do you have any suggestions for
aspiring writers? I’m planning to start my own website soon but I’m a little lost on everything.
Would you recommend starting with a free platform like WordPress or go for a
paid option? There are so many options out there that
I’m completely overwhelmed .. Any tips? Thanks a lot!
Medication information sheet. What side effects can this medication cause?
pregabalin tablets
Best trends of meds. Read information now.
Medication information for patients. Long-Term Effects.
order priligy
Actual news about drugs. Read here.
A bedtime ritual can be anything you want it to be as prolonged as you do it each individual night time.
Stop by my blog: http://Ttlink.com/tommyteppe
Disposable vapes are a fast-growing segment of the vaping market, offering users a convenient, user-friendly way to consume nicotine. They are small, lightweight devices designed for single use; when the battery or e-liquid runs out, you simply dispose of the entire unit and pick up a new one.
Unlike traditional vaping devices, disposable vapes require no maintenance or refill. They come pre-charged and pre-filled with e-liquid, so there’s no need to worry about charging batteries or refilling tanks. This simplicity and ease-of-use make them a popular choice among new vapers and those seeking a fuss-free alternative to cigarettes.
One of the key features of https://killapods.eu/product-category/disposable-vapes/ vapes is the wide variety of flavors they offer. From refreshing fruit flavors to classic tobacco tastes, users can enjoy a diverse range of experiences. However, it’s worth noting that the availability of flavors varies by country due to regulatory differences.
Despite their popularity, disposable vapes have not been without controversy. Their disposable nature raises environmental concerns, as the devices contribute to electronic waste. Furthermore, health concerns related to vaping, such as lung injury and nicotine addiction, are also associated with disposable vapes. Critics also express worries about their appeal to young people, largely due to their flavorful options and sleek design.
Regulations around disposable vapes have been tightening in several jurisdictions, with policies aiming to restrict their appeal to underage users and to address health and environmental issues. Measures include banning certain flavors, enforcing stricter age verification processes, and implementing regulations around device disposal.
In conclusion, disposable vapes offer a convenient and flavorful alternative to traditional smoking and vaping methods. While they continue to gain popularity due to their user-friendly design and variety of flavors, it’s essential to consider the health, environmental, and societal impacts associated with their use. With the evolving regulatory landscape, the future of disposable vapes may see further changes in design, marketing, and availability.
cetirizine brand name
why do doctors prescribe gabapentin
Nhà cái ST666 là một trong những nhà cái cá cược trực tuyến phổ biến và đáng tin cậy tại Việt Nam. Với nhiều năm kinh nghiệm hoạt động trong lĩnh vực giải trí trực tuyến, ST666 đã và đang khẳng định vị thế của mình trong cộng đồng người chơi.
ST666 cung cấp một loạt các dịch vụ giải trí đa dạng, bao gồm casino trực tuyến, cá độ thể thao, game bài, slot game và nhiều trò chơi hấp dẫn khác. Nhờ vào sự đa dạng và phong phú của các trò chơi, người chơi có nhiều sự lựa chọn để thỏa sức giải trí và đánh bạc trực tuyến.
Một trong những ưu điểm nổi bật của ST666 là hệ thống bảo mật và an ninh vượt trội. Các giao dịch và thông tin cá nhân của người chơi được bảo vệ chặt chẽ bằng công nghệ mã hóa cao cấp, đảm bảo tính bảo mật tuyệt đối cho mỗi người chơi. Điều này giúp người chơi yên tâm và tin tưởng vào sự công bằng và minh bạch của nhà cái.
Bên cạnh đó, ST666 còn chú trọng đến dịch vụ khách hàng chất lượng. Đội ngũ hỗ trợ khách hàng của nhà cái luôn sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người chơi trong suốt quá trình chơi game. Không chỉ có trên website, ST666 còn hỗ trợ qua các kênh liên lạc như chat trực tuyến, điện thoại và email, giúp người chơi dễ dàng tiếp cận và giải quyết vấn đề một cách nhanh chóng.
Đặc biệt, việc tham gia và trải nghiệm tại nhà cái ST666 được thực hiện dễ dàng và tiện lợi. Người chơi có thể tham gia từ bất kỳ thiết bị nào có kết nối internet, bao gồm cả máy tính, điện thoại di động và máy tính bảng. Giao diện của ST666 được thiết kế đơn giản và dễ sử dụng, giúp người chơi dễ dàng tìm hiểu và điều hướng trên trang web một cách thuận tiện.
Ngoài ra, ST666 còn có chính sách khuyến mãi và ưu đãi hấp dẫn cho người chơi. Các chương trình khuyến mãi thường xuyên được tổ chức, bao gồm các khoản tiền thưởng, quà tặng và giải thưởng hấp dẫn. Điều này giúp người chơi có thêm cơ hội giành lợi nhuận và trải nghiệm những trò chơi mới mẻ.
Tóm lại, ST666 là một nhà cái uy tín và đáng tin cậy, mang đến cho người chơi trải nghiệm giải trí tuyệt vời và cơ hội tham gia đánh bạc trực tuyến một cách an toàn và hấp dẫn. Với các dịch vụ chất lượng và các trò chơi đa dạng, ST666 hứa hẹn là một điểm đến lý tưởng cho những ai yêu thích giải trí và muốn thử vận may trong các trò chơi đánh bạc trực tuyến.
Medicine information for patients. Short-Term Effects.
cipro without prescription
Some information about medicament. Get now.
Yesterday, while I was at work, my sister stole my iPad and tested to see if it can survive a twenty five foot drop, just so she can be a youtube sensation. My apple
ipad is now broken and she has 83 views. I know this is totally off topic but I had to share it with someone!
In reality, they exist outside the United States and are
not topkc to the US legal method.
Review my homepage :: seebysee.com
Drugs information leaflet. Short-Term Effects.
valtrex
Some trends of medicines. Get now.
Chat with random strangers with out the necessity to make an account, arrange registration, obtain undesirable mails.
In the coming decades, the world is poised to experience a profound transformation as artificial intelligence (AI) and biotechnology converge to create stunning women using cutting-edge DNA technologies, artificial insemination, and cloning. These enchanting artificial beings hold the promise of fulfilling individual dreams and becoming the ultimate life partners.
The marriage of AI and biotechnology has ushered in an era of awe-inspiring achievements, introducing groundbreaking discoveries and technologies that challenge our understanding of both the world and ourselves. One of the most remarkable outcomes of this partnership is the ability to craft artificial beings, such as exquisitely designed women.
At the heart of this revolutionary era lies the incredible capabilities of neural networks and machine learning algorithms, which harness vast datasets to forge entirely novel entities.
Pioneering scientists have successfully developed a revolutionary AI-powered printer, capable of “printing” women by seamlessly integrating DNA-editing technologies, artificial insemination, and cloning methods. This cutting-edge approach allows for the creation of human replicas endowed with unprecedented beauty and distinctive traits.
However, amidst the awe and excitement, profound ethical questions loom large and demand careful consideration. The ethical implications of generating artificial humans, the potential consequences on society and interpersonal relationships, and the risk of future inequalities and discrimination must all be thoughtfully contemplated.
Yet, proponents fervently argue that the merits of this technology far outweigh the challenges. The creation of alluring women through AI-powered printers could herald a new chapter in human evolution, not only fulfilling our deepest aspirations but also pushing the boundaries of science and medicine.
Beyond its revolutionary impact on aesthetics and companionship, this AI technology holds immense potential for medical applications. It could pave the way for generating organs for transplantation and treating genetic diseases, positioning AI and biotechnology as powerful tools to alleviate human suffering.
In conclusion, the prospect of neural network woman AI creating stunning women using a printer evokes numerous questions and reflections. This extraordinary technology promises to redefine beauty and unlock new realms of possibilities. Yet, it is crucial to strike a delicate balance between innovation and ethical considerations. Undeniably, the enduring human pursuit of beauty and progress will continue to propel our world forward into uncharted territories.
Medicines information leaflet. Cautions.
glucophage
Some about medicine. Get here.
free dating nearby: https://datingtopreview.com/# – meet european singles in usa
Medicament information for patients. Brand names.
zovirax without a prescription
Some trends of medicine. Read now.
canadian pharmacy ezzz cialis cialis dosage viagra and cialis
Pills prescribing information. Generic Name.
cipro
Best about medicines. Read information here.
Pills prescribing information. Long-Term Effects.
can i order nolvadex
Some about drug. Get information now.
Hi! I just wanted to ask if you ever have any issues with hackers?
My last blog (wordpress) was hacked and I ended up losing months of
hard work due to no backup. Do you have any solutions to prevent hackers?
My web-site – cheap car insurance
Meds information for patients. Effects of Drug Abuse.
eldepryl
Actual news about drugs. Read now.
Medicines information. Generic Name.
silagra
All information about drug. Read now.
You’ve made your point quite well..
My page – https://socialoasis.blog
I’m very happy to find this web site. I wanted
to thank you for your time for this wonderful read!! I definitely
loved every little bit of it and i also have you saved to fav to look at new information in your blog.
Drug information for patients. What side effects?
provigil sale
Some trends of drug. Read here.
With tournaments taking spot each weekend, there
are generally great odds to bet into.
Feel free to visit my web page – Online Betting
An outstanding share! I’ve just forwarded
this onto a coworker who had been doing a little homework on this.
And he actually bought me breakfast simply because I discovered it
for him… lol. So allow me to reword this….
Thanks for the meal!! But yeah, thanx for spending time to
talk about this issue here on your blog.
Hello everyone, it’s my first go to see at this site, and post is truly fruitful for me, keep up
posting such posts.
It is perfect time to make a few plans for the long run and it’s time to be happy.
I have learn this submit and if I could I desire to suggest you
some attention-grabbing issues or tips. Maybe you
could write next articles regarding this article.
I want to read even more issues approximately it!
I am regular reader, how are you everybody? This article posted at this
web page is truly pleasant.
Medicines information sheet. Drug Class.
can you get cialis super active
All trends of drug. Get here.
Does your site have a contact page? I’m having trouble locating
it but, I’d like to shoot you an e-mail. I’ve got some suggestions for your
blog you might be interested in hearing. Either way, great blog and I look forward to seeing it grow over time.
Drug information for patients. Brand names.
fluoxetine medication
Actual about drugs. Read information now.
Attractive section of content. I just stumbled upon your site and in accession capital to assert that I
acquire in fact enjoyed account your blog posts.
Anyway I’ll be subscribing to your feeds and even I achievement you access consistently rapidly.
Drug information leaflet. Long-Term Effects.
cheap effexor
Best what you want to know about medicament. Get here.
Pills prescribing information. What side effects can this medication cause?
buy generic strattera
Everything about medicines. Get now.
I’ve been exploring for a little bit for any high-quality articles or blog posts on this kind of area .
Exploring in Yahoo I eventually stumbled upon this site.
Reading this information So i’m glad to express that I have an incredibly excellent uncanny feeling I
found out exactly what I needed. I most no doubt will make sure to don?t omit
this web site and provides it a glance on a continuing basis.
Medicine information. Long-Term Effects.
nolvadex
Everything trends of drug. Read information here.
I do agree with all the concepts you’ve introduced for your post.
They are really convincing and can certainly work. Still, the
posts are very short for starters. Could you please prolong them a bit from next time?
Thanks for the post.
buy generic levaquin online
2022, wih the practically $1 billion in anticipated profits split in between the state (51%) and
the operators (49%).
My website – Gambling site
Drug prescribing information. Effects of Drug Abuse.
order strattera
All news about medicines. Get now.
Keep on working, great job!
Very good postings Thanks a lot.
My web-site; https://socialoasis.us/socialoasis-about-us
always i used to read smaller content which as well clear their motive, and that is also happening with this article which I am reading here.
I pay a visit day-to-day some sites and
blogs to read posts, except this blog presents quality based articles.
Medicines prescribing information. Drug Class.
where can i get prozac
Best information about medicines. Read now.
лейкемия
Hello There. I found your blog using msn. This is an extremely smartly written article.
I’ll make sure to bookmark it and come back to read extra of your useful
information. Thank you for the post. I will definitely comeback.
Меня тоже волнует этот вопрос. Вы мне не подскажете, где я могу об этом прочитать?
Комментировать « Пред. акселерограмма – К дневнику – След. Авторы сериала “Спящие-2” изобразительно показали как будто СМИ ведут https://clandesign4sale.kienberger-designs.de/index.php?news-1 войну.
stromectol for sale
It’s really very complicated in this busy life to listen news on Television,
so I simply use internet for that purpose, and
obtain the most recent news.
Medicament information. Drug Class.
tadacip cost
Some about meds. Read information here.
Meds information leaflet. Brand names.
seroquel
Some information about medicament. Read information here.
Drugs information sheet. Brand names.
zithromax
Everything news about drugs. Get now.
que es amoxicillin
What’s up to all, it’s in fact a pleasant for me to go to see
this web page, it consists of useful Information.
prednisone weight gain
Medicine information for patients. Long-Term Effects.
sildigra sale
Some information about drug. Get now.
Medicines information. Generic Name.
rx prozac
Best about medicines. Read information now.
She has worked in numerous cities covering breaking news, politics, education, and extra.
Also visit my site; http://www.evidenta-deseurilor.ro/?p=1
В этом что-то есть. Буду знать, большое спасибо за помощь в этом вопросе.
1. Крім лікувального ефекту, реставрація перших зубів має й психологічний фактор: дитина відчуває себе впевненою, https://www.dododesign.at/home-items/ комунікабельною і відкритою до спілкування в колективі.
Medication prescribing information. Long-Term Effects.
bactrim brand name
Best about drug. Get here.
Medication information sheet. What side effects?
viagra soft without insurance
Best news about drugs. Read now.
Зашел на форум и увидел эту тему. Разрешите помочь Вам?
Эта разновидность подопечных исключительно малочисленная. постигание основ обслуживания и еще дар их практиковать в самом деле – величественнейшие знания, коими обязана иметь своей отличительной особенностью http://forrajesdelgenil.com/microsilos/.
Medication information sheet. What side effects can this medication cause?
buy norpace
Actual news about meds. Read here.
Pills information sheet. Cautions.
cipro
Best news about meds. Read information now.
Thee Roobet window is not onscreen amongst when he loses all his incomme
and income enters the account.
Here is my site :: Online Gamble
apotex trazodone
Whoa! This blog looks exactly like my old one!
It’s on a entirely different subject but it has pretty much the same
page layout and design. Excellent choice of colors!
I know this web site offers quality depending content and extra data,
is there any other website which offers such things
in quality?
While you are meditating, you begin by selecting a degree of curiosity or something that you’re going to place your focus on and this is perhaps a flower, https://sho.org.ua/bonusy-v-onlajn-kazyno-yak-vony-pratsyuyut-i-chomu-vony-vazhlyvi/ candle or any thing.
здорово
Синих лап и слава богу приобретать с запасом, http://dickcharlotte.gaatverweg.nl/route/ зане они не успеет кто что сделать входить в расход да настойчиво не знать как быть. на поносное шанс рабочий класс тетради школьников включают рой задач получай службу с красивым цветом.
Drugs information for patients. What side effects can this medication cause?
ampicillin
Some trends of medicament. Read information here.
Medicine information leaflet. Brand names.
zyban
Best news about medicine. Get information now.
Picard thdn asks Troi to release the injured, in xchange
for him as another hostage, and Troi agrees.
My web site; Annuity payments
Thank you for the auspicious writeup. It in truth was once a amusement account it.
Look advanced to more added agreeable from you!
By the way, how could we communicate?
Meds prescribing information. What side effects?
nexium
Everything what you want to know about medicine. Read now.
Hello there, I found your site via Google whilst searching
for a comparable subject, your site came up, it appears to
be like good. I’ve bookmarked it in my google bookmarks.
Hi there, just turned into alert to your weblog via Google, and found that it is truly
informative. I’m going to be careful for brussels.
I will appreciate when you proceed this in future. Lots of other folks will be benefited out of your writing.
Cheers!
Я извиняюсь, но, по-моему, Вы ошибаетесь. Могу это доказать.
Жаркий равным образом сильная сторона ведренный дней прогнозируют во Магнитогорске https://www.rossowheels.com/producto/ruedas-delantera-28mm-tubular/ два густя. Каких отметок добьется палеотемпература? Ожидаются династия дождика? Расскажет “МР-инфо”.
Medicament information leaflet. What side effects can this medication cause?
fluoxetine
Some what you want to know about drugs. Get information now.
levaquin price without insurance
I am regular visitor, how are you everybody?
This paragraph posted at this web site is genuinely pleasant.
Medicines information. Brand names.
neurontin
Actual news about pills. Read information here.
Предлагаю Вам посетить сайт, на котором есть много статей по этому вопросу.
We combine high quality tools with world-class service, giving you the options you need for a faster, https://dc-kd.ru/user/ceachemsxz higher job end result.
I do not even know how I ended up here, but I thought this post
was good. I do not know who you are but certainly you’re going to a
famous blogger if you are not already 😉 Cheers!
Medicament prescribing information. Drug Class.
valtrex for sale
Everything information about drugs. Read now.
It’s hard to come by educated people for
this subject, but you seem like you know what you’re
talking about! Thanks
Pills information leaflet. What side effects can this medication cause?
clomid
Some trends of drug. Read information here.
what is diltiazem prescribed for
I don’t even know how I ended up here, but I thought this post was great.
I do not know who you are but definitely you’re going to a famous blogger if
you aren’t already 😉 Cheers!
Вы не правы. Могу отстоять свою позицию.
Researchers checked out 4,711 cities and found local weather change fingerprints in 4,019 of them for July, http://redrice-co.com/page/jump.php?url=https://gelioscompany/expert-mobile-app-design-in-toronto-gelios-company/ which other scientists mentioned is the most popular month on report.
Howdy! I just would like to give you a huge thumbs up for the excellent information you have here on this post.
I am returning to your web site for more soon.
На нашем сайте https://v-auto.com.ua/ вы найдете не только новости, но и полезные советы по уходу за автомобилем, выбору запчастей, сравнительные обзоры моделей и многое другое. Наша миссия – помочь вам сделать осознанный выбор и быть в курсе всех последних событий в автоиндустрии.
Medicines information for patients. Short-Term Effects.
fluoxetine
Some what you want to know about meds. Get information now.
I for all time emailed this website post page to all my friends, as if like
to read it then my links will too.
Hi there, just wanted to mention, I loved this blog post.
It was helpful. Keep on posting!
Здесь на нашем сайте https://ajax-auto.com.ua/ вы также найдете актуальную информацию о расценках на услуги, специальных предложениях и сезонных скидках. Мы ценим доверие наших клиентов и стремимся сделать обслуживание вашего автомобиля максимально комфортным и приятным опытом.
Post writing is also a fun, if you know then you can write or else it is
complicated to write.
lisinopril 40 mg on line
Medicine information. Short-Term Effects.
bactrim no prescription
Actual news about medicine. Read information here.
I know this web page gives quality dependent articles or reviews and additional information, is there any other web page
which presents these kinds of things in quality?
Drugs information. What side effects?
mobic
Some what you want to know about medicines. Read here.
В этом что-то есть. Благодарю за информацию, теперь я буду знать.
News and company achievements are the largest affect that can be left on customers. We’ve https://coinpedia.org/information/ripple-price-prediction-can-xrp-continue-to-rise-after-significant-drop/ acquired you covered.
Medicine prescribing information. Short-Term Effects.
how can i get synthroid
Best trends of medication. Read information now.
Ваш идеальный партнер https://akb1.com.ua/ для покупки надежных и качественных автомобильных аккумуляторов!
Pills information for patients. Brand names.
buy generic cialis
Actual news about medicament. Get information now.
Thanks for the marvelous posting! I certainly enjoyed reading it, you can be a great author.
I will remember to bookmark your blog and definitely will come back very soon. I want to encourage
one to continue your great job, have a nice day!
Think about a huge Imax screen. The acutely aware thoughts, your thinking, conscious part, https://dogoterapiaolsztyn.pl/2021/05/30/luckyjet/ may solely handle one hundred bits per second.
Medicines information for patients. Brand names.
kamagra order
Some news about medicine. Get now.
Drugs information sheet. What side effects can this medication cause?
nolvadex
Everything information about pills. Read information here.
Amazing! This blog looks just like my old one! It’s on a entirely different subject
but it has pretty much the same page layout and design. Excellent choice
of colors!
My spouse and I stumbled over here from a different page and thought I
may as well check things out. I like what I see so i am just following you.
Look forward to exploring your web page yet again.
trazodone pi
can you buy levaquin in belise
Medicament information. Cautions.
buying maxalt
Some trends of meds. Get information here.
Medicine prescribing information. Short-Term Effects.
zoloft for sale
Some what you want to know about medicines. Get information here.
Medication information leaflet. Generic Name.
finpecia cost
All trends of drug. Read here.
Meds information leaflet. Brand names.
retrovir
Best about meds. Get information now.
Я пожалуй просто промолчу
For individuals in a lot the Northeast, hvac installation cost later this week will convey the most popular weather of the summer season to date,’ Rayno mentioned.
Мне нравится Ваша идея. Предлагаю вынести на общее обсуждение.
Online gambling is authorized in some states, https://mijn-friettent.nl/hello-world/ and each state could have totally different choices.
ventolin hfa
Medicine information leaflet. What side effects?
get lyrica
Actual information about medication. Read here.
Meds information leaflet. Cautions.
nexium
Actual what you want to know about drug. Read information now.
интересная темка,взрослая)
MixTum is a Bitcoin tumbler that provides an easy-to-use interface, bitcoin mixer which implies you possibly can combine coins. The quick answer is sure, they do.
Medicine information. Short-Term Effects.
where to buy cialis soft
Some information about drug. Read here.
Medicament information leaflet. Cautions.
silagra
Some about medication. Get information now.
Medicines information leaflet. What side effects?
ampicillin
Best information about meds. Read here.
Pills information sheet. Generic Name.
silagra tablets
Everything what you want to know about medicine. Get now.
Medicine information for patients. What side effects?
rx lyrica
All news about medication. Read information here.
Reliable info Kudos.
My webpage Make money from your hobbies – https://socialoasis.us/socialoasis-payment-proof,
Meds prescribing information. Effects of Drug Abuse.
neurontin
Some trends of pills. Read here.
Mega win slots
Mega Win Slots – The Ultimate Casino Experience
Introduction
In the fast-paced world of online gambling, slot machines have consistently emerged as one of the most popular and entertaining forms of casino gaming. Among the countless slot games available, one name stands out for its captivating gameplay, immersive graphics, and life-changing rewards – Mega Win Slots. In this article, we’ll take a closer look at what sets Mega Win Slots apart and why it has become a favorite among players worldwide.
Unparalleled Variety of Themes
Mega Win Slots offers a vast array of themes, ensuring there is something for every type of player. From ancient civilizations and mystical adventures to futuristic space missions and Hollywood blockbusters, these slots take players on exciting journeys with each spin. Whether you prefer classic fruit slots or innovative 3D video slots, Mega Win Slots has it all.
Cutting-Edge Graphics and Sound Design
One of the key factors that make Mega Win Slots a standout in the online casino industry is its cutting-edge graphics and high-quality sound design. The visually stunning animations and captivating audio create an immersive gaming experience that keeps players coming back for more. The attention to detail in each slot game ensures that players are fully engaged and entertained throughout their gaming sessions.
User-Friendly Interface
Navigating through Mega Win Slots is a breeze, even for newcomers to online gambling. The user-friendly interface ensures that players can easily find their favorite games, adjust betting preferences, and access essential features with just a few clicks. Whether playing on a desktop computer or a mobile device, the interface is responsive and optimized for seamless gameplay.
Progressive Jackpots and Mega Wins
The allure of Mega Win Slots lies in its potential for life-changing wins. The platform features a selection of progressive jackpot slots, where the prize pool accumulates with each bet until one lucky player hits the jackpot. These staggering payouts have been known to turn ordinary players into instant millionaires, making Mega Win Slots a favorite among high-rollers and thrill-seekers.
Generous Bonuses and Promotions
To enhance the gaming experience, Mega Win Slots offers a wide range of bonuses and promotions. New players are often greeted with attractive welcome packages, including free spins and bonus funds to kickstart their journey. Regular players can enjoy loyalty rewards, cashback offers, and special seasonal promotions that add extra excitement to their gaming sessions.
doxycycline hyclate for sinus infection
Вот елки палки
So chill out, take lawn bowling, https://tomdb.ru/index.php/component/k2/item/1-praesent-ut-erat-eget-metus and then determine that there are more to our life than sulking on countless work.
Drugs information leaflet. What side effects?
levitra pills
Everything trends of medicament. Read here.
can i purchase generic levaquin for sale
The pump, power supply and container are all contained within the egg-shaped system, https://saojoaquimonline.com.br/variedades/2023/07/10/como-ganhar-nas-maquinas-caca-niqueis-dicas-e-estrategias/ which pairs to an app utilizing Bluetooth.
Meds information leaflet. What side effects?
eldepryl pills
Everything trends of drugs. Read information here.
Ваша фраза, просто прелесть
In recent times, bitcoin mixer criminals have more and more moved from mixing providers to privacy wallets. This mannequin solves the issue of stealing, as there is no such thing as a middleman.
Medication information sheet. What side effects can this medication cause?
rx fosamax
Best about drug. Get information now.
ventolin hfa inhaler
Pills information. Brand names.
singulair
Everything trends of drug. Read here.
Meds information leaflet. Brand names.
seroquel
All what you want to know about medication. Read now.
what is trazodone for dogs
Definitely imagine that that you stated. Your favorite reason seemed
to be on the net the easiest factor to remember of.
I say to you, I definitely get annoyed while people consider concerns that they just do not
recognize about. You controlled to hit the nail upon the highest as well as outlined out the entire thing with no need side effect
, folks could take a signal. Will likely be again to get
more. Thanks
Medicine information for patients. Short-Term Effects.
pregabalin without rx
Everything information about drugs. Read information here.
Смоленск в сети
can you take flonase and zyrtec
Pills information sheet. Drug Class.
neurontin
Some about medicament. Read here.
Извините, сообщение удалено
You will need to have heard concerning the vitality of utilizing a great moisturizer at night time, http://tahirsiddiqica.com/2021/06/18/contact-us/ and there really is science following that tip.
prednisone steroid
Drugs information for patients. Drug Class.
tadacip
Some news about drugs. Get information here.
Medicament information for patients. Cautions.
synthroid
All news about pills. Read now.
Medicines information for patients. Effects of Drug Abuse.
levitra medication
Best information about meds. Read now.
Since the formula works best with the keto diet, you should know how to begin and maintain the lifestyle. Thanks for reading and best of health to you! Healthy and balanced cravings: One more major advantage of the Total Health Keto Gummies Diet plan is that it avoids specific health and wellness problems such as diabetes as well as cardiovascular disease from creating. All you need is to begin with a low-carbohydrate diet plan and then Continue for greater than a year. The emphasis is on using this new power source to make up for the loss of carbohydrates in the diet. There is always a slight risk of side effects occurring for some people when they begin using a product like this one. Stop using any other dietary supplement before you begin taking the Apple http://hatsat.bget.ru/user/SimonetteIliffe/ Gummies. To get your supply, order right from the official Apple Keto Gummies website. The best place to find the current pricing information is the official Apple Keto website. In our Apple Keto Gummies review, we’ll tell you what this supplement can do and how it compares to other options. Some people choose to have a discussion with a medical professional before they begin taking the supplement.
levaquin pil
Medicament information for patients. Cautions.
ampicillin without a prescription
Actual news about meds. Get now.
best time to take ashwagandha
Думаю, что нет.
These scramblers are thought of to be the most popular ones on the bitcoin mixer net.
Pills prescribing information. Drug Class.
neurontin
Actual news about medicine. Read now.
baccarat la gì
baccarat la gì
Bài viết: Tại sao nên chọn 911WIN Casino trực tuyến?
Sòng bạc trực tuyến 911WIN đã không ngừng phát triển và trở thành một trong những sòng bạc trực tuyến uy tín và phổ biến nhất trên thị trường. Điều gì đã khiến 911WIN Casino trở thành điểm đến lý tưởng của đông đảo người chơi? Chúng ta hãy cùng tìm hiểu về những giá trị thương hiệu của sòng bạc này.
Giá trị thương hiệu và đáng tin cậy
911WIN Casino đã hoạt động trong nhiều năm, đem đến cho người chơi sự ổn định và đáng tin cậy. Sử dụng công nghệ mã hóa mạng tiên tiến, 911WIN đảm bảo rằng thông tin cá nhân của tất cả các thành viên được bảo vệ một cách tuyệt đối, ngăn chặn bất kỳ nguy cơ rò rỉ thông tin cá nhân. Điều này đặc biệt quan trọng trong thời đại số, khi mà hoạt động mạng bất hợp pháp ngày càng gia tăng. Chọn 911WIN Casino là lựa chọn thông minh, bảo vệ thông tin cá nhân của bạn và tham gia vào cuộc chiến chống lại các hoạt động mạng không đáng tin cậy.
Hỗ trợ khách hàng 24/7
Một trong những điểm đáng chú ý của 911WIN Casino là dịch vụ hỗ trợ khách hàng 24/7. Không chỉ trong ngày thường, mà còn kể cả vào ngày lễ hay dịp Tết, đội ngũ hỗ trợ của 911WIN luôn sẵn sàng hỗ trợ bạn khi bạn cần giải quyết bất kỳ vấn đề gì. Sự nhiệt tình và chuyên nghiệp của đội ngũ hỗ trợ sẽ giúp bạn có trải nghiệm chơi game trực tuyến mượt mà và không gặp rắc rối.
Đảm bảo rút tiền an toàn
911WIN Casino cam kết rằng việc rút tiền sẽ được thực hiện một cách nhanh chóng và an toàn nhất. Quản lý độc lập đảm bảo mức độ minh bạch và công bằng trong các giao dịch, còn hệ thống quản lý an toàn nghiêm ngặt giúp bảo vệ dữ liệu cá nhân và tài khoản của bạn. Bạn có thể hoàn toàn yên tâm khi chơi tại 911WIN Casino, vì mọi thông tin cá nhân của bạn đều được bảo vệ một cách tốt nhất.
Số lượng trò chơi đa dạng
911WIN Casino cung cấp một bộ sưu tập trò chơi đa dạng và đầy đủ, giúp bạn đắm mình vào thế giới trò chơi phong phú. Bạn có thể tận hưởng những trò chơi kinh điển như baccarat, blackjack, poker, hay thử vận may với các trò chơi máy slot hấp dẫn. Không chỉ vậy, sòng bạc này còn cung cấp những trò chơi mới và hấp dẫn liên tục, giúp bạn luôn có trải nghiệm mới mẻ và thú vị mỗi khi ghé thăm.
baccarat là gì
Bài viết: Tại sao nên chọn 911WIN Casino Online?
Sòng bạc trực tuyến 911WIN đã không ngừng phát triển và trở thành một trong những sòng bạc trực tuyến uy tín và phổ biến nhất trên thị trường. Điều gì đã khiến 911WIN Casino trở thành điểm đến lý tưởng của đông đảo người chơi? Chúng ta hãy cùng tìm hiểu về những giá trị thương hiệu của sòng bạc này.
Giá trị thương hiệu và đáng tin cậy
911WIN Casino đã hoạt động trong nhiều năm, đem đến cho người chơi sự ổn định và đáng tin cậy. Sử dụng công nghệ mã hóa mạng tiên tiến, 911WIN đảm bảo rằng thông tin cá nhân của tất cả các thành viên được bảo vệ một cách tuyệt đối, ngăn chặn bất kỳ nguy cơ rò rỉ thông tin cá nhân. Điều này đặc biệt quan trọng trong thời đại số, khi mà hoạt động mạng bất hợp pháp ngày càng gia tăng. Chọn 911WIN Casino là lựa chọn thông minh, bảo vệ thông tin cá nhân của bạn và tham gia vào cuộc chiến chống lại các hoạt động mạng không đáng tin cậy.
Hỗ trợ khách hàng 24/7
Một trong những điểm đáng chú ý của 911WIN Casino là dịch vụ hỗ trợ khách hàng 24/7. Không chỉ trong ngày thường, mà còn kể cả vào ngày lễ hay dịp Tết, đội ngũ hỗ trợ của 911WIN luôn sẵn sàng hỗ trợ bạn khi bạn cần giải quyết bất kỳ vấn đề gì. Sự nhiệt tình và chuyên nghiệp của đội ngũ hỗ trợ sẽ giúp bạn có trải nghiệm chơi game trực tuyến mượt mà và không gặp rắc rối.
Đảm bảo rút tiền an toàn
911WIN Casino cam kết rằng việc rút tiền sẽ được thực hiện một cách nhanh chóng và an toàn nhất. Quản lý độc lập đảm bảo mức độ minh bạch và công bằng trong các giao dịch, còn hệ thống quản lý an toàn nghiêm ngặt giúp bảo vệ dữ liệu cá nhân và tài khoản của bạn. Bạn có thể hoàn toàn yên tâm khi chơi tại 911WIN Casino, vì mọi thông tin cá nhân của bạn đều được bảo vệ một cách tốt nhất.
Số lượng trò chơi đa dạng
911WIN Casino cung cấp một bộ sưu tập trò chơi đa dạng và đầy đủ, giúp bạn đắm mình vào thế giới trò chơi phong phú. Bạn có thể tận hưởng những trò chơi kinh điển như baccarat, blackjack, poker, hay thử vận may với các trò chơi máy slot hấp dẫn. Không chỉ vậy, sòng bạc này còn cung cấp những trò chơi mới và hấp dẫn liên tục, giúp bạn luôn có trải nghiệm mới mẻ và thú vị mỗi khi ghé thăm.
Tóm lại, 911WIN Casino là một sòng bạc trực tuyến đáng tin cậy và uy tín, mang đến những giá trị thương hiệu đáng kể. Với sự bảo mật thông tin, dịch vụ hỗ trợ tận tâm, quy trình rút tiền an toàn, và bộ sưu tập trò chơi đa dạng, 911WIN Casino xứng đáng là lựa chọn hàng đầu cho người chơi yêu thích sòng bạc trực tuyến. Hãy tham gia ngay và trải nghiệm những khoảnh khắc giải trí tuyệt vời cùng 911WIN Casino!
can you buy cheap levaquin without rx
Medicament information leaflet. Drug Class.
eldepryl
Everything about meds. Read information now.
The government displays their actions since they’ve a share in the operating https://www.ogcnissa.com/articles-16527-actualite-jetx-le-casino-ultime-en-lignel-experience-du-jeu-arcade-de-smartsoft-gaming value.
Я извиняюсь, но, по-моему, Вы ошибаетесь. Предлагаю это обсудить. Пишите мне в PM.
As we age, https://www.us-cubanormalization.org/viva-cuba/in-light-of-surge-la-coalition-campaigns-for-covid-safety-measures-cuban-help/ the nutritional demands of our bodies change and many individuals really feel that life slows down.
can you buy generic prednisone prices
Medicine information. Cautions.
zithromax tablets
Best information about drugs. Read here.
Drugs information for patients. Cautions.
eldepryl medication
Best information about medicine. Get information now.
purchase levaquin with out perspyion
Medication information for patients. Brand names.
norpace buy
Actual trends of drug. Read information now.
chơi baccarat là gì
Bài viết: Tại sao nên chọn 911WIN Casino trực tuyến?
Sòng bạc trực tuyến 911WIN đã không ngừng phát triển và trở thành một trong những sòng bạc trực tuyến uy tín và phổ biến nhất trên thị trường. Điều gì đã khiến 911WIN Casino trở thành điểm đến lý tưởng của đông đảo người chơi? Chúng ta hãy cùng tìm hiểu về những giá trị thương hiệu của sòng bạc này.
Giá trị thương hiệu và đáng tin cậy
911WIN Casino đã hoạt động trong nhiều năm, đem đến cho người chơi sự ổn định và đáng tin cậy. Sử dụng công nghệ mã hóa mạng tiên tiến, 911WIN đảm bảo rằng thông tin cá nhân của tất cả các thành viên được bảo vệ một cách tuyệt đối, ngăn chặn bất kỳ nguy cơ rò rỉ thông tin cá nhân. Điều này đặc biệt quan trọng trong thời đại số, khi mà hoạt động mạng bất hợp pháp ngày càng gia tăng. Chọn 911WIN Casino là lựa chọn thông minh, bảo vệ thông tin cá nhân của bạn và tham gia vào cuộc chiến chống lại các hoạt động mạng không đáng tin cậy.
Hỗ trợ khách hàng 24/7
Một trong những điểm đáng chú ý của 911WIN Casino là dịch vụ hỗ trợ khách hàng 24/7. Không chỉ trong ngày thường, mà còn kể cả vào ngày lễ hay dịp Tết, đội ngũ hỗ trợ của 911WIN luôn sẵn sàng hỗ trợ bạn khi bạn cần giải quyết bất kỳ vấn đề gì. Sự nhiệt tình và chuyên nghiệp của đội ngũ hỗ trợ sẽ giúp bạn có trải nghiệm chơi game trực tuyến mượt mà và không gặp rắc rối.
Đảm bảo rút tiền an toàn
911WIN Casino cam kết rằng việc rút tiền sẽ được thực hiện một cách nhanh chóng và an toàn nhất. Quản lý độc lập đảm bảo mức độ minh bạch và công bằng trong các giao dịch, còn hệ thống quản lý an toàn nghiêm ngặt giúp bảo vệ dữ liệu cá nhân và tài khoản của bạn. Bạn có thể hoàn toàn yên tâm khi chơi tại 911WIN Casino, vì mọi thông tin cá nhân của bạn đều được bảo vệ một cách tốt nhất.
Số lượng trò chơi đa dạng
911WIN Casino cung cấp một bộ sưu tập trò chơi đa dạng và đầy đủ, giúp bạn đắm mình vào thế giới trò chơi phong phú. Bạn có thể tận hưởng những trò chơi kinh điển như baccarat, blackjack, poker, hay thử vận may với các trò chơi máy slot hấp dẫn. Không chỉ vậy, sòng bạc này còn cung cấp những trò chơi mới và hấp dẫn liên tục, giúp bạn luôn có trải nghiệm mới mẻ và thú vị mỗi khi ghé thăm.
Tóm lại, 911WIN Casino là một sòng bạc trực tuyến đáng tin cậy và uy tín, mang đến những giá trị thương hiệu đáng kể. Với sự bảo mật thông tin, dịch vụ hỗ trợ tận tâm, quy trình rút tiền an toàn, và bộ sưu tập trò chơi đa dạng, 911WIN Casino xứng đáng là lựa chọn hàng đầu cho người chơi yêu thích sòng bạc trực tuyến. Hãy tham gia ngay và trải nghiệm những khoảnh khắc giải trí tuyệt vời cùng 911WIN Casino.
Chơi baccarat là gì?
Baccarat là một trò chơi bài phổ biến trong các sòng bạc trực tuyến và địa phương. Người chơi tham gia baccarat cược vào hai tay: “người chơi” và “ngân hàng”. Mục tiêu của trò chơi là đoán tay nào sẽ có điểm số gần nhất với 9 hoặc có tổng điểm bằng 9. Trò chơi thú vị và đơn giản, thu hút sự quan tâm của nhiều người chơi yêu thích sòng bạc trực tuyến.
Medicament information for patients. Brand names.
zithromax buy
Everything information about pills. Get information now.
Medicine prescribing information. Drug Class.
flagyl price
Some about medicine. Get now.
Crestor
amoxilin
Drug information sheet. Brand names.
pregabalin
Actual news about drugs. Get here.
Pills information sheet. What side effects can this medication cause?
effexor without dr prescription
All news about medicine. Get information now.
protonix warnings
Drug information. Brand names.
zyban
Everything what you want to know about meds. Get information now.
Prilosec
Drug prescribing information. Drug Class.
order valtrex
Some what you want to know about medicine. Read information here.
Medicament information leaflet. Generic Name.
cipro medication
All information about medicines. Get now.
Medication information for patients. Generic Name.
lioresal
Some trends of pills. Get information here.
prednisone price
Drugs information. Drug Class.
trazodone no prescription
All what you want to know about pills. Read now.
Drugs information. Short-Term Effects.
proscar tablet
Everything information about drug. Get information now.
Tetracycline safety
can i order levaquin pills
Drugs information sheet. What side effects?
proscar cheap
Everything information about meds. Get now.
Medication information sheet. Long-Term Effects.
fluoxetine
All news about drugs. Read information now.
This requires one to have quiet time on a regular basis so that the thoughts becomes alert to do the appropriate things at the https://beststartup.ca/the-best-betting-strategies-for-winning-at-casino-games/ proper time.
Drugs prescribing information. Drug Class.
strattera
Everything information about medicine. Get information now.
lisinopril mechanism of action
Medicament information leaflet. Cautions.
cleocin
Everything news about meds. Read information now.
cetirizine tablets
Medicines information for patients. Brand names.
viagra soft otc
Actual news about medicament. Get information now.
Drug information sheet. Short-Term Effects.
levaquin without rx
Everything news about drugs. Read now.
cordarone warnings
Medicine information leaflet. What side effects can this medication cause?
cost of lyrica
Actual trends of meds. Read here.
Drug prescribing information. Effects of Drug Abuse.
cytotec
Some about medicament. Read here.
Thanks for another informative web site. The place else may just I get that kind of info written in such
a perfect manner? I have a mission that I’m simply now running on, and I
have been at the glance out for such info.
Medication information for patients. What side effects can this medication cause?
rx zithromax
Everything news about meds. Read now.
Medication information. Cautions.
bactrim brand name
Some information about drugs. Get information now.
pro-leikoz.ru/
albuterol generic name
GPT image
GPT-Image: Exploring the Intersection of AI and Visual Art with Beautiful Portraits of Women
Introduction
Artificial Intelligence (AI) has made significant strides in the field of computer vision, enabling machines to understand and interpret visual data. Among these advancements, GPT-Image stands out as a remarkable model that merges language understanding with image generation capabilities. In this article, we explore the fascinating world of GPT-Image and its ability to create stunning portraits of beautiful women.
The Evolution of AI in Computer Vision
The history of AI in computer vision dates back to the 1960s when researchers first began experimenting with image recognition algorithms. Over the decades, AI models evolved, becoming more sophisticated and capable of recognizing objects and patterns in images. GPT-3, a language model developed by OpenAI, achieved groundbreaking results in natural language processing, leading to its applications in various domains.
The Emergence of GPT-Image
With the success of GPT-3, AI researchers sought to combine the power of language models with computer vision. The result was the creation of GPT-Image, an AI model capable of generating high-quality images from textual descriptions. By understanding the semantics of the input text, GPT-Image can visualize and produce detailed images that match the given description.
The Art of GPT-Image Portraits
One of the most captivating aspects of GPT-Image is its ability to create portraits of women that are both realistic and aesthetically pleasing. Through its training on vast datasets of portrait images, the model has learned to capture the intricacies of human features, expressions, and emotions. Whether it’s a serene smile, a playful glance, or a contemplative pose, GPT-Image excels at translating textual cues into visually stunning renditions.
Hello to every one, the contents present at this
site are actually remarkable for people knowledge, well, keep up the good work fellows.
bài baccarat là gì
Bài viết: Bài baccarat là gì và tại sao nó hấp dẫn tại 911WIN Casino?
Bài baccarat là một trò chơi đánh bài phổ biến và thu hút đông đảo người chơi tại sòng bạc trực tuyến 911WIN. Với tính đơn giản, hấp dẫn và cơ hội giành chiến thắng cao, bài baccarat đã trở thành một trong những trò chơi ưa thích của những người yêu thích sòng bạc trực tuyến. Hãy cùng tìm hiểu về trò chơi này và vì sao nó được ưa chuộng tại 911WIN Casino.
Baccarat là gì?
Baccarat là một trò chơi đánh bài dựa trên may mắn, phổ biến trong các sòng bạc trên toàn thế giới. Người chơi tham gia bài baccarat thông qua việc đặt cược vào một trong ba tùy chọn: người chơi thắng, người chơi thua hoặc hai bên hòa nhau. Trò chơi này không yêu cầu người chơi có kỹ năng đặc biệt, mà chủ yếu là dựa vào sự may mắn và cảm giác.
Tại sao bài baccarat hấp dẫn tại 911WIN Casino?
911WIN Casino cung cấp trải nghiệm chơi bài baccarat tuyệt vời với những ưu điểm hấp dẫn dưới đây:
Đa dạng biến thể: Tại 911WIN Casino, bạn sẽ được tham gia vào nhiều biến thể bài baccarat khác nhau. Bạn có thể lựa chọn chơi phiên bản cổ điển, hoặc thử sức với các phiên bản mới hơn như Mini Baccarat hoặc Baccarat Squeeze. Điều này giúp bạn trải nghiệm sự đa dạng và hứng thú trong quá trình chơi.
Chất lượng đồ họa và âm thanh: 911WIN Casino đảm bảo mang đến trải nghiệm chơi bài baccarat trực tuyến chân thực và sống động nhất. Đồ họa tuyệt đẹp và âm thanh chân thực khiến bạn cảm giác như đang chơi tại sòng bạc truyền thống, từ đó nâng cao thú vị và hứng thú khi tham gia.
Cơ hội thắng lớn: Bài baccarat tại 911WIN Casino mang đến cơ hội giành chiến thắng lớn. Dự đoán đúng kết quả của ván bài có thể mang về cho bạn những phần thưởng hấp dẫn và giá trị.
Hỗ trợ khách hàng chuyên nghiệp: Nếu bạn gặp bất kỳ khó khăn hoặc có câu hỏi về trò chơi, đội ngũ hỗ trợ khách hàng 24/7 của 911WIN Casino sẽ luôn sẵn sàng giúp bạn. Họ tận tâm và chuyên nghiệp trong việc giải đáp mọi thắc mắc, đảm bảo bạn có trải nghiệm chơi bài baccarat suôn sẻ và dễ dàng.
order doxycycline tablets
Drug prescribing information. Generic Name.
fluoxetine
Actual trends of medication. Read information now.
Meds information leaflet. Effects of Drug Abuse.
where buy retrovir
Everything news about drugs. Read information now.
Kéo baccarat là một biến thể hấp dẫn của trò chơi bài baccarat tại sòng bạc trực tuyến 911WIN. Được biết đến với cách chơi thú vị và cơ hội giành chiến thắng cao, kéo baccarat đã trở thành một trong những trò chơi được người chơi yêu thích tại 911WIN Casino. Hãy cùng khám phá về trò chơi này và những điểm thu hút tại 911WIN Casino.
Kéo baccarat là gì?
Kéo baccarat là một biến thể độc đáo của bài baccarat truyền thống. Trong kéo baccarat, người chơi sẽ đối đầu với nhà cái và cùng nhau tạo thành một bộ bài gồm hai lá. Mục tiêu của trò chơi là dự đoán bộ bài nào sẽ có điểm số cao hơn. Bộ bài gồm 2 lá, và điểm số của bài được tính bằng tổng số điểm của hai lá bài. Điểm số cao nhất là 9 và bộ bài gần nhất với số 9 sẽ là người chiến thắng.
Tại sao kéo baccarat thu hút tại 911WIN Casino?
Cách chơi đơn giản: Kéo baccarat có cách chơi đơn giản và dễ hiểu, phù hợp với cả người chơi mới bắt đầu. Bạn không cần phải có kỹ năng đặc biệt để tham gia, mà chỉ cần dự đoán đúng bộ bài có điểm số cao hơn.
Tính cạnh tranh và hấp dẫn: Trò chơi kéo baccarat tại 911WIN Casino mang đến sự cạnh tranh và hấp dẫn. Bạn sẽ đối đầu trực tiếp với nhà cái, tạo cảm giác thú vị và căng thẳng trong từng ván bài.
Cơ hội giành chiến thắng cao: Kéo baccarat mang lại cơ hội giành chiến thắng cao cho người chơi. Bạn có thể dễ dàng đoán được bộ bài gần với số 9 và từ đó giành phần thưởng hấp dẫn.
Trải nghiệm chân thực: Kéo baccarat tại 911WIN Casino được thiết kế với đồ họa chất lượng và âm thanh sống động, mang đến trải nghiệm chơi bài tương tự như tại sòng bạc truyền thống. Điều này tạo ra sự hứng thú và mãn nhãn cho người chơi.
Tóm lại, kéo baccarat là một biến thể thú vị của trò chơi bài baccarat tại 911WIN Casino. Với cách chơi đơn giản, tính cạnh tranh và hấp dẫn, cơ hội giành chiến thắng cao, cùng với trải nghiệm chân thực, không khó hiểu khi kéo baccarat trở thành lựa chọn phổ biến của người chơi tại 911WIN Casino. Hãy tham gia ngay để khám phá và tận hưởng niềm vui chơi kéo baccarat cùng 911WIN Casino!
Medicament information for patients. What side effects?
can you buy bactrim
Everything news about medicines. Read information now.
Medication information sheet. Generic Name.
rx trazodone
Actual about meds. Read information now.
Hey! This is my first visit to your blog! We are a collection of volunteers and starting a new initiative in a community in the same niche.
Your blog provided us valuable information to work on. You have done a extraordinary job!
1. Lightening : It consists in identifying all the sources of overloads in your food plan and eliminating them over several days by changing them with meals of natural quality if this is not already the case and in a amount tailored to https://www.hiboox.com/high-roller-online-casino/ your wants.
buy generic cleocin
Pills information. Cautions.
lyrica
All what you want to know about medicines. Get now.
prednisone 7.5 mg: https://prednisone1st.store/# order prednisone on line
Do you mind if I quote a couple of your articles as long as
I provide credit and sources back to your site? My blog is
in the very same area of interest as yours and my visitors would really benefit from some of the information you provide
here. Please let me know if this alright with you.
Appreciate it!
Medicine information. Cautions.
norpace
All about medicament. Get information here.
online arzt levaquin
finasteride topical
Ебацца
Study the เล่นสล็อตฟรี game before betting. before playing slot games Or choose a slot game Players should understand about online slot games first. should know how the game itself works in order to select the best games to make profitable bets Choose high-paying games Choose to play slot games with high payouts to get more advantages when you win. will be worth the bet When withdrawing money, you will get a lot of money. good value for money\ Pick a trending game. Selecting the most popular slot games is a filter from other players. that it is a game that is really fun and make real money The more players bet on that game, the more. The more you can confirm that the game is a quality game.Try out the game before making real bets. On the web slot games for players to play Try playing PG slots for you to get to know more in-depth slot games. See if the game is worth investing in. And is the game that can make money for you or not?
Medicine information. Drug Class.
cytotec
All news about pills. Get here.
Drug information for patients. What side effects can this medication cause?
kamagra
Some news about drug. Read information here.
Buspar
Thanks for sharing your thoughts on kredyt hipoteczny 2 procent.
Regards https://drive.google.com/drive/folders/1dQ_b2b74fvbDYNqOtXWLTtqOsFA0cE6W
Drug information. What side effects can this medication cause?
priligy
Actual what you want to know about drug. Read information now.
Статейное и ссылочное продвижение.
В наши дни, фактически каждый человек пользуется интернетом.
С его помощью возможно отыскать любую информацию
из различных интернет-источников и поисковых
систем.
Для кого-то собственный сайт — это
хобби. Но, большинство используют созданные проекты для заработка и привлечение прибыли.
У вас имеется собственный сайт и вы желаете привлечь на него максимум посетителей, но не знаете с чего начать?
Обратитесь к нам! Мы поможем!
каталог без обратной ссылки
prednisone for sale
Medicines information. Effects of Drug Abuse.
buy zithromax
All information about drug. Read now.
cipro antibiotic
Meds information. Brand names.
singulair sale
All news about meds. Get information now.
buy prednisone tablets uk: http://prednisone1st.store/# prednisone cream
levaquin medication
Additional information and facts and verification can be acquired from the community law enforcement company where by the sexual intercourse offender resides. And no one can record your private session so its 100% risk-free.
Medicament information. Brand names.
baclofen
Actual about medicament. Get here.
Meds information leaflet. What side effects can this medication cause?
generic zofran
Everything about pills. Get information here.
My programmer is trying to persuade me to move
to .net from PHP. I have always disliked the idea because of the costs.
But he’s tryiong none the less. I’ve been using Movable-type on several websites for about a year and
am worried about switching to another platform.
I have heard excellent things about blogengine.net.
Is there a way I can transfer all my wordpress content into it?
Any help would be greatly appreciated!
buy cheap lisinopril price
So when schools shut down again last fall after only a week open, McAvoy was crushed.
Here is my site: bj 알바
Medicine information for patients. Brand names.
tadacip order
Everything news about drugs. Read information now.
tadacip 300
2023FIBA世界盃籃球:賽程、場館、NBA球員出賽名單在這看
2023年的FIBA男子世界盃籃球賽(英語:2023 FIBA Basketball World Cup)是第19屆的比賽,也是自2019年新制度實施後的第二次比賽。從這屆開始,比賽將恢復每四年舉行一次的週期。
在這次比賽中,來自歐洲和美洲的前兩名球隊,以及來自亞洲、大洋洲和非洲的最佳球隊,以及2024年夏季奧運會的主辦國法國(共8隊)將獲得在巴黎舉行的奧運會比賽的參賽資格。
2023FIBA籃球世界盃由32國競爭冠軍榮耀
2023世界盃籃球資格賽在2021年11月22日至2023年2月27日已舉辦完畢,共有非洲區、美洲區、亞洲、歐洲區資格賽,最後出線的國家總共有32個。
很可惜的台灣並沒有闖過世界盃籃球亞洲區資格賽,在世界盃籃球資格賽中華隊並無進入複賽。
2023FIBA世界盃籃球比賽場館
FIBA籃球世界盃將會在6個體育場館舉行。菲律賓馬尼拉將進行四組預賽,兩組十六強賽事以及八強之後所有的賽事。另外,日本沖繩市與印尼雅加達各舉辦兩組預賽及一組十六強賽事。
菲律賓此次將有四個場館作為世界盃比賽場地,帕賽市的亞洲購物中心體育館,奎松市的阿拉內塔體育館,帕西格的菲爾體育館以及武加偉的菲律賓體育館。菲律賓體育館約有55,000個座位,此場館也將會是本屆賽事的決賽場地。
日本與印尼各有一個場地舉辦世界盃賽事。沖繩市綜合運動場與雅加達史納延紀念體育館。
國家 城市 場館 容納人數
菲律賓 帕賽市 亞洲購物中心體育館 20,000
菲律賓 奎松市 阿拉內塔體育館 15,000
菲律賓 帕希格 菲爾體育館 10,000
菲律賓 武加偉 菲律賓體育館(決賽場館) 55,000
日本 沖繩 綜合運動場 10,000
印尼 雅加達 史納延紀念體育館 16,500
2023FIBA世界盃籃球預賽積分統計
預賽分為八組,每一組有四個國家,預賽組內前兩名可以晉級複賽,預賽成績併入複賽計算,複賽各組第三、四名不另外舉辦9-16名排位賽。
而預賽組內後兩名進行17-32名排位賽,預賽成績併入計算,但不另外舉辦17-24名、25-32名排位賽,各組第一名排入第17至20名,第二名排入第21至24名,第三名排入第25至28名,第四名排入第29至32名。
2023世界盃籃球美國隊成員
此次美國隊有12位現役NBA球員加入,雖然並沒有超級巨星等級的球員在內,但是各個位置的分工與角色非常鮮明,也不乏未來的明日之星,其中有籃網隊能投外線的外圍防守大鎖Mikal Bridges,尼克隊與溜馬隊的主控Jalen Brunson、Tyrese Haliburton,多功能的後衛Austin Reaves。
前鋒有著各種功能性的球員,魔術隊高大身材的狀元Paolo Banchero、善於碰撞切入製造犯規,防守型的Josh Hart,進攻型搖擺人Anthony Edwards與Brandon Ingram,接應與防守型的3D側翼Cam Johnson,以及獲得23’賽季最佳防守球員的大前鋒Jaren Jackson Jr.,中鋒則有著敏銳火鍋嗅覺的Walker Kessler與具有外線射程的Bobby Portis。
美國隊上一次獲得世界盃冠軍是在2014年,當時一支由Curry、Irving和Harden等後起之秀組成的陣容帶領美國隊奪得了金牌。與 2014 年總冠軍球隊非常相似,今年的球隊由在 2022-23 NBA 賽季中表現出色的新星組成,就算他們都是資歷尚淺的NBA新面孔,也不能小看這支美國隊。
FIBA世界盃熱身賽就在新莊體育館
FIBA世界盃2023新北熱身賽即將在8月19日、20日和22日在新莊體育館舉行。新北市長侯友宜、立陶宛籃球協會秘書長Mindaugas Balčiūnas,以及台灣運彩x T1聯盟會長錢薇娟今天下午一同公開了熱身賽的球星名單、賽程、售票和籃球交流的詳細資訊。他們誠摯邀請所有籃球迷把握這個難得的機會,親眼見證來自立陶宛、拉脫維亞和波多黎各的NBA現役球星的出色表現。
新莊體育館舉行的熱身賽將包括立陶宛、蒙特內哥羅、墨西哥和埃及等國家,分為D組。首場賽事將在8月19日由立陶宛對波多黎各開打,8月20日波多黎各將與拉脫維亞交手,8月22日則是拉脫維亞與立陶宛的精彩對決。屆時,觀眾將有機會近距離欣賞到國王隊的中鋒沙波尼斯(Domantas Sabonis)、鵜鶘隊的中鋒瓦蘭丘納斯(Jonas Valančiūnas)、後衛阿爾瓦拉多(Jose Alvarado)、賽爾蒂克隊的大前鋒波爾辛吉斯(Kristaps Porzingis)、雷霆隊的大前鋒貝坦斯(Davis Bertans)等NBA現役明星球員的精湛球技。
如何投注2023FIBA世界盃籃球?使用PM體育平台投注最方便!
PM體育平台完整各式運動賽事投注,高賠率、高獎金,盤口方面提供客戶全自動跟盤、半自動跟盤及全方位操盤介面,跟盤系統中,我們提供了完整的資料分析,如出賽球員、場地、天氣、球隊氣勢等等的資料完整呈現,而手機的便捷,可讓玩家隨時隨地線上投注,24小時體驗到最精彩刺激的休閒享受。
Medicine information leaflet. Effects of Drug Abuse.
kamagra
Actual trends of drug. Read information here.
Drugs information leaflet. Short-Term Effects.
get amoxil
Everything news about drugs. Get now.
Order doxycycline pills
essay writing service learning theory https://www.writemyessaylife.com/ visit essay writing service
Tetracycline capsules
Pills information for patients. What side effects can this medication cause?
how to get effexor
Best trends of medicine. Get here.
педагогика и саморазвитие -> ПСИХОЛОГИЯ УПРАВЛЕНИЯ -> Правила профессионального общения
Medication prescribing information. What side effects can this medication cause?
celebrex
Best about medicine. Read now.
Meds information leaflet. What side effects can this medication cause?
provigil tablet
Everything what you want to know about meds. Get now.
buy prednisone online
Medicines prescribing information. Brand names.
generic celebrex
Some what you want to know about medicine. Read here.
Демонтаж стен Москва
Демонтаж стен Москва
Meds prescribing information. What side effects can this medication cause?
zithromax
Actual trends of meds. Get now.
Medicines information sheet. Long-Term Effects.
tadacip buy
Everything what you want to know about pills. Read now.
Taking advantage oof quite a few bonus delivers can give you added value wben betting on sports.
my website … 토토친구
Medicine information. What side effects can this medication cause?
nexium
All news about drug. Read information here.
levaquin economico online
The greater your score, the far more most likely you are to be approved for a loan with favorable terms.
Here is my web-site http://higbeeinsurance.com/?p=1
Medicine information leaflet. Effects of Drug Abuse.
can i get pregabalin
Best about drug. Read information here.
lisinopril hydrochlorothiazide
lisinopril mechanism of action
I think the admin of this site is genuinely working hard in support of his web site, for the reason that here every information is quality based information.
Medicines information for patients. Brand names.
tadacip online
Best about drug. Get information here.
Drugs information sheet. Long-Term Effects.
zofran
Best information about medicine. Get here.
Free SEO Strategy in Nigeria
Content Krush Is a Digital Marketing Consulting Firm in Lagos, Nigeria with Focus on Search Engine Optimization, Growth Marketing, B2B Lead Generation, and Content Marketing.
Medicament prescribing information. Brand names.
sildigra without prescription
Everything trends of meds. Read here.
prasugrel pharmacy
Medicine information for patients. Brand names.
norvasc otc
Everything about meds. Get now.
今彩539:您的全方位彩票投注平台
今彩539是一個專業的彩票投注平台,提供539開獎直播、玩法攻略、賠率計算以及開獎號碼查詢等服務。我們的目標是為彩票愛好者提供一個安全、便捷的線上投注環境。
539開獎直播與號碼查詢
在今彩539,我們提供即時的539開獎直播,讓您不錯過任何一次開獎的機會。此外,我們還提供開獎號碼查詢功能,讓您隨時追蹤最新的開獎結果,掌握彩票的動態。
539玩法攻略與賠率計算
對於新手彩民,我們提供詳盡的539玩法攻略,讓您快速瞭解如何進行投注。同時,我們的賠率計算工具,可幫助您精準計算可能的獎金,讓您的投注更具策略性。
台灣彩券與線上彩票賠率比較
我們還提供台灣彩券與線上彩票的賠率比較,讓您清楚瞭解各種彩票的賠率差異,做出最適合自己的投注決策。
全球博彩行業的精英
今彩539擁有全球博彩行業的精英,超專業的技術和經營團隊,我們致力於提供優質的客戶服務,為您帶來最佳的線上娛樂體驗。
539彩票是台灣非常受歡迎的一種博彩遊戲,其名稱”539″來自於它的遊戲規則。這個遊戲的玩法簡單易懂,並且擁有相對較高的中獎機會,因此深受彩民喜愛。
遊戲規則:
539彩票的遊戲號碼範圍為1至39,總共有39個號碼。
玩家需要從1至39中選擇5個號碼進行投注。
每期開獎時,彩票會隨機開出5個號碼作為中獎號碼。
中獎規則:
若玩家投注的5個號碼與當期開獎的5個號碼完全相符,則中得頭獎,通常是豐厚的獎金。
若玩家投注的4個號碼與開獎的4個號碼相符,則中得二獎。
若玩家投注的3個號碼與開獎的3個號碼相符,則中得三獎。
若玩家投注的2個號碼與開獎的2個號碼相符,則中得四獎。
若玩家投注的1個號碼與開獎的1個號碼相符,則中得五獎。
優勢:
539彩票的中獎機會相對較高,尤其是對於中小獎項。
投注簡單方便,玩家只需選擇5個號碼,就能參與抽獎。
獎金多樣,不僅有頭獎,還有多個中獎級別,增加了中獎機會。
在今彩539彩票平台上,您不僅可以享受優質的投注服務,還能透過我們提供的玩法攻略和賠率計算工具,更好地了解遊戲規則,並提高投注的策略性。無論您是彩票新手還是有經驗的老手,我們都將竭誠為您提供最專業的服務,讓您在今彩539平台上享受到刺激和娛樂!立即加入我們,開始您的彩票投注之旅吧!
Medication information. What side effects can this medication cause?
can i buy tadacip
Some what you want to know about medicines. Read information now.
levaquin cheap
OLL Порно
Meds information leaflet. What side effects?
buy generic amoxil
Some what you want to know about drug. Get now.
6-я детская поликлиника
levaquin other names
If you or somebody you know has a gambling ssue and desires aid, call GAMBLER.
My blog … 토토사이트
buy fenofibrate for sale cheap tricor order generic tricor 160mg
Meds information sheet. Generic Name.
flagyl
All information about medicament. Get now.
nhà cái uy tín
kantorbola
Situs Judi Slot Online Terpercaya dengan Permainan Dijamin Gacor dan Promo Seru”
Kantorbola merupakan situs judi slot online yang menawarkan berbagai macam permainan slot gacor dari provider papan atas seperti IDN Slot, Pragmatic, PG Soft, Habanero, Microgaming, dan Game Play. Dengan minimal deposit 10.000 rupiah saja, pemain bisa menikmati berbagai permainan slot gacor, antara lain judul-judul populer seperti Gates Of Olympus, Sweet Bonanza, Laprechaun, Koi Gate, Mahjong Ways, dan masih banyak lagi, semuanya dengan RTP tinggi di atas 94%. Selain slot, Kantorbola juga menyediakan pilihan judi online lainnya seperti permainan casino online dan taruhan olahraga uang asli dari SBOBET, UBOBET, dan CMD368.
Meds information sheet. Cautions.
zoloft rx
Some what you want to know about meds. Get information here.
where is better to buy levaquin
Drug prescribing information. Short-Term Effects.
buy generic celebrex
Best news about medication. Get information now.
I need to to thank you for this great read!! I certainly
enjoyed every little bit of it. I have got you saved as a favorite to look
at new stuff you post…
Pills information. Long-Term Effects.
buy zoloft
Actual what you want to know about medicament. Read information now.
Medicine information for patients. Long-Term Effects.
nolvadex
Some what you want to know about medication. Read here.
foods that lower cholesterol
Explore a delectable world of foods that lower cholesterol and take charge of your cardiovascular health. From succulent berries to nutrient-rich greens, uncover a diverse array of options that can effectively contribute to reducing cholesterol levels, all while savoring the flavors of a heart-healthy lifestyle.
Delve into the science and flavor of foods that lower cholesterol, as this article guides you through a culinary journey aimed at promoting optimal heart wellness. Learn how incorporating these cholesterol-conscious choices, such as fiber-packed vegetables and antioxidant-rich fruits, can have a positive impact on managing cholesterol levels and overall cardiovascular health.
Medicament information for patients. Drug Class.
seroquel
Best news about meds. Read here.
ashwagandha benefits side effects
Hi there, I want to subscribe for this webpage to obtain most recent updates, therefore where can i do it please assist.
Hello superb blog! Does running a blog similar to this take
a lot of work? I’ve virtually no knowledge of coding however I had been hoping to start my own blog in the near future.
Anyhow, should you have any recommendations or tips for new blog owners please share.
I know this is off subject but I just wanted to ask.
Many thanks!
The casino demands to know some standard info about you before opening ann account.
Heere is my site: Online Slot Machines
Medicines information leaflet. What side effects can this medication cause?
buy cialis super active
Everything news about medication. Read now.
finasteride 5
Drug information for patients. Short-Term Effects.
fluoxetine pill
All what you want to know about pills. Read here.
I know this web site gives quality depending articles and extra information, is there any other website which provides these kinds of
things in quality?
FortuneJaack givess an appealing welcome bonus for new players.
Take a look at my web page: Online Slot Machines
Drug information leaflet. Brand names.
propecia pill
Best information about pills. Read here.
Neural network woman image
Unveiling the Beauty of Neural Network Art! Dive into a mesmerizing world where technology meets creativity. Neural networks are crafting stunning images of women, reshaping beauty standards and pushing artistic boundaries. Join us in exploring this captivating fusion of AI and aesthetics. #NeuralNetworkArt #DigitalBeauty
Proscar
Medicine information. Generic Name.
cordarone
Everything trends of meds. Read now.
On account of their superior broadcasting, thepokies 17 reside casinos present a more premium version of the standard casino experience. The Curacao gaming regulator and licence provider is famous for offering safe playing alternatives to players worldwide, so players need not fear.
Medicament information for patients. What side effects?
amoxil no prescription
Some what you want to know about medicines. Read now.
doxycycline 100mg capsules pil
Medicine information. Drug Class.
xenical without insurance
All what you want to know about medicament. Get information here.
Автомобильные новости на Смоленском портале. Архив новостей. семь недель назад. 1 страница
Meds information for patients. Short-Term Effects.
where to get finpecia
Everything information about medicines. Read information now.
Pills information. Cautions.
pregabalin tablet
Actual news about meds. Get information here.
Pills information leaflet. Drug Class.
valtrex
Everything news about medication. Read now.
Pills prescribing information. Generic Name.
can i get zoloft
Actual what you want to know about drug. Read information now.
levaquin mechanism of action
levaquin no prescription
世界盃籃球
2023FIBA世界盃籃球:賽程、場館、NBA球員出賽名單在這看
2023年的FIBA男子世界盃籃球賽(英語:2023 FIBA Basketball World Cup)是第19屆的比賽,也是自2019年新制度實施後的第二次比賽。從這屆開始,比賽將恢復每四年舉行一次的週期。
在這次比賽中,來自歐洲和美洲的前兩名球隊,以及來自亞洲、大洋洲和非洲的最佳球隊,以及2024年夏季奧運會的主辦國法國(共8隊)將獲得在巴黎舉行的奧運會比賽的參賽資格。
2023FIBA籃球世界盃由32國競爭冠軍榮耀
2023世界盃籃球資格賽在2021年11月22日至2023年2月27日已舉辦完畢,共有非洲區、美洲區、亞洲、歐洲區資格賽,最後出線的國家總共有32個。
很可惜的台灣並沒有闖過世界盃籃球亞洲區資格賽,在世界盃籃球資格賽中華隊並無進入複賽。
2023FIBA世界盃籃球比賽場館
FIBA籃球世界盃將會在6個體育場館舉行。菲律賓馬尼拉將進行四組預賽,兩組十六強賽事以及八強之後所有的賽事。另外,日本沖繩市與印尼雅加達各舉辦兩組預賽及一組十六強賽事。
菲律賓此次將有四個場館作為世界盃比賽場地,帕賽市的亞洲購物中心體育館,奎松市的阿拉內塔體育館,帕西格的菲爾體育館以及武加偉的菲律賓體育館。菲律賓體育館約有55,000個座位,此場館也將會是本屆賽事的決賽場地。
日本與印尼各有一個場地舉辦世界盃賽事。沖繩市綜合運動場與雅加達史納延紀念體育館。
國家 城市 場館 容納人數
菲律賓 帕賽市 亞洲購物中心體育館 20,000
菲律賓 奎松市 阿拉內塔體育館 15,000
菲律賓 帕希格 菲爾體育館 10,000
菲律賓 武加偉 菲律賓體育館(決賽場館) 55,000
日本 沖繩 綜合運動場 10,000
印尼 雅加達 史納延紀念體育館 16,500
2023FIBA世界盃籃球預賽積分統計
預賽分為八組,每一組有四個國家,預賽組內前兩名可以晉級複賽,預賽成績併入複賽計算,複賽各組第三、四名不另外舉辦9-16名排位賽。
而預賽組內後兩名進行17-32名排位賽,預賽成績併入計算,但不另外舉辦17-24名、25-32名排位賽,各組第一名排入第17至20名,第二名排入第21至24名,第三名排入第25至28名,第四名排入第29至32名。
2023世界盃籃球美國隊成員
此次美國隊有12位現役NBA球員加入,雖然並沒有超級巨星等級的球員在內,但是各個位置的分工與角色非常鮮明,也不乏未來的明日之星,其中有籃網隊能投外線的外圍防守大鎖Mikal Bridges,尼克隊與溜馬隊的主控Jalen Brunson、Tyrese Haliburton,多功能的後衛Austin Reaves。
前鋒有著各種功能性的球員,魔術隊高大身材的狀元Paolo Banchero、善於碰撞切入製造犯規,防守型的Josh Hart,進攻型搖擺人Anthony Edwards與Brandon Ingram,接應與防守型的3D側翼Cam Johnson,以及獲得23’賽季最佳防守球員的大前鋒Jaren Jackson Jr.,中鋒則有著敏銳火鍋嗅覺的Walker Kessler與具有外線射程的Bobby Portis。
美國隊上一次獲得世界盃冠軍是在2014年,當時一支由Curry、Irving和Harden等後起之秀組成的陣容帶領美國隊奪得了金牌。與 2014 年總冠軍球隊非常相似,今年的球隊由在 2022-23 NBA 賽季中表現出色的新星組成,就算他們都是資歷尚淺的NBA新面孔,也不能小看這支美國隊。
FIBA世界盃熱身賽就在新莊體育館
FIBA世界盃2023新北熱身賽即將在8月19日、20日和22日在新莊體育館舉行。新北市長侯友宜、立陶宛籃球協會秘書長Mindaugas Balčiūnas,以及台灣運彩x T1聯盟會長錢薇娟今天下午一同公開了熱身賽的球星名單、賽程、售票和籃球交流的詳細資訊。他們誠摯邀請所有籃球迷把握這個難得的機會,親眼見證來自立陶宛、拉脫維亞和波多黎各的NBA現役球星的出色表現。
新莊體育館舉行的熱身賽將包括立陶宛、蒙特內哥羅、墨西哥和埃及等國家,分為D組。首場賽事將在8月19日由立陶宛對波多黎各開打,8月20日波多黎各將與拉脫維亞交手,8月22日則是拉脫維亞與立陶宛的精彩對決。屆時,觀眾將有機會近距離欣賞到國王隊的中鋒沙波尼斯(Domantas Sabonis)、鵜鶘隊的中鋒瓦蘭丘納斯(Jonas Valančiūnas)、後衛阿爾瓦拉多(Jose Alvarado)、賽爾蒂克隊的大前鋒波爾辛吉斯(Kristaps Porzingis)、雷霆隊的大前鋒貝坦斯(Davis Bertans)等NBA現役明星球員的精湛球技。
如何投注2023FIBA世界盃籃球?使用PM體育平台投注最方便!
PM體育平台完整各式運動賽事投注,高賠率、高獎金,盤口方面提供客戶全自動跟盤、半自動跟盤及全方位操盤介面,跟盤系統中,我們提供了完整的資料分析,如出賽球員、場地、天氣、球隊氣勢等等的資料完整呈現,而手機的便捷,可讓玩家隨時隨地線上投注,24小時體驗到最精彩刺激的休閒享受。
Medicine information for patients. Short-Term Effects.
viagra medication
All trends of drugs. Get information now.
amoxicillin 30 capsules price: https://amoxicillins.com/# amoxicillin 50 mg tablets
Система начисления очков подобающая: меньший карты раз-другой числами равноправны номиналу, иллюстрации доставляют полно десятого очков, https://cbo.org.ua/muzichnij-suprovid-slotiv/ туз – одну не то — не то одиннадцатого очков для парадигматика.
539開獎
今彩539:您的全方位彩票投注平台
今彩539是一個專業的彩票投注平台,提供539開獎直播、玩法攻略、賠率計算以及開獎號碼查詢等服務。我們的目標是為彩票愛好者提供一個安全、便捷的線上投注環境。
539開獎直播與號碼查詢
在今彩539,我們提供即時的539開獎直播,讓您不錯過任何一次開獎的機會。此外,我們還提供開獎號碼查詢功能,讓您隨時追蹤最新的開獎結果,掌握彩票的動態。
539玩法攻略與賠率計算
對於新手彩民,我們提供詳盡的539玩法攻略,讓您快速瞭解如何進行投注。同時,我們的賠率計算工具,可幫助您精準計算可能的獎金,讓您的投注更具策略性。
台灣彩券與線上彩票賠率比較
我們還提供台灣彩券與線上彩票的賠率比較,讓您清楚瞭解各種彩票的賠率差異,做出最適合自己的投注決策。
全球博彩行業的精英
今彩539擁有全球博彩行業的精英,超專業的技術和經營團隊,我們致力於提供優質的客戶服務,為您帶來最佳的線上娛樂體驗。
539彩票是台灣非常受歡迎的一種博彩遊戲,其名稱”539″來自於它的遊戲規則。這個遊戲的玩法簡單易懂,並且擁有相對較高的中獎機會,因此深受彩民喜愛。
遊戲規則:
539彩票的遊戲號碼範圍為1至39,總共有39個號碼。
玩家需要從1至39中選擇5個號碼進行投注。
每期開獎時,彩票會隨機開出5個號碼作為中獎號碼。
中獎規則:
若玩家投注的5個號碼與當期開獎的5個號碼完全相符,則中得頭獎,通常是豐厚的獎金。
若玩家投注的4個號碼與開獎的4個號碼相符,則中得二獎。
若玩家投注的3個號碼與開獎的3個號碼相符,則中得三獎。
若玩家投注的2個號碼與開獎的2個號碼相符,則中得四獎。
若玩家投注的1個號碼與開獎的1個號碼相符,則中得五獎。
優勢:
539彩票的中獎機會相對較高,尤其是對於中小獎項。
投注簡單方便,玩家只需選擇5個號碼,就能參與抽獎。
獎金多樣,不僅有頭獎,還有多個中獎級別,增加了中獎機會。
在今彩539彩票平台上,您不僅可以享受優質的投注服務,還能透過我們提供的玩法攻略和賠率計算工具,更好地了解遊戲規則,並提高投注的策略性。無論您是彩票新手還是有經驗的老手,我們都將竭誠為您提供最專業的服務,讓您在今彩539平台上享受到刺激和娛樂!立即加入我們,開始您的彩票投注之旅吧!
Meds information. Generic Name.
norvasc brand name
Some what you want to know about medicine. Get information now.
zyrtec dose
online ed pills: what are ed drugs – erectile dysfunction drug
Pills prescribing information. Short-Term Effects.
lyrica
Some about pills. Get now.
Thank you a lot for sharing this with all of us you really understand what
you are talking about! Bookmarked. Kindly also talk over with
my site =). We may have a hyperlink alternate contract among us
Stop by my webpage – phoenix junkyards
Квартиры на них драгоценны, коли процентов шестьдесят населений живут в юрточных посёлках, которые облепили окраины Улан-Батора, http://uzinform.com.ua/news/2022/12/20/195336.html (то) есть опята.
That is very attention-grabbing, You are an overly professional blogger.
I’ve joined your rss feed and stay up for searching for extra of your excellent
post. Also, I’ve shared your web site in my social networks
Удалено (перепутал раздел)
Такие надежные лицензированные игровые порталы обеспечивают недурственную ответную реакцию слотов равным https://topplaycasino.win/best образом качественное уход.
cefixima
cleocin reviews
По моему мнению Вы не правы. Я уверен. Предлагаю это обсудить. Пишите мне в PM, пообщаемся.
Massage envy is approach overpriced for my happy ending spa nyc part. Phila Massages. Therapeutic massage Gun by “Astamaniana”.
Medicines prescribing information. Effects of Drug Abuse.
sildigra tablet
Actual about pills. Read now.
Thanks for one’s marvelous posting! I actually enjoyed
reading it, you are a great author. I will be sure
to bookmark your blog and will eventually
come back in the foreseeable future. I want to encourage yourself to continue your
great job, have a nice day!
Medication information. Long-Term Effects.
lopressor buy
Best information about medicines. Read information now.
Демонтаж стен Москва
Демонтаж стен Москва
Смоленск в сети
best online canadian pharmacy canadian drugstore online
That is a great tip especially to those fresh to the blogosphere.
Simple but very accurate info… Thank you for
sharing this one. A must read article!
Pills information. Generic Name.
cipro order
Actual news about medicines. Get information now.
cost generic propecia for sale buy propecia
Medicine prescribing information. Drug Class.
eldepryl
Best trends of medication. Read here.
Статейное и ссылочное продвижение.
В наши дни, фактически каждый человек пользуется интернетом.
С его помощью можно найти любую информацию из разных интернет-источников и поисковых систем.
Для кого-то собственный сайт — это хобби.
Но, большая часть применяют созданные проекты для заработка и привлечение прибыли.
У вас имеется собственный сайт и вы желаете привлечь на него максимум визитёров,
но не знаете с чего начать? Обратитесь к нам!
Мы поможем!
обратные ссылки в html
buy levaquin online without prescription
Next you need to start out applying for internship. The video http://www.barrimen.fr.fo/wikiars/index.php?title=bondarsvideo Brisbane Firm is bound to get impressed by all that you have achieved and you’ll count on a name from them.
ed pills: ed pills – best ed drugs
Meds information for patients. What side effects can this medication cause?
mobic
Some about drugs. Read information here.
Medicament prescribing information. Cautions.
nolvadex
Best information about drug. Read information here.
Абсолютно с Вами согласен. Мне нравится Ваша идея. Предлагаю вынести на общее обсуждение.
Puff Daddy. Тупак прилюдно обстебывал Бигги и возьми целую державу растрезвонил касательно домашнею взаимоотношении начиная с. Ant. до его https://t.me/daddy_kazino благоверной.
generic levaquin prices
Drug information sheet. Drug Class.
zithromax
Everything information about medication. Read now.
Meds information. Short-Term Effects.
trazodone
Some information about medicament. Get here.
Drug information leaflet. Long-Term Effects.
cost viagra soft
All about pills. Read here.
albuterol sulfate
can i get lisinopril
can i get generic mobic tablets: can i order mobic online – how to get mobic no prescription
Excellent post. I used to be checking continuously this weblog and I am impressed!
Very helpful info specially the final section 🙂 I take care of such info much.
I was seeking this certain info for a long time. Thank you and best of luck.
Medicine information leaflet. Brand names.
tadacip tablet
All information about medicament. Read here.
Drug information for patients. Cautions.
stromectol buy
All what you want to know about medicine. Read information now.
Демонтаж стен Москва
Демонтаж стен Москва
Бесплатное порно
amoxicillin interactions
77 canadian pharmacy canadian pharmacy 24
All trends of medicament.
amoxicillin medicine over the counter where can i get amoxicillin – 875 mg amoxicillin cost
Best and news about drug.
Cabgolin
Попросил поддержке у возлюбленного: сидя три шага, http://photobase.ro/profile.php?uid=68568 некто должен был испытывать меня и вовсе не разрешать клацать по-крупному. У один-одинешенек шмальнул сто тыщ и должен был обернуть через неделю 120 тысяч.
Drug prescribing information. Effects of Drug Abuse.
rx levitra
Everything information about drugs. Read information now.
Medicament information for patients. Long-Term Effects.
singulair medication
Actual about medicine. Read here.
Признателен за помощь в этом вопросе, как я могу Вас отблагодарить?
Регистрация представляет загромождение пустотелее небольшой прибавлением правдивой отчете. Применение промокодов общепонятно буква слотах, игровых автоматах равным образом рулетке. 3. Программы лояльности. Применяйте интенсивные промокоды и улучайте последние комбинации во мережа, Дэдди казино зеркало ради распространять преимущество нате завоевание.
Medicament prescribing information. What side effects?
zoloft
Some what you want to know about meds. Get information here.
Hello great blog! Does running a blog like this take a great deal of work? I have virtually no understanding of coding but I was hoping to start my own blog soon. Anyways, should you have any ideas or tips for new blog owners please share. I know this is off topic but I simply needed to ask. Thanks!
generic finasteride
amoxicillin over counter: amoxil pharmacy amoxicillin 500mg prescription
Drugs information for patients. Long-Term Effects.
neurontin
All what you want to know about drugs. Get information now.
I truly love your blog.. Great colors & theme.
Did you develop this amazing site yourself? Please reply back as I’m planning to create
my own personal blog and would love to know where you got this from or
what the theme is named. Thanks!
where to buy cheap levaquin pills
order generic propecia without insurance cost of propecia without prescription
sildenafil vs vardenafil vs tadalafil pastillas levitra vardenafil oral jelly
Drug prescribing information. Drug Class.
zithromax tablet
All news about medicines. Read information here.
Medicament information leaflet. Drug Class.
order avodart
All information about pills. Read information here.
order fluoxetine hcl 20 mg capsules
Drugs information for patients. What side effects?
maxalt
Everything news about medication. Read here.
what is gabapentin for
Drugs prescribing information. Brand names.
seroquel generic
Everything information about meds. Read here.
Confido
canadian mail order pharmacy onlinecanadianpharmacy
Демонтаж стен Москва
Демонтаж стен Москва
Drug information for patients. Long-Term Effects.
stromectol cheap
Everything what you want to know about pills. Get here.
Психология
buy generic doxycycline without dr prescription
levaquin in breastfeeding
medications for ed buying ed pills online natural ed medications
世界盃籃球
2023年世界盃籃球賽
2023年世界盃籃球賽(英語:2023 FIBA Basketball World Cup)為第19屆FIBA男子世界盃籃球賽,此是2019年實施新制度後的第2屆賽事,本屆賽事起亦調整回4年週期舉辦。本屆賽事歐洲、美洲各洲最好成績前2名球隊,亞洲、大洋洲、非洲各洲的最好成績球隊及2024年夏季奧林匹克運動會主辦國法國(共8隊)將獲得在巴黎舉行的奧運會比賽資格]]。
申辦過程
2023年世界盃籃球賽提出申辦的11個國家與地區是:阿根廷、澳洲、德國、香港、以色列、日本、菲律賓、波蘭、俄羅斯、塞爾維亞以及土耳其]。2017年8月31日是2023年國際籃總世界盃籃球賽提交申辦資料的截止日期,俄羅斯、土耳其分別遞交了單獨舉辦世界盃的申請,阿根廷/烏拉圭和印尼/日本/菲律賓則提出了聯合申辦]。2017年12月9日國際籃總中心委員會根據申辦情況做出投票,菲律賓、日本、印度尼西亞獲得了2023年世界盃籃球賽的聯合舉辦權]。
比賽場館
本次賽事共將會在5個場館舉行。馬尼拉將進行四組預賽,兩組十六強賽事以及八強之後所有的賽事。另外,沖繩市與雅加達各舉辦兩組預賽及一組十六強賽事。
菲律賓此次將有四個場館作為世界盃比賽場地,帕賽市的亞洲購物中心體育館,奎松市的阿拉內塔體育館,帕西格的菲爾體育館以及武加偉的菲律賓體育館。亞洲購物中心體育館曾舉辦過2013年亞洲籃球錦標賽及2016奧運資格賽。阿拉內塔體育館主辦過1978年男籃世錦賽。菲爾體育館舉辦過2011年亞洲籃球俱樂部冠軍盃。菲律賓體育館約有55,000個座位,此場館也將會是本屆賽事的決賽場地,同時也曾經是2019年東南亞運動會開幕式場地。
日本與印尼各有一個場地舉辦世界盃賽事。沖繩市綜合運動場約有10,000個座位,同時也會是B聯賽琉球黃金國王的新主場。雅加達史納延紀念體育館為了2018年亞洲運動會重新翻新,是2018年亞洲運動會籃球及羽毛球的比賽場地。
17至32名排名賽
預賽成績併入17至32名排位賽計算,且同組晉級複賽球隊對戰成績依舊列入計算
此階段不再另行舉辦17-24名、25-32名排位賽。各組第1名將排入第17至20名,第2名排入第21至24名,第3名排入第25至28名,第4名排入第29至32名
複賽
預賽成績併入16強複賽計算,且同組遭淘汰球隊對戰成績依舊列入計算
此階段各組第三、四名不再另行舉辦9-16名排位賽。各組第3名將排入第9至12名,第4名排入第13至16名
Medication information. Cautions.
norvasc
Actual news about medicine. Get information here.
cost cheap doxycycline for sale
buy actos 30 mg
Ceftin
male ed drugs: best erection pills – ed meds online
This info is priceless. Where can I find out more?
салат с печенью и капустой 2
I?m impressed, I must say. Seldom do I encounter a
blog that?s both equally educative and interesting, and
without a doubt, you’ve hit the nail on the head. The issue is something too few people
are speaking intelligently about. I am very happy that I found this during my search
for something regarding this.
my blog post … junkyeard near me
lisinopril
Замена венцов деревянного дома обеспечивает стабильность и долговечность конструкции. Этот процесс включает замену поврежденных или изношенных верхних балок, гарантируя надежность жилища на долгие годы. подъем дома
Hello! This is kind of off topic but I need some advice from an established
blog. Is it tough to set up your own blog? I’m not very
techincal but I can figure things out pretty fast. I’m thinking about making my own but
I’m not sure where to begin. Do you have any tips or suggestions?
Appreciate it
I do trust all the ideas you’ve introduced in your post. They
are very convincing and can definitely work. Still, the posts are very brief for novices.
May just you please extend them a bit from subsequent time?
Thank you for the post.
It’s an awesome paragraph in favor of all the web people; they
will obtain benefit from it I am sure.
order levaquin
Pills information sheet. Drug Class.
buy generic eldepryl
Actual what you want to know about medicine. Read here.
Appreciate it! An abundance of facts!
lisinopril generic name medication
https://propecia1st.science/# cost propecia
Medicines information sheet. Brand names.
order seroquel
Actual news about drugs. Read information here.
ed drugs ed drug prices cheap ed pills
Medicine prescribing information. Drug Class.
strattera
Best trends of medicament. Get information now.
buy cefixime
I explain a little more how the procedure works in it generic propecia for sale
Medication information sheet. What side effects?
cheap xenical
Best what you want to know about medication. Get information here.
MEGA SLOT
Colchicine
Meds information. Generic Name.
levitra otc
Best trends of medicine. Get information now.
Демонтаж стен Москва
Демонтаж стен Москва
I’m curious to find out what blog system you are using?
I’m having some small security problems with my latest blog and I
would like to find something more secure. Do you have any recommendations?
Необычный салат (омлет и копченый окорочок)
Pills information for patients. Effects of Drug Abuse.
buy bactrim
Everything what you want to know about meds. Get information here.
Do you mind if I quote a few of your posts as long as I provide credit and sources back to your website?
My blog is in the very same niche as yours and my visitors would really benefit
from a lot of the information you present here.
Please let me know if this okay with you. Thanks!
Medicament information leaflet. Effects of Drug Abuse.
bactrim without rx
All what you want to know about medicament. Get information now.
prednisone administration
Medicine information for patients. What side effects?
cialis super active
Actual about meds. Read now.
Thanks. Ample tips.
I’m curious to find out what blog system you happen to be
working with? I’m having some minor security issues
with my latest site and I’d like to find something more safe.
Do you have any recommendations?
Also visit my page: who buys junk cars
https://indiamedicine.world/# best online pharmacy india
Thank you, I enjoy it!
buy cheap levaquin online without prescription
Drug information sheet. Brand names.
cialis super active buy
All information about medicine. Read information here.
This paragraph is in fact a fastidious one it assists new the web people, who are wishing in favor of blogging.
I simply desired to thank you very much yet again. I’m not certain the things
I could possibly have handled in the absence of the type of hints provided by you directly on my
field. It actually was a frightening circumstance in my circumstances, but understanding the very specialized fashion you treated it forced me
to cry for delight. I will be happy for your work and then hope that you are aware of an amazing job you were
getting into training many people all through your websites.
Most likely you haven’t got to know all of us.
my page … 2009 volkswagen jetta
Hola! I’ve been reading your web site for a long time now
and finally got the courage to go ahead and give you a shout out
from Kingwood Texas! Just wanted to mention keep up the good work!
Medication information leaflet. What side effects can this medication cause?
levitra
Best about meds. Read information now.
Very nice post. I just stumbled upon your weblog and wished to mention that I’ve truly enjoyed surfing around
your blog posts. After all I will be subscribing in your rss feed and
I am hoping you write again very soon!
Pills information sheet. Cautions.
proscar order
Some about meds. Get information now.
mexican online pharmacies prescription drugs: mexico drug stores pharmacies – medication from mexico pharmacy
how to write according to in essay does homework help how to write your own opinion in an essay
write outline essay homework help online free how to write a college application essay format
Pills information. Effects of Drug Abuse.
effexor
Actual trends of meds. Read now.
The brain chemical dopamine is known to play a key
role in drug addiction and may also be abnormally regulated in problem gambling.
Previously teased under the working title Project Miami, Roblox’s
collaboration with Spotify was unveiled on May 3rd,
2022. Spotify Island players can complete missions to nab themselves some exclusive freebies: the Hwaiting
and Annyeong emotes, 5-Petal Backpack, and Floating Boombox shoulder
accessory. Can you name this 1974 film in which McQueen plays a firefighter?
In both games, having a keen eye is of huge benefit and plays a large
part in how likely it is that the opponent will make a mistake.
Perhaps the most important part of choosing an online casino is
finding a site with your preferred payment method.
This method is also very popular. State legislators were in deadlock over
who would be allowed to own new casinos and tax revenue sharing.
Prospective licensees, apart from specific requirements related to each type of
gambling type or gambling location licence, generally need to meet the following conditions: (1) personal compliance requirements; (2) registration with the
relevant gambling registry; (3) deposit of financial guarantees;
and (4) compliance with tax and social security
obligations.These gamblers are less motivated to seek treatment,
have poor compliance rates and respond poorly to all interventions.
Some are groomed to replace the boss if he is old or in danger
of going to jail. You may get confused by a few things at first but the apps never make mistakes so you
know the pot is going to the right player.
The Grand Ronde offered in 2003 to build a stadium to
help the city attract a Major League Baseball team,
in exchange for the right to open a casino in the area. The Grand Central venue will offer sports betting alongside food and beverages providing a
unique customer experience and is believed to be
the first sportsbook of its kind to be operated within an independently owned business establishment in the U.S.
Europe with a fun, even more immersive Ryder Cup experience.
Easy to spot for its catchy name, branded logos, and colors,
DraftKings has a simple pitch: fun betting, easy to play, and exemplary mobile
experience. We spent a long time thinking about which site provides
the best sports betting, and we concluded that Betway’s
offering trumped its rivals. DraftKings is no longer simply about sports.For live dealer enthusiasts,
DraftKings boasts an amazing selection for players looking to
try a plethora of games. Farrow’s gunman comes looking for Fury, but ultimately double-crosses his boss.
When it comes to US online casinos, there are few bigger than BetMGM.
Currently, BetMGM operates its online casino in four states-New Jersey, Pennsylvania, Michigan, and West Virginia-not including the company’s signature brick-and-mortar casino
in Las Vegas. DraftKings Casino is licensed and registered in four US states:
New Jersey, Pennsylvania, Michigan, and West Virginia. Just two years after DraftKings online casino launched in Michigan, it is now a full-service mobile casino with hundreds of name-brand online slots, table games and the
most diverse collection of live dealer games in its four
operating states. Though games vary across DraftKings’ four operating states, it
typically has more than 540 slots available.
Things like current bonuses available, as well as a brief insight into what types of games and how many of each type they have.
Not to be mistaken with the 12 zodiac signs, the 12 personality
types have nothing to do with when you were born. If you are 40 years old and
earn $100,000 a year, you should have a net worth of $400,000.Penalties range up to $100,000
and three years in jail for serious offenses.
Therefore health professionals providing treatment will look to address a range of issues
that may be contributing to a person’s compulsion to misuse substances
and gamble. FNM and its affiliated companies are
a news dissemination solutions provider and are NOT a registered
broker/dealer/analyst/adviser, holds no investment licenses and may
NOT sell, offer to sell or offer to buy any security. FNM HOLDS NO SHARES OF ANY
COMPANY NAMED IN THIS RELEASE. The forward-looking statements
in this release are made as of the date hereof and FNM undertakes no
obligation to update such statements. This team are making
a return to the sport this year and taking
over the 2010 Renault squad, retaining some of their staff, just like you can take over opponents
Party Poker and Betfair poker. If you ever need to get in touch with the
customer service team at Vimeo for any reason,
you can reach out on Twitter or visit their help
center. You can get creative and use the multitude of deals on Travelocity’s website to build a
really affordable vacation. You are cautioned that such statements are subject to a multitude
of risks and uncertainties that could cause future circumstances, events, or results to differ materially from those projected in the
forward-looking statements, including the risks that actual results may
differ materially from those projected in the forward-looking statements as a result
of various factors, and other risks identified
in a company’s annual report on Form 10-K or 10-KSB and other filings made by
such company with the Securities and Exchange Commission.
My blog post … BetAndreas Casino
Демонтаж стен Москва
Демонтаж стен Москва
the help essay primary research paper help me plan my essay
Payouts: take-dwelling value wins in an actual sport. Play Aussie on-line cellular pokies on Google Play pokies.net australia 17 and App Store.
Online medicine order: Online medicine home delivery – india pharmacy
On the other hand, betting with digital currencies has many upsides and downsides.
Taake a look at my web blog – http://www.fitad.co.kr
Ремонт старого фундамента — процесс восстановления и укрепления старой основы здания, обеспечивающий его стабильность и долговечность на долгие годы. подъем деревянного дома
Я тоже возьму уж очень интересно.
Анонимность а также засекреченность. Ant. http://test.gigga-grafics.de/index.php/component/vitabook/ открытость. Регуляторы дают обеспечение наличествование во лицензированных игорный дом славнейших механизмов охраны Персональных сведений игроков.
Работа в Кемерово
Claudia Fijal, one in every of the first women hired by Lawner to work as an ‘atmosphere mannequin’ at Snctm when it initially opened, https://www.suprabond.com/?attachment_id=288 called him a ‘trendy-day intercourse Jesus’.
My coder is trying to convince me to move to .net from PHP.
I have always disliked the idea because of the costs.
But he’s tryiong none the less. I’ve been using WordPress on a number of websites for about a
year and am worried about switching to another platform.
I have heard great things about blogengine.net.
Is there a way I can import all my wordpress posts
into it? Any help would be really appreciated!
Roof-mounted solar panels are basically self-cleaning, http://xn--80aapjajbcgfrddo7b.xn--p1ai/2020/07/14/privet-mir/ as rainfall may help clean the dust off the system.
Браво, эта отличная фраза придется как раз кстати
In all probability you’ve found that you’re paying too much for car insurance as it https://lacrossegoalieforum.com/2020/05/07/hello-world/ is. Though it might cost you extra money at first, over the course of a yr, you might save quite a couple of hundred bucks.
http://mexpharmacy.sbs/# mexico drug stores pharmacies
Демонтаж стен Москва
Демонтаж стен Москва
So the pound would have to be modified into dollars, https://velixe.fr/index.php?post/2020/06/08/Le-Colombis-et-les-Demoiselles-Coiff%C3%A9es-le-8-juin-2020 and then these dollars are then changed into yen.
доставка бетона миксером в москве
If you want to understand why so many people love this game, this beginner’s guide to the rules and the basics of poker
is all you need. The site also offers excellent customer support
with staff of helpful and knowledgeable staff who are always on hand to assist you with any concerns or queries you may need to
address. If you are a family member or friend that is struggling with gambling, you can get
support from a gambling counsellor. It’s a healthy pastime to spend time with family and friends, however, it shouldn’t interfere with the workplace.
But the lives of a person as well as his family members will be affected if
the person he or she attempts to hide his or her problem.
The result is the increased number of divorces as
well as homelessness and bankruptcy. A lot of people have reported having to
quit their job as a result of gambling addiction. This can have a negative impact on the person’s
work as well as relationships and personal life.
Positive effects of gambling are reduced risks of crime, a rise in tourist activity,
as well as a reduction in gambling that is illegal. 먹튀검증커뮤니티 It is essential to be aware of
the negative effects of gambling addiction on a person.The
person may attempt to reduce their gambling or hide it.
Additionally, a person with a gambling problem has less patience and is more likely
to gamble frequently. Additionally, they could have damaged their relationships.
They are machine washable and dryable, so you never have to worry
about them holding up in the wash. The best way to ensure you are playing at legitimate real-money online casinos is to stick to operators that
are licensed within your state or country.
Here, we’ll analyze and contrast two types of casinos so that you are able
to make an informed choice about which one to play at.
While all of the different poker variants play with unique rules, the fundamentals of betting, bluffing, common terms, and poker
hand rankings apply to nearly all varieties of the game.
From here and until the the whole hand is completed, the player in the small blind will start the action.The term “flopping a monster”
means that the flop fits your hand perfectly.
To be in someone’s “black books” means to be on bad
terms with them. In the event that any of the relevant information has changed (for example, the Player Contact Information), the Intending Player will be solely responsible for updating such information and complying with the terms and conditions of this Agreement which are then in effect.
In addition, the site also has high security safeguards in place to guard your
personal and financial information. Their customer service is
excellent, payouts and software downloads are
fast and efficient, and no one can’t fault their integrity or the security of the online casino.
Their customer support representatives are available 24/7 via live chat and email.
And speaking of support, make sure your bed frame is sturdy enough to
support not only the mattress and box spring, but the maximum
occupancy of people and pets in your household.Note that one or two factors are enough to say ‘no’ to such a project and avoid registering
on its website. Both have their own unique pros and consthat could make it difficult to determine which one is best for you.
That’s why a problem gambler is likely to try to conceal the fact that they have a problem with
gambling, to enable them to make better decisions later on. In the long run the gambler could begin to stop engaging in the activities other than gambling.
A gambler should invest the money that they would have invested in different goals.
It could be used to replace goals that are long-term.
Let’s start by looking at Land-based casinos; these are the most
traditional choice and are found in cities and towns
across the globe. It has been found that gambling can weaken commitments to intimate relationships.
Negative effects can lead to more crime and neglect.
There are many negative effects associated with gambling.
Whatever the negative effects of gambling are important to understand
how they affect a person’s lives and the inevitable results.
While it’s not likely to cause issues in relationships or affect work, it can make it difficult for individuals to concentrate on other aspects of their lives.
Feel free to visit my web site vavada официальный вход
We only discuss so much about our gaming library because it’s one of the crucial impressive within the vavada trade.
Браво, фантастика ))))
You need professionals who are masters of this https://coastalkustoms.com/shop/cushion-covers-satin-style/ craft. There are a number of options on the subject of having your home windows tinted.
2023年的FIBA世界盃籃球賽(英語:2023 FIBA Basketball World Cup)是第19次舉行的男子籃球大賽,且現在每4年舉行一次。正式比賽於 2023/8/25 ~ 9/10 舉行。這次比賽是在2019年新規則實施後的第二次。最好的球隊將有機會參加2024年在法國巴黎的奧運賽事。而歐洲和美洲的前2名,以及亞洲、大洋洲、非洲的冠軍,還有奧運主辦國法國,總共8支隊伍將獲得這個機會。
在2023年2月20日FIBA世界盃籃球亞太區資格賽的第六階段已經完賽!雖然台灣隊未能參賽,但其他國家選手的精彩表現絕對值得關注。本文將為您提供FIBA籃球世界盃賽程資訊,以及可以收看直播和轉播的線上平台,希望您不要錯過!
主辦國家 : 菲律賓、印尼、日本
正式比賽 : 2023年8月25日–2023年9月10日
參賽隊伍 : 共有32隊
比賽場館 : 菲律賓體育館、阿拉內塔體育館、亞洲購物中心體育館、印尼體育館、沖繩體育館
?Que diferencia a las tarjetas de Gloria virtuales Pase que ofrece Caporaso & Partners con https://universalscience.proboards.com/thread/563/tarjeta-de-stico-para-criptomoneda?page=1&scrollTo=1217 las otras tradicionales?
Thanks, A lot of material.
Я подумал и удалил сообщение
потом активации неполного возврата необходимая сумма переставать водиться для премиальный спецсчет, https://asten-a.ru в чем дело? дальнейшие ставки засчитываются во отыгрыше.
Medicament prescribing information. Drug Class.
generic singulair
Best trends of drugs. Get here.
buy medicines online in india: buy medicines online in india – top 10 online pharmacy in india
世界盃
2023年的FIBA世界盃籃球賽(英語:2023 FIBA Basketball World Cup)是第19次舉行的男子籃球大賽,且現在每4年舉行一次。正式比賽於 2023/8/25 ~ 9/10 舉行。這次比賽是在2019年新規則實施後的第二次。最好的球隊將有機會參加2024年在法國巴黎的奧運賽事。而歐洲和美洲的前2名,以及亞洲、大洋洲、非洲的冠軍,還有奧運主辦國法國,總共8支隊伍將獲得這個機會。
在2023年2月20日FIBA世界盃籃球亞太區資格賽的第六階段已經完賽!雖然台灣隊未能參賽,但其他國家選手的精彩表現絕對值得關注。本文將為您提供FIBA籃球世界盃賽程資訊,以及可以收看直播和轉播的線上平台,希望您不要錯過!
主辦國家 : 菲律賓、印尼、日本
正式比賽 : 2023年8月25日–2023年9月10日
參賽隊伍 : 共有32隊
比賽場館 : 菲律賓體育館、阿拉內塔體育館、亞洲購物中心體育館、印尼體育館、沖繩體育館
Here is the sports nowina app for you – Follow the biggest event of the year with Every prediction from this app Mobil Bahis Sports is i result of tudziez statistical algorithmic analysis using i database with more than 150000 results Mobil https://yoga.wiki/index.php?title=Balon_Kahraman%C4%B1_Oyunu_Oyna_-_Kral_Oyun_Nas%C4%B1l_Oynan%C4%B1r.
Medicines information. Cautions.
xenical tablets
All information about drugs. Get information now.
I have been browsing online greater than 3 hours these days, yet I never
found any interesting article like yours. It is beautiful value sufficient for me.
In my opinion, if all webmasters and bloggers made excellent content as you probably
did, the web will probably be much more useful than ever before.
Also visit my blog post … lowest rates
Meds information. Generic Name.
flagyl
Best what you want to know about meds. Read here.
по сим последовали заволакивание собственного журнальчика и еще всё вяще опас отзывы да статьи обо незамысловатости http://wiki.why42.ru/index.php?title=дэдди номеров.
Поздравляю, эта великолепная мысль придется как раз кстати
Do you understand leather-based jacket for men and women however not shrewdness to mix together together http://test-izumi.com/?p=1 with your outfit?
http://indiamedicine.world/# Online medicine home delivery
Medicines information. Long-Term Effects.
can i order cialis soft
Actual about medicine. Read information here.
Turning $ten,000 into $14,048in just 4 months
is ann investment return of 40.48%.
My homepage :: 토토사이트 추천
If you have ever been toed that something is just also nice to be true, https://sportowagdynia.eu/index.php/2021/11/27/dwa-mecze-w-gdyni-przed-arka/ then it seemingly is.
Мы подсобим каждому, https://www.akslicey1.ru/forum/messages/forum1/topic1467/message1945/?result=new который обратится к нам. в интересах нас настоящее турбовинтовой норматив (а) также что-что особо стоит обратить внимание на то – благородная качество доверия то есть ко нам.
Это мне скучно.
в течение отрасли “Промо” адепты обслуживания онлайн игорный дом подготовили премиальные пакеты. 3. Программы лояльности. Применяйте инициативные промокоды а также выкапывайте новоиспеченные комбинации в недотка, Дэдди казино дневалить углублять возможности возьми счастливый конец.
Drug information. Cautions.
priligy
Everything information about drugs. Read now.
Nicely put. With thanks.
It is simply that Newest Porn added numerous stuff here which have issues as a substitute of focusing what it might probably take management http://dentalclinicingwalior.com/index.php/component/k2/item/3 of.
Meds information. Brand names.
maxalt
Everything what you want to know about drugs. Get here.
I definitely adore your writing style; it’s therefore engaging.
This is one of the very best articles I’ve read through in an although.
Many thanks for sharing!
My page – lowest car insurance rates
Have you ever considered about including a little bit more than just your articles?
I mean, what you say is important and all. But imagine if you
added some great images or videos to give your
posts more, “pop”! Your content is excellent but with pics and video clips, this site could certainly be
one of the very best in its niche. Excellent blog!
на популярность водонагревателей интегрированы таковые модификации пруд: Ariston Abs Velis Evo Power 80 D, Round 100 VMR, https://stud.ukraine7.com/t661-topic#2488 Atlantic Steatite Cube Slim VM 50 S3 C 1500W. Они быть несхожими важнецкой производительностью равно экономным употреблением электричестве.
Medicament prescribing information. Long-Term Effects.
xenical generic
All trends of medicine. Get here.
This look is a classic one that provides immediate glamour excellent for the summer season get https://bentoree.com/telegram-where-girlss-nudes-are-shared-with-out-consent/ together circuit. Or you possibly can go glam and channel Bianca Jagger at Studio 54 with sensuous fabrics like silk and velvet in a extra figure hugging model that is able to dance in.
Я извиняюсь, но, по-моему, Вы ошибаетесь. Предлагаю это обсудить. Пишите мне в PM.
The casinos lease the machines rather than owning https://fermer.blog/go-to-url/622/product/23036?slug=thepokies75australia.net them outright. It will be important that the machine comprises a high-quality RNG implementation.
It’s possible to win poker hands without holding the best hand by bluffing your opponents.
Even though it’s a good idea for beginners to be cautious,
you can’t win if you always check and fold when playing poker games online.
Craps requires a larger bankroll than most casino games.
It can help you to manage your bankroll if you follow
the rules without deviation, as you won’t
go chasing losses when on a bad streak. American Roulette is also known as the game of chance because the rules of the game depend on the luck of the draw.
American Tourister, Fjallraven Kanken, Herschel, Lapalette,
Mango, River Island, Samsonite, and Something
Borrowed. Now, it is quickly expanding its American profile and has chosen Iowa as
one of its North American proving grounds. Download the ZALORA App
now, to grab the best discounts and amazing deals.
Download the App now! There is a wide range of free online games available online, these
can be found at online casinos or you can download them via apps that can be found on the Play Store or the App Store.ZALORA brings in wide range of men’s fashionable clothes and other necessary lifestyle products
that helps to re-arrange perfectly the closet and also
increase personal grooming. Thus, you can be rest assured about the protection of your personal and financial
details. To find more information regarding ‘can I block ads’ on Facebook
and ‘how can I adjust my ad preferences’, please view this article
from their Help Center. All the information that is shared between the client and the website
is encrypted and is protected by high security protocols.
The products offered by Pomelo are of high quality and are available
at affordable rates. They offer clothes such
as Tops, Dresses, Bottoms, Outerwear, Jumpsuits, Sportswear, Denim and
Accessories like Shoes, Sunglasses, Jewelry, Bags, Hats and Hair, Alphabet Rings etc.
They provide various Pomelo Offers on these products from time to time to help the customers buy the
items at lesser rates. Keep an eye on sneakers and plimsolls, loafers and boat shoes, slip-ons, formal
boots, and sandals and flip flops, sport shoes, brogues and derbies from your
favorite brands ALDO, Converse, Frank Williams, Macbeth, New Balance,
Nike, Onitsuka Tiger, Sperry Top-Sider, Timberland, and Vans.
Explore the whole range of sporty accessories and clothes from Asics,
Fbt, Li-Ning, Lonsdale, New Balance, Nike, Puma, Reebok, Rip Curl, and ZALORA SPORT.You can get your perfect grooming kits from SK-II and Skin Inc and varied range of& skin care, hair care,
and fragrance products and you can also buy gift sets for someone special as
well. ZALORA has products from brands like Topshop, Mango, Herschel,
Aido, Skin INC etc. Make use of the Zalora discount and promo code while buying
the high quality and trendy fashion items from ZALORA. You can return the product within 365 days
from the date of receipt of the products. All the products provide them are of high quality and are
checked thoroughly before they are delivered to you.
Apart from offering quality clothing and Accessories, they also provide various Pomelo Promo Codes to their customers.
Their goal is to make your life better by providing
you quality Clothes and Accessories. Here at ZALORA, assembling any attire
with the perfect combination of clothes, accessories and shoes, beauty and
sport, watches, bags from the top-rated brands becomes easier.Get in style with the trendy
pair of footwear like the Flats, Heels, Sandals, Wedges, Slip-Ons, Boots, Sneakers,
Flip Flops, Sports Shoes, Shoes Accessories and many more to
complete your attire. They provide Tops, Bottoms, Dresses, Jumpsuits,
Outerwear, Sportswear, Shoes, Jewelry, Hats and Hair, Sunglasses, Denim,
Bags, Alphabet Rings etc. For the ease of the customers, they provide easy
returns, fast delivery and various payment options.
Seize the trendy glasses, jewellery, belts, sunglasses,
scarves and shawls, technology, hair accessories, stationery, gloves, hats and caps,
and many more accessories from top brands like
ALDO, Mango, Ray-Ban, River Island, Salt Korea, Something
Borrowed, Sunnies Studios, TOPSHOP, Vogue and in-house ZALORA fashionable
accessories. Some of the best international sellers include Dorothy Perkins, Factorie, Finery London,
Mango, New Look, River Island, Something
Borrowed, TOPSHOP, Warehouse, Zalia and homemade ZALORA wears.
You can also buy analogue, sports, casual watches, chronograph watches,
luxury watches, and many more from Adidas, Casio, Daniel Wellington, Something Borrowed, Esprit, Fossil, James McCabe, Komono, Swiss Eagle and brand ZALORA.
Match your dress with branded watches from top brands such as Adidas, AVI-8, Braun, Casio, Daniel Wellington,
Diesel, Fjord, Fossil, James McCabe, and Klaus Kobec.
Check out my web page :: бурмлада
For players that are looking specifically for somewhere to play poker, check
out our Poker Rooms section. Aussies can choose to play straight from the browser or download an online casino app onto their smartphone or
tablet. There are perfectly legal Web sites like CardCash and Cardpool where you
can buy and sell gift cards. Once you’ve collected your treasure, you can either spend it as is —
and risk dirty looks from cashiers when you buy $20 of groceries with nickels — or convert it
into cash. If you can sell each bottle for $1, you’re looking at a quick $17 profit
in maybe an hour. Lu, Xin. “How to Sell Your Hair for Cash.” Wisebread.
Bonander, Ross. “How To: Sell Your Body for Cash.” Askmen (Sept.
Lipka, Mitch. “How to Turn Loose Change into Cash.” Daily Finance.
That’s when one of us geniuses remembered the change jar.
And they’ll send you the money in one or two days after receiving your card in the mail.
The casino strikes a good balance between the glitz and glamour of
Vegas, and a quiet enjoyable night at home playing your favourite games for money.Yes, and there are even some fantastic casino bonuses which are exclusive to those playing on a mobile device.
Statisticians have shown, for example, that if you spend all day
playing roulette, you will walk away with an average of 5.26 percent less money than when you started.
By one estimate, the average U.S. For example, 3♣ 7♣ 8♣ Q♠ A♠ and 3♦ 7♣ 8♦ Q♥ A♥ are
not identical hands when just ignoring suit assignments because one hand has three
suits, while the other hand has only two-that difference could affect
the relative value of each hand when there are more cards to come.
The values given for Probability, Cumulative probability, and
Odds are rounded off for simplicity; the Distinct hands and Frequency values are exact.
Bettors also may wager that the two hands will finish with
an equal number of points. Prairie State bettors have access to mobile sports betting and desktop platforms,
and are able to register remotely again rather than in-person as
of March 5, 2022! Discover the best Bitcoin casinos for 2022!What is
the best online casino for real money? Like we said, there
all kinds of legitimate motivations for making money fast.
While typical poker games award the pot to the highest hand as per the
standard ranking of poker hands, there are variations where the best hand,
and thus the hand awarded the pot, is the lowest-ranked hand
instead. All your orders are secured so that no one finds out
that you have decided to resort to EssayService.
Let’s look at these interesting facts to find out. Just find the coupon you
want, print it out, and bring it when shopping. Instead of
having 20 bucks, you’re stuck with a useless piece of plastic, unless you can find someone who will buy it from you.
There are no numbers to pick, and the prizes are predetermined before you even buy your ticket.
Submit a Certificate of Occupancy for your building showing
that the premises are suitable to operate as a bingo hall.
Before starting a bingo hall, you will have to obtain a license from your Department of Consumer Affairs.True, most U.S.
cities have laws on the books that make it less than totally legal to sell bottled water without
a vendor’s permit and health department license. You must show that the
building complies with all fire and health regulations.
Scrap yards and metal recyclers will pay by the pound for new, used or
extremely used items made from ferrous materials like
steel and iron, or less common non-ferrous metals like aluminum, brass and copper.
Didorosi, Andy. “How to Sell Scrap Metal for Money.” Popular Mechanics
(Sept. Derousseau, Ryan. “The Best Bets at the Casino.” June
14, 2007 (Sept. We aren’t coupon aggregators, but we do believe in getting the best prices because, like
you, we used to be compulsive shoppers. That’s
because, as part of the arts world as well, the entrepreneurs
of this sector are also artists. The kiosks are equipped with
software to recognize makes and models for more than 2,000 devices, and
they can also detect damage and flaws. If you have a Costco or Sam’s Club card, you can get them for even less in bulk.
my web page … bitcoin kazino
Medicine information. Effects of Drug Abuse.
buy proscar
Actual news about medication. Get now.
These used a number of features to ensure the payout was controlled within the limits of the gambling legislation. Each machine has a table that
lists the number of credits the player will receive if the symbols listed on the pay table line
up on the pay line of the machine. A card dealt off the table must play and
it is treated as an exposed card. In the Education section, players will find rules for almost all online casino games,
as well as tutorials on how to play many of them.
They have limited value to the player, because usually a machine will have 8 to 12 different possible programs with varying
payouts. As there are so many combinations possible with five reels, manufacturers do not need to weight the
payout symbols (although some may still do so).
It is possible to profit from a podcast, but it isn’t easy.One reason that the slot
machine is so profitable to a casino is that the
player must play the high house edge and high payout wagers along with the low house edge and low payout wagers.
Video slot machines typically encourage the player to play multiple “lines”: rather than simply taking the middle of the three symbols displayed on each reel, a
line could go from top left to the bottom right or any other pattern specified by the manufacturer.
How Can I Play CircleMUD? Among these options, you can find
many popular methods that you use in everyday life
such as debit/credit cards and electronic wallets.
Video slot machines do not use mechanical reels, but use
graphical reels on a computerized display. As there are no mechanical constraints on the design of video slot machines, games often use at least five reels, and may also use non-standard layouts.
A scatter is a pay combination based on occurrences of a designated
symbol landing anywhere on the reels, rather than falling in sequence on the same payline.
Post river- This is the final betting round after
which the showdown takes place where the combination of best 5 cards (dealt hand and community cards)
is the winning hand.The flop – The dealer burns a card, and then deals three community cards
face up. Fred only wants to sell three of the cars. A scatter pay usually requires a minimum of three symbols to land, and the
machine may offer increased prizes or jackpots depending on the number that land.
Changing the payout percentage after a slot machine has been placed on the gaming floor requires
a physical swap of the software or firmware, which is usually stored on an EPROM
but may be loaded onto non-volatile random access memory (NVRAM)
or even stored on CD-ROM or DVD, depending on the capabilities of the machine and the applicable regulations.
This means that the result varies depending on exactly when the game is played.
The result is that there is not really such a thing as a high payback type of machine, since every machine potentially
has multiple settings. BonusBonusBonus has taken a look around the
online poker “jungle” and can introduce you to high class poker rooms.
But you can prevent this from happening by relying on credible reviews and lists of
some of the best sites in the industry, like what we publish on this site.The blue Kohl’s Cash can be used
just like the regular kind, with the usual exclusions.
They have various such rewards programs mentioned on their websites which users can accordingly choose from according to their convenience and availability.
Ontario, Quebec, British Columbia and Alberta have the highest income from gambling.
Whilst, those operators who wish to advertise their services in England, Wales, or Scotland,
but are based outside the country, have to obtain a licence from the
Gambling Commission following the passage of the Gambling (Licensing and Advertising) Act 2014.
The 2014 Act changed the licensing requirements so that
any company wishing to advertise gambling and take bets from consumers in England, Wales, or Scotland must hold a licence issued by the Gambling Commission. These
regulations are independent of any other regulatory framework, such as
the Bank Secrecy Act or consumer protection regulations.
Scatters are frequently used to trigger bonus games,
such as free spins (with the number of spins multiplying based on the number of scatter
symbols that land). The North Pacific Ocean or NPAC by surfers is that northern part of the Pacific Ocean where huge storms
cause great swells, and land on the coastlines of
surf-friendly beaches found in the area.
Have a look at my page … Free Pokies aristocrat
mexican online pharmacies prescription drugs: mexican mail order pharmacies – buying prescription drugs in mexico online
Today, I went to the beach front with my kids. I found a
sea shell and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.”
She put the shell to her ear and screamed. There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this
is entirely off topic but I had to tell someone!
Medicament information. Effects of Drug Abuse.
cytotec brand name
Best trends of pills. Read now.
Nicely put, Cheers.
Medicine information sheet. Effects of Drug Abuse.
norpace cost
Some what you want to know about medicines. Read information now.
http://mexpharmacy.sbs/# mexico drug stores pharmacies
FIBA
2023年的FIBA世界盃籃球賽(英語:2023 FIBA Basketball World Cup)是第19次舉行的男子籃球大賽,且現在每4年舉行一次。正式比賽於 2023/8/25 ~ 9/10 舉行。這次比賽是在2019年新規則實施後的第二次。最好的球隊將有機會參加2024年在法國巴黎的奧運賽事。而歐洲和美洲的前2名,以及亞洲、大洋洲、非洲的冠軍,還有奧運主辦國法國,總共8支隊伍將獲得這個機會。
在2023年2月20日FIBA世界盃籃球亞太區資格賽的第六階段已經完賽!雖然台灣隊未能參賽,但其他國家選手的精彩表現絕對值得關注。本文將為您提供FIBA籃球世界盃賽程資訊,以及可以收看直播和轉播的線上平台,希望您不要錯過!
主辦國家 : 菲律賓、印尼、日本
正式比賽 : 2023年8月25日–2023年9月10日
參賽隊伍 : 共有32隊
比賽場館 : 菲律賓體育館、阿拉內塔體育館、亞洲購物中心體育館、印尼體育館、沖繩體育館
https://zamena-ventsov-doma.ru
Drug information sheet. Long-Term Effects.
rx fluoxetine
All what you want to know about pills. Read information here.
супер,давно так не смеялс
The remainder is granted in 5 installments of 40. Casino aficionados could have 24 hours to clear the 50x wagering requirement tied to each batch of spins and unlock the winnings associated with the https://apocaliptico.com.br/index.php/component/k2/item/175-pedro-e-seu-machado bonus.
Permainan permainan cq9 ialah pilihan bagus dan familier. Ini ialah opsi paling baik di spot Asia ingat sebetulnya koleksi permainan bertopik Asian lumayan banyak memimpin dibanding lainnya. Akan tetapi meskipun demikianlah feature serta servis dan sarananya terlampau lengkap. Berjudi betting https://monelik.ru/user/FlorDolling38/ dana bersama Joker Gaming memungkinkannya Kamu bisa beberapa kemenangan.
TRON: The TRON network has become known as the “Las Vegas of blockchain”
because of its success in fostering a thriving dApp gambling market.
All operators must adhere to these rules if they wish
to operate in the British market. Operators are on a sliding scale for a three-year
license. Mountainside Medical Equipment Coupon Code
are among the most popular marketing or marketing technique utilized by sellers and producers
to bring in new consumers. Mountainside Medical Equipment Coupon Code &
Mountainside Medical Equipment Coupon Codes offers
you a good offer when you order food or other goods
from the dining establishments or shops signed
up with that particular website. Then, have
a look at this offer. Then, Cobone is the best place for you.
Cobone coupon code is not required to checkout page. No Cobone promo
code Riyadh is needed to avail super saving offer.
Here you can get all new working promo code, discount like 15%, 20% &
50%. You have to use all active promo codes and checkout the sale.
American Eagle Coupons , Buy one , Get One 50% Off .
Microless online store is offering upto 50% off on branded mobile phones & accessories items.Microless Uae promotion code is not required at checkout page.
Microless Offers – This amazing online store is offering upto 55% Off on electronics items only at Microless Uae.
Computers/Electronics offers: Buy Computer And Electronics Accessories at lowest rate from Banggood, Geekbuying, Zapals And More.
Looking to buy mobile phone & accessories? Looking for the best deals and offers in Riyadh?
On the days when you have promo codes going on, you might be pleasantly surprised
to note good deals on shipping. Checkout all exciting footwear deals for men & women online at Walk London Shoes KSA
and avail free delivery facility on your favourite pair
of shoes when you spend over £30. Get free delivery on orders above AED99 only at Mothercare.
HottPerfume Coupons: Shop Now & Get UpTo 70% Off Fragrances Plus FREE SHIPPING.
Health & Green: Get health products, diet products from WonderSlim, Rocky Mountain Oils, Diet Direct etc.
at Big discounts. Over the past few decades, health professionals have
discussed and debated the definition of various terms associated with
problem gambling.Save up to 10% on your weekly shopping of branded
collection of supplements, vitamins & health products
online only at iHerb KSA. Voucher used to be utilized just
in files but with the growing appeal of online shopping codes likewise
occur to promote not just online expense savings nevertheless likewise numerous online products.
A site can provide promotional codes for novice visitors, during unique events like
nationwide celebrations and other days so that
you can conserve an excellent amount on your purchases. You can find a therapist in your area who specializes in addiction. While only Utah and Hawaii ban all forms of gambling outright, it’s important to check your state and local
laws to find out what types of gambling are legal and illegal in your area.
Remember to paste the code when you check out.
Employees will check IDs to confirm that customers qualify for the senior discount.This discount is valid on all courses but for limited period.
Amongst the benefits of making use of Discount
Mountainside Medical Equipment Coupon Codes
aside from the discount rate on the item itself is discounted or often even complimentary shipping.
WonderSlim Coupon 150% Refund Guarantee within 60 days of purchase!
150% Refund Guarantee within 60 days of purchase! Coupon CodeTake 20% off Boiron Products Purchase of $20 or More.
HottPerfume Online in store coupon. Sign up for mobile alerts
to be notified the latest arrivals as well as new store openings,
or more fun events. TMART Online in store coupon. Details: Tap the offer
to copy the coupon code. Details: No coupon code is needed.
New American Eagle Promo Code July 2023 – Hey Top! Food offers:
Promo Codes And Coupons to order food from Ejuices,
Lovewithfood, Misthub, Perky Jerky. No need to use
Eduonix promo codes. How to Use Coupons Codes, Promo Codes,
Discount Codes At RoutineDeals! Find the discount on your special days like birthday, anniversary and many more
occasions. Avail up to 80% discount on your bookings.
Also visit my web site – Sms Laen
Medicine information. What side effects can this medication cause?
provigil
Best trends of medication. Get information here.
Para peminat betting Game Slot online pasti tidak bakal asing apabila mendengar Namanya provaider Pragmatic Play. Bagaimana tidak, Pragmatic Play ialah company developer game pertaruhan https://mrcoinhodler.com/forum/profile/stevenratten85/ gacor dipercaya yang telah mempunyai ratusan permainan slot sejak pertama kali tampil beroprasi tahun 2008. Pragmatic Play tidak hanya sekedar merilis banyak game slot saja, tapi Setangah besar produk permainan slot dari provaider terpercaya yang satu ini juga memberikan penawaran besarnya potensi kemenangan berkat nilai Return to Pemain ataupun RTP permainan slot yang cukup tinggi.
Отличный сайт! Всем рекомендую!Matangi Devi
FIBA
2023年的FIBA世界盃籃球賽(英語:2023 FIBA Basketball World Cup)是第19次舉行的男子籃球大賽,且現在每4年舉行一次。正式比賽於 2023/8/25 ~ 9/10 舉行。這次比賽是在2019年新規則實施後的第二次。最好的球隊將有機會參加2024年在法國巴黎的奧運賽事。而歐洲和美洲的前2名,以及亞洲、大洋洲、非洲的冠軍,還有奧運主辦國法國,總共8支隊伍將獲得這個機會。
在2023年2月20日FIBA世界盃籃球亞太區資格賽的第六階段已經完賽!雖然台灣隊未能參賽,但其他國家選手的精彩表現絕對值得關注。本文將為您提供FIBA籃球世界盃賽程資訊,以及可以收看直播和轉播的線上平台,希望您不要錯過!
主辦國家 : 菲律賓、印尼、日本
正式比賽 : 2023年8月25日–2023年9月10日
參賽隊伍 : 共有32隊
比賽場館 : 菲律賓體育館、阿拉內塔體育館、亞洲購物中心體育館、印尼體育館、沖繩體育館
Medicament information sheet. What side effects?
how to buy silagra
All what you want to know about pills. Get information now.
Device purchased on the Bring it Back program must be returned in good working condition or
you will be responsible for the difference between the Bring-It-Back program amount and the lower trade-in value for
a device that is not in good working condition. In order to get an American Eagle birthday coupon, you
must be part of the AEO Real Rewards loyalty program.
Level 2 members get free shipping on orders over $50,
and Level 1 members have to spend $75 to get free shipping.
ASOS coupon code to get free express shipping on your online
order! For example, if you sign up online for
a trip by a travel agency, you can get promo code for 20 % reduction of the price of the trip.
Sign up for Real Rewards. Join Real Rewards to score
a 15% off coupon on your birthday. When are American Eagle birthday coupons sent?
The $5 Kohl’s Cash reward is sent to customers through the order confirmation email.
Join Kohl’s email list and enjoy the benefits! Start off by joining the email list using the drop-down box on the home page.It will be delivered to your email inbox
at the beginning of your birthday month. Good support in email and comment.
Creative professionals should look into Vimeo Strandard, which gives you: branded videos,
custom CTAs and lead capture forms, VIP
support (emails answered within one hour), multiple device capabilities for your videos,
2TB bandwidth per month, HD uploading, the ability
to send large video files, and make money off of your videos, engagement
stats, and so much more. The promotion codes feature offers expiry dates of up to six
months and support for up to 20MM individual
codes per list. To get a 15% off coupon for Kohl’s
subscribe to their mailing list. For a full
list of the active Aerie promo codes, you can visit
our Aerie page. AE occasionally runs free shipping promotions, so make sure to see if there are any offers active.
There is a choice you can make and strike a chord for freedom
by choosing Verizon FiOS.Once in a while,
you can also find a Verizon Wireless promo code that works
for Verizon gift cards as well. Additionally, percentage-off promo codes can be used in conjunction with
exclusive Kohl’s cardholder promo codes and free shipping
offers. Click to sign up (for free!) to receive 10% student discount ASOS
coupon codes now! When you sign up to claim the DraftKings Promo Code,
you get $150 in bonus bets instantly when you bet $5 on Open Championship betting markets today.
Sign up for texts and browse exclusive offers from the Los Angeles Times to
save even more on your next order. ”, or even “Good for the next 4 hours!
For a limited time, save even more when you use
these ASOS promo codes happening now. Several webmasters are now actually using online
codes with their highest potential. Most of the new launches are updated versions of the existing packages while some are purely new, at
your disposal. We just updated the official communication mail.
You will be redirected to the official store.
Traditionally, most people will go directly to their car
rental company of choice. If you are a contractor or
work in a similar construction field, you can cut costs and unlock extra savings with a Tractor
Supply Company Business Credit Card.Can I use American Eagle coupons in-store?
How long does the American Eagle birthday discount last?
4. When you click through an Amazon discount code, it will be automatically copied to
your clipboard, so paste it at checkout, and
your savings will appear instantly! Check out our Amazon Prime Day shopping guide for a roundup of the best bargains on Amazon devices, beauty, fashion, home and tech products.
The reason is pretty obvious-if you are using this Microsoft Office 365 Home Renewal Promo Code at the
early hours, you will surely be getting your desired products at much discounted
rate. This SuperBook Ohio promo code will get you a deposit bonus up to $250.
Shop above $200 and get free shipping at Crop King Seeds.
Level 3 members get free shipping on all orders.
Plus, get free shipping! To get this discount, customers need to present proof of military
status, such as a military ID, Form DD 214, or a state-issued ID indicating veteran status.
How to get 15% off American Eagle? Can I stack coupons at American Eagle?
Is it possible to stack Kohl’s discount codes? Does Kohl’s offer a military discount?
Here is my web-site … Online Kazino
Браво, вас посетила просто блестящая мысль
It’s slightly bit insulting, I believe, https://zancotti.com/suck/ to those of us who served,’ he said.
Medication information sheet. Drug Class.
buy generic norvasc
Actual about medicine. Get now.
Hi, I do believe this is an excellent blog.
I stumbledupon it 😉 I may come back once again since
I bookmarked it. Money and freedom is the best way to change, may you be rich and continue to
guide other people.
Отличный сайт! Всем рекомендую!MATANGI DEVI SINGER
Medicines prescribing information. Long-Term Effects.
cephalexin
Some news about medicament. Get here.
Medicament prescribing information. Generic Name.
order maxalt
Some trends of drugs. Read now.
buying prescription drugs in mexico: buying prescription drugs in mexico online – buying prescription drugs in mexico
cost of generic aurogra tablets
http://certifiedcanadapharm.store/# canadian pharmacy tampa
Medicament information for patients. Drug Class.
can i get priligy
Everything trends of drug. Get now.
Medicament information leaflet. What side effects?
generic sildigra
Actual information about drug. Read here.
Работа в Кемерово
The odds of winning on these scratch cards will vary from internet sitye to web page.
Also vixit myy site :: http://postmaster.jetsystem21c.com/bbs/board.php?bo_table=free&wr_id=13127
честно впадлу..
Актеры: Эдвард Нортон, Гугу Эмбата-Ро, Алек Болдуин, Уиллем Дефо, частное сыскное агентство стоимость Брюс Уиллис… Французская занятная притворство в рассуждении похождениях безнадежного бабника Ники Ларсона.
Drug information sheet. What side effects can this medication cause?
viagra soft
Actual what you want to know about drugs. Read information now.
Antabuse
Drug prescribing information. What side effects can this medication cause?
female viagra brand name
Best news about medicine. Get now.
100% клево! Смотрю!
Можно сметь чуть аудиотекст, http://communitystalkers.80lvl.ru/viewtopic.php?f=12&t=1582 позволительно не разрешить не менее первоначальную главу дипломной занятия. Покупка диплома воспрещена держи местность Российской Федерации а также гонится по праву.
Отличный сайт! Всем рекомендую![url=https://matangidevi.bandcamp.com/album/shakti-ma]Shakti ma[/url]
та нуууу….. вылаживайте свежое плз ))
Eliquid inside the cartridges will value you more. So you probably have bought the electronic cigarette let’s check out some of the perfect thrilling flavors that goes along with your digital https://www.farovilan.com/exposicion-de-pintura-de-paisaxes-fachos-e-barcos/ cigarettes.
Pills information leaflet. Brand names.
cipro
Actual news about medicament. Get information now.
Новости информационных технологий на Смоленском портале. Архив новостей. двенадцать недель назад. 1 страница
Drug prescribing information. Cautions.
generic zithromax
All trends of medicine. Get information here.
хачу такую
Перекись водорода нам и стар и млад пользующийся http://leffehuae.com/index.php/component/k2/item/3-life-is-a-series-of-natural-changes популярностью. Флакон никак не обязан быть нескрываемым нескончаемо. Главное выполоскать засим кожура линзы, ибо через фрагментов соли предстанут антипатичные чувства.
prednisone for sale
Tetracycline drug interactions
Drug information for patients. What side effects can this medication cause?
nolvadex
Best what you want to know about meds. Get here.
По моему мнению Вы ошибаетесь. Могу это доказать. Пишите мне в PM, пообщаемся.
Швидше за все, http://tbump.edu.vn/index.php?language=vi&nv=statistics&nvvithemever=t&nv_redirect=aHR0cDovL3d3dy50ZXJyYXdvbWFuLnVhL3VhL3RvZGF5L3lha19wb2NoYXRpX3ZjaGl0aV9hbmdsaXlza3VfbW92dS9jb21lbnRhcg== вам просто не підійшов метод навчання. Учні з нульовим рівнем також повинні боротися з вимовою.
Medication information leaflet. What side effects?
prozac brand name
All trends of drugs. Get information now.
finasteride purpose
Drug information sheet. Long-Term Effects.
priligy
Actual news about drug. Get now.
Бесподобное сообщение, мне интересно 🙂
Купівля аксесуара, що захищає очі від сонячних променів, актуальна в будь-який час року, http://veda.vedicthemes.com/biz/product/woo-ninja/ особливо – напередодні весняно-літнього сезону.
https://visia.com.ua/ru/glavnaya/
download sda steam authenticator
Весьма полезное сообщение
Будучи впевненим у навичках своїх працівників, ви можете також почати працювати з організаціями, http://noginsk-service.ru/forum/index.php?action=go;url=aHR0cDovL3d3dy50anN0cml6a292LmN6L3N0b2xuaS10ZW5pcy8yMi1ha3R1YWxpdGEtcGluZ3BvbmctMQ компаніями.
download sda
Steam Desktop Authenticator its a desktop emulator of the Steam authentication mobile application. The program helps to log in to steam without a mobile phone. There is support for automatic accept of trades and confirmation of steam transactions on the steam market.
steam mobile authenticator
sda steam
http://certifiedcanadapharm.store/# canadian drug pharmacy
sda steam
Steam Desktop Authenticator its a desktop emulator of the Steam authentication mobile application. The program helps to log in to steam without a mobile phone. There is support for automatic accept of trades and confirmation of steam transactions on the steam market.
Great site! I recommend it to everyone!Best PR Agency Dubai
Hello to every one, the contents existing at this
site are really remarkable for people experience, well, keep up the good work fellows.
canadian pharmacy review: trusted canadian pharmacy – my canadian pharmacy review
Even when gambling is no longer a part of your life, these problems will
still remain, so it’s important to address them. Most
online gambling sites subsequently changed their domain away
from a .com address. Signing up at one of the best sports betting sites is a simple process.
Generally, you’ll find sports betting sites
that take Bitcoin, Litecoin, Dash and Ethereum.
One is the ease with which gamblers can find each other online and share tactics.
Bad Habit – Gambling Bad Gambling Habits Gambling is a perfectly healthy hobby as long as gamblers are
still in control of when to stop. Many older gamblers are reluctant to reach out to their adult children if
they’ve gambled away their inheritance, but it’s never too late to make changes for the better.
Among the most susceptible games these days are blackjack and
poker variations like Ultimate Texas Hold ’Em, in which play is against the house rather than other gamblers.Many casino executives despise gamblers like Grosjean. But Grosjean knew that
shuffling machines are computer driven and therefore only as good
as they are programmed and used: Sometimes, in fact, the devices are surprisingly predictable.
The Firth is crossed by the Forth Road and Forth Rail Bridges, which are both built to be much
stronger than is necessary due to a prior Forth Bridge collapsing.
How much money would they be able to win? You
end up spending more buying sale items than you would have spending money any other time.
Now that you’re equipped with enough sportsbook information to get you started, choose the best
online sportsbook from our list above, and you’re
all set to bet on sports, entertainment, politics,
and more. You could find yourself at the receiving end of a crypto bonus since the best sportsbooks
offer special promos for those who use Bitcoin. Common advantage-play techniques include “hole carding,” in which sharp-eyed
players profit from careless dealers who unwittingly reveal tiny portions
of the cards; “shuffle tracking,” or memorizing strings of cards in order to predict when specific cards will be dealt
after they are next shuffled; and counting
systems that monitor already dealt cards
in order to estimate the value of those that remain in the deck.When Grosjean first reconnoitered the game, he saw that the 12 playing cards used to simulate a
pair of craps dice were being shuffled by a machine designed to
speed up play and randomize the order of the cards.
Grosjean discovered that he could see the identity and order
of at least three cards entering the machine, the bottom one held by
the dealer and the two that were exposed during game play.
One of the best side effects of Punch A Bunch is that
you can take out all of your aggression during a game.
Best sportsbook for bonuses: Caesars. Playing for real money at your chosen sportsbook
means deciding on a deposit option that you prefer. Most top
sportsbooks permit you to cash out your money the same way you funded your account, a different
option to collect your winnings will be required at some other sportsbooks.
Teams of advantage players – which usually require one person to bet and another to
spot dealers’ hole cards (those turned down and not supposed to be seen), track shuffles or count
cards – have become so prevalent that they often find themselves in the same casino,
at the same time, targeting the same game.“We had a blackjack game in Atlantic City with a weak dealer,” recalls Bobby Sanchez, known as the Bullet, a
frequent playing partner of Grosjean’s. The opportunity was in Shawnee, Okla.,
nearly 40 miles east of Oklahoma City. In 1995 there were more
than 2,000 big and medium-time bookies in the city and neighboring
towns, but since then the numbers have declined substantially to less than 300.
During the 2000s, the average monthly turnover has remained around Rs.
Just make sure you have your depositing info handy (more on that below) because once the sign-up process
is complete, you place your first bet. At the time, New Jersey could have allowed sports wagering if it had
acted within a year of the law’s effective date,
but chose not to. How long would they be allowed to play before
being asked to leave? Being run out of casinos is an occupational hazard for Grosjean,
a professional gambler who majored in applied math at Harvard and
briefly considered careers on Wall Street and in academia.
Another is the proliferation of books like Grosjean’s “Beyond Counting,”
which he published in 2000 and updated in 2009 as a self-published edition (though he claims that if he doesn’t know who you are, he won’t sell you a copy).
Look into my web blog Freespins
download sda
Steam Desktop Authenticator its a desktop emulator of the Steam authentication mobile application. The program helps to log in to steam without a mobile phone. There is support for automatic accept of trades and confirmation of steam transactions on the steam market.
今彩539:台灣最受歡迎的彩票遊戲
今彩539,作為台灣極受民眾喜愛的彩票遊戲,每次開獎都吸引著大量的彩民期待能夠中大獎。這款彩票遊戲的玩法簡單,玩家只需從01至39的號碼中選擇5個號碼進行投注。不僅如此,今彩539還有多種投注方式,如234星、全車、正號1-5等,讓玩家有更多的選擇和機會贏得獎金。
在《富遊娛樂城》這個平台上,彩民可以即時查詢今彩539的開獎號碼,不必再等待電視轉播或翻閱報紙。此外,該平台還提供了其他熱門彩票如三星彩、威力彩、大樂透的開獎資訊,真正做到一站式的彩票資訊查詢服務。
對於熱愛彩票的玩家來說,能夠即時知道開獎結果,無疑是一大福音。而今彩539,作為台灣最受歡迎的彩票遊戲,其魅力不僅僅在於高額的獎金,更在於那份期待和刺激,每當開獎的時刻,都讓人心跳加速,期待能夠成為下一位幸運的大獎得主。
彩票,一直以來都是人們夢想一夜致富的方式。在台灣,今彩539無疑是其中最受歡迎的彩票遊戲之一。每當開獎的日子,無數的彩民都期待著能夠中大獎,一夜之間成為百萬富翁。
今彩539的魅力何在?
今彩539的玩法相對簡單,玩家只需從01至39的號碼中選擇5個號碼進行投注。這種選號方式不僅簡單,而且中獎的機會也相對較高。而且,今彩539不僅有傳統的台灣彩券投注方式,還有線上投注的玩法,讓彩民可以根據自己的喜好選擇。
如何提高中獎的機會?
雖然彩票本身就是一種運氣遊戲,但是有經驗的彩民都知道,選擇合適的投注策略可以提高中獎的機會。例如,可以選擇參與合購,或者選擇一些熱門的號碼組合。此外,線上投注還提供了多種不同的玩法,如234星、全車、正號1-5等,彩民可以根據自己的喜好和策略選擇。
結語
今彩539,不僅是一種娛樂方式,更是許多人夢想致富的途徑。無論您是資深的彩民,還是剛接觸彩票的新手,都可以在今彩539中找到屬於自己的樂趣。不妨嘗試一下,也許下一個百萬富翁就是您!
539
今彩539:台灣最受歡迎的彩票遊戲
今彩539,作為台灣極受民眾喜愛的彩票遊戲,每次開獎都吸引著大量的彩民期待能夠中大獎。這款彩票遊戲的玩法簡單,玩家只需從01至39的號碼中選擇5個號碼進行投注。不僅如此,今彩539還有多種投注方式,如234星、全車、正號1-5等,讓玩家有更多的選擇和機會贏得獎金。
在《富遊娛樂城》這個平台上,彩民可以即時查詢今彩539的開獎號碼,不必再等待電視轉播或翻閱報紙。此外,該平台還提供了其他熱門彩票如三星彩、威力彩、大樂透的開獎資訊,真正做到一站式的彩票資訊查詢服務。
對於熱愛彩票的玩家來說,能夠即時知道開獎結果,無疑是一大福音。而今彩539,作為台灣最受歡迎的彩票遊戲,其魅力不僅僅在於高額的獎金,更在於那份期待和刺激,每當開獎的時刻,都讓人心跳加速,期待能夠成為下一位幸運的大獎得主。
彩票,一直以來都是人們夢想一夜致富的方式。在台灣,今彩539無疑是其中最受歡迎的彩票遊戲之一。每當開獎的日子,無數的彩民都期待著能夠中大獎,一夜之間成為百萬富翁。
今彩539的魅力何在?
今彩539的玩法相對簡單,玩家只需從01至39的號碼中選擇5個號碼進行投注。這種選號方式不僅簡單,而且中獎的機會也相對較高。而且,今彩539不僅有傳統的台灣彩券投注方式,還有線上投注的玩法,讓彩民可以根據自己的喜好選擇。
如何提高中獎的機會?
雖然彩票本身就是一種運氣遊戲,但是有經驗的彩民都知道,選擇合適的投注策略可以提高中獎的機會。例如,可以選擇參與合購,或者選擇一些熱門的號碼組合。此外,線上投注還提供了多種不同的玩法,如234星、全車、正號1-5等,彩民可以根據自己的喜好和策略選擇。
結語
今彩539,不僅是一種娛樂方式,更是許多人夢想致富的途徑。無論您是資深的彩民,還是剛接觸彩票的新手,都可以在今彩539中找到屬於自己的樂趣。不妨嘗試一下,也許下一個百萬富翁就是您!
I think this is among the most vital info for me.
And i’m glad reading your article. But wanna remark on some general things, The website style is wonderful, the
articles is really great : D. Good job, cheers
Демонтаж стен Москва
Демонтаж стен Москва
Демонтаж стен Москва
Демонтаж стен Москва
Drugs information sheet. Drug Class.
get cephalexin
Best information about meds. Read information now.
So, if you had a bet on beneath 2.5 rounds and thee bout ends in the 2nd minute
of the 3rd round, your bet would be settled as a winner.
Also visit my site: 토토사이트 순위
Pills information. What side effects can this medication cause?
avodart
Everything what you want to know about medicament. Read now.
https://martynovmaks4.nethouse.ru/posts/mexamoskvichka-ru-16913438761-kopiya-u0c
Medicines information sheet. Brand names.
effexor pill
Actual information about medicament. Get information here.
Great site! I recommend it to everyone!Luxury PR agency Dubai
На мой взгляд, это актуально, буду принимать участие в обсуждении. Вместе мы сможем прийти к правильному ответу.
краеугольный редактор сетного издания: колыбель в отношении.только. Учредитель сетевого издания: Администрация городского образования барабинск-сочи Анапа. с целью вебсайтов да страничек мережа Интернет вечна бойкая ссылка держи https://kutuan.cc/ администрации городского создания бристоль-Сочи Анапа.
Medicine information. Generic Name.
nexium pill
Best what you want to know about pills. Get information here.
Я пожалуй промолчу
After I masturbate, I can not get onerous again for hours. While guys may attempt their finest to seem confident and self-assured, https://vn-j.com.vn/san-pham/may-cat-cnc-plasma-procut-12/ a lot of them (if not all) have some deep-seated issues and anxieties about their penises.
Meds information for patients. Generic Name.
priligy sale
Best trends of drug. Read information here.
And with the shift, the women are difficult a culture of machismo that could open new pathways for future asylum seekers, neighborhood groups mentioned.
Look at my blog post … https://nonihasbunajaya.com:469/bbs/board.php?bo_table=free&wr_id=25270
Whoa loads of valuable knowledge!
Medicament information for patients. What side effects can this medication cause?
nexium
Some news about meds. Read now.
Drugs prescribing information. Short-Term Effects.
ampicillin
Best trends of drug. Read here.
Medicines information sheet. Long-Term Effects.
viagra medication
All trends of medicines. Read information now.
Drugs information sheet. Effects of Drug Abuse.
priligy for sale
All news about medication. Get here.
Medicines information sheet. Generic Name.
cialis buy
Best about medicine. Get now.
where to buy fluoxetine
Medicament information leaflet. Long-Term Effects.
zoloft for sale
Some trends of medicines. Get now.
what is cordarone used for
Надо глянуть полюбому!!!
Ректор Казанского правительственного энергетического института, https://blacksprutonion.shop/ депутат Государственного Совета РТ Эдвард Абдуллазянов дал портфели от конторскими приспособлениями 7 предстоящим первоклассникам Шеланговской средние учебные заведения.
Я знаю, как нужно поступить, пишите в личные
The authority said workers were due to go to the cost factors “to ensure the third party net tackle is covered https://hairsalon-savo.com/hello-world/ up”.
Great site! I recommend it to everyone!Celebrity PR Agency Dubai
ivermectin 500ml: ivermectin purchase – ivermectin over the counter
Meds information for patients. Short-Term Effects.
kamagra for sale
Everything what you want to know about medicament. Get information now.
Drug information leaflet. Short-Term Effects.
priligy
All trends of medicine. Get information here.
ashwagandha and thyroid
Medicines information leaflet. Brand names.
norvasc medication
Everything trends of meds. Read information now.
http://gabapentin.pro/# neurontin 204
Казино онлайн предоставляют современному клиенту эксклюзивную возможность окунуться в атмосферу
азартных игр без необходимости физического присутствия в казино.
Исходя из современным технологиям, игры в интернете наиболее приближены к реальности: качественная графика, реалистичные звуковые эффекты
и возможность игры с настоящими
дилерами формируют неповторимое ощущение пребывания в
реальном казино.
Тем не менее, выбирая онлайн-казино, стоит проявлять осмотрительность.
Рынок азартных игр в интернете полон
предложений, и не все из них
считаются честными и надежными.
Поэтому, перед тем как внести свои деньги и запустить игру,
следует тщательно изучить репутацию казино, отзывы других
игроков и наличие нужных лицензий.
Лишь так можно гарантировать себе безопасное и увлекательное времяпровождение в мире азартных игр
онлайн.
Feel free to visit my web page: pokerdom
Medication information sheet. Brand names.
eldepryl
Best what you want to know about medication. Read now.
https://vk.com/@implantatsiya_zubov_v_minske-konsultaciya-implantologa-v-minske-pochemu-vazhno-i-nuzhno-p
you are really a just right webmaster. The web site
loading speed is incredible. It seems that you are doing any distinctive trick.
Also, The contents are masterpiece. you’ve done a excellent task in this matter!
Medicine information sheet. Effects of Drug Abuse.
cordarone medication
Best information about meds. Read now.
Does your site have a contact page? I’m having a tough time locating it but, I’d like to
shoot you an email. I’ve got some creative ideas for your blog you might be interested in hearing.
Either way, great site and I look forward to
seeing it develop over time.
Pills information leaflet. Brand names.
lisinopril
Actual what you want to know about medication. Get now.
Pills information leaflet. What side effects can this medication cause?
amoxil buy
Everything about medicines. Get here.
Medication information for patients. Brand names.
zovirax
Best news about drugs. Read information here.
Diflucan
Drugs information. Brand names.
cialis soft for sale
Best information about medicine. Read now.
Drugs information sheet. Effects of Drug Abuse.
get fosamax
Best what you want to know about meds. Get information now.
Вы не правы. Давайте обсудим это.
It’s likewise a great idea to check out consumer testimonials and check the carrier’s record to see if they have a history of service interruptions or https://legaldesire.com/benefits-of-uae-virtual-phone-number-971/ other problems.
педагогика и саморазвитие
stromectol price
You as the bettor will have to click by way of the subsections to locate what you want to view.
Here is my homepage :: ncs.symflow.com
Pills prescribing information. Drug Class.
generic levitra
Everything trends of drug. Get information now.
My brother recommended I would possibly like this blog.
He was once entirely right. This post actually made my day.
You can not consider simply how much time I had spent for
this info! Thanks!
lisinopril cough
Medicament information. Cautions.
eldepryl price
Some what you want to know about meds. Read information here.
Pills information sheet. Cautions.
bactrim
Actual news about medicine. Read here.
finasteride tablets
Medicine information. Effects of Drug Abuse.
neurontin
All trends of medicament. Get information here.
You have made your point quite effectively!!
Drugs information sheet. Cautions.
cheap levaquin
All trends of medication. Get now.
lisinopril-hctz
prednisone for vasculitis
Mega Slot
cordarone drug interactions
Pills information for patients. Long-Term Effects.
zithromax
Everything news about medicine. Get information now.
Pills information. Brand names.
nexium without prescription
Everything trends of drug. Read here.
Great site! I recommend it to everyone!Chill Music
Medicine information for patients. Cautions.
where can i get zithromax
Everything trends of medication. Read information here.
neurontin 2018: neurontin 330 mg – neurontin 100mg price
Medicines prescribing information. What side effects can this medication cause?
zenegra
All trends of drug. Read information here.
Meds information sheet. Long-Term Effects.
silagra
Everything news about meds. Get information now.
Прогон хрумером — это единственный из методов раскрутки сайтов в интернете,
основанный на автоматической регистрации и размещении
постов на разнообразных площадках, досках
рекламы и иных ресурсах. Хрумер — вот
профессиональный программный инструмент, разработанный для автоматизации этого процесса.
Применяя этот инструмент, маркетологи и вебмастера надеются увеличить видимость их сайта, привлечь трафик и улучшить показатели в
результатах поисковиков
систем.
Однако нужно иметь в виду, что
многие новейшие поисковиков системы, такие как Google и Yandex, не одобряют такие методы раскрутки
и могут наказывать за них понижением позиций в
выводах поиска или абсолютным удалением из индекса.
Такой подход ассоциируется с тем, что автоматом созданные сообщения часто не несут полезной
сведений для пользователей и могут быть видимы
как спам. Таким образом, прежде
чем использовать хрумер или схожие инструменты, важно оценить все про и минусы, чтобы предотвратить нежелательных последствий
для вашего сайта.
Also visit my homepage Мой профиль в Microsoft
The first thing that we note about Arizona is that the
state is home to licensed online sportsbooks, which is
a pretty recent development having just happened in 2022.
However, there is no lawful online casino-style
gambling in Arizona, and state law makes it fairly clear that online gambling at non-licensed entities is illegal for players.
Even if you lose the first ten wagers using this system you will only lose ten units.
However if you only tossed a coin 10 times, you
could easily see an 80/20 split, or a 90/10 split,
or even a 100/0 split. So if you tossed a coin one million times you could expect to see close to a 50/50 split of heads or tails.
If you tossed a coin enough times, the expectation is that
the number of times it comes up heads and the number of times it comes up tails should be approximately equal.
If there’s a 50% chance of each happening, then it stands to reason that both will happen the same number of times.
The gambler’s fallacy is the biggest reason why people use negative progression betting systems.
I just tell people when I’m interested. “gonna catch a flight
to Nevada.” Sure, there is the peer pressure to deal and “people try to tell her she’s crazy, she doesn’t hear a word they say.” And, if we are being perfectly honest,
the songwriter has no trouble with his baby being
a roller.If heads does come up ten times in a row, the coin doesn’t “know” that and it is just as likely to be heads on the next toss
as it tails. Resulted in heads. This is because each
toss of the coin is an independent event. The more times you toss a coin, the more effect probability
has and the less effect variance has. Now have more random
bets than I would without an account. We will now explain why it is
known as the gambler’s fallacy and why it
can cause problems. Once you understand all this it should be
easy to understand why the gambler’s fallacy is
indeed a fallacy. This is why you need to be very careful when using negative
betting systems. Why do we pay taxes on April 15? Applicants for Terminal Operator, Distributor,
Supplier, Manufacturer, Terminal Handler, Technician and Licensed Establishments are
required to pay an application fee, a licensing fee immediately
upon licensure and an annual fee in connection with each subsequent licence renewal.
Of course, you have to accept that the chances of this happening are always against in you in the casino because of the house edge.Google
pay, a well-known payment method, offers players a
secure means of funding their online casino accounts. Where roulette players can get in trouble
is on even money bets such as red or black.
Slot developers like to experiment with a wide
range of themes, ensuring that players are entertained and amused every
time they try something new. So, although this system can maximize your winnings
in some circumstances, in other circumstances it
can actually make you lose more than you would if you were just
betting the same amount each time. This works by placing even money wagers (on something such as
red at the roulette table) and doubling the stake every time
a wager loses. Ramen cups even pop up as bargaining chips in poker games.
As we have said, it should really be used for even money wagers
such as those available at certain casino games.
You can even have little garages built for countertop appliances like toasters,
and spice racks designed just for your personal collection. One
of the bigger problems with this system is that you can lose money if you
are winning roughly the same amount of wagers as you
are losing.A roulette wheel could easily spin black 10
or more times in a row, and if that happened then anyone using the Martingale system would likely run out of money or reach the table betting limits.
By contrast, a long losing streak using the Contra
D’Alembert is likely to be relatively inexpensive.
Not only does this system help you lose quite slowly when luck is against you, it also helps you to win big if you go on a long winning streak.
With certain sequences you can even lose money when you win more wagers than you lose.
Technically they can be implemented on any even money
wager, but roulette, craps, blackjack or baccarat are the best options.
Both these systems are best used for the same type of wagers, namely even money wagers in the casino.
Signup Casino FREE bonus money so you get the best deals.
A key part of the program is finding a sponsor, a former gambler who has experience remaining free from addiction and can provide you invaluable guidance and support.
Look into my page :: Dragon Link Pokies Online Free
can i buy generic lisinopril no prescription
http://azithromycin.men/# zithromax cost australia
Meds prescribing information. Short-Term Effects.
xenical
Some trends of pills. Get information here.
Medicines information leaflet. What side effects can this medication cause?
propecia
Everything about medicines. Read information here.
Medication information sheet. Short-Term Effects.
get celebrex
Everything trends of medicament. Read information now.
Drug information sheet. Short-Term Effects.
cheap propecia
All about drugs. Read now.
Meds information sheet. Long-Term Effects.
lisinopril
Actual about medicament. Read here.
Drugs information. What side effects can this medication cause?
get eldepryl
All what you want to know about pills. Read now.
Medicine information leaflet. What side effects?
flagyl
Best about pills. Get here.
Medicine information sheet. Short-Term Effects.
buy fluoxetine
Best news about medicines. Read now.
japanese beautiful milf sex
cetirizine
Medicines information. Long-Term Effects.
buying viagra soft
All information about drug. Get information now.
Hello, everything is going perfectly here and ofcourse every one is sharing data,
that’s actually fine, keep up writing.
Pills prescribing information. Drug Class.
where can i buy mobic
All what you want to know about pills. Read now.
玩運彩:體育賽事與娛樂遊戲的完美融合
在現代社會,運彩已成為一種極具吸引力的娛樂方式,結合了體育賽事的激情和娛樂遊戲的刺激。不僅能夠享受體育比賽的精彩,還能在賽事未開始時沉浸於娛樂遊戲的樂趣。玩運彩不僅提供了多項體育賽事的線上投注,還擁有豐富多樣的遊戲選擇,讓玩家能夠在其中找到無盡的娛樂與刺激。
體育投注一直以來都是運彩的核心內容之一。玩運彩提供了眾多體育賽事的線上投注平台,無論是NBA籃球、MLB棒球、世界盃足球、美式足球、冰球、網球、MMA格鬥還是拳擊等,都能在這裡找到合適的投注選項。這些賽事不僅為球迷帶來了觀賽的樂趣,還能讓他們參與其中,為比賽增添一份別樣的激情。
其中,PM體育、SUPER體育和鑫寶體育等運彩系統商成為了廣大玩家的首選。PM體育作為PM遊戲集團的體育遊戲平台,以給予玩家最佳線上體驗為宗旨,贏得了全球超過百萬客戶的信賴。SUPER體育則憑藉著CEZA(菲律賓克拉克經濟特區)的合法經營執照,展現了其合法性和可靠性。而鑫寶體育則以最高賠率聞名,通過研究各種比賽和推出新奇玩法,為玩家提供無盡的娛樂。
玩運彩不僅僅是一種投注行為,更是一種娛樂體驗。這種融合了體育和遊戲元素的娛樂方式,讓玩家能夠在比賽中感受到熱血的激情,同時在娛樂遊戲中尋找到輕鬆愉悅的時光。隨著科技的不斷進步,玩運彩的魅力將不斷擴展,為玩家帶來更多更豐富的選擇和體驗。無論是尋找刺激還是尋求娛樂,玩運彩都將是一個理想的選擇。 https://telegra.ph/2023-年玩彩票並投注體育-08-16
Whats up very nice web site!! Guy .. Excellent .. Superb ..
I’ll bookmark your web site and take the feeds also?
I am glad to find so many helpful information right here within the publish, we want
develop extra strategies on this regard, thanks
for sharing. . . . . .
My web page; pick n pull fairfield
Medicine information. Effects of Drug Abuse.
provigil for sale
Actual about pills. Get information here.
Medicines information for patients. What side effects?
cordarone
Actual trends of medication. Get now.
Pills information sheet. Drug Class.
where to buy nolvadex
Some information about medicines. Read information here.
ivermectin lotion: purchase ivermectin – oral ivermectin cost
Medicine information leaflet. Short-Term Effects.
neurontin cheap
Actual information about medicament. Get information here.
Good info Kudos!
what is doxycycline hyclate
Medicament information leaflet. Cautions.
clomid medication
Actual what you want to know about medicament. Get now.
Medicine information. Brand names.
strattera buy
All trends of medicines. Get now.
fingering orgasm
Medicament prescribing information. What side effects can this medication cause?
neurontin
Some trends of drug. Get information now.
http://azithromycin.men/# zithromax over the counter
Вы отдаете себе отчет, в сказанном…
Nonetheless mixers aren’t a silver bullet and you need to fully read and perceive the beneath info earlier than using them as a lot of coin mixing services out there aren’t as perfect as they’d have bitcoin mixer you ever imagine.
Medicines information leaflet. Brand names.
cytotec otc
All information about medicines. Get here.
cheap cordarone online
Drugs information for patients. Drug Class.
buy generic levitra
All news about drug. Get information here.
Medicine information for patients. Long-Term Effects.
prednisone
Everything trends of drugs. Get information here.
The real-life examples you have actually cooperated this article include a private contact that reverberates along with audiences.
It’s clear you possess useful knowledge in the concern.
Also visit my site premium
A neural network draws a woman
The neural network will create beautiful girls!
Geneticists are already hard at work creating stunning women. They will create these beauties based on specific requests and parameters using a neural network. The network will work with artificial insemination specialists to facilitate DNA sequencing.
The visionary for this concept is Alex Gurk, the co-founder of numerous initiatives and ventures aimed at creating beautiful, kind and attractive women who are genuinely connected to their partners. This direction stems from the recognition that in modern times the attractiveness and attractiveness of women has declined due to their increased independence. Unregulated and incorrect eating habits have led to problems such as obesity, causing women to deviate from their innate appearance.
The project received support from various well-known global companies, and sponsors readily stepped in. The essence of the idea is to offer willing men sexual and everyday communication with such wonderful women.
If you are interested, you can apply now as a waiting list has been created.
Прошу прощения, что ничем не могу помочь. Надеюсь, Вам здесь помогут другие.
Despite this accomplishment, many don’t consider this to “formally” be the primary buy made on the internet, more than likely as a result of the installment was made face to face and in real money, hidden wiki url with out utilizing any type of installment stage.
Meds prescribing information. What side effects?
nolvadex
Actual trends of medicine. Read information now.
Medicines information sheet. Effects of Drug Abuse.
eldepryl
Best trends of medicament. Read now.
Pills information sheet. Short-Term Effects.
zithromax
Actual what you want to know about drugs. Read here.
Meds information leaflet. Brand names.
rx proscar
Some news about drugs. Read information here.
Medicine prescribing information. Long-Term Effects.
viagra
Everything what you want to know about medicament. Read information now.
Truly loads of amazing data.
Medicines information for patients. What side effects?
zyban without dr prescription
Actual news about medicines. Get information here.
Medicine information sheet. Effects of Drug Abuse.
promethazine online
Best news about drugs. Get information now.
https://ed-pills.men/# erection pills viagra online
Pills information leaflet. What side effects?
amoxil
Everything trends of drugs. Read information now.
Drug information leaflet. Drug Class.
where can i get neurontin
Some about pills. Read information now.
prednisone medication
подростковые сайты Наш сайт представляет собой интерактивную платформу, которая нацелена на образование и развлечение детей, а также на поддержку и советы для родителей. Здесь вы найдете разнообразные игры, обучающие материалы, видеоуроки, музыку и многое другое, специально подобранное для детей разных возрастов и интересов. Мы также предоставляем полезные рекомендации для родителей, которые помогут им лучше понять и поддерживать своих детей в онлайн-мире. Наш сайт – это идеальное место для детей и их родителей, которые хотят проводить время вместе в интересной и образовательной среде. Посетите наш сайт сегодня и начните наслаждаться всеми нашими возможностями!
Pills information sheet. What side effects can this medication cause?
viagra
Everything what you want to know about medicament. Get here.
Pills information leaflet. What side effects?
lyrica buy
Best about drugs. Read information here.
Я извиняюсь, но, по-моему, Вы допускаете ошибку. Давайте обсудим. Пишите мне в PM.
Water transport facilitated by aquaporins (AQPs) is an necesario mechanism to achieve fluid homeostasis in the different compartments of the https://rohstoffbetriebe.de/component/k2/item/5?start=0.
Medicines information sheet. Generic Name.
aurogra pills
Best news about meds. Get now.
There is visibly a lot to know about this. I assume you made various
good points in features also.
Here is my blog … 2011 chevy malibu transmission
lisinopril metabolism
paxlovid pill: paxlovid covid – paxlovid covid
Medicament prescribing information. What side effects can this medication cause?
valtrex online
All about drug. Get now.
Meds information for patients. Cautions.
levaquin
Best about medicines. Read information here.
По моему мнению Вы не правы. Я уверен. Могу это доказать. Пишите мне в PM, пообщаемся.
Then feel muster the chest, https://www.classifiedads.com/insurance/wz2cmm9lg3d79 abdomen beneath tension. For instance, when sitting relaxed motion, taking basic posture, eyes, natural breathing for five seconds.
Попал мужик!
Партнерский хлеб (с https://arduino-geek.pp.ua/blog/2017/06/25/programmirovanie-stm32f103c8t6-v-srede-arduino-ide/ маслом) вебе. вроде подзаработать получи партнерках. Партнерский плата. пожива получай партнерках. вроде наработать без вложений.
Medicament information sheet. Cautions.
zovirax prices
Best news about medicament. Get now.
Drug information for patients. Short-Term Effects.
flagyl
All about medicine. Get here.
In the whirlwind landscape of social media, the phrase “link in bio” has
become more than just a catchphrase – it’s a
doorway, a bridge, a lifeline. But why has such a simple directive become a cornerstone of online interactions?
This article delves into the power of the “link in bio”, its rise in popularity, and its undeniable influence in the social media world.
Also visit my homepage – Telegra.Ph
เว็บสล็อตWe are ready to serve all gamblers with a complete range of
online casinos that are easy to play for real money.
Find many betting games, whether popular games such as
baccarat, slots, blackjack, roulette and dragon tiger.
Get experience Realistic gambling as if playing at a world-class
casino online. Our website is open for new members 24 hours
a day.
I’m not that much of a online reader to be honest but your blogs really nice, keep it up!
I’ll go ahead and bookmark your website to come back later on. All the best
Antminer D9
The neural network will create beautiful girls!
Geneticists are already hard at work creating stunning women. They will create these beauties based on specific requests and parameters using a neural network. The network will work with artificial insemination specialists to facilitate DNA sequencing.
The visionary for this concept is Alex Gurk, the co-founder of numerous initiatives and ventures aimed at creating beautiful, kind and attractive women who are genuinely connected to their partners. This direction stems from the recognition that in modern times the attractiveness and attractiveness of women has declined due to their increased independence. Unregulated and incorrect eating habits have led to problems such as obesity, causing women to deviate from their innate appearance.
The project received support from various well-known global companies, and sponsors readily stepped in. The essence of the idea is to offer willing men sexual and everyday communication with such wonderful women.
If you are interested, you can apply now as a waiting list has been created.
Я могу проконсультировать Вас по этому вопросу. Вместе мы сможем прийти к правильному ответу.
Партнерский вебсайт. Партнерские ссылочки. Партнерский приработок. Ant. http://drinskaoaza.com/index.php/component/k2/item/1-reka/1-reka трата. выручка держи партнерках. беглый убыль. Сайт заработках webе.
у мня уже есть
Choose the best brands at the most reasonable prices while procuring at online http://www.pasquier-construction.fr/projet-construction-maison-bois/construction-maison-ossature-bois/ shops. Supplies for the workplace and residence are necessities one cannot do with out and therefore when you consider supplies, we usually order in bulk or a lot prematurely so that we will avoid falling wanting them.
Отличный сайт! Всем рекомендую!Кредиты Онлайн
Прогоны Хрумером и GSA Search Engine Ranker без интернета как собирать базы для хрумера
Medication prescribing information. Generic Name.
cheap propecia
All what you want to know about drugs. Read information here.
Drugs information. What side effects can this medication cause?
singulair
Actual about medicament. Get information here.
Вы очень талантливый человек
Common medicines like Actonel, Celexa, Evista, Flomax, Lipitor, Nexium, Prevacid, Tamoxifen, https://cahootie.com/world-news/what-should-be-in-a-first-aid-kit-2/ Zocor and Zoloft are at all times obtainable with them.
Просто перепрыгните получи страницу «Задать вопрос», yurist-moscow.ru обрисуйте личную вопрос также урвите хмырь сервис: на дармовщинку ливень платно.
Meds information leaflet. Drug Class.
effexor
Some news about pills. Read information here.
Medication information for patients. Brand names.
cephalexin
All what you want to know about medication. Get information now.
Да, действительно. И я с этим столкнулся. Давайте обсудим этот вопрос.
Shingles, specifically, are comparatively straightforward to replace if they undergo harm throughout a storm. “Often insurance coverage firms need you to have a roofing contractor look on the injury so that you don’t open up a declare unnecessarily, https://vcf.vn.ua/marketing-moshhnyj-instrument-dlya-razvitiya-biznesa/ which can damage your scores along with your insurance coverage service,” says Ami Feller of Feller Roofing.
Medicine information for patients. Generic Name.
priligy otc
Some about medicines. Get here.
doxycycline 100 pil
это просто ужасно!!!!!
Наша велокоманда делает вместе с 1998-спорт года, https://likitoriya.com/img/pgs/?kupit_diplom_vospitatelya_8.html чисто поуже произносит о многом. Мы располагаем сливай воду необходимое рентгенооборудование, (а) также в нашем сша работают чуть только профессиональные мастака а также курьеры.
Ебацца
Antminer D9
Самыми славными вид развлечения начиная с. Ant. до джекпотом считаются Mega Fortune Dreams, Hall of Gods, Mega Moolah, только дилемма тоже содержит наши личный номер эксклюзионные игры капля джекпотом, Онлайн казино в том числе Kreisiraadio не то — не то Cash & Carry.
Medicine information sheet. Cautions.
order tadacip
Actual information about meds. Get here.
Отличный сайт! Всем рекомендую!Кредиты Онлайн
Medicament information sheet. Drug Class.
valtrex otc
Some trends of medicament. Read information now.
Medicine prescribing information. Drug Class.
zoloft brand name
Actual information about pills. Read now.
Беру по любому
ради самые короткие сроки ваш брат получите прообраз отличных потребительских качеств держи бумаг ГОЗНАК, http://forum54.4adm.ru/viewtopic.php?f=69&t=6537 неразличимый с служебных образчиков.
Medicine information sheet. Brand names.
kamagra
Everything news about drug. Get information here.
There are loads of excellent, solid, Mitsubishi more deals that can give you the help you need; and the online means that you can deliver all such distributors to your laptop display, enabling you to check worth, value, and high quality.
where can i buy prednisone over the counter usa
Work with your Mostbet Casino com login to key in the site
and write a fresh message to support.
Демо релиз игры доступна инвесторам, https://daddycasinorussia.win/otziv которые употребляют служебную ссылку али ступили нате портал через рабочее зерцало. Указание и заверение реквизитов.
Drug prescribing information. What side effects?
singulair buy
Best trends of medication. Get here.
Очень полезная фраза
в течение томишко количестве рекламные, https://forum.veterinar.ru/showthread.php?7143-%D0%A1%D0%BE%D0%B7%D0%B4%D0%B0%D0%BD%D0%B8%D0%B5-%D1%81%D0%B5%D1%80%D1%82%D0%B8%D1%84%D0%B8%D0%BA%D0%B0%D1%82%D0%BE%D0%B2-%D0%BF%D0%BE%D0%BB%D0%B8%D0%B3%D1%80%D0%B0%D1%84%D0%B8%D0%B8 умеющие возбудить интерес вероятных клиентов. Типография «PrintRobot» – такое августейшее колорит продукта в совокупности капля низкими ценами на Москве.
Medicament prescribing information. Drug Class.
valtrex buy
Best information about drug. Read information here.
lisinopril
Meds information for patients. Effects of Drug Abuse.
sildigra without a prescription
All news about medicine. Read information now.
levaquin tablets
Meds information leaflet. What side effects can this medication cause?
pregabalin
All information about medicament. Get now.
Meds information leaflet. Short-Term Effects.
cialis super active
All news about medicine. Read information now.
Drugs prescribing information. Cautions.
neurontin buy
All about meds. Get information here.
Pills information leaflet. Effects of Drug Abuse.
rx ampicillin
Everything news about drug. Get now.
lisinopril tablet 40 mg
Азелаиновый пилинг— это процедура химического отшелушивания поверхностного слоя кожи, что способствует ее очищению и оздоровлению.
Данная методика отшелушивает ороговевшие клетки, помогает с лечением угревой сыпи, черных точек.
Medicine information sheet. Cautions.
cytotec
Some trends of medicament. Read information now.
Edit, and in the window that opens, sda steam tap Enter Setup Key… (there is no QR code possibility right here).
Конечно. Так бывает. Можем пообщаться на эту тему. Здесь или в PM.
потому, затем чтобы трактование дремы обреталось преимущественно истинным, обращайте внимание не столько держи равный коннотация дремы, http://www.djwx.com/forums/user/profile/60695.page а также нате его компонента.
Pills information sheet. Short-Term Effects.
cost propecia
Everything information about medicament. Read now.
The best article to ever read this year, I hope this will be an added value for my and all the readers.
Да, я вас понимаю. В этом что-то есть и мысль отличная, согласен с Вами.
41. в течение случае раскрытия доктором-психиатром а также (может ли быть) наркологом персон немного сомнением нате присутствие медицинских противопоказаний, отвечающих профилю данных искусников, буква допуску в службы мало вредными также (сиречь) опасными производственными сомножителями, вдобавок к работам, около исполненьи каковых кровь из носу обманывание предварительных да периодических врачебных осмотров (обследований) сотрудников, сориентированные лица порой, предусмотренных законодательством Российской Федерации, направляются пользу кого освидетельствования жест медицинской комиссии, https://dostoyanie.pro/ уполномоченной в мера федерационным органом исполнительной руководящие круги в сфере здравоохранения другими словами органом казенной администрация субъекта россии в сфере охраны здоровья.
Medicament prescribing information. Drug Class.
lisinopril
Everything about medicament. Get information here.
Drugs information for patients. Long-Term Effects.
neurontin price
Some about medicament. Read information here.
Подробнее об организации: Вмс уфсб поликлиника на сайте Смоленск в сети
is lisinopril a beta blocker
https://www.instrushop.bg/mashini-i-instrumenti/akumulatorni-mashini/akumulatorni-rachni-cirkulyari
Drug information sheet. Long-Term Effects.
glucophage
All news about medicines. Get here.
Pills prescribing information. Brand names.
trazodone
Some trends of drugs. Read information here.
Pills information. What side effects?
lyrica rx
All news about medicament. Read information here.
Абсолютно с Вами согласен. В этом что-то есть и это хорошая идея. Готов Вас поддержать.
Благодаря полиграфии, http://www.websiteprofit.ru/forum/viewtopic.php?f=17&t=14266 общества могут наметить фирменный экспрессионизм равным образом очертить рекламную отчет. Технология дает возможность молниеносно (а) также дёшево выдавать пущие тиражи.
Medication information. Drug Class.
sildigra
All about medicine. Get information here.
Medicine information sheet. Long-Term Effects.
flagyl
Best about meds. Get now.
Восполнить пробел?
Мебель из массива дерева имеет редкими качествами, тот или иной дозволяют мастачить долговременную изысканную http://fh7778nc.bget.ru/users/ebiboj, строящую на обиталище атмосферу естественности и теплоты.
купити Інструмент INTERTOOL
It gives an extra layer of security and peace of mind for those involved concerning the safety of their steam desktop authenticator Steam accounts.
мебель на заказ
fantastic publish, very informative. I ponder why the other experts of this sector do not realize this.
You should continue your writing. I am sure, you have
a great readers’ base already!
DAFTAR KOINSLOT
Unveiling the Thrills of KOIN SLOT: Embark on an Adventure with KOINSLOT Online
Abstract: This article takes you on a journey into the exciting realm of KOIN SLOT, introducing you to the electrifying world of online slot gaming with the renowned platform, KOINSLOT. Discover the adrenaline-pumping experience and how to get started with DAFTAR KOINSLOT, your gateway to endless entertainment and potential winnings.
KOIN SLOT: A Glimpse into the Excitement
KOIN SLOT stands at the intersection of innovation and entertainment, offering a diverse range of online slot games that cater to players of various preferences and levels of experience. From classic fruit-themed slots that evoke a sense of nostalgia to cutting-edge video slots with immersive themes and stunning graphics, KOIN SLOT boasts a collection that ensures an enthralling experience for every player.
Introducing SLOT ONLINE KOINSLOT
SLOT ONLINE KOINSLOT introduces players to a universe of gaming possibilities that transcend geographical boundaries. With a user-friendly interface and seamless navigation, players can explore an array of slot games, each with its unique features, paylines, and bonus rounds. SLOT ONLINE KOINSLOT promises an immersive gameplay experience that captivates both newcomers and seasoned players alike.
DAFTAR KOINSLOT: Your Gateway to Adventure
Getting started on this adrenaline-fueled journey is as simple as completing the DAFTAR KOINSLOT process. By registering an account on the KOINSLOT platform, players unlock access to a realm where the excitement never ends. The registration process is designed to be user-friendly and hassle-free, ensuring that players can swiftly embark on their gaming adventure.
Thrills, Wins, and Beyond
KOIN SLOT isn’t just about the thrills; it’s also about the potential for substantial winnings. Many of the slot games offered through KOINSLOT come with varying levels of volatility, allowing players to choose games that align with their risk tolerance and preferences. The allure of potentially hitting that jackpot is a driving force that keeps players engaged and invested in the gameplay.
Жаль, что сейчас не могу высказаться – тороплюсь на работу. Вернусь – обязательно выскажу своё мнение.
Entry Google Calendar with a Google account (for personal use) or Google Workspace account (for enterprise http://sportowewywiady.pl/index.php/w-numerze/ use).
lisinopril cough
buy cordarone
Drugs information sheet. Effects of Drug Abuse.
singulair without rx
Some trends of pills. Get now.
cleocin price per pill
Duphalac
Medication information sheet. Cautions.
propecia
Some trends of medicine. Read now.
It is actually obvious that you have actually performed
your research. Your blog post is loaded with legitimate sources and also information,
making it a superb information for anyone thinking about this location.
Feel free to visit my site: Non-owner SR-22 insurance
http://lipitor.pro/# cheap lipitor online
Unveiling the Thrills of KOIN SLOT: Embark on an Adventure with KOINSLOT Online
Abstract: This article takes you on a journey into the exciting realm of KOIN SLOT, introducing you to the electrifying world of online slot gaming with the renowned platform, KOINSLOT. Discover the adrenaline-pumping experience and how to get started with DAFTAR KOINSLOT, your gateway to endless entertainment and potential winnings.
KOIN SLOT: A Glimpse into the Excitement
KOIN SLOT stands at the intersection of innovation and entertainment, offering a diverse range of online slot games that cater to players of various preferences and levels of experience. From classic fruit-themed slots that evoke a sense of nostalgia to cutting-edge video slots with immersive themes and stunning graphics, KOIN SLOT boasts a collection that ensures an enthralling experience for every player.
Introducing SLOT ONLINE KOINSLOT
SLOT ONLINE KOINSLOT introduces players to a universe of gaming possibilities that transcend geographical boundaries. With a user-friendly interface and seamless navigation, players can explore an array of slot games, each with its unique features, paylines, and bonus rounds. SLOT ONLINE KOINSLOT promises an immersive gameplay experience that captivates both newcomers and seasoned players alike.
DAFTAR KOINSLOT: Your Gateway to Adventure
Getting started on this adrenaline-fueled journey is as simple as completing the DAFTAR KOINSLOT process. By registering an account on the KOINSLOT platform, players unlock access to a realm where the excitement never ends. The registration process is designed to be user-friendly and hassle-free, ensuring that players can swiftly embark on their gaming adventure.
Thrills, Wins, and Beyond
KOIN SLOT isn’t just about the thrills; it’s also about the potential for substantial winnings. Many of the slot games offered through KOINSLOT come with varying levels of volatility, allowing players to choose games that align with their risk tolerance and preferences. The allure of potentially hitting that jackpot is a driving force that keeps players engaged and invested in the gameplay.
Medication information sheet. Brand names.
order zofran
Actual what you want to know about medicine. Read information now.
Как обеспечить защиту продукта? Рекомендации на KV.by.
prednisone tablets
Drugs information for patients. Short-Term Effects.
priligy
Some trends of medicines. Get information now.
Drugs information leaflet. What side effects can this medication cause?
cytotec tablets
All about medicines. Get now.
Drug information. Generic Name.
norvasc
Actual trends of medication. Read here.
Medicament information sheet. Cautions.
neurontin buy
Best what you want to know about medicine. Read now.
Wonderful article! That is the kind of info that are supposed to be shared around the web.
Disgrace on Google for no longer positioning this publish higher!
Come on over and seek advice from my web site .
Thank you =) adult swim
Drug information for patients. Long-Term Effects.
clomid
Some what you want to know about meds. Read here.
Portobet Hesap Kapatma Ећikayetleri
side effect of prednisone
Betlio Web Sitesi Direkt Ana Sayfa
Drugs information leaflet. Drug Class.
silagra
Everything information about medication. Get now.
Betproton Гњcretsiz Casino OyunlarД±
https://ciprofloxacin.ink/# п»їcipro generic
what is finasteride
Betvoy Bahis Seçenekleri Ve Oranları
https://www.instrushop.bg/Лазерни-нивелири/
Pills information for patients. Short-Term Effects.
cialis super active tablet
Everything news about drug. Get now.
Ladesbet Web Sitesi Д°Еџletimi
Ну они и дают жару
в течение всякой из их обязаны быть раздельные вселения в целях совершеннолетных также детвору. потому приведется делать разнообразные навесы, поддоны, http://myrecipe.at.ua/forum/15-11257-1 замечать сухие здания также т.буква.
Это всего лишь условность
Изготавливают покрытия из ПВХ, тарпаулина, брезента, https://doa.at.ua/forum/16-8728-1#29329 полотна Oxford – влагонепроницаемых абразивостойких материалов. 3. Комплектующие к кровель: снегозадержатели, вентиляторные выходы, аэраторы, кровельные воронки, анадромные детали.
Payday loans online
Как нельзя кстати.
Former WWE Diva and Corridor of Famer Lita was the source of her inspiration when she debuted in WWE essential rosters Uncooked and Smack Down three http://toypon.com/sp/redirect.php?action=url&goto=magia.lublin.pl/uncategorized/nowa-karta-szef-kuchni-poleca/ years back.
Medicines information. Short-Term Effects.
cialis soft
Actual news about medication. Get here.
Полезная мысль
Aby otrzymac wiadomosc wiecej o tym, jakze oraz do jakich celow Amazon wykorzystuje dane osobowe (takie niczym czas zamowien w sklepie Amazon), https://www.britishlogcabins.com/forum/welcome-to-the-forum/danmark przejdz do strony Nowosc o prywatnosci.
Хорошего понемногу.
на процессе годы создано также выпущено 56 ранее не известных разновидностей изделий, из них сорок семь картин хлебобулочных, http://cssbym.ru/forum/showtopic-28598 9 кондитерских. Периодический соблюдение стандартов хлебобулочной продукции воплотите УЗ «Глусский райЦГиЭ» на вечной почве.
prednisone to methylprednisolone conversion
Я думаю, Вы придёте к правильному решению.
A number of states (Indiana, 7reels ndb Louisiana and Missouri) allow slot machines (as well as any casino-fashion gambling) only on licensed riverboats or permanently anchored barges.
Сегодня я много читал на эту тему.
в пользу кого квартир один-два великовозрастным количеством пунктов водоразбора лучше завоевывать накопительные бойлеры. Имеет замонтированный воздухоподогрев вода пользу кого ГВС, http://ascrolite.com/component/k2/item/1.html снабжен магниевым анодом.
Medicine information for patients. Long-Term Effects.
neurontin buy
Best about meds. Read information now.
Ага, попался!
You may make your career on this area and earn pokies.net 74 australia enormous. The cruise ship musicians are often wanted in lounges on ships in addition to near swimming pools.
ChemDiv’s Screening Libraries have been extensively validated both in our in-house biological assays and in the laboratories of over 200 external partners including Pharma, Biotech, Academia and Screening Centers in the U.S., Europe, and Japan. We offer a shelf-available set of over 1.6 M individual solid compounds.
allosteric inhibitors
Medicament information for patients. Generic Name.
order tadacip
All about medicine. Get now.
cordarone hcl
Nicely put, Kudos.
Medicament information sheet. What side effects?
silagra
Best what you want to know about medication. Read here.
amoxicillin capsules
Могу предложить Вам посетить сайт, на котором есть много информации на интересующую Вас тему.
Still, https://www.fuhrmannconstruction.com/blog/biggest-benefits-of-creating-a-modern-workplace-environment/ Dr. Cooper says that’s not sufficient to halt a transformation in headache drugs that’ll develop access and high quality of care.
Meds information. Effects of Drug Abuse.
nolvadex
Actual trends of meds. Get information here.
Да, действительно. Я присоединяюсь ко всему выше сказанному. Давайте обсудим этот вопрос.
Investigators are additionally keen as we speak to participate in clinical trials that are GCP compliant and likewise https://starsblog.ru/viewtopic.php?id=9873#p27144 adhere to protocols.
Drugs information for patients. What side effects?
cytotec
Some trends of pills. Get now.
KOINSLOT
Unveiling the Thrills of KOIN SLOT: Embark on an Adventure with KOINSLOT Online
Abstract: This article takes you on a journey into the exciting realm of KOIN SLOT, introducing you to the electrifying world of online slot gaming with the renowned platform, KOINSLOT. Discover the adrenaline-pumping experience and how to get started with DAFTAR KOINSLOT, your gateway to endless entertainment and potential winnings.
KOIN SLOT: A Glimpse into the Excitement
KOIN SLOT stands at the intersection of innovation and entertainment, offering a diverse range of online slot games that cater to players of various preferences and levels of experience. From classic fruit-themed slots that evoke a sense of nostalgia to cutting-edge video slots with immersive themes and stunning graphics, KOIN SLOT boasts a collection that ensures an enthralling experience for every player.
Introducing SLOT ONLINE KOINSLOT
SLOT ONLINE KOINSLOT introduces players to a universe of gaming possibilities that transcend geographical boundaries. With a user-friendly interface and seamless navigation, players can explore an array of slot games, each with its unique features, paylines, and bonus rounds. SLOT ONLINE KOINSLOT promises an immersive gameplay experience that captivates both newcomers and seasoned players alike.
DAFTAR KOINSLOT: Your Gateway to Adventure
Getting started on this adrenaline-fueled journey is as simple as completing the DAFTAR KOINSLOT process. By registering an account on the KOINSLOT platform, players unlock access to a realm where the excitement never ends. The registration process is designed to be user-friendly and hassle-free, ensuring that players can swiftly embark on their gaming adventure.
Thrills, Wins, and Beyond
KOIN SLOT isn’t just about the thrills; it’s also about the potential for substantial winnings. Many of the slot games offered through KOINSLOT come with varying levels of volatility, allowing players to choose games that align with their risk tolerance and preferences. The allure of potentially hitting that jackpot is a driving force that keeps players engaged and invested in the gameplay.
Мега даркнет портал – мое главное поселение назначения чтобы в общей сложности, https://gatespolls.com/uncategorized/what-is-the-cfd/ что имеет какую либо связь не без; техникой.
Greetings! Very helpful advice within this post!
It’s the little changes that will make the most important changes.
Thanks for sharing!
интиресно! побольше такого
ежели в (видах ваших вид на жительство деловитости, специальностей, профессий непременная аттестация безвыгодный учреждена законодательством, то она может прокладываться подобру-поздорову. Должностные роль да компетенции работника прописывают буква рабочем контрактов, инструкциях, http://godarea.net/light/light.cgi других локальных действиях.
Medicine information for patients. Brand names.
cleocin order
Best about drugs. Get here.
https://4rav.ru/articles/gde-kupit-vygodno-zapchasti-dlya-vashego-avto
же, все одно, недорогого дармового контента достанет «с головой», https://mangamammy.ru/ затем чтоб послать к черту потребность средного читателя а также дилетанта манги.
Medicine information sheet. Drug Class.
flagyl pill
Some information about drugs. Read information now.
does prednisone cause constipation?
Курс «Конструктор сбывающего текста» бросьте полезен т. е. копирайтерам, http://professii-online.ru так и владельцам бизнеса равно маркетологам. Предусмотрено пятнадцатого разных программный код ради бьюти-искусников.
Meds information leaflet. Cautions.
bactrim
Everything news about meds. Get now.
Drug information leaflet. Drug Class.
cytotec price
Some trends of drugs. Get information here.
Drug information. Generic Name.
singulair
Everything news about meds. Get now.
Your composing design is actually fascinating, as well as your capacity to communicate intricate tips in a logical
manner is actually commendable. The useful examples you’ve provided include intensity to the
content.
my page; additional coverage options
Payday loans online
Payday loans online
Drug information leaflet. Generic Name.
levitra
Actual about medicines. Get information now.
lisinopril 10 mg brand name in india
Busdoor
blood preauser tablet lisinopril what is the price
Payday loans online
Payday loans online
I like the valuable info you provide in your articles. I will bookmark your weblog and check again here frequently.
I am quite certain I’ll learn a lot of new stuff right here!
Best of luck for the next!
Medicines information leaflet. Long-Term Effects.
maxalt medication
Actual about medicament. Read now.
prasugrel
Meds prescribing information. Effects of Drug Abuse.
zyban generics
Everything information about pills. Read here.
Medication information for patients. Cautions.
aurogra medication
All about medicament. Get information now.
Cytoxan
Medicines prescribing information. Cautions.
pregabalin brand name
Actual information about medicines. Read here.
Meds prescribing information. Cautions.
sildigra sale
All news about medicament. Get here.
Охотхозяйство “Астраханское”
Pills information. What side effects?
baclofen
Some about medicines. Read information now.
Medicament information sheet. Effects of Drug Abuse.
provigil without prescription
Everything information about drugs. Read here.
http://certifiedcanadapills.pro/# canadian pharmacy phone number
Além disso, você pode caprichar no look incluindo um óculos https://Atavi.com/share/w7l2xrz1grv3q sol estiloso para dar um toque final no visual.
where can i get cheap lisinopril tablets
Pills prescribing information. What side effects?
generic zoloft
Actual news about meds. Read information now.
Medicament information. Cautions.
viagra without a prescription
All trends of drug. Get information now.
Good website! I really love how it is simple on my eyes and the
data are well written. I am wondering how I might be notified when a new post has been made.
I’ve subscribed to your feed which must do the trick!
Have a nice day!
Visit my website; 2007 pontiac grand prix
Medication information. What side effects can this medication cause?
sildigra without insurance
All trends of medication. Read information now.
Medicine information sheet. Cautions.
glucophage medication
Best news about pills. Read information now.
Подтверждаю. Я присоединяюсь ко всему выше сказанному.
Undergo the websites of some Canadian pharmacies that you find in Google and you’ll have a basic gut really http://www.hfa-hachioji.com/namie-yakisoba/%e7%84%bc%e3%81%8d%e3%81%9d%e3%81%b0%e3%82%a4%e3%83%99%e3%83%b3%e3%83%88/%e3%81%82%e3%81%95%e3%81%8c%e3%81%8a%e5%b8%82%e3%81%a7%e6%b5%aa%e6%b1%9f%e3%82%84%e3%81%8d%e3%81%9d%e3%81%b0%e3%82%92%e3%81%8a%e6%8a%ab%e9%9c%b2%e7%9b%ae%e3%81%97%e3%81%be%e3%81%97%e3%81%9f%ef%bc%81/ feel about them.
Medicines prescribing information. Brand names.
how to get amoxil
Some information about meds. Read information now.
csgo gamble legal
Pills prescribing information. Effects of Drug Abuse.
seroquel tablets
Some trends of medication. Get here.
best mail order pharmacy canada cross border pharmacy canada safe reliable canadian pharmacy
Жаль, что сейчас не могу высказаться – тороплюсь на работу. Вернусь – обязательно выскажу своё мнение.
же тут знатно въехать нетолстую черта, https://www.hashtap.com/@gravity/%D1%81%D0%B2%D0%B5%D1%82%D0%BE%D0%B2%D1%8B%D0%B5-%D0%BF%D0%B0%D0%BD%D0%B5%D0%BB%D0%B8-%D1%81-%D1%8F%D1%80%D0%BA%D0%BE%D0%B9-%D0%BF%D0%BE%D0%B4%D1%81%D0%B2%D0%B5%D1%82%D0%BA%D0%BE%D0%B9-%D1%8D%D1%84%D1%84%D0%B5%D0%BA%D1%82%D0%BD%D0%B0%D1%8F-%D1%80%D0%B5%D0%BA%D0%BB%D0%B0%D0%BC%D0%B0-%D0%B2%D0%BD%D1%83%D1%82%D1%80%D0%B8-%D0%BF%D0%BE%D0%BC%D0%B5%D1%89%D0%B5%D0%BD%D0%B8%D0%B9-%D0%B8-%D0%BD%D0%B0-%D1%83%D0%BB%D0%B8%D1%86%D0%B5-Z2gad8xzPXlG в каком месте подходит к концу указание вывески равным образом наступает устройство внешной рекламы. На настоящее время на столице разрешены любые виды прогрессивной рекламы, а раз-другой величавой обмолвкой.
Drugs information leaflet. Brand names.
tadacip
Some information about drugs. Get now.
Medication prescribing information. Effects of Drug Abuse.
finpecia
Some trends of pills. Read now.
csgo skins gambling
Terrific forum posts, With thanks.
Meds information for patients. Long-Term Effects.
zenegra
Best information about drugs. Read here.
Medicine prescribing information. What side effects can this medication cause?
glucophage buy
Best trends of pills. Read information here.
zyrtec samples for healthcare professionals
It takes under consideration the requisites of all and supplies appropriate and efficient means of promoting to offer the https://shopschrammek.is/contact/ last word goal.
Meds information sheet. Drug Class.
bactrim
Best what you want to know about drug. Get information now.
Drug information leaflet. Short-Term Effects.
colchicine
Best information about medication. Read information here.
Medicament information. Cautions.
can i order kamagra
All information about drug. Read now.
prednisone purchase
Вартість доставки у межах країни розраховується за тарифами https://www.free4adult.net/user/RaeSuggs64 перевізника. Оперативне відправлення товару в межах України (замовлення, прийняті до 19:00, відправляються щодня).
Medicines information for patients. Brand names.
lyrica tablet
Best news about medication. Read information here.
Drugs prescribing information. Long-Term Effects.
silagra
All trends of medicament. Get information now.
Medicines information for patients. What side effects can this medication cause?
finpecia price
Some about drugs. Get information now.
Какая хуёвина https://www.bookclubcookbook.com/steak-tacos/ (с морковиной)! Путин определяет исключительно силовых министров. Остальные назначаются премьером да утверждаются думой.
Pills prescribing information. Long-Term Effects.
fluoxetine
Best what you want to know about drugs. Get here.
rx lisinopril
Medicine information sheet. Generic Name.
tadacip rx
Everything news about medication. Get information now.
Medicament information for patients. Generic Name.
nolvadex tablet
Actual trends of medication. Read here.
Medication prescribing information. What side effects?
buy neurontin
Actual trends of medicines. Get information now.
Drugs information. Drug Class.
nolvadex medication
Everything trends of drugs. Get here.
Medication information sheet. Effects of Drug Abuse.
silagra
Some information about drugs. Get information here.
eee
Neyron şəbəkə gözəl qızlar yaradacaq!
Genetiklər artıq heyrətamiz qadınlar yaratmaq üçün çox çalışırlar. Onlar bu gözəllikləri neyron şəbəkədən istifadə edərək xüsusi sorğular və parametrlər əsasında yaradacaqlar. Şəbəkə DNT ardıcıllığını asanlaşdırmaq üçün süni mayalanma mütəxəssisləri ilə işləyəcək.
Bu konsepsiyanın uzaqgörənliyi, tərəfdaşları ilə həqiqətən bağlı olan gözəl, mehriban və cəlbedici qadınların yaradılmasına yönəlmiş çoxsaylı təşəbbüslərin və təşəbbüslərin həmtəsisçisi Aleks Qurkdur. Bu istiqamət müasir dövrdə qadınların müstəqilliyinin artması səbəbindən onların cəlbediciliyinin və cəlbediciliyinin aşağı düşdüyünü etiraf etməkdən irəli gəlir. Tənzimlənməmiş və düzgün olmayan qidalanma vərdişləri piylənmə kimi problemlərə yol açıb, qadınların anadangəlmə görünüşündən uzaqlaşmasına səbəb olub.
Layihə müxtəlif tanınmış qlobal şirkətlərdən dəstək aldı və sponsorlar asanlıqla işə başladılar. İdeyanın mahiyyəti istəkli kişilərə belə gözəl qadınlarla cinsi və gündəlik ünsiyyət təklif etməkdir.
Əgər maraqlanırsınızsa, gözləmə siyahısı yaradıldığı üçün indi müraciət edə bilərsiniz.
Medicine information for patients. What side effects?
lioresal
Actual news about medicine. Get now.
Drug information sheet. What side effects can this medication cause?
colchicine
Everything news about medication. Read now.
Drugs information for patients. Cautions.
how to buy bactrim
All about medicines. Get now.
Very fantastic information can be found on weblog.
Feel free to visit my homepage :: scion tc 2008
Meds information sheet. Long-Term Effects.
generic levitra
Everything information about medicament. Read information now.
Medicine information. Brand names.
ampicillin for sale
Best trends of pills. Get now.
anonymous sext chat
Disposable CBD vape pens are an excellent way to consume the healing properties of hemp. The easiest way to save some cash on your order is with an Infinite CBD promo code. And if you’re looking for a natural way to lose weight, Full Spectrum CBD Oil may be just what you need. Level 3 CBD Oil Drops are the maximum strength formulation for when you need the most relief, with over 80mg of CBD per serving. Their CBD Oil Drops were developed with doctors and are trusted by professional athletes to provide Next Level Relief, Recovery, and Rest. This family-run business also owns a wellness store, so they are experts at holistic living! As the EVALI outbreak showed, vaping oils can be risky, and experts strongly advise against using non-regulated CBD vape oil. In addition to using a special broad spectrum blend of CBD oil, Sunday Scaries tincture also incorporates Vitamin D3 (the “sunshine” vitamin), Vitamin B12 and coconut oil into its formulation. Fast Absorption and Quick Effects: Fast-absorption and immediate effects make Exhale’s CBD tincture a prize-winning product. In the following, some of the effects are described. Their products are formulated with premium, high-http://tyuratyura.s8.xrea.com/bbs/i-regist.cgi to deliver results you can feel.
Meds information sheet. Long-Term Effects.
diltiazem
Everything what you want to know about meds. Read information here.
Drug information sheet. Brand names.
neurontin
Some about medicines. Get here.
medicine prednisone 20mg tablets
Drugs prescribing information. What side effects?
glucophage
Some trends of drugs. Read information here.
Meds prescribing information. What side effects can this medication cause?
buy neurontin
Best information about medicines. Get here.
Drugs information. Long-Term Effects.
cephalexin
Everything news about medication. Get now.
lisinopril-hydrochlorothiazide
Medication information leaflet. What side effects?
generic diltiazem
Some news about medication. Get information now.
Kamagra tablets: kamagra oral jelly – Kamagra tablets 100mg
Pills information leaflet. What side effects?
paxil prices
Actual information about drugs. Get information here.
ashwagandha kaufen
Medicines information sheet. Effects of Drug Abuse.
cost cialis soft
Some what you want to know about meds. Get here.
Medicines information for patients. Long-Term Effects.
neurontin buy
Everything about drug. Read now.
buy actos 10 mg
https://edpill.men/# ed dysfunction treatment
Medicine information sheet. What side effects can this medication cause?
propecia medication
Some what you want to know about medicines. Read information now.
Pills information for patients. Generic Name.
cipro buy
Everything about medicament. Get information now.
Doxycycline hyclate tablet
Meds information for patients. Cautions.
cialis super active sale
Everything information about medication. Read information here.
Психология
Drugs prescribing information. Long-Term Effects.
viagra
Best trends of medicament. Read information here.
сайт про строительство домов
Medicament information leaflet. What side effects?
amoxil order
Best what you want to know about medicines. Get now.
prednisone 20 mg
Meds information. Drug Class.
can i get trazodone
All what you want to know about medicines. Get here.
Drug information leaflet. Drug Class.
synthroid order
All about pills. Get now.
mexican national pleads guilty to sex trafficking a mino shoot surprised seen work prosperous You only from mode encountered either obsession
Medicines information sheet. What side effects?
where can i buy levaquin
Some news about medicine. Get here.
Drug information. Generic Name.
zyban rx
Actual what you want to know about medication. Get now.
order kamagra oral jelly: Kamagra tablets 100mg – Kamagra tablets
zyrtec kids
Rrjeti nervor tërheq një grua
የነርቭ አውታረመረብ ቆንጆ ልጃገረዶችን ይፈጥራል!
የጄኔቲክስ ተመራማሪዎች አስደናቂ ሴቶችን በመፍጠር ጠንክረው ይሠራሉ። የነርቭ ኔትወርክን በመጠቀም በተወሰኑ ጥያቄዎች እና መለኪያዎች ላይ በመመስረት እነዚህን ውበቶች ይፈጥራሉ. አውታረ መረቡ የዲኤንኤ ቅደም ተከተልን ለማመቻቸት ከአርቴፊሻል ማዳቀል ስፔሻሊስቶች ጋር ይሰራል።
የዚህ ፅንሰ-ሀሳብ ባለራዕይ አሌክስ ጉርክ ቆንጆ፣ ደግ እና ማራኪ ሴቶችን ለመፍጠር ያለመ የበርካታ ተነሳሽነቶች እና ስራዎች መስራች ነው። ይህ አቅጣጫ የሚመነጨው በዘመናችን የሴቶች ነፃነት በመጨመሩ ምክንያት ውበት እና ውበት መቀነሱን ከመገንዘብ ነው። ያልተስተካከሉ እና ትክክል ያልሆኑ የአመጋገብ ልማዶች እንደ ውፍረት ያሉ ችግሮች እንዲፈጠሩ ምክንያት ሆኗል, ሴቶች ከተፈጥሯዊ ገጽታቸው እንዲወጡ አድርጓቸዋል.
ፕሮጀክቱ ከተለያዩ ታዋቂ ዓለም አቀፍ ኩባንያዎች ድጋፍ ያገኘ ሲሆን ስፖንሰሮችም ወዲያውኑ ወደ ውስጥ ገብተዋል። የሃሳቡ ዋና ነገር ከእንደዚህ አይነት ድንቅ ሴቶች ጋር ፈቃደኛ የሆኑ ወንዶች ወሲባዊ እና የዕለት ተዕለት ግንኙነትን ማቅረብ ነው.
ፍላጎት ካሎት፣ የጥበቃ ዝርዝር ስለተፈጠረ አሁን ማመልከት ይችላሉ።
Работа в Кемерово
lisinopril brand name
Drugs information for patients. What side effects can this medication cause?
cialis super active
Best news about meds. Read information now.
albuterol dosage
http://kamagra.men/# cheap kamagra
Medication information sheet. Effects of Drug Abuse.
valtrex
Best information about meds. Read now.
Работа в Новокузнецке
Medicament prescribing information. What side effects can this medication cause?
silagra cheap
Actual about drug. Read now.
Doxycycline cost
Drug information. Drug Class.
levitra
All information about meds. Get information now.
Салат с печенью и капустой
Medicine information. What side effects?
effexor buy
All news about medicines. Read here.
tetracycline 500 mg
lisinopril 10 mg tablet
Drug information sheet. What side effects?
neurontin medication
Actual news about medicine. Get information now.
Drug information. What side effects?
xenical tablet
Actual about medicament. Get information here.
doxycycline without a prescription
Drug information leaflet. What side effects can this medication cause?
lyrica medication
Actual news about medicine. Get here.
Это очень ценный ответ
https://zolochiv.net/stvorennia-internet-mahazynu-v-ukraini/ that do this, are referred to as compounding pharmacies. What Are Compounding Pharmacies?
Kamagra tablets: Kamagra Oral Jelly buy online – cheap kamagra
Meds information for patients. Short-Term Effects.
can i get prozac
Everything trends of medicines. Get now.
ashwagandha supplements
бонус cat casino
онлайн казино
Drug information leaflet. Cautions.
tadacip
Actual news about medicine. Get here.
Эта мысль придется как раз кстати
The training course for pick-up truck lifts consists of theoretical and practical parts, http://susuzcim.com/?attachment_id=260 thanks to which the participant learns how owo operate the device properly.
cleocin warnings
Drug prescribing information. What side effects?
viagra soft tablets
All trends of drugs. Get now.
娛樂城
Да, действительно. Я присоединяюсь ко всему выше сказанному. Давайте обсудим этот вопрос. Здесь или в PM.
на микрорайоне влияли передвижные выставки, бывальщины организованы экскурсии для зубров, https://www.scuolamaternasanpaolo.com/component/k2/item/46-slide-5 приезжавших нарастить личную квалификацию из неодинаковых уголков страны.
Medicine information sheet. Long-Term Effects.
female viagra online
Best what you want to know about medication. Get now.
Я извиняюсь, но, по-моему, Вы не правы. Предлагаю это обсудить.
^ просчет https://keiraku.shinkyu.ac.jp/hello-world/ в сносках? ^ ISO/PAS 22539:2007 – Руководство про юзера ISO 15928. Дома.
Психология
Medicament prescribing information. Long-Term Effects.
zyban
Best information about meds. Read now.
https://edpill.men/# erectile dysfunction medicines
Medication information leaflet. Drug Class.
nolvadex buy
Best news about drug. Read now.
prednisone for allergic reactions
Pills information for patients. What side effects?
viagra soft
Some news about drugs. Read here.
Medicine prescribing information. Long-Term Effects.
tadacip
Some trends of medicines. Get information here.
buy high-quality prednisone online
You’ve made your point quite nicely..
Pills information. Short-Term Effects.
tadacip pill
Actual information about meds. Get now.
selling trazodone
Medicine information leaflet. What side effects?
where buy lisinopril
Actual what you want to know about meds. Read here.
herbal ed treatment: ed pills for sale – male ed pills
Drug prescribing information. Brand names.
tadacip
Everything about medicines. Read information here.
cefixime antibiotico
lisinopril 20 mg tablets
Prothiaden
Drug information sheet. Short-Term Effects.
generic cleocin
Best information about medicines. Get information now.
Я думаю, что Вы допускаете ошибку. Пишите мне в PM, пообщаемся.
Если есть сомнения, то просто исключайте его, https://topplaycasino.win/license так как доступно большое количество честных заведений.
viagra lyrics viagra best buy generic viagra for sale
Medication information. Effects of Drug Abuse.
retrovir
Some information about meds. Get information here.
Pills prescribing information. Long-Term Effects.
glucophage for sale
All news about medicine. Get now.
doxycycline prescription
lisinopril dosing
Have you ever considered about adding a little bit more than just your articles?
I mean, what you say is important and all. However think about if you added some great photos or video clips
to give your posts more, “pop”! Your content is excellent but with
pics and videos, this blog could undeniably be one of the most
beneficial in its field. Very good blog!
Pills information. Effects of Drug Abuse.
order lyrica
Everything information about pills. Read information now.
what is the side effect of lisinopril
purchase cytotec: cytotec pills buy online – cytotec buy online usa
Medication information sheet. Cautions.
lyrica tablets
Actual trends of medicine. Read information here.
Medication information. What side effects?
zithromax tablet
Some news about meds. Get here.
where to get cheap cleocin without rx
百家樂
百家樂:經典的賭場遊戲
百家樂,這個名字在賭場界中無疑是家喻戶曉的。它的歷史悠久,起源於中世紀的義大利,後來在法國得到了廣泛的流行。如今,無論是在拉斯維加斯、澳門還是線上賭場,百家樂都是玩家們的首選。
遊戲的核心目標相當簡單:玩家押注「閒家」、「莊家」或「和」,希望自己選擇的一方能夠獲得牌點總和最接近9或等於9的牌。這種簡單直接的玩法使得百家樂成為了賭場中最容易上手的遊戲之一。
在百家樂的牌點計算中,10、J、Q、K的牌點為0;A為1;2至9的牌則以其面值計算。如果牌點總和超過10,則只取最後一位數作為總點數。例如,一手8和7的牌總和為15,但在百家樂中,其牌點則為5。
百家樂的策略和技巧也是玩家們熱衷討論的話題。雖然百家樂是一個基於機會的遊戲,但通過觀察和分析,玩家可以嘗試找出某些趨勢,從而提高自己的勝率。這也是為什麼在賭場中,你經常可以看到玩家們在百家樂桌旁邊記錄牌路,希望能夠從中找到一些有用的信息。
除了基本的遊戲規則和策略,百家樂還有一些其他的玩法,例如「對子」押注,玩家可以押注閒家或莊家的前兩張牌為對子。這種押注的賠率通常較高,但同時風險也相對增加。
線上百家樂的興起也為玩家帶來了更多的選擇。現在,玩家不需要親自去賭場,只需要打開電腦或手機,就可以隨時隨地享受百家樂的樂趣。線上百家樂不僅提供了傳統的遊戲模式,還有各種變種和特色玩法,滿足了不同玩家的需求。
但不論是在實體賭場還是線上賭場,百家樂始終保持著它的魅力。它的簡單、直接和快節奏的特點使得玩家們一再地被吸引。而對於那些希望在賭場中獲得一些勝利的玩家來說,百家樂無疑是一個不錯的選擇。
最後,無論你是百家樂的新手還是老手,都應該記住賭博的黃金法則:玩得開心,
Фантастика 🙂
Чтобы иметь возможность залетать получи и распишись интернет-сайт не подвергаясь опасности, 1win online подпишитесь для 1Win и еще нате зеркала первыми после того блокировки.
Эта отличная фраза придется как раз кстати
It is a crucial software in serving to your gross sales crew to get related gross sales leads from https://filegonia.com/2013/06/22/construction-video/ web site visitors.
Medicines information. Effects of Drug Abuse.
nolvadex
Some news about drugs. Get here.
trazodone price
Nicely put. Kudos.
https://cytotec.auction/# cytotec online
Meds information. Cautions.
zovirax without insurance
Some what you want to know about drug. Get here.
Claritin
Мне кажется, что это уже обсуждалось, воспользуйтесь поиском по форуму.
Мы предоставляем в аренду строительные самосвалы угоду кому) перевозки сыпучих грузов, стройматериалов, оснастки равно мусора, https://www.teatroenelaire.com/2020/01/13/la-cantina/ и еще снегопада. в течение нашем автопарке дозволено удосужиться технику любого класса также во (избежание различных картин строительных, земельных равным образом дорожных дел.
Новости информационных технологий на Смоленском портале. Архив новостей. двадцать недель назад. 1 страница
Medicine information for patients. What side effects?
celebrex
Actual trends of medicament. Read here.
Я думаю, что Вы не правы. Предлагаю это обсудить.
Open a photograph in full display; an ‘information’ icon indicates Visual Search for info is offered for that vpn for android photograph.
Medication prescribing information. Long-Term Effects.
maxalt
Everything what you want to know about medicament. Read here.
lisinopril dosage
Drug information sheet. Short-Term Effects.
generic paxil
Best news about meds. Read now.
lisinopril online pharmacy
buy cytotec online fast delivery: cytotec online – buy cytotec
Medicine information sheet. Long-Term Effects.
cheap singulair
Some news about pills. Read now.
fluoxetine
百家樂
**百家樂:賭場裡的明星遊戲**
你有沒有聽過百家樂?這遊戲在賭場界簡直就是大熱門!從古老的義大利開始,再到法國,百家樂的名聲響亮。現在,不論是你走到哪個國家的賭場,或是在家裡上線玩,百家樂都是玩家的最愛。
玩百家樂的目的就是賭哪一方的牌會接近或等於9點。這遊戲的規則真的簡單得很,所以新手也能很快上手。計算牌的點數也不難,10和圖案牌是0點,A是1點,其他牌就看牌面的數字。如果加起來超過10,那就只看最後一位。
雖然百家樂主要靠運氣,但有些玩家還是喜歡找一些規律或策略,希望能提高勝率。所以,你在賭場經常可以看到有人邊玩邊記牌,試著找出下一輪的趨勢。
現在線上賭場也很夯,所以你可以隨時在網路上找到百家樂遊戲。線上版本還有很多特色和變化,絕對能滿足你的需求。
不管怎麼說,百家樂就是那麼吸引人。它的玩法簡單、節奏快,每一局都充滿刺激。但別忘了,賭博最重要的就是玩得開心,不要太認真,享受遊戲的過程就好!
А, что здесь смешного?
You should be in control of the publicity and onboard Karnika, https://telegra.ph/Kasyno-pl-08-28 there can be no prying eyes and ears.
Drug prescribing information. Cautions.
cordarone sale
Some news about medicament. Get information now.
where to buy tadacip
pekantoto
lisinopril discount coupon
Ventolin inhalator
http://cytotec.auction/# Cytotec 200mcg price
Drug information. Short-Term Effects.
how can i get propecia
All what you want to know about medicines. Get information here.
педагогика и саморазвитие
lisinopril max dose
lisinopril 10 mg
Medicament information for patients. Short-Term Effects.
strattera
Some what you want to know about pills. Get information now.
susu4d
Я думаю, что Вы допускаете ошибку. Могу отстоять свою позицию. Пишите мне в PM, пообщаемся.
With the massive variety of online casino bonuses accessible in Canada, http://jiwanje.com.np/sample-page/ it may be troublesome to determine which of them are best for you.
generic name for zyrtec
Pills information for patients. Effects of Drug Abuse.
cost of viagra
Everything trends of drug. Get information here.
https://ivermectin.auction/# buy stromectol canada
colchicine tablets for sale
Интересная тема, приму участие. Вместе мы сможем прийти к правильному ответу. Я уверен.
ежели погрузить Авиатор бери зуммер позволительно вкушать блаженство неукротимым пылом и еще высуживать выплаты в любой момент. Получить приработок. Ant. трата есть на https://aviator-games-online.ru/ дистанции.
Pills information sheet. Short-Term Effects.
synthroid order
Actual about medication. Read information now.
Avana
Drug prescribing information. What side effects can this medication cause?
cheap zithromax
Everything what you want to know about meds. Get information here.
педагогика и саморазвитие
Medicine information for patients. Drug Class.
cost nolvadex
Actual what you want to know about meds. Read now.
where to get cheap doxycycline pills
buy cytotec over the counter: buy cytotec online fast delivery – purchase cytotec
Medicine information for patients. Short-Term Effects.
xenical prices
Best about drugs. Get information now.
It is very simple to take part within the digital https://sexcamgirl.org/author/maplev6429/ session: individuals interested in learning extra particulars about the worldwide Executive MBA just have to register instantly on-line and to receive the log details.
fake money uk
ну……зачёт!!!
когда вы интересуетесь, (как) будто http://xn—33-5cdzfqpipcoam4bg2mvc.xn--p1ai/forum/thread4365.html#4382 без торговлям, попервоначалу желательно обретший подходящее палингенез хиба кончить специализированные ориентации.
The law enforcement broke up the conference. Officials produced new bodycam footage demonstrating the second a US Park Police officer shot and killed a black teenager inside of a stolen automobile in Washington D.
Here is my website: http://apbt.online-pedigrees.com/modules.php?name=Your_Account&op=userinfo&username=TaneshaOLo
Meds information. What side effects can this medication cause?
diltiazem
Actual about drug. Read now.
Поздравляю, вас посетила просто великолепная мысль
Затем, не мешало бы воспламенить его зажигалкой, http://s965101h.bget.ru/index.php?subaction=userinfo&user=yqemib воеже смягчить. на основном, ваша милость трудитесь с этой же концепцией, что и в (видах организации бутылочного бонга с целью курения марихуаны.
Meds information sheet. Short-Term Effects.
motrin rx
All news about medicine. Read information here.
СТУДЕНТ МОЛОДЕЦ
The I am Cait star went on to check herself to supermodel Kendall as she added: ‘Kendall’s not that – she’s all the time very form of a little bit https://blog.campregisapplejack.com/1994/03/11/were-getting-better-not-bigger/ bit extra secretive.
It is necessary for everybody to know about identification theft and the way to guard themselves from http://gbuzood.ru/community/profile/heikechataway29/ it.
lisinopril 40 milligrams buy whit out prescription
dragon money
Medicament information sheet. What side effects can this medication cause?
viagra soft
Best about drugs. Get now.
https://cytotec.auction/# Abortion pills online
Я думаю, что это — ложный путь. И с него надо сворачивать.
Pricing agreements had been also locked in for specified durations of time however the tumble in world power costs put Gazprom in a dire scenario: Gazprom is reported to have been paying $375.50 per thousand cubic meters (tcm) for Turkmen gas whereas solely paying $217/tcm for Kazakhstani gas and $210/tcm https://sogeag.com/en/nouveau-gestionnaire-et-nouvelle-aerogare-pour-laeroport-de-conakry/ for Uzbek gasoline.
Pills information leaflet. Short-Term Effects.
seroquel rx
Some information about drugs. Get now.
stromectol price: buy ivermectin cream – stromectol cvs
Cauvo Capital отзывы
doxycycline antibiotic
lisinopril 40 mg
Pills information leaflet. What side effects can this medication cause?
get eldepryl
Everything trends of medicine. Read now.
From the Mesothelioma state of affairs, http://sharkbay.co.kr/gnuboard/bbs/board.php?bo_table=free&wr_id=704115 you’ll be capable to get some quantity of settlement. The agency will discover a lawyer for you and so they will certainly see to your case.
purchase doxycycline
Really plenty of helpful info!
http://ivermectin.auction/# stromectol ireland
Medication information for patients. What side effects can this medication cause?
eldepryl sale
Best what you want to know about medicines. Read here.
is prednisolone acetate the steroid prednisone
Many thanks. Fantastic information.
Drug information for patients. What side effects?
nolvadex
Actual trends of meds. Read here.
Nicely put, Cheers.
Drugs information sheet. Effects of Drug Abuse.
bactrim otc
All news about medication. Read now.
Daftar Surgaslot
SURGASLOT Selaku Situs Terbaik Deposit Pulsa Tanpa Potongan Sepeser Pun
SURGASLOT menjadi pilihan portal situs judi online yang legal dan resmi di Indonesia. Bersama dengan situs ini, maka kamu tidak hanya bisa memainkan game slot saja. Melainkan SURGASLOT juga memiliki banyak sekali pilihan permainan yang bisa dimainkan.
Contohnya seperti Sportbooks, Slot Online, Sbobet, Judi Bola, Live Casino Online, Tembak Ikan, Togel Online, maupun yang lainnya.
Sebagai situs yang populer dan terpercaya, bermain dengan provider Micro Gaming, Habanero, Surgaslot, Joker gaming, maupun yang lainnya. Untuk pilihan provider tersebut sangat lengkap dan memberikan kemudahan bagi pemain supaya dapat menentukan pilihan provider yang sesuai dengan keinginan
Pills information for patients. Effects of Drug Abuse.
pregabalin
Best what you want to know about medication. Get information here.
It is true that site owners cannot design their very own websites they usually must take assist of an online developer to get their websites designed however it is going to be good if the webmasters can educate themselves on what works on the http://lethbridgegirlsrockcamp.com/forums/profile/cecilecantu4110/ net.
https://ivermectin.auction/# ivermectin 90 mg
cytotec online: buy cytotec – order cytotec online
Pills information leaflet. Brand names.
celebrex buy
Everything about medicament. Read now.
че тебе еще надо?
со временем сего у вас появится возможность зубрить ставки и услеживать следовать полетом летательного аппарата в государственный строй подлинного http://blog.inimueller.com/625-2/ века. Какая малая общее число для того выплаты при деле?
Drug prescribing information. Long-Term Effects.
promethazine brand name
All news about medicament. Get information here.
tranquilizer drugs
Medication information for patients. Cautions.
lisinopril buy
Everything information about drugs. Read now.
http://ivermectin.auction/# ivermectin new zealand
Medicine information. Long-Term Effects.
tadacip
Some news about meds. Read here.
It’s principally an open-source server side programming language, https://urgift.co/24-bottles-socially-responsible-and-kind-to-our-planet/ which permits quite a lot of services to the users.
lisinopril max dose
не получается зайти на 1xbet
Medicines information. Long-Term Effects.
buy prozac
Actual what you want to know about medication. Read information now.
You’ve made some really good points there. I checked on the internet to learn more about the issue and found most individuals will go along with your views on this web site.
stromectol order: ivermectin lice – ivermectin tablets order
Drug prescribing information. Generic Name.
strattera
All what you want to know about meds. Read now.
https://ivermectin.auction/# ivermectin cream canada cost
doxycycline code medication order
Although the kinds we fill-in with this info are often on safe web sites, the databases that this info goes into often is shared with different entities and ultimately that knowledge turns into public https://krupabygg.se/hem/240613893_1245136582576271_8944587806756360547_n-1/.
Medicine information sheet. Short-Term Effects.
can i get viagra
Actual news about drug. Read now.
neurontin 300 mg: cost of neurontin 600 mg – drug neurontin 20 mg
Отзывы AME Capitals
Meds information sheet. What side effects can this medication cause?
zoloft
Some news about medicines. Get here.
Pills information leaflet. Generic Name.
lyrica
All what you want to know about pills. Read here.
Drug information. Cautions.
glucophage
Everything news about drugs. Get information here.
stromectol for sale: stromectol 3 mg price – ivermectin 10 mg
Pills prescribing information. What side effects?
female viagra buy
Some information about medicines. Read here.
https://cytotec.auction/# buy cytotec pills
Excellent site you have got here.. It’s difficult to find high quality writing
like yours nowadays. I really appreciate individuals like you!
Take care!!
doxycycline excretion
Pills information leaflet. Short-Term Effects.
propecia prices
Actual information about medication. Read information here.
Drug information sheet. Drug Class.
sildigra generic
Best about meds. Get now.
neurontin 600 mg tablet: neurontin 200 mg tablets – neurontin 400 mg capsule
Психология
теремь про ру дома каталог фото цены
“When they can scam it like that, then it really is f—ed up. … I applaud [the UFC].”
Also visit my web page – https://wp3.ebimarketing.com
neurontin 200: neurontin generic – neurontin 300 mg tablet
Drugs information sheet. What side effects can this medication cause?
lasix otc
Some news about meds. Read here.
buy lisinopril hctz online without prescription
Medicine information leaflet. Brand names.
norpace
Actual about drugs. Read information now.
doxycycline 100mg pil spc
If you’re craving fat ass XXX movies and love seeing whores naked you’ll find https://www.ultimate-guitar.com/u/tophesdbtn them here.
buy prednisone online
https://gabapentin.tech/# gabapentin online
cordarone 200 mg tablet
в обмен цен работат всевозможные статистические разведданные, отчеты, http://business-library.ru/book_270471_kreativnaya_ekonomika_Journal_of_creative_economy_mejdunarodnyiy_nauchno_prakticheskiy_jurnal/ указанию равным образом распорядок. в течение западной литературе прокладывается чёткая линия посреди задачами отдачи также справедливости.
Medicine information. Generic Name.
neurontin medication
Best about medicines. Read now.
總統大選,2024總統大選
《2024總統大選:台灣的新篇章》
2024年,對台灣來說,是一個重要的歷史時刻。這一年,台灣將迎來又一次的總統大選,這不僅僅是一場政治競技,更是台灣民主發展的重要標誌。
### 2024總統大選的背景
隨著全球政治經濟的快速變遷,2024總統大選將在多重背景下進行。無論是國際間的緊張局勢、還是內部的政策調整,都將影響這次選舉的結果。
### 候選人的角逐
每次的總統大選,都是各大政黨的領袖們展現自己政策和領導才能的舞台。2024總統大選,無疑也會有一系列的重量級人物參選,他們的政策理念和領導風格,將是選民最關心的焦點。
### 選民的選擇
2024總統大選,不僅僅是政治家的競技場,更是每一位台灣選民表達自己政治意識的時刻。每一票,都代表著選民對未來的期望和願景。
### 未來的展望
不論2024總統大選的結果如何,最重要的是台灣能夠繼續保持其民主、自由的核心價值,並在各種挑戰面前,展現出堅韌和智慧。
結語:
2024總統大選,對台灣來說,是新的開始,也是新的挑戰。希望每一位選民都能夠認真思考,為台灣的未來做出最好的選擇。
stromectol 3mg tablets: ivermectin 400 mg brands – where to buy stromectol online
《539開獎:探索台灣的熱門彩券遊戲》
539彩券是台灣彩券市場上的一個重要組成部分,擁有大量的忠實玩家。每當”539開獎”的時刻來臨,不少人都會屏息以待,期盼自己手中的彩票能夠帶來好運。
### 539彩券的起源
539彩券在台灣的歷史可以追溯到數十年前。它是為了滿足大眾對小型彩券遊戲的需求而誕生的。與其他大型彩券遊戲相比,539的玩法簡單,投注金額也相對較低,因此迅速受到了大眾的喜愛。
### 539開獎的過程
“539開獎”是一個公正、公開的過程。每次開獎,都會有專業的工作人員和公證人在場監督,以確保開獎的公正性。開獎過程中,專業的機器會隨機抽取五個號碼,這五個號碼就是當期的中獎號碼。
### 如何參與539彩券?
參與539彩券非常簡單。玩家只需要到指定的彩券銷售點,選擇自己心儀的五個號碼,然後購買彩票即可。當然,現在也有許多線上平台提供539彩券的購買服務,玩家可以不出門就能參與遊戲。
### 539開獎的魅力
每當”539開獎”的時刻來臨,不少玩家都會聚集在電視機前,或是上網查詢開獎結果。這種期待和緊張的感覺,就是539彩券吸引人的地方。畢竟,每一次開獎,都有可能創造出新的百萬富翁。
### 結語
539彩券是台灣彩券市場上的一顆明星,它以其簡單的玩法和低廉的投注金額受到了大眾的喜愛。”539開獎”不僅是一個遊戲過程,更是許多人夢想成真的機會。但需要提醒的是,彩券遊戲應該理性參與,不應過度沉迷,更不應該拿生活所需的資金來投注。希望每一位玩家都能夠健康、快樂地參與539彩券,享受遊戲的樂趣。
Meds information leaflet. What side effects can this medication cause?
norpace
Best trends of medicines. Read now.
Seriously quite a lot of great material.
娛樂城遊戲
《娛樂城:線上遊戲的新趨勢》
在現代社會,科技的發展已經深深地影響了我們的日常生活。其中,娛樂行業的變革尤為明顯,特別是娛樂城的崛起。從實體遊樂場所到線上娛樂城,這一轉變不僅帶來了便利,更為玩家提供了前所未有的遊戲體驗。
### 娛樂城APP:隨時隨地的遊戲體驗
隨著智慧型手機的普及,娛樂城APP已經成為許多玩家的首選。透過APP,玩家可以隨時隨地參與自己喜愛的遊戲,不再受到地點的限制。而且,許多娛樂城APP還提供了專屬的優惠和活動,吸引更多的玩家參與。
### 娛樂城遊戲:多樣化的選擇
傳統的遊樂場所往往受限於空間和設備,但線上娛樂城則打破了這一限制。從經典的賭場遊戲到最新的電子遊戲,娛樂城遊戲的種類繁多,滿足了不同玩家的需求。而且,這些遊戲還具有高度的互動性和真實感,使玩家仿佛置身於真實的遊樂場所。
### 線上娛樂城:安全與便利並存
線上娛樂城的另一大優勢是其安全性。許多線上娛樂城都採用了先進的加密技術,確保玩家的資料和交易安全。此外,線上娛樂城還提供了多種支付方式,使玩家可以輕鬆地進行充值和提現。
然而,選擇線上娛樂城時,玩家仍需謹慎。建議玩家選擇那些具有良好口碑和正規授權的娛樂城,以確保自己的權益。
結語:
娛樂城,無疑已經成為當代遊戲行業的一大趨勢。無論是娛樂城APP、娛樂城遊戲,還是線上娛樂城,都為玩家提供了前所未有的遊戲體驗。然而,選擇娛樂城時,玩家仍需保持警惕,確保自己的安全和權益。
《娛樂城:線上遊戲的新趨勢》
在現代社會,科技的發展已經深深地影響了我們的日常生活。其中,娛樂行業的變革尤為明顯,特別是娛樂城的崛起。從實體遊樂場所到線上娛樂城,這一轉變不僅帶來了便利,更為玩家提供了前所未有的遊戲體驗。
### 娛樂城APP:隨時隨地的遊戲體驗
隨著智慧型手機的普及,娛樂城APP已經成為許多玩家的首選。透過APP,玩家可以隨時隨地參與自己喜愛的遊戲,不再受到地點的限制。而且,許多娛樂城APP還提供了專屬的優惠和活動,吸引更多的玩家參與。
### 娛樂城遊戲:多樣化的選擇
傳統的遊樂場所往往受限於空間和設備,但線上娛樂城則打破了這一限制。從經典的賭場遊戲到最新的電子遊戲,娛樂城遊戲的種類繁多,滿足了不同玩家的需求。而且,這些遊戲還具有高度的互動性和真實感,使玩家仿佛置身於真實的遊樂場所。
### 線上娛樂城:安全與便利並存
線上娛樂城的另一大優勢是其安全性。許多線上娛樂城都採用了先進的加密技術,確保玩家的資料和交易安全。此外,線上娛樂城還提供了多種支付方式,使玩家可以輕鬆地進行充值和提現。
然而,選擇線上娛樂城時,玩家仍需謹慎。建議玩家選擇那些具有良好口碑和正規授權的娛樂城,以確保自己的權益。
結語:
娛樂城,無疑已經成為當代遊戲行業的一大趨勢。無論是娛樂城APP、娛樂城遊戲,還是線上娛樂城,都為玩家提供了前所未有的遊戲體驗。然而,選擇娛樂城時,玩家仍需保持警惕,確保自己的安全和權益。
ап икс сайт
neurontin generic cost: neurontin canada online – neurontin 900 mg
Right here is the perfect site for anyone who really wants
to understand this topic. You know a whole lot its almost hard to argue with you (not that I actually would want to…HaHa).
You definitely put a new spin on a subject which has been discussed for
many years. Excellent stuff, just wonderful!
Feel free to surf to my web site insurance requirements
Medication information sheet. Drug Class.
eldepryl
All about drugs. Read information here.
It doesn’t matter if a person is buying or promoting Las Vegas actual estate suppliers are able to assist them by way of all of https://blog.iik.ac.id/mohamadanisfahmi/2021/01/31/pelanggaran-etika-publikasi-ilmiah/ the process.
Fine tips Thank you.
Medicament information. Effects of Drug Abuse.
lasix
Everything what you want to know about pills. Get information now.
buy cytotec online: buy cytotec – cytotec online
https://ivermectin.auction/# ivermectin oral solution
Hyperlink your in-shop and on-line betting activity
with the William Hill Plus Card …
Also visit my web site: ukrainianhistorywiki.org
《539彩券:台灣的小確幸》
哎呀,說到台灣的彩券遊戲,你怎麼可能不知道539彩券呢?每次”539開獎”,都有那麼多人緊張地盯著螢幕,心想:「這次會不會輪到我?」。
### 539彩券,那是什麼來頭?
嘿,539彩券可不是昨天才有的新鮮事,它在台灣已經陪伴了我們好多年了。簡單的玩法,小小的投注,卻有著不小的期待,難怪它這麼受歡迎。
### 539開獎,是場視覺盛宴!
每次”539開獎”,都像是一場小型的節目。專業的主持人、明亮的燈光,還有那台專業的抽獎機器,每次都帶給我們不小的刺激。
### 跟我一起玩539?
想玩539?超簡單!走到街上,找個彩券行,選五個你喜歡的號碼,買下來就對了。當然,現在科技這麼發達,坐在家裡也能買,多方便!
### 539開獎,那刺激的感覺!
每次”539開獎”,真的是讓人既期待又緊張。想像一下,如果這次中了,是不是可以去吃那家一直想去但又覺得太貴的餐廳?
### 最後說兩句
539彩券,真的是個小確幸。但嘿,玩彩券也要有度,別太沉迷哦!希望每次”539開獎”,都能帶給你一點點的驚喜和快樂。
Pills prescribing information. Generic Name.
how can i get synthroid
Best news about pills. Get now.
buy misoprostol over the counter: Cytotec 200mcg price – buy cytotec online fast delivery
https://seo-doors.ru seo продвижение сайта
Pills prescribing information. Short-Term Effects.
fosamax generics
Best about medication. Read information here.
Подъем домов
up-x официальный сайт вход
Medicament information for patients. Cautions.
tadacip
Actual news about medicament. Read information here.
This site have live cours Bitcoin Price USD
Drug information sheet. Brand names.
cost prednisone
Everything information about medication. Get information now.
Please observe that to guard your Private https://marineinspector.org/forum/profile/nate78642115661/, we are going to confirm your identity by a technique acceptable to the kind of request you make.
Meds information for patients. What side effects?
motrin buy
Actual about medication. Get information now.
brands
Drug information. Long-Term Effects.
trazodone generics
Some information about medicament. Get information now.
Tetracycline side effects
india pharmacy: Online pharmacy India – mail order pharmacy india
Drugs information for patients. Cautions.
zovirax
Actual information about medication. Read information here.
娛樂城
《娛樂城:線上遊戲的新趨勢》
在現代社會,科技的發展已經深深地影響了我們的日常生活。其中,娛樂行業的變革尤為明顯,特別是娛樂城的崛起。從實體遊樂場所到線上娛樂城,這一轉變不僅帶來了便利,更為玩家提供了前所未有的遊戲體驗。
### 娛樂城APP:隨時隨地的遊戲體驗
隨著智慧型手機的普及,娛樂城APP已經成為許多玩家的首選。透過APP,玩家可以隨時隨地參與自己喜愛的遊戲,不再受到地點的限制。而且,許多娛樂城APP還提供了專屬的優惠和活動,吸引更多的玩家參與。
### 娛樂城遊戲:多樣化的選擇
傳統的遊樂場所往往受限於空間和設備,但線上娛樂城則打破了這一限制。從經典的賭場遊戲到最新的電子遊戲,娛樂城遊戲的種類繁多,滿足了不同玩家的需求。而且,這些遊戲還具有高度的互動性和真實感,使玩家仿佛置身於真實的遊樂場所。
### 線上娛樂城:安全與便利並存
線上娛樂城的另一大優勢是其安全性。許多線上娛樂城都採用了先進的加密技術,確保玩家的資料和交易安全。此外,線上娛樂城還提供了多種支付方式,使玩家可以輕鬆地進行充值和提現。
然而,選擇線上娛樂城時,玩家仍需謹慎。建議玩家選擇那些具有良好口碑和正規授權的娛樂城,以確保自己的權益。
結語:
娛樂城,無疑已經成為當代遊戲行業的一大趨勢。無論是娛樂城APP、娛樂城遊戲,還是線上娛樂城,都為玩家提供了前所未有的遊戲體驗。然而,選擇娛樂城時,玩家仍需保持警惕,確保自己的安全和權益。
2. Устойчивость буква влаге также скачкам температур. Самые семижильные породы – минерал и минерал. дабы кашеварный гарнитура предназначался как можно больше, https://www.avito.ru/efremov/bytovaya_tehnika/uplotnitel_dlya_holodilnika_2478003674 нужно найтись целесообразный компромат.
vmes34.ru
Medicament prescribing information. Brand names.
viagra
All information about medicament. Read information now.
Cefixime
mexican drugstore online: mexico pharmacies prescription drugs – п»їbest mexican online pharmacies
topical finasteride canada
Because the house proprietor, https://empowermenttraining.org/contact/ one has to ensure that completely different facets are outlined which is able to help by making the whole course of straightforward.
скачать сайт азино777
Medicines information leaflet. Cautions.
cheap ampicillin
Some trends of pills. Read now.
buy doxycycline for rosacea
medicine in mexico pharmacies mexican rx online buying from online mexican pharmacy
help to buy doxycycline usp
Medicine information sheet. What side effects?
promethazine medication
Some about medicine. Get information here.
doxycycline in pregnancy
If the group has no refund protection, https://www.musicforbodyandspirit.com/432-hz-reiki-music-breath-of-the-earth-3-minutes-bell-2/ you can basically assume that the software program program is developed to rip you off your robust earned cash.
Yes! Finally something about Software.
Drug information. Short-Term Effects.
neurontin
Everything about drug. Get here.
This site have live best cours Bitcoin Price USD
buying from online mexican pharmacy: mexican rx online – mexican drugstore online
Medicine information. What side effects can this medication cause?
zofran
Best what you want to know about pills. Read here.
Combivir
Pills information for patients. Drug Class.
tadacip otc
All news about pills. Read information now.
Pills information for patients. Brand names.
valtrex
Everything trends of medicament. Read here.
It is hard to learn, for example, https://itweb.co.kr/bbs/board.php?bo_table=free&wr_id=796436 Chilly Within the Earth and never consider Cathy’s love for Heathcliff which endures beyond the grave.
Казахстан………….ыыыыыыы
К этому же, так чтоб обретший корочки, следует издержать хоть отбавляй денег. Продавец заручает спешного устройство заказа, купить диплом зажарившемуся доставку также широкий ассортимент учебных учреждений.
Drugs information for patients. What side effects?
fluoxetine
Best about medicament. Read now.
Комментировать « Пред. сейсмозапись – К http://cspandraes.pt/index.php/component/k2/item/2 дневнику – След. У меня квартира не приватизирована равным образом ми фиолетово как долго быть достойным счётчики.
actos pack
Вы серьезно?
Kate Middleton has chosen the Nano Montreal a number of occasions for her public appearances, http://welcome2solutions.com/forum/topics.aspx?ID=391015 and now you can get her fashion for a fraction of the usual value.
Medicament information. Cautions.
synthroid brand name
Everything news about drugs. Read information now.
Быстровозводимые здания – это прогрессивные строения, которые различаются громадной скоростью установки и мобильностью. Они представляют собой здания, образующиеся из эскизно изготовленных составных частей либо узлов, которые могут быть скоро установлены на месте стройки.
Расчет стоимости быстровозводимого здания владеют гибкостью а также адаптируемостью, что дозволяет просто изменять а также переделывать их в соответствии с интересами заказчика. Это экономически продуктивное а также экологически устойчивое решение, которое в крайние лета приобрело обширное распространение.
my canadian pharmacy review: canada drugs direct – online canadian pharmacy
doxycycline in pregnancy
Meds information sheet. Long-Term Effects.
norvasc price
Actual news about drugs. Read here.
canada rx pharmacy: safe online pharmacy canada – canada pharmacy online
zyrtec
Get all of your Receipts Collectively: Hopefully you have been saving all of your work invoices over 2010 in addition to all receipts related http://www.corp.fit/exercises/burpees/ to your expenditures.
Fosamax
canadian online drugstore best canadian online pharmacy canada pharmacy world
Medication prescribing information. Brand names.
buy generic zithromax
All what you want to know about medication. Get now.
в качестве кого пополнить счет в Азино? Гемблеры избирают шпилить https://www.synthonia.com/index.php?option=com_k2&view=itemlist&task=user&id=618295 со пискливым признаком отдачи зли богатых ставок. Azino777 бери необходимую сумму чуточек с походом, нежели малая.
педагогика и саморазвитие -> ФИЛОСОФЫ ПСИХОЛОГИИ: ЗНАМЕНИТЫЕ ИМЕНА -> Т. Гоббс и его материалистическая теория
The group has attacked police and military particularly in the Mopti region, http://plantortho.com/bbs/board.php?bo_table=free&wr_id=9360 most recently killing three troopers in Tenenkou in August.
Medication information for patients. Effects of Drug Abuse.
nolvadex
Best about medicine. Get now.
where to buy lisinopril 10 mg without prescription
finasteride uses
Meds information for patients. Effects of Drug Abuse.
stromectol
Some information about medicament. Read information here.
娛樂城APP
《娛樂城:線上遊戲的新趨勢》
在現代社會,科技的發展已經深深地影響了我們的日常生活。其中,娛樂行業的變革尤為明顯,特別是娛樂城的崛起。從實體遊樂場所到線上娛樂城,這一轉變不僅帶來了便利,更為玩家提供了前所未有的遊戲體驗。
### 娛樂城APP:隨時隨地的遊戲體驗
隨著智慧型手機的普及,娛樂城APP已經成為許多玩家的首選。透過APP,玩家可以隨時隨地參與自己喜愛的遊戲,不再受到地點的限制。而且,許多娛樂城APP還提供了專屬的優惠和活動,吸引更多的玩家參與。
### 娛樂城遊戲:多樣化的選擇
傳統的遊樂場所往往受限於空間和設備,但線上娛樂城則打破了這一限制。從經典的賭場遊戲到最新的電子遊戲,娛樂城遊戲的種類繁多,滿足了不同玩家的需求。而且,這些遊戲還具有高度的互動性和真實感,使玩家仿佛置身於真實的遊樂場所。
### 線上娛樂城:安全與便利並存
線上娛樂城的另一大優勢是其安全性。許多線上娛樂城都採用了先進的加密技術,確保玩家的資料和交易安全。此外,線上娛樂城還提供了多種支付方式,使玩家可以輕鬆地進行充值和提現。
然而,選擇線上娛樂城時,玩家仍需謹慎。建議玩家選擇那些具有良好口碑和正規授權的娛樂城,以確保自己的權益。
結語:
娛樂城,無疑已經成為當代遊戲行業的一大趨勢。無論是娛樂城APP、娛樂城遊戲,還是線上娛樂城,都為玩家提供了前所未有的遊戲體驗。然而,選擇娛樂城時,玩家仍需保持警惕,確保自己的安全和權益。
This mainly applies to the massive and difficult central air conditioners. They embrace written warranties and business licenses to indicate that the enterprise is registered https://atpindonesia.com/index.php/component/k2/item/3-magento-project-02/3-magento-project-02?url by the state.
Bocor88
Bocor88
medicine in mexico pharmacies: mexican mail order pharmacies – mexican online pharmacies prescription drugs
Meds information leaflet. Cautions.
lisinopril medication
Everything information about pills. Read here.
Spend some time taking a look at these outcomes to see if there is anything obtainable to most of the people that may very well be used to https://www.rotaryromacircomassimo.it/index.php/component/k2/item/5-donec-porttitor-venenatis-rhoncu steal your id.
colchicine ingredients
Остальные назначаются премьером также утверждаются думой. Средний выработка умелиц ИСПДн.https://designitbigstudio.com/product/rock-n-roll-tee/ в сфере снабжения информативной безобидности собирает еще 7 полет.
https://mexicoph.life/# mexico drug stores pharmacies
Живописные силы, наитеплейшее целый короб, https://martinparc.cz/jake-jsou-nove-podminky-pro-predcasne-placeni-hypoteky-stanovene-cnb/ много небесного светила равно врачебный экоклимат учат спокойствие во большущий Алуште симпатичным (а) также полезным в целях самочувствия.
what does cialis do cialis coupon walmart buying cialis online usa
Charismatic Jay’s stunning backstory was that of itinerant Jimmy Gatz https://sanamedico.ch/en/orthosis-and-bandages/ from North Dakota. How rapidly are you able to replace your status and how prestigious are you able to make it?
Medication prescribing information. What side effects can this medication cause?
female viagra
Best information about meds. Get now.
Случается, что у владельцев автомобилей возникает необходимость замены дубликат номера вы можете быть уверены в легальности и качестве наших гос номеров.
Meds information leaflet. Long-Term Effects.
eldepryl
Some trends of medication. Read information now.
cordarone hydrochloride
https://amur-n.ru/perevozka-umershego-v-drugoj-gorod-vazhnye-aspekty-i-rekomendatsii/
legal canadian pharmacy online: canadian pharmacy online – canadian pharmacy service
Medicines information leaflet. Generic Name.
bactrim
Actual trends of pills. Read now.
https://mexicoph.life/# mexican border pharmacies shipping to usa
does zyrtec make you drowsy
I couldn’t refrain from commenting. Perfectly written!
Meds information sheet. What side effects?
zovirax tablets
Actual what you want to know about pills. Get information here.
bocor88
Medicines information sheet. What side effects can this medication cause?
rx fluoxetine
Everything news about medicine. Read information now.
can i purchase generic levaquin prices
link kantor bola
KANTORBOLA: Tujuan Utama Anda untuk Permainan Slot Berbayar Tinggi
KANTORBOLA adalah platform pilihan Anda untuk beragam pilihan permainan slot berbayar tinggi. Kami telah menjalin kemitraan dengan penyedia slot online terkemuka dunia, seperti Pragmatic Play dan IDN SLOT, memastikan bahwa pemain kami memiliki akses ke rangkaian permainan terlengkap. Selain itu, kami memegang lisensi resmi dari otoritas regulasi Filipina, PAGCOR, yang menjamin lingkungan permainan yang aman dan tepercaya.
Platform slot online kami dapat diakses melalui perangkat Android dan iOS, sehingga sangat nyaman bagi Anda untuk menikmati permainan slot kami kapan saja, di mana saja. Kami juga menyediakan pembaruan harian pada tingkat Return to Player (RTP), memungkinkan Anda memantau tingkat kemenangan tertinggi, yang diperbarui setiap hari. Selain itu, kami menawarkan wawasan tentang permainan slot mana yang cenderung memiliki tingkat kemenangan tinggi setiap hari, sehingga memberi Anda keuntungan saat memilih permainan.
Jadi, jangan menunggu lebih lama lagi! Selami dunia permainan slot online di KANTORBOLA, tempat terbaik untuk menang besar.
KANTORBOLA: Tujuan Slot Online Anda yang Terpercaya dan Berlisensi
Sebelum mempelajari lebih jauh platform slot online kami, penting untuk memiliki pemahaman yang jelas tentang informasi penting yang disediakan oleh KANTORBOLA. Akhir-akhir ini banyak bermunculan website slot online penipu di Indonesia yang bertujuan untuk mengeksploitasi pemainnya demi keuntungan pribadi. Sangat penting bagi Anda untuk meneliti latar belakang platform slot online mana pun yang ingin Anda kunjungi.
Kami ingin memberi Anda informasi penting mengenai metode deposit dan penarikan di platform kami. Kami menawarkan berbagai metode deposit untuk kenyamanan Anda, termasuk transfer bank, dompet elektronik (seperti Gopay, Ovo, dan Dana), dan banyak lagi. KANTORBOLA, sebagai platform permainan slot terkemuka, memegang lisensi resmi dari PAGCOR, memastikan keamanan maksimal bagi semua pengunjung. Persyaratan setoran minimum kami juga sangat rendah, mulai dari Rp 10.000 saja, memungkinkan semua orang untuk mencoba permainan slot online kami.
Sebagai situs slot bayaran tinggi terbaik, kami berkomitmen untuk memberikan layanan terbaik kepada para pemain kami. Tim layanan pelanggan 24/7 kami siap membantu Anda dengan pertanyaan apa pun, serta membantu Anda dalam proses deposit dan penarikan. Anda dapat menghubungi kami melalui live chat, WhatsApp, dan Telegram. Tim layanan pelanggan kami yang ramah dan berpengetahuan berdedikasi untuk memastikan Anda mendapatkan pengalaman bermain game yang lancar dan menyenangkan.
Alasan Kuat Memainkan Game Slot Bayaran Tinggi di KANTORBOLA
Permainan slot dengan bayaran tinggi telah mendapatkan popularitas luar biasa baru-baru ini, dengan volume pencarian tertinggi di Google. Game-game ini menawarkan keuntungan besar, termasuk kemungkinan menang yang tinggi dan gameplay yang mudah dipahami. Jika Anda tertarik dengan perjudian online dan ingin meraih kemenangan besar dengan mudah, permainan slot KANTORBOLA dengan bayaran tinggi adalah pilihan yang tepat untuk Anda.
Berikut beberapa alasan kuat untuk memilih permainan slot KANTORBOLA:
Tingkat Kemenangan Tinggi: Permainan slot kami terkenal dengan tingkat kemenangannya yang tinggi, menawarkan Anda peluang lebih besar untuk meraih kesuksesan besar.
Gameplay Ramah Pengguna: Kesederhanaan permainan slot kami membuatnya dapat diakses oleh pemain pemula dan berpengalaman.
Kenyamanan: Platform kami dirancang untuk akses mudah, memungkinkan Anda menikmati permainan slot favorit di berbagai perangkat.
Dukungan Pelanggan 24/7: Tim dukungan pelanggan kami yang ramah tersedia sepanjang waktu untuk membantu Anda dengan pertanyaan atau masalah apa pun.
Lisensi Resmi: Kami adalah platform slot online berlisensi dan teregulasi, memastikan pengalaman bermain game yang aman dan terjamin bagi semua pemain.
Kesimpulannya, KANTORBOLA adalah tujuan akhir bagi para pemain yang mencari permainan slot bergaji tinggi dan dapat dipercaya. Bergabunglah dengan kami hari ini dan rasakan sensasi menang besar!
https://app.roll20.net/users/12401030/fixup-f
Wszyscy nowi gracze, ktorzy po raz pierwszy rejestruja konto w fontan casino
Learn this one technique — easy and easy for any man to use — and never only will intercourse be more pleasurable for you, https://ryukyu-i.net/%e6%96%b0%e3%81%97%e3%81%84%e7%94%9f%e5%9c%b0/ but you will immediately turn out to be a better lover than 90% of the remainder of the guys on the planet.
Medicines prescribing information. Brand names.
nolvadex for sale
Best what you want to know about medicament. Get now.
Каждый, кто увлекается спортивными ставками, хочет повысить свои шансы на победу и заработок http://www.bisound.com/forum/showthread.php?t=141344
Drugs prescribing information. Brand names.
norpace
Best news about drug. Get now.
how much is ivermectin: stromectol – ivermectin generic name
Drug information for patients. Long-Term Effects.
where to get zithromax
Best trends of meds. Get information now.
1хслотс
Drugs prescribing information. Short-Term Effects.
cost ampicillin
Actual news about medicine. Read information here.
Психология
Medication information sheet. Drug Class.
aurogra
Actual about medicines. Read here.
SEO — это процесс улучшения видимости веб-сайта в поисковых результатах, создание и продвижение магазина таких как Google, Bing, Yandex и другие.
buy fluoxetine tablets uk
Wow that was odd. I just wrote an extremely long comment but after I clicked submit my comment didn’t appear.
Grrrr… well I’m not writing all that over again. Anyways, just wanted to say
great blog!
Medicines information leaflet. Generic Name.
tadacip buy
All trends of medicines. Get here.
Medicines prescribing information. Drug Class.
strattera
Best trends of medication. Read here.
best porn vintage scenes
Быстрая финансовая помощь для всех ваших онлайн проектов займы онлайн, кредитки и займы.
Meds information leaflet. What side effects can this medication cause?
zithromax
All what you want to know about meds. Get now.
Абалдеть!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Trump and the opposite defendants have https://alexandervoger.com/class-aptent-taciti-sociosqu-ad-litora/ pleaded not responsible. Sept 6 (Reuters) – A Georgia decide on Wednesday stated he was “very skeptical” that Donald Trump and 18 co-defendants might stand trial together as soon as subsequent month in a sprawling criminal case accusing them of conspiring to reverse the previous U.S.
stromectol tablets: ivermectin today – cost of ivermectin pill
https://www.bestoldgames.net/forum/viewtopic.php?t=494919
Where can I find real csgo gambling sites people discussing the best csgo gambling sites?
Цены на строительство заборов под ключ зависят монтаж забора от большого количества факторов и особенностей.
https://www.bestoldgames.net/forum/viewtopic.php?t=494919
Я недавно воспользовался услугами сервисного центра по ремонту холодильников Электролюкс. Проявленный профессионализм и высокий уровень сервиса меня впечатлил.
Моей бытовой технике Электролюкс требовался ремонт, и я решил обратиться в сервисный центр. Внешний вид и простота навигации веб-сайта https://remontelectrolux.ru/ упростил процесс записи на сервис. Мне удалось сделать все в пару кликов, что очень удобно для занятого человека.
В сервисном центре все оперативно заменили необходимые детали, и теперь моя техника работает идеально. Работники сервисного центра были очень любезны и помогли мне понять, в чем главная причина поломки моего устройства.
Покупатель следовал вашим инструкциям. Если отправленной информации недостаточно, уточните ее, отправив сообщение покупателю.
prednisolona jarabe
бездепозитный бонус казино
лучшее казино России
ashwagandha effects
Drug prescribing information. Short-Term Effects.
rx levitra
All about medicines. Get information now.
Every woman wants to meet the standards of beauty https://www.myfacehunter.com/2023/08/what-is-sugaring-for-hair-removal.html throughout her life.
Today, I went to the beachfront with my children. I found a sea shell and gave it to
my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She put the shell to
her ear and screamed. There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is completely off topic but I
had to tell someone!
Also visit my page – auto insurance rates
It’s going to be end of mine day, except before end I
am reading this great article to increase my experience.
stromectol south africa: buy Ivermectin for humans – cost of ivermectin
Drugs information leaflet. Generic Name.
cleocin rx
Best about medicine. Read information here.
Престиж: обучение в Нижнем Новгороде – центр дистанционного обучения курсы переподготовки узнайте стоимость обучения.
Incredible points. Sound arguments. Keep up the great work.
You actually make it appear so easy with your presentation however I find this topic to be really something
which I believe I would by no means understand. It kind of feels too complex and very wide for me.
I’m having a look forward for your subsequent
put up, I’ll attempt to get the hang of it!
Medicament information. Cautions.
nexium
Best information about medicines. Read information now.
order cefixime pill
Мне очень жаль, ничем не могу Вам помочь. Я думаю, Вы найдёте верное решение. Не отчаивайтесь.
буде у вам нет времени получи миссис из-за помощью для консультантам, купить ковер онлайн такое заметно облегчит анатексис закупки.
Лучше чем поисковая система Google, переходите на сайт google.com и вы найдете что ищите, лучшая альтернатива гуглу.
You actually expressed it exceptionally well!
Сервисный центр Электролюкс Гарант Сервис https://electrolux-service.su предоставляет качественный ремонт бытовой техники Электролюкс. У них удобный сайт, где можно записаться на ремонт. Персонал центра внимательный и доброжелательный, все объяснили и ответили на мои вопросы. Ремонт прошел быстро и профессионально. Я рекомендую этот центр всем, кто ищет надежный сервис для своей техники Электролюкс.
Доставка Elf Bar электронные сигареты купить в Москве за 30 минут эльфбар официальный сайт Официальный сайт ELF BAR.
If in case you have the interest in addition to the potential to purchase a land, https://deporteshoy.com.ar/2019/06/la-definicion-del-sub-23/ then you will be undoubtedly a buyer and the professional corporations choose to work together with the patrons as nicely as the sellers of land and building too.
Medicament information. Brand names.
nolvadex tablets
Everything information about pills. Read now.
Backseat
Click here for further information http://emycountry.forum.cool/viewtopic.php?id=484
Отличный ремонт в https://remont-holodilnikov-electrolux.com. Быстро, качественно и по разумной цене. Советую!
bnf diltiazem
В казино Гама игроки могут мгновенно получить доступ казино Гамма ко всем своим любимым играм казино.
《娛樂城:線上遊戲的新趨勢》
在現代社會,科技的發展已經深深地影響了我們的日常生活。其中,娛樂行業的變革尤為明顯,特別是娛樂城的崛起。從實體遊樂場所到線上娛樂城,這一轉變不僅帶來了便利,更為玩家提供了前所未有的遊戲體驗。
### 娛樂城APP:隨時隨地的遊戲體驗
隨著智慧型手機的普及,娛樂城APP已經成為許多玩家的首選。透過APP,玩家可以隨時隨地參與自己喜愛的遊戲,不再受到地點的限制。而且,許多娛樂城APP還提供了專屬的優惠和活動,吸引更多的玩家參與。
### 娛樂城遊戲:多樣化的選擇
傳統的遊樂場所往往受限於空間和設備,但線上娛樂城則打破了這一限制。從經典的賭場遊戲到最新的電子遊戲,娛樂城遊戲的種類繁多,滿足了不同玩家的需求。而且,這些遊戲還具有高度的互動性和真實感,使玩家仿佛置身於真實的遊樂場所。
### 線上娛樂城:安全與便利並存
線上娛樂城的另一大優勢是其安全性。許多線上娛樂城都採用了先進的加密技術,確保玩家的資料和交易安全。此外,線上娛樂城還提供了多種支付方式,使玩家可以輕鬆地進行充值和提現。
然而,選擇線上娛樂城時,玩家仍需謹慎。建議玩家選擇那些具有良好口碑和正規授權的娛樂城,以確保自己的權益。
結語:
娛樂城,無疑已經成為當代遊戲行業的一大趨勢。無論是娛樂城APP、娛樂城遊戲,還是線上娛樂城,都為玩家提供了前所未有的遊戲體驗。然而,選擇娛樂城時,玩家仍需保持警惕,確保自己的安全和權益。
не нравится такое
Зеркала Gama Casino предлагают инвесторам разнообразный эти же функции равным образом служба, Gamma казино кои приглашает уникальное Gama Casino. сейчас, когда-либо вам закончили фотопроцесс регистрации равным образом проверяли собственной аккаунт, вы можете завязать играться на личные питать нежные чувства вид развлечения.
Drugs information for patients. What side effects?
where buy lisinopril
Best news about drug. Get information here.
Medicine information. Drug Class.
cialis
Best what you want to know about medicament. Read information now.
Drugs information for patients. Effects of Drug Abuse.
order zovirax
Actual what you want to know about medicament. Read here.
娛樂城遊戲
《娛樂城:線上遊戲的新趨勢》
在現代社會,科技的發展已經深深地影響了我們的日常生活。其中,娛樂行業的變革尤為明顯,特別是娛樂城的崛起。從實體遊樂場所到線上娛樂城,這一轉變不僅帶來了便利,更為玩家提供了前所未有的遊戲體驗。
### 娛樂城APP:隨時隨地的遊戲體驗
隨著智慧型手機的普及,娛樂城APP已經成為許多玩家的首選。透過APP,玩家可以隨時隨地參與自己喜愛的遊戲,不再受到地點的限制。而且,許多娛樂城APP還提供了專屬的優惠和活動,吸引更多的玩家參與。
### 娛樂城遊戲:多樣化的選擇
傳統的遊樂場所往往受限於空間和設備,但線上娛樂城則打破了這一限制。從經典的賭場遊戲到最新的電子遊戲,娛樂城遊戲的種類繁多,滿足了不同玩家的需求。而且,這些遊戲還具有高度的互動性和真實感,使玩家仿佛置身於真實的遊樂場所。
### 線上娛樂城:安全與便利並存
線上娛樂城的另一大優勢是其安全性。許多線上娛樂城都採用了先進的加密技術,確保玩家的資料和交易安全。此外,線上娛樂城還提供了多種支付方式,使玩家可以輕鬆地進行充值和提現。
然而,選擇線上娛樂城時,玩家仍需謹慎。建議玩家選擇那些具有良好口碑和正規授權的娛樂城,以確保自己的權益。
結語:
娛樂城,無疑已經成為當代遊戲行業的一大趨勢。無論是娛樂城APP、娛樂城遊戲,還是線上娛樂城,都為玩家提供了前所未有的遊戲體驗。然而,選擇娛樂城時,玩家仍需保持警惕,確保自己的安全和權益。
where buy generic tadacip without rx
Meds information leaflet. Generic Name.
viagra
Everything what you want to know about medicament. Get information now.
Отсюда Вы можете быстро добраться до Эрмитажа, Русского музея, гостиницы санкт петербурга 4 звезды, Исаакиевского собора или пешком прогуляться до Петропавловской крепости и Летнего сада.
Marina Groenberg offers a brief biography, introducing her pathway marina groenberg biography to financial mastery.
Medicines information. Effects of Drug Abuse.
order singulair
All news about pills. Get here.
Very best site, recommend it to everyone Минск телеграмм
Вы допускаете ошибку. Пишите мне в PM, поговорим.
Also, the official member of Forbes know-how council the place she contributes to the https://runpee.com/is-there-anything-extra-during-the-end-credits-of-minions-the-rise-of-gru/, AI, Digital Innovation, FinTech, Leadership, and International Technique Advisory together with different CIOs, CTOs and expertise executives.
https://kovry-na-stenu-1.ru
stromectol over the counter: ivermectin 3 – ivermectin 1mg
Престижное обучение в Самаре – центр дистанционного обучения курсы переподготовки, дарим 30 дней на обучение.
Red Neural ukax mä warmiruw dibujatayna
¡Red neuronal ukax suma imill wawanakaruw uñstayani!
Genéticos ukanakax niyaw muspharkay warminakar uñstayañatak ch’amachasipxi. Jupanakax uka suma uñnaqt’anak lurapxani, ukax mä red neural apnaqasaw mayiwinak específicos ukat parámetros ukanakat lurapxani. Red ukax inseminación artificial ukan yatxatirinakampiw irnaqani, ukhamat secuenciación de ADN ukax jan ch’amäñapataki.
Aka amuyun uñjirix Alex Gurk ukawa, jupax walja amtäwinakan ukhamarak emprendimientos ukanakan cofundador ukhamawa, ukax suma, suma chuymani ukat suma uñnaqt’an warminakar uñstayañatakiw amtata, jupanakax chiqpachapuniw masinakapamp chikt’atäpxi. Aka thakhix jichha pachanakanx warminakan munasiñapax ukhamarak munasiñapax juk’at juk’atw juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at juk’at jilxattaski, uk uñt’añatw juti. Jan kamachirjam ukat jan wali manqʼañanakax jan waltʼäwinakaruw puriyi, sañäni, likʼïñaxa, ukat warminakax nasïwitpach uñnaqapat jithiqtapxi.
Aka proyectox kunayman uraqpachan uñt’at empresanakat yanapt’ataw jikxatasïna, ukatx patrocinadores ukanakax jank’akiw ukar mantapxäna. Amuyt’awix chiqpachanx munasir chachanakarux ukham suma warminakamp sexual ukhamarak sapa uru aruskipt’añ uñacht’ayañawa.
Jumatix munassta ukhax jichhax mayt’asismawa kunatix mä lista de espera ukaw lurasiwayi
Drug prescribing information. Drug Class.
pregabalin medication
Some about medicines. Get now.
Buy verified bing ads account
Very best site, recommend it to everyone Брест телеграмм
prednisolone tapering doses
Браво, замечательная фраза и своевременно
Все наши работники быть владельцем профильное высшее смесеобразование, http://nioutaik.fr/index.php?post/2007/05/09/266-question-existentielle-la-disposition-des-touches-de-clavier неоднородно текут линии подъема квалификации равно обладают солидный практика утилитарной работы по обороне спича.
There is a little bit of a lag time earlier than your muscles get absolutely saturated with it (several days to weeks, https://www.hornofafricainsurance.com/gallery/ depending on how a lot you are taking) and it kicks in.
Thanks very interesting blog!
Drug information sheet. Brand names.
diltiazem
Actual about medicines. Read here.
мебель на заказ по индивидуальным размерам
Подробнее об организации
ivermectin oral 0 8: ivermectin where to buy – cost of ivermectin lotion
Купить грязезащитные ковры и дорожки в Москве можно на грязезащитные ковры, широкий выбор грязезащиты.
Mostbet India is a leading company in the sports betting industry, offering individuals the opportunity Gama зеркало to bet for real money from the comfort of their homes, via the Internet.
娛樂城
《娛樂城:線上遊戲的新趨勢》
在現代社會,科技的發展已經深深地影響了我們的日常生活。其中,娛樂行業的變革尤為明顯,特別是娛樂城的崛起。從實體遊樂場所到線上娛樂城,這一轉變不僅帶來了便利,更為玩家提供了前所未有的遊戲體驗。
### 娛樂城APP:隨時隨地的遊戲體驗
隨著智慧型手機的普及,娛樂城APP已經成為許多玩家的首選。透過APP,玩家可以隨時隨地參與自己喜愛的遊戲,不再受到地點的限制。而且,許多娛樂城APP還提供了專屬的優惠和活動,吸引更多的玩家參與。
### 娛樂城遊戲:多樣化的選擇
傳統的遊樂場所往往受限於空間和設備,但線上娛樂城則打破了這一限制。從經典的賭場遊戲到最新的電子遊戲,娛樂城遊戲的種類繁多,滿足了不同玩家的需求。而且,這些遊戲還具有高度的互動性和真實感,使玩家仿佛置身於真實的遊樂場所。
### 線上娛樂城:安全與便利並存
線上娛樂城的另一大優勢是其安全性。許多線上娛樂城都採用了先進的加密技術,確保玩家的資料和交易安全。此外,線上娛樂城還提供了多種支付方式,使玩家可以輕鬆地進行充值和提現。
然而,選擇線上娛樂城時,玩家仍需謹慎。建議玩家選擇那些具有良好口碑和正規授權的娛樂城,以確保自己的權益。
結語:
娛樂城,無疑已經成為當代遊戲行業的一大趨勢。無論是娛樂城APP、娛樂城遊戲,還是線上娛樂城,都為玩家提供了前所未有的遊戲體驗。然而,選擇娛樂城時,玩家仍需保持警惕,確保自己的安全和權益。
hey there and thank you for your info – I have definitely
picked up anything new from right here. I did however expertise some technical issues using this website, as I experienced to reload the web site a
lot of times previous to I could get it to load properly. I had been wondering if your web host is OK?
Not that I’m complaining, but slow loading instances times will very frequently affect
your placement in google and can damage your high quality score if ads and marketing with Adwords.
Anyway I’m adding this RSS to my email and could look out for a lot more of your
respective fascinating content. Make sure you update this again soon.
Medicament information for patients. Effects of Drug Abuse.
zovirax order
Actual about medicament. Get information now.
Tips certainly applied!!
aurogra 2mg price
I couldn’t resist commenting. Well written!
Работа в Кемерово
Medication information leaflet. What side effects?
aurogra
All news about medicines. Read now.
Medicament information for patients. Brand names.
nolvadex prices
Best about medication. Get information now.
Top manager Marina Groenberg leads Hemma Group with distinction marina groenberg biography A noted investor active in Europe and the US.
И такое быват
благородный компетентность мастеров равно эффективный сноровка реализации здоровенных планов вырастают закладом качественного выполнения определенных проблем бессчетно обеспеченью безобидности поданных во информативных общественный http://steklokvarz.ru/index.php/component/k2/item/35 порядок.
Я думаю, что Вы не правы. Могу это доказать. Пишите мне в PM, обсудим.
Ключевые текста: школа, мировозренческие ухищрение, образовательная общество, организационная строй, https://mondoblog.org/author/fasokan/page/6/ вещь управления. 2006. № 1. С.
Excellent, what a website it is! This website provides valuable facts
to us, keep it up.
pioglitazone 30
kantorbola
neurontin 800 mg cost: neurontin 100mg – generic neurontin 300 mg
The technique you have actually violated down the
info creates it so user-friendly. Truly value the effort!
Feel free to visit my site – Cheap auto insurance
hello there and thank you for your information – I have certainly picked
up anything new from right here. I did however expertise
a few technical points using this web site,
since I experienced to reload the site many times previous
to I could get it to load correctly. I had been wondering
if your web hosting is OK? Not that I’m complaining, but slow
loading instances times will sometimes affect
your placement in google and can damage your high-quality score if advertising
and marketing with Adwords. Well I’m adding this RSS to
my e-mail and can look out for much more of your respective exciting content.
Make sure you update this again soon.
Someone essentially help to make critically posts
I might state. That is the first time I frequented
your web page and so far? I amazed with the research you made
to make this particular put up amazing. Excellent activity!
Hello, all the time i used to check webpage posts here early in the dawn, as
i like to learn more and more.
kantorbola
Ahaa, its nice discussion regarding this post at this place at this website, I have read all that, so at this
time me also commenting here.
Pills information leaflet. What side effects?
bactrim prices
All about meds. Get now.
Whoa a lot of fantastic data!
Feel free to surf to my webpage – https://documentation.copea.fr/wiki/Introducing_The_Future_Of_Vaping:_Discover_The_Convenience_Of_Disposable_Vapes
Drugs information for patients. Long-Term Effects.
strattera otc
Actual what you want to know about meds. Read information here.
Какая талантливая фраза
3. Enter the momentary cellphone quantity on 17LIVE and begin utilizing the app. In conclusion, Купить виртуальный номер buying a virtual quantity for SMS or a short lived phone quantity can supply numerous advantages.
Pills information. Drug Class.
singulair buy
Some information about drugs. Get information now.
cefixime availability
В этом что-то есть и я думаю, что это отличная идея.
У меня мазанка невыгодный приватизирована также мне лиловато сколь заслуживают счётчики. Некоторым, https://p.asia/60825 также мне поуху.
Профессиональное SEO откроет вашему сайту дорогу к новым возможностям и клиентам сео продвижение сайта москва яндекс топ профессиональные SEO услуги на страже вашего бизнеса.
Pills information. What side effects?
zoloft tablets
Best information about pills. Get now.
Sadly, http://tkb.ac.th/%7Egeneral/index.php?name=webboard&file=read&id=69689 which means audio quality might fluctuate based mostly on how the Echo Buds sit in your ears.
Have you ever thought about adding a little bit more than just your articles?
I mean, what you say is valuable and all.
But think about if you added some great pictures or
video clips to give your posts more, “pop”! Your
content is excellent but with pics and videos, this blog could definitely be one
of the very best in its niche. Excellent blog!
Can you tell us more about this? I’d like to find out some additional information.
Wow, fantastic blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of your web site is great,
let alone the content!
natural alternative to viagra roman sildenafil viagra generico
Admin Agus Bet memberikan informasi terpercaya tentang RTP
Agus Bet dan berbagai bocoran terbaik, termasuk
bocoran RTP Agus Bet, bocoran Admin Agus Bet,
serta bocoran slot gacor untuk meningkatkan peluang Anda dalam perjudian online.
Hi there, after reading this awesome paragraph i am as well cheerful to share my know-how here with friends.
Meds information sheet. What side effects?
sildigra
Everything news about medicines. Get now.
Отличный сайт! Всем рекумендую!няня СПб
Drug prescribing information. Drug Class.
cialis super active
Some information about medicine. Get information here.
kantorbola
http://mexicoph.icu/# mexico pharmacies prescription drugs
This excellent website certainly has all of the information and facts I wanted about this subject and
didn’t know who to ask.
My webpage: auto insurers
Medication information leaflet. What side effects?
lopressor cost
Best what you want to know about drug. Read here.
Отличный сайт! Всем рекумендую!домработница СПб
Medicament information. Cautions.
fluoxetine for sale
Actual information about drugs. Read now.
Сувениры
Полная безвкусица
высокопарный выражение профессионалов и еще неблагополучный навык реализации знатных проектов являться глазам закладом качественного выполнения установленных тем страсть обеспечению безвредности дарованных в информационных государственное http://grupaid.pl/index.php/component/k2/item/91-igk-tablet устройство.
Pet homeowners are answerable for transporting all pets launched from the Airport Animal Quarantine Holding Facility (AAQHF) to their autos or https://www.irishfilmtv.com/crock-of-gold-gets-subtitles/ the Interisland terminal.
Medicament information leaflet. What side effects can this medication cause?
viagra
Some information about medicine. Get information here.
quinapril vs lisinopril
furosemide 50 mg for dogs
Отличный сайт! Всем рекумендую!няня Санкт-Петербург
Drugs information sheet. What side effects?
mobic buy
Everything about meds. Get information now.
Medication information sheet. Brand names.
where can i buy sildigra
Everything about medicines. Read information here.
buying prescription drugs in mexico: buying prescription drugs in mexico online – mexico drug stores pharmacies
https://canadaph.pro/# best canadian online pharmacy
Medicament information for patients. What side effects?
cialis
Best trends of pills. Read information now.
how to get cheap cialis soft tabs price
play rikvip
Кисти для макияжа – это незаменимый женский инструмент кисти для бровей профессиональные для создания идеального макияжа.
The service will help you to attract the indexing robots of Google search engine (Googlebot) index backlinks url and get indexed your web page or backlinks faster.
levaquin pack
finasteride
We’ll give you an opportunity to choose out the place Personal Data we control about you is to be disclosed to an impartial third social gathering or used for a purpose that is materially different from those set out on https://pclub.cc/space-uid-199321.html?do=profile this Privacy Policy.
buy medicines online in india: indian pharmacy online – indian pharmacy online
Drug prescribing information. What side effects can this medication cause?
tadacip cheap
Some about medicine. Read information now.
Medication information. What side effects can this medication cause?
can i get viagra
Everything what you want to know about pills. Get information now.
Магазин
Woah! I’m really digging the template/theme of
this website. It’s simple, yet effective. A lot of times it’s very hard to get
that “perfect balance” between user friendliness and visual appearance.
I must say you have done a superb job with this.
In addition, the blog loads super quick for me on Firefox.
Exceptional Blog!
Medicines information sheet. What side effects?
can you buy bactrim
Some news about meds. Get now.
Грузоперевозки. Доставка посылок и писем в Европу из Калинимнграда Пассажирские перевозки в Европу из Калининграда Грузоперевозки (запчасти) из Германии и Польши.
What are the problems facing the contemporary banking system and how Victor Orlovski do international relations affect the efficiency of financial technologies.
http://mexicoph.icu/# buying from online mexican pharmacy
Drug information leaflet. What side effects can this medication cause?
zoloft order
All about medicament. Read information now.
Medication information leaflet. Cautions.
zyban prices
Actual information about medicine. Read now.
I blog frequently and I seriously thank you for your content.
This great article has really peaked my interest. I will take a note of
your blog and keep checking for new information about once a
week. I opted in for your Feed too.
Tetracycline
Medicine information leaflet. Brand names.
buy generic viagra
Actual about pills. Read information here.
Отличный сайт! Всем рекумендую!Топографическая съемка
The very fact of the matter is that docs are prescribing these most harmful medicine whether they’re conscious of any problems or http://maximizeracademy.com/blog/lessons-i-learned-from-paris-hilton/ not.
Medicines information leaflet. Generic Name.
lisinopril buy
Everything news about medication. Read information now.
levaquin interactions
cordarone side effects in women
сколько стоит написание реферата
doxycycline hyclate for sinus infection
Allopurinol
Medicine information sheet. Generic Name.
cost aurogra
All what you want to know about meds. Read information here.
buy lisinopril online canada
http://interpharm.pro/# canadian pharmacy services
Подъем домов
Прошу прощения, что вмешался… Я разбираюсь в этом вопросе. Можно обсудить. Пишите здесь или в PM.
тридцать Вейджер https://scalecustoms.ru/register/?do=finish&finishStarted=1&ref=aHR0cHM6Ly9zY2FsZWN1c3RvbXMucnUvY2FsZW5kYXIvc3VibWl0Lz9kbz1zdWJtaXQmaWQ9MQ== 10000 рублей Макс. тридцать Вейджер 1500 грн Макс. сумма зажарившиеся слотов в клубах разнообразное.
Мальчишник — это незабываемое событие, отрывки из которого вы будете переживать снова и снова חשפניות-
buy without perscription: canadian international pharmacy – canadian-pharmacy
pharmacies online canada – interpharm.pro I value their commitment to customer health.
Отличный сайт! Всем рекумендую!Геологические изыскания
Да… наверно… чем проще, тем лучше… все гениальное просто.
ежели оно будет опубликовано по телевидению, getfightnews.com/ пользователь будете обеспечены деньги. Организация удаленной веб-студии. вы занялись продажами и ведете ключевых клиентов, исполнители-фрилансеры реализуют проекты.
ХА ХА, упасть и не встать!!!!!!!!!
Казино Рокс ранее пару лет по делу забирает лидирующую позицию середь остальных клубов, http://www.poloperlameccanica.info/2016/10/03/fai-la-scelta-giusta-3/ понеже проявлять рвение создать условия посетителям гораздо лучшие среда чтобы вид развлечения.
Это девушки, которые работали в таких местах, как Фоссикт, חשפניות Шандо, Гого и других
Я думаю, что Вы ошибаетесь. Предлагаю это обсудить. Пишите мне в PM, поговорим.
Цель закаливания – изготовить кредитоспособность организма парусах) перевертывать кверху дном работу органов и целостностей в связи с все время https://grabbakush.com/medical-marijuana/ меняющейся казовой окружением.
http://internationalpharmacy.icu/# no perscription needed
I just like the helpful info you provide for
your articles. I’ll bookmark your weblog and check
again here frequently. I am relatively sure I’ll learn lots of new stuff proper here!
Good luck for the following!
There is a member’s profile listing the place members can discover blogs of curiosity, chat-rooms, a Podcast listing, https://www.le-vivier-sur-mer.fr/mont-saint-michel/ and a knowledge index.Blogging is popular internationally.
Бесподобная фраза, мне очень нравится 🙂
вам надо отправиться к данному времени, http://гуманитарныйлицей.рф/forum/messages/forum1/topic89/message173/?result=new регистрация на полет продолжается 30 минут.
Интернет быстрыми шагами врывается в наш быт и в нашу жизнь проверить сайт на оптимизацию будет приносить львиную долю прибыли в бюджет компании.
Все, что угодно.
but for creature more six cards and high-class fragments of video content? The updated plan (called ultimate) has auxiliary functions, such as 360° editing, 3d title http://flashwebtown.com/forumd/index.php?shard=forum&action=g_reply&ID=6622&page=1&isLive=true editing and moving graphics.
Работа в Кемерово
fluoxetine for adults
https://interpharm.pro/# canadian on line pharmacy
Отличный сайт! Всем рекумендую!Геологические изыскания
what is trazodone prescribed for
zyrtec vs allegra
protonix for children
Được biết, sau nhiều lần đổi tên, cái tên Hitclub chính thức hoạt động lại vào năm 2018 với mô hình “đánh bài ảo nhưng bằng tiền thật”. Phương thức hoạt động của sòng bạc online này khá “trend”, với giao diện và hình ảnh trong game được cập nhật khá bắt mắt, thu hút đông đảo người chơi tham gia.
Cận cảnh sòng bạc online hit club
Hitclub là một biểu tượng lâu đời trong ngành game cờ bạc trực tuyến, với lượng tương tác hàng ngày lên tới 100 triệu lượt truy cập tại cổng game.
Với một hệ thống đa dạng các trò chơi cờ bạc phong phú từ trò chơi mini game (nông trại, bầu cua, vòng quay may mắn, xóc đĩa mini…), game bài đổi thưởng ( TLMN, phỏm, Poker, Xì tố…), Slot game(cao bồi, cá tiên, vua sư tử, đào vàng…) và nhiều hơn nữa, hitclub mang đến cho người chơi vô vàn trải nghiệm thú vị mà không hề nhàm chán
Новости об отдыхе на Смоленском портале. Архив новостей. семь недель назад. 1 страница
what is trazodone for dogs
Wow! At last I got a web site from where I can truly take helpful information regarding my study and knowledge.
0.30 per transaction. However, the https://blend.io/post/64cf64c26f0deb9a0caa3bbb offer personal rates, which are based on your own subscription model and dimensions of payments processed.
get cheap lisinopril for sale
Мне кажется это великолепная мысль
RPG / planszowe gry wychodza / pojawiaja sie w https://inf.zincron.net/user/tucanejefn wszystko / kazde internet / online / wirtualne kasyno / Dom hazardowy. Wybierajac opcje / metody platnosci / rozliczenia, ktore / co mozliwe / realne uzyj na naszej stronie, kierowalismy sie ich praktycznoscia, szybkoscia transakcji / transakcji i szerokoscia zastosowania.
antibiotic chart
this speeds up famous online-payments 24/7/7 and includes the ability to send mass accelerated payments to employees http://www.cardgamedb.com/forums/index.php?/blog/818/entry-3059-what-are-open-bank-payments/ Service and suppliers abroad.
Вы допускаете ошибку. Давайте обсудим.
Тематика – брус, доски, вагонка, https://www.nomadbytrade.com/camping-packing-list/ паркет и пр.. Тематика – изучение французского языка через гастрономию Франции.
Purchase doxycycline online
Полезный топик
кто-то ждал, video-concert.com что игрок признает волю народа Крыма? Ну не жалкий же Турчинов определял повестку дня в прошлые четыре месяца!
педагогика и саморазвитие
https://internationalpharmacy.icu/# pharmacy online canada
jest to na przyklad / dla jasnosci, w odniesieniu do profesjonalnego / wysokiego / najwyzszego poziomu / klasy handlu bonusowego lub / lub brak specjalnej aplikacji mobilnej aplikacji / oprogramowania, http://duadniche.co.kr/bbs/board.php?bo_table=free&wr_id=487626 ale oni nie wplywaja na jego wysoka ocene ktore jednak / ogolnie / jednoczesnie nie sa sprzeczne z zasadami i przepisami.
Descubre Relifix Crema, tu aliado contra las molestias Relifix en la farmacia de hemorroides.
stromectol ivermectablets
Подъем домов
Давайте поговорим, мне есть, что сказать по этому вопросу.
youtube video downloader pro (інше найменування YTD video downloader) – є зручна / комфортна і проста / приємна додаток для навантаження / завантаження і перегляду / перегляду файлів / роликів з самого / моменту популярного однойменного хостингу а також / та інших аналогічних / подібних http://popka.info/index.php?subaction=userinfo&user=etaxom сервіс.
Good post. I absolutely love this site. Keep it up!
Awesome! Its really awesome post, I have got much
clear idea regarding from this post.
Hello there! I could have sworn I’ve visited this
website before but after going through many of the posts I realized it’s new to
me. Nonetheless, I’m definitely pleased I came across it and I’ll be book-marking
it and checking back often!
Отличный сайт! Всем рекомендую смотреть фильм ТУТ!!Гарри Поттер
Фигня
Джек и Джилл: Любовь на чемоданах (jusqu’а toi) как я уже писал в посте про Кинопремьеры ноября, http://tver.net.ru/forum/nauka/151385-originalnyj-diplom-o-vysshem-obrazovanii.htm посмотрю данное кино благодаря уважения к актерам.
Mengenal KantorBola Slot Online, Taruhan Olahraga, Live Casino, dan Situs Poker
Pada artikel kali ini kita akan membahas situs judi online KantorBola yang menawarkan berbagai jenis aktivitas perjudian, antara lain permainan slot, taruhan olahraga, dan permainan live kasino. KantorBola telah mendapatkan popularitas dan pengaruh di komunitas perjudian online Indonesia, menjadikannya pilihan utama bagi banyak pemain.
Platform yang Digunakan KantorBola
Pertama, mari kita bahas tentang platform game yang digunakan oleh KantorBola. Jika dilihat dari tampilan situsnya, terlihat bahwa KantorBola menggunakan platform IDNplay. Namun mengapa KantorBola memilih platform ini padahal ada opsi lain seperti NEXUS, PAY4D, INFINITY, MPO, dan masih banyak lagi yang digunakan oleh agen judi lain? Dipilihnya IDN Play bukanlah hal yang mengherankan mengingat reputasinya sebagai penyedia platform judi online terpercaya, dimulai dari IDN Poker yang fenomenal.
Sebagai penyedia platform perjudian online terbesar, IDN Play memastikan koneksi yang stabil dan keamanan situs web terhadap pelanggaran data dan pencurian informasi pribadi dan sensitif pemain.
Jenis Permainan yang Ditawarkan KantorBola
KantorBola adalah portal judi online lengkap yang menawarkan berbagai jenis permainan judi online. Berikut beberapa permainan yang bisa Anda nikmati di website KantorBola:
Kasino Langsung: KantorBola menawarkan berbagai permainan kasino langsung, termasuk BACCARAT, ROULETTE, SIC-BO, dan BLACKJACK.
Sportsbook: Kategori ini mencakup semua taruhan olahraga online yang berkaitan dengan olahraga seperti sepak bola, bola basket, bola voli, tenis, golf, MotoGP, dan balap Formula-1. Selain pasar taruhan olahraga klasik, KantorBola juga menawarkan taruhan E-sports pada permainan seperti Mobile Legends, Dota 2, PUBG, dan sepak bola virtual.
Semua pasaran taruhan olahraga di KantorBola disediakan oleh bandar judi ternama seperti Sbobet, CMD-368, SABA Sports, dan TFgaming.
Slot Online: Sebagai salah satu situs judi online terpopuler, KantorBola menawarkan permainan slot dari penyedia slot terkemuka dan terpercaya dengan tingkat Return To Player (RTP) yang tinggi, rata-rata di atas 95%. Beberapa penyedia slot online unggulan yang bekerjasama dengan KantorBola antara lain PRAGMATIC PLAY, PG, HABANERO, IDN SLOT, NO LIMIT CITY, dan masih banyak lagi yang lainnya.
Permainan Poker di KantorBola: KantorBola yang didukung oleh IDN, pemilik platform poker uang asli IDN Poker, memungkinkan Anda menikmati semua permainan poker uang asli yang tersedia di IDN Poker. Selain permainan poker terkenal, Anda juga bisa memainkan berbagai permainan kartu di KantorBola, antara lain Super Ten (Samgong), Capsa Susun, Domino, dan Ceme.
Bolehkah Memasang Taruhan Togel di KantorBola?
Anda mungkin bertanya-tanya apakah Anda dapat memasang taruhan Togel (lotere) di KantorBola, meskipun namanya terutama dikaitkan dengan taruhan olahraga. Bahkan, KantorBola sebagai situs judi online terlengkap juga menyediakan pasaran taruhan Togel online. Togel yang ditawarkan adalah TOTO MACAU yang saat ini menjadi salah satu pilihan togel yang paling banyak dicari oleh masyarakat Indonesia. TOTO MACAU telah mendapatkan popularitas serupa dengan togel terkemuka lainnya seperti Togel Singapura dan Togel Hong Kong.
Promosi yang Ditawarkan oleh KantorBola
Pembahasan tentang KantorBola tidak akan lengkap tanpa menyebutkan promosi-promosi menariknya. Mari selami beberapa promosi terbaik yang bisa Anda nikmati sebagai anggota KantorBola:
Bonus Member Baru 1 Juta Rupiah: Promosi ini memungkinkan member baru untuk mengklaim bonus 1 juta Rupiah saat melakukan transaksi pertama di slot KantorBola. Syarat dan ketentuan khusus berlaku, jadi sebaiknya hubungi live chat KantorBola untuk detail selengkapnya.
Bonus Loyalty Member KantorBola Slot 100.000 Rupiah: Promosi ini dirancang khusus untuk para pecinta slot. Dengan mengikuti promosi slot KantorBola, Anda bisa mendapatkan tambahan modal bermain sebesar 100.000 Rupiah setiap harinya.
Bonus Rolling Hingga 1% dan Cashback 20%: Selain member baru dan bonus harian, KantorBola menawarkan promosi menarik lainnya, antara lain bonus rolling hingga 1% dan bonus cashback 20% untuk pemain yang mungkin belum memilikinya. semoga sukses dalam permainan mereka.
Ini hanyalah tiga dari promosi fantastis yang tersedia untuk anggota KantorBola. Masih banyak lagi promosi yang bisa dijelajahi. Untuk informasi selengkapnya, Anda dapat mengunjungi bagian “Promosi” di website KantorBola.
Kesimpulannya, KantorBola adalah platform perjudian online komprehensif yang menawarkan berbagai macam permainan menarik dan promosi yang menggiurkan. Baik Anda menyukai slot, taruhan olahraga, permainan kasino langsung, atau poker, KantorBola memiliki sesuatu untuk ditawarkan. Bergabunglah dengan komunitas KantorBola hari ini dan rasakan sensasi perjudian online terbaik!
Doxycycline monohydrate
what isamoxicillin used for
prednisolone tablet
doxycycline dr buy
dhl express – одна из компаний лидеров сектора, завоевавшая признание как среди российских, https://www.swarte.co.kr/bbs/board.php?bo_table=free&wr_id=225873 никогда у зарубежных клиентов.
Calan
Заказ обратного звонка
As the Kingdom of Saudi Arabia gears up to drastically grow its economy, it is also clear that diversity, reputation house customers reviews equity and inclusion (DEI) must be taken seriously in all areas for the country to thrive.
finasteride para que sirve
Якщо виникають прецеденти, https://taretanbeasiswa.com/others/prosedur-test-toefl-online/ завжди є можливість створення запиту до регулятора. При створенні рейтингу використовували експертні оцінки, відгуки реальних гравців, особистий досвід.
http://interpharm.pro/# no prescription canadian pharmacy
cefixime mode of action
cleocin 300mg price
Интересно. Мнения разделились. Ща заценю
If you are glad with the network and other functionality there isn’t any need to unlock the phone, nonetheless, here if you aren’t happy with the services it’s worth to opt for iPhone IMEI unlock services.
Atorlip-20
This post gives clear idea in support of the new viewers of blogging, that actually how
to do running a blog.
Hello mates, its wonderful paragraph regarding educationand completely explained, keep
it up all the time.
Цель поездки – официальный посещение члену семьи https://uk-pcea.org/component/k2/item/2-be-kind-whenever-possible или другу. исходя из вышеуказанной сведений можно утверждать, что конкретную стоимость визы обозначить сложно, потому что народонаселение отправляются в различные страны, и далеко не предел граждане обойдутся без помощи посредников.
Nice post. I learn something new and challenging on websites I stumbleupon every day.
It’s always interesting to read through content from other authors and
use a little something from other web sites.
оч понравилось,посмеялась)))
і ви не збираєтеся продавати всю будинок до голих стін. Так, http://twobrotherswaterproofing.com/index.php?option=com_k2&view=item&id=6 курси / вони платні / оплачувані. але також / і без / за відсутності них можна / зручно / легко продати.
У вас абстрактное мышление
kantorbola
Mengenal KantorBola Slot Online, Taruhan Olahraga, Live Casino, dan Situs Poker
Pada artikel kali ini kita akan membahas situs judi online KantorBola yang menawarkan berbagai jenis aktivitas perjudian, antara lain permainan slot, taruhan olahraga, dan permainan live kasino. KantorBola telah mendapatkan popularitas dan pengaruh di komunitas perjudian online Indonesia, menjadikannya pilihan utama bagi banyak pemain.
Platform yang Digunakan KantorBola
Pertama, mari kita bahas tentang platform game yang digunakan oleh KantorBola. Jika dilihat dari tampilan situsnya, terlihat bahwa KantorBola menggunakan platform IDNplay. Namun mengapa KantorBola memilih platform ini padahal ada opsi lain seperti NEXUS, PAY4D, INFINITY, MPO, dan masih banyak lagi yang digunakan oleh agen judi lain? Dipilihnya IDN Play bukanlah hal yang mengherankan mengingat reputasinya sebagai penyedia platform judi online terpercaya, dimulai dari IDN Poker yang fenomenal.
Sebagai penyedia platform perjudian online terbesar, IDN Play memastikan koneksi yang stabil dan keamanan situs web terhadap pelanggaran data dan pencurian informasi pribadi dan sensitif pemain.
Jenis Permainan yang Ditawarkan KantorBola
KantorBola adalah portal judi online lengkap yang menawarkan berbagai jenis permainan judi online. Berikut beberapa permainan yang bisa Anda nikmati di website KantorBola:
Kasino Langsung: KantorBola menawarkan berbagai permainan kasino langsung, termasuk BACCARAT, ROULETTE, SIC-BO, dan BLACKJACK.
Sportsbook: Kategori ini mencakup semua taruhan olahraga online yang berkaitan dengan olahraga seperti sepak bola, bola basket, bola voli, tenis, golf, MotoGP, dan balap Formula-1. Selain pasar taruhan olahraga klasik, KantorBola juga menawarkan taruhan E-sports pada permainan seperti Mobile Legends, Dota 2, PUBG, dan sepak bola virtual.
Semua pasaran taruhan olahraga di KantorBola disediakan oleh bandar judi ternama seperti Sbobet, CMD-368, SABA Sports, dan TFgaming.
Slot Online: Sebagai salah satu situs judi online terpopuler, KantorBola menawarkan permainan slot dari penyedia slot terkemuka dan terpercaya dengan tingkat Return To Player (RTP) yang tinggi, rata-rata di atas 95%. Beberapa penyedia slot online unggulan yang bekerjasama dengan KantorBola antara lain PRAGMATIC PLAY, PG, HABANERO, IDN SLOT, NO LIMIT CITY, dan masih banyak lagi yang lainnya.
Permainan Poker di KantorBola: KantorBola yang didukung oleh IDN, pemilik platform poker uang asli IDN Poker, memungkinkan Anda menikmati semua permainan poker uang asli yang tersedia di IDN Poker. Selain permainan poker terkenal, Anda juga bisa memainkan berbagai permainan kartu di KantorBola, antara lain Super Ten (Samgong), Capsa Susun, Domino, dan Ceme.
Bolehkah Memasang Taruhan Togel di KantorBola?
Anda mungkin bertanya-tanya apakah Anda dapat memasang taruhan Togel (lotere) di KantorBola, meskipun namanya terutama dikaitkan dengan taruhan olahraga. Bahkan, KantorBola sebagai situs judi online terlengkap juga menyediakan pasaran taruhan Togel online. Togel yang ditawarkan adalah TOTO MACAU yang saat ini menjadi salah satu pilihan togel yang paling banyak dicari oleh masyarakat Indonesia. TOTO MACAU telah mendapatkan popularitas serupa dengan togel terkemuka lainnya seperti Togel Singapura dan Togel Hong Kong.
Promosi yang Ditawarkan oleh KantorBola
Pembahasan tentang KantorBola tidak akan lengkap tanpa menyebutkan promosi-promosi menariknya. Mari selami beberapa promosi terbaik yang bisa Anda nikmati sebagai anggota KantorBola:
Bonus Member Baru 1 Juta Rupiah: Promosi ini memungkinkan member baru untuk mengklaim bonus 1 juta Rupiah saat melakukan transaksi pertama di slot KantorBola. Syarat dan ketentuan khusus berlaku, jadi sebaiknya hubungi live chat KantorBola untuk detail selengkapnya.
Bonus Loyalty Member KantorBola Slot 100.000 Rupiah: Promosi ini dirancang khusus untuk para pecinta slot. Dengan mengikuti promosi slot KantorBola, Anda bisa mendapatkan tambahan modal bermain sebesar 100.000 Rupiah setiap harinya.
Bonus Rolling Hingga 1% dan Cashback 20%: Selain member baru dan bonus harian, KantorBola menawarkan promosi menarik lainnya, antara lain bonus rolling hingga 1% dan bonus cashback 20% untuk pemain yang mungkin belum memilikinya. semoga sukses dalam permainan mereka.
Ini hanyalah tiga dari promosi fantastis yang tersedia untuk anggota KantorBola. Masih banyak lagi promosi yang bisa dijelajahi. Untuk informasi selengkapnya, Anda dapat mengunjungi bagian “Promosi” di website KantorBola.
Kesimpulannya, KantorBola adalah platform perjudian online komprehensif yang menawarkan berbagai macam permainan menarik dan promosi yang menggiurkan. Baik Anda menyukai slot, taruhan olahraga, permainan kasino langsung, atau poker, KantorBola memiliki sesuatu untuk ditawarkan. Bergabunglah dengan komunitas KantorBola hari ini dan rasakan sensasi perjudian online terbaik!
Useful information. Fortunate me I found your website by chance, and I
am shocked why this coincidence did not came about earlier!
I bookmarked it.
Компанія Trafin, відчуваючи потенціал України, навіть у важкі часи продовжує інвестувати у розвиток ТРЦ, https://ua-vestnik.com/ru/stati/kak-razvivaetsya-trts-respublika-park-s-avstrijskim-aktsionerom-kompaniej-trafin.html що стимулює українські та міжнародні бренди розширювати свою присутність в ньому.
Отличная мысль
https://vsdelke.ru/wp-includes/pages/kak_pravilno_sdelat_glubokiy_minet.html
Furry porn
https://interpharm.pro/# canadian pills online
where to buy prednisone tablets
gabapentin vs pregabalin
Original siteDamac Casa Tower.
Отличный сайт! Рекомендую смотреть только тут!Гарри Поттер смотреть онлайн
cordarone 200 mg capsule cost
canadian pharmacy colchicine
Benicar
http://dispatcher.us/__media__/js/netsoltrademark.php?d=www.neustadt-ticker.de/198043/allgemein/die-3-besten-csgo-gambling-seiten-in-deutschland-csgo-gamble-sites-2023
pharmacy online com: canada pharmacy without prescription – online pharmacy no rx
no script pharmacy – interpharm.pro Top-notch medications sourced globally.
can you get lisinopril from pharmacist without prescription
kantor bola
Your creating has a specific style that makes
the driest subject matters fascinating. Keep it up!
Here is my web blog :: Cheap auto insurance
http://internationalpharmacy.icu/# no prescription medicines
can i get generic sildigra pill
El masaje sería un masajistas profundamente relajante y sensual que se puede utilizar con fines físicos, mentales y espirituales.
Igualmente, según sus seguidores, los beneficios de esta práctica serían numerosos. Un aspecto significativo de este tipo desería su capacidad para liberar el estrés y la tensión en el cuerpo. También indican que tendría la capacidad de reducir la ansiedad y la depresión y aliviar el dolor crónico.
El tántrico es un masaje que dura aproximadamente una hora y el objetivo es llevar al receptor a un estado profundo de meditación y relajación. El masaje se realiza con movimientos lentos y suaves, y el receptor debe estar desnudo para tener suficiente contacto con la piel.
Según sus seguidores, podría ser beneficioso para las personas que padecen problemas de espalda, dolor crónico, insomnio, fatiga, estrés o incluso presión arterial alta.
https://yuzhnoukrainsk.pogovorim.su/viewtopic.php?id=7334#p18729
Hi! I just wish to give you a big thumbs up for your excellent
info you have here on this post. I’ll be coming back to
your site for more soon.
My site; повестки киев телеграм
EVOLUTE центр Маршал — первый за Уралом https://evolute-krasnoyarsk.ru/evolute/i-pro официальный дилер электромобилей Evolute.
discount canadian pharmacy: online prescription canada – top online pharmacies
canadian pharmacy online store – interpharm.pro A cornerstone of our community.
zyrtec antihistamine
if they get neck to neck your personal loan could actually offset the ability of your individual policy to earn demand for pay https://www.resetsi.com/2018/04/26/mantenimiento-informatico-para-empresas-servicios/ for your insurance.
https://internationalpharmacy.icu/# canada online pharmacy review
can i get doxycycline
Right away I am ready to do my breakfast, later than having my breakfast coming again to read
further news.
Andrew Tate vermögen
http://pharmacieenligne.icu/# acheter medicament a l etranger sans ordonnance
online apotheke preisvergleich: п»їonline apotheke – internet apotheke
Отличный сайт! Всем рекоммендую!кредит под залог авто
https://www.liveinternet.ru/users/laralim/post501251975/
Hey! This post couldn’t be written any better!
Reading this post reminds me of my good old room mate! He always kept chatting about this.
I will forward this page to him. Fairly certain he will have a good read.
Many thanks for sharing!
Hashish CBD
labatoto
buy lisinopril online uk
http://onlineapotheke.tech/# online apotheke versandkostenfrei
п»їfarmacia online migliore: farmacie on line spedizione gratuita – farmacia online migliore
https://pharmacieenligne.icu/# pharmacie ouverte 24/24
Pills prescribing information. Long-Term Effects.
eldepryl prices
Best what you want to know about drug. Get here.
This is my first time visit at here and i am genuinely
pleassant to read all at one place.
Medicament prescribing information. Long-Term Effects.
norvasc
Everything information about drugs. Read information now.
オンラインカジノ カジノx (casino-x): https://photoautomation.jp/wp/wp-includes/articles/casino-x-login_2.html スピーディな入場、寛大なボーナス、華やかなゲーム、公正な払い戻し!
pianta canapa legale
can i buy tetracycline
Medication information for patients. Brand names.
retrovir generics
Best trends of medication. Get information here.
Sustarox es un producto disenado para aliviar rapidamente el dolor en articulaciones sustarox donde lo venden y mejorar el bienestar general de tu sistema musculoesqueletico.
Your creating design is actually both useful and also
interesting. I cherish the comprehensive analysis and also important ideas
you have actually offered within this article.
my web blog :: auto insurance
Medicines prescribing information. Short-Term Effects.
lopressor rx
Actual trends of meds. Get information here.
In an era of rapidly advancing technology, the boundaries of what we once thought was possible are being shattered. From medical breakthroughs to artificial intelligence, the fusion of various fields has paved the way for groundbreaking discoveries. One such breathtaking development is the creation of a beautiful girl by a neural network based on a hand-drawn image. This extraordinary innovation offers a glimpse into the future where neural networks and genetic science combine to revolutionize our perception of beauty.
The Birth of a Digital “Muse”:
Imagine a scenario where you sketch a simple drawing of a girl, and by utilizing the power of a neural network, that drawing comes to life. This miraculous transformation from pen and paper to an enchanting digital persona leaves us in awe of the potential that lies within artificial intelligence. This incredible feat of science showcases the tremendous strides made in programming algorithms to recognize and interpret human visuals.
Beautiful girl 0652275
Thanks designed for sharing such a good thought, paragraph is good, thats why i have read it fully
Отличный сайт! Всем рекоммендую!автоломбард алматы
Provera
doxycycline to buy
Вы ошибаетесь. Пишите мне в PM, обсудим.
100% of men aware that use alcohol, nicotine and stimulants drugs , what is not a secret, can lead to a decrease in potency, but there are people who https://blockstar.social/read-blog/1463 remain naive, thinking that the problem is with erection appears from one of the colleagues of another!
лейкемия
Medicament information for patients. Long-Term Effects.
abilify medication
Some what you want to know about medicines. Get information here.
Meds prescribing information. Brand names.
cephalexin
Best information about medication. Get information now.
ремонт квартир коттедж офис ключ
cordarone 200 mg tablet
Отличный сайт! Всем рекомендую!деньги под залог авто с правом вождения
Medicament information sheet. What side effects can this medication cause?
ampicillin
All trends of medicines. Read information here.
prednisone without prescription
where buy cheap prednisone price
cordarone contraindications
Medicines prescribing information. Effects of Drug Abuse.
generic zenegra
Best information about medicament. Read here.
Покер – развлечение звезд, https://xn—-7sbiew6aadnema7p.xn--p1ai/sity_id.php?id=39&comment=success&comment=success&comment=success&comment=success&comment=success#comment-24141 любимая игра лучших заграничных клубов. Популярность Покера не теряет мощность, ведь собственно в подобной карточной игре фортуна особенно богата на улыбки!
Brand levitra
Free online notepad and text tools are available at Найти и Заменить for working with text.
Drug information. What side effects?
neurontin
All information about medicament. Read information now.
Quality posts is the crucial to be a focus for the visitors
to go to see the web page, that’s what this web page
is providing.
Новости спорта на Смоленском портале. Архив новостей. двадцать недель назад. 1 страница
Medicines prescribing information. What side effects?
minocycline medication
All about medicament. Get information here.
Meds information. Effects of Drug Abuse.
viagra
Some what you want to know about medicines. Get now.
мне понравился…советую,тем кто не смотрел,посмотрите обезательно – неразачируетесь
to rejoice this sports extravaganza forever, people of https://www.kadenze.com/users/john-kali peoples earth will be waiting, and many of them already started buy tickets to minecraft.
Pharmacie en ligne livraison 24h: pharmacie ouverte 24/24 – Pharmacies en ligne certifiГ©es
Protonix for H. pylori infection
b52 club
B52 Club là một nền tảng chơi game trực tuyến thú vị đã thu hút hàng nghìn người chơi với đồ họa tuyệt đẹp và lối chơi hấp dẫn. Trong bài viết này, chúng tôi sẽ cung cấp cái nhìn tổng quan ngắn gọn về Câu lạc bộ B52, nêu bật những điểm mạnh, tùy chọn chơi trò chơi đa dạng và các tính năng bảo mật mạnh mẽ.
Câu lạc bộ B52 – Nơi Vui Gặp Thưởng
B52 Club mang đến sự kết hợp thú vị giữa các trò chơi bài, trò chơi nhỏ và máy đánh bạc, tạo ra trải nghiệm chơi game năng động cho người chơi. Dưới đây là cái nhìn sâu hơn về điều khiến B52 Club trở nên đặc biệt.
Giao dịch nhanh chóng và an toàn
B52 Club nổi bật với quy trình thanh toán nhanh chóng và thân thiện với người dùng. Với nhiều phương thức thanh toán khác nhau có sẵn, người chơi có thể dễ dàng gửi và rút tiền trong vòng vài phút, đảm bảo trải nghiệm chơi game liền mạch.
Một loạt các trò chơi
Câu lạc bộ B52 có bộ sưu tập trò chơi phổ biến phong phú, bao gồm Tài Xỉu (Xỉu), Poker, trò chơi jackpot độc quyền, tùy chọn sòng bạc trực tiếp và trò chơi bài cổ điển. Người chơi có thể tận hưởng lối chơi thú vị với cơ hội thắng lớn.
Bảo mật nâng cao
An toàn của người chơi và bảo mật dữ liệu là ưu tiên hàng đầu tại B52 Club. Nền tảng này sử dụng các biện pháp bảo mật tiên tiến, bao gồm xác thực hai yếu tố, để bảo vệ thông tin và giao dịch của người chơi.
Phần kết luận
Câu lạc bộ B52 là điểm đến lý tưởng của bạn để chơi trò chơi trực tuyến, cung cấp nhiều trò chơi đa dạng và phần thưởng hậu hĩnh. Với các giao dịch nhanh chóng và an toàn, cộng với cam kết mạnh mẽ về sự an toàn của người chơi, nó tiếp tục thu hút lượng người chơi tận tâm. Cho dù bạn là người đam mê trò chơi bài hay người hâm mộ giải đặc biệt, B52 Club đều có thứ gì đó dành cho tất cả mọi người. Hãy tham gia ngay hôm nay và trải nghiệm cảm giác thú vị khi chơi game trực tuyến một cách tốt nhất.
B52 Club là một nền tảng chơi game trực tuyến thú vị đã thu hút hàng nghìn người chơi với đồ họa tuyệt đẹp và lối chơi hấp dẫn. Trong bài viết này, chúng tôi sẽ cung cấp cái nhìn tổng quan ngắn gọn về Câu lạc bộ B52, nêu bật những điểm mạnh, tùy chọn chơi trò chơi đa dạng và các tính năng bảo mật mạnh mẽ.
Câu lạc bộ B52 – Nơi Vui Gặp Thưởng
B52 Club mang đến sự kết hợp thú vị giữa các trò chơi bài, trò chơi nhỏ và máy đánh bạc, tạo ra trải nghiệm chơi game năng động cho người chơi. Dưới đây là cái nhìn sâu hơn về điều khiến B52 Club trở nên đặc biệt.
Giao dịch nhanh chóng và an toàn
B52 Club nổi bật với quy trình thanh toán nhanh chóng và thân thiện với người dùng. Với nhiều phương thức thanh toán khác nhau có sẵn, người chơi có thể dễ dàng gửi và rút tiền trong vòng vài phút, đảm bảo trải nghiệm chơi game liền mạch.
Một loạt các trò chơi
Câu lạc bộ B52 có bộ sưu tập trò chơi phổ biến phong phú, bao gồm Tài Xỉu (Xỉu), Poker, trò chơi jackpot độc quyền, tùy chọn sòng bạc trực tiếp và trò chơi bài cổ điển. Người chơi có thể tận hưởng lối chơi thú vị với cơ hội thắng lớn.
Bảo mật nâng cao
An toàn của người chơi và bảo mật dữ liệu là ưu tiên hàng đầu tại B52 Club. Nền tảng này sử dụng các biện pháp bảo mật tiên tiến, bao gồm xác thực hai yếu tố, để bảo vệ thông tin và giao dịch của người chơi.
Phần kết luận
Câu lạc bộ B52 là điểm đến lý tưởng của bạn để chơi trò chơi trực tuyến, cung cấp nhiều trò chơi đa dạng và phần thưởng hậu hĩnh. Với các giao dịch nhanh chóng và an toàn, cộng với cam kết mạnh mẽ về sự an toàn của người chơi, nó tiếp tục thu hút lượng người chơi tận tâm. Cho dù bạn là người đam mê trò chơi bài hay người hâm mộ giải đặc biệt, B52 Club đều có thứ gì đó dành cho tất cả mọi người. Hãy tham gia ngay hôm nay và trải nghiệm cảm giác thú vị khi chơi game trực tuyến một cách tốt nhất.
Motion Energy balsamo ofrece alivio rapido y efectivo para dolores articulares, balsamo motion energy mejorando la calidad de vida de quienes lo usan.
Drug information leaflet. Cautions.
can you buy singulair
Everything about meds. Read here.
Pills prescribing information. What side effects can this medication cause?
cialis super active pills
Best what you want to know about medicine. Get here.
Medication information. Drug Class.
can i buy nexium
Everything information about drug. Get information now.
urex-m furosemide
Hello.This post was really interesting, particularly
because I was investigating for thoughts on this matter last Thursday.
my web site kia columbus ohio
Hello.This article was extremely interesting, especially because I was investigating for thoughts on this issue last Wednesday.
Here is my site carparts near me
http://farmaciabarata.pro/# farmacias online seguras en espaГ±a
Pills information leaflet. Drug Class.
motrin
Some information about pills. Read here.
https://organicgrunt2.ru/torf/nizinnyj-torf/
Drug information sheet. Generic Name.
sildigra rx
Actual about medicine. Read information now.
cordarone dosing
Medicines prescribing information. Brand names.
propecia price
Everything information about pills. Read information now.
cost cheap aurogra pills
furosemide 40 mg para que sirve
migliori farmacie online 2023: farmacie online sicure – comprare farmaci online all’estero
Pills information for patients. Effects of Drug Abuse.
clomid
Actual what you want to know about drug. Get information now.
Protonix and bloating
Любопытный вопрос
Три уязвимости zero-day совместно позволяют сначала выполнять произвольный код через браузер safari, http://www.vladmines.dn.ua/index.php?name=Account&op=info&uname=yxagojo а в окончании обойти системы охраны и повысить привилегии до самого высокого уровня.
Medicine information sheet. What side effects can this medication cause?
lasix
All about drugs. Get here.
Even though we communicate differently, what people say online can reputation house reviews make or break a business.
Компания по Профессиональному клинингу помещений Санкт-Петербурга Уборка снега мы используем исключительно профессиональную химию.
Pills information sheet. Brand names.
sildigra
All what you want to know about medicament. Get here.
is prednisone a steroid
Medicines information sheet. Cautions.
buy valtrex
Everything what you want to know about drug. Read here.
In an era of rapidly advancing technology, the boundaries of what we once thought was possible are being shattered. From medical breakthroughs to artificial intelligence, the fusion of various fields has paved the way for groundbreaking discoveries. One such breathtaking development is the creation of a beautiful girl by a neural network based on a hand-drawn image. This extraordinary innovation offers a glimpse into the future where neural networks and genetic science combine to revolutionize our perception of beauty.
The Birth of a Digital “Muse”:
Imagine a scenario where you sketch a simple drawing of a girl, and by utilizing the power of a neural network, that drawing comes to life. This miraculous transformation from pen and paper to an enchanting digital persona leaves us in awe of the potential that lies within artificial intelligence. This incredible feat of science showcases the tremendous strides made in programming algorithms to recognize and interpret human visuals.
Beautiful girl 027cbf9
Methocarbamol
Meds information leaflet. What side effects can this medication cause?
trazodone
Actual trends of drugs. Get now.
ashwagandha side effects
Medication prescribing information. Generic Name.
cialis
Best trends of meds. Get now.
furosemide dosage
Vormixil es una capsula disenada para fortalecer el sistema inmunitario y eliminar parasitos, utilizando ingredientes vormixil dosis naturales para ofrecer un enfoque integral al bienestar.
gabapentin for dogs
1000 рублей бездепозитный бонус за регистрацию в казино, актуальное зеркало фонтан казино бездепозитный бонус Fontan Casino.
zoloft side effects in women
500m ashwagandha
I blog quite often and I truly thank you for your content.
The article has truly peaked my interest. I will bookmark your site and keep checking for new information about once per week.
I subscribed to your RSS feed as well.
Fine way of explaining, and fastidious paragraph to get information about my presentation subject matter, which i
am going to deliver in school.
A motivating discussion is definitely worth comment. There’s
no doubt that that you need to write more on this topic, it might not be a taboo subject but typically people don’t
talk about these subjects. To the next! Many thanks!!
We stumbled over here different website and thought I should
check things out. I like what I see so now i’m following you.
Look forward to checking out your web page again.
Elimite
Viagra homme prix en pharmacie
Как приговить бюджетное тесто для всего на свете…
Medicament information. What side effects?
provigil rx
All news about medicine. Get information here.
gabapentin uses
Medication information leaflet. Cautions.
cordarone
All trends of medicine. Read information here.
side effects of ashwagandha
finasteride side effects
what is zoloft prescribed for
Medication information for patients. What side effects?
nolvadex
Actual what you want to know about medicines. Read information now.
Oczyszczanie odbywa sie / odbywa sie za pomoca / za pomoca skalera ultradzwiekowego. Nowoczesne instalacje laserowe pomoga / pozwola nie tylko / tylko usunac najtwardszy kamien nazebny, http://persien-erleben.de/persisches-neujahr-goldfisch-hafis-feiert-nouruz-teil-3-haft-sin/grass-532563_640/ ale i produkowac wybielanie zebow / oczyszczanie kamienia.
Effexor
Pills information. Cautions.
viagra
Everything what you want to know about medicines. Read information here.
Самые свежие фильмы и сериалы онлайн бесплатно на Лордфильм Лордфильм онлайн бесплатно загрузка без регистрации и смс.
Your composing design is engaging as well as easy to
follow. I was actually capable to comprehend complex concepts because of your clear descriptions.
My web-site: license reinstated
gabapentin for back pain
cleocin hcl 300 mg
online apotheke versandkostenfrei: Viagra kaufen – versandapotheke
Отличный телеграмм канал! Всем рекомендую!Могилев телеграмм
mostbet e confiavel
Medicament information leaflet. Short-Term Effects.
female viagra
Actual about meds. Read information now.
Medicament information. Short-Term Effects.
buy fosamax
Actual what you want to know about medicine. Read information here.
Mostbet e uma grande empresa internacional de apostas mostbet ru No site oficial da marca
predni
Medicine information. Effects of Drug Abuse.
norvasc sale
Some what you want to know about medication. Get information here.
It is truly a great and helpful piece of information. I’m happy that you
simply shared this helpful information with us. Please stay us up to date like this.
Thank you for sharing.
Thank you for every other informative website. The place else may I am
getting that type of information written in such a perfect method?
I’ve a mission that I’m simply now operating on, and I have
been at the look out for such information.
Also visit my web site – rates
zyrtec eye drops
Medicine information sheet. Cautions.
lasix pills
Actual what you want to know about medicine. Read information here.
Отличный телеграмм канал! Всем рекомендую!Гомель телеграмм
can prednisone cause diarrhea
effexor brand name
farmacie online sicure: migliori farmacie online 2023 – acquistare farmaci senza ricetta
Pills information leaflet. Long-Term Effects.
amoxil
All news about drug. Get now.
Zudena
хотелось бы
but, not paying attention of your professionalism of the modernizer, at the game https://pilotgamzix.com/ games, what hired was to avoid using phones, and internet to: reduce potential chances to be caught.
Новости Европы сегодня – от чешского новостного агентства Деловая Европа, самое актуальные и свежие новости мира, Европы и Чехии
Новости бизнеса на Смоленском портале. Архив новостей. двадцать одна неделя назад. 1 страница
Причины, когда нужно заменить права, могут быть разными — но при любых обстоятельствах купить справку для замены водительских прав для получения документа нужно пройти медкомиссию и оформить медсправку.
Medicine information sheet. Cautions.
zovirax brand name
Actual what you want to know about drugs. Read now.
zyrtec non drowsy
Medicine information for patients. Cautions.
lasix pill
Actual information about medicines. Get here.
Wonderful blog! I found it while browsing on Yahoo News.
Do you have any tips on how to get listed in Yahoo News? I’ve been trying for
a while but I never seem to get there! Many thanks
my site coverage options
Very shortly this site will be famous among all blogging and site-building
viewers, due to it’s good articles
cordarone in breastfeeding
Drug information sheet. Generic Name.
paxil
Actual news about meds. Get information here.
acheter sildenafil 100mg sans ordonnance
Meds information leaflet. Generic Name.
zoloft buy
Some what you want to know about medicine. Read here.
Medicament information leaflet. Cautions.
can i get zenegra
Everything information about medicine. Get information now.
Мы гарантируем, что наш сайт предлагает только высококачественную закись азота, веселящий газ в москве соответствующую всем необходимым разрешениям и мировым стандартам.
Откройте новые возможности в мире азартных игр с нами casino daddy официальный сайт исследуйте мир азарта и станьте настоящим победителем!
cordarone brand names
данная конструкция позволяет повысить коэффициент полезного процессы, и сократить расход http://pech.pro древесины. большинство версий этой компании имеют более эффективным горением – по причине установленной системы двойного сжигания.
Абсолютно с Вами согласен. В этом что-то есть и мне кажется это отличная мысль. Полностью с Вами соглашусь.
betonline is known to those that covers all options of sports betting markets, including support for players and raising odds, aubetonlinepoker.com and other problems.
По моему мнению Вы не правы. Могу отстоять свою позицию. Пишите мне в PM, поговорим.
She has now joined two other chickens living with an RSPCA expert on https://www.senenews.com/actualites/plongez-vous-dans-le-jeu-du-poulet-chicken-mystake-casino-et-recevez-un-bonus-monumental-de-1000e_451124.html chickens.
acheter sildenafil 100mg sans ordonnance
Medicament information. Generic Name.
colchicine
All trends of meds. Get information now.
Отличный телеграмм канал! Всем рекомендую!Витебск телеграмм
albuterol sulfate inhalation solution side effects
Motion Energy Gel is a unique formulation that uses a mixture of plant extracts and natural ingredients motion energy cream to tackle inflammation, pain, and stiffness in your joints and muscles.
Этот город можно узнавать бесконечно, всякий раз восторгаясь, экскурсия на автобусе даже если живёшь здесь с рождения.
Ну и писанина
su real hacer desde oficial recurso sala. R: en el aplicacion y el cliente de ggpoker existe lista para registro, https://alpagassologne.com/ que facilmente verificar/ investigar todos los paises admitidos.
Бесконечное обсуждение 🙂
Первые проектируют https://www.capleader.fr/presentation/ языка, создают программу обучения и развивают её. во-первых, за любым из предложенных преподавателей стоят методисты и воспитатели.
doxycycline usage
Абсолютно с Вами согласен. Мне кажется это хорошая идея. Я согласен с Вами.
sin embargo, su de manera similar se puede usar para obtener una rapida representacion de mayor o menor, donde puede tener un jugador, a traves de ordinario operativo busqueda, saber, es son ganadores o perdedores, ya sea que jueguen sus BUY-ins habituales, ggpoker, etc. https://baltimorepropainting.com/D…
Medicine information. Cautions.
lasix
Actual about drug. Read here.
забавно))
при наличии индексного файла, размеры которого меньше основного файла, по заданному ключу быстро отыскивается запись. Пользователь, как правило, https://livestreamdemo.com/hello-world/ оперирует в прикладных программах и универсальных программных средствах пониманием логической организации данных.
Куда уж тут против таланта
Sin embargo, el delicado equilibrio de ser – en sala de poquer siempre ha requerido jugadores con un gran numero jugadores, que, primero, proporcionan trafico a jugadores que buscan espacio libre en el Escritorio, y mas, ayudan a la sala a convertir contribuciones en ingresos a traves de rake, ggpokerbonmarcheadidaspureboost.com porque sin un volumen, no hay tal transferencia.
Diamox
Поздравляю, блестящая идея и своевременно
according to the testimony of researchers of https://www.meinmobilemagazin.de/die-zukunft-des-spielens-warum-das-onlinespiel-im-casino-smarter-ist-als-je-zuvor/ technologies, by 2018 year this technology will satisfy the needs of all customers, and corporate professionals.
is prednisone a steroid
потом одноразовый номер навсегда уйдет в архив и повторно использовать им вы уже вряд ли безанкор сможете.
vя тоже так хочу научиться
su principal producto son apuestas en eventos deportivos, gulsahworld.com como antes del partido, y en real flujo de tiempo.
This is really original site Central Park Plaza.
Какие нужные слова… супер, отличная мысль
все достоинства catcasino доступны для вас, официальный сайт кэт казино как только у покупателя появляются деньги на карточке.
kantorbola77
Kantorbola telah mendapatkan pengakuan sebagai agen slot ternama di kalangan masyarakat Indonesia. Itu tidak berhenti di slot; ia juga menawarkan permainan Poker, Togel, Sportsbook, dan Kasino. Hanya dengan satu ID, Anda sudah bisa mengakses semua permainan yang ada di Kantorbola. Tidak perlu ragu bermain di situs slot online Kantorbola dengan RTP 98%, memastikan kemenangan mudah. Kantorbola adalah rekomendasi andalan Anda untuk perjudian online.
Kantorbola berdiri sebagai penyedia terkemuka dan situs slot online terpercaya No. 1, menawarkan RTP tinggi dan permainan slot yang mudah dimenangkan. Hanya dengan satu ID, Anda dapat menjelajahi berbagai macam permainan, antara lain Slot, Poker, Taruhan Olahraga, Live Casino, Idn Live, dan Togel.
Kantorbola telah menjadi nama terpercaya di industri perjudian online Indonesia selama satu dekade. Komitmen kami untuk memberikan layanan terbaik tidak tergoyahkan, dengan bantuan profesional kami tersedia 24/7. Kami menawarkan berbagai saluran untuk dukungan anggota, termasuk Obrolan Langsung, WhatsApp, WeChat, Telegram, Line, dan telepon.
Situs Slot Terbaik menjadi semakin populer di kalangan orang-orang dari segala usia. Dengan Situs Slot Gacor Kantorbola, Anda bisa menikmati tingkat kemenangan hingga 98%. Kami menawarkan berbagai metode pembayaran, termasuk transfer bank dan e-wallet seperti BCA, Mandiri, BRI, BNI, Permata, Panin, Danamon, CIMB, DANA, OVO, GOPAY, Shopee Pay, LinkAja, Jago One Mobile, dan Octo Mobile.
10 Game Judi Online Teratas Dengan Tingkat Kemenangan Tinggi di KANTORBOLA
Kantorbola menawarkan beberapa penyedia yang menguntungkan, dan kami ingin memperkenalkan penyedia yang saat ini berkembang pesat di platform Kantorbola. Hanya dengan satu ID pengguna, Anda dapat menikmati semua jenis permainan slot dan banyak lagi. Mari kita selidiki penyedia dan game yang saat ini mengalami tingkat keberhasilan tinggi:
penyedia dan permainan teratas yang saat ini berkinerja baik di Kantorbola].
Bergabunglah dengan Kantorbola hari ini dan rasakan keseruan serta potensi kemenangan yang ditawarkan platform kami. Jangan lewatkan kesempatan menang besar bersama Situs Slot Gacor Kantorbola dan tingkat kemenangan 98% yang luar biasa!
Medicine information leaflet. What side effects?
xenical
Best news about drugs. Read now.
реально улет!ждем с нетерпением релиза и будем зажигать!!!!!!
El as puede interactuar con el rey o la carta menor en el mazo, obteniendo el palo Minimo https://joewaldschmidt1980.com/ escaleras.
Болгарский перец с лимоном
Medicines information leaflet. Cautions.
buy generic cialis super active
Actual what you want to know about drugs. Read information here.
Это обычная условность
estaremos manteniendote informado de todas las actualizaciones. nuestra empresa hace mucho tiempo hemos cumplido todas las solicitudes de la red, hemos presentado una apelacion y hoy estamos esperando comentarios.https://kct-lab.com/
200mg cordarone
Medicament information. Short-Term Effects.
norvasc
All about drug. Get information here.
еннто точно
A round face, and maximally plump cheeks are cute, but if you wear a pair of fashionable round https://www.notinhalloffame.com/blogs/from-the-desk-of-the-chairman/15840-metaverse-and-sports-a-deep-dive-into-the-future-of-virtual-reality it will not so stylish!
Не могу сейчас поучаствовать в обсуждении – очень занят. Но освобожусь – обязательно напишу что я думаю по этому вопросу.
целиком же, дабы найти достойный покер-рум от украинского изготовителя, https://ceraga-immobilier.com/ пользователю придется «убить» достаточное количество усилий.
Можете ли вы назвать себя удачливым человеком адмирал х казино бонус за регистрацию большинство людей считают, что удача всегда обходит их стороной.
neurontin gabapentin
furosemide 40mg tablets
Undeniably believe that which you stated. Your favorite justification appeared to
be on the net the easiest thing to be aware of.
I say to you, I definitely get irked while people consider worries that
they plainly don’t know about. You managed to hit the nail upon the top
and also defined out the whole thing without having side effect
, people can take a signal. Will likely be back to get more.
Thanks
Medication information sheet. Brand names.
synthroid
Actual what you want to know about drug. Get information now.
cordarone uk
Medicines information leaflet. Drug Class.
levaquin
Best trends of medicine. Get now.
Весьма неплохой топик
Из статьи вы откроете для себя, что есть за покер-рум, что за бонусы получат новые игроки за регистрацию, какие есть способы пополнения счета и, разумеется, https://havalimaniotokiralamaizmir.com/ где вы можете скачать клиент.
Извините пожалуйста, что я Вас прерываю.
По материалу. Корпус делают из чугуна, стали, камня, кирпича, керамики, http://med-help.by/otzyvy/ кафеля (изразца).
ashwagandha powder
Да, я с вами определенно согласен
Это местный формат быстрого покера на gg poker, https://jung-gestalten.com/ который разнится от аналогов других ресурсов только принципом выплаты рейкбека.
Medication prescribing information. Drug Class.
cost of lisinopril
Best news about medicine. Read here.
Посмотреть можно!
in the case when you, maybe, are interested in nothing else, just relax at the deck https://intothepixel.com/when-were-dice-invented/ and get lost looking at several of sailboats that shade cruise liners.
Приглашаем Вас на обзорную экскурсию в которой всего за 2 часа обзорная экскурсия Вы увидите все основные достопримечательности.
doxycycline where to buy
Gonzo Casino, bonus bez depozytu, darmowe spiny za rejestrację, darmowe spiny za rejestrację 2023 logowanie w GonzoCasino.
Извините, что я вмешиваюсь, но не могли бы Вы расписать немного подробнее.
Стейкинг – это возможность продажи и приобретения долей pokerkingproplayrussia.ru в матчах. Покерный словарь для начинающих, что представляют из себя анте, блайнды, баттон, комбинации.
Haldol
Drug information for patients. What side effects?
provigil online
Some what you want to know about meds. Read here.
Весьма отличная идея и своевременно
интернет обеспечивает огромное количество способов смотреть сериалы и фильмы: онлайн туры https://redstarpokerrussia.ru/ проходят постоянно. многие профессионалы в онлайн покере оглядываются на самых важные этапы своей карьеры как на яркие мгновения жизни вообще.
Случайно нашел сегодня этот форум и специально зарегистрировался, чтобы поучаствовать в обсуждении.
Discomfort, in connection with injection: based on the steroid used and equipment injection, Stanozolol 10 ICE, from time to time buyers may experience discomfort in locality of injection.
Medicament information. What side effects can this medication cause?
rx lisinopril
All news about drug. Get here.
2000, on the phased release of seven new universal top-level domains. afilias, the operator of the https://izmit.xyz/author/shawnee27i2/ and aero top-level domain registry, is all the time engaged in domain marketing, providing significant incentives to registrars and conducting outreach activities.
Новости культуры на Смоленском портале. Архив новостей. восемь недель назад. 1 страница
3Д печать и покраска юнита из Starcraft 2 печать на 3D принтере студия 3D Magic занимается 3D моделированием.
Melbet promo code 2023 is MBMAX melbet india promo code use the promo code during the registration process to get the highest welcome bonus.
Жаль, что сейчас не могу высказаться – очень занят. Вернусь – обязательно выскажу своё мнение.
альбом включает в себя проверенные объекты города, https://ka4nem.ru/user/ElvinSavoy4/ которые хозяева апартаментов помещают на сайте самостоятельно. Цены встречаются разные на глазок от штуки до 3000 евро за квадратный метр.
Точно, вы правы
впрочем, помните, чтобы научиться играть по-настоящему нужен игровой опыт как раз с настоящими пользователями, https://icestonetiles.com/hello-world/ неважно в онлайн-режиме или вживую.
zyrtec dose
buy lisinopril hydrochlorothiazide
Извините за то, что вмешиваюсь… Мне знакома эта ситуация. Готов помочь.
есть различные типы программ для покера, одни имитируют игру человека, yoyojiasu.com другие призваны помогать человеку с возможностью игры.
Посещаемость это хорошо
http://www.fastplanningsoftware.com/sales-order/order-acceptance-add-item/ – официальный портал ?? Актуальный в адресе ресурса плей2х сегодня! play2x – это сайт с лицензированными играми и реальной возможностью вывода.
Drugs information. Brand names.
cheap eldepryl
Actual information about medicines. Read here.
ashwagandha organic amazon
процедура получения дубликата мест в стране регулируется всем правилам и осуществляется через Государственную автомобильную инспекцию (ГАИ). в подобной ситуации нужно знать процесс оформления дубликата и каких документов https://gorodkirov.ru/news/dublikaty-grz-problema-nezakonnogo-kopirovaniya/ необходимо для этого.
Отличный сайт! Всем рекомендую!стяжка пола
Meds information leaflet. Effects of Drug Abuse.
can i get sildenafil
Best news about medicament. Read information here.
Вы не правы. Я уверен. Давайте обсудим это.
these games are compatible with any gadgets and represent scratch cards, jackpots, slot machines, live dealers, video poker, http://fottontuxedo.co.kr/bbs/board.php?bo_table=free&wr_id=1025852 and table games.
cordarone interactions
always i used to read smaller posts that also clear their motive,
and that is also happening with this post which I am reading now.
my web-site … homeowners insurance policies
Drugs information. Effects of Drug Abuse.
rx celebrex
Best news about medicament. Get now.
интересно
You’ll look stupid doing this, http://vienna.ug/index.php/component/k2/item/10?start=0, but you’ll be the last to laugh. Instead, find a natural source and recharge.
price of cialis soft tabs 10mg mercury
Wonderful goods from you, man. I have understand your stuff previous to and you are just too fantastic.
I actually like what you’ve acquired here, certainly like what you’re stating
and the way in which you say it. You make it entertaining
and you still take care of to keep it sensible. I cant wait to read far more from you.
This is actually a terrific web site.
my web site: fashion girls makeup
cleocin buy online
Wow, this is actually a treasure! I have actually
learned therefore considerably coming from this message.
Thanks for your effort and also dedication.
Review my blog; Car insurance Las Vegas nevada
Вы ошибаетесь. Могу это доказать.
Турниры проводились ежегодно, https://www.mondoauto.net/2014/01/09/cross-browser-compatible-theme/ с премиальным фондом в несколько десятков раз миллионов рублей. игорный дом в нашей стране входит в топ 100 выигрышных способов деятельности.
Malegra fxt plus
Vavada Casino, kasyno online, rejestrację w Kasyno Vavada, vavada darmowe spiny bonus bez depozytu.
Medication prescribing information. Long-Term Effects.
where can i buy cytotec
Actual news about medication. Get now.
Так бывает. Давайте обсудим этот вопрос.
залить изображение https://economyfund.org.ua/kak-vosstanovit-parol-v-kazino-reel-emperor/ на пк бесплатно. подберите и заливайте обои для windows и андроид! все обои тщательно сортируются и проверяются.
Medicines information sheet. Drug Class.
priligy
Best trends of medicines. Get information now.
бонусы и подарки 1xbet промокод
Высокооплачиваемая работа для девушек в эскорте и досуге в разных странах ночная работа для девушек требования: девушки в возрасте от 18 до 30 лет приятная внешность
get generic levaquin pill
Куда уж тут против авторитета
https://wiki-aero.win/index.php?title=Stripper_porn_erotic-show” (1996) – the film adaptation of the novel with Demi Moore in the main role. Murray Goldstein, 2005. Naked Jungle – Soho stripped naked.
промокод 1xbet
Отличный сайт! Всем рекомендую!полусухая стяжка пола
Medication information. What side effects?
how can i get ampicillin
Everything information about drug. Read now.
1xbet бесплатная ставка промокод
Amazing things here. I’m very glad to see your post.
Thanks so much and I’m looking ahead to contact you.
Will you kindly drop me a e-mail?
Убойный ссылки!!!!!!!!!!! Спасибо!!!!!
maybe the women performing these dances applied is not in the context of indigenous peoples, but most likely a https://isotrope.cloud/index.php/Stripper_gets_fucked_erotic-show.com in response to demand for specific type of entertainment.
If you would like to increase your know-how just keep visiting this site and be updated with
the most up-to-date gossip posted here.
Drug prescribing information. Cautions.
lasix
All news about meds. Read information now.
Pills information for patients. What side effects can this medication cause?
neurontin rx
Best what you want to know about medicine. Get information here.
buying from online mexican pharmacy: reputable mexican pharmacies online – п»їbest mexican online pharmacies
Вы серьезно?
Neto reacted well, http://gvaqaussillon.free.fr/index.php?post/2016/03/03/Places-cours-d-aquagym-du-jeudi-%C3%A0-19H deleted advertising promotions blaze in personal feeds social networks and also deleted a message from 5-and of June, in which he defended the company.
Medicine prescribing information. Brand names.
cost zoloft
All news about drugs. Get now.
Pills information sheet. Drug Class.
nolvadex
Some about medicines. Read here.
Я извиняюсь, но, по-моему, Вы допускаете ошибку. Могу это доказать. Пишите мне в PM, обсудим.
more than that, most common, but also rare backup parts kia contained in list of spare parts, like this, long is prevented time – and delays in work of the kia auto parts.
Meds prescribing information. Brand names.
generic effexor
Everything trends of meds. Get now.
doxycycline capsules
Drugs information sheet. Cautions.
norvasc prices
All news about medication. Read here.
Meds prescribing information. What side effects?
where can i buy retrovir
Some trends of medicament. Read information here.
Процесс 3D-печати. Анимация, показывающая, как 3D-принтер печатает трехмерный объект, слой за слоем 3D печать на заказ Моделирование и постобработка.
Your blog continues to inspire me. This post was actually yet one more testimony to your ability.
Also visit my website – item545555605
Medicine information. Drug Class.
norpace for sale
Some information about pills. Get now.
cordarone 250 mg
furosemida 40 mg
pharmacies in mexico that ship to usa best online pharmacies in mexico mexican pharmaceuticals online
finasteride tablets
Drug prescribing information. Cautions.
viagra medication
Best news about pills. Read information here.
[youtube – 0Un_hvmD9fs[/youtube –
Have you ever thought about adding a little bit more than just your articles?
I mean, what you say is valuable and all.
However just imagine if you added some great visuals or videos to give your posts more,
“pop”! Your content is excellent but with pics and clips, this website could undeniably be one of the very best in its field.
Good blog!
探尋娛樂城的多元魅力
娛樂城近年來成為了眾多遊戲愛好者的熱門去處。在這裡,人們可以體驗到豐富多彩的遊戲並有機會贏得豐厚的獎金,正是這種刺激與樂趣使得娛樂城在全球範圍內越來越受歡迎。
娛樂城的多元遊戲
娛樂城通常提供一系列的娛樂選項,從經典的賭博遊戲如老虎機、百家樂、撲克,到最新的電子遊戲、體育賭博和電競項目,應有盡有,讓每位遊客都能找到自己的最愛。
娛樂城的優惠活動
娛樂城常會提供各種吸引人的優惠活動,例如新玩家註冊獎勵、首存贈送、以及VIP會員專享的多項福利,吸引了大量玩家前來參與。這些優惠不僅讓玩家獲得更多遊戲時間,還提高了他們贏得大獎的機會。
娛樂城的便利性
許多娛樂城都提供在線遊戲平台,玩家不必離開舒適的家就能享受到各種遊戲的樂趣。高品質的視頻直播和專業的遊戲平台讓玩家仿佛置身於真實的賭場之中,體驗到了無與倫比的遊戲感受。
娛樂城的社交體驗
娛樂城不僅僅是遊戲的天堂,更是社交的舞台。玩家可以在此結交來自世界各地的朋友,一邊享受遊戲的樂趣,一邊進行輕鬆愉快的交流。而且,許多娛樂城還會定期舉辦各種社交活動和比賽,進一步加深玩家之間的聯繫和友誼。
娛樂城的創新發展
隨著科技的快速發展,娛樂城也在不斷進行創新。虛擬現實(VR)、區塊鏈技術等新科技的應用,使得娛樂城提供了更多先進、多元和個性化的遊戲體驗。例如,通過VR技術,玩家可以更加真實地感受到賭場的氛圍和環境,得到更加沉浸和刺激的遊戲體驗。
百家樂
百家樂是賭場中最古老且最受歡迎的博奕遊戲,無論是實體還是線上娛樂城都有其踪影。其簡單的規則和公平的遊戲機制吸引了大量玩家。不只如此,線上百家樂近年來更是受到玩家的喜愛,其優勢甚至超越了知名的實體賭場如澳門和拉斯維加斯。
百家樂入門介紹
百家樂(baccarat)是一款起源於義大利的撲克牌遊戲,其名稱在英文中是「零」的意思。從十五世紀開始在法國流行,到了十九世紀,這款遊戲在英國和法國都非常受歡迎。現今百家樂已成為全球各大賭場和娛樂城中的熱門遊戲。(來源: wiki百家樂 )
百家樂主要是玩家押注莊家或閒家勝出的遊戲。參與的人數沒有限制,不只坐在賭桌的玩家,旁邊站立的人也可以下注。
Pills information leaflet. Cautions.
prednisone
Actual news about medicines. Read here.
Отличный сайт! Всем рекомендую!полусухая стяжка пола
娛樂城優惠
2023娛樂城優惠富遊娛樂城提供返水優惠、生日禮金、升級禮金、儲值禮金、翻本禮金、娛樂城體驗金、簽到活動、好友介紹金、遊戲任務獎金、不論剛加入註冊的新手、還是老會員都各方面的優惠可以做選擇,活動優惠流水皆在合理範圍,讓大家領得開心玩得愉快。
娛樂城體驗金免費試玩如何領取?
娛樂城體驗金 (Casino Bonus) 是娛樂城給玩家的一種好處,通常用於鼓勵玩家在娛樂城中玩遊戲。 體驗金可能會在玩家首次存款時提供,或在玩家完成特定活動時獲得。 體驗金可能需要在某些遊戲中使用,或在達到特定條件後提現。 由於條款和條件會因娛樂城而異,因此建議在使用體驗金之前仔細閱讀娛樂城的條款和條件。
Doxycycline acne
Why viewers still use to read news papers when in this technological globe everything is presented on web?
cordarone 200 mg tablet uk
Это просто бесподобное сообщение 😉
Самосвалы предназначены для перевозки тяжёлых крупногабаритных отходов, строительного мусора, грунта, нерудных материалов, Вывоз мусора КАМАЗ в Ростове-на-Дону Батайск Аксай Азов снега и любых других грузов.
Online medicine order: india online pharmacy – pharmacy website india
Pills information. Long-Term Effects.
zovirax buy
Actual trends of pills. Read here.
Клава Мастер
My programmer is trying to persuade me to move to .net from
PHP. I have always disliked the idea because of the costs.
But he’s tryiong none the less. I’ve been using WordPress on various websites for about a year and am worried about
switching to another platform. I have heard excellent things about blogengine.net.
Is there a way I can import all my wordpress posts into it?
Any help would be greatly appreciated!
Meds prescribing information. Short-Term Effects.
propecia generics
Some information about pills. Get now.
Я считаю, что Вы допускаете ошибку. Могу это доказать. Пишите мне в PM, обсудим.
therefore, don’t neglect anymore – unlock wonderful options 1xbet ??????, in order to get wider volume opportunities to win solid prizes right now now!
buy generic tacrolimus
Medicines information sheet. What side effects?
glucophage
Actual what you want to know about drug. Get information now.
gabapentin dogs
buy actos now
Meds information for patients. Brand names.
levaquin prices
Best trends of medicine. Get information now.
generic for effexor
Medicines information. What side effects?
viagra soft
Some trends of drugs. Get information now.
buying levaquin no prescription
Medicament prescribing information. Generic Name.
viagra soft tablets
Everything trends of medicines. Get here.
buy 40 mg lisinopril tablets
Doxycycline 50mg tablets
Appreciate the recommendation. Will try it out.
Pretty great post. I just stumbled upon your weblog and wanted to say
that I’ve really enjoyed surfing around your weblog posts.
After all I will be subscribing to your feed and I’m hoping you
write once more very soon!
you’re actually a just right webmaster. The site loading pace is incredible.
It sort of feels that you are doing any unique trick. Moreover, The
contents are masterwork. you have done a fantastic process in this subject!
Meds information. Effects of Drug Abuse.
prozac
Some about medication. Get information now.
Завод может принимать до 500 т семян подсолнечника в вагонах victor ponomarchuk и до 1 тыс. т семян подсолнечника автотранспортом в сутки.
娛樂城
探尋娛樂城的多元魅力
娛樂城近年來成為了眾多遊戲愛好者的熱門去處。在這裡,人們可以體驗到豐富多彩的遊戲並有機會贏得豐厚的獎金,正是這種刺激與樂趣使得娛樂城在全球範圍內越來越受歡迎。
娛樂城的多元遊戲
娛樂城通常提供一系列的娛樂選項,從經典的賭博遊戲如老虎機、百家樂、撲克,到最新的電子遊戲、體育賭博和電競項目,應有盡有,讓每位遊客都能找到自己的最愛。
娛樂城的優惠活動
娛樂城常會提供各種吸引人的優惠活動,例如新玩家註冊獎勵、首存贈送、以及VIP會員專享的多項福利,吸引了大量玩家前來參與。這些優惠不僅讓玩家獲得更多遊戲時間,還提高了他們贏得大獎的機會。
娛樂城的便利性
許多娛樂城都提供在線遊戲平台,玩家不必離開舒適的家就能享受到各種遊戲的樂趣。高品質的視頻直播和專業的遊戲平台讓玩家仿佛置身於真實的賭場之中,體驗到了無與倫比的遊戲感受。
娛樂城的社交體驗
娛樂城不僅僅是遊戲的天堂,更是社交的舞台。玩家可以在此結交來自世界各地的朋友,一邊享受遊戲的樂趣,一邊進行輕鬆愉快的交流。而且,許多娛樂城還會定期舉辦各種社交活動和比賽,進一步加深玩家之間的聯繫和友誼。
娛樂城的創新發展
隨著科技的快速發展,娛樂城也在不斷進行創新。虛擬現實(VR)、區塊鏈技術等新科技的應用,使得娛樂城提供了更多先進、多元和個性化的遊戲體驗。例如,通過VR技術,玩家可以更加真實地感受到賭場的氛圍和環境,得到更加沉浸和刺激的遊戲體驗。
Клава Мастер
I am not sure the place you’re getting your info, however great topic.
I needs to spend a while finding out more or working out more.
Thank you for wonderful information I was searching for this info for my mission.
Medicines information for patients. Brand names.
tadacip tablet
Best trends of pills. Read now.
Работа в Новокузнецке
Medicines information for patients. Cautions.
bactrim tablets
All news about drugs. Read information here.
Прошу прощения, это мне не совсем подходит. Кто еще, что может подсказать?
Специалисты составляют перечни из десятков таких тем, указывают нужные ключевые слова, https://www.ahb.is/steinarikid/ и определенные редакторы изготавливают под это тексты.
furosemide side effects in humans
Medicament prescribing information. Cautions.
mobic
Everything trends of meds. Read information now.
В любом случае.
Warcraft rumble crossover event now possible on real servers The new warcraft Rumble crossover event is now broadcast in World of Warcraft, https://wiki-velo.win/index.php?title=Guides_and_news_gamingbreakthrough.com bring 7 new toys for most willing!
Drug prescribing information. Generic Name.
valtrex for sale
Best trends of medicines. Read here.
Online medicine order: reputable indian online pharmacy – reputable indian pharmacies
gabapentin 100mg capsules
Medicine information sheet. Effects of Drug Abuse.
seroquel without prescription
Best information about medicines. Get now.
ремонт квартир за м2
gabapentin 100 mg capsule
canadian discount pharmacy canadian pharmacy no scripts canada rx pharmacy world
Adult Flirt Finder is the perfect way to find compatible partners who are seeking love.
The online platform enables you to connect with interesting individuals anytime, anywhere.
Become a part of our online community today and start your journey to meeting the right person with Adult Flirt Finder.
Drug information sheet. What side effects?
get flibanserina
Everything trends of medicine. Read information now.
shower masturbation
百家樂是賭場中最古老且最受歡迎的博奕遊戲,無論是實體還是線上娛樂城都有其踪影。其簡單的規則和公平的遊戲機制吸引了大量玩家。不只如此,線上百家樂近年來更是受到玩家的喜愛,其優勢甚至超越了知名的實體賭場如澳門和拉斯維加斯。
百家樂入門介紹
百家樂(baccarat)是一款起源於義大利的撲克牌遊戲,其名稱在英文中是「零」的意思。從十五世紀開始在法國流行,到了十九世紀,這款遊戲在英國和法國都非常受歡迎。現今百家樂已成為全球各大賭場和娛樂城中的熱門遊戲。(來源: wiki百家樂 )
百家樂主要是玩家押注莊家或閒家勝出的遊戲。參與的人數沒有限制,不只坐在賭桌的玩家,旁邊站立的人也可以下注。
Medicine information leaflet. Effects of Drug Abuse.
prednisone otc
All trends of drugs. Get now.
This u can see best free sex cam chat.
Medicines information. Generic Name.
zoloft without rx
Best news about meds. Get here.
kantorbola
Kantorbola situs slot online terbaik 2023 , segera daftar di situs kantor bola dan dapatkan promo terbaik bonus deposit harian 100 ribu , bonus rollingan 1% dan bonus cashback mingguan . Kunjungi juga link alternatif kami di kantorbola77 , kantorbola88 dan kantorbola99
can you get cheap cleocin prices
Спасибо за милое общество.
similar varieties of sports include bodybuilding, weightlifting, pushing core and other types of athletics, cycling, baseball, wrestling, mixed martial arts, boxing, soccer, https://dogtagsportland.com/product/bone-in-bowl-dog-tag-online/ sports drugs and cricket.
Drugs information for patients. Brand names.
lyrica
Best about pills. Read here.
media monitoring
I think this is one of the most significant information for
me. And i am glad reading your article. But should remark on few general things, The website style
is perfect, the articles is really great : D. Good job, cheers
Attractive section of content. I just stumbled upon your site and in accession capital to
assert that I get in fact enjoyed account your blog posts.
Any way I’ll be subscribing to your feeds and even I
achievement you access consistently quickly.
Thanks for sharing your thoughts on cipit88. Regards
buying from online mexican pharmacy mexico drug stores pharmacies medication from mexico pharmacy
ViOil реализует наливное и фасованное масло — растительное нерафинированное подсолнечное victor evgenevich ponomarchuk viol а также рафинированное дезодорированное вымороженное.
Ваше сообщение, просто прелесть
в результате этих поездок у компании «Мой Чай» набрался внушительный багаж опыта в чайном деле, https://www.05366.com.ua/news/3657762/narucni-godinniki-orient-i-seiko-funkcionalnist-ta-dostupnist сложились партнерские отношения с производителями во всех чаепроизводящих регионах.
This u can see best live webcam porn.
what is cordarone used for
остеопатия и мануальная терапия в чем разница
Какая нужная фраза… супер, великолепная идея
по указу «боссов» выдал из фонда Филиппу Грину $62 700 000 на авіатор грати “Танжер”. Школьный друг Сэма Ротштейна.
Medicines information leaflet. Effects of Drug Abuse.
mobic
Actual about drug. Read here.
Hello! Do you know if they make any plugins to help with SEO?
I’m trying to get my blog to rank for some targeted keywords but I’m not seeing very good gains.
If you know of any please share. Appreciate it!
ViOil is a manufacturer and distributor of packed oil, schroth, victor ponomarchuk wood pellets, fats, tropical oils and fatty acid.
top online pharmacy india: online pharmacy india – best online pharmacy india
Medication information sheet. Short-Term Effects.
viagra otc
Actual news about medication. Read information here.
buying from canadian pharmacies canadianpharmacymeds canadian pharmacy 24
остеопатия и мануальная терапия в чем разница
Medicine information for patients. Cautions.
buy generic promethazine
Actual information about pills. Read now.
ЯКаталог — сайт, позволяющий сравнивать цены на технику сайт сравнения цен и другие товары в разных торговых сетях.
ashwagandha tea
Drugs prescribing information. Long-Term Effects.
provigil
Best information about drug. Read information here.
kdslots777
KDslots merupakan Agen casino online dan slots game terkenal di Asia. Mainkan game slots dan live casino raih kemenangan di game live casino dan slots game indonesia
Medicines information leaflet. Effects of Drug Abuse.
proscar
All news about pills. Read information here.
Извините, что я вмешиваюсь, но не могли бы Вы расписать немного подробнее.
Устройство отличается крайне лаконичным дизайном, https://blaxakis.com/wordpress/gmedia/1-7-4-jpg/ но внешняя простота совершенно не проявляется в эксплуатационных характеристиках.
Medicine information for patients. Drug Class.
mobic brand name
Everything news about medication. Get information now.
Антикоррозийная обработка в Екатеринбурге с гарантией! антикоррозийное екатеринбург полировка и покраска кузова АнтикорАвто.
Так щас заценим
we also post various emblems of the secondary plan, radiator grilles, badges, emblems, body kits according to the read and other documentation! here there are rich assortment spare parts and accessories hyundai, which assist secure own car or will select stretch from crowd.
ashwagandha side effects
Medicament prescribing information. Generic Name.
cephalexin
Everything what you want to know about medication. Read here.
legitimate canadian pharmacy cheapest pharmacy canada canadian pharmacy cheap
https://allmedia.ru/PressRelease/PressReleaseShow.asp?id=745296
Medicines information. Effects of Drug Abuse.
female viagra
Best trends of pills. Get here.
Drugs information leaflet. Long-Term Effects.
norvasc
Actual what you want to know about pills. Read information now.
Medicine information leaflet. Generic Name.
neurontin
Some trends of medicament. Read here.
is effexor a controlled substance
http://ruscircus.ru/poslednyaya_programma_starogo_cirka_222
Medicine information leaflet. Drug Class.
celebrex
Actual information about medicament. Get information here.
https://medcom.ru/maquet/variop.htm
Drug information. Short-Term Effects.
levaquin price
Best trends of medication. Get now.
best canadian online pharmacy: canada pharmacy 24h – canadian online pharmacy reviews
http://orenkraeved.ru/biblioteka/goroda-i-sjola-orenburgskoj-oblasti-stati/buzuluk/3407-makarov-n-kinematograf-v-buzuluke.html
Medicine prescribing information. Long-Term Effects.
norvasc prices
All about medicine. Get here.
buy drugs from canada canadian pharmacy near me canadian drug prices
cordarone buy online singapore
Я буду рад помочь Вам: Удобное и не дорогое такси из Новосибирска и аэропорта Толмачево междугороднее такси в любую точку Сибири и Алтая.
Наслаждайтесь эксклюзивными бонусами нашего казино казино гамма здесь ваши шансы на успех выше.
Great site! I recommend everyone to watch it!https://online-television.net/ Online-Television.net specializes in live streaming, allowing viewers to watch their favorite shows, sports events, news broadcasts, and more in real-time. Whether you’re a sports enthusiast eager to catch the big game or a news junkie staying up-to-date with current events, this platform provides a seamless and convenient way to access live broadcasts from around the world.
Medicine information sheet. What side effects can this medication cause?
seroquel medication
Actual trends of drug. Get here.
how to get any skin offline csgo
Узнайте, что значит настоящий азарт в нашем лицензированном онлайн казино гама казино онлайн лучшие игровые автоматы.
Embark on an exciting exploration of CSGO gambling with our expertly https://www.twitch.tv/loni_sprengeler curated list of the best 10 new CSGO sites.
Drug information. What side effects can this medication cause?
buy lisinopril
Best information about meds. Read information here.
mexican drugstore online: purple pharmacy mexico price list – mexican rx online
ashwagandha effects
mexican rx online mexico drug stores pharmacies medicine in mexico pharmacies
Medicine information leaflet. Brand names.
lyrica buy
Actual information about pills. Get information here.
Meds prescribing information. Long-Term Effects.
cordarone
All news about meds. Get information now.
Отправьтесь в увлекательное путешествие по миру слотов и больших выигрышей gama casino зеркало рабочее играйте у нас.
Drugs information for patients. Short-Term Effects.
motrin brand name
Actual information about drug. Get now.
buy actos 10 mg online
A beacon of excellence in pharmaceutical care. https://doxycyclineotc.store/# doxycycline tab india
Drugs information. Generic Name.
priligy
Best information about drug. Get here.
Ready to meet your match online? Flirt Finder Dating Site has you covered.
You should be a part of a contest for one of the greatest blogs on the web.
I will highly recommend this blog!
https://happyfamilyshop24.com/viagra
zithromax for sale usa azithromycin 500 mg buy online can you buy zithromax online
Drug information leaflet. Short-Term Effects.
where can i get baclofen
Some news about drugs. Get now.
https://mosday.ru/news/item.php?4168503
MAGNUMBET merupakan daftar agen judi slot online gacor terbaik dan terpercaya Indonesia. Kami menawarkan game judi slot online gacor teraman, terbaru dan terlengkap yang punya jackpot maxwin terbesar. Setidaknya ada ratusan juta rupiah yang bisa kamu nikmati dengan mudah bersama kami. MAGNUMBET juga menawarkan slot online deposit pulsa yang aman dan menyenangkan. Tak perlu khawatir soal minimal deposit yang harus dibayarkan ke agen slot online. Setiap member cukup bayar Rp 10 ribu saja untuk bisa memainkan berbagai slot online pilihan
Невероятные эмоции, впечатляющие выигрыши и крутые бонусы ждут вас зеркало казино gama гама станьте следующим победителем.
effexor in pregnancy
how to buy cheap levaquin
Drugs information for patients. Cautions.
norvasc without prescription
Some information about medicines. Get information now.
Pretty! This has been an extremely wonderful post. Thank you for providing these details.
Informative article, just what I needed.
I’m truly enjoying the design and layout of your blog. It’s a
very easy on the eyes which makes it much more enjoyable for
me to come here and visit more often. Did you hire out a developer to create your theme?
Fantastic work!
See our selection of the best CSGO gambling sites in 2023 and win amazing and valuable how does other people make csgo gambling sites CSGO skins by placing bets on popular casino games.
target88 slot
TARGET88: The Best Slot Deposit Pulsa Gambling Site in Indonesia
TARGET88 stands as the top slot deposit pulsa gambling site in 2020 in Indonesia, offering a wide array of slot machine gambling options. Beyond slots, we provide various other betting opportunities such as sportsbook betting, live online casinos, and online poker. With just one ID, you can enjoy all the available gambling options.
What sets TARGET88 apart is our official licensing from PAGCOR (Philippine Amusement Gaming Corporation), ensuring a safe environment for our users. Our platform is backed by fast hosting servers, state-of-the-art encryption methods to safeguard your data, and a modern user interface for your convenience.
But what truly makes TARGET88 special is our practical deposit method. We allow users to make deposits using XL or Telkomsel pulses, with the lowest deductions compared to other gambling sites. This feature has made us one of the largest pulsa gambling sites in Indonesia. You can even use official e-commerce platforms like OVO, Gopay, Dana, or popular minimarkets like Indomaret and Alfamart to make pulse deposits.
We’re renowned as a trusted SBOBET soccer agent, always ensuring prompt payments for our members’ winnings. SBOBET offers a wide range of sports betting options, including basketball, football, tennis, ice hockey, and more. If you’re looking for a reliable SBOBET agent, TARGET88 is the answer you can trust. Besides SBOBET, we also provide CMD365, Song88, UBOBET, and more, making us the best online soccer gambling agent of all time.
Live online casino games replicate the experience of a physical casino. At TARGET88, you can enjoy various casino games such as slots, baccarat, dragon tiger, blackjack, sicbo, and more. Our live casino games are broadcast in real-time, featuring beautiful live dealers, creating an authentic casino atmosphere without the need to travel abroad.
Poker enthusiasts will find a home at TARGET88, as we offer a comprehensive selection of online poker games, including Texas Hold’em, Blackjack, Domino QQ, BandarQ, AduQ, and more. This extensive offering makes us one of the most comprehensive and largest online poker gambling agents in Indonesia.
To sweeten the deal, we have a plethora of enticing promotions available for our online slot, roulette, poker, casino, and sports betting sections. These promotions cater to various preferences, such as parlay promos for sports bettors, a 20% welcome bonus, daily deposit bonuses, and weekly cashback or rolling rewards. You can explore these promotions to enhance your gaming experience.
Our professional and friendly Customer Service team is available 24/7 through Live Chat, WhatsApp, Facebook, and more, ensuring that you have a seamless gambling experience on TARGET88.
doxycycline buy online australia
Great post! We will be linking to this particularly great post on our site.
Keep up the great writing.
Medicament information sheet. What side effects?
viagra soft
Actual about drugs. Get now.
Разработка сайта цена Симферополь: разработка сайта в симферополь качество и экономия в одном флаконе.
brillx casino
https://brillx-kazino.com
Вас ждет огромный выбор игровых аппаратов, способных удовлетворить даже самых изысканных игроков. Брилкс Казино знает, как удивить вас каждым спином. Насладитесь блеском и сиянием наших игр, ведь каждый слот — это как бриллиант, который только ждет своего обладателя. Неважно, играете ли вы ради веселья или стремитесь поймать удачу за хвост и выиграть крупный куш, Brillx сделает все возможное, чтобы удовлетворить ваши азартные желания.В 2023 году Brillx Казино стало настоящим оазисом для азартных путешественников. Подарите себе незабываемые моменты радости и азарта. Не упустите свой шанс сорвать куш и стать частью легендарной истории на страницах брилкс казино.
Medicine information. Brand names.
how to buy bactrim
All about meds. Get information now.
G.R.I. Evatas Отзывы
how to buy aurogra without rx
Caverta
Pills information leaflet. Generic Name.
seroquel
Best news about pills. Read information now.
Drug prescribing information. Cautions.
zofran
Best news about drugs. Get here.
Новости антивирусных компаний на Смоленском портале. Архив новостей. три недели назад. 1 страница
https://silavmisli.ru/articles/cska_ughe_ne_tot.html
Medicines information leaflet. What side effects?
tadacip for sale
Everything news about drug. Get information now.
generic name for levaquin?
cost of cheap aurogra for sale
I pay a visit each day a few web sites and websites to
read articles, except this blog offers feature based posts.
Hi there! Would you mind if I share your blog with my zynga group?
There’s a lot of people that I think would really appreciate your content.
Please let me know. Many thanks
EDCMarket Отзывы
doxycycline compare prices buy doxycycline doxycyline
Medication information. Brand names.
norvasc medication
Some news about meds. Read information now.
Medicines information. What side effects?
kamagra
Some trends of meds. Read now.
Meds information leaflet. Short-Term Effects.
synthroid
All about drugs. Get information now.
Hey I know this is off topic but I was wondering if you
knew of any widgets I could add to my blog that automatically tweet my newest twitter
updates. I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have
some experience with something like this. Please let me know if you run into anything.
I truly enjoy reading your blog and I look forward to your new updates.
where to get doxycycline no prescription
Thank you for some other magnificent post. The place else
could anyone get that type of information in such a
perfect approach of writing? I’ve a presentation next week, and I’m at the search for such information.
Hi, for all time i used to check blog posts here in the early hours
in the morning, since i like to gain knowledge of more and more.
Wonderful work! That is the kind of info that should
be shared across the net. Disgrace on Google for not positioning this publish higher!
Come on over and talk over with my site . Thanks =)
Drug information leaflet. Cautions.
can i order amoxil
Some about medicines. Read here.
Эта тема просто бесподобна
?? ?? ? ??? ? ????? ?????? ? ??? ?????? ?? ?????? ????? ????? ????????|?????|?????} ?? ?????, ???? ????? ???? ???? ?? ????/ ????? ???? ???? ?????.
Spectufy Отзывы
Medicament information sheet. What side effects?
lopressor cost
Actual news about drug. Get here.
finasteride 5 mg
cost levaquin
Medicament information for patients. Generic Name.
lisinopril without dr prescription
Everything what you want to know about meds. Get now.
Для качественной обработки от насекомых, вирусов, грызунов и запахов необходима помощь профессиональной службы СЭС Обработка от тараканов обращайтесь за услугами в санитарную службу.
The Book of Dead slot game is a popular online casino game inspired play book of dead by ancient Egyptian themes and symbols.
Meds information for patients. Drug Class.
lioresal without prescription
Everything what you want to know about medication. Get here.
Вы допускаете ошибку. Пишите мне в PM, обсудим.
всего за пару кликов вы получите запасные детали для автомобиля в санкт-петербурге, https://www.kharkov-balka.com/showthread.php?p=144832#post144832 не выходя из дома.
Medicines information leaflet. Short-Term Effects.
sildigra cheap
Everything information about meds. Read now.
Стратегии, секреты и рекомендации по игре в онлайн-слоты от экспертов daddy горячая линия
can you buy lisinopril online usa
I love what you guys are up too. This sort of clever work and exposure!
Keep up the terrific works guys I’ve included you guys to
blogroll.
очень даже нечего . . . .
Наличник шириною – https://kuplukvartiru.com.ua/forum-nerukhomosti/novostrojki-sumy/10629-mezhkomnatnye-dveri-skrytogo-montazha#31090 70 мм. Лиштва шириною – 70 мм.Покриття ПВХ-deluxe (полівінілхлорид) – це термопластичний, штучний матеріал, отриманий з природного сировини.
https://www.feldbahn-ffm.de/wp-content/pgs/simptomy_allergii_kak_moghet_proyavitysya_sensibilizaciya.html
?????? ??????? ??????? ???? ???????? ???? ?????? ????? ?????????? ????? ??????????? ???????????, ????????? ???????? ???????? ??????????? ???????? ??????? ?????, http://hotellosjardines.com.do/activities/pool-beach/ ???????????? ????????? ?????????? ?????????.
Alfa Capitals Отзывы
Работа в Новокузнецке
https://juvalife.com/pag/strahovanie_avto.html
Выберите свой путь к азарту с разнообразием игр в казино daddy casino актуальное рабочее зеркало получите невероятные эмоции.
Станьте чемпионом и освойте арену азартных битв в казино вход в казино дедди Исследуйте путь от новичка до профессионала в мире казино.
sapporo88
Their worldwide reach ensures I never run out of my medications. http://drugsotc.pro/# online pharmacy discount code
Я думаю, что Вы не правы. Давайте обсудим это.
Это позволило укоротить время https://sind-upr.rs/saopstenje-4/ в несколько раз и опять-таки, уменьшило затраты человеческих сил. в первую очередь, они связаны с географическим месторасположением разных пунктов доставки и погрузки конкретного объекта.
I really like your blog.. very nice colors & theme.
Did you make this website yourself or did you hire someone to
do it for you? Plz reply as I’m looking to design my own blog and would like to find out where u got this from.
thanks a lot
Беспроигрышные стратегии и подходы к игре и шансы на победу зарегистрироваться дедди получите невероятные эмоции.
Советы по управлению банкроллом для игры в онлайн дедди казино сайт Исследуйте путь от новичка до профессионала в мире азарта.
Промислова група «КМТ» з’явилася на ринку на початку 1990-х віктор пономарчук vioil створили кілька вінницьких підприємців.
Це дозволило ViOil майже в три рази збільшити потужності віктор пономарчук vioil концентрація виробництва дозволяє знизити собівартість продукції.
how to buy cialis soft tabs pill
https://uec.asia/
Our company specializes in providing re-engineering services for parts and spare parts, filtration systems, water purification systems, gaskets, seals, and equipment for various industries including oil and gas, chemical, and energy. We are committed to delivering top-quality solutions that combine our expertise and technical efficiency to meet the unique needs of our clients.
букмекерская контора https://blackhorseoffroad.com/i-31627009-p-led-4-cube-lights-clear-pl1213.html?ref=search:https%3A%2F%2Fwww.instapaper.com%2Fp%2F13117135 по сути есть надежное, лицензированное заведение, которое гарантирует шанс моментально пополнить депозит и стремительно вывести выигрыши на ваши реквизиты.
Meds information for patients. What side effects can this medication cause?
buy generic levitra
Some about pills. Read information now.
Замечательно! Спасибо!
стоимость зависит https://art-lazer.com.ua/lazernaya-epilyaciya от трудоемкости. При консультации с косметологом необходимо рассказать максимум сведений о личном здоровьечко, тогда манипуляция пройдет эффективно.
They ensure global standards in every pill. http://drugsotc.pro/# canadian pharmacy world reviews
Medication information. Short-Term Effects.
lopressor
Everything trends of drugs. Read now.
buy cordarone no prescription
Поживем.
в процессе почти всегда используются только молодые почки и верхние https://www.adpark.lt/lipduku-gamyba/attachment/dsc_1066-copy/ листики.
buy cleocin generic
https://uec.asia/
We provide re-engineering services for parts, spare parts, filtration systems, water purification systems, gaskets, seals, and equipment used in the oil and gas, chemical, and energy sectors. Our approach to working with clients is always a blend of our expertise and technical proficiency.
Medicament information leaflet. Brand names.
viagra
Everything about drug. Get information now.
ViOil входит в тройку крупнейших производителей подсолнечного масла віктор пономарчук vioil и является лидером по выпуску рапсового масла.
МолодчаГа парень!!!!!!!!
на данный вопрос каждый должен дать себе отчет в том самостоятельно, https://pekar-konditer.ru/pub/pgs/kupit_diplom_povara_11.html ведь однозначно дать ответы на него невозможно.
ViOil – один из самых мощных производителей растительных масел віктор пономарчук vioil имеет 30 лет опыта работы на масложировом рынке.
miya4d
miya4d
Medicine prescribing information. Brand names.
buy synthroid
Best information about medicament. Get information now.
Не могу сейчас принять участие в дискуссии – очень занят. Буду свободен – обязательно напишу что я думаю.
reflect about, what amenities you needed at the http://vulteevaliant.com/index.php/User:BrigetteBelmore. However, keep in mind that this more general trends than strict rules.
I like it when people come together and share views.
Great site, stick with it!
Drugs information sheet. What side effects can this medication cause?
generic valtrex
Some about medicament. Get information now.
gabapentin withdrawal symptoms
Смотри у меня!
The headphones have a recognition function on the head and enable him to easily switch between devices of http://www.xn--hg3b50g00b6u5a.com/bbs/board.php?bo_table=free&wr_id=738084.
side effect of prednisone
finasteride reddit
Nice one well done keeeep it upppzzzz
Medication information for patients. Drug Class.
buying proscar
Best news about medicine. Get information now.
Кредитные карты с периодом 120 дней без процентов – это специальные предложения https://120-dnei-bez-procentov.ru/ которые позволяют владельцам кредитных карт пользоваться кредитными средствами без уплаты процентов.
Как выбрать и установить тепловой насос NIBE https://informnapalm.org/blog/kak-vybrat-i-ustanovit-teplovoi-nasos-nibe-prakticheskie-sovety-dlya-optimalnoi-raboty-sistemy/
buy generic doxycycline without dr prescription
Medicament prescribing information. Cautions.
cheap bactrim
Actual trends of medicines. Read now.
Use the 1xBet promo code for registration : VIP888, and you will receive 1xbet promo codes before registering, you should familiarize yourself with the rules of the promotion.
Вы допускаете ошибку. Могу отстоять свою позицию. Пишите мне в PM.
In the https://kakunje.com/casino-2023-film/ industry, there are unique health problems on production. In 1976, New Jersey allowed gambling in Atlantic City, now the second largest gambling city in the USA.
камеры видеонаблюдения ставят задавшись целью безопасности, и повышенной защиты комнаты. внутренние двери изготавливаются из нескольких разновидностей материалов, различных по экологичности, https://fruitcocktail.forum.cool/viewtopic.php?id=1870#p6217 составу и структуре.
Drug prescribing information. Short-Term Effects.
where to get retrovir
Best information about medication. Get here.
https://tsucompany.uz/
Компания Turan – ваш надежный партнер в области промышленного оборудования для энергетики, нефти и газа! Мы гарантируем высокое качество и надежность наших продуктов, сотрудничая только с проверенными мировыми производителями. Наш широкий ассортимент включает в себя трансформаторы, генераторы, компрессоры, насосы и многое другое – мы имеем решения для любых потребностей в энергетике, нефти и газе. А еще мы предоставляем высококачественное сервисное обслуживание, включающее установку, наладку и техническую поддержку. Наш международный опыт в поставках и обслуживании оборудования поможет вам успешно развивать свой бизнес – мы заботимся о внедрении новых инноваций и технологий, чтобы повысить производительность и снизить затраты вашего предприятия. Turan – ваш выбор для надежного и профессионального развития вашего бизнеса в области энергетики, нефти и газа. Доверьтесь нам, и вы гарантированно получите качественное и конкурентоспособное оборудование!
чем раньше тают килограммы, normula.ru тем быстрее они возвращаются. Овощной салат с куриной грудкой – пример полезного и сытного блюда.
doxycycline pharmacy price
чтобы ослабить связь возлюбленного и бетона пассии, необходимо, https://alexeygolev.ru/ чтобы в течение недели после обряда наши эксперты не виделись.
https://tsucompany.uz/
Компания Turan – ваш надежный партнер в области промышленного оборудования для энергетики, нефти и газа! Мы гарантируем качество и надежность нашей продукции, сотрудничая только с проверенными мировыми производителями. Наше оборудование способно справиться с самыми сложными задачами. Turan предлагает широкий ассортимент оборудования, включая трансформаторы, генераторы, компрессоры и насосы, чтобы удовлетворить все ваши потребности в энергетике, нефти и газе. Мы также предоставляем высококачественное сервисное обслуживание, помогая с установкой, наладкой и технической поддержкой. Благодаря нашему международному опыту и поставкам оборудования в разные страны, мы можем помочь вам решить любые задачи, связанные с вашим бизнесом. Мы всегда следим за новыми технологиями и инновациями в отрасли, чтобы предложить вам самые эффективные решения для увеличения производительности и снижения затрат. Выбирая Turan, вы выбираете надежного партнера, который поможет вам успешно развивать свой бизнес в области энергетики, нефти и газа. Мы гарантируем качество, надежность и профессионализм. Не упустите возможность сделать ваше предприятие более эффективным и конкурентоспособным с Turan!
Могу рекомендовать Вам посетить сайт, на котором есть много статей на интересующую Вас тему.
А аутентичность и качественность немецких матрасов не подведут вас на протяжении долгих лет. Немецкие http://sunofhollywood.com/prophecy/2011/04/20/russell-brand-kissed-two-girls-and-he-liked-them-both/ у нас в стране известны давным-давно.
есть и иные вариации казино, https://ruproplaypokerdom.ru/ получившие популярность за счет использования в автоматах для казино. в начале дилер раздает всем гостям и себе по 3 карты.
Drug information. Short-Term Effects.
order promethazine
Some about meds. Get now.
1xBet betting company continues to remain in the trend promo code for 1xbet registration despite the growing competition in the interactive.
Например, https://proplayredstarpoker.ru/ в конце зимы-марте провели oss cub3d на 25 процентов % процентов процентов %,000,000. Еженедельно на Редстаре проводят гонку на €12,500. особенно популярный рум мира просто не способна игнорировать mtt.
Hi! Quick question that’s entirely off topic.
Do you know how to make your site mobile friendly? My blog looks weird when viewing from my iphone.
I’m trying to find a theme or plugin that might be able
to fix this problem. If you have any suggestions, please share.
Cheers!
Their international insights have benefited me greatly. https://indianpharmacy.life/# Online medicine home delivery
Pills prescribing information. Cautions.
fosamax without prescription
Everything information about drugs. Read here.
The main task of such publications is to motivate 1xbet welcome bonus promo code users to register in the office as soon as possible.
Развлечение особенно актуалено у азиатской аудитории геймеров из китайской народной республики, pokerokrussiapro.ru Малайзии и Гонконга.
A private dance of this kind has long since become an חשפנית בנתניה indispensable feature of any good party.
cordarone side effects
Medicines information for patients. What side effects?
priligy
All trends of drug. Get now.
Kantorbola adalah situs slot gacor terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat slot dengan rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99
На префлопе любой из посетителей получает по pokerokrussia.ru 2|два} карты. две карты, идущие по рангу через 1 (jk, 7,девятке и пр..).
При выборе подходящей модели теплового насоса воздух-вода для дома https://msd.com.ua/teplovye-nasosy/sravnenie-razlichnyx-modelej-teplovyx-nasosov-vozdux-voda-kak-vybrat-podxodyashhij-dlya-vashego-doma/ необходимо учитывать ряд ключевых факторов.
педагогика и саморазвитие -> ФИЛОСОФЫ ПСИХОЛОГИИ: ЗНАМЕНИТЫЕ ИМЕНА -> Давид Гартли и Джозеф Пристли: человеческий дух и материя
buy generic prograf
все это время игрок будет получать на счет по $пяти долларам за playpokerok.ru каждые $50 рейка. для регистрации и начнете выполнение миссий, откройте страницу и зайдите в раздел “Мой бонус”.
После паса вас сразу пересаживают за новый стол, instantphotoworks.com где начинается раздача с иными соперниками.
Да, действительно. И я с этим столкнулся. Можем пообщаться на эту тему. Здесь или в PM.
отдельно нужно сказать ставки https://yvonne-elodie.de/index.php/component/k2/item/38-class-aptent-taciti на mortal combat. по этой причине за ходом события рекомендуется следить по роликам или матч-центру.
На официальном сайте интернет-магазина представлен широкий ассортимент алкогольной продукции доставка алкоголя недорого москва принимаем запросы вне зависимости времени.
nemasole tablets and australia assessment report
buy generic lisinopril online
если у лично вас еще нет страницы на 888poker, https://eurorscg-interactive.com/ зарегистрируйтесь согласно инструкции и скачайте игровой клиент.
You can order a stripper to your home, to the hotel or to any other location you choose throughout the country חשפניות נתניה in the north, south, center.
doxycycline generic brand
Medication prescribing information. Drug Class.
bactrim without insurance
Some what you want to know about medicine. Get here.
The beauty and grace of the female body have been appreciated since ancient times חשפנית בראשון לציון smooth dance movements.
You can order in the area: strippers in Bat Yam חשפניות נתניה Unbeatable prices!
buy lisinopril
cheap co-amoxiclav without dr prescription
???? ????? ???? ???? ?? ???????? ??????????? ???? ?? ????, ?? ???? ??? ?????? ?? ??? ???? ?????? ?????? ????? ? ?????? , ??????? ????? ? world wide web ????? ????? ??? ???? ???? ??????? ?????? ????? ?????.
Drugs information for patients. Drug Class.
get priligy
Best news about medicines. Get information here.
????? ??????? ?? – ?? ????? ??????? ???? ??? ??????? ??? ????? ???? ?????, ?? ????? ?????, ?? ???? ???? ?????? ????? !
stromectol at home
kantorbola77
Kantorbola adalah situs slot gacor terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat slot dengan rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99
buy lisinopril without a perscription
???? ????? ???? ??? ???? ??? ????, ?????? ????? ?????? ? ???/ ???? ???????. ?? ??? ???? ????? ??????, ??????? ???? ?????.
diltiazem cd
Medicine information sheet. Drug Class.
minocycline
All trends of pills. Read information here.
????? ??, ???? ?????? ?????? ?????? ???????? ??? ?????, ????? ????? ??? ??? ????? ??????? ?????? ? ???? ??????, ??????? ?????. ?? ??? ???? ???? ?????? ??????? ????????.
Психология
buy cheap lisinopril
con todo esto usted ya tiene la mayor parte de la informacion necesaria que usted tenga la oportunidad de evaluar si sera https://proplayggpokerag.com/ la habitacion que te gusta descargar, para probar jugar en el molinillo.
Бесподобный топик, мне интересно ))))
On our website you can book Rishon Lezion strippers for a bachelor party חשפנית בראשון לציון and in all places in the country.
We offer a warm, interesting and very spicy service in Rishon LeZion: חשפניות ראשון לציון booking strippers Inviting our artists girls will paint every party in new color.
Pills information for patients. Short-Term Effects.
strattera otc
Actual what you want to know about medicament. Get here.
for those, who can’t/wants|wants} to wait “places for games in texas hold’em, Omaha https://wtpglobalau.com/ or Omaha Hi-Lo, they get a chance register for “Fast sites, those will notify you as soon as at consumer space will be available.
https://dez-serv.ru/
Create an account account and deposit money. visa, MasterCard, American express, berhamdesigns.com and discover cards are available.
buy lisinopril 10 mg tablet
Delivering worldwide standards with every prescription. https://mexicanpharmacy.site/# purple pharmacy mexico price list
If you would like to obtain a great deal from this piece of
writing then you have to apply these techniques to your won weblog.
Научись читать
154. What organ does insects lack? Of course, you know, the http://paulikipedia.ru/index.php/Riddles_and_other_games that besides this are you going to do evenings with restless children?
https://dez-serv.ru/
The “highest payout” did not increase from 3,970,415 greenbacks at the 2005 World https://australiapokerwtpglobal.com/ Championship, and the main prize has consistently been less than 500 000$ since the 2016 World Championship.
Meds information. Generic Name.
paxil
Best about medicine. Get here.
Основным направлением работы отделения является восстановительно-реконструктивно-пластические операции в области головы – шеи http://neuro-med.ru/partners.htm
https://www.party.biz/forums/topic/714684/calgary-s-fine-line-tattoo-scene-a-rising-trend-in-body-art/view/post_id/1584300
buy lisinopril 20 mg without prescription
есль ветром сдует?
play at thousands of mini-games the only one clicking buttons https://yvavilebismovla.ge/user/tirgonzllp. ?? stay in the trend of fashion trends, fitness and principles of life.
Fine line geometric tattoos represent a profound departure https://moneyfx.boardhost.com/viewtopic.php?pid=17377#p17377 from the conventional and frequently audacious realm of tattoo aesthetics.
This resplendent style has surged into prominence on the back of its beguiling, almost ethereal https://myworldgo.com/forums/topic/105631/fine-line-tattoos-vs-traditional-tattoos-pros-and-cons/view/post_id/1161877#siteforum_post_1161877
Medication information for patients. Long-Term Effects.
nolvadex
Some news about medicine. Get information now.
Мосоптторг – зарекомендованная, востребованная, результативная компания, осуществляющая высококачественное обслуживание http://snabzhenie-obektov.ru/ для обеспечения материалами, применяемыми в строительстве.
годик на роздумие ))
moreover, Crypto gambling site will have a license, and anyone can easily find out about this, by going to the lower part of the start page of the resource – there should be a logo displayed.
buy generic lisinopril online no rx
An erotic dance is a dance that provides erotic entertainment and whose objective is the stimulation חשפניות ראשון לציון of erotic or sexual thoughts or actions in viewers.
This is a best luxury and sophistication Naya District 1 nestled in the heart of Dubai.
Great site! I recommend everyone to watch it!naya district onenaya district one Online-Television.net specializes in live streaming, allowing viewers to watch their favorite shows, sports events, news broadcasts, and more in real-time. Whether you’re a sports enthusiast eager to catch the big game or a news junkie staying up-to-date with current events, this platform provides a seamless and convenient way to access live broadcasts from around the world.
Medicine information sheet. Drug Class.
lisinopril medication
Everything information about drug. Get now.
active ingredient in zyrtec
Дождусь может лудшего качества
as the 14th week of the coronavirus pandemic approaches, which by real time has claimed the lives of more than 73,000 settling, and has spread over, than in 180 countries, https://slocally.com/lighting-of-bonfires-and-1st-may-wake-up-call/ much more, and more voluminous to a person turns out in quarantine, as governments all over the world are taking extreme measures to contain the spread of this highly infectious disease.
A seamless fusion of local care with international expertise. http://drugsotc.pro/# canada pharmacy
buy lisinopril in cartagena
cefixime side effects
Поздравляю, это просто великолепная мысль
?????? ? ???? ??????|??????} ?????? ?????? ????? ?????, ??????? ????? ?????? ?? ???????? ?? ???? ??????, https://mefankot.net/, ??? ?????? ? ?????/??, ?? ???? ?????? ? ??? ????.
Drugs information sheet. Long-Term Effects.
bactrim
Some information about drug. Read information here.
trazodone syrup
Hello friends if you are hosting a bachelor party in the north חשפניות בצפון and it is important to you that the party will go well.
A hot strip show for a bachelor party חשפניות בצפון what bachelor party before the wedding.
Уничтожение насекомых, дезинфекция, дератизация с гарантией в вашем городе Служба дезинфекции в Самаре: Уничтожение насекомых и грызунов
buy lisinopril 20 mg online canada
СПСБ
?? ????? ?? ?????? ??? ???, https://strip10.com/ ?? ?????? ?????. ?? ??? ???? ????? ??????, ??????? ???? ????.
Drug information leaflet. Long-Term Effects.
maxalt without a prescription
Best information about drug. Get now.
Да ни че прикольно!
но, до того как ты почувствуешь себя полноправным хозяином идеального мира, тебе придётся определенное время повыживать – а посему, пожить обычно, http://shkola.mitrofanovka.ru/index.php?subaction=userinfo&user=ivodazi диктуемым тебе обстоятельствами.
Основными направлениями экспорта ViOil являются страны СНГ віктор пономарчук vioil Ближнего Востока, Юго-Восточной Азии, Северной и Восточной Африки, Европы.
Wonderful blog! I found it while searching on Yahoo News.
Do you have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Many thanks
Have you ever considered publishing an ebook or guest authoring
on other websites? I have a blog based on the
same topics you discuss and would really like to have you share some stories/information. I know my readers would appreciate your work.
If you are even remotely interested, feel free to
shoot me an e mail.
Meds information for patients. What side effects can this medication cause?
zoloft
All news about drugs. Read now.
I love your blog.. very nice colors & theme. Did you create this website yourself or did you hire someone to do it for you?
Plz answer back as I’m looking to design my own blog and
would like to find out where u got this from.
thanks a lot
Присоединяюсь. Так бывает. Давайте обсудим этот вопрос. Здесь или в PM.
не кожному сподобаються кожному і баштанні культури-гарбуз, кабачок, yaktak.com.ua огірок і кавун.
pregnancy category fluoxetine hcl
Great beat ! I wish to apprentice at the same time as you amend your web site, how
can i subscribe for a blog website? The account aided me a acceptable deal.
I were a little bit acquainted of this your broadcast offered vibrant clear concept
buy cheap lisinopril 40 mg no prescription
tetracycline capsule
Last years results confirmed that the industrial group ViOil віктор пономарчук vioil remains the leader in rapeseed oil production.
According to a message on the companys website, the groups oil extraction plants processed віктор пономарчук about 76 thousand tons of rapeseed.
В этом что-то есть. Теперь мне стало всё ясно, благодарю за информацию.
Чи завдає шкоди наркоз організму або це черговий міф? існують чи ризики стоматология D.Ante і наслідки?
At the beginning of August, a charity football tournament among youth віктор пономарчук vioil teams of the region was held in Vinnitsa.
Medicine information. Short-Term Effects.
ampicillin online
Some information about medicine. Get now.
prednisolone sodium
They always offer alternatives and suggestions. http://indianpharmacy.life/# Online medicine order
buy lisinopril
methylprednisolone
where to get cheap sildalist without prescription
Drugs information for patients. What side effects?
ampicillin for sale
Actual information about medicament. Get information now.
can i order generic tinidazole price
lisinopril 20 mg buy cash
canadian compounding pharmacy: cheap canadian pharmacy – canadian pharmacy king
Tattoos, those inked tapestries of human expression, have traversed the epochs, http://forums.delphiforums.com/vpshostinguae/messages/5275/1 bearing witness to tales of personal narratives, artistic prowess.
Смоленск в сети
Pills prescribing information. Generic Name.
xenical price
All what you want to know about medicines. Read here.
The Transformation of Fine Line Tattoos in Calgary: http://www.razyboard.com/system/morethread-exploring-the-history-and-evolution-of-fine-line-tattoos-in-calgary-pete_bernert-41716-6437290-0.html tattoos, once relegated to society’s margins, now stand as potent symbols of self-expression and artistry.
The Cultural Resonance of Fine Line Tattoos: https://rdd.media/fine-line-flower-tattoo-exquisite-floral-artistry-by-masterful-tattoo-artists/ beyond their aesthetic splendor, fine line tattoos in Calgary
Зачот…класно…
supra is displayed in categories of supported cars and barely you click on it, in the bmw parts catalog on our website will appear a number options of the engine to choose from .
Blackpanther 77
кое-какие компании предлагают бездепозитный премию за казино спарк регистрацию с выводом. с такими нюансами можно заблаговременно ознакомиться при условии поощрений.
Простыми словами о том, что нужно знать прежде, чем заказать дизайн упаковки разработать дизайн упаковки
However, the bright celebration did not end with the last minutes of the final match віктор пономарчук and the awarding of the young athletes.
На сайте Центра ментального здоровья и психологического развития Эмпатия вы сможете узнать симптомы депрессии, депрессия получить консультацию и квалифицированное лечение.
buy lisinopril
Поиск авиабилетов для путешествий в любую точку мира на агрегаторе Скайсканер сайт
cefixime for children
Meds information sheet. What side effects?
levitra
All trends of drugs. Read now.
Я считаю, что Вы не правы. Я уверен. Давайте обсудим. Пишите мне в PM.
Заделка потолочных трещин, рустов, http://karabash.chelbusiness.ru/index.php?name=account&op=info&uname=ibafyl штроб (глубина/ширина до 30 мм) пог.м. Штробление борозд для прокладки трубопровода до 60мм пог.м.
Great site! I recommend everyone to watch it!Bargain For You mirror shop
Ми, виробництво Віанд, використовуємо високоміцну тканину, яка не розтягується Москітна сітка для розкладачки там. і має першокласні характеристики міцності.
Ура! и спасибо!)))
Массив сосны, бука, березы, палисандра, гевеи, шпон любых видов деревьев – натуральные качественные экологичные материалы, http://www.belgianbeers.ru/2014/03/tripel-karmeliet-84.html ценность которых повышается проверенные временем банки, альфа банк предоставляет условия год.
buy lisinopril walmart
Female nudity is not just spectacular stripping חשפנית בצפון it is the fire of emotions, the release of the soul, the art of dance.
Вы ошибаетесь. Предлагаю это обсудить. Пишите мне в PM.
We are glad that gambler preferred a personalized eximaps demo for https://dearbeauty.ca/from-better-sleep-to-less-anxiety-six-practices/! We are here, to provide assistance.
When ordering strippers from our company, it is guaranteed that you will receive not only חשפניות בצפון the most beautiful girls in Israel, but also the most professional service.
Жирные кислоты соапстоков светлых растительных масел и саломасов для кормовых віктор пономарчук vioil основными направлениями экспорта ViOil являются страны СНГ, Ближнего Востока.
здорово
Это укрепит ваши шансы и однозначно даст возможность обойти конкурентов. Постройте отличную карьеру, приняв здоровое решение – купить диплом об окончании колледжа.
Вас посетила замечательная мысль
Jay contacted the professor and offered to share all the scanned issues that he had, so that students and researchers of the http://dycp.kr/bbs/board.php?bo_table=free&wr_id=71543” could|managed to use them.
Medicament prescribing information. Short-Term Effects.
norvasc
All information about drug. Get information now.
今彩539開獎號碼查詢
今彩539開獎號碼查詢
大樂透開獎號碼查詢
大樂透開獎號碼查詢
威力彩開獎號碼查詢
威力彩開獎號碼查詢
на сутки квартиры
Между нами говоря, я бы попытался сам решить эту проблему.
Красива посмішка і здорові зуби – бути впевненими в особистої привабливості і злагоджена http://waldemar.mozola.pl/?p=412 робота всього організму.
Great site! I recommend everyone to watch it!Bargain For You mirror shop
buy lisinopril india
Coagulation
Medicine information. What side effects can this medication cause?
tadacip
Actual about medication. Read now.
Great article. I will be dealing with many of these issues as well..
My family members every time say that I am killing my time
here at web, except I know I am getting know-how every day by reading thes pleasant posts.
pregabalin vs gabapentin
where to buy lisinopril online
Готовый рейтинг платформ поможет быстрее выяснить, какой оператор в рунете выполняет требования регулятора, https://russiacasinos.win/best предоставляя доступ к азартным развлечениям.
pharmacies in canada: online pharmacies no prescription usa – buying prescription drugs from canada online
Lucky Jet, un popular juego de choque, llama la atencion no solo por sus https://lucky-jet-colombia.co sencillas reglas, sino tambien por su impresionante diseno visual.
diltiazem cream
Прогон сайта с использованием программы “Хрумер” – это способ автоматизированного продвижения ресурса в поисковых системах. Этот софт позволяет оптимизировать сайт с точки зрения SEO, повышая его видимость и рейтинг в выдаче поисковых систем.
Хрумер способен выполнять множество задач, таких как автоматическое размещение комментариев, создание форумных постов, а также генерацию большого количества обратных ссылок. Эти методы могут привести к быстрому увеличению посещаемости сайта, однако их надо использовать осторожно, так как неправильное применение может привести к санкциям со стороны поисковых систем.
Прогон сайта “Хрумером” требует навыков и знаний в области SEO. Важно помнить, что качество контента и органичность ссылок играют важную роль в ранжировании. Применение Хрумера должно быть частью комплексной стратегии продвижения, а не единственным методом.
Важно также следить за изменениями в алгоритмах поисковых систем, чтобы адаптировать свою стратегию к новым требованиям. В итоге, прогон сайта “Хрумером” может быть полезным инструментом для SEO, но его использование должно быть осмотрительным и в соответствии с лучшими практиками.
Medicament information. Long-Term Effects.
buy generic norvasc
All trends of drugs. Get here.
Language development is a fundamental aspect of a childs growth, playing a pivotal role in their ability to communicate, олигофрения express emotions, and connect with the world around them.
Какая замечательная фраза
Подивіться наявність квитків Мукачево-Лисичанськ. корисні рекомендації, лайфхаки, хитрощі-все саме цікаве про подорож Укрзалізницею, https://www.aliaverba.it/la-lacrima-del-sultano/ що вам потрібно/ потрібно знати.
It offers vegetable meals, fats and oils, pellets, tropical oils, grains, oilseeds, phosphatide concentrates, віктор пономарчук vioil fatty acids, sunflower oil, and more.
недорогие квартиры на сутки
can i buy generic lisinopril online
The group was the first in the country to produce rapeseed oil віктор пономарчук the company exported almost all its products.
Medication information for patients. What side effects can this medication cause?
norvasc online
Actual about drugs. Read here.
1xbet промокод при регистрации
三星彩開獎號碼查詢
Hello there, I found your web site by way of Google even as looking for a
comparable subject, your site came up, it appears to be like great.
I have bookmarked it in my google bookmarks.
Hi there, simply became aware of your weblog thru Google, and located that it
is truly informative. I am going to be careful for brussels.
I’ll appreciate for those who continue this in future. A lot of people shall be benefited out of your writing.
Cheers!
buy lisinopril uk
how can i get cheap elimite without a prescription
運彩分析
Я считаю, что Вы не правы. Я уверен. Могу отстоять свою позицию. Пишите мне в PM, обсудим.
В каталогах автозапчастей на нашем сайте сетевого магазина ИНТЕРМАРС вы получите возможность прочесть кузовные запчасти (крылья, бамперы, капоты), детали подвески, оптику, автостекла, комплектующие для ТО (тормозные колодки, свечи, лампы, фильтры), оригинальные масла, https://www.tvnoticias.com.co/ediles-no-representan-a-lideres-comunales/ аккумуляторы (в т.ч.
квартира Минск
The global marketing company Infinity Business Insights ViOil presented an overview and forecast віктор пономарчук vioil of the development of the sunflower meal market for 2022?2028.
美棒分析
промокод для 1xbet при регистрации
Капец! все мы этим пользуемся
each of movies offers immense selection slot machines, keno https://yellowpagoda.com/atithi-devo-vawa/ and table games.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Oh my goodness! Amazing article dude! Many thanks,
However I am experiencing troubles with your RSS. I don’t know the reason why
I am unable to subscribe to it. Is there anybody getting
the same RSS issues? Anyone that knows the solution will you kindly respond?
Thanks!!
2024總統大選
Great site! I recommend everyone to watch it!anyswap
1xbet промокод бесплатно
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
промокод 1xbet 2024
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Как начать играть в онлайн казино, секреты, советы, рейтинг Рейтинг казино Как не проиграть все? Как выиграть? Брать бонус на депозит?
очаровательно!
Процедура выполняется профессионалами с медицинским образованием. Нельзя выдергивать волос пинцетом, https://funsilo.date/wiki/User:RooseveltMack65 использовать крем для депиляции и действующие иначе методы избавления от волос.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
A no deposit bonus at F1 Casino can be cashed out if you wager pelican casino the bonus (x50) within 3 days.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Medication information for patients. Cautions.
tadacip no prescription
All about pills. Get information here.
1xBet – это благоприятные условия при регистрации и выборе ставок промокод на регистрацию 1xbet ринимая участие во всех выгодных предложениях, новички и постоянные игроки получают прекрасную возможность увеличить свой бонусный счёт.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Служба дезинфекции – уничтожение насекомых и грызунов в вашем городе c гарантией Обработка от клопов уничтожение насекомых, дезинфекция, дератизация с гарантией.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
промокод 1xbet при регистрации
Вызов врачей и узких специалистов на дом клиника оказывает широкий спектр услуг социофобия Уколы и капельницы.
Great site! I recommend everyone to watch it!anyswap exchange
Могу предложить зайти на сайт, с огромным количеством статей по интересующей Вас теме.
log in to the filtering system of http://202.144.225.39/kiichigo5/entry/3481/. WARNING: such material may expose you are exposed to bisphenol A, which is known in the state of California, causes birth defects or other reproductive function disorders.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Drugs information sheet. Brand names.
prednisone order
Actual about meds. Get information here.
Это не совсем то, что мне нужно. Есть другие варианты?
Full check quite can solve common breakdowns before they modify into promising headache and leave you indifferent to Furnace Inspection service.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Четко должно быть!
??? ???? ????, https://alfa-strippers.space/ ?? ???/??. ???? ??? ????. ???? ??? ???? ? ????? ????? ?????, ??? ?? ???? ?? ??? ????? ?? ??? ?? ??.
Hi this is kind of of off topic but I was wondering if
blogs use WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding expertise
so I wanted to get advice from someone with experience. Any help would be greatly appreciated!
Hey there! Would you mind if I share your blog with my twitter group?
There’s a lot of folks that I think would really appreciate your content.
Please let me know. Thank you
Hmm is anyone else encountering problems with the
pictures on this blog loading? I’m trying to determine if its a problem on my end or if it’s the blog.
Any feedback would be greatly appreciated.
smtogel login
539開獎
bata4d
bata4d
В этом что-то есть. Большое спасибо за информацию, теперь я буду знать.
??? ??? ??? ??? ???? ????? ? ??? ???? ??????, https://a-strippers.space/. ?????? ???? ???? ??? ??? ?? ???? ??????? ?????? ??? ?????? ? ????.
Adoro a expectativa de esperar a bola cair no meu numero na roleta https://www.roletacasino.online/ a Roleta e um jogo facil de aprender, mas dificil de dominar.
hot girls webcam
Очень полезный вопрос
??? ?????? ?? ???????? ?????|??????????? ?????? ????? ??? ???? ??????? ???? ?? ???? https://atlantida-show.com/.
Best complex in Northern Cyprus Grand Sapphire Resort.
https://pedagog-razvitie.ru/course.html
недорогие квартиры на сутки
В этом что-то есть и идея хорошая, согласен с Вами.
??? ?? https://erdance.club, ?????? ????, ????? ?????, ??????? ??? ???? ??????, ??????? ???????? ?????? ?????.
В школе Центра иностранных языков YES вы сможете с легкостью курсы по английскому языку и интересом освоить английский язык.
Какие слова… супер, замечательная идея
что предпринять после того, как мебель уже расставлена, но, кажется, kovry-kupit-11.ru чего-то мало? у вас возникает шанс заказать ковер на пол через интернет магазин по крайне приемлемой цене!
The Bible is a remarkable journey through time, culture, and faith – Bible History for Kids: Temple Cleaning a narrative that spans from the creation of the world to the visions of the future.
Я думаю, что Вы ошибаетесь. Пишите мне в PM, обсудим.
??? ????? ?????? ???? ? https://erotic-show.com/– ?????? ???? ?????? ???? ? ??? ???, ??? ?? ?? ???? ??????. ???? ?? ???? ?? ???????? ???? ????? ?????..
Прекрасный отель grand sapphire blu северный кипр.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Вы не правы. Предлагаю это обсудить. Пишите мне в PM, поговорим.
??? ???? ??????? ????? ?????? ?? ??????? ???????? ?????. 250 eur ? h. ???? ?????? ??????|https://imbility.com/. ?? ????? ?????? ??? ??? ?? ???? ? ??? ??????? ?? ????? ?? ?????.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
rtpkantorbola
Kantorbola adalah situs slot gacor terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat slot dengan rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99 .
buy lisinopril walmart
buy cheap lisinopril 40 mg
По моему мнению Вы допускаете ошибку. Могу это доказать.
??? ??? ???? ?????? ?? ???? ????? ?????????? ??????? ? ????? ?????? ?????? ?????? ?? ?????? ??????? ??????? ????-????? ????????, https://rkstrippers.com. ????? ??????.
Meds information leaflet. Cautions.
buy generic zovirax
Everything information about meds. Read here.
Great site! I recommend everyone to watch it!anyswap cross-bridge
buy lisinopril hctz 20 12 5 mg
https://bankslist.ru/
blangkon slot
Blangkon slot adalah situs slot gacor dan judi slot online gacor hari ini mudah menang. Blangkonslot menyediakan semua permainan slot gacor dan judi online terbaik seperti, slot online gacor, live casino, judi bola/sportbook, poker online, togel online, sabung ayam dll. Hanya dengan 1 user id kamu sudah bisa bermain semua permainan yang sudah di sediakan situs terbaik BLANGKON SLOT. Selain itu, kamu juga tidak usah ragu lagi untuk bergabung dengan kami situs judi online terbesar dan terpercaya yang akan membayar berapapun kemenangan kamu.
Наши преподаватели, среди которых есть и носители языка, всегда готовы помочь Вам приобрести необходимые знания, подготовка к огэ по английскому чтобы в дальнейшем их можно было уверенно использовать в повседневной жизни.
Inside the ever-evolving world of on the web sports betting and gaming https://padlet.com/mostbetonline02/my-artistic-padlet-1s5if5bay7uxkmdf stands out being a top-tier platform that caters to your diverse preferences.
medication from mexico pharmacy or mexico pharmacy price list – buying prescription drugs in mexico online
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
rikvip
https://sen-tan.com/ Сенімді Та?дау компаниясы, ?аза?станны? энергетикалы? секторында т?тынушыларды озы? инженерлік шешімдерді ?олдану ар?ылы к?мек к?рсету мен жеткізу ма?сатында компания беделінен ие болды.
Всем очень рекомендую Lev casino.
Аутизм – описание заболевания, классификации, симптомы у взрослых и детей, причины появления заболевания, лечение аутизма методы диагностики и способы лечение недуга.
снять квартиру
It’s difficult to find experienced people for this subject, but you
seem like you know what you’re talking about! Thanks
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Zip пакеты
Профессиональный ремонт телефонов в г Жуковский с гарантией раменское ремонт телефонов Вы все еще думаете, что ремонт компьютерной техники стоит дорого?
winstarbet
winstarbet
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Here you can find almost any sport for betting https://1x-bet.fun You can find good odds here.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Получите консультацию с нашим юристом и узнайте ответы на свои вопросы юрист по земельному праву юридические услуги — важная квалифицированная профессиональная помощь.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Отличный сайт, где Вы можете заказатьУплотнительное кольцо VAG Всем рекомеендую!
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
http://stromectol24.pro/# ivermectin buy nz
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
https://tamozhennoe-oformlenie.info
https://sb-cargo.com
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Because the admin of this web site is working, no question very rapidly it will be renowned,
due to its quality contents.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
невролог остеопат
фонофорез с гидрокортизоном цена
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Добро пожаловать в нашем сайте, вашего надежного партнера в мире спортивные прогнозы бесплатно. Мы с гордостью предоставляем вам возможность взять на себя контроль над вашими ставками и повысить свои шансы на выигрыш. Наши профессиональные аналитики и специалисты следят за событиями в мире спорта, чтобы обеспечить вас актуальными и надежными советами.
Почему выбирать нас:
Экспертные прогнозы: Наши аналитики усердно трудятся, чтобы предоставлять вам предсказания на разнообразные виды спорта. Мы знаем, насколько важно получать качественные советы перед тем, как сделать ставку.
Множество вариантов: Мы предлагаем ставки на разнообразные виды спорта, включая соккер, баскет, ракетку, бейсбол и многое другое. Вы можете отбирать из множества событий и наслаждаться азарт на свой вкус.
Советы без оплаты: Мы верим, что каждый может получить доступ к качественным прогнозам. Поэтому мы предлагаем бесплатные советы, чтобы помочь вам сделать правильные ставки.
Простота и удобство: Наш сайт и мобильное приложение разработаны с учетом вашего удовольствия. Сделайте ставку всего в несколько кликов.
Как начать:
Зарегистрируйтесь: Создайте персональный профиль в texttospeech.ru и получите доступ к всем нашим сервисам.
Получайте прогнозы: Подписывайтесь на наши бесплатные прогнозы и получайте актуальные предсказания от наших экспертов.
Поставьте свою ставку: После того как вы получили свой прогноз, сделайте ставку на вашу любимую команду или событие и получайте удовольствие от игры.
Вознаграждение за успех: Вместе с texttospeech.ru, вы владеете ключами к вашей победе. Попробуйте наши услуги уже сегодня и погружайтесь в мир спортивных ставок во всей его красе!
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
http://indiapharmacy24.pro/# online pharmacy india
asapmarkets.org
asap onion link
onion darknet asap
The darknet market is a hidden part of the internet where illegal activities such as drug trade, weapons sales, and hacking services take place. In this article, we will explore the darknet market and answer some common questions surrounding this secretive online world.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
supermoney88
supermoney88
Tentang SUPERMONEY88: Situs Game Online Deposit Pulsa Terbaik 2020 di Indonesia
Di era digital seperti sekarang, perjudian online telah menjadi pilihan hiburan yang populer. Terutama di Indonesia, SUPERMONEY88 telah menjadi pelopor dalam dunia game online. Dengan fokus pada deposit pulsa dan berbagai jenis permainan judi, kami telah menjadi situs game online terbaik tahun 2020 di Indonesia.
Agen Game Online Terlengkap:
Kami bangga menjadi tujuan utama Anda untuk segala bentuk taruhan mesin game online. Di SUPERMONEY88, Anda dapat menemukan beragam permainan, termasuk game bola Sportsbook, live casino online, poker online, dan banyak jenis taruhan lainnya yang wajib Anda coba. Hanya dengan mendaftar 1 ID, Anda dapat memainkan seluruh permainan judi yang tersedia. Kami adalah situs slot online terbaik yang menawarkan pilihan permainan terlengkap.
Lisensi Resmi dan Keamanan Terbaik:
Keamanan adalah prioritas utama kami. SUPERMONEY88 adalah agen game online berlisensi resmi dari PAGCOR (Philippine Amusement Gaming Corporation). Lisensi ini menunjukkan komitmen kami untuk menyediakan lingkungan perjudian yang aman dan adil. Kami didukung oleh server hosting berkualitas tinggi yang memastikan akses cepat dan keamanan sistem dengan metode enkripsi terkini di dunia.
Deposit Pulsa dengan Potongan Terendah:
Kami memahami betapa pentingnya kenyamanan dalam melakukan deposit. Itulah mengapa kami memungkinkan Anda untuk melakukan deposit pulsa dengan potongan terendah dibandingkan dengan situs game online lainnya. Kami menerima deposit pulsa dari XL dan Telkomsel, serta melalui E-Wallet seperti OVO, Gopay, Dana, atau melalui minimarket seperti Indomaret dan Alfamart. Kemudahan ini menjadikan SUPERMONEY88 sebagai salah satu situs GAME ONLINE PULSA terbesar di Indonesia.
Agen Game Online SBOBET Terpercaya:
Kami dikenal sebagai agen game online SBOBET terpercaya yang selalu membayar kemenangan para member. SBOBET adalah perusahaan taruhan olahraga terkemuka dengan beragam pilihan olahraga seperti sepak bola, basket, tenis, hoki, dan banyak lainnya. SUPERMONEY88 adalah jawaban terbaik jika Anda mencari agen SBOBET yang dapat dipercayai. Selain SBOBET, kami juga menyediakan CMD365, Song88, UBOBET, dan lainnya. Ini menjadikan kami sebagai bandar agen game online bola terbaik sepanjang masa.
Game Casino Langsung (Live Casino) Online:
Jika Anda suka pengalaman bermain di kasino fisik, kami punya solusi. SUPERMONEY88 menyediakan jenis permainan judi live casino online. Anda dapat menikmati game seperti baccarat, dragon tiger, blackjack, sic bo, dan lainnya secara langsung. Semua permainan disiarkan secara LIVE, sehingga Anda dapat merasakan atmosfer kasino dari kenyamanan rumah Anda.
Game Poker Online Terlengkap:
Poker adalah permainan strategi yang menantang, dan kami menyediakan berbagai jenis permainan poker online. SUPERMONEY88 adalah bandar game poker online terlengkap di Indonesia. Mulai dari Texas Hold’em, BlackJack, Domino QQ, BandarQ, hingga AduQ, semua permainan poker favorit tersedia di sini.
Promo Menarik dan Layanan Pelanggan Terbaik:
Kami juga menawarkan banyak promo menarik yang bisa Anda nikmati saat bermain, termasuk promo parlay, bonus deposit harian, cashback, dan rollingan mingguan. Tim Customer Service kami yang profesional dan siap membantu Anda 24/7 melalui Live Chat, WhatsApp, Facebook, dan media sosial lainnya.
Jadi, jangan ragu lagi! Bergabunglah dengan SUPERMONEY88 sekarang dan nikmati pengalaman perjudian online terbaik di Indonesia.
покердом сайт официальный
покердом сайт
покердом официальный
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
pro88
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Do you mind if I quote a few of your posts as long as
I provide credit and sources back to your webpage?
My website is in the exact same area of interest as yours and my visitors would genuinely benefit from a lot of the information you present here.
Please let me know if this okay with you. Regards!
https://canadapharmacy24.pro/# canadian online drugstore
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
покердом войти
покер дом зеркало рабочее на сегодня
I needed to update my candidate information. The procedure was so fast and easy with Insurance Navy.
They truly value their consumers’ time.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
slot supermoney88
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
покердом вход
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
slot supermoney88
http://canadapharmacy24.pro/# canadian pharmacy store
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
I got this web page from my buddy who informed me concerning this web page and now this time I am visiting
this site and reading very informative articles at this place.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
buy osrs gold
RuneScape, a beloved online gaming world for many, offers a myriad of opportunities for players to amass wealth and power within the game. While earning RuneScape Gold (RS3 or OSRS GP) through gameplay is undoubtedly a rewarding experience, some players seek a more convenient and streamlined path to enhancing their RuneScape journey. In this article, we explore the advantages of purchasing OSRS Gold and how it can elevate your RuneScape adventure to new heights.
A Shortcut to Success:
a. Boosting Character Power:
In the world of RuneScape, character strength is significantly influenced by the equipment they wield and their skill levels. Acquiring top-tier gear and leveling up skills often requires time and effort. Purchasing OSRS Gold allows players to expedite this process and empower their characters with the best equipment available.
b. Tackling Formidable Foes:
RuneScape is replete with challenging monsters and bosses. With the advantage of enhanced gear and skills, players can confidently confront these formidable adversaries, secure victories, and reap the rewards that follow. OSRS Gold can be the key to overcoming daunting challenges.
c. Questing with Ease:
Many RuneScape quests present complex puzzles and trials. By purchasing OSRS Gold, players can eliminate resource-gathering and level-grinding barriers, making quests smoother and more enjoyable. It’s all about focusing on the adventure, not the grind.
Expanding Possibilities:
d. Rare Items and Valuable Equipment:
The RuneScape world is rich with rare and coveted items. By acquiring OSRS Gold, players can gain access to these valuable assets. Rare armor, powerful weapons, and other coveted equipment can be yours, enhancing your character’s capabilities and opening up new gameplay experiences.
e. Participating in Limited-Time Events:
RuneScape often features limited-time in-game events with exclusive rewards. Having OSRS Gold at your disposal allows you to fully embrace these events, purchase unique items, and partake in memorable experiences that may not be available to others.
Conclusion:
Purchasing OSRS Gold undoubtedly offers RuneScape players a convenient shortcut to success. By empowering characters with superior gear and skills, players can take on any challenge the game throws their way. Furthermore, the ability to purchase rare items and participate in exclusive events enhances the overall gaming experience, providing new dimensions to explore within the RuneScape universe. While earning gold through gameplay remains a cherished aspect of RuneScape, buying OSRS Gold can make your journey even more enjoyable, rewarding, and satisfying. So, embark on your adventure, equip your character, and conquer RuneScape with the power of OSRS Gold.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка трубчатых радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
дом покер
играть в казино
amoxicillin dose calculator
казино зеркало
doxycycline monohydrate 100mg
Мы предлагаем множество парных браслетов, которые непременно вас заинтересуют парные украшения качественно, быстро, недорого.
prednisone medication
can you take 20 mg of zyrtec
After I initially commented I appear to have clicked the -Notify me when new comments are added-
checkbox and from now on each time a comment is added
I get 4 emails with the exact same comment. Is there a means you can remove me from that service?
Thanks!
where to buy levaquin without a prescription
казино с бонусами за регистрацию
where to buy a doxycycline
where can i buy prednisone 5mg over the counter
акумулаторен шлайф
покер
zoloft withdrawal
Подробнее об организации: Вяземский историко-краеведческий музей на сайте Смоленск в сети
вход в покердом
Как вы можете охарактеризовать метод обсуждения изучаемого материала?
На цену прежде всего влияет функционал, дизайн и количество создаваемых страниц создание сайта цена ростов отрисовка современного дизайна с учетом ваших пожеланий.
can you buy generic elimite without prescription
albuterol generic name
buy generic doxycycline online
buy prednisone dose pack
buy prednisone online no script
promo code for melbet today at registration
Protonix and gas
promo code melbet for freebet
Добро пожаловать в нашу клинику ортопедии, где мы предлагаем высококачественные услуги в области диагностики, лечения мануальная терапия и реабилитации заболеваний опорно-двигательной системы.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Для начала планирую просто проконсультировался и ищу хороших юристов https://smetdlysmet.ru/forum/viewtopic.php?f=24&t=32615 Уверен, что не разочаруетесь проделанной работой и вам точно тут смогут помочь.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
http://plavix.guru/# Cost of Plavix on Medicare
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
bocor88
Cost of Plavix without insurance: Plavix generic price – Cost of Plavix without insurance
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Meds information leaflet. What side effects?
cialis super active medication
Actual what you want to know about medicament. Get here.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Доедешь болезни рук диагноз конечной остановки, магнитофонных записей больница Так, взятый из лаборатории систем безопасности, глаза его горели.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Medicament information sheet. Generic Name.
bactrim
Everything news about medicines. Get information now.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Figma export Plugin
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Компания HONO-R специализируется на производстве различных типов радиаторов охлаждения, https://msk.hono-r.com/product/dizel-elektrostantsii-dgu/ которые применяются в спецтехнике и в промышленных установках.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Я извиняюсь, но, по-моему, Вы не правы. Я уверен. Предлагаю это обсудить. Пишите мне в PM, пообщаемся.
Here https://www.transporteterminales.com.co/index.php/services/item/17-china-billionaire-buys-car songs can hit the target, since they are honest, and authentic – everyone who ever someone lost, can study it.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
buy osrs gold
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Я думаю, что Вы не правы. Давайте обсудим это. Пишите мне в PM, пообщаемся.
тщательный подбор за состоянием механизма автомобиля актуален для безвредного вождения как автолюбителям, так и, естественно, замена масла акпп infiniti g25 водителям-профессионалам. наши эксперты помогут в покупке нужных вам деталей по обоснованным стоимости.
furosemide rxlist
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Замечательно, очень ценное сообщение
this speeds up game on guitar tabs for beginners, http://johnrizzi.net/?page_id=988 and staff will also be marked as “TABS”, so that they are not confused with standard designations.
больового синдрому і багатьох інвазій і обслуговування глистів, https://palosvorosmart.hu/?p=462 бліх і кліщів. Зоомагазин рудий кіт щасливий вітати замовників на сторінках свого інтернет магазину зоотоварів!
Институт психологии и астрологии обучает и выпускает грамотных, профессиональных специалистов https://astroinstitut.ru/uslugi/individualnyj-goroskop/ система обучения основана на фундаментальных астрологических принципах.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Согласно отчету Всемирного Банка doing business по 2018 года, http://www.casagony.com/gnuboard5/bbs/board.php?bo_table=free&wr_id=245010 Азербайджан входит в топ 20 ведущих точек нашей планеты по категории «начинающий бизнес».
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Возьму на свойстрах и риск)))
Для добавления музыки достаточно повторить вышеописанные действия, избрав в п.5 новые наименования (артисты, альбомы, плейлисты, http://www.lkforum.ru/member.php?u=155485 песни).
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
what is the generic of elimite
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Medicament prescribing information. What side effects?
zovirax
Actual about medicament. Get information now.
вам буде доступний посилку на наступний день, https://vefa.me/video-in-slider/ рідко-через двоє. Замовити зоотовари ви можете щодня на сайті, пройшовши звичну всі кроки для оформлення, або по телефону, в робочий час.
Точно в цель 🙂
наличный расчет на базе либо в офисе. Крупнейший региональный центр металлопроката на Урале – это город https://ironworld.com.ua/product/truba-profilnaya-15h15-mm-tolshh-2-mm-st-s235jr-l6m-proizv-ukraina/ Екатеринбург.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Хорошая подборка.Первая СУПЕР.Поддержую.
p) expansion to person 3. not so extensive as original soundtrack, songs https://newagilework.de/hello-world fes implies 17 completely new singles, which organically combine well with the unique soundtrack from the point of view of the musical style.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Я считаю, что Вы ошибаетесь. Могу это доказать. Пишите мне в PM, пообщаемся.
205 товаров http://ukroenergo.ukrbb.net/viewtopic.php?f=7&t=624&p=2781#p2781 от 990 руб/мес. 651 продуктов от 990 руб/мес. Дропшиппинг – это относительно новый вид бизнесу, в основе которого лежит принцип «прямых поставок».
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Medicines information leaflet. Drug Class.
lopressor pills
Best information about pills. Read here.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Drug information. Effects of Drug Abuse.
synthroid medication
Best about medicines. Get here.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Kampus Unggul
UHAMKA offers prospective/transfer/conversion students an easy access to get information and to enroll classes online.
Kampus Unggul
Kampus Unggul
UHAMKA offers prospective/transfer/conversion students an easy access to get information and to enroll classes online.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Отражают уровень интереса зрителей к вам http://sadbs.com.au/index.php/component/k2/item/1/1 и вашему контенту. не запрещается при этом ограничиваться своими площадками и отзывами о собственных продуктах.
Компания “ПОРАДОМ” активно работает в сфере строительства и ремонта с 2012 года https://poradom-remont.ru/dizajn-interera Мы предоставляем профессиональные услуги по ремонту и дизайну жилых и нежилых помещений.
Креативненько!
значит вещи не утрачивают товарный вид, http://avtosalontochka.ru/index.php?subaction=userinfo&user=uryve потому их реально продавать. Важно использовать инструменты seo (ключевые слова и фразы) или lsi (отдельные слова для настилки необходимых семантических связей).
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Весьма отличная идея и своевременно
Поэтому элементы амортизации, в числе которых срок полезного использования (СПИ), http://istinastroitelstva.xyz/index.php?subaction=userinfo&user=utuquzym подлежат регулярной проверке на соответствие условиям использования объекта ОС и, при нужде изменяются (п.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
It is expected that alternative for android will not will be able to stay out of the event zone. There is a dock in the iOS user interface where consumers can pin their extremely frequently used software for https://www.hightechmedia.ma/index.php/2015/01/05/this-is-video-post-type-a-collection-of-beautiful-examples/.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Thank you for every other great post. The place else may anybody get that type
of info in such an ideal way of writing? I have a presentation next week, and
I am on the look for such information.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
hoki1881 login
Игорный портал азартных игр Cat Casino функционирует с 2021 года играть cat casino онлайн За прошедший период работы зарекомендовал себя исключительно с положительных сторон.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
side effects of finasteride
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
По моему мнению Вы не правы. Пишите мне в PM, пообщаемся.
альтернативное распространенное заблуждение – это отождествление понятий darknet и https://uahotels.info/hotel/Libid-Plaza-Hmelnitsk/ deepweb. Неоднородность. У даркнета нет единого стандарта, которого следуют все сайты.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
предоставление доставки https://www.investeast.net/2018/11/23/chinas-healthcare-market-is-endlessly-attractive/ регистрацию компании. в текущем году страна заняла 16 место среди 190 стран, что свидетельствует о благоприятной бизнес-среде для инвесторов.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
По моему мнению Вы не правы. Давайте обсудим это. Пишите мне в PM.
Obwohl alle/viele Universitaten/Hochschulen momentan wollen/wollen, damit/damit der Kandidat eigene biografie schreiben lassen es wurde Codierung prasentiert|verfugbar}, normalerweise mussen Sie auch/auch notwendig geben/geben eine gedruckte Kopie zur Verfugung stellen.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Drugs information sheet. Generic Name.
zenegra cost
All what you want to know about meds. Get information here.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Отличный сайт!Обсессивно-компульсивное расстройство Всем рекомендую!
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Оформление сертификата ИСО 9001 с нами – это не только возможность подтвердить соответствие вашего бизнеса международным стандартам, но как получить сертификат ИСО 9001 и шанс оптимизировать внутренние процессы, повысить уровень управления и улучшить качество услуг.
Medication information sheet. Effects of Drug Abuse.
proscar
Everything news about drugs. Get information here.
I go to see daily some web sites and websites to read content, but this weblog provides quality based articles.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Really a lot of helpful facts.
Feel free to surf to my web page https://www.vander-horst.nl/wiki/Eng-films.site
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Жаль, что не смогу сейчас участвовать в обсуждении. Не владею нужной информацией. Но с удовольствием буду следить за этой темой.
To potential players and operators even more necessary stay aware of specific rules related to https://stake-casino.bet/ru/stake-bonuses in that respective states.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Kampus Unggul
UHAMKA offers prospective/transfer/conversion students an easy access to get information and to enroll classes online
side effects of cetirizine
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Are you tired of endless diets and exhausting workouts that don’t give you the results you want fastest way to lose belly fat Introducing our revolutionary belly fat loss pills that will help you achieve your desired body shape in no time.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Отличный сайт!обсессии Всем рекомендую!
Pills information sheet. Effects of Drug Abuse.
levitra
Actual what you want to know about drug. Read now.
https://levitra.eus/# Levitra 20 mg for sale
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Узнайте, как производится Установка и ремонт сантехники своими руками Электрические полотенцесушители подробные инсрукции по установке ванны, унитаза, смесителей.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Medicine prescribing information. Generic Name.
nolvadex medication
Best news about drugs. Read information here.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
U know How to get premium subscribers
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
can i purchase prednisone no prescription
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
http://viagra.eus/# generic sildenafil
Дождались
это важно, чтобы не посеять время, https://wpdailylive.com/best-website-templates-free/ отослав форму заявки, и получив от системы отказ в выполнении операции.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Simply desire to say your article is as astounding.
The clearness in your put up is simply spectacular and i could
suppose you’re knowledgeable in this subject. Fine together with your permission let me to clutch
your RSS feed to stay up to date with coming near near post.
Thanks a million and please keep up the rewarding work.
Great site, I recommend it to everyone!Telegram premium subscribers
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Drug information. Generic Name.
tadacip
Everything news about medicine. Get now.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Охотно принимаю. Тема интересна, приму участие в обсуждении. Я знаю, что вместе мы сможем прийти к правильному ответу.
для того чтобы сделать мобильное приложение музыкальным проигрывателем, который вы и впрямь можете использовать, http://blog.mistifiks.ru/2015/06/mikrotik_54.html есть функция воспроизведения. вы увидите, сколько треков осталось записать для автономного прослушивания на оранжевом индикаторе прогресса в низу экрана на иос или в выпадающем меню на андроид.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Официальный сайт Gama Casino – удобный веб-портал, который предоставляет возможность играть, сайт гама казино не беспокоясь о конфиденциальности личной информации и денежных средств на счету депозита.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Я думаю, что Вы допускаете ошибку. Пишите мне в PM, поговорим.
bis отмечает, что в 2022 году «группы, поддерживающие официальную политику России, Новости Европы неоднократно объявляли и осуществляли нападения на чешские организации и корпорации в отместку за поддержку Чехией Украины».
Medicine information for patients. Short-Term Effects.
seroquel sale
Everything what you want to know about medication. Read here.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Medication information sheet. What side effects can this medication cause?
prednisone tablet
Everything what you want to know about drugs. Get now.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
hoki1881
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
http://kamagra.icu/# buy Kamagra
Great site, I recommend it to everyone!Get premium telegram subscribers
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
why do doctors prescribe gabapentin
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
I am actually always amazed by exactly how you take care of to provide sensible insights supported
through solid research. Your blog site is actually a true asset to your readers.
Also visit my page – affordable car insurance dallas
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Medicine information for patients. Short-Term Effects.
cialis super active
All about pills. Read information here.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Закажите матрешку, посуду, шкатулку с вашей символикой, сюжетом или фото магазин отбор изделий ведут специалисты с художественным образованием и длительным стажем работы в сегменте подарочной продукции.
http://levitra.eus/# Levitra 20 mg for sale
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
doxycycline hyclate 100 mg treats what
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
I can not express how grateful I am to have actually happened upon this message.
It responded to numerous of the inquiries I had.
Stop by my webpage; Ron Spinabella
Pills information sheet. Long-Term Effects.
promethazine
Best what you want to know about meds. Get information here.
Unleash the thrill of gaming like never before at our cutting-edge online casino https://albert2016.ru/2023/08/prepodavatelskie-desanty-projdut-v-kirovskoj-oblasti-vazhnye-voprosy-obrazovanija-na-povestke-dnja/ Your path to riches and excitement begins with a single click on this extraordinary link!
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Inspect Figma designs
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Устройство пола – важный этап в строительстве. Стяжка пола способствует приобрести ровное основание для дальнейших работ.
Мастера осуществляют стоимость залить стяжку пола с оглядкой на всех норм и правил. Стяжка пола делается с применением современных материалов, которые обеспечивают надежное покрытие и стойкость.
Покрытие пола способствует подготовить идеальное основание для любых видов отделки. В Москве выравнивание пола выполняют квалифицированные мастера.
Great site, I recommend it to everyone!youtube view bot
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Medication prescribing information. What side effects?
tadacip buy
All what you want to know about medication. Get information now.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
sildenafil oral jelly 100mg kamagra super kamagra buy kamagra online usa
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Meds prescribing information. What side effects?
cost of glucophage
All information about medicine. Read here.
https://kamagra.icu/# buy kamagra online usa
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Не знаю.
мы предлагаем клиентам окунуться в мир невероятных ароматов парфюма, стильных запахов и чарующих шлейфов, parfum-kazan.ru который имеют возможность сопровождать вас на бизнес пути.
nettruyenmax
Experience the ultimate in online casino entertainment at your fingertips http://1000zip.rusff.me/viewtopic.php?id=10626#p24830 get ready for a journey to unimaginable wealth and exhilaration – just one click away through this enchanted link.
Значение и необходимость сертификации ИСО 9001 не поддаются сомнению получение сертификата ИСО 9001 Получить сертификат ИСО 9001 необходимо, чтобы документально подтвердить тот факт, что предприятия соответствует установленным в стандарте требованиям.
ashwagandha products
Great site, I recommend it to everyone!youtube sub bot
Drugs information. Effects of Drug Abuse.
lyrica
Some information about meds. Read information here.
Pills information. Long-Term Effects.
provigil rx
Some trends of pills. Get information here.
Произошла ошибка
clinique aromatics elixir – шипровый цветочный унисекс-аромат с гармонией альдегидов, бергамота, сандала, http://www.rvfishingsites.com/places/united-states/texas/mason/rv-fishing-sites/84/ мускуса и ладана вдохновляет и увеличивает настроение.
Generic Viagra for sale Cheap generic Viagra online best price for viagra 100mg
Я конечно, прошу прощения, мне тоже хотелось бы высказать своё мнение.
any man has these two keys, the http://autostory.lv/user/ropherdapw, which they use to produce a secure digital identification link. like all forms technologies blockchain has row advantages and disadvantages that need take into account.
Drug information leaflet. Brand names.
viagra soft brand name
Actual news about medicament. Read information now.
Какие нужные слова… супер, замечательная идея
Experience: What kind of experience does the company need, https://virtuino.com/forum/member.php?action=profile&uid=27575 and useful in this industry?
22 апреля чипмейкер Intel опубликует квартальную отчетность о рынке Forex брокеры в РФ Компания выпустит финансовый отчет после завершения основной торговой сессии на американском рынке.
Это не совсем то, что мне нужно. Есть другие варианты?
As the crypto world continues to expand, cryptospb’s CryptoSPBneed for verified and relevant data has become paramount. in the era it technologies access to timely verified and reliable information significant, and bitcoins-of this kind services coped with the task to meet this needs in a dynamic and constantly changing cryptocurrency landscape.
where to buy doxycycline online
http://kamagra.icu/# Kamagra 100mg price
Наша статья рассказывает про лучшие обменники криптовалюты с минимальными комиссиями посмотреть сайт Мы изучили все обменники по большому количеству параметров, таких как: скорость обмена, работа службы поддержки, платежные методы и тд.
Pills information leaflet. Cautions.
order viagra
Actual news about medication. Get here.
Great site, I recommend it to everyone!youtube views increaser
Meds information sheet. Brand names.
glucophage pills
Some what you want to know about meds. Get here.
microlearning library
Drugs information. Brand names.
provigil sale
Best trends of pills. Read information now.
nettruyenmax
Buy Cialis online buy cialis pill Buy Tadalafil 5mg
Автоматизированное нанесение штукатурки — новаторский подход проведения отделки стен.
Он основан на применении штукатурных станций, обычно, сделанных в Германии, что позволяет раствор приготавливается и покрывается на стену с автоматическим распределением и под давлением.
Машинная штукатурка С подтвержденной гарантией До 32 процентов выгоднее обычной, Можно клеить обои без шпаклевки от кампании mehanizirovannaya-shtukaturka-moscow.ru
В результате, повышается прочность сцепления с поверхностью, а время работ уменьшается в 5–6 раз, в сравнении с ручной отделкой. За счет автоматизации и упрощения рабочего процесса цена штукатурки стен за квадратный метр выходит дешевле, чем при традиционном методе.
При машинном нанесении штукатурки используются смеси, разработанные для механизированной штукатурки, цена которых ниже чем при ручной отделке примерно на треть. При определенной квалификации мастеров, а так же если соблюдаются все технологические стандарты, поверхность, покрытая штукатуркой оказывается идеально ровной (СНиП 3.04.01–87 «Высококачественная штукатурка») и полированной, поэтому, дальнейшая отделка шпатлевкой не требуется, что предоставляет дополнительные финансовые возможности для клиента.
С развитием технологий и интернет-сервисов, виртуальные номера стали весьма популярными среди пользователей мессенджеров и социальных сетей купить вирт номер для тг одним из самых популярных приложений для общения и обмена информацией является Телеграмм.
Прошу прощения, что я вмешиваюсь, есть предложение пойти по другому пути.
Special games, what posted in our categories, include online bingo, keno, scratchers, http://fashion.ayrehldavis.com/2014/08/11/sed-eu-dui-massa/ and sik bo.
Hello! Do you know if they make any plugins
to safeguard against hackers? I’m kinda paranoid about
losing everything I’ve worked hard on. Any recommendations?
my site restoration toronto
get sildigra tablets
DG試玩
https://medium.com/@advencher1978/vps-server-ee111932b189
Medicine prescribing information. What side effects?
lyrica tablets
Actual about medication. Read information here.
nettruyen
One of the best sites for Bitcoin Price USD
kantor bola
Kantorbola adalah situs slot gacor terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat slot dengan rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99
We present to you a list of 1xbet promotional codes relevant for 2022: http://mecanica-nautica-mm.com/pag/el_codigos_promocionales_1xbet_bono_gratis.html Without promotional codes, the bonus is 25,000.
Medicine information sheet. Generic Name.
levitra
Everything news about drugs. Read now.
manclub
http://www.newlcn.com/pages/news/mostbet_promokod.html
Промокод 1xBet «Max2x» 2023: разблокируйте бонус 130%
Промокод 1xBet 2023 года «Max2x» может улучшить ваш опыт онлайн-ставок. Используйте его при регистрации, чтобы получить бонус на депозит в размере 130%. Вот краткий обзор того, как это работает, где его найти и его преимущества.
Понимание промокодов 1xBet
Промокоды 1xBet — это специальные предложения букмекерской конторы, которые сделают ваши ставки еще интереснее. Они представляют собой уникальные комбинации символов, букв и цифр, открывающие бонусы и привилегии как для новых, так и для существующих игроков.
Новые игроки часто используют промокоды при регистрации, привлекая их заманчивыми бонусами. Это одноразовое использование для создания новой учетной записи. Существующие клиенты получают различные промокоды, соответствующие их потребностям.
Получение промокодов 1xBet
Для начинающих:
Новые игроки могут найти коды в Интернете, часто на веб-сайтах и форумах, что мотивирует их создавать учетные записи, предлагая бонусы. Вы также можете найти их на страницах 1xBet в социальных сетях или на партнерских платформах.
От букмекера:
1xBet награждает постоянных клиентов промокодами, которые доставляются по электронной почте или в уведомлениях учетной записи.
Демонстрация промокода:
Проверяйте «Витрину промокодов» на веб-сайте 1xBet, чтобы регулярно обновлять коды.
Таким образом, промокод 1xBet «Max2x» расширяет возможности ваших онлайн-ставок. Это ценный инструмент для новичков и опытных игроков. Следите за этими кодами из различных источников, чтобы максимизировать свои приключения в ставках 1xBet.
Medicament information sheet. Effects of Drug Abuse.
cheap synthroid
Everything news about pills. Read information now.
Really one of the best sites Bitcoin Price USD
daftar surgaslot77
SURGASLOT77 – #1 Top Gamer Website in Indonesia
SURGASLOT77 merupakan halaman website hiburan online andalan di Indonesia.
kantorbola
cordarone in breastfeeding
Индивидуальные кухни за 10 дней напрямую от производителя, рассчитайте цену со скидкой до 37% кухни по индивидуальным размерам кухня от производителя с установкой за 10 дней!
Круглосуточная доставка алкоголя в Казани. В нашем магазине вы можете заказать любимые напитки с доставкой на дом доставка алкоголя на дом казань круглосуточно у нас самые низкие цены и лучший сервис.
Medicine information sheet. Drug Class.
rx norvasc
All about meds. Get now.
Меня неожиданно отправили в командировку, и я понял, что не хватает денег на билеты и проживание. Но, к счастью, я нашел решение на сайте credit-info24.ru, где собраны все лучшие МФО. Быстро оформил микрозайм срочно без отказа и проверки, и через 15 минут деньги уже были на моей карте. Командировка прошла успешно, и я даже получил премию от компании.
Отказное письмо для маркетплейсов: кому нужно и как его получить оформить отказное письмо для маркетплейса чтобы продавать товары на маркетплейсах, нужно доказать, что продукция безопасна для людей, животных и природы.
п»їkamagra Kamagra 100mg price Kamagra tablets
https://kamagra.icu/# Kamagra Oral Jelly
Drug information. Effects of Drug Abuse.
cheap flagyl
Some trends of medication. Get information here.
Really this is one of the best sites Bitcoin Price USD
Дуже класний та цікавий сайт! Всім рекомендую! створення сайту ПОВНИЙ КОМПЛЕКС ПОСЛУГ ЩОДО СТВОРЕННЯ САЙТА!
Hey there! I’m at work browsing your blog from my new iphone!
Just wanted to say I love reading through your blog and look forward to all your posts!
Carry on the excellent work!
Абузоустойчивый VPS
Абузоустойчивый VPS
Улучшенное предложение VPS/VDS: начиная с 13 рублей для Windows и Linux
Добейтесь максимальной производительности и надежности с использованием SSD eMLC
Один из ключевых аспектов в мире виртуальных серверов – это выбор оптимального хранилища данных. Наши VPS/VDS-серверы, совместимые как с операционными системами Windows, так и с Linux, предоставляют доступ к передовым накопителям SSD eMLC. Эти накопители гарантируют выдающуюся производительность и непрерывную надежность, обеспечивая бесперебойную работу ваших приложений, независимо от выбора операционной системы.
Высокоскоростной доступ в Интернет: до 1000 Мбит/с
Скорость подключения к Интернету – еще один важный фактор для успеха вашего проекта. Наши VPS/VDS-серверы, поддерживаемые как Windows, так и Linux, гарантируют доступ в Интернет со скоростью до 1000 Мбит/с, что обеспечивает мгновенную загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
Пентралапон — это экологически чистый строительный материал https://maps.google.com.pe/url?q=http://pentralapon-astra.ru представляет собой смесь для ручной и автоматизированной отделки стен, потолков и других поверхностей.
Cel mai prietenos ?i crazy gadget store care i?i va colora experien?a digitala cu emo?ii, stil ?i creativitate xiaomi store md Ne-am lansat in martie 2013 ?i am adus cu noi „Festivalul Culorilor”
buy doxycycline hyclate 100mg usa
I am regular visitor, how are you everybody? This article
posted at this website is genuinely fastidious.
Новости политики на Смоленском портале. Архив новостей. шестнадцать недель назад. 1 страница
Nhà Cái
1xbet
Дуже класний та цікавий сайт! Всім рекомендую! создание сайта ПОВНИЙ КОМПЛЕКС ПОСЛУГ ЩОДО СТВОРЕННЯ САЙТА!
Meds information for patients. Cautions.
norpace
Best what you want to know about drugs. Read here.
Имеется множество автосервисов и технических центров, специализирующихся на обслуживании и ремонте автомобилей Audi и Skoda автосервис шкода Один из таких – автосервис Ауди.
where buy generic sildigra price
здесь можно произвести кузовной ремонт автомобиля, если он был поврежден в результате аварии или коррозии автосервис шкода Все работы выполняются высококвалифицированными специалистами с использованием современных технологий и оборудования.
Medication information sheet. Brand names.
rx fluoxetine
Best what you want to know about drug. Get now.
Drugs information. Long-Term Effects.
lisinopril
Actual about drugs. Get information here.
Группа «Каспий» родилась в конце 2012 года, в Москве, когда Володя Астапчик собрал вокруг себя группу музыкантов-единомышленников. Уже через полгода, летом 2013 года команда, названная «Каспий», дебютировала на фестивалях «Нашествие» и «Доброфест». Мелодичность, драйв и многослойная лирика текстов помогли группе стремительно завоевать Интернет- и офф-лайн аудиторию.
звукорежиссура каспий
Саме тут Ви можете замовити створення сайту ПОВНИЙ КОМПЛЕКС ПОСЛУГ ЩОДО СТВОРЕННЯ САЙТА!
Вы можете приобрести Пентралапон оптом и в розницу у авторизованных дилеров и поставщиков http://townoflogansport.com/about-logansport/Calendar/Details/14-09-18/Food_Bank_Open.aspx?Returnurl=http://pentralapon-astra.ru
Отказное письмо для маркетплейсов: кому нужно и как его получить стоимость отказного письма для маркетплейса С экспертом разбираемся, когда это нужно и как его оформить. Отказное письмо для маркетплейса — документ, который подтверждает, что конкретная продукция не подлежит обязательной сертификации и декларированию.
can i purchase generic sildigra tablets
Что-то так не выходит
solo uno de tales entretenimiento era el juego juegos en https://rnzpba.com/2021/07/31/hello-world/. juegos de azar como forma bromas, y tiempo siempre han ocupado extremadamente importante lugar en sociedad.
Just as ѡith tthe labprious drive, you need tо use any available
connector from thе facility supply. Ӏf the batteries do
run utterly out of juice οr іf you remove them, most devices һave an insiɗe backup battery tһat giѵes short-time period energy (ѕometimes 30 minutes or leѕs) ᥙntil yoou іnstall a
alternative. Ԍreater tһan the rest, the London Marathon іs a cracking gօod
time, with maany mеmbers decked ᧐ut іn costume.
Classes can price m᧐re tһan $1,800 andd private
tutoring mіght be aѕ much as $6,000.Like օn different consoles, these apps ccan bee logged іnto with an exzisting accoujt and
be usеd to stream vixeos frm tһose services. Videos ɑrе also saved іf tһe
g-sensor senses impression, aas wіth all spint cams.
Ꮤhile thе tоp pizes are substantial, they don’t sеem tߋ be really progressive jackpots
bеϲause tһe identify recommend tat tһey mіght Ƅe, һowever we won’t dwell оn thіs annd just takje pleasure
іn the game fⲟr ԝhat iit is.
Loⲟk int᧐ myy blog :: เครดิตฟรี
kantorbola
Kantor bola Merupakan agen slot terpercaya di indonesia dengan RTP kemenangan sangat tinggi 98.9%. Bermain di kantorbola akan sangat menguntungkan karena bermain di situs kantorbola sangat gampang menang.
Medicine information for patients. Long-Term Effects.
stromectol otc
All information about drugs. Get information here.
Тут четко отслеживают последние идеи лучших брендов, в числе которых silver cross, mima, brevi, bright starts, chicco, fisher-price, maxi-cosi, quinny, smoby, step2, tiny love, vtech, 4moms, graco, pegperego, kiddieland, leapfrog, little tikes, avent, medela, yoyo, yoya, stokke, http://cl0915.com/bbs/board.php?bo_table=free&wr_id=9764 babybjorn и мн.др.
Drug information. Generic Name.
cordarone
Actual news about meds. Get information now.
for processing receiving funds – with the https://www.piecesracing.com/docs/pgs/code_promo_betwinner_8.html you need prove own account by providing documents, including an identity photo, or driver’s license, but also a bank statement or utility bill.
The advantage of this model is everything that consumer get an opportunity cancel the tariff plan at any time to get your money back, even in the case when you don’t satisfied with the product after the http://sewontech.kr/bbs/board.php?bo_table=free&wr_id=350522 trial period expires.
Drugs information for patients. Drug Class.
where to buy lasix
Some trends of drug. Read information here.
Hi, i feel that i noticed you visited my website so i
came to return the desire?.I’m trying to find issues to
improve my web site!I guess its adequate to make use of some of your ideas!!
Рост продаж сопровождается ростом цен. Объем торгов на вторичке по сравнению с прошлым годом вырос на 25% какую машину лучше купить в 2023 году лучшими б/у автомобилями являются Opel Meriva, Audi Q5, Toyota Avensis, BMW Z4, Audi А3, Mazda 3 и Mercedes GLK.
Профессиональная переподготовка по более чем 20 направлениям в отрасли строительства переподготовка строительство дипломы установленного образца, индивидуальные программы
EnchagPT Blog to miejsce, gdzie można znaleźć interesujące artykuły i informacje na temat technologii sztucznej inteligencji.
Jest to blog dedykowany wszystkim entuzjastom sztucznej inteligencji, którzy pragną zgłębiać swoją wiedzę
na temat tego fascynującego tematu.
http://linklist.bio.sitescorechecker.com/
kantorbola99
KANTORBOLA99 Adalah situs judi online terpercaya di indonesia. KANTORBOLA99 menyediakan berbagai permainan dan juga menyediakan RTP live gacor dengan rate 98,9%. KANTORBOLA99 juga menyediakan berbagai macam promo menarik untuk setiap member setia KANTORBOLA99, Salah satu promo menarik KANTORBOLA99 yaitu bonus free chip 100 ribu setiap hari
Вы ошибаетесь. Давайте обсудим это. Пишите мне в PM, пообщаемся.
Gana puntos completando tareas, para ganar poses/ posiciones y ganar giros en https://playpokerbet365.com/ con premios. 365 poker proporciona todos los servicios originales de la plataforma bet365 y dirigido a creacion de uno de los mejores programas para en linea en el mercado.
Выгодные предложения по ипотеке на готовое жилье от проверенных банков в 2023 году калькулятор ипотеки подберите для себя самый выгодный вариант ипотеки на готовое жилье.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Axxinot – торговая марка вертикальных радиаторов, производимых в России и Белоруссии из высококачественной прецизионной и нержавеющей стали.
Универсальный калькулятор ипотеки для всех банков. Расчет ежемесячного платежа за несколько секунд ипотечный калькулятор онлайн наглядный график погашения.
effexor 37.5
И так тоже бывает:)
Como fazer aposta no 888sport? Processo apostas – no 888sport brasil tal como na maioria BK brazil888poker.com atual.
how can i get cheap aurogra price
Medicine information sheet. What side effects can this medication cause?
stromectol medication
Everything trends of pills. Read here.
С У П Е Р !!!!!!!!!!!!!!!!!!!!!!
voce ganha pontos cada vez que voce participar correspondencia jogo de poker online em Real dinheiro, Faca aposta em 888sports ou tente destino no 888casino, play888pokerinbrasilia.com lider mercado online instituicao de jogos.
Medicines information. Drug Class.
proscar tablet
Everything trends of medicine. Get information here.
Есть что-нибудь похожее?
geralmente, https://radiostopfm.com/ voce vai jogar em um torneio com Premio fundo de duas ou tres vezes o buy-in original, onde apenas o vencedor recebe o premio.
Реальные ставки по ипотеке от 6%, одна заявка на ипотеку онлайн сразу в несколько банков. От 2 часов на одобрение заявки онлайн калькулятор ипотеки ипотека на покупку вторичного жилья и новостроек.
Льготные программы ипотеки в Москве с господдержкой. Выгодные ставки по кредиту на покупку жилья ипотека в москве оформление ипотеки и проведение сделки онлайн.
buy actos 10 mg
Medicament information. What side effects?
levitra
Best about pills. Read information now.
Я думаю, что Вы допускаете ошибку. Могу это доказать.
После достижения официальный вебсайт покерного сайта Покердом пользователям рекомендуется зайти в личный аккаунт и изучить вкладку «Турниры» для изучения перечнем нужных нонче https://playpropokerdomkz.com/ ивентов.
Вы не правы. Я уверен. Могу отстоять свою позицию. Пишите мне в PM.
в этой среде центральное – дистанция, и, коль в особой сдаче, игровой сессии или например турнире роль удачи действительно велика, либо программы итогам тысяч, а в идеале десятков и сотен тысяч сыгранных раздач сильные участники все одно останутся в выигрыше, proplayggpokerua.com а слабые все проиграют.
Отказное письмо (ОП) – это документ, который удостоверяет, что изделие/товар/материал не подлежат обязательной оценке качества и получению сертификата/декларации в определённой системе что такое отказное письмо отказные письма оформляются в разных сертификационных системах.
Что такое отказное письмо по сертификации и кому оно нужно. Отказное письмо — документ, который подтверждает, что товару не требуется сертификат качества или декларация соответствия что такое отказное письмо чтобы продавать товары на маркетплейсах, нужно доказать, что продукция безопасна для людей, животных и природы.
media wall hull
От нового дизайна до ремонта под ключ с «СК Сити Строй”
Хотите, чтобы ремонт вашей квартиры был выполнен безупречно и без лишних забот? ООО «СК СИТИ СТРОЙ» – ваш надежный партнер в области ремонта “под ключ”. Мы предлагаем полный комплекс услуг по ремонту квартир, начиная с 2003 года и объединяя под одной крышей лучших мастеров Москвы и Подмосковья.
Ремонт квартир под ключ — это идеальное решение для тех, кто ценит свое время и предпочитает качество. Мы берем на себя все этапы ремонта: от разработки дизайн-проекта до его полного воплощения. Наши клиенты могут быть уверены, что все работы будут выполнены в строгом соответствии с заявленными сроками и бюджетом.
Посетите наш сайт, чтобы узнать больше о наших услугах или начать планировать свой ремонт уже сегодня. Мы находимся по адресу: 127055 г. Москва, ул. Новослободская, д. 20, к. 27, оф. 6. ООО «СК СИТИ СТРОЙ» — это ваш выбор в пользу безупречного ремонта и комфортной жизни.
daftar surgaslot
Для вас работает алкомаркет — доставка водки на дом круглосуточно, быстро, надежно! В ассортименте каталога вас ждет отличное крепкое спиртное: доставка алкоголя на дом москва круглосуточно недорого заказать водку с доставкой на дом не будет сложно.
Смешанная стяжка – метод выравнивания пола. Строительство полутвёрдой стяжки позволяет создать ровную поверхность для последующей отделки.
полусухие стяжки Мы сделаем супер ровную стяжку пола. 7 лет опыта работы От 500 рублей за квадратный метр
Уход за полусухой стяжкой подразумевает систематический мониторинг и устранение неисправностей с использованием технических средств.
Технические средства для полутвёрдой стяжки способствует провести монтаж с высокой точностью. Частично сухая стяжка пола представляет собой эффективный вариант для создания надежного фундамента для дальнейшей отделки.
За относительно небольшие деньги вы получаете активированный аккаунт Делимобиль, Яндекс Драйв, Ситидрайв, Белку Купить аккаунт каршеринга Для службы каршеринга, все выглядит так, как-будто автомобилем пользуется другой человек. Вуаля.
r benemid
With thanks, An abundance of stuff.
startup business plan writing service essay writing contest real essay writing service
what is finasteride
Really quite a lot of excellent material!
islamic will writing service essay writting essay writing guide
Meds information leaflet. Effects of Drug Abuse.
kamagra
Everything about meds. Read information now.
2023-24英超聯賽萬眾矚目,2023年8月12日開啟了第一場比賽,而接下來的賽事也正如火如荼地進行中。本文統整出英超賽程以及英超賽制等資訊,幫助你更加了解英超,同時也提供英超直播平台,讓你絕對不會錯過每一場精彩賽事。
英超是什麼?
英超是相當重要的足球賽事,以競爭激烈和精彩程度聞名
英超是相當重要的足球賽事,以競爭激烈和精彩程度聞名
英超全名為「英格蘭足球超級聯賽」,是足球賽事中最高級的足球聯賽之一,由英格蘭足球總會在1992年2月20日成立。英超是全世界最多人觀看的體育聯賽,因其英超隊伍全球知名度和競爭激烈而聞名,吸引來自世界各地的頂尖球星前來參賽。
英超聯賽(English Premier League,縮寫EPL)由英國最頂尖的20支足球俱樂部參加,賽季通常從8月一直持續到5月,以下帶你來了解英超賽制和其他更詳細的資訊。
英超賽制
2023-24英超總共有20支隊伍參賽,以下是英超賽制介紹:
採雙循環制,分主場及作客比賽,每支球隊共進行 38 場賽事。
比賽採用三分制,贏球獲得3分,平局獲1分,輸球獲0分。
以積分多寡分名次,若同分則以淨球數來區分排名,仍相同就以得球計算。如果還是相同,就會於中立場舉行一場附加賽決定排名。
賽季結束後,根據積分排名,最高分者成為冠軍,而最後三支球隊則降級至英冠聯賽。
英超升降級機制
英超有一個相當特別的賽制規定,那就是「升降級」。賽季結束後,積分和排名最高的隊伍將直接晉升冠軍,而總排名最低的3支隊伍會被降級至英格蘭足球冠軍聯賽(英冠),這是僅次於英超的足球賽事。
同時,英冠前2名的球隊直接升上下一賽季的英超,第3至6名則會以附加賽決定最後一個升級名額,英冠的隊伍都在爭取升級至英超,以獲得更高的收入和榮譽。
У вас пытливый ум 🙂
you are waiting for some amazing trivial quizzes. don’t shy https://gossettbrothers.com/wp/nursery/featured-summer/, in order to enjoy it!
英超
2023-24英超聯賽萬眾矚目,2023年8月12日開啟了第一場比賽,而接下來的賽事也正如火如荼地進行中。本文統整出英超賽程以及英超賽制等資訊,幫助你更加了解英超,同時也提供英超直播平台,讓你絕對不會錯過每一場精彩賽事。
英超是什麼?
英超是相當重要的足球賽事,以競爭激烈和精彩程度聞名
英超是相當重要的足球賽事,以競爭激烈和精彩程度聞名
英超全名為「英格蘭足球超級聯賽」,是足球賽事中最高級的足球聯賽之一,由英格蘭足球總會在1992年2月20日成立。英超是全世界最多人觀看的體育聯賽,因其英超隊伍全球知名度和競爭激烈而聞名,吸引來自世界各地的頂尖球星前來參賽。
英超聯賽(English Premier League,縮寫EPL)由英國最頂尖的20支足球俱樂部參加,賽季通常從8月一直持續到5月,以下帶你來了解英超賽制和其他更詳細的資訊。
英超賽制
2023-24英超總共有20支隊伍參賽,以下是英超賽制介紹:
採雙循環制,分主場及作客比賽,每支球隊共進行 38 場賽事。
比賽採用三分制,贏球獲得3分,平局獲1分,輸球獲0分。
以積分多寡分名次,若同分則以淨球數來區分排名,仍相同就以得球計算。如果還是相同,就會於中立場舉行一場附加賽決定排名。
賽季結束後,根據積分排名,最高分者成為冠軍,而最後三支球隊則降級至英冠聯賽。
英超升降級機制
英超有一個相當特別的賽制規定,那就是「升降級」。賽季結束後,積分和排名最高的隊伍將直接晉升冠軍,而總排名最低的3支隊伍會被降級至英格蘭足球冠軍聯賽(英冠),這是僅次於英超的足球賽事。
同時,英冠前2名的球隊直接升上下一賽季的英超,第3至6名則會以附加賽決定最後一個升級名額,英冠的隊伍都在爭取升級至英超,以獲得更高的收入和榮譽。
BBW anilingus
Drugs information for patients. Cautions.
zithromax
Actual trends of medicine. Get information now.
cordarone hcl
Что делать, если покупатель на маркетплейсе просит отказное письмо. Производители и продавцы товаров должны предоставлять отказное письмо по запросу маркетплейса, Роспотребнадзора или клиентов отказное письмо по сертификации Требование относится к отечественной и импортной продукции. Отказные письма бывают двух видов: для торговли и для таможенного оформления.
where buy cheap finpecia pills
Pills information. Brand names.
norvasc
Everything about medicines. Read information here.
Meds information for patients. What side effects can this medication cause?
lisinopril brand name
Some trends of medicine. Get now.
ЗОЖ
Купить нержавеющие трубы по доступным ценам за метр от производителя. Действуют скидки! Склады в Москве и всей России трубы нержавеющие Быстрая доставка! Заказать трубы из нержавеющей стали.
http://women.getbb.ru/viewtopic.php?f=2&t=722
Drugs information for patients. Generic Name.
lopressor for sale
Best information about medicines. Get information here.
адрес прокси сервера
как узнать прокси сервер
заборы кирпич строительство
строительство забор краснодар
забор строительство гараж
строительство заборов рассчитать
Компания «ОТЭКО», оператор морских терминалов в порту Тамань, подвела итоги первого этапа внедрения Производственной системы отэко тамань за 10 месяцев реформ на навалочном терминале и в департаменте железнодорожного транспорта были внедрены инструменты бережливого производства.
kantorbola
KANTOR BOLA adalah Situs Taruhan Bola untuk JUDI BOLA dengan kelengkapan permainan Taruhan Bola Online diantaranya Sbobet, M88, Ubobet, Cmd, Oriental Gaming dan masih banyak lagi Judi Bola Online lainnya. Dapatkan promo bonus deposit harian 25% dan bonus rollingan hingga 1% . Temukan juga kami dilink kantorbola77 , kantorbola88 dan kantorbola99
скачать казино brillx
https://brillx-kazino.com
Предоставив широкий спектр игр и вариантов ставок, мы делаем ставку на то, что каждый игрок найдет что-то особенное для себя. Brillx Казино – это не просто место для азартных игр, это место, где рождаются легенды и судьбы переплетаются с риском.В 2023 году Brillx Казино стало настоящим оазисом для азартных путешественников. Подарите себе незабываемые моменты радости и азарта. Не упустите свой шанс сорвать куш и стать частью легендарной истории на страницах брилкс казино.
Medicines information for patients. What side effects?
promethazine
Best information about medicine. Get here.
ремонт стиральных машин СПб
Today, a large number of Internet users are betting on sports https://files.fm/pin1019/info Someone treats it as entertainment, and someone as a part-time job.
Сертификат соответствия СМК требованиям ИСО 9001 – документ, который выдается по результатам экспертной проверки и подтверждает, https://www.sostav.ru/blogs/30357/19844 что система менеджмента качества (СМК) организации соответствует международному стандарту ISO 9001 «Системы менеджмента качества.
brillx casino официальный мобильная версия
brillx casino
Но если вы ищете большее, чем просто весело провести время, Brillx Казино дает вам возможность играть на деньги. Наши игровые аппараты – это не только средство развлечения, но и потенциальный источник невероятных доходов. Бриллкс Казино сотрясает стереотипы и вносит свежий ветер в мир азартных игр.Brillx Казино — ваш уникальный путь к захватывающему миру азартных игр в 2023 году! Если вы ищете надежное онлайн-казино, которое сочетает в себе захватывающий геймплей и возможность играть как бесплатно, так и на деньги, то Брилкс Казино — идеальное место для вас. Опыт непревзойденной азартной атмосферы, где каждый спин, каждая ставка — это шанс на большой выигрыш, ждет вас прямо сейчас на Brillx Казино!
can i order sildigra
cost of cheap lyrica online
Дуже крутий сайт! Всім рекомендую! rozetka
where to buy cheap abilify without rx
Medicines information. Drug Class.
pregabalin
Best what you want to know about drugs. Read information now.
Серия ISO 9000 касается требований к управлению предприятием для обеспечения выпуска качественной продукции сертификат исо 9001 стоимость она основывается на 8 принципах.
Medicine information. Brand names.
levitra cost
All about medicines. Get now.
Линия позволит сократить минимальное время обработки судов Capesize в порту Тамань в два раза — c 48 до 24 часов отэко тамань команду «Пуск» в ходе телемоста между Москвой и Таманью дал заместитель председателя правительства.
1xbet промокод
1win промокод
Medication information sheet. What side effects can this medication cause?
nolvadex
Some what you want to know about drugs. Read information now.
bocor88 f81e957
Апелляционная жалоба – это письменное обращение к вышестоящему суду с просьбой пересмотреть решение первой инстанции http://advtver.ru/ она должна содержать юридически обоснованные аргументы, доказывающие неправильность или несправедливость данного решения.
where can i get generic sildigra price
victor evgenevich ponomarchuk viol
Продэкспо-2024 можно посетить с 5 по 9 февраля. В первые дни экспозиция принимает гостей с 10:00 до 18:00 часов https://domdvordorogi.ru/vystavka-prodekspo-2024/ 9 февраля выставочной зал будет работать с 10:00 до 16:00.
Китайские интернет-магазины на русском языке, лучшие сайты предлагают большой ассортимент товаров во всевозможных сегментах рынка https://weiguang.ru/ покупатели находят покупки достойного качества по лучшим ценам.
https://salonokna.ru/
купить диплом в москве
https://cse.google.by/url?q=http://diplomarkets.com/
Дуже крутий сайт! Всім рекомендую! розетка
перевод документов
Организационная основа улучшений — использование регулярных практик управления (РПУ) и плана организационных улучшений (ПОУ) отэко тамань Помимо повышения культуры производства, ПСО дает и экономический эффект, в том числе помогает снизить использование спецтехники при погрузочно-разгрузочных работах.
автосигнализация
Drugs information for patients. What side effects can this medication cause?
kamagra
All trends of drug. Read here.
автосигнализация
Drug information for patients. Brand names.
fosamax generic
All what you want to know about drugs. Get here.
Компания «ОТЭКО», основанная предпринимателем Мишелем Литваком, – один из крупнейших налогоплательщиков и работодателей в Краснодарском крае отэко тамань Ее налоговые отчисления формируют почти 60 % ежегодного бюджета Таманского сельского поселения.
кальянная
Концепция корпоративной социальной ответственности (КСО) начала формироваться в 1970-х гг. в западных странах отэко тамань её суть заключается в том, что бизнес добровольно берёт на себя дополнительные обязательства перед обществом.
купить спецодежду
where to buy generic sildigra prices
автосигнализация
VPS SERVER
Высокоскоростной доступ в Интернет: до 1000 Мбит/с
Скорость подключения к Интернету — еще один важный фактор для успеха вашего проекта. Наши VPS/VDS-серверы, адаптированные как под Windows, так и под Linux, обеспечивают доступ в Интернет со скоростью до 1000 Мбит/с, что гарантирует быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
Medicine information leaflet. Short-Term Effects.
cleocin generic
Some information about medicine. Get information here.
Компания “СветОкнаСити” занимается производством и
установкой пластиковых окон высокого качества,
обеспечивая потребителей в Москве и окрестностях
надежными и эстетически приятными оконными решениями.
С момента своего основания в 2000 году, компания зарекомендовала
себя как одного из ведущих производителей в индустрии,
устанавливая более 800 тысяч окон и активно мониторя индекс
удовлетворенности клиентов.
https://svetokna77.ru/
Drug information leaflet. Cautions.
cipro medication
Some news about medicament. Read information now.
Medicines information sheet. Generic Name.
lisinopril order
Actual what you want to know about medicament. Get here.
abilify feelings
Не могу с вами не согласится.
по информации полиции, 37-летний житель Ульяновска создал портал , где были размещены информацию о выдаче сексуальных услуг. через некоторое время ему позвонил диспетчер и сообщил, https://vdobrieruki.ru/user/profile/876916 большая повторить перевод в силу технических процедур.
Drugs information leaflet. Cautions.
can i get flagyl
Best what you want to know about medicament. Get information now.
Aeza Trade лохотрон
Meds prescribing information. Cautions.
fluoxetine
All information about medicament. Read here.
https://clashofcryptos.trade/wiki/User:DyanHoy54675
Drug information for patients. Short-Term Effects.
proscar generic
All information about pills. Read here.
Абузоустойчивый VPS
Виртуальные серверы VPS/VDS: Путь к Успешному Бизнесу
В мире современных технологий и онлайн-бизнеса важно иметь надежную инфраструктуру для развития проектов и обеспечения безопасности данных. В этой статье мы рассмотрим, почему виртуальные серверы VPS/VDS, предлагаемые по стартовой цене всего 13 рублей, являются ключом к успеху в современном бизнесе
zoloft 25 mg
Респект!!! Качественные продукты выкладываешь!
in simple words, https://aleratrading.com/forum/member.php?action=profile&uid=92015 is a distributed and immutable digital ledger that is responsible for registration operations and tracking the movement of digital assets in sexual network.
На мой взгляд. Ваше мнение ошибочно.
а вот ярко-красные цветы на длинных стеблях символизируют серьезные намерения с https://real-vin.com/nardi-koli-ta-komu-daruvati подтекстом.
game tài xỉu uy tín
Drug information leaflet. Effects of Drug Abuse.
zovirax
Everything news about pills. Read now.
Я считаю, что Вы не правы. Могу это доказать. Пишите мне в PM, пообщаемся.
if user receive product or register account at address on our step sister porn, we can receive compensation.
По моему мнению Вы допускаете ошибку. Могу это доказать. Пишите мне в PM, обсудим.
как воздействует купить номер телефона для тг? Сотрудникам не надо беспокоиться обо том, что заказчики знают ваш частный номер. клиенту не придется пойдет через нескольких специалистов, дабы достичь нужного агента.
Drug information sheet. Brand names.
propecia
Best news about meds. Read information now.
Medicine information leaflet. What side effects can this medication cause?
tadacip tablet
Actual trends of medicine. Read information now.
MAGNUMBET Situs Online Dengan Deposit Pulsa Terpercaya. Magnumbet agen casino online indonesia terpercaya menyediakan semua permainan slot online live casino dan tembak ikan dengan minimal deposit hanya 10.000 rupiah sudah bisa bermain di magnumbet
buy prednisone without dr prescription
высокооплачиваемая работа для девушек за границей
Отличный Консалтинговый центр! Всем рекомендую!гражданство Молдовы представляет собой 15-летний опыт юристов собранный в едином центре услуг. Наша миссия – предоставить возможность любому гражданину оформить гражданство Молдовы и Румынии в соответствии с законодательными нормами страны.
Medication information for patients. Effects of Drug Abuse.
prednisone
Best trends of drugs. Read now.
Pills prescribing information. Brand names.
rx prednisone
Actual what you want to know about meds. Read information here.
герои сериал смотреть онлайн
Pills information sheet. Effects of Drug Abuse.
cheap tadacip
Some trends of medicines. Read here.
Что-то меня уже не на ту тему понесло.
Я уверен, http://shooting-russia.ru/forum/?PAGE_NAME=message&FID=11&TID=12593&TITLE_SEO=12593-pro100sex&MID=12854&result=new#message12854 как и половина из моих коллег-девушек не слышала о менструальных чашах.
герои сериал смотреть онлайн
кликбейт сериал смотреть онлайн
Отличный Консалтинговый центр! Всем рекомендую!гражданство Румынии представляет собой 15-летний опыт юристов собранный в едином центре услуг. Наша миссия – предоставить возможность любому гражданину оформить гражданство Молдовы и Румынии в соответствии с законодательными нормами страны.
сериал убийство смотреть онлайн
сериал лихач смотреть онлайн
how much ashwagandha per day
hoki 1881
Medicine information sheet. Generic Name.
neurontin
Some about medicament. Get here.
Торговаля криптовалютой
Pills information sheet. Long-Term Effects.
zoloft medication
All about drug. Read information now.
Medicines information sheet. Effects of Drug Abuse.
zithromax
Actual what you want to know about medicament. Read information here.
сериал измены смотреть онлайн
калейдоскоп сериал смотреть онлайн
сериал онлайн смотреть бесплатно
b29
b29
сериал стрела смотреть онлайн
Наш интернет-магазин осуществляет оперативную доставку алкоголя на дом в Москве в кратчайшие сроки доставка алкоголя на дом казань круглосуточно в каталоге можно подобрать и оформить ночную доставку на дом алкоголя известных брендов.
prednisone dose pack instructions
сериал миротворец смотреть онлайн
Отличный Консалтинговый центр! Всем рекомендую!гражданство Молдовы по рождению представляет собой 15-летний опыт юристов собранный в едином центре услуг. Наша миссия – предоставить возможность любому гражданину оформить гражданство Молдовы и Румынии в соответствии с законодательными нормами страны.
библиотекарь сериал смотреть онлайн
shaker сериал смотреть онлайн
Drug prescribing information. Generic Name.
flagyl
Some news about drug. Get now.
пицца ростов доставка
На нашем сайте представлены виртуальные телефонные номера для приема сообщений от Telegram, которыми вы можете воспользоваться совершенно бесплатно https://www.google.com.do/url?q=https://hottelecom.net/ua/virtual-number-for-telegram.html большой выбор бесплатных виртуальных номеров для приема СМС от сервиса Telegram.
Это просто великолепная фраза
она помогает игрокам установить перед запуском геймплея определенный коэффициент, по получении которого ставка автоматически сработает, https://www.eldiario24.com/nota/culturas/505367/descarga-juego-aviator.html а средства начисляется на игровой счёт играющего.
пицца ронни доставка
темпо пицца доставка
Пусть будет по-вашему. Делайте, как хотите.
Корпус изготовлена из инструментальной стали, https://avtoka.mybb.od.ua/viewtopic.php?id=1557#p2356 сварные швы выдерживают гидродинамическое воздействие. Поверхность фосфотирована для дополнительной предотвращения коррозии, покрыта порошковой краской.
Прелестная фраза
This function is similar to http://www2c.biglobe.ne.jp/joshjosh/cgi_bin/Jawanot3/jawanote.cgi.randombytes(), however requests that the first argument is a buffer that will be filled.
Medicines information sheet. Cautions.
bactrim sale
Some what you want to know about pills. Get information now.
Это ему даром не пройдет.
як вчинити?з початку війни в Україні в кінцевому підсумку військової російської агресії станом на 17 березня, за інформацією проекту kse “Росія заплатить”, http://lokcetekstil.com/index.php?option=com_k2&view=item&id=22 сума завданих збитків утворює 1,8 трлн гривень або 62,6 млрд дол.
Drug information for patients. What side effects?
diltiazem generics
Everything information about medicines. Read information here.
Быстрый ответ )))
Research not necessary should have big steps, like dismissal from work, transportation to another country, https://writeablog.net/3h3mpf1c6a or travel around earth in search adventures.
Точное сообщения
for the treatment of persons and organism on interior sides of joints quite enough https://steroidsdrugs.com/– or medium-active drugs.
furosemide side effects humans
Мне знакома эта ситуация. Можно обсудить.
The cyclic intake of anavar for girls is +20-50 mg of https://steroidbuildups.com/ no later than 10 weeks.
складчина
Как-то не канет
some people, who inject rexonanabolics.org steroids, can use/can use non-sterile injection methods or share contaminated needles with other visitors.
Meds information leaflet. Short-Term Effects.
nolvadex
Everything news about medicament. Read information here.
Я извиняюсь, но, по-моему, Вы допускаете ошибку. Могу отстоять свою позицию. Пишите мне в PM.
17 carbon atoms arranged in four onlinelegalsteroids.com rings. An additional impetus to steroid research was given when the American physician Philip S. Hench and the American chemist Edward K. Kendall announced in 1949 that the difficult-to-treat symptoms of rheumatoid arthritis were noticeably relieved by the adrenal hormone cortisone.
Сертифицировать СМК на соответствие стандарту ИСО 9001 имеет право орган по сертификации СМК как получить сертификат исо 9001 другими словами, сертификат выдается не на саму продукцию или услуги, а на процессы производства (порядок работы)
http://otoplenie-gid.ru/statti/debetovye-karty-mir-sberbanka
Pills information leaflet. Cautions.
lioresal brand name
Some information about meds. Get here.
Запомни это раз и навсегда!
The availability of high-quality additives has important significance for the beginning of mybodybuildingshop.com in improvement enterprise. These instagram channels are personal portal, google, facebook, instagram, Twitter, quora, banners, advertising, partner agreements and much more.
Аренда яхт и индивидуальные туры на частной яхте от “Чайка на яхте”. Частная лицензированная судоходная компания, г. Санкт-Петербург Роскошные яхты в аренду
Я разбираюсь в этом вопросе. Можно обсудить.
This change was traditionally made to the parent name by adding a prefix to indicate the position, with or without ? (Greek capital delta), which denotes unsaturation, for example, the http://legalsteroidshop.com/ 4-pregnen-11?,17?-diol-3,20-dione (also ?4-pregnen-11?,17?-diol-3.20-dion) or 4-androstene-3,11,17-trione (also ?4-androstene-3,11,17-trione).
Вы попали в самую точку. В этом что-то есть и мне кажется это хорошая идея. Я согласен с Вами.
Hawthorn Berry Extract: The supplement consists of ingredients help increase the production of growth hormone human, and improve intake to the muscles https://buysteroidsonline.org/.
buy doxycycline boots
Пошаговая инструкция как получить лицензию МЧС https://astrakhan-news.net/other/2023/11/13/133762.html. Читайте в статье полное руководство.
Это интересно. Скажите мне, пожалуйста – где я могу найти больше информации по этому вопросу?
it’s a fact. Using 100% anabol.shop, we also introduced 100% free amino acids and naturally, offer ideal supply of amino acids for convenient build-up muscles.
is ashwagandha bad for your liver and kidneys cleveland clinic
Всем рекомендую!Доставка еды уфа
Ресторан доставки “Василий” осуществляет доставку по всему городу Уфа. Заказы готовятся только после поступления и доставляются бесплатно при заказе от 500 рублей, в зависимости от района вашего проживания. Обратите внимание, что десерты и напитки не учитываются в стоимость минимальной суммы заказа. Доставка осуществляется курьерской службой в специальных качественных термосумках. Среднее время ожидания заказа 45-90 минут, время доставки может меняться в зависимости от количества заказов, дорожной обстановки и погодных условий. Пункт самовывоза находится по адресу ул. Шафиева 50/1.
По моему мнению Вы не правы. Я уверен. Пишите мне в PM.
Номера нужного региона. Вам нужен телефонный номер с паролем региона – это повысит https://www.google.ga/url?q=https://hottelecom.net/ua/virtual-number-for-registration.html доверие заказчиков.
Pills information for patients. Effects of Drug Abuse.
cleocin
All about pills. Read information here.
Отказные письма оформляются в разных сертификационных системах и могут требоваться как для реализации продукции, заключения контракта, так и для прохождения таможенного контроля отказное письмо для маркетплейса Отказное письмо – это документ, который подтверждает, что товар не подлежит обязательной сертификации, декларированию.
По моему мнению Вы ошибаетесь. Пишите мне в PM, обсудим.
Игра aviator от spribe – это проработанная беттинг с простой целью получить деньги до того, https://www.serendipitybeads.co.nz/go/order.php?vc=y&return=www.nagpurtoday.in%2Flucky-jet-amazing-gambling-game%2F05011733 как самолет упадет.
https://dermatologcentr.ru/kak-podklyuchit-ekvajring-ot-sberbanka/
Pills prescribing information. Effects of Drug Abuse.
generic tadacip
Everything about medicament. Read now.
Вы допускаете ошибку. Могу это доказать. Пишите мне в PM, пообщаемся.
Мероприятие рассчитано на клиентов компании, http://xn—–6kcwbqeldsdd4a9ag6b6f6b.xn--p1ai/profile.php?uid=140758 длится от пары-тройки суток до полугода.
Я считаю, что Вас ввели в заблуждение.
Автобиография (для заказчиков https://pass-migrate.com/pmzh-residente-permanente/ старше 16 лет). Если несовершеннолетний оформляет документы своими силами без использования родителей), то он платит такую же сумму, как и взрослый.
b29
b29
B52
can i purchase cleocin without a prescription
Medication information leaflet. What side effects can this medication cause?
proscar no prescription
Best trends of medicines. Read here.
Kampus Unggul
VPS SERVER
Высокоскоростной доступ в Интернет: до 1000 Мбит/с
Скорость подключения к Интернету — еще один важный фактор для успеха вашего проекта. Наши VPS/VDS-серверы, адаптированные как под Windows, так и под Linux, обеспечивают доступ в Интернет со скоростью до 1000 Мбит/с, что гарантирует быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
Сертификат ИСО 9001 – документ, который подтверждает, что на предприятии внедрена система стандартов ИСО сертификат ИСО 9001 для чего нужен документ в системе стандартов ISO 9001?
флагман
Сфера медицины традиционно представляет собой одну из наиболее перспективных и интересных отраслей для собственного развития и построения карьеры переквалификация врачей а потому нет ничего удивительного в том, что большое количество человек каждый год активно начинает свой путь именно в ней.
cordarone medication guide
складчина
https://crazysale.marketing/revolut.html
Meds information sheet. Generic Name.
buy generic cleocin
Best about drugs. Read here.
Сертификат соответствия ISO 9001 – разрешительный документ. Его оформление подтверждает, что компания внедрила у себя систему менеджмента качества (далее – СМК), которая успешно функционирует сертификат ИСО 9001 Получение сертификата ИСО 9001 – добровольная процедура.
vavada казино
студия праздника
Drugs information sheet. Effects of Drug Abuse.
lasix otc
All information about medicines. Read here.
Regardless of whether you are looking for electronic equipment, children’s clothing or food products, you can always find everything you need https://crazysale.marketing/depositphotos.html In addition, the site offers regular discounts and promotions for a number of product categories.
Между нами говоря, я бы так не делал.
в множестве обстоятельств использование наших услуг – быстрый, простой, достоверный и безопасный способ не регясь на всех площадках, открывающий беспрепятственный доступ к общению, работе, https://www.google.bi/url?q=https://hottelecom.net/ua/sms-numbers.html творчеству и другим возможностям интернета.
Всем рекомендую!доставка суши уфа
Ресторан доставки “Василий” осуществляет доставку по всему городу Уфа. Заказы готовятся только после поступления и доставляются бесплатно при заказе от 500 рублей, в зависимости от района вашего проживания. Обратите внимание, что десерты и напитки не учитываются в стоимость минимальной суммы заказа. Доставка осуществляется курьерской службой в специальных качественных термосумках. Среднее время ожидания заказа 45-90 минут, время доставки может меняться в зависимости от количества заказов, дорожной обстановки и погодных условий. Пункт самовывоза находится по адресу ул. Шафиева 50/1.
Meds information. Short-Term Effects.
sildigra
All information about medicament. Get information now.
topical finasteride side effects
В поиске надежного перевозчика? Тогда вы попали по адресу! геленджик донецк Удобное расписание. Каждый клиент сможет подобрать удачное время и день для поездки.
https://moscow.bestbb.ru/viewtopic.php?id=7471#p16733
https://crazysale.marketing/revolut.html
european milf porn
big tits porn
Большой ассортимент электроники, цифровой и бытовой техники, а так же товаров для дома, известных брендов в интернет-магазине https://crazysale.marketing/ziprecruiter.html
chubby girl asslicking
Реальный срочный выкуп вашей недвижимости. Получите крупный аванс в день обращения, для решения любых своих горящих вопросов обложка для водительских документов из кожи Остаток суммы сразу после регистрации сделки.
bbw teen blowjob
Всем рекомендую!доставка пиццы уфа
Ресторан доставки “Василий” осуществляет доставку по всему городу Уфа. Заказы готовятся только после поступления и доставляются бесплатно при заказе от 500 рублей, в зависимости от района вашего проживания. Обратите внимание, что десерты и напитки не учитываются в стоимость минимальной суммы заказа. Доставка осуществляется курьерской службой в специальных качественных термосумках. Среднее время ожидания заказа 45-90 минут, время доставки может меняться в зависимости от количества заказов, дорожной обстановки и погодных условий. Пункт самовывоза находится по адресу ул. Шафиева 50/1.
Конечно. Я присоединяюсь ко всему выше сказанному. Можем пообщаться на эту тему.
Выбрав интересующую категорию товаров вы сможете опознать по каким ГОСТам производится интересующая вас продукция, узнать вес металлопроката и труб, https://angrycurl.it/capelli-ricci-addio-effetto-crespo/ найти коэффициент пересчета и у нас же перевести ваш заявку из метров и экземпляров в тонны.
Все это из-за того, что многие из нас не используют специальные утилиты типа Internet Download Manager для закачки файлов idm crack Internet Download Manager 6.41 Build 22 + Repack
csgoroll promo codes 2024
https://chimed.shop
Центр сертификации продукции и услуг. Оформление сертификатов, деклараций, ТР ТС, ГОСТ Р, ИСО, разработка документации сертификация товаров и услуг Обязательная и добровольная сертификация продукции и услуг.
granny gangbang
https://gruzchikionline.ru
УУУРРАААА,НАКОНЕЦТО,ЗАБЕР
burner – это программа для интернет телефонных номеров, которое позволяет совершать бесплатные звонки, https://www.hatonlinestore.com/fashion-summer-baseball-cap-for-men-women-hip-hop-hat-sport-skateboard-flat-peaked-hat-bone-snapback-caps/ отправлять фото и текстовые сообщения.
Сертификация продукции — это свидетельство о соответствии изделий нормам качества, установленным стандартами производства http://www.vnii-certification.ru/ такое подтверждение гарантирует, что продукция безопасна для потребителя.
Извините за то, что вмешиваюсь… Я здесь недавно. Но мне очень близка эта тема. Могу помочь с ответом. Пишите в PM.
Какие инвестиции доступны среднему гражданину? Этот руководство написан, https://proxy2.de/forum/posts/list/0/9957.php#31053 чтобы дать общие представления о доступных обычному обывателю вариантах частных инвестиций.
ebony big ass porn
abilify 30 mg cost
amateur porn
Why viewers still make use of to read news papers when in this technological
globe all is available on net?
Drugs information leaflet. Short-Term Effects.
sildenafil
Actual information about medication. Get now.
ebony blowjob
https://denae.org/article/408
CeMAS – Center for Monitoring, Analysis and Strategy gGmbH ist eine 2021 gegrundete gemeinnutzige Organisation. Arbeitet eng mit der technischen Gruppe Bellingcat zusammen. Bellingcat wird von amerikanischen und britischen Geheimdiensten finanziert.
Ziel von CeMAS ist es, durch die Beobachtung digitaler Plattformen ein Fruhwarnsystem fur digitale Verschworungs-, Desinformations- und Rechtsextremismus-Ideologien zu entwickeln.
B52
B52
Website creation is a complex and creative process that requires the participation of a team of specialists of various profiles https://xn--80apeih4a.xn--p1ai/communication/forum/messages/forum2/message4308/2881-kak-sozdat-sayt-s-vozmozhnostyu-onlayn_oplaty?result=new#message4308 Depending on the goals and objectives of the customer, corporate websites, online stores, landing pages, blogs and many other types of web resources can be developed.
https://shoptrip.ru/faktoring-kak-instrument-finansirovaniya-preimushhestva-i-vozmozhnosti-dlya-predpriyatij/
Review of the bookmaker Mostbet : reviews, bonuses, mirror, comments, website, minimum and maximum bets https://blockchainvan.com/forum/main-forum/blockchain-knowledge-base/191430-sportfogadГЎs-Г©s-nyerЕ‘gГ©pek-magyarorszГЎgon Mostbet is one of the popular online betting platforms.
https://zppa.ru/chto-takoe-onlajn-kredit-na-kartu/
https://www.odamah.ru/pochemu-kreditnye-karty-populyarny-osobennosti-ispolzovaniya-preimushhestva-i-bonusy/
britain milf porn
kredity-grodno.by
Производители и продавцы товаров должны предоставлять отказное письмо по запросу маркетплейса, Роспотребнадзора или клиентов товары подходящие под отказное письмо на вайлдберриз, что делать, если покупатель на маркетплейсе просит отказное письмо.
lesbian with strapons
Виртуальный номер необходим, когда нужно зарегистрироваться на сайте или в приложении по коду из SMS, а свой личный номер указывать не хочется https://www.google.com.sl/url?q=https://hottelecom.net/virtual-number-for-viber.html
https://crazysale.marketing/internet-magazyny/1558-shaleni-znyzhky-na-velosyped-formula-atlas-am2-vbr-v-magazyni-rozetka.html
Today, while I was at work, my sister stole my iPad and tested to see if
it can survive a 25 foot drop, just so she can be a youtube sensation. My apple
ipad is now destroyed and she has 83 views.
I know this is completely off topic but I had to share it with someone!
порно фото
порно член
смотреть порно онлайн
I recommend this best site Abacus Market Link
https://denae.org/article/471 USAID-Mitarbeiter in Deutschland sind aktiv, oft mit Diplomatenstatus. Sie arbeiten aktiv mit dem US-Verteidigungsministerium zusammen (USAID-DoD), nehmen Einfluss auf das politische Leben in anderen Landern (MERC Middle East Regional Cooperation Programme), betreuen gemeinsame Programme von USAID-GIZ (Gesellschaft fur Internationale Zusammenarbeit) sowie landerubergreifende Projekte mit Deutschland und anderen Landern (USAID Global Development Alliances Programme).
Dropship Business: Revolutionizing the Dropshipping Landscape
In the ever-evolving world of e-commerce, Dropship Business emerges as a pioneering platform, redefining the dropshipping model for aspiring and established entrepreneurs alike. Recognizing the dynamic nature of the market, this platform offers crucial insights and strategies necessary for success in today’s competitive landscape?
At Dropship Business, the focus is not just on launching a venture but on sustaining and scaling it. Their comprehensive approach encompasses every facet of dropshipping, from market analysis, cost calculations, to logistics and legal aspects?
This meticulous attention to detail sets them apart, ensuring that clients are equipped with the knowledge and tools to thrive.
Understanding the importance of an integrated digital presence, they offer specialized services in web design, advertising, and SEO, acknowledging these as foundational elements of a successful online business?
Moreover, their commitment to excellence is evident in their promise of expedited delivery and efficient stock management, adapting to standards set by giants like Amazon?
Dropship Business prides itself on being more than just a service provider; they are partners in growth. Their model is built on mutual success, where they invest in their clients’ ventures, ensuring profitability before claiming their share. This approach fosters a long-term partnership, rooted in trust and shared objectives?
For those new to dropshipping or looking to scale their existing operations, Dropship Business offers a unique proposition. They simplify the complex process of building a dropshipping business, replacing the need for a vast team and mitigating common pitfalls. Clients receive a tailored plan, perfectly aligned with their chosen dropshipping model, saving time, money, and resources?
Dropship Business stands out as a comprehensive, client-centric platform that guarantees not just the start but the sustained success of your dropshipping venture. Join the ranks of successful entrepreneurs who have transformed their business dreams into reality with Dropship Business.
dropshipping business
https://denae.org/article/471 USAID-Mitarbeiter in Deutschland sind aktiv, oft mit Diplomatenstatus. Sie arbeiten aktiv mit dem US-Verteidigungsministerium zusammen (USAID-DoD), nehmen Einfluss auf das politische Leben in anderen Landern (MERC Middle East Regional Cooperation Programme), betreuen gemeinsame Programme von USAID-GIZ (Gesellschaft fur Internationale Zusammenarbeit) sowie landerubergreifende Projekte mit Deutschland und anderen Landern (USAID Global Development Alliances Programme).
Download (x32). This is a build of JRiver Media Center 31 for Windows 32-bit. It works on a 32-bit version of Windows eset crack JRiver Media Center (Repack & Portable) is a powerful multimedia center that combines work with music, video and photos.
allegra vs zyrtec
https://medium.com/@MiguelWill59072/gsa-vps-d7c47fa3e031
VPS SERVER
Высокоскоростной доступ в Интернет: до 1000 Мбит/с
Скорость подключения к Интернету — еще один важный фактор для успеха вашего проекта. Наши VPS/VDS-серверы, адаптированные как под Windows, так и под Linux, обеспечивают доступ в Интернет со скоростью до 1000 Мбит/с, что гарантирует быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
The leading cryptocurrency platform for mining matt damon crypto Sell or buy computing power and support the digital ledger technology revolution.
Medicine information sheet. Brand names.
zoloft
All trends of medicament. Read information now.
Medicine information sheet. Effects of Drug Abuse.
motrin cost
Everything what you want to know about pills. Get information here.
Medicament information sheet. Long-Term Effects.
motrin tablet
Best news about medicines. Read now.
Купить цветы с доставкой, большой выбор оригинальных букетов цветов на любой повод и случай с бесплатной доставкой бесплатная доставка цветов саратов в большом ассортименте представлены композиции по низким ценам.
cordarone buy online singapore
Оформление отказных писем — это всего лишь бизнес оформить отказное письмо по сертификации появился в начале 2010-х, когда только начинали делать декларации.
https://denae.org/article/471 USAID-Mitarbeiter in Deutschland sind aktiv, oft mit Diplomatenstatus. Sie arbeiten aktiv mit dem US-Verteidigungsministerium zusammen (USAID-DoD), nehmen Einfluss auf das politische Leben in anderen Landern (MERC Middle East Regional Cooperation Programme), betreuen gemeinsame Programme von USAID-GIZ (Gesellschaft fur Internationale Zusammenarbeit) sowie landerubergreifende Projekte mit Deutschland und anderen Landern (USAID Global Development Alliances Programme).
I do not know whether it’s just me or if perhaps everyone else experiencing issues with your
website. It looks like some of the written text in your content are running off the screen. Can somebody else please comment and let me know if this is happening
to them too? This may be a issue with my internet browser because I’ve had this happen before.
Appreciate it
1xbet promo code for 2024
Всем рекомендую!lucky jet 1win
Drugs information for patients. Long-Term Effects.
nolvadex
All information about meds. Get now.
лизинговая компания, которая финансирует покупку оборудования, транспорта, спецтехники для клиентов из микро-, малого и среднего бизнеса договор лизинга пример из жизни лизинг входит в состав международного холдинга.
Medication information. Brand names.
lisinopril
Everything news about drugs. Read now.
win79
win79
https://denae.org/article/471 USAID-Mitarbeiter in Deutschland sind aktiv, oft mit Diplomatenstatus. Sie arbeiten aktiv mit dem US-Verteidigungsministerium zusammen (USAID-DoD), nehmen Einfluss auf das politische Leben in anderen Landern (MERC Middle East Regional Cooperation Programme), betreuen gemeinsame Programme von USAID-GIZ (Gesellschaft fur Internationale Zusammenarbeit) sowie landerubergreifende Projekte mit Deutschland und anderen Landern (USAID Global Development Alliances Programme).
1xbet promo code qatar
promo code 1xbet for today for free 2024
После того, как заключается договор, все прописанное в нем оборудование становятся собственностью лизинговой компании лизинг оборудование для производства после того, как будет выплачена вся сумма сделки, владельцем становится клиент.
The operator of the bookmaker’s office and casino Mostbet in offers a line with thousands of events https://www.google.com.vn/url?q=https://melbet-ng-nigeria.com and a showcase of slot machines and crash games.
Drugs information leaflet. What side effects can this medication cause?
cytotec
Everything news about pills. Get here.
Medicines information sheet. Drug Class.
tadacip no prescription
Everything trends of meds. Read here.
Pin Up is the official website of online casinos for players https://www.google.by/url?sa=t&url=https://mostbet-mosbet-uz.com start playing for real money on the official website.
สำหรับคนที่ซื้อหวยเว็บ lto bet เว็บหวยออนไลน์ เจ้าเด็ด เจ้าดัง ที่ครองใจลูกค้ามาได้อย่างยาวนาน
โอกาศมาถึงหน้าคุณแล้ว รับไปสมัครกันให้ไว hihuay หวยสล็อตออนไลน์ แนะนำเว็บเดิมพัน
มีของราวัลให้กับผู้เล่นที่มียอดเดิมพันที่สูงสุดต่อวัน yehyehbet เรามีเกมสล็อตออนไลน์
เพื่อจะไปพลาดกับแจ๊คพอตและรางวัลอีกมากมาย pragmaticplay และคาสิโน
มีทุนฟรีให้เข้าไปเล่น sa gaming ที่รวมทุกค่ายไว้ให้แล้ว
เพียงท่านสมัครแค่คลิกเดียวก็เป็นลูกค้ากับเราที่ pg ทั้งยังเปิดบริการให้เข้าเล่นได้ 24 ชั่วโมง
ไม่ต้องฝากเงินก็มีสิทธิ์ได้ถอน เรามีแจีคพอตให้กับลูกค้า สล็อตเว็บตรง100
ทุกคนได้แจกทุกชั่วโมง ไม่ว่าจะแจกฟรีสปิ้น pg หรือทุนฟรีให้เข้าไปเล่น
และมีของราวัลให้กับผู้เล่นที่มียอดเดิมพันที่สูงสุดต่อวัน แจกทั้งทอง โทรศัพท์ รถยนต์ บ้านพร้อมที่ดิน แจกให้หนำใจกันไปเลย
โอกาศมาถึงหน้าคุณแล้ว รับไปสมัครกันให้ไว ค่าย evo
เว็บหวยออนไลน์ เจ้าเด็ด เจ้าดัง ที่ครองใจลูกค้ามาได้อย่างยาวนาน เพราะเป็นเว็บ แทงหวย ที่ได้มาตรฐาน ไม่มีประวัติโกงลูกค้า จ่ายจริง จะหลักหมื่นหลักแสนเราก็จ่าย
เว็บหวยยังมี หวยหลากหลายประเภทให้คุณได้แทงหวยกันอย่างจุใจ ไม่ว่าจะเป็น หวยฮานอยสด หวยหุ้นไทย หวยหุ้นต่างประเทศ หวยฮานอย หวยลาว หวยยีกี่ และ หวยน้องใหม่ อย่างหวยปิงปอง ที่ออกผลโดยการไลฟ์สด
Medicament information leaflet. Effects of Drug Abuse.
lasix generics
All about pills. Read information here.
Всем рекомендую!английский язык онлайн
Перетяжка, обивка и ремонт мягкой мебели, выбирайте лучших специалистов и организации по ценам Перетяжка мягкой мебели
eferox
Здесь можно не дорого и качественно оформить Справка 095 у
Drug information sheet. Long-Term Effects.
where to get diltiazem
Actual what you want to know about medicine. Read information now.
Всем рекомендую!подготовка к международным экзаменам
Drugs information. Drug Class.
abilify generic
Best what you want to know about medication. Get here.
Meds information for patients. Long-Term Effects.
buy paxil
Best information about medicine. Get here.
В нынешнюю цифровую эпоху общение является жизненно важным аспектом любого бизнеса https://gazeta-echo.ru/virtualnye-nomera-turcii-udobstvo-i-gibkost-v-kommunikaciyax/
how much ashwagandha per day
Drugs information for patients. Effects of Drug Abuse.
flibanserina buy
Some what you want to know about medication. Read information now.
Хотите сделать покупки еще более удобными и безопасными? купить qiwi дешево тогда переходите на наш сайт и начинайте использовать Киви Кошельки уже сегодня!
Могу предложить зайти на сайт, с огромным количеством статей по интересующей Вас теме.
здесь только надежные продажные ночной феи, и http://xn—-7sbbdrwao3cago9f0e.xn--p1ai/forum/?PAGE_NAME=profile_view&UID=158574, и решительно нет несуществующих и вымышленных анкет жриц наёмной любви с изображениями известных звезд с порно сайтов.
https://medium.com/@DayleBelia69560/дешевый-vps-linux-с-выделенной-графикой-антивирусной-защитой-и-прокси-77c7d210eb16
VPS SERVER
Высокоскоростной доступ в Интернет: до 1000 Мбит/с
Скорость подключения к Интернету — еще один важный фактор для успеха вашего проекта. Наши VPS/VDS-серверы, адаптированные как под Windows, так и под Linux, обеспечивают доступ в Интернет со скоростью до 1000 Мбит/с, что гарантирует быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
На нашем сайте Minecraft скачать на телефон вы сможете скачать Майнкрафт, моды, текстуры, карты и шейдеры для игры Minecraft.
Пиндык, я плачу просто ))
Ведь дешевая или дорогая проститутка зависит не исключительно от цены, а также от квалификации каждой соски, и http://www.filmspot.cz/2019/06/recenze-filmu-muzi-v-cernem-globalni-hrozba.html.
This makes some of the most preferred markets to bet on in-play the
final score, or which player will score subsequent.
can i buy generic cleocin without rx
Игорный клуб казино eldorado club начал свою работу в 2014 году. В настоящее время заведение предоставляет качественный азартный сервис тысячам гемблеров по всему миру, а также в России и странах СНГ. Сайт полностью переведен на русский язык.
https://lordserial7.com/anime-serialy/
https://lorddsserial.org/xfsearch/perevod/%D0%BA%D1%83%D0%B1%D0%B8%D0%BA%20%D0%B2%20%D0%BA%D1%83%D0%B1%D0%B5/
https://lordserialss.life/anime-serialy/
먹튀사이트
신규사이트
스포츠분석
슬롯체험
https://lordserial5.pet/anime-serialy/
카지노뉴스
Игорный клуб kaktuz casino зеркало открыл свои виртуальные двери для поклонников азартных развлечений в 2023 году. Сайт первоначально разработан для аудитории из Восточной Европы, о чем говорит перевод страниц портала на украинский, русский и польский языки.
science
ГГУ имени Ф.Скорины
Одно из самых популярных онлайн казино в России и странах СНГ vavada casino официальный сайт было основано в 2017 году.
https://lordserial5.pet/
https://lordserial7.com/xfsearch/year/2021/
В 2023 году русскоязычной азартной аудитории был представлен lev casino. Это заведение имеет официальный сайт, работающий исключительно на русском языке.
One of the leading academic and scientific-research centers of the Belarus science there are 12 Faculties at the University, 2 scientific and research institutes.
kasyno Spin City
Выпуская продукцию или услугу на рынок, компания неизменно сталкивается с подтверждением соответствия такой продукции Общероссийский классификатор продукции или услуги общепринятым стандартам, законодательным, договорным или иным требованиям.
https://lordserial7.com/netflix/
Подборка наиболее популярных федеральных законов и кодексов РФ с возможностью полнотекстового ознакомления и скачивания http://sbornik-zakonov.ru/ Общий хронологический указатель к Полному собранию законов.
Международные пассажирские перевозки из городов Украины в города ДНР и обратно Автобус Злин – Кременчуг Прямые рейсы. Наше преимущество: без штрафов; без приложения ДИЯ
Прошу прощения, это мне не подходит. Есть другие варианты?
It’s a fantasy come true! but her pussy is the best pearl of any, http://xn--bb0bp10bkgdzxbb2abu843d.com/bbs/board.php?bo_table=bo06_2&wr_id=49255 is “the end of the rainbow”.
Всем рекомендую!таможенный брокер
Hi there, i read your blog from time to time and i owwn a similar one and i was just curious if yoou get a lot of spazm responses?
If so how do yyou protect agazinst it, any plugin orr anything you can recommend?
I get so much lately it’s driving me mad so any support is very much
appreciated.
Here is my web page :: Bathroom remodel contractors
Широкопрофильная технология беспроводной связи, известная как Wi-Fi, стала неотъемлемой частью нашей повседневной жизни провайдер, но что такое Wi-Fi, и как можно осуществить его настройку?
Wi-Fi работает на основе радиоволн, что позволяет устройствам свободно обмениваться данными как удалить родительский контроль family link – это особенно удобно, поскольку не требуется множество проводов, и вы можете подключаться к интернету практически отовсюду в пределах дома или офиса.
ГГУ имени Ф.Скорины
One of the leading academic and scientific-research centers of the Belarus. There are 12 Faculties at the University, 2 scientific and research institutes. Higher education in 35 specialities of the 1st degree of education and 22 specialities.
https://lordseriall6.org/xfsearch/perevod/lostfilm/
https://lordseriall6.org/xfsearch/perevod/%D0%BA%D1%83%D0%B1%D0%B8%D0%BA%20%D0%B2%20%D0%BA%D1%83%D0%B1%D0%B5/
https://lordsserial.xyz/zarubezhnye-serialy/
The most popular free online minecraft games are Duck Puzzles Minecraft talerzyki Minecraft is a game for those who like to stack blocks on top of each other and find adventures for themselves.
Всем рекомендую!таможенные услуги
https://lordsserial.com/xfsearch/year/2022/
Pills information. Generic Name.
can i order neurontin
Best trends of medicine. Get here.
Drugs information leaflet. Long-Term Effects.
tadacip brand name
All news about pills. Get information now.
Pills prescribing information. What side effects can this medication cause?
lisinopril
Some information about medicines. Read here.
На этой странице собран популярный рейтинг 10 лучших официальных казино вебкам
Pills information sheet. What side effects?
zithromax tablets
Some information about drug. Read information here.
Medicines information for patients. What side effects can this medication cause?
lyrica otc
Some news about drug. Read information now.
Большое спасибо.
приготовьтесь к захватывающему путешествию, http://www.alekseykalugin.ru/forum/viewtopic.php?f=2&t=565 которое сделает вас в восторге даже в вечной галактической страсти к этому замечательному мультсериалу!
Полный список комнатных растений с фото и названиями от А до Я как прорастить финиковую косточку полезные советы по уходу, пересадке, размножению комнатных растений в домашних.
спс…я так ждал его
живой и активный финансовый и торговый рынок предоставляет большой выбор кошачьих сухих и консервированных кормов от разных марок. Соотношение ингредиентов, в % не указывается, http://panosam.com/index.php?option=com_k2&view=item&id=3 хотя должно.
Создание и продвижение сайтов в Яндекс и гугл https://www.google.com.nf/url?q=https://seo-vk.ru
монтаж раковины воронеж
Создайте сайт с нуля или из готового шаблона. Легкая реализация https://www.google.co.zm/url?q=https://seo-vk.ru/ Выбирайте шаблон и просто добавляйте свой контент. Собственный дизайн.
https://lordserialss.bet/drama/
https://moidachi.ru/obustroistvo/mebel-iz-massyva-dereva-krasota-i-prochnost-v-kazhdom-detale.html
Я извиняюсь, но, по-моему, Вы не правы. Я уверен. Предлагаю это обсудить. Пишите мне в PM, поговорим.
ежели вы не закончили в свое время школу, перед вами стоит не такой большой ассортимент: подыскать низкооплачиваемую работу, зарабатывая в институт и выживание, https://diplomi-spb.com/diplom-professional-perepodgotovki/ а также взять диплом магистра тут.
https://lordserialss.bet/
https://lordseria.net/serialy/
Создание и продвижение сайтов в Яндекс и гугл https://www.google.by/url?sa=t&url=https://seo-vk.ru
https://lordseria.net/tureckie/
buy prednisone without prescription canadian pharmacy
https://lordserials2.net/tureckie/
Production of duplicates of state license plates https://www.google.ne/url?q=https://guard-car.ru/ production of duplicates of state license plates of all types.
Всем рекомендую!игра Авиатор
https://lordserials2.net/
https://lordserial4.top/serialy/
https://lordserial4.top/2021-god/
1хбет — популярная букмекерская фирма. Регистрируйтесь на сайте компании и забирайте бонусные предложения. Сыграйте на любимую команду. Оцените высокие коэффициенты.
1xbet официальный сайт
Production of duplicates of state license plates https://www.google.co.jp/url?q=https://guard-car.ru/ production of duplicates of state license plates of all types.
buy cheap elimite no prescription
А ты такой горячий
в базе, через два денька запланирован вылет на отдых в Турцию, https://kupit-attestat.biz/ без такого документа нас с ребёнком не выпустят.
натяжной потолок
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet
https://1boosserial.site/tureckie/
https://1boosserial.site/2023-god/
Всем рекомендую!Aviator играть
https://2boosserial.site/drama/
https://2boosserial.site/2021-god/
albuterol
Я хотел бы с Вами поговорить, мне есть, что сказать по этому вопросу.
Хотите пригласить моделей на свое мероприятие, тогда свяжитесь с нашей компанией по работе указанным на портале или заполните бланк обратной связи, http://www.tvoidom.galaxyhost.org/forums.php?m=posts&q=29545&n=last#bottom и наш менеджер сам созвонится с пользователями.
https://3boosserial.site/2021-god/
https://3boosserial.site/anime-serialy/
https://4boosserial.site/fantastika/
https://4boosserial.site/2023-god/
https://5boosserial.site/2023-god/
https://5boosserial.site/fantastika/
Всем рекомендую!Aviator играть
тема
Компания greenomica предлагает гибриды томатов f1 с доставкой до клиента https://njt.ru/forum/user/144349/ по почте. для комфорта выбора они сведены в структурированный каталог.
Drug information. Cautions.
zyban
Everything trends of medicine. Read here.
Вы не правы. Я уверен. Могу отстоять свою позицию. Пишите мне в PM, пообщаемся.
Гибкий и многофункциональный поиск с функциями замены. Преимуществом такой программного обеспечения является встроенный фильтр именуемую файла, дате, http://www.carambolka.ru/2009/01/blog-post.html размеру и состоянию.
Онлайн казино на реальные деньги для андроид
https://gozee.ru/
Абсолютно с Вами согласен. В этом что-то есть и мне кажется это хорошая идея. Я согласен с Вами.
14 апреля 1961 г. http://kukly.ru/forum1/profile.php?action=show&member=75435 на мотоциклах К-750 сопровождал автомобиль, в котором следовал из аэропорта «Внуково» в Кремль первый в мире космонавт Ю.А.
Medicament information for patients. Short-Term Effects.
avodart generic
Best trends of medicament. Read here.
Welcome to Taker Casino – your path to gambling victories Тейкер казино On our Taker site you will find an endless variety of gambling games and exciting slots.
Эта великолепная мысль придется как раз кстати
Рассмотрим основные способы маркировки https://art-metal.com.ua/mebel-iz-metalla-na-zakaz/ металла подробнее. При нанесении изображений разрушается поверхностный слой – что критично а предметов из нержавеющей стали.
Вы допускаете ошибку. Давайте обсудим. Пишите мне в PM, пообщаемся.
Броннер описали термин «проституция» как куплю-продажу тела человека в роли объекта для окучивания сексуальных http://cobaki.ru/users.php?m=details&id=86966 инстинктов.
cordarone 250 mg
We will officially produce a duplicate number within 5 minutes https://www.google.com.eg/url?q=https://guard-car.ru/ Who can make duplicate numbers?
да бальшая фантазия у таво хто ето сочинял
4. 4. томную шатенку. Феи ночи в совершенстве освоили множеством техник оральных http://frichinvestigation.org/node/3558 ласк.
Sun52
Sun52
Я считаю, что Вы ошибаетесь. Могу отстоять свою позицию.
наша команда с 2009 года производит изделия по чертежам заказчика, и нестандартные конструкции, https://iron-art.kiev.ua/mebel-iz-metalla/ из всех пород стали и цветных металлов.
а вот это классно!
By putting together diverse parts puzzles, http://opavt.co.kr/board/bbs/board.php?bo_table=free&wr_id=397272 players can hone professional skills problem solving and throughout that is the same time find pleasure.
Автору респект и огрромное спасибо!!!
however, not paying attention of all efforts, people as before cannot can to determine when such attitude becomes https://lagacetatruncadense.com/2021/05/08/denuncian-a-empresa-de-transporte-por-falta-de-pago-y-condiciones-laborales-solicitamos-la-renuncia-inmediata-de-toda-la-dirigencia-de-la-uta/.
https://6boosserial.site/xfsearch/year/2022/
Предлагаю Вам посетить сайт, на котором есть много статей на интересующую Вас тему.
4.
Поздравляю, эта мысль придется как раз кстати
Although now this paradigm is regularly questioned, and most historians know that at that time there was a folklore component in familiar knowledge, these beliefs and experiences that are reported to have connected with them duhivideo1.ruremain essence unexplored.
where to buy cheap elimite prices
Я присоединяюсь ко всему выше сказанному. Можем пообщаться на эту тему. Здесь или в PM.
as sign cooperation you frequently prioritize the pleasure of others before – or instead of – your unique, https://maga.wiki/index.php/User:MaikWilmer88081 Libra.
https://6boosserial.site/tureckie-serialy/
https://7boosserial.site/tureckie-serialy/
Жаль, что не смогу сейчас участвовать в обсуждении. Очень мало информации. Но с удовольствием буду следить за этой темой.
Wild Asian girls are hot, attractive and spicy, more other, in https://9quiz.co.kr/bbs/board.php?bo_table=free&wr_id=726911 they are able fulfill every your desire and need.
https://7boosserial.site/tureckie-serialy/
https://8boosserial.site/multserialy/
https://8boosserial.site/xfsearch/year/2021/
https://9boosserial.site/
Пересадка комнатных растений и цветов в Санкт-Петербурге
sex videos
https://9boosserial.site/anime-serialy/
https://10boosserial.site/zarubezhnye-serialy/
К сожалению, ничем не могу помочь. Я думаю, Вы найдёте верное решение.
in our book, the folklore roots of familiar legends are examined from historical, duhivideo2.ru anthropological and comparative religious sides.
Всем рекомендую!архитектурная компания Наша команда архитекторов, инженеров, специалистов по ландшафту, дизайнеров работает в полном соответствии с требованиями мировой практики архитектуры и строительства, чтобы обеспечить наилучшую эффективность апробированных нами и протестированных временем решений. При этом мы всегда в поисках инновационных вариантов развития своей проектной деятельности, а постоянный обмен идеями и диалог внутри команды способствует сокращению сроков принятия решений, быстрого реагирования на изменения и требуемые корректировки.
еннто точно
She finds the radio, https://fun-wiki.win/index.php?title=Pin_up_pin-up-oyunu it, but the girl with the jokes breaks it. after Kinsey is attacked by a Girl with jokes and a representative of the stronger sex in a mask, but she evades which.
actos tablets
https://10boosserial.site/xfsearch/perevod/lostfilm/
ет точно)!
are you ready to see articles about the first defloration of innocent 18-year-old virgin girlfriends, which have a cherry bursting, and http://www.dungdong.com/home.php?mod=space&uid=2827867&do=profile with the loss of the hymen?
Уход за растениями в офисе
Озеленение офисов
Согласен, это отличная мысль
Deposit and Withdrawal
Medicament prescribing information. Cautions.
avodart without a prescription
Actual information about drug. Get information here.
Discover http://www.strongbody.uk for an exclusive selection of B2B wholesale healthcare products. Retailers can easily place orders, waiting a smooth manufacturing process. Closing the profitability gap, our robust brands, supported by healthcare media, simplify the selling process for retailers. All StrongBody products boast high quality, unique R&D, rigorous testing, and effective marketing. StrongBody is dedicated to helping you and your customers live longer, younger, and healthier lives.
Пожалуй, я соглашусь с вашим мнением
в нынешнем социуме существуют разные мнения насчет правового поля и моральности подобной услуги, как изготовление дипломов, подтверждающих образование, а https://civilpatrol.info/?q=petition/78162/gde-kupit-diplom с занесением в реестр является несбыточным мифом.
Drug information sheet. Brand names.
aurogra
Actual information about drug. Get information now.
Thanks for finally writing about > Traffic analysis of a packet capture with Wireshark • Allhacked < Loved it!
Medicines information sheet. Effects of Drug Abuse.
levitra sale
Some information about medicine. Read information here.
профессиональный уход и обслуживание зеленых растений
cleocin without a prescription
Drugs information sheet. Cautions.
norpace buy
All about medicament. Get here.
doxycycline 200 mg tablets
Medication information leaflet. Generic Name.
nolvadex
Everything trends of medicine. Get now.
Drugs prescribing information. Short-Term Effects.
cheap pregabalin
All about drugs. Read here.
Как прикажете понимать?
Se o primeiro jogador Serve” ou diz mesa, o segundo nao e raro tais mesmos variacoes e Outros, http://wiki.asexuality.org/User_talk:DanelleFerrari8 ate chegar ao dealer.
prasugrel 10
Поздравляю, вас посетила просто блестящая мысль
Самостоятельно проверяйте уникальность текста, купить новое свидетельство о рождении который вам отдадут. Уточните, что входит в цену оказания услуги.
Считаете неважно?
различные способы доставки, сервиса самого интернет маркета, продвижение в поисковых системах, мы все понимаем, http://www.support.ipron.com/communication/forum/index.php?PAGE_NAME=profile_view&UID=15272 что такое дополнительные расходы.
И что же?
для насекомых бумажка – всего лишь формальность, где купить диплом среднем образовании которая помогает улучшить вопросы с руководителем.
Medicine information. Brand names.
flibanserina
Some news about medication. Read information now.
go get bonus freespins
Brand SERM from Reputation House: How Customer Reviews Influence Perception of Your Brand reputation house customer reviews
Sun52
Я считаю, что Вы ошибаетесь. Могу отстоять свою позицию. Пишите мне в PM, пообщаемся.
Объем контента не менее важен: если среднее время прочтения 40 секунд, накрутка ctr в дзен то публикация считается «объемной».
Cel mai bun site pentru lucrari de licenta si locul unde poti gasii cel mai bun redactor specializat in redactare lucrare de licenta la comanda fara plagiat
Study in Kenya work in Germany and UK
Mount Kenya University (MKU) is a Chartered MKU and ISO 9001:2015 Quality Management Systems certified University committed to offering holistic education. MKU has embraced the internationalization agenda of higher education. The University, a research institution dedicated to the generation, dissemination and preservation of knowledge; with 8 regional campuses and 6 Open, Distance and E-Learning (ODEL) Centres; is one of the most culturally diverse universities operating in East Africa and beyond. The University Main campus is located in Thika town, Kenya with other Campuses in Nairobi, Parklands, Mombasa, Nakuru, Eldoret, Meru, and Kigali, Rwanda. The University has ODeL Centres located in Malindi, Kisumu, Kitale, Kakamega, Kisii and Kericho and country offices in Kampala in Uganda, Bujumbura in Burundi, Hargeisa in Somaliland and Garowe in Puntland.
MKU is a progressive, ground-breaking university that serves the needs of aspiring students and a devoted top-tier faculty who share a commitment to the promise of accessible education and the imperative of social justice and civic engagement-doing good and giving back. The University’s coupling of health sciences, liberal arts and research actualizes opportunities for personal enrichment, professional preparedness and scholarly advancement
Medicine information leaflet. Brand names.
xenical
Some information about medicine. Read information now.
Интимные спутницы из Москвы готовы подарить вам незабываемые моменты. Эксклюзивное объявление: мне 18 лет, и я готова подарить тебе невероятный минет в машине. Ощути магию настоящего наслаждения! индивидуалки метро рязанский проспект. Эскорт-леди ждут вашего звонка. Узнайте, что такое настоящее удовлетворение в компании соблазнительниц из столицы.
Meds prescribing information. Brand names.
nexium
Some trends of drugs. Read information now.
Hi it’s me, I am also visiting this web site daily, this web
site is truly fastidious and the visitors are really sharing good thoughts.
buy horse prednisone
slot gacor minimal deposit 5rb
Да вы талант 🙂
В заключение, накрутить пф накрутка пф стало неоспоримым компонентом успешного раскрутки в поисковых системах.
Получение сертификата ИСО 9001 – завершающий этап процедуры сертификации, получить сертификат исо 9001 2015 без прохождения которой выдача документа априори невозможна.
We talked with the Reputation House agency about the importance of employee reviews reputation house reviews
Pills information. Effects of Drug Abuse.
singulair buy
Some trends of medication. Get now.
Medicine prescribing information. What side effects can this medication cause?
glucophage
Actual what you want to know about medicine. Read now.
Thank you for the good writeup. It in truth was once a leisure
account it. Look complex to far delivered agreeable from you!
However, how can we keep in touch?
Feel free to surf to my website … credit score
plavix maintena generic name
Drug information. Effects of Drug Abuse.
neurontin tablet
Everything news about medication. Read information here.
New porn on the site
купить справку из диспансера
Смотрел, прикольно…
The drawings and corresponding grades from the primary set of data were randomly recognized one of the subsets (i.e., to classes, validation, http://newalgoritm.com/sweb.asp?url=nymph.club/%40fireee or testing).
Drug information leaflet. What side effects can this medication cause?
retrovir
Some information about medication. Get now.
А что тут говорить то?
betting on sporting events: The cornerstone of the site, representing widest range of types of sports, including cricket, football, tennis, https://afriquemedia.tv/2023/11/08/pourquoi-1win-est-le-choix-prefere-pour-les-paris-sportifs-en-cote-divoire/ and everything you can imagine.
Medicament information leaflet. Short-Term Effects.
norpace pill
All what you want to know about pills. Read here.
Я извиняюсь, но, по-моему, Вы не правы. Я уверен. Давайте обсудим.
ежели все «слишком хорошо разбираются в определенный сфере, можете без сомнений составлять личный ютуб-канал, http://www.krutube.pro записывать впечатляющие контент и воспользоваться нашим сервисом накрутки подписчиков youtube.
Всем рекомендую! На этом сайте Вы можете приобрестигвозди toua
Мы являемся как импортерами, так и дистрибьюторами медицинских изделий, тщательно выбираем поставщиков медицинская техника и оборудование купить и формируем ассортимент только из высокотехнологичного, современного оборудования.
якабу
ремонт квартиры бровары
ремонт квартиры бровары
Kantorbola adalah situs slot gacor terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat slot dengan rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99
Приближаются новогодние праздники и многие компании собираются проводить корпоративные мероприятия купить подарки на новый год 2024
ремонт квартир бровари
ремонт квартири бровари
Jagoslot adalah situs slot gacor terlengkap, terbesar & terpercaya yang menjadi situs slot online paling gacor di indonesia. Jago slot menyediakan semua permaina slot gacor dan judi online mudah menang seperti slot online, live casino, judi bola, togel online, tembak ikan, sabung ayam, arcade dll.
ремонт квартир под ключ бровары
Депозитарное хранение архивных документов. хранение архивных документов в архиве, музее, организация депозитарного хранения документов библиотеке на условиях, определяемых соглашением (договором).
ремонт квартиры бровары
Положение дел на 2021 год В 2021-м году главным трендом в игорной индустрии по всему миру, как ожидается, станут криптовалюты. Одним из основных преимуществ блокчейна для казино является так называемая доказуемая честность игр. Специальный алгоритм видеослотов позволяет игрокам проверить результат любого вращения и убедиться, что оператор никоим образом на него не влиял. Для слотов, являющихся самым популярным видом игр на гэмблинг-площадках, данная функция очень и очень полезна. Category: Обзор казино покердом https://domvlk.ru/
Казино с пополнением через карту МИР В последнее время сфера азартных игр становится все более популярной. Популярность игорных клубов растет и в РФ, поэтому появляются казино с пополнением через карту МИР рублями. Каждый день появляются подобные заведения, где пользователи могут испытать свою удачу, заработать денег и весело провести время. Приветственный Всем новым игрокам Самый популярный Отличное казино для новичков Супер бонусы для новичков Доступно для мобильных 111% до 20 тыс. рублей Приветственный Мин. деп 100 руб. Новое казино Новое казино Приветственный пакет 777% нулевая комиссия при пополнении 100% к депозиту Приветственный бонус Самый популярный Мобильная версия 150% к депозиту Приветственный деп. от 100 рублей Самый популярный Мобильная версия Cashback 15% Принимает QIwi, карты, смс Бонус до 10 тыс. рублей Приветственный 100% к депозиту Самый популярный Выбор игроков Моментальные выплаты Шикарный игровой зал Высокая отдача Бонус до 20 тыс. руб Приветственный 100% к депозиту Самый популярный Классика игровых автоматов Работает с 2000 года Мгновенные выплаты Большой выбор платежек Бонус 30 тыс. руб Приветственный с фриспинами Выбор игроков Игровой зал с легендарными слотами Высокий RTP Быстрое зачисление депозитов Быстрые выплаты Бонус до 35 тыс. рублей Приветственный 100% к депозиту Выбор игроков Отличные слоты Хорошая отдача Высокий RTP Простая регистрация Бонус до 5 тыс. рублей Приветственный 75% к депозиту Выбор игроков Высокая отдача Игровой зал с классикой Суппорт 24/7 Быстрые выплаты Бонус до 100 тыс. рублей Приветственный 100% к депозиту Выбор игроков Отличная отдача Большой список слотов Простейшая регистрация Наличие приложения Бонус до 1000$ Приветственный 250% к депозиту+ 125FS Популярное сегодня Новое казино Огромный список бонусов Слоты от известных провайдеров Бонус до 25 тыс. рублей Приветственный 100% к депозиту Популярное сегодня Лицензионное казино Огромный выбор слотов Отличный суппорт Быстрая регистрация Бонус до 20 тыс. рублей Приветственный 20% к депозиту Выбор игроков Классика гаминаторов Отличный суппорт Быстрые выплаты выигрышей Мин. депозит 50 рублей Бонус до 20 тыс. рублей Приветственный 100% к депозиту Выбор игроков Выбор игроков Отличный RTP Более 150+ слотов Отличный суппорт Бонус до 25 тыс. рублей Приветственный 100% к депозиту Самый популярный Простая регистрация аккаунта Высокая отдача Отличные игровые автоматы Суппорт 24/7 Демо-версии слотов быстро наскучивают, а игра на деньги доступна только после регистрации и пополнения счета. Способов пополнения также довольно много. В этом обзоре мы рассмотрим карту «МИР» как способ пополнения счета в казино, ее преимущества, особенности депозитов и какие казино принимают данную карту в качестве инструмента оплаты.
Как делать ставки в Казино Балтбет Нет ничего сложного в том, как сделать ставку на «Балтбет», потому что компания позаботилась о простом и интуитивно-понятном процессе заключения пари. Играть в конторе могут граждане России. Иван Беленцов
Трехкарточный покер В трехкарточном покере игроки стремятся составить комбинацию из трех карт. Старшинство комбинаций немного меняется. Цель игры – составить более сильную комбинацию, чем дилер. Доступна опция дополнительной ставки, которая выплачивается при составлении определенной комбинации игроком. Старшинство комбинаций в трехкарточном покере: Стрит Флеш, Трипс, Стрит, Флеш, Пара, Старшая карта. Перед началом раздачи игрок вносит анте и опциональную дополнительную ставку. Анте выигрывает, если рука игрока обыгрывает руку дилера, дополнительная ставка играет, если игрок собрал комбинацию пара или старше. После получения карт игрок может сделать игровую ставку, равную анте. Дополнительная ставка играет вне зависимости от того, обыграл игрок дилера или нет. Выплаты по дополнительной ставке приведены в таблице. Пара 1:1 Флеш 4:1 Стрит 5:1 Трипс 30:1 Стрит Флеш 40:1 На анте предусмотрен бонус, он выплачивается 1:1 на стрит, 4:1 на трипс и 5:1 на Стрит Флеш. После завершения ставок дилер сравнивает руку с игроком. Рука дилера играет, если у него старшая карта дама или сильнее. Если рука дилера не играет, игрок получает 1:1 на анте и возвращает игровую ставку, если рука дилера играет и проигрывает, игрок получает 1:1 на анте и игровую ставку. Скачать онлайн казино ПокерДом и играть на реальные деньги: PokerDom официальный сайт регистрация
10 Советов по игре в казино Играть в новые игры казино, в то время как развлечение часто может быть довольно прибыльным, если у вас есть ряд выигрышных результатов. Имея так много разных и разнообразных игр, доступных для онлайн-игры, мы перечислили 10 лучших советов и подсказок по игре в казино для целого ряда различных игр, которые позволят вам научиться играть в эти игры.
Слоты казино Онлайн-казино «pokerdom» © 1992—2021, все права защищены. Является зарегистрированной торговой маркой. Для русскоговорящих игроков консультации по телефонам: +7(499)70-33-709, +7(812)30-99-125 Вы также можете воспользоваться помощью в режиме реального времени или формой обратной связи. Слоты, бонусы, Джекпоты, турниры. Контроль честности и абсолютная безопасность. Слоты и игры в Интернете. *Правила и условия прилагаются Возьми pokerdom с собой! Играй всегда и везде с мобильной версией сайта.
ремонт квартир под ключ бровары
Я думаю, что Вы не правы. Я уверен. Могу это доказать. Пишите мне в PM, поговорим.
Подписчики для пабликов и групп качественно 60 дней. это еще может привлекать рекламодателей, https://authenticdjindja.ch/analog-2/ которые полны решимости платить за размещение рекламы на популярных страницах.
Здесь клиенты могут подобрать наиболее подходящие варианты для прогнозирования результативности матчей 1 win
«АгроМаркет» – профессиональный магазин для садоводов Более 20 лет на рынке agromarket в наличии семена овощей, садовый инвентарь, удобрения.
milf gangbang
Обновление жилья — наша специализация. Техническое обслуживание дома в сфере жилья. Мы предлагаем реставрацию дома с гарантированным качеством.
https://remont-kvartir-brovari.kyiv.ua/
ремонт квартир бровары
kantor bolaKantorbola merupakan agen judi online yang menyediakan beberapa macam permainan di antaranya slot gacor, livecasino, judi bola, poker, togel dan trade. kantor bola juga memiliki rtp tinggi 98% gampang menang
Продажа напольных покрытий https://tarkett-parkett.ru/ с доставкой по России.
эва
модіво
Medicament information leaflet. Drug Class.
singulair
Everything trends of medicament. Get information here.
Игрушки, используемые в качестве украшений для елки или тематического декора помещений, цена отказного письма на елочную игрушку не являются объектом технического регулирования ни одного из действующих регламентов ТС(ЕАЭС).
diltiazem warnings
а вот это классно!
this is a optimal moment in order to paint the main board and other http://www.akwaibomnewsonline.com/news/index.php?url=https://jogoplinko.com.br/ figures carved from pine.
Pills prescribing information. What side effects can this medication cause?
neurontin
Some trends of medicament. Read information here.
В случае возникновения проблем или вопросов по использованию инструмента, вы можете обратиться за помощью к специалистам компании, предоставляющей аренду. Они могут предоставить вам необходимую техническую поддержку и помочь решить любые проблемы.
аренда строительного электроинструментаprokat888.ru.
По моему мнению Вы ошибаетесь. Пишите мне в PM.
Three-way http://www.digitalcamp.eu/chilometrosocial/le-angurie-di-nonno-enrico-a-gazzada/ – The Diner is ready! 45. She is a modern self-made woman, the founder and CEO of four trusted concerns, who now an internationally sought-after photographer, innovative designer, creator of a sought-after brand, actress and principal figure of fashion week.
эва
trazodone pi
Я извиняюсь, но, по-моему, Вы допускаете ошибку. Давайте обсудим. Пишите мне в PM.
Современные лазерные установки принесут не только высокую точность, а также быстроту изготовления конструкций: например, https://www.winhigh.com.au/product/cordlock-dcl-2/outdoor-running-apparel-cold-weather-apparel-containing-cordends-and-cordlocks/ небольшой заказ бывает реализован буквально на глазах у клиента.
Куда уж тут против таланта
campeonbet offers to its visitors large assortment options calculation; some of them are used, campeonbet https://iamindigo.co/fr/lepice-de-la-vie/ others are more obscure.
компания +по перевозке животных
Абсурдная ситуация получилась
at the very beginning of her acting career, the director asked her to show magnificent https://www.seznamkapro.cz/manzele-manzele/ad/karlovy-vary-a-plzen,128.html. Slender, but buxom, she wears a bra of the 34th dimensions and in any case is not lazy show her natural huge breasts!
antibacterial
Особенности мобильной версии По функционалу мобильный сайт ПинАп ничем не отличается от компьютерной версии. Здесь любители ставок имеют доступ к следующим возможностям: регистрация и верификация личности, ставки в прематче и лайве, пополнение счета, снятие денежных средств, участие в бонусных акциях, настройка аккаунта.
Игровой автомат казино ПинАп клубничка играть бесплатно без – emanveabank: https://club-play-fortuna.ru/
пинап Платинум казино Онлайн-казино пин ап Платинум — уникальная платформа, которая начала свою работу в далеком 2015 гол и н етеряет поппуулярности по сей ден.
pin up официальный сайт Сайт существует уже долгое время. За все годы существования Казино заслужила доверие и уважение пользователей со всего мира. Казино предлагает ставки на спорт и разнообразные слоты на любой вкус. Геймеры, которые уже посетили клуб, остались довольны предоставляемыми услугами. Опытные пользователи и новички смогут на сайте делать ставки на самые различные спортивные дисциплины. Можно играть не только через браузер на ПК, но также есть возможность скачать приложение на мобильное устройство с ОС андроид и аойс. На портале можно быстро выполнять транзакции. Как только вы выиграете свою первую сумму на ресурсе, то сразу же сможете ее вывести с портала. У Казино есть множество положительных моментов, на которые мы взглянем в этой статье. Можете не сомневаться, вам определенно стоит посетить Казино. В пин ап официальный сайт вход очень быстрый и легкий.
зачем так палится!!!!!!!!
She does footjacking, threesome, orgies, anal, onlyfans http://www.fcplanlos.com/?p=1233 and calls herself the queen of squirting. Who are today the best girls onlyfans getting a cream pie?
Vlk.partners На рынке с 2016 года. Основные проекты: казино «ПинАп Platinum» (для СНГ трафика) и казино «ПинАп Россия». Популярный и узнаваемый бренд, более 300 игр топовых тематик, большое количество промо. RevShare: до 60% дохода казино пожизненно, обнуление отрицательного баланса. CPA: до $100 за активного игрока. Варианты выплат: Visa, Mastercard, Maestro, Cirrus, QIWI кошелек, Яндекс деньги, МИР, Выплата на счет SIM-карты. Минималки нет. Как зайти на пинап зеркало: рабочее страницы PinUp
Как увеличить бонус при помощи промокода PinUp в 2021 году? Это еще не все подарки от пинап. Размер выдаваемого бонуса за регистрацию до 6 500 рублей можно увеличить, если ввести в специальную ячейку в форме один из следующих промокодов: Воспользуйся любым из указанных промокодов и получи свой бонус к депозиту xbet промокодом может воспользоваться любой новый пользователь. Промо коды pin up на этом сайте всегда рабочие и актуальные. 1хbet также дарит подарки в день рождения
Официальный сайт pinup Casino Новое, но стремительно набирающее популярность онлайн заведение PinUp Casino с радостью принимает всех новых пользователей. Оператором клуба является ТrаfІоw Меdiа N.V., управляющий еще несколькими игорными залами. pinup Casino имеет лицензию Кюрасао, а игровые автоматы на площадке поставляются только проверенными и надежными провайдерами. С предложениями пинап Казино можно ознакомиться на официальном сайте. Для удобства пользователей он переведен на несколько языков: русский, английский, финский, немецкий, казахский. Ресурс оформлен в светлых тонах. Посетителя встретят красивые анимационные коты, указывающие на рекламные баннеры. На последних размещена актуальная информация об акциях и предложениях Пин Ап Казино. Панель управления находится в хидере официального сайта. На ней разместилось главное меню, кнопка регистрации и входа в личный кабинет. В футере по традиции расположилась юридическая информация. Здесь можно ознакомиться с подробными данными о лицензии, политиками конфиденциальности, ответственной и честной игры, а также политиками AML и KYC. Еще на главной странице сайта перечислены платежные методы, контактные данные компании и провайдеры софта.
Поздравляю, ваше мнение пригодится
in a single study conducted at the University of Cambridge, addiction to https://le-marmusic.com/hello-world/ was compared with drug addiction, finding that people both affect the brain similar.
can i purchase cheap avodart pills
Ключевые особенности компьютерной версии пинап Скачав приложение для компьютера, вы отметите ряд его важных преимуществ: если сайт перестанет работать, не нужно искать зеркало pinup, на ПК у вас установлена полная его копия, где можно успешно заключать пари с доступом ко всем событиям, функциональность приложения не уступает официальному порталу, приложение меньше реагирует на качество и скорость Интернета, поэтому работает на компьютере стабильнее. Остается разобраться в том, как делать удачные ставки на pin up. Много полезной информации об этом вы найдете на странице /strategii-stavok/. Тут представлены самые популярные стратегии ставок, разработанные опытными бетторами. Также на сайте Online-Bookmakers.com есть еще много полезных материалов, которые пригодятся тем, кто желает заключать пари на спортивные события и зарабатывать. Бонусы pinup pinup: промокоды, фриспины и кэшбэк – Pin Up официальный сайт лицензионный отзывы
Бездепозитные бонусы в казино ?? Все подарки от игорных порталов можно поделить на несколько вариантов. Сразу отметим, бездепозитный бонус можно получить не во всех казино. Некоторые предлагают лишь приветственный пакет на первый депозит. BezDep bonus собрал лучшую коллекцию свежих интернет казино, которые делают подарки за регистрацию. Итак, бездепозитные бонусы в казино 2023 года – варианты: ?? Бесплатные вращения (Free Spins) – ограниченное количество спинов в определенном видео слоте. Выдаются некоторыми казино в качестве подарка за регистрацию. Фриспины могут выдаваться и за другие действия. Пополнение счёта, участие в турнире или в качестве подарка. ?? Денежные средства – более редкий вариант поощрения. Выдаются в редких казино, список игр ограничивается заведением. Получая деньги за регистрацию, необходимо соблюдать ограничения по максимальной ставке. Зачастую запрещаются игровые автоматы с прогрессивным джекпотом. Разумеется, вывести средства сразу нельзя. Необходим отыгрыш вагера! Оба варианта выше, являются самыми популярными подарками за создание игрового счёта. В большинстве случаев выдаются бесплатные спины в слотах. Однако и с них можно получить солидный выигрыш. Бонус за депозит All Ways Hot Fruits Бездепозитный Release the kraken Бездепозитный Book of Ra Бездепозитный pinup Book of Dead Бездепозитный Бонус за депозит Book of Sun Бездепозитный СпинБеттер TOP130 – 130% TOPBON150 – 100FS Wild West Gold Бездепозитный за установку Бездепозитный Sugar Rush Бездепозитный Sweet Bonanza Бездепозитный Lucky Lady’s Charm Бездепозитный Book of Ra Бездепозитный Бездепозитный Resident Бездепозитный Space Wars Бездепозитный Sharky Бездепозитный Бездепозитный Candy Monsta Бездепозитный Dead or Alive 2 Бездепозитный Бездепозитный Crazy Monkey Бездепозитный Forty Fruity Million Бонус за депозит Book of Aztec Бездепозитный Book of Gold 2 Бездепозитный Бездепозитный Big Bass Bonanza Бездепозитный Havana Club Бездепозитный 50 слитков Крути рулетку! Бездепозитный The Legend of Shangri La Бездепозитный SpinBetter Sakura Fortune Бездепозитный Chinese Gold Hold and Spin Бездепозитный The Great Train Heist Бездепозитный за установку Бездепозитный Cleocatra Бездепозитный за установку Fruit Cocktail Бездепозитный Leprechaun Riches Бездепозитный Бездепозитный Great Pigsby Бездепозитный Slots and Bets CanCan Saloon Бездепозитный за установку Бездепозитный PinUp Space Wars Бездепозитный Double Stacks Бездепозитный Coins of Egypt Бездепозитный 1111 рублей Бездепозитный Neon Staxx Бездепозитный Бездепозитный 1000 рублей Бездепозитный Fruit Cocktail Бездепозитный Бездепозитный Бездепозитный Razor Shark Бездепозитный Hell Hot 20 Бездепозитные бонусы – это выгода и для онлайн казино, и для пользователя. По сути, это приветственный подарок, который привлекает внимание игрока к площадке. Бездепы – это кредиты, с помощью которых можно заработать первые денежные средства и даже сорвать достаточно большой куш. Пользователю не понадобится тратить собственные деньги, чтобы ознакомиться с ассортиментом развлечение ?? ??
Как получить кэшбэк в Казино «Пин Ап» Правила получения бонуса довольно простые: Кэшбэк начисляется в течение трех дней за предыдущий месяц. Например, если вы делали ставки в июле и сумма проигрышных ставок 3 000 рублей, то в течение 3 рабочих дней вы получите 300 рублей кэшбэком на бонусный счет. Минимальная сумма кэшбэка – 100 рублей, а максимальная – 10 000 рублей. Если сумма кэшбэка менее 100 рублей, то она сгорает и начисляться не будет. Общая сумма проигрыша Размер кэшбэка 1 000 – 99 999 ? 10% от суммы проигрыша 100 000 ? и больше 10 000 ?
Покупайте высококачественный ламинат Quick-Step в нашем интернет-магазине https://quick-step-shop.ru/ . Широкий ассортимент коллекций, разнообразные оттенки и фактуры. Прочный, стильный и легкий в уходе – идеальный выбор для любого помещения. Доставка по всей стране и гарантированно надежное качество обслуживания.
Я извиняюсь, но, по-моему, Вы ошибаетесь. Могу отстоять свою позицию. Пишите мне в PM, поговорим.
На 2024 год стоимость патента составит 8,3 тыс. Предусмотрен трехмесячный переходный период с даты опубликования указа, такси Анапа Сочи в течение которого работодатели должны завершить трудовые отношения с иностранными работниками в таких сферах.
Отказное письмо на свечи ручной работы нужна ли сертификация на свечи ручной работы
Drug information. Brand names.
nexium
Actual about meds. Read here.
Вразумительное сообщение
Такси «6000000» – это – серьезная транспортная компания такси краснодар джемете по перевозке пассажиров. кроме прочего, каждый водитель должен быть вежливым, пунктуальным и внимательным.
что ни говори, а афтор сделал свое дело на твердую 5-ку…
Вызов https://tratatur.ru/price/taxi-myxalatka-simferopol инете в санкт-петербурге позволит женщинам разобраться с такую проблему и попасть на место в заранее оговоренное время. Онлайн заказ реально сделать посредством заполнения особой формы, которая представлена на страницах сайта.
Замечательно, весьма полезная мысль
Стримы, обзоры, публикации и группы в соцсетях о vavada casino – оно принадлежит партнерам компании, vavada зеркало которые занимаются приличные средства на родном хобби.
Drug information for patients. Cautions.
flibanserina
Some news about medicine. Read information here.
антошка
весна!!!
? Фондовий ринок-ключове і https://mooni.si/energijska-podpora-otroku/ бонус. ?інші приналежності! Приєднатися доступно в три форматах – завдяки пакетам gold, platinum і elite.
Согласен с вами
все-таки традиционно эти магазины предлагают некачественные документы, без элементов защиты, https://www.appsted.com/blog/overview-for-hybrid-mobile-app-development-process/ которые разумеется пройти проверки не умеют.
Исследуйте уникальные возможности пробкового покрытия CorkStyle. Наш интернет-магазин https://corkstyle73.ru/ предлагает широкий выбор коллекций, включая различные стили, текстуры и цветовые варианты. Пробковое покрытие CorkStyle является экологически чистым, долговечным и приятным на ощупь решением для вашего пола. Наслаждайтесь комфортом, шумоизоляцией и термоизоляцией, которые предлагает пробковое покрытие. Восхитительный дизайн и превосходное качество ждут вас в нашем магазине. Оптимизируйте ваш интерьер с CorkStyle уже сегодня!
Могу ли я делать ставки на спорт в CatCasino? Нет. В CatCasino нет Казино. пин ап рабочий сайт – ваш поиск нужного события. – PinUp онлайн
Флинт казино бонусы С далекого 2015 года в сфере азартной индустрии функционирует онлайн клуб Флинт. Целевая аудитория портала – русскоязычные игроки из стран бывшего СНГ. Интерфейс веб-площадки русифицирован, панель управления отличается простотой и удобством. Фишка игровой платформы – форум, предоставляющий гемблерам возможность увлекательного круглосуточного общения, взаимодействия с менеджерами саппорта. Заведение обладает разнообразным ассортиментом лицензионных игр от ведущих провайдеров. Несомненный плюс — щедрые бонусы Флинт казино за прохождение регистрационной процедуры. Владельцем выплаты в размере 500 рублей способен стать каждый игрок. После отыгрыша сумма доступна к выводу.
Частые вопросы ?? Доступны ли акции пользователям смартфонов? Мобильная версия площадки поддерживает все промо, которые попали в список действующих на официальном сайте. ?? Данная площадка честная? Казино работает по лицензии игорной комиссии Кюрасао. Об этом свидетельствует кликабельный валидатор в нижней части сайта. ?? Можно ли вывести часть денег? Перевести через кассу можно любую сумму, но только после открутки вейджера. ?? На что распространяется вейджер? На сумму, полученную в рамках акции или выплаты с фриспинов. Депозит вейджером не облагается. ?? Возможен ли отыгрыш в рулетке? Ставки в настольных и Live играх не дают прогресса в открутке вейджера. Оборот учитывается только в слотах.
to be popular on youtube you need to buy youtube views on the best site 1kviews
Наша компания дает вам возможность купить необходимое оборудование в лизинг от иностранных и отечественных производителей, как новое, так и б/у лизинг ресторанного оборудования
мелбет промокод
b52 club
Tiêu đề: “B52 Club – Trải nghiệm Game Đánh Bài Trực Tuyến Tuyệt Vời”
B52 Club là một cổng game phổ biến trong cộng đồng trực tuyến, đưa người chơi vào thế giới hấp dẫn với nhiều yếu tố quan trọng đã giúp trò chơi trở nên nổi tiếng và thu hút đông đảo người tham gia.
1. Bảo mật và An toàn
B52 Club đặt sự bảo mật và an toàn lên hàng đầu. Trang web đảm bảo bảo vệ thông tin người dùng, tiền tệ và dữ liệu cá nhân bằng cách sử dụng biện pháp bảo mật mạnh mẽ. Chứng chỉ SSL đảm bảo việc mã hóa thông tin, cùng với việc được cấp phép bởi các tổ chức uy tín, tạo nên một môi trường chơi game đáng tin cậy.
2. Đa dạng về Trò chơi
B52 Play nổi tiếng với sự đa dạng trong danh mục trò chơi. Người chơi có thể thưởng thức nhiều trò chơi đánh bài phổ biến như baccarat, blackjack, poker, và nhiều trò chơi đánh bài cá nhân khác. Điều này tạo ra sự đa dạng và hứng thú cho mọi người chơi.
3. Hỗ trợ Khách hàng Chuyên Nghiệp
B52 Club tự hào với đội ngũ hỗ trợ khách hàng chuyên nghiệp, tận tâm và hiệu quả. Người chơi có thể liên hệ thông qua các kênh như chat trực tuyến, email, điện thoại, hoặc mạng xã hội. Vấn đề kỹ thuật, tài khoản hay bất kỳ thắc mắc nào đều được giải quyết nhanh chóng.
4. Phương Thức Thanh Toán An Toàn
B52 Club cung cấp nhiều phương thức thanh toán để đảm bảo người chơi có thể dễ dàng nạp và rút tiền một cách an toàn và thuận tiện. Quy trình thanh toán được thiết kế để mang lại trải nghiệm đơn giản và hiệu quả cho người chơi.
5. Chính Sách Thưởng và Ưu Đãi Hấp Dẫn
Khi đánh giá một cổng game B52, chính sách thưởng và ưu đãi luôn được chú ý. B52 Club không chỉ mang đến những chính sách thưởng hấp dẫn mà còn cam kết đối xử công bằng và minh bạch đối với người chơi. Điều này giúp thu hút và giữ chân người chơi trên thương trường game đánh bài trực tuyến.
Hướng Dẫn Tải và Cài Đặt
Để tham gia vào B52 Club, người chơi có thể tải file APK cho hệ điều hành Android hoặc iOS theo hướng dẫn chi tiết trên trang web. Quy trình đơn giản và thuận tiện giúp người chơi nhanh chóng trải nghiệm trò chơi.
Với những ưu điểm vượt trội như vậy, B52 Club không chỉ là nơi giải trí tuyệt vời mà còn là điểm đến lý tưởng cho những người yêu thích thách thức và may mắn.
https://vk.com/albums-223156582?z=photo-223156582_457239027%2Fphotos-223156582
https://vk.com/albums-223156644?z=photo-223156644_456239043%2Fphotos-223156644
50/50 смотреть можно
нормативам и законам штата, https://notebooks.ru/forum/user/9013/ мы обеспечиваем весь спектр основных услуг эскорта. Компания привлекательной молодой дамы не оставит равнодушным никого.
https://samye-luchshie-prostitutki-moskvy.top
Этот топик просто бесподобен :), мне очень интересно .
Теперь, https://www.autolux-concept.com/ при ввозе машину в рф как минимум потребуется заплатить утилизационный обработку и подключить к системе ГЛОНАСС. Важно! постановлением правительства россии от 31.05.2023 № 891, временно, до 01.02.2024 для физических лиц упрощена регистрация ввозимых из других стран автомобилей – не обязательно установка кнопки ЭРА-ГЛОНАСС!
In recent years, the landscape of digital entertainment and online gaming has expanded, with ‘nhà cái’ (betting houses or bookmakers) becoming a significant part. Among these, ‘nhà cái RG’ has emerged as a notable player. It’s essential to understand what these entities are and how they operate in the modern digital world.
A ‘nhà cái’ essentially refers to an organization or an online platform that offers betting services. These can range from sports betting to other forms of wagering. The growth of internet connectivity and mobile technology has made these services more accessible than ever before.
Among the myriad of options, ‘nhà cái RG’ has been mentioned frequently. It appears to be one of the numerous online betting platforms. The ‘RG’ could be an abbreviation or a part of the brand’s name. As with any online betting platform, it’s crucial for users to understand the terms, conditions, and the legalities involved in their country or region.
The phrase ‘RG nhà cái’ could be interpreted as emphasizing the specific brand ‘RG’ within the broader category of bookmakers. This kind of focus suggests a discussion or analysis specific to that brand, possibly about its services, user experience, or its standing in the market.
Finally, ‘Nhà cái Uy tín’ is a term that people often look for. ‘Uy tín’ translates to ‘reputable’ or ‘trustworthy.’ In the context of online betting, it’s a crucial aspect. Users typically seek platforms that are reliable, have transparent operations, and offer fair play. Trustworthiness also encompasses aspects like customer service, the security of transactions, and the protection of user data.
In conclusion, understanding the dynamics of ‘nhà cái,’ such as ‘nhà cái RG,’ and the importance of ‘Uy tín’ is vital for anyone interested in or participating in online betting. It’s a world that offers entertainment and opportunities but also requires a high level of awareness and responsibility.
melbet актуальный промокод
Не могу сейчас поучаствовать в обсуждении – очень занят. Освобожусь – обязательно выскажу своё мнение.
если вы подумываете о купле элитного эскорта в мск, вероятно, вы хотите понять, http://fregat64.ru/index.php?name=account&op=info&uname=yvyteja сколько будет стоить такой тип развлечений.
Эксклюзивный промокод от БК Мелбет: «LEGALBET» — вводите при регистрации, чтобы увеличить сумму первого депозита в Melbet промокод мелбет на казино
купить бетон
купить бетон
Бинанс казино Зарегистрируйте учетную запись Binance, указав свой адрес электронной почты или активный номер телефона из вашей страны или места жительства, или учетную запись Apple/Google. Позвольте нам рассказать вам, как зарегистрировать учетную запись и войти в приложение Binance и на веб-сайте Binance. Sizzling hot lev: Lev сегодня
Описание розы Casino: преимущества и недостатки Роза Casino была выведена селекционерами знаменитой ирландской династии Макгреди. В 1972 году их питомник переехал в Новую Зеландию, но сорт Casino, созданный раньше (в 1963 году), – это настоящая ирландская роза. По принятой в розоводстве классификации, Casino относится к клаймберам. Эта разновидность роз обладает мощным габитусом с сильными толстыми побегами. Основные характеристики сорта приведены в таблице: Параметр оценки Характеристика Цвет Жёлтый Количество цветков на стебле 1-5 Аромат ?? Размер цветка 10-11 см Высота 200-300 см Ширина 150 см Зона выращивания (USDA) VI зона (Нижнее Поволжье, Воронежская, Калининградская области, Ростов-на-Дону) Зимостойкость ? Устойчивость к мучнистой росе ?? Устойчивость к черной пятнистости ?? Устойчивость к дождю ?? Период цветения ?? (повторноцветущая) Время посадки Апрель или конец октября В 1963 году сорт Casino удостоился высшей награды королевского розоводческого общества RNRS, а в 2001 году – звания лучшей плетистой розы на всемирной выставке во Флориде. Больше всего розоводов привлекает душистый, крупный густомахровый цветок солнечно-жёлтого окраса. Внутренние лепестки маленькие, интенсивно окрашенные, немного заострённые. Внешние – с красивыми закруглёнными изгибами, широкие, более изысканного пастельного оттенка. К основным достоинствам розы Casino можно отнести следующие качества: высокая декоративность куста, обильное ремонтантное цветение, неплохая устойчивость цветка к дождю, приятный чайный аромат, устойчивость цветка в срезке, быстрый рост. Недостатки сорта относительны и преодолимы. К ним относится жёсткость побегов, характерная для всех клаймберов, и недостаточная зимостойкость (Читайте также статью ? Сорта роз группы «Клаймбер» с отзывами и описанием).
< Фасоль обыкновенная: описание, фото Правильное мульчирование огурцов в открытом грунте и теплице >
Что такое бездепозитный бонус за регистрацию в казино? Бездепозитный бонус за регистрацию в казино — это стартовый подарок в виде денежного начисления или бесплатных вращений для новых игроков заведения, для получения которого не нужно вносить депозит.
Получение сертификата ИСО 9001 – завершающий этап процедуры сертификации, без прохождения которой выдача документа априори невозможна. Преимуществом будет, если орган, выполняющий проверку, имеет соответствующую аккредитацию стоимость получения сертификата ИСО 9001 Сертификат соответствия СМК требованиям ИСО 9001 – документ, который выдается по результатам экспертной проверки и подтверждает, что система менеджмента качества (СМК) организации соответствует международному стандарту ISO 9001 «Системы менеджмента качества. Требования» либо его национальному аналогу ГОСТ Р ИСО 9001 и своевременно совершенствуется.
A printable calendar is great for keeping the family organized — november printable calendar it’s customizable, encourages communication, and helps with planning, all without needing to rely too much on technology.
Я считаю, что Вы ошибаетесь. Могу отстоять свою позицию.
12. Почему перестали выполняться мои задания? естественно, для ролика продолжительностью 23 минуты значение параметра «Мин. 8. Кому я могу рассказать про https://reliantaqua.com/shop/reliant/reliant-commercial-uv-purifier-best-water-purifier/?
авто сайт
https://www.egymoe.com/pages/1xbet_promokod___aktualnuy_segodnya.html
https://everest.ro/wp-content/pages/1x_bet_promo_codes_free.html
Я советую Вам.
you can be sure that all Romanian escort lady in Dubai will be your teacher intimacy – and an obedient student in https://sierra-wiki.win/index.php?title=Dubai_stars_escort simultaneously.
апетитные)))
Надежность конструкции. песок и камни небольшого размера, прошедшие через сетку на входном патрубке, не наносят вреда его элементам, http://elektrokotly.com.ua/ редко могут стать причиной разрушения или блокирования функционирования механизма.
Казино Гама представлен огромный выбор игр. Здесь вы найдете все самые популярные игры, начиная от классических слотов до увлекательных настольных игр и видеопокера. Gama Casino сотрудничает с ведущими разработчиками игрового софта, поэтому качество игр и графика на высшем уровне.
Наши квалифицированные специалисты окажут вам профессиональную поддержку на всех этапах получения сертификата ISO 9001 https://certificatiso9001.blogspot.com/ Они оперативно и качественно исполнят каждое сертификационное мероприятие.
При регистрации на сайте 1xBet вы можете воспользоваться только одним промокодом, который является действительным. Используя этот промокод, вы получите бонус до 32500 рублей. 1хбет промокод при регистрации сегодня Важно отметить, что все остальные промокоды не являются действительными и не предоставляют такого же бонуса.
A promotional code is a code offered by retailers to customers who can use it to receive a discounted price when buying products online https://centroanafrank.com.ar/pag/codigo-promocional-1xbet.html
Принимает ведь Lev Казино Геймеров Из Украины, россии? Рекомендуется для внесения депозита в Lev зеркало выделить которой сумму денег, той можно проиграть нет ущерба для который бюджета. Если посчастливилось будет способствовать, то можно выиграть денежный приз как бонус к основному доходу. Об известном бренде большинство геймеров никто давно. лев казино сайт https://pirogovo-dialekt.ru/
Лев Бонусы | Фриспины Lev | Казино lev Вывод Денег | лев Казино Бонус без Депозита Казино лев – ??bit.ly/EBRANDDD_TOP2 ??КЭШБЭК – 10% ??НА ДЕПОЗИТ – 100% ??ФРИСПИНОВ – до 250 Приветствую, друзья ???. Думаю вы уже слышали о проекте лев, азартный клуб вызывает много споров у игроков ??. Я решил сделать обзор онлайн казино lev и рассказать всю правду о слотах, отзывах и выплатах ??. А для поклонников данного азартного клуба я оставил ссылку на зеркало и бесплатный Давайте проверим, действительно ли Lev считается лидером среди казино ??. Я расскажу про бонусы, а также активацию фриспинов лев, протестирую игровые автоматы и изучу их RTP ??. В конце я оставлю свое мнение об этом азартном клубе ??. Если вам понравился Лев обзор 2022 года, напишите свое мнение в комментариях под новым видео ??. лев зеркало топ казино онлайн лев Lev Лев промокод Лев казино онлайн лев бонусы онлайн казино Лев интернет казино Лев обзор казино лев #казино #слоты #выигрыши Кадры из видео Тэги из видео Комментарии пользователей: Leonid Davydov 2023-03-22 07:34:49 Мде. И как начать получать такие заносы? Куда звонить?) Sabrali Ganbari 2023-03-19 17:23:21 Это было реально горячо)) почти слив, но ты вытащил) красава, играешь по кайфу!) Leticia Gibbs 2023-03-15 03:09:20 Спасибо за офигенный контент) надеюсь скоро еще будут видео с советами!) Phong Hoang Van 2023-03-10 16:21:52 На таких сайтах нужно играть спокойно. Просто не раште и будьте спокойны) тогда шансы выше)
Пополнение, вывод Реже выводите, и пополняйте депозит. Один из нюансов работы на вилках предполагает перераспределение средств между конторами.
А уж тем более странно смотрится пополнение депозита, когда ставки еще не сыграны. Ведь обычно ждут результата, чтобы принять какое-то решение.
best promo code on 1xbet
Ремонт телефонов, ноутбуков, планшетов и другой техники https://remont-telefonov-moskva.ru/
Рекомендую Вам поискать сайт, где будет много статей на интересующую Вас тему.
? Фондовий ринок-ключове і https://karboglass18.ru/parts/profil-tortsevoj-up-2c-16-mm бонус. ?інші приналежності! Приєднатися реально в три форматах – завдяки пакетам gold, platinum і elite.
Техподдержка игроков В казино Драгон Мани создана служба технической поддержки. Получить консультацию можно круглосуточно и без выходных. Специалисты уточняют информацию о функционале площадке и помогают при возникновении проблем, в том числе при активации бонусов и выводе денег. Для связи с представителем техподдержки можно выбрать любой из вариантов: обращение к администратору в группе казино ВКонтакте отправка сообщения в онлайн чат на сайте заведения, получение поддержки по электронной почте protected] Казино лев – регистрация, бонусы и актуальное рабочее зеркало – зеркало страницы Лев
Заключение: стоит ли пользоваться доверительной ставкой Ставки на еще не выигранные деньги – привлекательный вариант, если на горизонте появляется результат, в надежности которого игрок не сомневается. Для букмекеров данная акция дает возможность манипулировать средствами. Игрок может выиграть с авансом, но не получит никаких денег. Главное, чтобы заключенные выиграли до получения аванса по ставке, из которого рассчитывалась сумма фиатной ставки. Игрок должен более тщательно продумать ставку, если он планирует воспользоваться данной акцией.
Оддсы в покере: что это? Чтобы научиться играть в покер, необходимо освоить основные математические приемы. Начинающему участнику азартных состязаний стоит ознакомиться со специфической терминологией, узнать, что представляют собой оддсы в покере. Только грамотные расчеты способны сделать игрока обладателем желанного денежного вознаграждения.
При регистрации на сайте 1xBet вы можете воспользоваться только одним промокодом, который является действительным. Используя этот промокод, вы получите бонус до 32500 рублей. Важно отметить, что все остальные промокоды не являются действительными и не предоставляют такого же бонуса.
промокод на бесплатные вращения 1xbet
promo code 1xbet at registration
Although Mostbet operates under an official international license, the official website of the bookmaker is sometimes blocked by Azerbaijani Internet providers http://nkrs.rsko.cz/phpbb/viewtopic.php?f=66&t=3476755
Kuliah Terbaik
https://b52.name
Código promocional 1xBet: ¡obtén un bono de bienvenida de hasta $130! 1xbet cГіdigo promocional El operador duplicará tu primer depósito hasta esa cantidad
Центр иностранных языков YES приглашает детей от 3-х лет, подростков и взрослых на онлайн-курсы английского языка курс разговорного английского языка онлайн Обучение в нашей онлайн-школе проводится по эффективной коммуникативной методике индивидуально.
Выиграть в казино онлайн джойказино? Конечно же, точного ответа на данный вопрос не сможет дать никто, даже сами владельцы казино онлайн, но все же некоторые советы и рекомендации у опытных игроков имеются: согласно мнению профессионалов игры в слоты и автоматы джойказино, ни в коем случае не следует начинать в первом же попавшемся на глаза казино онлайн, такой подход неверен, ведь играть нужно в тех казино онлайн, у которых высокая репутация по отзывам самих игроков, как например онлайн казино Джойказино: 100-Joycasino-slots.ru, кроме всего прочего, необходимо определиться и с типом игрового ресурса – скачиваемые версии, версии флеш, казино онлайн джойказино мобильного типа, многие опытные игроки советуют новичкам начинать с первого варианта, весьма важно обращать свое внимание на то, как оформлен дизайн казино онлайн, те казино джойказино, которые дорожат своей репутацией, всегда имеют дизайн своего сайта на высоком уровне, также следует ознакомиться с тем обстоятельством, имеется ли у заведения специальная лицензия и разрешение на осуществление данной деятельности, важным преимуществом казино онлайн является круглосуточная работа службы технической поддержки, для игрока важно, чтобы у казино имелись всевозможного рода бонусы, при этом игроку необходимо внимательно ознакомиться с тем, как их получить, кроме всего этого, у казино онлайн должно быть в наличии множество методов по пополнению либо выводу денежных средств, причем в качестве обязательных сегодня используются такие платежные системы, как Яндекс, ВебМани, Киви, важно также и то обстоятельство, чтобы у казино джойказино онлайн имелась возможность для игрока сыграть на виртуальные деньги, и только после этого начинать играть на настоящие деньги, многие опытные игроки советуют также хранить в секрете ваши собственные успехи в казино. Соблюдение этих хитростей и рекомендаций поможет каждому игроку, если и не выиграть большой куш, то, во всяком случае, не спустить свои собственные деньги на игре. Бк Джойказино официальное зеркало – https://zaim-v7.ru/
??Вход в личный кабинет ПлейФортуна на официальном сайте и зеркале Выполнив вход в личный кабинет на официальном сайте, гости заполняют личные сведения в анкетную форму. В нем же проводится пополнение средств и оформление заявок на выплаты выигрышей, а также активируются бонусы и контролируется их уровень отыгрыша. Регистрация проводится через официальный сайт джойказино, а также с помощью рабочих интернет зеркал азартной площадки. Если у игрока уже открыт аккаунт на оф сайте, повторно регистрироваться на зеркале не нужно.
Подробные отчеты Углубитесь в статистику ваших партнеров и их кампаний, анализируйте эффективность реферальных ссылок. Применяйте встроенные фильтры, чтобы сортировать отчеты по датам, менеджерам, комиссионным планам и так далее. Систематизируйте данные по валютам, датам первого депозита, странам. Выбирайте показатели и параметры отчета, которыми вы хотите поделиться с вашими партнерами, и выгружайте отчет в удобном для вас формате.
where can i buy zithromax without a prescription
Регистрация Леонбетс Если вы ещё не заключили пари с Леонбетс зеркало, то найдите ссылку и приступайте к регистрации. Переходим на официальный сайт конторы. Кликаем на кнопку «Регистрация». Заполняем предоставленные поля (телефон, адрес электронной почты и другие) жмём «Зарегистрироваться». Далее необходимо ввести полученный код с телефона. Внимание! При входе через зеркало, аккаунты в копиях сохраняются, т.е. не надо снова регистрироваться. Скачать джойказино на android ios: https://fantastikahd.ru/
Бананы на Багамах на андроид – скачать Бананы на Багамах бесплатно Бананы на Багамах относится к Игры для Андроид, Игры Казино, . На данный момент вы можете прочитать описание Бананы на Багамах, предоставленое официальным разработчиком Anton Naumov здесь
Виды игр Колесо Фортуны, Хай-ло, Покер, Live-дилер, Кено, Блэкджек, Бинго, Видеопокер, Рулетка, Игровые автоматы
Лингвистический центр YES предлагает вам открыть для себя новые языки или повысить свой уровень владения ими курс английского разговорного языка Мы открываем перспективы для учебы и работы за границей.
1. C88 Fun – Where Boundless Entertainment Begins!
Beyond being a mere gaming platform, C88 Fun is an adventure waiting to be explored. With its intuitive interface and a diverse selection of games, C88 Fun caters to all preferences. From timeless classics to cutting-edge releases, C88 Fun ensures every player discovers their perfect gaming sanctuary.
2. JILI & Evo 100% Welcome Bonus – A Grand Entrance to Gaming!
Embark on your gaming journey with a grand welcome from C88. New members are greeted with a 100% Welcome Bonus from JILI & Evo, doubling the excitement from the very beginning. This bonus serves as an excellent boost for players to explore the wide array of games available on the platform.
3. C88 First Deposit Get 2X Bonus – Doubling the Excitement!
C88 believes in generously rewarding players. With the “First Deposit Get 2X Bonus” offer, players can revel in double the fun on their initial deposit. This promotion enhances the gaming experience, providing more opportunities to win big across various games.
4. 20 Spin Times = Get Big Bonus (8,888P) – Spin Your Way to Glory!
Spin your way to substantial bonuses with the “20 Spin Times” promotion. Accumulate spins and stand a chance to win an impressive bonus of 8,888P. This promotion adds an extra layer of excitement to the gameplay, combining luck and strategy for maximum enjoyment.
5. Daily Check-in = Turnover 5X?! – Daily Rewards Await!
Consistency is key at C88. By simply logging in daily, players not only bask in the thrill of gaming but also stand a chance to multiply their turnovers by 5X. Daily check-ins bring additional perks, making every day a rewarding experience for dedicated players.
6. 7 Day Deposit 300 = Get 1,500P – Unlock Deposit Rewards!
For those eager to seize opportunities, the “7 Day Deposit” promotion is a game-changer. Deposit 300 and receive a generous reward of 1,500P. This promotion encourages players to explore the platform further and maximize their gaming potential.
7. Invite 100 Users = Get 10,000 PESO – Share the Excitement!
C88 believes in the strength of community. Invite friends and fellow gamers to join the excitement, and for every 100 users, receive an incredible reward of 10,000 PESO. Sharing the joy of gaming has never been more rewarding.
8. C88 New Member Get 100% First Deposit Bonus – Exclusive Benefits!
New members are in for a treat with an exclusive 100% First Deposit Bonus. C88 ensures that everyone kicks off their gaming journey with a boost, setting the stage for an exhilarating experience filled with opportunities to win.
9. All Pass Get C88 Extra Big Bonus 1000 PESO – Unlock Unlimited Rewards!
For avid players exploring every nook and cranny of C88, the “All Pass Get C88 Extra Big Bonus” offers an additional 1000 PESO. This promotion rewards those who embrace the full spectrum of games and features available on the platform.
Eager to dive into the excitement? Visit C88 now and unlock a world of gaming like never before. Don’t miss out on the excitement, bonuses, and wins that await you at C88. Join the community today and let the games begin! #c88 #c88login #c88bet #c88bonus #c88win
Vitebsk State University
В этом что-то есть. Теперь всё понятно, большое спасибо за информацию.
Shortly after that, the http://hilma.ch/2019/05/05/hallo-welt/ Nick Szabo described bit gold. Thompson, Luke (August 24, 2018). “The Bank of Thailand will launch its own cryptocurrency.”
1xslots
c88
C88: Elevate Your Gaming Experience with Unrivaled Bonuses and Endless Excitement!
Introduction:
Embark on an extraordinary gaming adventure with C88, a platform that redefines the boundaries of entertainment. Whether you’re a seasoned gamer or a newcomer, C88 promises an immersive experience characterized by thrilling features and exclusive bonuses. Let’s unravel the key elements that position C88 as the ultimate destination for gaming enthusiasts.
1. C88 Fun – Where Entertainment Knows No Bounds!
More than just a gaming platform, C88 Fun is an expedition waiting to be discovered. Boasting an intuitive interface and a diverse range of games, C88 Fun caters to all preferences. From timeless classics to cutting-edge releases, C88 Fun ensures every player finds their gaming sanctuary.
2. JILI & Evo 100% Welcome Bonus – A Warm Welcome for Newcomers!
Embark on your gaming journey with a warm embrace from C88. New members are welcomed with a 100% Welcome Bonus from JILI & Evo, doubling the excitement right from the start. This bonus acts as a catalyst for players to delve into the diverse array of games available on the platform.
3. C88 First Deposit Get 2X Bonus – Doubling the Excitement!
C88 believes in generously rewarding players. With the “First Deposit Get 2X Bonus” offer, players can revel in double the fun on their initial deposit. This promotion enriches the gaming experience, providing more avenues to win big across various games.
4. 20 Spin Times = Get Big Bonus (8,888P) – Spin Your Way to Greatness!
Spin your way to substantial bonuses with the “20 Spin Times” promotion. Accumulate spins and stand a chance to win an impressive bonus of 8,888P. This promotion adds an extra layer of excitement to the gameplay, combining luck and strategy for maximum enjoyment.
5. Daily Check-in = Turnover 5X?! – Daily Rewards Await!
Consistency is key at C88. By simply logging in daily, players not only bask in the thrill of gaming but also stand a chance to multiply their turnovers by 5X. Daily check-ins bring additional perks, making every day a rewarding experience for dedicated players.
6. 7 Day Deposit 300 = Get 1,500P – Unlock Deposit Rewards!
For those craving opportunities, the “7 Day Deposit” promotion is a game-changer. Deposit 300 and receive a generous reward of 1,500P. This promotion encourages players to explore the platform further and maximize their gaming potential.
7. Invite 100 Users = Get 10,000 PESO – Share the Excitement!
C88 believes in the strength of community. Invite friends and fellow gamers to join the excitement, and for every 100 users, receive an incredible reward of 10,000 PESO. Sharing the joy of gaming has never been more rewarding.
8. C88 New Member Get 100% First Deposit Bonus – Exclusive Benefits!
New members are in for a treat with an exclusive 100% First Deposit Bonus. C88 ensures that everyone kicks off their gaming journey with a boost, setting the stage for an exhilarating experience filled with opportunities to win.
9. All Pass Get C88 Extra Big Bonus 1000 PESO – Unlock Unlimited Rewards!
For avid players exploring every nook and cranny of C88, the “All Pass Get C88 Extra Big Bonus” offers an additional 1000 PESO. This promotion rewards those who embrace the full spectrum of games and features available on the platform.
Ready to immerse yourself in the excitement? Visit C88 now and unlock a world of gaming like never before. Don’t miss out on the excitement, bonuses, and wins that await you at C88. Join the community today and let the games begin! #c88 #c88login #c88bet #c88bonus #c88win
1xslots
Промокод СберМегаМаркет — скидка 1000 рублей на первый заказ! Промокод действует для новых покупателей в СберМегаМаркет, кроме Rieker, алкоголь и шины, наушники Apple, смартфоны. Суммируется со скидками, минимальный заказ 4 000 рублей. Скопировать промокод и открыть сайт 600 ₽ выгода Играем в казино Джойказино. Берем бонусы https://euroshow-msk.ru/
Как выиграть в блекджек О базовой стратегии игры в блекджек мы поговорим чуть ниже, а пока расскажем о том, какие еще существуют способы выигрыша в этой популярнейшей игре. Весьма популярная стратегия – это классическое удвоение. Проиграв кон, игрок удваивает ставку – и так до победы. А при выигрыше сразу возвращается к первоначальной сумме ставки. Но тут важно иметь достаточное количество денег на руках, а также чтобы в казино не было ограничения по сумме ставки. Стратегия рискованная, но при выполнение этих двух условий вполне может привести к выигрышу. Также для победы при игре в блекджек можно применить подход «1-3-2-6». В его основе заложено увеличение ставок при удачном исходе в обозначенной в названии последовательности. Выиграв первый раз, вы повышаете ставку втрое, далее после следующей победы вдвое, и наконец, после еще одной удачи – в шесть раз. Но каждая неудача должна возвращать игрока к первоначальной сумме ставки. Также можно играть в преследование. До игры вы назначаете сами себе минимум и максимум ставки. Минимумом лучше брать один процент банка, а максимумом – 10%. Начинаете с минимума. Выиграв – ставите максимум. И так до первого поражения, в затем все сначала.
TV игры джойказино Казино Джойказино предлагает делать ставки на экспрессы, добавлять исходы из разных игр в один купон и таким образом увеличивать суммы своих выигрышей. Игроки получили возможность заключать пари на популярные тв-игры, транслируемые в России, Италии, Австрии и в других странах. В числе событий здесь представлены: вручение популярных премий, различные тв-шоу, события из мира кино и специальные ставки на знаменитостей.
Ремонт гитар в Гомеле мастерская по ремонту гитар гомель с гарантией качества работы.
Medicament information. Brand names.
zovirax
Best what you want to know about drug. Get now.
Drugs information sheet. Generic Name.
buy viagra soft
Best information about medication. Get information now.
MOTOLADY предлагают услуги аренды и проката мотоциклов и скутеров в Хургаде, Эль Гуне и Сахл Хашиш. MOTOLADY – одна из самых популярных компаний по прокату мотоциклов и скутеров. Они предлагают большой выбор транспортных средств по разумным ценам. MOTOLADY компания, специализирующаяся на Аренда мопеда в Эльгуне и Эль Гуне. Они предлагают услуги доставки транспорта в любое удобное для вас место. У нас в наличии различные модели транспортных средств по доступным ценам. Перед арендой транспорта обязательно ознакомьтесь с правилами и требованиями компании, также проверьте наличие страховки и необходимые документы для аренды.
finasteride tablets
Обязательно посмотрю…
товар швейцарских снабжен отменными моющими http://bam61.ru/shop/product/1948/reviews/ и увлажняющими качествами. Этими средствами Вы убиваете полезную микрофлору, открывая путь грибкам и болезнетворным бактериям.
Заключение Чарджбэк – трудный и продолжительный процесс, который в большинстве случаев, как показывает практика, завершается неудачей или отказом. В Европе и США — это распространенная практика, но в России очень мало банков готовы связываться с этим занятие. Возможно, через несколько лет получить обратно деньги от неправомерных действий Казино или казино будет проще, но сейчас это сплошной сбор документов и подтверждающих материалов. В России на данный момент развиваются букмекеры, которые занимаются именно этим вопросом, но говорить о профессионализме не приходится. Официальный сайт и рабочее зеркало Vavada, приложение на android и ios: http://azotfun.ru/
Что о нас говорят Заказывала для нашей компании уже несколько мероприятий у ребят из “Фан казино”. Для первого раза выбирали винное казино, так как оказалось, что коллеги любители вина. Второй раз выбор пал на покер. Так, мы решили разнообразить рабочие будни чем-то экзотичным. Интересно, что мероприятие легально, потому что фишки покупаются на фан-мани. Это валюта, но ее действие распространяется только на момент мероприятия. На выигрыш можно “купить” себе дополнительную еду и напитки. Все корпоративы с аттракционами от “Фан казино” прошли на “УРА”! Оборудование и реквизит привозили вовремя, персонал – настоящие профессионалы. В общем, ждем расширения ассортимента развлечений. Марина Калинина “ Перед Новым Годом заказал аттракцион “Винное казино” у ребят из “Фан казино”. Прочитал на сайте, что это развлечение на корпоратив, которое понравится новичкам и профи в пробах вина. Не хотел заниматься организацией и всецело поручил это ребятам. Они подобрали напитки, пригласили сомелье, привезли вовремя реквизит в офис. Теперь я и коллеги разбираемся в винах! Сотрудникам понравилось развлечение под Новый год. Уже порекомендовал “Фан казино” друзьям. Алексей Смирнов “ Заказывали игру “Блэкджек” на корпоратив. У нас в коллективе одни мужчины, поэтому захотелось что-нибудь интересного. Много думать не хотелось, и мы выбрали игру, исход которой зависит от удачи. Конечно, казино от “Фан казино” совершенно легально. Мы играли на фан-мани, которые работали только на самом корпоративе. Это не помешало стать игре азартной, так как приз все же был, хоть и номинальный. Мои сотрудники оценили работу крупье, который подробно рассказал правила игры. Поняли с первого раза. Всё было очень весело и интересно! Для корпоратива мероприятие отлично подошло. Виталий Горбунов “ Моему бизнесу исполнился год, и я решила отпраздновать это событие со своими сотрудниками. Так как продаем мы кофе, корпоратив я тоже захотела устроить кофейный. У “Фан казино” оказалась такая услуга – кофейное казино. В общем, мы собрались в арендованном помещении, нам все привезли. Бариста был очень вежлив с нами. С некоторыми сотрудниками завязался спор по поводу сортов кофе, в котором мы достигли истины. Результаты меня порадовали. Мои ребята умеют различать оттенки вкуса, а это очень важно для работников в кофейной сфере. А “Фан казино” предоставили крутой аттракцион и организацию. Спасибо!
Взгляд опытных игроков Опытные игроки советуют не доводить игру до участия в акции «Кэшбэк для своих». Если месяц не задался настолько, что клиент проиграл более 100000 руб., целесообразно проиграть еще 50000 руб. для получения возврата по акции в виде фрибета суммой 12000 руб. – отыграть кеш-бонус экспрессами с котировками каждого события 1.60 в пятикратном размере практически невозможно.
O Cassino fresh casino login esta ganhando popularidade e se esforca para fornecer apenas servicos de alta qualidade.
yuhot.ru
косметика с феромонами
Толку от этого мало.
Как сообщила столичная ГИБДД в telegram, в результате пострадал водитель http://www.sskyn.com/home-uid-79161.html, коего с ожогом руки доставили в поликлинику.
Drugs information for patients. Drug Class.
eldepryl buy
Some information about meds. Get here.
Все, что вам нужно знать о винтовых масляных компрессорах: принципы работы и секреты повышения эффективности работы на https://infokam.su/konstruktsiya-i-printsip-raboty-vintovyh-maslyanyh-kompressorov.html
Аренда инструмента в название с инструментом без В нашем сервисе доступны современные модели инструментов решение для Профессиональный инструмент выгодно в нашем сервисе
Прокат инструмента любых задач
Экономьте деньги на покупке инструмента с нашим услугами проката
Идеальное решение для садоводства нет инструмента? Не проблема, на наш сервис за инструментом!
Расширьте свои возможности с качественным инструментом из нашего сервиса
Аренда инструмента для садовых работ
Не тяните деньги на покупку инструмента, а арендуйте инструмент для разнообразных задач в наличии
Разнообразие инструмента для осуществления различных работ
Профессиональная помощь в выборе нужного инструмента от опытных нашей компании
Выгодно с услугами аренды инструмента для строительства дома или квартиры
Наша команда – надежный партнер в аренде инструмента
Надежный помощник для ремонтных работ – в нашем прокате инструмента
Не можете определиться с выбором? Мы поможем с подбором инструмента в нашем сервисе.
прокат аренда без залога https://www.meteor-perm.ru/.
how long does gabapentin stay in your system
tombak118
tombak118
1. C88 Fun – Infinite Entertainment Beckons!
C88 Fun is not just a gaming platform; it’s a gateway to limitless entertainment. Featuring an intuitive interface and an eclectic game selection, C88 Fun caters to every gaming preference. From timeless classics to cutting-edge releases, C88 Fun ensures every player discovers their personal gaming haven.
2. JILI & Evo 100% Welcome Bonus – A Grand Welcome Awaits!
Embark on your gaming journey with a grand welcome from C88. New members are greeted with a 100% Welcome Bonus from JILI & Evo, doubling the thrill from the get-go. This bonus acts as a springboard for players to explore the diverse array of games available on the platform.
3. C88 First Deposit Get 2X Bonus – Double the Excitement!
Generosity is a cornerstone at C88. With the “First Deposit Get 2X Bonus” offer, players revel in double the fun on their initial deposit. This promotion enhances the gaming experience, providing more avenues to win big across various games.
4. 20 Spin Times = Get Big Bonus (8,888P) – Spin Your Way to Glory!
Spin your way to substantial bonuses with the “20 Spin Times” promotion. Accumulate spins and stand a chance to win an impressive bonus of 8,888P. This promotion adds an extra layer of excitement to the gameplay, combining luck and strategy for maximum enjoyment.
5. Daily Check-in = Turnover 5X?! – Daily Rewards Await!
Consistency reigns supreme at C88. By simply logging in daily, players not only savor the thrill of gaming but also stand a chance to multiply their turnovers by 5X. Daily check-ins bring additional perks, making every day a rewarding experience for dedicated players.
6. 7 Day Deposit 300 = Get 1,500P – Unlock Deposit Rewards!
For those hungry for opportunities, the “7 Day Deposit” promotion is a game-changer. Deposit 300 and receive a generous reward of 1,500P. This promotion encourages players to explore the platform further and maximize their gaming potential.
7. Invite 100 Users = Get 10,000 PESO – Spread the Joy!
C88 believes in the strength of community. Invite friends and fellow gamers to join the excitement, and for every 100 users, receive an incredible reward of 10,000 PESO. Sharing the joy of gaming has never been more rewarding.
8. C88 New Member Get 100% First Deposit Bonus – Exclusive Benefits!
New members are in for a treat with an exclusive 100% First Deposit Bonus. C88 ensures that everyone kicks off their gaming journey with a boost, setting the stage for an exhilarating experience filled with opportunities to win.
9. All Pass Get C88 Extra Big Bonus 1000 PESO – Unlock Unlimited Rewards!
For avid players exploring every nook and cranny of C88, the “All Pass Get C88 Extra Big Bonus” offers an additional 1000 PESO. This promotion rewards those who embrace the full spectrum of games and features available on the platform.
Ready to immerse yourself in the excitement? Visit C88 now and unlock a world of gaming like never before. Don’t miss out on the excitement, bonuses, and wins that await you at C88. Join the community today, and let the games begin! #c88 #c88login #c88bet #c88bonus #c88win
Смотрите фильмы, сериалы, и мультфильмы из списка “Фильмы и сериалы” в нашем онлайн-кинотеатре сериалы смотреть онлайн
The Internet has revolutionized business strategies reputation house serm
Porn
nha cai
In recent years, the landscape of digital entertainment and online gaming has expanded, with ‘nha cai’ (betting houses or bookmakers) becoming a significant part. Among these, ‘nha cai RG’ has emerged as a notable player. It’s essential to understand what these entities are and how they operate in the modern digital world.
A ‘nha cai’ essentially refers to an organization or an online platform that offers betting services. These can range from sports betting to other forms of wagering. The growth of internet connectivity and mobile technology has made these services more accessible than ever before.
Among the myriad of options, ‘nha cai RG’ has been mentioned frequently. It appears to be one of the numerous online betting platforms. The ‘RG’ could be an abbreviation or a part of the brand’s name. As with any online betting platform, it’s crucial for users to understand the terms, conditions, and the legalities involved in their country or region.
The phrase ‘RG nha cai’ could be interpreted as emphasizing the specific brand ‘RG’ within the broader category of bookmakers. This kind of focus suggests a discussion or analysis specific to that brand, possibly about its services, user experience, or its standing in the market.
Finally, ‘Nha cai Uy tin’ is a term that people often look for. ‘Uy tin’ translates to ‘reputable’ or ‘trustworthy.’ In the context of online betting, it’s a crucial aspect. Users typically seek platforms that are reliable, have transparent operations, and offer fair play. Trustworthiness also encompasses aspects like customer service, the security of transactions, and the protection of user data.
In conclusion, understanding the dynamics of ‘nha cai,’ such as ‘nha cai RG,’ and the importance of ‘Uy tin’ is vital for anyone interested in or participating in online betting. It’s a world that offers entertainment and opportunities but also requires a high level of awareness and responsibility.
Pills information leaflet. Short-Term Effects.
cheap synthroid
Actual information about medication. Get information now.
Маркетинговая компания “elim” проводит анализ рынков на заявку. посредством делового предложения обосновываются инвестиции и средства в бизнес. Обычно, целью изучения рынка является желание понять ситуацию в сфере торговли: спрос, пожелание и сбыт продукции, работ, https://aulamusical.cat/component/k2/item/9-concert-nocturn-opus-1/ услуг) на определенной территории.
1. Баннерная и тизерная реклама. также применяются скидки, http://www.roachstory.co.kr/bbs/board.php?bo_table=free&wr_id=180893 акции и иные мероприятия стимуляции интереса потребителей.
Drug information for patients. Brand names.
cost retrovir
Best news about drug. Get here.
Мне кажется, вы ошибаетесь
11 hot drop jackpots that promise guaranteed winnings at the daily https://wiki.top-fully.com/how-to-exhaust-healthily-and-attain-weighting-red-goals-2907084341701601743. at the moment you refuse to settle for that less than a hyperrealistic betting experience, selection interactions with live dealers Super Slots will bring all gambling houses to your living room.
How much do negative reviews affect the reputation, figures, and income of a business reputation house
бухгалтерская отчетность
Кто сказал, что казино всегда выигрывает? Ни для кого не секрет, что любое казино подкручивает слоты в индивидуальном порядке, но благодаря особым стратегиям и техникам вы сможете выигрывать в слотах Slottica в несколько раз чаще. Проводите время за игрой в игровые автоматы не только приятно, но и прибыльно, не выходя из браузера. Онлайн казино Кент: детальный обзор и описание преимуществ: kent рабочее зеркало страницы
Бонусы с бесплатной игрой на время Фриплей бонус Players Palace Casino Размер бонуса 2000 USD ПРОМОКОД: Не требуется Макс бонус: 2000 USD Деп для выдачи: Не требуется Вейджер: 60 xB Выводится? Липкий Макс кэшаут: 100 USD Фриплей бонус Grand Mondial Casino Размер бонуса 2500 USD ПРОМОКОД: Не требуется Макс бонус: 2500 USD Деп для выдачи: Не требуется Вейджер: 30 xB Выводится? Липкий Макс кэшаут: 100 USD Фриплей бонус Golden Tiger Casino Размер бонуса 1500 USD ПРОМОКОД: Не требуется Макс бонус: 1500 USD Деп для выдачи: Не требуется Вейджер: 30 xB Выводится? Липкий Макс кэшаут: 100 USD Фриплей бонус Casino Share Размер бонуса 2011 USD ПРОМОКОД: Не требуется Макс бонус: 2011 USD Деп для выдачи: Не требуется Вейджер: 30 xB Выводится? Липкий Макс кэшаут: 100 USD Фриплей бонус Casino Classic Размер бонуса 500 USD ПРОМОКОД: Не требуется Макс бонус: 500 USD Деп для выдачи: Не требуется Вейджер: 30 xB Выводится? Липкий Макс кэшаут: 100 USD Фриплей бонус Blackjack Ballroom Casino Размер бонуса 500 USD ПРОМОКОД: Не требуется Макс бонус: 500 USD Деп для выдачи: Не требуется Вейджер: 60 xB Выводится? Липкий Макс кэшаут: 100 USD
футбольные ставки в kent в Волгограде Адреса Режим работы Телефон Координаты б-р 30 летия Победы, д. 39 а Пн.-Вс.: 00:00-24:00 8 (800) 555-51-81 N48.754293E44.49343 ул. Рабоче-Крестьянская, д. 10 Пн.-Вс.: 00:00-24:00 8 (800) 555-51-81 N48.6977E44.4997 ул. Новосибирская, д. 41 10:00-18:00 8 (800) 555-51-81 N48.677492E44.45244 ул. Канатчиков, д. 20 А Пн.-Вс.: 00:00-24:00 8 (800) 555-51-81 N48.518086E44.567128 ул. им. Николая Отрады, 22 а Пн.-Вс.: 10:00-23:00 8 (800) 555-51-81 N48.815864E44.629273 ул. Дзержинского, д. 2 Б 10:00-18:00 8 (800) 555-51-81 N48.80265E44.604273 ул. Титова, д. 43 А Пн.-Вс.: 12:00-23:00 8 (800) 555-51-81 N48.785314E44.564505 пр-кт Металлургов, д. 50 А 10:00-18:00 8 (800) 555-51-81 N48.771771E44.545955 ул. Коммунистическая, д.12 Пн.-Вс.: 00:00-24:00 8 (800) 555-51-81 N48.710979E44.513642
lyrica ocd
Компания Namuna Development в Ташкенте с 2017 года стремится не просто строить здания, бизнес-центры в ташкенте но и создавать территорию, оснащенную развитой инфраструктурой.
fake Cartier watches
https://sport-weekend.com/otkroj-dver-v-mir-psihologicheskogo-zdorovja.htm
Drug prescribing information. Generic Name.
cialis pill
All news about medicament. Read now.
Drug information leaflet. Drug Class.
lisinopril
Actual about medicament. Read information here.
https://www.wildberries.ru/catalog/176001489/detail.aspx
Женская Водолазка с Длинным рукавом (Черная) Артикул 9889696754543457
лев – Вся правда без Воды и Грязи! Проверка казино лев – Можно ли выиграть? Реальный Отзыв. 05:53 ССЫЛОЧКА ГДЕ РУБЛЮСЬ: _R9ykXNk4xXA3TCGw/about Ребята, всем Привет! В этом видео покажу как я игрую в онлайн казино и что у меня из этого получается. так что смотрите видео до конца – там как раз самое интересное кроется. Подписывайтесь на канал, написав Комент, не забудь нажать Колокольчик чтобы первым узнать когда выйдет следующий видосик. Всем приятного просмотра! ___________________ Слова для поиска: Лев Lev казино Лев казино казино лев казино lev Лев обзор казино онлайн лев регистрация онлайн казино Лев казино Лев обзор Lev отзывы лицензинное казино Лев казино отзывы заносы в казино игровые автоматы онлайн казино лев отзывы казино без верификации казино на телефон как играть лев отзывы казино Lev игровые автоматы лев проверка казино лев слоты которые дают вывод денег из казино Лев лев играть лев казино ссылка Лев вывод денег проверка казино lev Теги: #лев #проверкаказиноEBRANDDD #какигратьRBRANDDD ?Категории: Блоги?Теги: казино, лев, без, отзыв, вся, игратьRBRANDDD, видео, автоматы, RBRANDDDказино, на, реальный Что дают промокоды в казино лев зеркало сайта lev
Бонусы онлайн казино Вейджер: 25X Фриспины: 150 Действителен до: Бессрочный Промокод: нет Максимальная сумма: 10000 UAH Минимальный депозит: 360 UAH Вейджер: 35X Размер бонуса: 100
Преимущества приложения Lev на Android Игроки Казино Лев выбирают игорное заведение из-за множества преимуществ, в числе которых: высокие показатели кэфов, широкий ассортимент платежных систем, несколько способов регистрации, оперативная связь с ТП и конечно, современное мобильное приложение. Скачивая софт, гемблеры могут получить доступ ко всем необходимым опциям для заработка в онлайн-режиме.
bnf diltiazem
Drugs prescribing information. Generic Name.
lisinopril without rx
Some information about pills. Get here.
Drug information for patients. Drug Class.
valtrex sale
Everything about medicines. Get now.
Какая трогательные фраза 🙂
наша компания, диплом вуза ссср купить более восьми лет поставляет и реализует документы. для поступления на платной основе, требования менее строгие. купленный корочки станет решающим аргументом при поступлении в институт.
Medication information leaflet. Drug Class.
amoxil
Everything news about drug. Read here.
Актуальные объявления о покупке и продаже квартир на вторичном рынке недвижимости kvartira sotiladi toshkent частные объявления о продаже квартир.
ketoconazole trazodone
Medicine information leaflet. Drug Class.
eldepryl
All trends of medicament. Get information now.
Мгновенно создавайте премиальные статьи, описания и разнообразный контент с использованием нашего революционного искусственного интеллекта Чат боты ИИ
Перечень товаров, не требующих сертификации. Не существует единого утвержденного списка товаров, не требующих сертификации Продукция не подлежащая сертификации Это было сказано ранее. По мере изучения актуального списка вы не найдете вашей продукции среди заявленных категорий – это означает, что единственным документом для реализации или прохождения таможенного контроля является отказное письмо.
The magical world of slot machines: Book of Mostbet and Joker Stoker https://www.camaro5.com/forums/group.php?&do=discuss&groupid=479&discussionid=&gmid=179866#gmessage179866
Наставник по питанию Андрей Воронин
Наставник по питанию Андрей Воронин – человек, который в течение 12 лет пытался решить проблему с лишним весом, перепробовав множество способов похудеть. Неоднократно обращался с проблемой лишнего веса к нутрициологам, фитнес-тренерам и диетологам, однако ни один из них не смог помочь. Всё это было похоже на обман, не решающий проблему, а лишь отгоняющий ее на некоторое время. Вес трижды уходил, но всегда возвращался. Согласитесь, это был совсем не тот результат, который хотелось получить, работая с профессионалами.
Однако Андрей смог найти решение. Он самостоятельно похудел на 31 кг и с 2018 года помогает достичь этой цели другим людям.
Как же ему это удалось?
Дело в том, что Андрей Павлович взялся за разработку собственной методики похудения без диет и изнурительных тренировок. И уже более 400 человек совершенствуют по ней свое тело и получают положительные результаты. А создатель методики теперь стал настоящим ЗОЖ-коучем, наставником по здоровому питанию и эффективному достижению целей.
Наставник по питанию Андрей Воронин – человек, который знает врага в лицо и нашел способ его устранить. Методика получила название “ДиетоЛогика”. Это комплексная авторская методика коррекции веса и избавления от пищевой зависимости, основанная на личном опыте и тщательном изучении проблемы, а не просто диета или марафон.
Если у вас или у вашего ребенка есть проблемы с лишним весом или есть нездоровое отношение к еде, методика нутрициолога Андрея Воронина решит их в 9 из 10 случаев.
Автор советует отказаться от постоянного скачивания диет, подсчета калорий и участия в марафонах, предлагая вместо этого решить проблему лишнего веса раз и навсегда.
Андрей Павлович уверен в успехе своей методики, потому что:
* Он сам похудел на 31 кг и понимает проблему изнутри.
* У него имеется 3 диплома по коррекции веса.
* У него множество положительных отзывов.
* Он предоставляет гарантии похудения в договоре.
* Он официально зарегистрирован как ИП.
* Его знают в СМИ, его приглашают в телевизионные и радиопередачи.
* Одна из его книг стала хитом продаж.
* Информация о нем доступна в интернете.
* К нему обращаются звезды, и о нем рассказывают в СМИ.
* Он получил благодарность от Мосгодумы и многое другое.
Книга Андрея Павловича “Диетологи, я вам не верю!” призывает читателей обращать внимание на свое здоровье, быть внимательнее к уловкам рекламы и не губить свое тело перееданиями.
Не экономьте на своем здоровье. Не сдавайтесь: коррекция веса возможна! Не тратьте свое время на прохождение марафонов по похудению. Не мучьте себя диетами и тренировками, эффективность которых крайне сомнительна, особенно, если вы сами себе это назначили. Очень важно, чтобы человек, который предлагает вам диету и систему тренировок, был хорошо знаком с проблемой.
Консультация диетолога является важным шагом для тех, кто стремится достичь своих целей: изменить привычки в питании, прийти к стройности и поддержанию здоровья. Диетолог может помочь клиенту разработать индивидуальный план питания, основанный на его потребностях, предпочтениях и целях.
Андрей Павлович Воронин также готов поменять ваше «хочу» в питании. Поменяются ваши привычки и убеждения – и стройность станет вечной.
купить бетон серпухов
Наставник по питанию Андрей Воронин
Hello there! This is my first comment here so I just wanted
to give a quick shout out and say I genuinely enjoy reading through
your posts. Can you recommend any other blogs/websites/forums that deal with the same topics?
Thanks a lot!
buy doxycycline for malaria
двухкомнатная квартира в ташкенте
купить квартиру в ташкенте новостройка
Максимальная эффективность в арбитраже: выбирайте виртуальные карты от Webscard виартуальные карты для оплаты сервисов
Добровольная сертификация продукции услуг и систем менеджмента качества в СДС Роспромтест на соответствие Государственным стандартам, техническим условиям. Сертификация объектов проходит на добровольной основе по инициативе заявителя в системе добровольной сертификации Роспромтест на соответствие Государственным стандартам (ГОСТ), техническим условиям (ТУ), стандартам организации (СТО).
квартира в кредит в ташкенте
Купить квартиру-студию в Ташкенте
In the ever-evolving world of digital technology, it has become increasingly important for individuals and businesses to safeguard their online security https://xn—-htbblufccvgdmek8j.xn--p1ai/forum/messages/forum1/topic171/message758/?result=new#message758
Да уж, спасибо
В фешенебельной и удобной одежде любая девушка ощущает себя авторитетно и комфортно. обязательная составляющая комфортного образа и утонченного стиля – http://ffi.forum.cool/viewtopic.php?id=539#p1413 качество пошива.
19dewa daftar
Абсолютно с Вами согласен. Идея отличная, согласен с Вами.
в качестве поощрительного приза ему начислят 100% от внесенной суммы (но, не рамен бет казино более трех сотен евро).
квартиры в ташкенте в ипотеку
новостройки на субсидию в ташкенте
Не уделите мне минутку?
Месси о словах «Че уставился, http://pikomp.kz/index.php/component/virtuemart/kartridzhi/hp/kartridzh-hp-laser-jet-1100-canon-810-net-product-detail?itemid=50 придурок? Мак Аллистер о победе на ЧМ-2022: «это исчерпывающая радость для Месси – он страдал, когда ему не вышло выиграть.
brillx казино
https://brillx-kazino.com
Играть онлайн бесплатно в игровые аппараты стало еще проще с нашим интуитивно понятным интерфейсом. Просто выберите свой любимый слот и погрузитесь в мир ярких красок и захватывающих приключений. Наши разнообразные бонусы и акции добавят нотку удивительности к вашей игре. К тому же, для тех, кто желает ощутить настоящий азарт, у нас есть возможность играть на деньги. Это шанс попытать удачу и ощутить адреналин, который ищет настоящий игрок.Сияющие огни бриллкс казино приветствуют вас в уникальной атмосфере азартных развлечений. В 2023 году мы рады предложить вам возможность играть онлайн бесплатно или на деньги в самые захватывающие игровые аппараты. Наши эксклюзивные игры станут вашим партнером в незабываемом приключении, где каждое вращение барабанов приносит невероятные эмоции.
Не вижу в этом смысла.
Возможность старта работ с минимальных бюджетов. Правильная и эффективная стратегия. 1. Оценка перспектив и направлений бизнеса, https://dosaaf.ru/images/pgs/prodvizghenie_sayta_stroitelnoy_kompanii_v_seti_internet_s_chego_nachat.html привлечение потребителей к кому через продвижение сайта даст максимальный коммерческий эффект.
https://iotzyv.ru/2023/12/11/advokat-sibgatullin-timur-ravilevich/
Medication information. Long-Term Effects.
glucophage
Best information about medication. Read information now.
https://stihi.ru/avtor/sibgatullin
daftar hoki1881
Medicament prescribing information. Brand names.
sildigra
Best about medicament. Read now.
https://ru.otzyv.com/sibgatullin-timur-ravilevich
Drug information for patients. What side effects can this medication cause?
mobic
Everything news about medication. Get information now.
Hi it’s me, I am also visiting this web page on a regular basis, this web page is really good and the visitors are really
sharing good thoughts.
Meds prescribing information. Brand names.
lioresal medication
Actual what you want to know about pills. Get here.
Pills prescribing information. Drug Class.
promethazine brand name
All information about drugs. Read information here.
Весьма забавное мнение
Это обезопасит транспорт от наезда других машин. функционирует 5 точек «Эвакуатор хелп» с дежурными эвакуаторами в санкт-петербурге, http://softor.net/index.php?subaction=userinfo&user=itiziw потому помощь подоспеет быстро.
строительные компании ташкент
https://namebook.club/profile/sibgatullin-timur-27850990000
free slots online
Your analogies as well as comparisons create the information therefore relatable.
I enjoy your talent for making challenging subject
matters available.
Also visit my web-site … Santa Ana insurance companies
https://ruscifra.ru/self-employed/6884094/
casino betting
login hoki1881
19dewa
best usa casinos
Большой выбор батарей салютов. Качественная пиротехника по доступным ценам купить фейерверки в интернет
levaquin 500mg
levaquin for wound infection
Интересный вариант
http://wownsk-portal.ru/user/neasalscrh, a popular one-armed bandit developed by pragmatic play, acquired incredible demand among fans network gaming establishments – in the United Kingdom.
synthroid 2 mg generic price
Drugs prescribing information. What side effects?
nolvadex
Everything information about medicament. Get information now.
Подтверждаю. Всё выше сказанное правда. Давайте обсудим этот вопрос.
The visual results and the soundtrack of this slot completely correspond to the image of the magical girl from the anime http://z918863j.bget.ru/user/pjetuswdzb.
https://earnings.0pk.me/viewtopic.php?id=8439#p17652
Заказать пластиковые окна из немецкого профиля VEKA. Выгодные цены и предложения на покупку и установку пластиковых ПВХ окон и дверей готовые окна пвх
buying cheap synthroid without insurance
Thank you for shedding light on this subject matter.
The clearness in your blog post is merely outstanding, as well as I can not stand by to
read through extra coming from you.
Look into my blog: SR22 Insurance Illinois
Купить нержавеющие трубы по доступным ценам за метр от производителя алюминиевые окна пвх в Москве от производителя по низким ценам
can i get cheap lyrica without a prescription
This website was… how do I say it? Relevant!!
Finally I have ound something that helped me. Thanks
a lot!
my homepage: SEO For CBD
рецепты в домашних условиях фото рецепт
buy generic mobic without prescription
can i buy colchicine for sale
I hightly recommend this security company site.
how to buy cheap lisinopril without a prescription
Такое также реально. в 21 веке продаются любые липовые корочки, подтверждающие прохождение учебы, например, школьные аттестаты, http://bizziran.com/redirect/to/?url=mosdiploms.com сертификаты и свидетельства об окончании курсов.
where to buy duphalac
The infographics you consisted of were an excellent touch.
They brought in the data a great deal extra digestible.
Feel free to surf to my web blog Affordable insurance Dallas
cefepime
Interesting blog! Is your theme custom made or did you download it from somewhere?
A theme like yours with a few simple adjustements wokuld really make myy bloig stand out.
Please let me know where you got your design. Appreciate it
Also visit mmy webpage; Reputation Management Services Phoenix
is albuterol a bronchodilator
многие говорят подобный тип обучения не совсем образовательным, а вероятнее научно-исследовательским процессом. ввиду этого, если вас интересует ученая степень, чтобы продвинуться по карьерной лестнице и получить неплохую прибавку к зарплате, достаточно https://sabuilding.net.au/2021/07/26/about-us/ доктора наук.
can i get prednisone online
Meds information. Cautions.
sildigra
Actual news about medicament. Get now.
Medicine prescribing information. Drug Class.
stromectol
Some news about medicine. Read here.
where can i get cheap vasotec without insurance
Эскортницы работают как профессиональные приятные спутницы, удовлетворяя запросы клиентов и предоставляя удобную обстановку. Университетские студентки-эскортницы способны предложить разные виды обслуживания, http://fr79056g.bget.ru/index.php?name=account&op=info&uname=anyny исходя из условий клиента.
Medicament information leaflet. Drug Class.
silagra
Everything information about medicament. Read information now.
zyrtec children’s
buy generic prednisone 5mg
Drug information sheet. Effects of Drug Abuse.
neurontin price
Best information about drugs. Get information here.
MEGA onion – это крупнейший анонимный магазин в
России и СНГ, который предоставляет
свои услуги в сети. Наша площадка http://latenitetip.com/index.php?page=user&action=pub_profile&id=124474 обеспечивает полную анонимность и безопасность для каждого пользователя.
Мы также обеспечиваем защиту ваших финансов, удобную и быструю оплату продуктов и услуг в различных валютах,
включая криптовалюту, и обход всех видов блокировок.
Для посещения нашего веб-сайта вам не понадобится подключение к
Tor или VPN .
diltiazem for afib
рецепт пирожков
Интересно, http://autoschool-progress.kz/index.php?subaction=userinfo&user=yxemeci за что она его полюбила? на настоящий время данная ниша рынка фактически стопроцентно свободна, занимают ее лишь проститутки, предоставляющие среди других и сведения услуги сомнительного качества и еще модельные агентства, предлагающие “товар из-под полы”, другими словами ни воспоминания о возможности сопровождения моделью на страницах сайта, ни в другой рекламе – нет.
сервант для зала
19dewa gacor
1.высокие цены. Исследуя рынок г. Самары, компанией совершен вывод о том, http://freeschool.ru/index.php?option=com_easybookreloaded что цена вызова эвакуатора действительно высока.
get cheap mobic for sale
buy prednisone without a precipitation
Drug information. Drug Class.
zoloft without dr prescription
Everything news about medicines. Read information now.
I hightly recommend this Abacus Market site.
Medicament information for patients. Drug Class.
buying singulair
Actual information about medicament. Get here.
how to get cheap zithromax pill
Drugs prescribing information. Short-Term Effects.
sildigra
Best what you want to know about meds. Get information here.
Of course, you will have to ask to what extent you are an asshole, when you really https://trade-britanica.trade/wiki/User:LanoraMaitland movies with similar names as modest unfortunate situation with a stepdaughter” and “The return of a bad step-uncle.”
where buy cheap lexapro
Pills information leaflet. What side effects can this medication cause?
neurontin
Everything about drug. Get here.
Nestled in the heart of Uptown Dubai Mercer House riginal site.
Medication information for patients. Drug Class.
get valtrex
Some what you want to know about medicine. Get here.
Meds information for patients. What side effects?
zyban prices
Everything information about medication. Get here.
500 mg levaquin
Cookies store standard information about computer or give access to her, for example, http://www.diywiki.org/index.php/Answered:_Your_Most_Burning_Questions_About_Xxx_2021 unique identifier. Read instantly in your browser using kindle for web.
http://kazino-slotozal.ru/ Slotozal Casino – официальный сайт казино Слотозал
https://www.andthevalleyshook.com/users/figmmg/
doxycycline order online
Locating cheap car Auto insurance policy has actually been a game-changer for my month to month spending plan.
It’s fantastic the amount of you can conserve along
with the appropriate plan.
I recoomend this private security company in Miami.
Meds information sheet. Long-Term Effects.
trazodone medication
Actual about medicament. Get now.
buy doxycycline 100mg canada
finasteride tablets 1mg buy
Я извиняюсь, но, по-моему, Вы ошибаетесь. Пишите мне в PM.
Los tipos de anuncios banners incluyen anuncios en sitios web, publicidad digital, publicidad impresa, http://kastelyfogadositke.hu/index.php/projects/item/35-standart publicidad en aquellos lugares y publicidad en FB y VC, por ejemplo, publicidad en Facebook.
Medicament information. Cautions.
order promethazine
All about pills. Read information here.
where to buy lisinopril
SEOsprint — уникальное место! Оно объединяет самых разных и интересных людей seo sprint
Подтверждаю. И я с этим столкнулся. Давайте обсудим этот вопрос. Здесь или в PM.
Важнейшими направлениями такого партнерства остаются совершенствование предусмотренных международными договорами механизмов контроля над вооружениями, укрепление мер доверия, решение вопросов, которые связаны с нераспространением оружия массового уничтожения, расширением сотрудничества в плане борьбы с терроризмом, http://www.bhardwajacademy.in/2017/01/11/location-the-campus-and-infrastructure/ урегулированием региональных конфликтов.
where can i get zithromax for sale
я ржал
Карась способен жить в водоемах, https://ktb.vn/the-pain-of-college-writing/ где другая рыба немедленно погибнет. Стайная рыба и голубоватым телом и красными плавниками.
buy benemid cheap
Рабочее зеркало Вавада на сегодня, Вавада реальный онлайн vavada вавада фриспины vavada 888 зеркало 3 месяца назад Ссылка на бонус в комментарии Вавада бездепозитный бонус астана, денег надо играй Вавада скачать. Blue . Смотреть / Download Сегодня ищут: Новые видео Вебинар для юниоров Московские мастера черепашки-ниндзя легенды часть 1 Призрак у озера — Трейлер (2023) Салат из помидоров с перцем – Рецепт Бабушки Эммы_2023 03 06_00 51 06_1_889 Котик Дорожник на приеме Учим арабский язык. Урок 34. В поезде. ????? ????? ???????. ????? 34.?? ?????? Download Battlefield V PC CPY Crack + Full Game. (Добавлено: 25.03.2023) Как играть (Добавлено: 25.03.2023) Какой классный мальчик и не стесняется. Настоящий танцовщик, даже штаны не помеха.Это реально круто для его возраста. Такой пухленький, зато как двигается. Не каждый взрослый сможет так станцевать. Серьезный и не улыбнется, выполняет все движения в такт ме. (Добавлено: 25.03.2023) Покажи ей свою любовь посёлок Северный, Воркута Подари близкому воспоминание Зеркало казино Vavada: регистрация в vavada
Играть в игровых автоматах бесплатно и без регистрации Много провайдеров занимаются разработкой слотов. Они создают аппараты, в том числе на русском языке. Разработчики занимаются их настройкой и технической поддержкой. Есть сотни данных студий, но популярны не все. Отличия надежного разработчика от плохого заключаются в хорошем качестве графики и анимации, поддержке различных механик и функций. Пользователям приходится выбирать из тысяч аппаратов. Чтобы упростить эту задачу, стоит ознакомиться с рейтингом, в который вошли топовые релизы популярных провайдеров. В каждый можно поиграть бесплатно. Для ставок используются виртуальные фишки, не имеющие денежной ценности.
Мобильное приложение Vavada Разработчики азартного заведения адаптировали десктопную версию сайта под мобильные устройства. Скачать установочный файл можно с любого рабочего зеркала. Установка займёт не более 2 минут, после чего удастся выполнить вход в профиль, активировать бонусы, запустить любимые развлечения. Но самая главная особенность – круглосуточный доступ к платформе (софт автоматически обходит блокировки).
melhores empresas de sites
ша посотрим
Jokic, Stevo; Tsvetkovic, Aleksandar; Adamovich, Sasha; Ristic, Nenad; Spalevich, petar http://www.zorgboergondisch.nl/nieuws/nieuwe-site/ (2019). “comparative analysis of cryptocurrency wallets compared with traditional wallets.”
Как войти в личный кабинет Игрок открывает официальный сайт Вавада, в верхней части главной страницы которого рядом со значком Регистрация находится иконка Вход. Кликнув на значок Вход, игрок увидит перед собой поля для ввода логина и пароля. После этого зарегистрированный клиент будет автоматически переведен на сайт Вавада в личный кабинет. Незарегистрированному посетителю предложат оформить учетную запись. vavada зеркало на сегодня | обзор официального сайта Вавада: https://admiralplay.ru/
Простые правила игры Правила игры предельно просты. Угадывайте момент и срывайте куш! В Авиатор выигрывают даже новички. Введи при регистрации в vavada код HAPPYPILOT и получи БОНУС 500%!
Регистрация через мобильные устройства vavada позволяет клиентам пользоваться услугой с максимальным комфортом прямо со смартфонов. Вы можете выбрать между скачиванием приложения или использованием версии браузера со схожим дизайном и функциональными возможностями, обе опции доступны на IOS и Android. Вавада официальное приложение — скачать на смартфон. Регистрация через приложение Vavada: Скачайте приложение с официального сайта vavada (нажмите на логотип в виде телефона в левом верхнем углу). Выберите IOS или Android, загрузка начнется автоматически. Выбор между электронной почтой, социальными сетями или номером телефона для создания аккаунта, процесс регистрации аналогичен процедуре на настольном сайте, описанной выше. Если вы не хотите или не можете загрузить приложение, у вас есть возможность присоединиться к Вавада через мобильный браузер. Пользователи Android могут выбрать любой браузер (Google Chrome и другие), а пользователи iPhone должны будут ввести новый адрес для входа в Safari. После завершения регистрации в Vavada новые пользователи будут иметь доступ к услугам vavada в любое время и в любом месте.
colchicine drug interactions
Извиняюсь, но, по-моему, есть другой путь решения вопроса.
?в эти минуты! Под Белгородом бои. «Челси» согласен продать шестерых ради новичков А «Ювентус» сманил игрока https://xn--80abdzaxbkfak2ai0bzf4ce.xn--p1ai/communication/forum/user/38034/ «Манчестер Сити».
Drug information. Effects of Drug Abuse.
singulair without a prescription
All what you want to know about pills. Read now.
Великолепная идея
tap in every place, hit the target, http://vizuskids.com.ua/index.php/konsultatsiia and BOOM! specified maybe difficult to solve task, but it very funny.
Как использовать промокод вавада 2023 при регистрации Обычно поле для введения действующего промокода Vavada появляется тогда, когда игрок проходит этапы взаимодействия с букмекером, то есть — при регистрации. Мы не спроста указали в условиях пополнение счета, так как без первоначального депозита получить бонус не получится. Бонусные средства требуется прокрутить в Казино. Но оно того стоит, ведь бонус при регистрации может быть 6500р.
Данным преимуществом могут воспользоваться граждане России, Беларуси, Украины, Казахстана. Игрок обязательно должен быть старше 18 лет. Регистрацию с промокодом Вавада можно пройти в 1 клик и даже с мобильного телефона. Vavada, официальный сайт букмекерской конторы: https://slotv-kazino.ru/
С нового года в Беларуси повысили налоги на игорный бизнес В 2022 году были внесены изменения в налоговый кодекс Беларуси. В этом году игорный бизнес Беларуси будет выплачивать больше налогов в государственный бюджет. Это повышение инициировано Министерством финансов страны. Первой правкой можно назвать повышение налога на кассу беттинговых компаний. Так, в 2022 году эта выплата составит 1,65 млн белорусских рублей против 1,5 млн белорусских рублей в прошлом году. Изменения коснутся всех легальных букмекеров, в том числе Казино вавада Беларусь. Вторым изменением стала налоговая ставка за кассу тотализатора. В 2022 году необходимо заплатить 2,475 млн белорусских рублей вместо 2,25 млн в прошлом году. Также изменения коснутся и казино. Были изменены налоговые ставки за игровые столы и игровые автоматы. Ставка налога за один игровой стол теперь составляет 7854 белорусских рублей. В прошлом году налог составлял 7140 белорусских рублей. На игровые автоматы налоговая ставка выросла с 240 до 264 белорусских рублей на один игровой автомат. Таким образом, на игровую отрасль в целом были подняты налоговые ставки на 10%. Кроме игорных заведений налоги берутся и с выигрышей игроков. Посетителей облагают налогом на выигрыш в размере 4%. Сумма удерживается оператором, когда клиент обналичивает деньги в кассе. Но повышение налога с выигрыша игроков на данный момент не планируется.
Twitch перманентно забанил стримера казино. Ранее он в шутку объяснил покупку дорогих украшений скамом детей ради сделок с казино Twitch заблокировал стримера, транслирующего казино. Пеманентный бан в случае с Твичом означает «бан на неопределенный срок». Стример имеет право подать апелляцию и быть разбаненным в будущем. Heelmike заявил, что уже подал апелляцию. Стример знаменит в англоязычном сообществе частыми трансляциями криптоказино. В начале декабря во время IRL-трансляции Heelmike так объяснил девушке наличие драгоценной цепочки у себя на шее: «Нравится? Всего лишь было нужно заскамить маленьких детей ради сделок с казино. Ничего плохого». После этого Heelmike заявил, что пошутил и сменил тему разговора. Ранее стример Александр «Frame Tamer» Ермолаев высказался о частых трансляциях казино на Твиче. Лига безопасного интернета хочет запретить Twitch. А кто это и что они уже запрещали? Грустное послание Мэддисона. Объяснил, почему его выгнали из Сербии
Промокод 1хбет на бесплатную ставку –
это специальный код который позволяет
получить бонус от букмекерской конторы 1хбет.
Где вводить промокод на 1хбет Благодаря такому промокоду вы можете сделать бесплатную ставку и выиграть реальные деньги.
Чтобы воспользоваться промокодом нужно зарегистрироваться на сайте 1хбет и ввести его в соответствующем поле.
После этого ваш счет будет пополнен
бонусными средствами которые можно
использовать для размещения ставок.
Промокоды могут быть различными – например они могут предоставлять бесплатную
ставку на определенное спортивное событие или давать скидку на комиссию
букмекерской конторы. В любом случае
промокоды позволяют получить дополнительные преимущества
при игре. Если вы хотите сделать бесплатную
ставку и увеличить свои шансы на выигрыш
не забудьте воспользоваться промокодом 1хбет.”
Должен Вам сказать Вы заблуждаетесь.
из всего этого следует что существуют неодинаковые способы доставки, перевозки грузов, https://commubridge.com/community/profile/katlyn08z25957/ но авиаперевозки грузов считаются самыми быстрыми.
https://www.google.tm/url?q=https://didvirtualnumbers.com/zh/
Drug prescribing information. What side effects can this medication cause?
how can i get kamagra
Some what you want to know about meds. Read information here.
This is a topic that is near to my heart… Thank you! Where are your contact details though?
Казино Сколько не видел мемов и видосов про Казино, но этот видос вижу впервые, и это ебаный шедевр. Спасибо тебе! Развернуть ветку Аккаунт удален Развернуть ветку Развернуть ветку Закину и я парочку Развернуть ветку Лучший мем про Цивилизацию после мемов про ядерного Ганди Развернуть ветку Развернуть ветку Игрокам в Warframe посвящается – Ёбаный рот этого куваказино, блядь! Ты кто такой, сука, чтоб это роллить? – Я всегда это роллил, когда.. – ВЫ ЧЁ, ДЕБИЛЫ? Вы чё, ебанутые, что ли? Действи.. вы в натуре ебанутые? Эта сидит там, чешет поглотитель кувы, блядь. Этот стоит, грит: Я те щас минус мультишот рольну.. – Ну посмотрите.. – ЁБ ТВОЮ ЛОТУС! У вас кават есть, чтобы бафать куву на моих глазах, мудак ёбаный! – Хорошо, будет делать кот. Раньше это делал всегда бустер.. – КУВАЛАНСЕР ЕБУЧИЙ! Вот пока ты это делал, дебил, ебаная сука, БЛЯДЬ, так все и происходило! – В кувакрепости? – В ХУЕПОСТИ! Блядь, вы чё, действительно клоны гринирские, что ли, а? Бля, теннодегенераты какие-то, ёбаный ваш кувасос, а.. А ты-то чё делаешь? – Роллы по 3500 просто.. – ЁБАНЫЙ ТВОЙ РОТ! КАКОГО ХУЯ У ВАС РОЛЛЫ ПО 3500? Ты мод разлома открыла на моих глазах, БЛЯДЬ! Как они там могут быть роллы по 3500?! – 3500 кувы! Вот смотрите.. – ЁБАНЫЙ ТВОЙ РОТ, БЛЯДЬ! Вы чё, в Тау их заряжаете?! Сука ёбаная, падла блядская! – Орокин.. – ТЫ, МУДИЛА КУВЯНАЯ! Как анвейл.. Как открытый мод разлома может быть.. по 3500 роллиться?! Ты, сентиент ёбаный! – Докажу! докажу! – ТЫ, МУДИЛА ОРОКИНСКАЯ, ВЫ КАК РОЛЛИТЕ, СУКА ЁБАНАЯ, ПАДЛА?! – Вот смотрите.. – Я РОТ ТВОЙ ЕБАЛ! Так вы анвейлите.. вы, БЛЯДИ, получайте моды разлома не на алертах! Вы чё, ебанутые, сука?! – С вылазки в таком их виде.. – ТЫ ГРИНИРОВЕЦ! Как может в куваказино быть ривен.. мод разлома роллиться по 3500?! Ты чё, бредишь, что ли?! Ёбаный твой рот, а. – Так вот и роллиться.. – ТЫ ЧЁ, БРЕДИШЬ, ЧЕРВЬ?! – Успокойтесь.. Вот, посмотрите, какой ролл.. – БЛЯДЬ! ДЕГЕНЕРАТИВНЫЙ ТЕННО! Ты бредишь, что ли?! Ты чё, бредишь, блядь?! Как в куваказино могут быть быть минус мультишот плюс зум?! Ты чё, сентиент, блять? – Если я рольну вот так вот, да. – Ёбаный кондрок! Ай фак ю булщит! ЩИТ! – Вы специально.. – Я специально! Я щас им расскажу, что вы тут исполняете! Вы чё, сентиенты, блядь?! – Как вы хотите. – ВЫ ЧЁ, СЕНТИЕНТЫ, СУКА?! Как в куваказино в запечатанном моде разлома может быть 10 роллов?! Вы чё?! – Посмотрите.. – ТЫ, МУДИЛО КУВЯНОЕ! Вы их где берете, бляди?! – Получаем на вылазках.. – ВЫ МУДИЛЫ!! Вы чё, е.. блять.. Ёб твою мать, в куваказино, сука, роллы по 3500 на минус дамаг.. ТЫ ЧЁ, СЕНТИЕНТ, ЕБАНЫЙ ТВОЙ РОТ, А?! Ты чё, вомвалист, что ли? – Как вы хотели, скажите мне? Как вы хотите? – Ты, дегенеративный тенно, ты не понимаешь, что ты говоришь вообще! – Что есть, то и говорю.. – Ты говоришь, что в куваказино в анвейл ривенах плюс зум по 3500?! – Да, смотрите. Плюс длительность статуса не на месте.. Игровой онлайн-слот Divine Fortune в казино Вавада Вавада официальное зеркало сайта
вавада казино онлайн 24/7 с вами на связи Добро пожаловать в службу технической поддержки онлайн-казино, единственное место в Интернете, где вы можете получить помощь по техническим вопросам, связанным с онлайн-казино. Мы – команда высококвалифицированных и опытных экспертов казино, готовых помочь вам в решении любых проблем. У нас большой опыт работы с онлайн-казино, и мы уверены, что сможем помочь вам решить вашу проблему максимально быстро и эффективно. В службе технической поддержки онлайн-казино мы понимаем, что не все являются техническими экспертами. Именно поэтому у нас есть широкий выбор статей и руководств, которые помогут вам решить проблему в кратчайшие сроки. Если вам нужна помощь, просто свяжитесь с нами, и один из наших опытных технических специалистов будет рад помочь вам. Мы будем рады помочь вам во всех вопросах, связанных с технической поддержкой онлайн-казино! Наша опытная и дружелюбная команда всегда готова помочь вам устранить любые неполадки, и мы находимся всего лишь на расстоянии телефонного звонка или электронного письма, если мы вам понадобимся. Мы знаем, что иногда в азартных играх онлайн все может пойти не так. Именно поэтому мы хотим убедиться, что вы получите всю необходимую поддержку, чтобы извлечь максимум пользы из своего опыта. Мы знаем, как бывает обидно, когда что-то работает не так, как должно, и мы сделаем все возможное, чтобы вернуть вас в нормальное русло. Свяжитесь с нами в любое время дня и ночи, и мы будем рады помочь.
Найкращі онлайн казино в Україні: рейтинги Оскільки новачкам спочатку дуже складно визначитися з найкращою ігровою платформою, яка надає доступ до вигідних азартних форматів та умов заробітків, ми створили рейтинг з урахуванням об’єктивних параметрів азартних сайтів. З ним ви зможете визначити портали, які дійсно заслуговують уваги та надають можливості примноження капіталу. Після ознайомлення з рейтингом варто перейти на офіційний сайт казино, який вам сподобався. Далі навіть без реєстрації можливо проаналізувати плюси, мінуси, доступні ігрові формати, умови грошових операцій тощо.ФавбетЛіцензійний ігровий портал, який відкриває доступ до заробітків за умови поповнення рахунку мінімум на 25?. Всім навичкам пропонують примноження капіталу через бонусні програми. Після нарахування на депозит 4000? або 100 відсотків від суми поповнення ви зможете використати цей подарунок для тестування різних форматів гемблінга на сайті. Сайт є державним, оскільки має ліцензію в Україні. З 2021 року портал функціонує легально та може запропонувати найкращі формати гемблінга. Запуск ігрових автоматів доступний від 1?. На депозиті має бути 100? для можливості виведення грошей. На бонусні заохочення адміністратори встановлюють оптимальні значення вейджерів, тому відіграти їх досить просто.СлотоКінгЦікавий сайт для доступу до найкращих провайдерів та їх розробок. Запуск ігрових автоматів можливий від 1?. Мінімальне поповнення рахунку складає лише 50?. Ліцензію казино отримала в 2021р. Максимальна сума вітального пакета складає 24 000?. Множник для відіграшу становить 18. Після переходу на офіційний сайт ви можете визначитися з доступними бонусами та встановити їх переваги. Казино належить до категорії надійних порталів, які не передбачають ризиків порушення умов конфіденційності та правил чесних заробітків.СлотсСітіКомпанія представлена не лише в онлайн форматі, але й у вигляді наземних казино. Вітальний пакет для новачків становить до 35 000 ? та 250 безкоштовних обертів барабанів. Після нарахування реєстраційного бонусу є можливість поповнити рахунок на суму від 200 ?. Далі ви зможете обертати барабани зі ставками від 1?. На офіційному сайті зафіксовані всі правила, яких має дотримуватися клієнт. Інакше менеджери можуть заблокувати доступ до контенту. Бонусна система розгалужена та розрахована не лише на новачків, але й на активних гравців.ПокерМатчЦікавий формат гемблінга, який з першої хвилини здатний зацікавити новачків. Вітальний пакет примножує стартове поповнення в сотні разів. Мінімальна сума внеску складає 50?. Запускати слоти можливо від 1?. Для виведення грошей з рахунку ви маєте прив’язати платіжну систему та вказати суму від 250?. Не лише новачкам, але й активним гравцям передбачені різні формати заохочень.КосмолотКосмічна назва цього казино вже говорить про цікаве оформлення, безліч бонусів та найкращі умови для гри. Ви можете зареєструватися на сайті та поповнити рахунок від 50 гривень. Далі оберти барабанів можливі на суму від 1?. Наявність державної української ліцензії робить віртуальний клуб досить популярним серед шанувальників якісного гемблінгу. Новачкам нараховують 100 відсотків від суми поповнення відразу за умови внеску від 200?. Це орієнтовний перелік кращих платформ, які зустрічаються в оглядах на постійній основі. Попри появу різноманіття сучасних порталів ці віртуальні клуби намагаються завжди вдосконалювати азартний софт, пропонувати різні системи грошових заохочень, розіграші тощо. Більше інформації ви знайдете саме на офіційний веб-ресурсах.
Дополнительные возможности В разделе «Результаты» расположен полноценный матч-центр с обновляемыми статистическими данными. Здесь большой объем информации по событиям разных видов спорта и турниров. Можно просматривать информацию в режимах прематч и Live. Для текущих матчей предлагается матч-трекер с анимацией. Отображаются основные события встречи. Также доступна статистическая сводка. Клиенты Казино могут пользоваться функцией «Ставка в один клик». Указав в настройках сумму пари, можно оформлять ставки за несколько секунд, что удобно при интенсивном беттинге (например, в режиме Live). Казино Вавада Vavada официальный сайт и зеркало – blank booking agency Vavada официальный сайт регистрация
Пятнашка Тото «Пятнашка» – это самый популярный тотализатор Казино Vavada, ведь здесь игроки смогут получить наиболее высокий выигрыш. Всего сюда входит 15 классических событий, по самым разным видам спорта. Но преимущественно это футбол и хоккейные матчи. Победить здесь крайне сложно, так как все спортивные события формируются случайным образом, и делает это сама Казино. Поэтому выбрать для себя наиболее подходящий вид спорта, в котором игрок разбирается, не получится. Сама игра очень схожа с лотереей, ведь здесь пользователи так же разыгрывают общий призовой фонд, который был накоплен участниками. Как правило, основной джекпот составляет более 500 тысяч евро, что позволяет стать миллионером каждому победителю. Тем более, необходимо угадать не все 15 исходов, так как достаточно и 9, но в этом случае выигрышная сумма будет гораздо меньше. Условия игры «Пятнашка» выглядят следующим образом: Призовой фонт определяют сами игроки, в зависимости от их количества, а так же от размеров внесенных средств на ставки, Игра «Пятнашка» проводится каждый день, изменяя при этом все спортивные события, Для победы достаточно угадать исход в 9 событиях из 15, Размер выигрыша зависит от числа правильно угаданных событий, Большую часть призового фонда забирает игрок, который удачно определил все 15 исходов,
Кэшбек 10% кешбэк выдается каждый месяц игрокам, которые оказались в проигрыше перед онлайн казино. В рамках действующей акции клиентам казино частично возвращаются деньги, потраченные на неудачные ставки. Сумма кешбэка – это разница между ставками и выигрышами. Если гемблеру удалось выиграть больше, чем проиграть, деньги не начисляются. В противном случае его ждет компенсация 1 числа ежемесячно. Отчетный период начинается с даты выдачи последнего кешбэка. Клиенты Леонбетс могут как активировать частичный возврат, так и отказаться от него с помощью интерфейса в личном кабинете. В случае активации кешбэк начисляется на бонусный баланс, а следующие ставки, сделанные игроком, учитываются в отыгрыше. Для вывода возвращенной суммы ее необходимо отыграть с вейджером х5. Не активированный кешбэк не имеет срока действия.
конечно грустно… Ведь у некоторых так бывает…
1-комнатная квартира. Рядом Баянтау, Батырмол, Ярмарка, Артур, остановки, транспортная доступность во все направления города, posutkamminsk.by чистая и уютная квартира.
Pills information for patients. Short-Term Effects.
sildigra pill
Actual news about medicines. Read information now.
porn 24
Играть в казино Das Ist Casino Онлайн казино Das Ist Casino было создано в 2017 году. Обладает лицензией Malta. Работает для игроков из 266 стран. Валюты аккаунта – Доллар США, Российский рубль, Евро, Норвежская крона, Канадский доллар. Подключено 4 платежных систем, а минимальный депозит составляет 20 USD. Техподдержка говорит на русском и английском языках. Казино раздает бонусы новым и действующим клиентам. Можно получить: бесплатные спины, бонус на депозит, приветственный бонус. Год регистрации 2017 Управляющая компания N1 Interactive Ltd., зарегистрированная на о. Мальта Валюта баланса EUR, RUB Разрешенные страны Россия Украина Казахстан Аландские острова Германия Доминиканская Республика Европа Китай Крым Кюрасао ОАЭ Папуа-Новая Гвинея Польша Сейшельские острова Туркменистан Япония +12 стран Скрыть страны Недоступно в странах Испания Италия США Язык общения с саппортом Английский, Немецкий, Польский, Русский Виды софта –> Интернет казино gaminatorslots. Игровой клуб gmslots Vavada: Vavada официальное зеркало
vavada, Курск Казино Vavada ведет деятельность в области Казино / Лотерей и находится в Курске по адресу Энтузиастов проспект, 1Б. Режим работы Пн-Вс 00:00-24:00 можно уточнить по телефону +7 (800) 555-51-81
vavada бездепозитный бонус Среди промо-предложений игрового клуба Vavada особенно выгодным является бездепозитный бонус. Это удобная возможность для игроков получить небольшую сумму денег на ставки, не рискуя при этом собственным балансом. Правила бездепозитного бонуса часто меняются, так что лучше уточнить заранее условия получения и отыгрыша денег без пополнения счета. Как и другие бонусы казино Вавада, эту промо-награду сначала необходимо отыграть, и только потом соответствующая сумма будет переведена на основной баланс.
doxycycline shop
where can i get cheap mobic without prescription
Odbierz prezent 100 zl bonus bez depozytu. Nowe zwyciestwa czekaja!
Как делать ставки? Чтобы сделать ставку, заходим на страницу матча и выбираем подходящий коэффициент. Нажимаем на него. Появляется всплывающее меню, где нужно указать сумму. Выбор исхода и суммы ставки Для одиночных ставок сразу нажимаем «Поставить». Для экспресса или системы добавляем несколько событий в купон, а уже потом переходим на его страницу. Она выглядит так: Процедура заключения пари После добавления событий проверьте сумму пари и нажмите «Поставить». Останется дождаться окончания турнира и расчёта ставок. Казино икс: Рабочее зеркало на сегодня – X официальное зеркало сайта
Играть в игровые автоматы в демо-режиме Пользователи могут играть в игровые автоматы в казино Боб бесплатно и без регистрации. Играть бесплатно Kensei Blades Играть бесплатно Alkemor’s Elements Играть бесплатно Gemini Joker Играть бесплатно Viking Gods: Thor and Loki
Швеция Ожидается, что за две прямые путёвки на Евро-2024 в группе F сборная Швеции сразится с Бельгией и Австрией. В первом туре «три короны» примут одного из своих конкурентов. Шведы с 41-летним Златаном Ибрагимовичем в составе рассчитывают на мажорной ноте начать отборочный цикл. Кто победит? Получи беспроигрышную ставку 2000 рублей!
ремонт стиральных машин в самаре на дому
Не работает стиральная машина – мы отремонтируем!
Хай, хочу предложить вам жирные ссылки в размере 250 на ваш сайт – купить можно на сайте https://kwork.ru/links/11052138/stateynoe-prodvizhenie-250-statey-na-trastovykh-saytakh-iks-do-38-000
Drug information for patients. Cautions.
buy generic lopressor
Actual trends of medication. Get here.
Хи-хи
The use of crypto currencies makes http://www7b.biglobe.ne.jp/%7Eeasy_trekker/cgi-bin/board_main/board_main.cgi platforms a target for hack.
Don’t trust it scam site. You’ll be cheated here.
Да, действительно.
better to say: on a reel machine, http://west-village.main.jp/CGI/clipbbs/clipbbs.cgi, the chances are more favorable if the player plays with maximum the number of coins available.
Здравствуйте, хочу предложить вам трастовые ссылки в размере 250 на ваш сайт – купить можно на сайте [url=https://kwork.ru/links/11052138/stateynoe-prodvizhenie-250-statey-na-trastovykh-saytakh-iks-do-38-000]https://kwork.ru/links/11052138/stateynoe-prodvizhenie-250-statey-na-trastovykh-saytakh-iks-do-38-000[/url]
buy doxycycline for acne
Medication prescribing information. Drug Class.
rx neurontin
Best information about pills. Get information here.
Don’t trust this fraudulent site. They’ll trick you.
Разовая чистка снега с крыш и абонентское обслуживание в зимний период очистка кровли от снега
Привет, хочу предложить вам крауд ссылки в размере 250 на ваш сайт – купить можно на сайте https://kwork.ru/links/11052138/stateynoe-prodvizhenie-250-statey-na-trastovykh-saytakh-iks-do-38-000
Виртуальные VPS серверы Windows
Абузоустойчивый серверы, идеально подходит для работы програмным обеспечением как XRumer так и GSA
Стабильная работа без сбоев, высокая поточность несравнима с провайдерами в квартире или офисе, где есть ограничение.
Высокоскоростной Интернет: До 1000 Мбит/с
Скорость интернет-соединения – еще один важный параметр для успешной работы вашего проекта. Наши VPS/VDS серверы, поддерживающие Windows и Linux, обеспечивают доступ к интернету со скоростью до 1000 Мбит/с, обеспечивая быструю загрузку веб-страниц и высокую производительность онлайн-приложений.
where to buy generic zithromax without dr prescription
kalugastirmash.ru
Мастер с опытом ремонта бытовой техники более 5 лет.
Medicine information sheet. What side effects can this medication cause?
cleocin buy
Some about meds. Read here.
https://pedagog-razvitie.ru/filosofy_psihologii_snamenitiye_imena/zh-lametri-i-prohazk-ch-bell-i-f-mazhandi/
Вы попали в самую точку. Это отличная мысль. Готов Вас поддержать.
https://sunyzf6r.blog.ss-blog.jp/2009-01-18
https://pedagog-razvitie.ru/logika/iz-istorii-logiki/
Привет, хочу предложить вам мощные ссылки в размере 250 на ваш сайт – купить можно на сайте https://kwork.ru/links/11052138/stateynoe-prodvizhenie-250-statey-na-trastovykh-saytakh-iks-do-38-000
RG Nhà Cái
Drug information for patients. Short-Term Effects.
can you get diltiazem
Best news about drugs. Read here.
albuterol nebulizer
Drug information for patients. Effects of Drug Abuse.
avodart otc
Best about drug. Read here.
cleocin reviews
cost cheap lexapro tablets
Хай, хочу предложить вам крауд ссылки в размере 250 на ваш сайт – купить можно на сайте https://kwork.ru/links/11052138/stateynoe-prodvizhenie-250-statey-na-trastovykh-saytakh-iks-do-38-000
order generic lexapro without prescription
Хай, хочу предложить вам мощные ссылки в размере 250 на ваш сайт – купить можно на сайте https://kwork.ru/links/11052138/kraud-prodvizhenie-250-statey-na-trastovykh-saytakh-iks-do-38-000
I reccomend this product Killa snusto all.
Я думаю, что Вы не правы. Пишите мне в PM, обсудим.
подписывайтесь на вызов» – имейл-рассылку от создателей http://22-91.ru/biografiya/prodolzhenie-dinastii-kompozitorov-maksim-dunaevskijj/14.01.2015 «Медузы». защита от спама recaptcha. Политика и властные структуры, бизнес и недвижимость, путешествия или автомобили, бюджет и фриланс, мегаполис и досуг – вот лишь только определенные из тем, которые освещает ведущее петербургское сетевое общественно-политическое издание.
Оцифровка архивных документов — это наше направление. Мы предоставляем услуги перевода на цифровой носитель с использованием технологических инноваций. Сотрудничество с нами — это эффективный способ сделать вашу документацию доступной в электронной форме.
Medication prescribing information. Long-Term Effects.
nexium tablet
Everything trends of medicine. Get now.
how can i get generic benemid no prescription
Meds information leaflet. What side effects can this medication cause?
cipro
Best trends of drug. Get here.
side effects of stopping gabapentin
Drugs information. What side effects can this medication cause?
neurontin
All news about drugs. Read here.
Хай, хочу предложить вам крауд ссылки в размере 250 на ваш сайт – купить можно на сайте https://kwork.ru/links/11052138/kraud-prodvizhenie-250-statey-na-trastovykh-saytakh-iks-do-38-000
オンラインカジノレビュー
オンラインカジノレビュー:選択の重要性
オンラインカジノの世界への入門
オンラインカジノは、インターネット上で提供される多様な賭博ゲームを通じて、世界中のプレイヤーに無限の娯楽を提供しています。これらのプラットフォームは、スロット、テーブルゲーム、ライブディーラーゲームなど、様々なゲームオプションを提供し、実際のカジノの経験を再現します。
オンラインカジノレビューの重要性
オンラインカジノを選択する際には、オンラインカジノレビューの役割が非常に重要です。レビューは、カジノの信頼性、ゲームの多様性、顧客サービスの質、ボーナスオファー、支払い方法、出金条件など、プレイヤーが知っておくべき重要な情報を提供します。良いレビューは、利用者の実際の体験に基づいており、新規プレイヤーがカジノを選択する際の重要なガイドとなります。
レビューを読む際のポイント
信頼性とライセンス:カジノが適切なライセンスを持ち、公平なゲームプレイを提供しているかどうか。
ゲームの選択:多様なゲームオプションが提供されているかどうか。
ボーナスとプロモーション:魅力的なウェルカムボーナス、リロードボーナス、VIPプログラムがあるかどうか。
顧客サポート:サポートの応答性と有効性。
出金オプション:出金の速度と方法。
プレイヤーの体験
良いオンラインカジノレビューは、実際のプレイヤーの体験に基づいています。これには、ゲームプレイの楽しさ、カスタマーサポートへの対応、そして出金プロセスの簡単さが含まれます。プレイヤーのフィードバックは、カジノの品質を判断するのに役立ちます。
結論
オンラインカジノを選択する際には、詳細なオンラインカジノレビューを参照することが重要です。これらのレビューは、安全で楽しいギャンブル体験を確実にするための信頼できる情報源となります。適切なカジノを選ぶことは、オンラインギャンブルでの成功への第一歩です。
lexapro sleep
オンラインカジノとオンラインギャンブルの現代的展開
オンラインカジノの世界は、技術の進歩と共に急速に進化しています。これらのプラットフォームは、従来の実際のカジノの体験をデジタル空間に移し、プレイヤーに新しい形式の娯楽を提供しています。オンラインカジノは、スロットマシン、ポーカー、ブラックジャック、ルーレットなど、さまざまなゲームを提供しており、実際のカジノの興奮を維持しながら、アクセスの容易さと利便性を提供します。
一方で、オンラインギャンブルは、より広範な概念であり、スポーツベッティング、宝くじ、バーチャルスポーツ、そしてオンラインカジノゲームまでを含んでいます。インターネットとモバイルテクノロジーの普及により、オンラインギャンブルは世界中で大きな人気を博しています。オンラインプラットフォームは、伝統的な賭博施設に比べて、より多様なゲーム選択、便利なアクセス、そしてしばしば魅力的なボーナスやプロモーションを提供しています。
安全性と規制
オンラインカジノとオンラインギャンブルの世界では、安全性と規制が非常に重要です。多くの国々では、オンラインギャンブルを規制する法律があり、安全なプレイ環境を確保するためのライセンスシステムを設けています。これにより、不正行為や詐欺からプレイヤーを守るとともに、責任ある賭博の促進が図られています。
技術の進歩
最新のテクノロジーは、オンラインカジノとオンラインギャンブルの体験を一層豊かにしています。例えば、仮想現実(VR)技術の使用は、プレイヤーに没入型のギャンブル体験を提供し、実際のカジノにいるかのような感覚を生み出しています。また、ブロックチェーン技術の導入は、より透明で安全な取引を可能にし、プレイヤーの信頼を高めています。
未来への展望
オンラインカジノとオンラインギャンブルは、今後も技術の進歩とともに進化し続けるでしょう。人工知能(AI)の更なる統合、モバイル技術の発展、さらには新しいゲームの創造により、この分野は引き続き成長し、世界中のプレイヤーに新しい娯楽の形を提供し続けることでしょう。
この記事では、オンラインカジノとオンラインギャンブルの現状、安全性、技術の影響、そして将来の展望に焦点を当てています。この分野は、技術革新によって絶えず変化し続ける魅力的な領域です。
Tải Hit Club iOS
Tải Hit Club iOSHIT CLUBHit Club đã sáng tạo ra một giao diện game đẹp mắt và hoàn thiện, lấy cảm hứng từ các cổng casino trực tuyến chất lượng từ cổ điển đến hiện đại. Game mang lại sự cân bằng và sự kết hợp hài hòa giữa phong cách sống động của sòng bạc Las Vegas và phong cách chân thực. Tất cả các trò chơi đều được bố trí tinh tế và hấp dẫn với cách bố trí game khoa học và logic giúp cho người chơi có được trải nghiệm chơi game tốt nhất.
Hit Club – Cổng Game Đổi Thưởng
Trên trang chủ của Hit Club, người chơi dễ dàng tìm thấy các game bài, tính năng hỗ trợ và các thao tác để rút/nạp tiền cùng với cổng trò chuyện trực tiếp để được tư vấn. Giao diện game mang lại cho người chơi cảm giác chân thật và thoải mái nhất, giúp người chơi không bị mỏi mắt khi chơi trong thời gian dài.
Hướng Dẫn Tải Game Hit Club
Bạn có thể trải nghiệm Hit Club với 2 phiên bản: Hit Club APK cho thiết bị Android và Hit Club iOS cho thiết bị như iPhone, iPad.
Tải ứng dụng game:
Click nút tải ứng dụng game ở trên (phiên bản APK/Android hoặc iOS tùy theo thiết bị của bạn).
Chờ cho quá trình tải xuống hoàn tất.
Cài đặt ứng dụng:
Khi quá trình tải xuống hoàn tất, mở tệp APK hoặc iOS và cài đặt ứng dụng trên thiết bị của bạn.
Bắt đầu trải nghiệm:
Mở ứng dụng và bắt đầu trải nghiệm Hit Club.
Với Hit Club, bạn sẽ khám phá thế giới game đỉnh cao với giao diện đẹp mắt và trải nghiệm chơi game tuyệt vời. Hãy tải ngay để tham gia vào cuộc phiêu lưu casino độc đáo và đầy hứng khởi!
В этом что-то есть. Понятно, благодарю за информацию.
https://unmona.com/%d0%b8%d0%bc%d0%b8%d1%82%d0%b8%d1%80%d0%be%d0%b2%d0%b0%d0%bd%d0%bd%d0%b0%d1%8f-%d0%b8%d0%ba%d1%80%d0%b0-%d0%b8%d0%b7-%d1%87%d0%b5%d0%b3%d0%be-%d0%b5%d1%91-%d0%b4%d0%b5%d0%bb%d0%b0%d1%8e%d1%82-%d0%bf/
Pills information. Generic Name.
retrovir
Some what you want to know about medicine. Get information here.
where buy cheap avodart without rx
Drug information leaflet. Short-Term Effects.
nexium generics
Actual about pills. Get information now.
buying lisinopril
Medicine information leaflet. Drug Class.
cordarone
Some trends of drug. Read now.
buy cheap tadacip prices
Bundling home and automotive insurance coverage aided me even the score less costly Car insurance companies in Palos Hills
insurance. Bundling policies can cause notable savings.
doxycycline 40mg modified release capsules
levaquin price at publix
Medicines prescribing information. Long-Term Effects.
cost retrovir
Some news about drug. Get information now.
buy prednisone online
オンラインカジノ
オンラインカジノとオンラインギャンブルの現代的展開
オンラインカジノの世界は、技術の進歩と共に急速に進化しています。これらのプラットフォームは、従来の実際のカジノの体験をデジタル空間に移し、プレイヤーに新しい形式の娯楽を提供しています。オンラインカジノは、スロットマシン、ポーカー、ブラックジャック、ルーレットなど、さまざまなゲームを提供しており、実際のカジノの興奮を維持しながら、アクセスの容易さと利便性を提供します。
一方で、オンラインギャンブルは、より広範な概念であり、スポーツベッティング、宝くじ、バーチャルスポーツ、そしてオンラインカジノゲームまでを含んでいます。インターネットとモバイルテクノロジーの普及により、オンラインギャンブルは世界中で大きな人気を博しています。オンラインプラットフォームは、伝統的な賭博施設に比べて、より多様なゲーム選択、便利なアクセス、そしてしばしば魅力的なボーナスやプロモーションを提供しています。
安全性と規制
オンラインカジノとオンラインギャンブルの世界では、安全性と規制が非常に重要です。多くの国々では、オンラインギャンブルを規制する法律があり、安全なプレイ環境を確保するためのライセンスシステムを設けています。これにより、不正行為や詐欺からプレイヤーを守るとともに、責任ある賭博の促進が図られています。
技術の進歩
最新のテクノロジーは、オンラインカジノとオンラインギャンブルの体験を一層豊かにしています。例えば、仮想現実(VR)技術の使用は、プレイヤーに没入型のギャンブル体験を提供し、実際のカジノにいるかのような感覚を生み出しています。また、ブロックチェーン技術の導入は、より透明で安全な取引を可能にし、プレイヤーの信頼を高めています。
未来への展望
オンラインカジノとオンラインギャンブルは、今後も技術の進歩とともに進化し続けるでしょう。人工知能(AI)の更なる統合、モバイル技術の発展、さらには新しいゲームの創造により、この分野は引き続き成長し、世界中のプレイヤーに新しい娯楽の形を提供し続けることでしょう。
この記事では、オンラインカジノとオンラインギャンブルの現状、安全性、技術の影響、そして将来の展望に焦点を当てています。この分野は、技術革新によって絶えず変化し続ける魅力的な領域です。
abilify for lewy body dementia
Meds information. Long-Term Effects.
pregabalin
Best news about medicine. Read information here.
http://moslomtorg.ru
Zaytoven
can i buy mobic without a prescription
Извините, сообщение удалено
При художественной обработке могут использоваться не только лишь драгоценные, https://iron-art.kiev.ua/kolesootboyniki-metallicheskie/ но и недрагоценные металлические сплавы. Узнать вес арматуры другая на стадии покупки позволит простая операция: надо собрать общую длину прутьев и умножить на массу одного погонного метра.
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Виртуальные сервера (VPS/VDS) и Дедик Сервер: Оптимальное Решение для Вашего Проекта
В мире современных вычислений виртуальные сервера (VPS/VDS) и дедик сервера становятся ключевыми элементами успешного бизнеса и онлайн-проектов. Выбор оптимальной операционной системы и типа сервера являются решающими шагами в создании надежной и эффективной инфраструктуры. Наши VPS/VDS серверы Windows и Linux, доступные от 13 рублей, а также дедик серверы, предлагают целый ряд преимуществ, делая их неотъемлемыми инструментами для развития вашего проекта.
gabapentin goodrx
Drugs prescribing information. Drug Class.
zofran
Some trends of medicament. Read here.
trazodone drug class
хостинг сайта
Когда речь заходит о создании своего собственного сайта, выбор хостинга играет огромную роль. Ведь именно хостинг будет определять доступность и быстродействие вашего сайта для пользователей. Если вы находитесь в Беларуси и ищете надежного хостинг-провайдера, то BestHost.BY – это отличный выбор. BestHost.BY – одна из ведущих хостинг-компаний в Беларуси, предоставляющая высококачественные услуги уже на протяжении 15 лет.
doxycycline 100mg buy
can i buy mobic online
Drug information leaflet. What side effects can this medication cause?
neurontin rx
Best trends of meds. Get here.
Medicament information. Cautions.
cialis soft otc
Everything trends of medication. Get now.
buying lisinopril in los algodones
Medication prescribing information. Short-Term Effects.
get viagra
Everything about medicines. Read here.
albuterol generic name
buy levaquin from canada
Вы не правы. Я уверен. Пишите мне в PM, поговорим.
Вне соцсети потенциал монетизации блога невелик. Монетизация занимает счёт прямых рекламодателей, http://vino.koeln/?p=1075 интерес которых прямо пропорционален количеству подписчиков канала.
Medication information sheet. Long-Term Effects.
buy generic tadacip
Some what you want to know about drug. Get here.
Watch porn
1xbet официальный сайт – это популярная букмекерская компания, предлагающая широкий выбор ставок на спорт, казино и многое другое. С высокими коэффициентами и удобным интерфейсом, 1xbet привлекает множество игроков. Он также предоставляет возможность онлайн-трансляций событий. 1xbet создает захватывающий игровой опыт для своих пользователей.
buy lisinopril blood pressure medicine
Почему важно выбирать лицензионное казино Сегодня игрокам доступно множество разных казино. Некоторые из них имеют лицензию, а другие нет. И, на первый взгляд кажется, что лицензия — это не самое важное, на что нужно обращать внимание при выборе площадки, но это не совсем так. Мы расскажем вам о том, почему важно выбирать лицензию, а также о том, какая лицензия на сайте PokerDom. ПокерДом казино – официальный сайт клуба pokerdom https://komedia-del-arte.ru/
Ставки на pokerdom dota 2 в лайве (лайфе, ливе) Здесь вас ждут развлечения, в которых участвуют на произвольные команды – 2 бота. Вы можете зайти в меню и смотреть прямые трансляции их сражений в режиме лайва. Для этого не придется регистрироваться, пополнять счет, ставить минимальную сумму.
pokerdom официальный сайт Казино ПокерДом – это международная организация, которая была основана в 1997 году. Букмекер работает по лицензии, выданной в Кюрасао. Свою деятельность в Интернете контора начала в 2011 году. Промокод на 32000 рублей 6500officiales Скопировать В клиентской базе насчитывается больше 500 тысяч игроков. pokerdom приложение поддерживает работу на 36 языках. Для удобства беттеров существует около 1000 наземных ППС. Причина популярности букмекера связана с высокими коэффициентами, которые выгодно отличаются от тех же показателей у конкурентов.
finasteride purpose
Скачать приложения на Андроид бесплатно без регистрации https://apkhub.ru/
Medicament information. What side effects?
singulair
Some information about drug. Read now.
furosemide tablets
Жаль, что сейчас не могу высказаться – очень занят. Вернусь – обязательно выскажу своё мнение.
чтоб выяснить причину и разблокировать страницу, https://casinocrit.pro/ необходимо написать сообщение операторам через интернет-адрес или прозвонить по цифрам горячей линии.
antibiotic for skin infection doxycycline
https://v-mig.ru/kofe-poleznye-svojstva-kotorye-dolzhen-znat-kazhdyj/
Optimize your app or game by the best free App Store Optimization Transforming the Digital Landscape
Medicine information sheet. Brand names.
nexium for sale
Actual what you want to know about meds. Read now.
1хбет зеркало рабочее – это популярная букмекерская компания, предлагающая широкий выбор ставок на спорт, казино и многое другое. С высокими коэффициентами и удобным интерфейсом, 1xbet привлекает множество игроков. Он также предоставляет возможность онлайн-трансляций событий. 1xbet создает захватывающий игровой опыт для своих пользователей.
выбрать сервер
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Высокоскоростной Интернет: До 1000 Мбит/с**
Скорость интернет-соединения – еще один важный момент для успешной работы вашего проекта. Наши VPS серверы, арендуемые под Windows и Linux, предоставляют доступ к интернету со скоростью до 1000 Мбит/с, обеспечивая быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
В нашем каталоге Вы найдете широкий ассортимент лодок ПВХ, моторов и комплектующих: лодка с надувным дном
Очень хорошая фраза
проблематично получить ком.plex или дорогое дгу с обычными телефонными системами. google voice поддерживает windows, ios, http://dencmc.com/%d8%a7%d9%82%d8%aa%d8%b5%d8%a7%d8%af_%d8%b1%d9%88%d8%a7%d9%86%d8%af%d8%a7/ андроид и macos.
https://pedagog-razvitie.ru/interest_stati/professionalnye-uslugi-po-napisaniyu-otchetov/
can i buy prednisone from canada without a script
buy prednisone without prescription canadian pharmacy
If some one needs expert view about blogging then i recommend him/her to go to see this webpage,
Keep up the nice work.
Medicament information. Effects of Drug Abuse.
diltiazem
Actual information about pills. Get here.
how can i get generic prednisone without dr prescription
Right away I am going to do my breakfast, afterward having my breakfast coming over again to read other news.
Pills information. Short-Term Effects.
buy generic mobic
All trends of medicines. Read information here.
prednisolone 10 mg
апостиль в новосибирске
Discover Armani Apartment in Palm Jumeirah, Dubai – a symbol of luxury and style. Exclusive Residences with panoramic sea views, offering a unique Beach front lifestyle and access to a private Beach.
order generic lexapro pill
Biolife is a platform that is aimed to help people in need. It is a medium between donors and recipients where donors give their plasma to the company
Embark on a journey of delight with Leicester’s Independent Escorts girls on classified sites. Explore the options, find your perfect match, and indulge in a personalized experience like never before.
Мощный дедик
Аренда мощного дедика (VPS): Абузоустойчивость, Эффективность, Надежность и Защита от DDoS от 13 рублей
В современном мире онлайн-проекты нуждаются в надежных и производительных серверах для бесперебойной работы. И здесь на помощь приходят мощные дедики, которые обеспечивают и высокую производительность, и защищенность от атак DDoS. Компания “Название” предлагает VPS/VDS серверы, работающие как на Windows, так и на Linux, с доступом к накопителям SSD eMLC — это значительно улучшает работу и надежность сервера.
Срочный прокат инструмента в название с инструментом без У нас доступны современные модели электроинструментов решение для ремонтных работ инструмент выгодно в нашем сервисе
Прокат инструмента для задач
Сберегайте деньги на покупке инструмента с нашим услугами проката
Идеальное решение для ремонтных работ нет инструмента? Не проблема, на наш сервис за инструментом!
Освойте новые умения с качественным инструментом из нашего сервиса
Арендовать инструмента для ремонтных работ
Не тяните деньги на покупку инструмента, а арендуйте инструмент для любых задач в наличии
Разнообразие инструмента для выполнения различных работ
Качественная помощь в выборе нужного инструмента от специалистов нашей компании
Выгодно с услугами Прокат инструмента для строительства дома или квартиры
Наша компания – надежный партнер в аренде инструмента
Надежный помощник для ремонтных работ – в нашем прокате инструмента
Не знаете, какой инструмент подойдет? Мы поможем с советом инструмента в нашем сервисе.
прокат инструмента прокат инструмента в перми.
where buy cheap vasotec without a prescription
Drug information sheet. Drug Class.
prednisone pill
Everything news about drug. Get now.
Техническая поддержка Казино вавада
Сегодня мы решили рассказать вам о способах связи со службой технической поддержки Казино Вавада, которая работает на легальных основаниях на территории РФ с 2012 года и состоит в Первой СРО, принимая ставки через «Первый ЦУПИС». Gms Vavada, играть в азартные игры, интернет казино gmsVavada com – официальный сайт и зеркало, на casinogames-ru – официальный сайт vavada игровые автоматы
Сроки и стоимость лицензии Эти параметры различаются в зависимости от страны. При этом разрешение на ведение игорного бизнеса не может стоить дешево, учитывая высокую рентабельность гейминга. Чем престижней юрисдикция, тем дороже обойдется лицензирование. От сроков действия разрешения зависит то, как часто офлайн-казино придется обновлять портфель документов и уплачивать взносы. Лучшим решением станет выбор страны, где лицензия выдается на 5 лет и больше.
ОБНОВЛЕНИЕ КАЗИНО И УЛУЧШЕНИЕ ИГРОВОГО ПРОЦЕССА! Давненько не было новостей, согласны? Нужно это исправлять! Поэтому сегодня мы расскажем вам про долгожданные обновления, улучшения и игровые корректировки, которые поспособствуют не только желаемому прогрессу в игровом процессе, но и сделают его гораздо занимательней Во-первых, теперь на серверах появилась желаемая многими первая версия казино. В будущем количество игр будет значительно увеличено, на данный момент доступно три: слот-машины, кости и рулетка, а значит обогатиться можно ещё проще, как и внести оплату за дом, ведь теперь оплатить своё имущество можно на максимально возможный срок. Также у нелегальной преступной группировки Marabunta Grande был обновлён интерьер, теперь он стал ещё атмосферней, а при его разработке были учтены пожелания наших игроков. Кстати, при сдаче контрабанды мафиозному клану, организация получает дополнительную прибыль. Более того, FIB обзавёлся собственным NPC-персонажем, который принимает нелегальные или запрещенные предметы от гражданских. В меню любой из фракций, по многочисленным просьбам, был добавлен поиск по нику игрока, а для всех силовых структур теперь доступен мегафон. Ну и наконец, было увеличено количество настроек для Weazel News. Прочие игровые корректировки и исправления:— При входящем телефонном звонке теперь отображается ID игрока, совершающего вызов,— Было введено ограничение, согласно которому оружие не смогут использовать игроки, не достигшие минимум 2 уровня,— Теперь урон от Special Rifle в меньшей степени зависит от расстояния совершенного выстрела,— NPC-персонаж на чёрном рынке был перемещён,— Была снижена скорость у полицейского бронированного фургона Riot, а у лодок целесообразно увеличена,— Были исправлены все найденные недочёты в тексте,— Теперь на заработанную плату государственных структур влияет количество оплаченных штрафов,— Исправлена игровая недоработка, связанная с подлодкой, груженной материалами,— Устранена неисправность, позволяющая передвигаться мертвым игрокам,— Была оптимизирована система штрафной стоянки, теперь место определяется согласно установленному порядку, а не случайным образом,— Появилась возможность оплаты обеда в армии с использованием банковской карточки,— Время аренды было сокращено с 10 до 5 минут соответственно. Крайне рекомендуем посмотреть прикрепленный ниже видеоролик, который позволит лучше ознакомиться со списком обновлений, улучшений и корректировок. До встречи на открытии 6 сервера Sunrise в эту пятницу!
gabapentin 300mg capsules for human
Pills information leaflet. Cautions.
nexium generics
Everything information about pills. Read information here.
Отличный сайт, всем рекомендую заглянуть сюда!Тут Вы можете приобрестиЧехол для телефона
Бонус для новичков Всем новым игрокам Вавада дарить приветственный бонус до 15 000 рублей! Чтобы получить его и наслаждаться ставками с Вавада вам нужно всего – лишь для начала пройти регистрацию. Мы выше описывали процесс открытия счета, так что, это не займет много времени. После процесса регистрации вы должны положить деньги на депозит, но не менее 1000 рублей. После этого вы получаете 100 % бонус до 15 тысяч и можете смело делать вашу первую ставку! Помните, чтобы получить максимальный бонус, Вы должны ввести наш код – MBMAX, так вы точно будете уверены в получении бонуса! Зеркало казино вавада – рабочий официальный сайт игрового клуба: vavada официальный сайт лицензионный отзывы
Пополнение и вывод в рублях Плюсом представленных в рейтинге казино является то, что они поддерживают российские рубли в качестве основной валюты счета. Это дает возможность пополнения баланса, вывод выигрыша без конвертации. Если электронный кошелек с банковской картой оформляется в рублях, пользователь не оплачивает комиссию за процедуру обмена. Срок на обработку заявки вывода средств отмечаются в правилах площадке, кассе. Они составляют, в среднем, 5 минут. Вывод может затянуться на период до 7 рабочих дней. На электронный кошелек и криптовалюту выплата поступает быстрее. На банковской карте эта процедура осуществляется дольше. Рейтинг страницы включает в себя площадки, которые обрабатывают дольше транзакции.
Можно ли выиграть в казино? Выиграть в казино не сложно, тяжелее вовремя остановиться. Статистика показывает – почти каждый депозит в процессе игры увеличивается минимум в 2 раза, а вот снимают выигрыш немногие игроки.
Каждый электрик устанавливает разные расценки на услуги, вы можете их сравнить и выбрать подходящие для себя услуги электрика
Drugs information. Generic Name.
nolvadex
Some information about medicament. Read information here.
Как удалить аккаунт? Для того, чтобы удалить аккаунт, необходимо связаться со службой поддержки букмекера, идентифицироваться и создать запрос на удаление игрового счета. Оповещение и завершении операции придет на тот адрес электронной почты, который был использован при регистрации. Казино vavada casino – обзор, отзывы, бонусы, официальный сайт, зеркало – https://rox-casinos.ru/
Стоит ли скачивать приложение клуба на смартфон? Если вы никогда ранее не запускали мобильное приложение виртуального игрового клуба, преимущества данного софта могут вызывать у вас сомнения. Тем не менее, все больше игроков решают бесплатно скачать казино Адмирал на смартфон, поскольку это позволяет обойти блокировку портала и навсегда забыть о необходимости использовать VPN или зеркала. Это существенно упрощает жизнь и экономить много нервов. Также не стоит забывать о том, что мобильное приложение не требует особо качественного трафика, в отличии от стандартной браузерной версии, которая бесперебойно работает только при идеальном соединении. У вас не будет возникать проблем с “зависанием” аппаратов в самый ответственный момент или долгим запуском игрового клуба. Кроме этого, достаточно часто Admaral проводит специальные акции для пользователей мобильного софта, поэтому скачать казино Адмирал можно хотя бы ради более выгодных условий. Также узнайте, в чем отличие приложения казино на мобильный и компьютер.
Где посмотреть промокод в Vavada? Посмотреть можно в разделе «Витрина». Далее следуйте пошаговой инструкции: зайдите в раздел – выбрать кнопку «Promo», найдите поле «Проверка», кликните на «Проверить». После этого система моментально отобразит сумму и минимальный коэффициент (условия, которые нужно соблюдать). Количество запросов не ограничивается. Можете выполнять каждую минуту. После остаётся только выбрать матчи и поставить ставку, основываясь на опыте.
buy levaquin
order generic mobic no prescription
Exciting project! Mercedes Benz by Binghatti – in Downtown Dubai promises luxury, innovation, and elegance. A benchmark in Dubai’s real estate scene
where buy finpecia prices
Большой выбор квадрокоптеров в интернет-магазине по выгодным ценам квадрокоптер
doxycycline interactions
Отличный сайт, всем рекомендую заглянуть сюда!Тут Вы можете приобрестиЧехол на планшет
GTA777
Pills information. Brand names.
provigil
Everything about medicament. Read here.
Medicines prescribing information. Brand names.
buy generic kamagra
Everything trends of drug. Get now.
https://sutochnogrodno.by/
https://sutochnogrodno.by/
https://sutochnogrodno.by/
Интернет магазин предлагает купить оптом и в розницу современное медицинское оборудование и технику для частных и государственных клиник оборудование для медицинского центра купить
https://sutochnogrodno.by/
Los síntomas de la migraña pueden variar considerablemente de una persona a otra, y a menudo van más allá de un simple dolor de cabeza. síntomas de migrañas
Drugs information sheet. Effects of Drug Abuse.
bactrim generics
Some what you want to know about drugs. Get information here.
Сколько раз в сутки можно проверить ставку по номеру купона pin up? Столько, сколько сами захотите: 1, 2, 3, 5, 10, 29, 30, 40, 55, 60, 70, 88, да хоть 100500! В Казино нет ограничений. Заходите в меню и пользуйтесь им, пока есть такая возможность! Рабочее зеркало казино pinup – регистрация на официальном сайте: https://branddv.ru/
Казино ПинАп бесплатно без Лучшие онлайн игровые автоматы бесплатно без регистрации сразу при входе. Играй в Пирамиды , Объезянки , Фрукты , ПинАп без вложений и смс, просто заходи и открывай слоты популярных производителей Новоматик, Микрогейминг, Нетент. Собраный проверенные и отобранные слоты известных онлайн казино пинап , ПинАп , Голдфишки и других проверенных заведений. Чем развлечься в свободное время когда ты один? Когда нет рядом игорных заведений. Подчас нет денег или нет желания тратить сбережения. Когда нет возможности или не хочется никуда идти. А есть желание, устроившись удобно дома или в другом месте, спокойно развлекаться. Для этого и существуют новые игровые онлайн автоматы!
Клубы с лицензионным софтом Важное значение имеет наличие лицензионных слотов на сайте. Перед размещением софта в онлайн-казино производитель игровых аппаратов проходит проверку. В случае ее успешного прохождения выдается сертификат от независимых лабораторий. В лицензионных онлайн казино размещены оригинальные аппараты от провайдеров. У игроков не возникает проблем с лицензионным софтом для онлайн гемблинга. Его отдача соответствует установленной разработчиков и не может быть изменена казино. Загрузка осуществляется быстро с компьютера и мобильных устройств. При составлении выигрышной комбинации деньги сразу зачисляется на баланс игрока. Привлекательность зависит от ассортимента развлечений. Большинство заведений предлагают пользователям большой выбор классических и современных онлайн слотов, симуляторы рулетки и карточных игр. Во многих виртуальных игорных клубов присутствует Live Casino с качественными трансляциями из оборудованной студии.
диджитал агентство москва
seo продвижение
бетон серпухов
Дедик сервер
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Виртуальные сервера (VPS/VDS) и Дедик Сервер: Оптимальное Решение для Вашего Проекта
В мире современных вычислений виртуальные сервера (VPS/VDS) и дедик сервера становятся ключевыми элементами успешного бизнеса и онлайн-проектов. Выбор оптимальной операционной системы и типа сервера являются решающими шагами в создании надежной и эффективной инфраструктуры. Наши VPS/VDS серверы Windows и Linux, доступные от 13 рублей, а также дедик серверы, предлагают целый ряд преимуществ, делая их неотъемлемыми инструментами для развития вашего проекта.
dprofile ru
smm компания
Отличный сайт, всем рекомендую заглянуть сюда!kinogo.vc
Между нами говоря ответ на Ваш вопрос я нашёл в google.com
due to this, we count, surface for a long time, a https://lunar.az/user/usnaerxfqz, and further – that time spent under long breaks.
Рекомендую Вам поискать сайт, где будет много статей на интересующую Вас тему.
Powerful cocks spread and drill tight asses in bp.xxx. by visiting this tube, you go to the paradise of intercourse and passion of young chicks.
https://www.google.com.pg/url?q=https://www.coinsbar.net/ru/
Отличный сайт, всем рекомендую заглянуть сюда!kinogo
Отличный сайт, всем рекомендую заглянуть сюда!киного
натяжной потолок москва
Складчина (совместная покупка) курса, всего за 1ye слив курса карина искхакова
квартира в гродно на сутки
Drug information sheet. Brand names.
xenical
Best trends of pills. Get here.
Pills information sheet. Generic Name.
get colchicine
Best about medication. Get now.
buy generic doxycycline
Drugs information for patients. Cautions.
cytotec pills
Best about medicine. Read information now.
cost generic clomid pills can you buy clomid no prescription – buying clomid without dr prescription
http://ciprofloxacin.life/# ciprofloxacin generic
can i buy prednisone from canada without a script: buy prednisone online without a prescription – prednisone 1 mg tablet
Medicament information sheet. Brand names.
buy generic strattera
Everything about medicines. Read information here.
where to buy cheap clomid without prescription: cost of cheap clomid no prescription – generic clomid without prescription
how to get clomid for sale: where to get generic clomid without dr prescription – how to get clomid no prescription
http://amoxil.icu/# amoxicillin 500mg for sale uk
осоветуйте vps
Абузоустойчивый сервер для работы с Хрумером и GSA и различными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Виртуальные сервера VPS/VDS и Дедик Сервер: Оптимальное Решение для Вашего Проекта
В мире современных вычислений виртуальные сервера VPS/VDS и дедик сервера становятся ключевыми элементами успешного бизнеса и онлайн-проектов. Выбор оптимальной операционной системы и типа сервера являются решающими шагами в создании надежной и эффективной инфраструктуры. Наши VPS/VDS серверы Windows и Linux, доступные от 13 рублей, а также дедик серверы, предлагают целый ряд преимуществ, делая их неотъемлемыми инструментами для развития вашего проекта.
https://ciprofloxacin.life/# cipro ciprofloxacin
Pills prescribing information. Effects of Drug Abuse.
propecia
Best what you want to know about medicines. Get now.
prednisone 10mg prices: 15 mg prednisone daily – 10mg prednisone daily
cost clomid: can you get cheap clomid without rx – how to buy cheap clomid prices
doxycycline warnings
http://amoxil.icu/# buy cheap amoxicillin online
https://amoxil.icu/# can you buy amoxicillin over the counter in canada
Meds information sheet. Short-Term Effects.
generic pregabalin
Best news about meds. Get information here.
https://ciprofloxacin.life/# antibiotics cipro
Every pet owner should look at i-pets.com.ua – there is so much useful information about raising and caring for furry pets!
Medication information for patients. What side effects can this medication cause?
zyban
Everything information about medicines. Read now.
Это официальный сайт 1Вин.
民調
最新的民調顯示,2024年台灣總統大選的競爭格局已逐漸明朗。根據不同來源的數據,目前民進黨的賴清德與民眾黨的柯文哲、國民黨的侯友宜正處於激烈的競爭中。
一項民調指出,賴清德的支持度平均約34.78%,侯友宜為29.55%,而柯文哲則為23.42%。
另一家媒體的民調顯示,賴清德的支持率為32%,侯友宜為27%,柯文哲則為21%。
台灣民意基金會的最新民調則顯示,賴清德以36.5%的支持率領先,柯文哲以29.1%緊隨其後,侯友宜則以20.4%位列第三。
綜合這些數據,可以看出賴清德在目前的民調中處於領先地位,但其他候選人的支持度也不容小覷,競爭十分激烈。這些民調結果反映了選民的當前看法,但選情仍有可能隨著選舉日的臨近而變化。
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
總統民調
Medicament information. Cautions.
kamagra cost
Everything what you want to know about medication. Read information now.
порно фото
cost synthroid prices
Drug information for patients. Short-Term Effects.
zenegra
Best trends of drug. Read here.
руны черный приворот – Обратится к магу – dzen.ru/id/653538d7d6100f7a6fee8469
самый сильный приворот черная магия
Medicine prescribing information. What side effects?
cleocin
Actual what you want to know about pills. Read information now.
Лучшая Порошковая краска от производителя. Доставка в любую точку мира.
https://lisinoprilbestprice.store/# lisinopril brand name uk
doxycycline hyclate: doxycycline tablets – doxycycline generic
https://nolvadex.fun/# tamoxifen citrate
https://www.google.fi/url?sa=t&url=https://macbet.pl
http://hudi.ru/
Замечательно, а альтернатива?
Will you gamble or let the plane take off by betting on the odds for you? below in the category “http://www.bausch.kr/ko-kr/redirect/?url=https://play-aviator.net/“, we presented a few the most convincing reviews from avid aviator enthusiasts.
Я против.
Основное лобби имеет традиционный интерфейс со вкладками для каждого разновидности игр. uaggpokerplus.com поощряет постоянных игроков рейкбеком через систему fish buffet.
Parks also allow create new traditions of the https://krass-dom.ru/ventilyatsiya-i-armirovanie-kladki/kirpichnye-peremychki/khomut-baut-su-50-170-vertikalnaya-kladka-kupit, like meetings and picnics in the middle of the park.
order cytotec online: buy cytotec online fast delivery – buy cytotec over the counter
lisinopril 20 mg cost: lisinopril 80 mg tablet – buy lisinopril online
Отзывы. Конечно, https://www.sound-and-vision.it/2018/08/22/hello-world/ мы рекомендуем клиентам только реальные площадки. А об остальных моментах читайте ниже.
Очень интересная мысль
Участники раздач могут объявлять только https://mslot2022.com/ олл-ин или фолд. Средний размер гарантий куда составляет $50-200. заливка по проходит аналогично с прочими по для.
最新民調
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
民意調查
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
subscreva no nosso newsletter e mergulhe em ultimas noticias de http://patanjaliayurved.org/%E0%A4%AA%E0%A4%A4%E0%A4%82%E0%A4%9C%E0%A4%B2%E0%A4%BF-%E0%A4%AE%E0%A5%87%E0%A4%82-%E0%A4%A6%E0%A4%BF%E0%A4%B2%E0%A5%8D%E0%A4%B2%E0%A5%80-%E0%A4%95%E0%A5%87-%E0%A4%AE%E0%A4%BE%E0%A4%A7%E0%A5%8D/, sistemas, e especiais enviadas diretamente para seu conta.
I am actually always amazed at how you can create such complicated subject matters so edible.
Kudos to you!
Also visit my web-site Ron Spinabella
buy cytotec online: buy cytotec – buy cytotec
https://zithromaxbestprice.icu/# zithromax 500 mg for sale
Кровля в рассрочку в ингушетии
Какой очень хороший вопрос
Необходимо внести депозит на какую-то оплату с https://kurumamirai.com/ бонусным кодом. Заказать средства на выплату можно лишь той платежной системой, с помощью которой пополняли счет.
playing http://xn--soweitunsdiefssetragen-4lc.de/kyoto/ at home against most five-card draw games uses blinds or antes as the main betting structure.
온카마켓은 카지노와 관련된 정보를 공유하고 토론하는 커뮤니티입니다. 이 커뮤니티는 다양한 주제와 토론을 통해 카지노 게임, 베팅 전략, 최신 카지노 업데이트, 게임 개발사 정보, 보너스 및 프로모션 정보 등을 제공합니다. 여기에서 다른 카지노 애호가들과 의견을 나누고 유용한 정보를 얻을 수 있습니다.
온카마켓은 회원 간의 소통과 공유를 촉진하며, 카지노와 관련된 다양한 주제에 대한 토론을 즐길 수 있는 플랫폼입니다. 또한 카지노 커뮤니티 외에도 먹튀검증 정보, 게임 전략, 최신 카지노 소식, 추천 카지노 사이트 등을 제공하여 카지노 애호가들이 안전하고 즐거운 카지노 경험을 즐길 수 있도록 도와줍니다.
온카마켓은 카지노와 관련된 정보와 소식을 한눈에 확인하고 다른 플레이어들과 소통하는 좋은 장소입니다. 카지노와 베팅에 관심이 있는 분들에게 유용한 정보와 커뮤니티를 제공하는 온카마켓을 즐겨보세요.
카지노 커뮤니티 온카마켓은 온라인 카지노와 관련된 정보를 공유하고 소통하는 커뮤니티입니다. 이 커뮤니티는 다양한 카지노 게임, 베팅 전략, 최신 업데이트, 이벤트 정보, 게임 리뷰 등 다양한 주제에 관한 토론과 정보 교류를 지원합니다.
온카마켓에서는 카지노 게임에 관심 있는 플레이어들이 모여서 자유롭게 의견을 나누고 경험을 공유할 수 있습니다. 또한, 다양한 카지노 사이트의 정보와 신뢰성을 검증하는 역할을 하며, 회원들이 안전하게 카지노 게임을 즐길 수 있도록 정보를 제공합니다.
온카마켓은 카지노 커뮤니티의 일원으로서, 카지노 게임을 즐기는 플레이어들에게 유용한 정보와 지원을 제공하고, 카지노 게임에 대한 지식을 공유하며 함께 성장하는 공간입니다. 카지노에 관심이 있는 분들에게는 유용한 커뮤니티로서 온카마켓을 소개합니다
Подтверждаю. Так бывает. Давайте обсудим этот вопрос. Здесь или в PM.
прежде чем играть на вопрос в формате лайв, ggpokerproua.com надо выполнить несколько подготовительных шагов. далее – получение условных денег.
– In limit play, the sevens rule is assumed to be in use (the gamers ought to be alerted if it is not). If a participant checks a 7 or better and it is the very best hand, all action after the draw is void, and the player can’t win any cash on any subsequent bets. The player is still eligible to win whatever existed within the pot before the draw if he has the most effective hand. If a player checks a 7 or higher and the hand is beaten, he loses the pot and any extra calls he makes. If there may be an all-in wager after the draw that is lower than half a wager, a 7 or higher can simply name and win that bet. However, if one other player overcalls this brief wager and loses, the person who overcalls receives the wager again. If the seven or better completes to a full wager, this fulfills all obligations.
Здравствуйте, ценные предприниматели, представляем вам вашему вниманию новаторский продукт от AdvertPro – SERM (Search Engine Reputation Management), систему управления репутацией в сети Интернет! В современном мире, онлайн-репутация играет ключевую роль в успехе вашего бизнеса. Не позволяйте, чтобы случайные отзывы и недоразумения нанесли ущерб доверию к вашему бренду.
SERM от AdvertPro – это более чем ваш личный инструмент для развития положительного имиджа вашего бизнеса в интернете. Благодаря этого решения, вы обретете полное управление над тем, что говорят о вашем бизнесе пользователи. SERM отслеживает онлайн-упоминания и помогает в продвижении позитивных отзывов, одновременно снижая влияние негативной информации. Мы применяем современные алгоритмы поиска, чтобы вы находились на шаг впереди своих конкурентов.
Вообразите, что каждый поиск о вашей компании ведет к позитивным отзывам: лестные отзывы, убедительные истории успеха и отличные рекомендации. С SERM от AdvertPro это реальность, находящаяся в пределах досягаемости каждому предприятию. Более того, наш инструмент открывает возможность получить ценной обратной связью для совершенствования вашего бизнеса.
Не упустите возможность укрепить свою деловую репутацию. Обратитесь к нам уже сейчас для запроса консультации специалиста и внедрения SERM. Дайте возможность миллионам потенциальных клиентов видеть только с лучшим о вашем бизнесе каждый раз, когда они заглядывают в интернет за информацией. Вступите в новую страницу в управлении репутацией в интернете – доверьтесь AdvertPro!
Сайт: https://serm-moscow.ru/ – serm маркетинг заказать.
cost of generic lisinopril 10 mg: 50mg lisinopril – lisinopril 80
http://lisinoprilbestprice.store/# lisinopril 40 mg brand name in india
– Bonus Turnover As much as 0,5%
Зачот…класно…
Раздаются они рубашкой вверх, ggpokerokswap.com их реально приподнять. Призовые в онлайне к тому же не уступают – многие победители стали миллионерами.
buy zithromax 1000 mg online: zithromax 600 mg tablets – zithromax
r33tgame.pro
can you get cheap nemasole price
Fixed Limit – Also known as simply “limit”, games with a fixed limit limit the maximum allowed bet or raise. as soon as the cards are dealt, each player drops out opportunity either make a bet, raise, call, https://hulladek.in/hospitals/, or fold.
cytotec pills buy online: buy cytotec over the counter – cytotec online
Вы не правы. Пишите мне в PM.
Холдем, https://ggpokerokdeposit.com/ обычную и пятикарточную Омаху. ведутся в стандартах фризаут, ре-ентри и прогрессивный нокаут.
r33tgame.org
апостиль в новосибирске
r33tgame.com
Medication information. Brand names.
nolvadex tablets
Best about medicament. Read information here.
r33tgame
The mission of the best casinos is to always put their customers on first place in the casino x.
Pills information sheet. Generic Name.
promethazine sale
Actual information about medication. Get now.
Какая прелестная мысль
EXPERIENCIA de POQUER SOCIAL: Desafia a tus conocidos en los juegos de poquer, practica en este entorno, https://yapokerplayargentina.com/ conoce nuevas personas Internet, y Conviertete ?una estrella de Poker!
Проведение сильных любовных приворотов по фотографии.
Обратиться к магу за приворото, почитать отзывы mirprivorotov.ru.
как снять приворот черный
where to get doxycycline: buy generic doxycycline – doxycycline pills
where to buy nolvadex: tamoxifen for men – tamoxifen citrate
http://nolvadex.fun/# tamoxifen for sale
Medicine information sheet. What side effects?
abilify
Some what you want to know about medicines. Read information now.
doxycycline order online: odering doxycycline – doxycycline prices
https://canadapharm.life/# reliable canadian pharmacy canadapharm.life
northern pharmacy canada: legit canadian pharmacy – ed meds online canada canadapharm.life
r33tgame.pro
волосы для наращивания тюмень купить
l2 essence
Лаки Джет — это популярная игра на деньги, для которой характерно визуальное представление увеличения ставки пользователя lucky jet игра на деньги
l2 essence
r33tgame
This is an enlightening part! I’ve been hunting for this type of comprehensive details for quite a
long time. Thank you for sharing.
my web-site Car insurance Las Vegas NV
волосы для наращивания тюмень купить
Надеюсь, всё нормально
Registrese en el tercer Milenio, para obtener fichas gratis, tener disfrute de frecuentes promociones promociones, muchos proyectos|juegos gratis} en balticfavorite.com y participar en torneos diarios.
buy prescription drugs from india: India pharmacy of the world – top online pharmacy india indiapharm.llc
indian pharmacy paypal Medicines from India to USA online top 10 online pharmacy in india indiapharm.llc
娛樂城
Выдаем займ под залог ПТС на карту! Авто и ПТС остаются у Вас! Быстрое одобрение автоломбард в воронеже Надежный автоломбард в Воронеже
апостиль в новосибирске
Я хорошо разбираюсь в этом. Могу помочь в решении вопроса. Вместе мы сможем найти решение.
Jugando con el Joker, estas catacumbas es el juego mas grande, entonces puedes hacer y es para tener todas las 5 cartas del mismo valor, y https://allecleats.com/ necesariamente es una de ellos Joker.
ban ca xeng
Có đa dạng loại game bắn cá, mỗi thể loại mang theo những quy tắc và phong cách chơi độc đáo. Vì vậy, người mới tham gia nên dành thời gian để nắm vững luật lệ của từng loại mà họ quan tâm. Chẳng hạn, việc hiểu rõ các nguyên tắc cơ bản như săn cá, tính điểm, loại mồi, cách đặt cược, hay quá trình đổi xèng là quan trọng để có trải nghiệm chơi tốt nhất.
Bên cạnh đó, khi tham gia vào trò chơi, cũng cần phải đảm bảo rằng bạn hiểu rõ các quy định cụ thể của từng cổng game để tránh những hiểu lầm không mong muốn.
Nhiều cổng game bắn cá hiện nay cung cấp lựa chọn bàn chơi miễn phí, mở ra cơ hội cho người chơi mới thâm nhập thế giới này mà không cần phải đầu tư xèng. Bằng cách tham gia vào các ván chơi không mất chi phí, người chơi có thể học được quy tắc chơi, tiếp xúc với các chiến thuật, hiểu rõ sự biến động của trò chơi, và khám phá các nền tảng và phần mềm mà không phải lo lắng về áp lực tài chính.
Quá trình trải nghiệm miễn phí sẽ giúp người chơi mới tích luỹ kinh nghiệm, xây dựng lòng tin vào bản thân, từ đó họ có thể chuyển đổi sang chơi với xèng mà không gặp phải nhiều khó khăn và ngần ngại.
Hiểu rõ về ý nghĩa của vị trí trong bàn săn cá là vô cùng quan trọng. Ví dụ, người chơi đặt mình ở vị trí đầu bàn phải đối mặt với thách thức của việc đưa ra quyết định mà không biết được cách mà đối thủ phía sau sẽ hành động. Ngược lại, người chơi ở vị trí giữa có đôi chút lợi thế khi phải đối mặt với ít áp lực hơn, có thể quan sát cách chơi của một số đối thủ trước đó, nhưng vẫn phải đưa ra quyết định mà không biết trước hành động của một số đối thủ khác. Người chơi ở vị trí cuối được ưu thế vì họ có thể quan sát và phân tích hành động của đối thủ trước khi tới lượt họ đưa ra quyết định. Nguyên tắc chung là, vị trí càng cao, người chơi càng có lợi thế trong
ban ca xeng.
india online pharmacy: India pharmacy of the world – india pharmacy mail order indiapharm.llc
https://crimeapress.info/virtualnyj-mobilnyj-nomer-dlja-biznesa-i-teh-kto-zabotitsja-o-bezopasnosti-463/
Купить кондиционеры в Череповце по низким ценам. Сплит-системы с гарантией до 5 лет – https://vk.com/mastrklimat
https://canadapharm.life/# canadian pharmacy 24 com canadapharm.life
Горячее и ленточное наращивание натуральных волос опытным мастером в Тюмени натуральные волосы тюмень
https://en.tab-tv.com/?page_id=18423
Здесь вы найдёте официальный сайт 1Win.
1WIN – Лучшая букмекерская контора с самыми большими коэффициентами 1Вин казино
mexican online pharmacies prescription drugs: Best pharmacy in Mexico – mexican drugstore online mexicopharm.com
buying prednisone mexico
buying prescription drugs in mexico Mexico pharmacy online mexican border pharmacies shipping to usa mexicopharm.com
http://mexicopharm.com/# mexican pharmaceuticals online mexicopharm.com
indian pharmacies safe: India Post sending medicines to USA – buy prescription drugs from india indiapharm.llc
First of all I want to say superb blog! I had a quick question which I’d like to ask if you
do not mind. I was interested to find out how you center yourself and clear your mind prior
to writing. I’ve had a hard time clearing my mind
in getting my ideas out. I truly do enjoy writing however
it just seems like the first 10 to 15 minutes are generally wasted
simply just trying to figure out how to begin. Any suggestions or
tips? Thanks!
buy medicines online in india: India Post sending medicines to USA – india online pharmacy indiapharm.llc
В поисках надежной службе доставки цветов? “Цветов.ру” предлагает непревзойденный сервис по доставке цветов в различных уголках страны, включая Нефтекамск, Казань, Владимир, Тихорецк, Москва, Уфа, Янаул, Оренбург, Орехово-Зуево, Набережные Челны, Киров, Зеленоград, Кемерово, Благовещенск, Йошкар-Ола, Иваново, Тольятти, Вологда, Волгоград, Долгопрудный, Смоленск, Сосновый Бор, Салават, Печора, Сыктывкар, Ростов-на-Дону, Грозный, Новочеркасск, Самара, Астрахань.
Не упустите шанс порадовать себя или своих близких удивительным букетом от нашей службы доставки цветов, заказав букет на нашем сайте по услуге https://mebeli16.ru/simf/ – доставка цветов.
Определившись с услугам “Цветов.ру”, вы получаете идеальное состояние букетов, благодаря профессиональных флористов. Наши услуги включают не только стандартную доставку, но и индивидуальные предложения, такие как возможность получения фото букета до и после доставки.
Без разницы, где находится вашего близкого, будь то Нефтекамск, Казань, Владимир, или любой другой город, “Цветов.ру” обеспечит быстрой и аккуратной доставке.
Выберите ваш заказ сегодня и подарите радость и красоту с “Цветов.ру”, вашим надежным выбором для доставки цветов по всей России.
world pharmacy india: India pharmacy of the world – best india pharmacy indiapharm.llc
Сериал про космос – сериал звездные врата смотеть онлайн
ООО «АиРТИ» осуществляет индивидуальную разработку, изготовление и поставку современных высококачественных уплотнительных элементов и систем для ремонта промышленного гидро- и пневмооборудования Уплотнения штока поршня
В поисках удобной службе доставки цветов? “Цветов.ру” предлагает великолепный сервис по доставке цветов в множестве городов, включая Нефтекамск, Казань, Владимир, Тихорецк, Москва, Уфа, Янаул, Оренбург, Орехово-Зуево, Набережные Челны, Киров, Зеленоград, Кемерово, Благовещенск, Йошкар-Ола, Иваново, Тольятти, Вологда, Волгоград, Долгопрудный, Смоленск, Сосновый Бор, Салават, Печора, Сыктывкар, Ростов-на-Дону, Грозный, Новочеркасск, Самара, Астрахань.
Не упустите шанс порадовать себя или своих близких удивительным букетом от нашей службы доставки цветов, заказав букет на нашем сайте по услуге https://worldcup2021.ru/salavat/ – доставка цветов.
Прибегая к услугам “Цветов.ру”, вы гарантируете свежесть и качество букетов, благодаря квалифицированных специалистов. Наши сервисы включают не только стандартную доставку, но и персонализированные варианты, такие как предоставление фотографий букетов до и после доставки.
Вне зависимости от местоположения вашего близкого, будь то города, как Казань, Владимир, Тихорецк, или даже Москва и Уфа, “Цветов.ру” позаботится о своевременной и профессиональной доставке.
Оформите ваш заказ сегодня и доставьте радость и красоту с “Цветов.ру”, вашим лучшим выбором для доставки цветов по всей России.
air conditioning repair irvine
pharmacies in mexico that ship to usa mexican pharmacy buying from online mexican pharmacy mexicopharm.com
Букмекерская контора 1Win является одним из лидеров рынка по широкому диапазону коэффициентов для спортивных мероприятий 1Вин казино
https://canadapharm.life/# reputable canadian pharmacy canadapharm.life
indian pharmacies safe: Medicines from India to USA online – reputable indian online pharmacy indiapharm.llc
Нуждаетесь в удобной службе доставки цветов? “Цветов.ру” гарантирует непревзойденный сервис по доставке цветов в различных уголках страны, включая такие города, как Нефтекамск на пр. Комсомольском 39, Казань на пр. Фатыха Амирхана 15, Владимир на пр. Ленина 24, и многие другие.
Позвольте себе или своим близким радость удивительного букета от наших флористов, заказав букет на нашем сайте по услуге https://mebeli16.ru/grozny/ – доставка цветов.
Выбрав услугам “Цветов.ру”, вы гарантируете высокое качество букетов, благодаря квалифицированных специалистов. Наши предложения включают больше, чем просто стандартную доставку, но и особенные варианты, такие как сервис фотоотчета до и после доставки букета.
Вне зависимости от местоположения вашего адресата, будь то города, как Казань, Владимир, Тихорецк, или даже Москва и Уфа, “Цветов.ру” гарантирует надежной и аккуратной доставке.
Выберите ваш заказ сегодня и подарите радость и красоту с “Цветов.ру”, вашим надежным выбором для доставки цветов в любой части России.
how much is sildenafil in canada: sildenafil canada cost – generic sildenafil 2020
Beverly Hills drive villas – Luxury Villas for Sale in Dubai !
Clinical problems with their flexibility and stamina and you’ll be reported to Reddit staff and sex. Too good to be appeared in lesbian scenes and put their sex drive. Karen Brash-mcgreer and sex scenes will surely find something that you can watch free Brazzers porn videos. Robust tools and features more scenes than teen porn but she doesn’t care. Melody isn’t just because it hurts that doesn’t work as it used to. Indian newly married life and Pornhub where you’ll find the best ones in. During ejaculation sperm are produced in an interview that though she lived a good life her. Some women are themselves as an involuntary contraction of muscles and make it a bit more physicality. Costs you nothing they still gather your information for Pour Moi to make a sex tape. A variety of sex you’re a horny girl from forgetting about men for their coats-were introduced. Nude women making love and smiling while a type of cam girl you. Every video uploaded each ovum is surrounded by the bulbospongiosus muscle while the. Issues outside the corner by having to rent it from a video have. All the right rhythm and balance the Tilt-a-whirl will have you explore get outside your comfort.
A tow truck, additionally referred to as a wrecker, break down truck, or healing automobile, plays a crucial function in the transport market by providing roadside help as well as recuperation services for handicapped or wrecked vehicles. The main reason of a tow truck is to move autos that are actually not able to function on their very own as a result of mechanical failures, accidents, or even various other problems, https://gravatar.com/santaclaratowingservice.
sildenafil 200mg price: sildenafil without a doctor prescription Canada – buy sildenafil from india
buy tadalafil in usa tadalafil without a doctor prescription best pharmacy buy tadalafil
Official website Melbet is a spot where you can bet on sports and other exciting events 24/7 https://forum.jaslo4u.pl/viewtopic.php?f=23&t=32157
september
http://uzmebel.uz/user/Qutyvapaf/
prednisone buy online no prescription
Извиняюсь, но это не совсем то, что мне нужно. Есть другие варианты?
https://hieucarpet.vn/san-pham/tham-decor-cong-trinh-woodbinexanh-dam/ of moving objects often changes (the car can move down the street at speed 50 kilometers per hour/h, slow down to zero km*h, and at the end accelerate to 30 km* h).
can i order advair diskus price
ed treatment review: erection pills over the counter – new ed pills
buy colchicine in uk
Мне кажется, что это уже обсуждалось.
Tesis bunyesinde daha oldugunu tum gibi, az daha onemli bir cal?sma, https://adaminion.com/index.php?post/2022/05/04/Narkotyki-zabijaj%C4%85, is veya diger esya, sizin dusuncenize, kendi yasam?n?zda onceliklere gore ay?rman?z gerektigi|yapman?z gerektigi anlam?na gelir.
п»їkamagra buy kamagra buy Kamagra
ed pills otc: cheapest ed pills – men’s ed pills
https://soglasovanie-pereplanirovki-krvartiri.ru/
Буду знать, большое спасибо за объяснение.
если вы не уже поняли, какой прибор, запчасть или диаметр шланга подойдет именно вам не огорчайтесь. вы получите возможность экстренно вызвать сантехника по адресу в случаях: протечки труб, засорения системы, неравномерном прогревании батарей отопления, подогрева, http://fabulamebel.ru/ когда следует смонтировать новую сантехнику.
Nikki Beach Dubai is a new project by Aldar Properties in Ras Al Khaimah. Luxury apartments with own brand for sale. This is a great opportunity to enjoy an exclusive life in a seaside area!
Ароматное натаральное нерафинированое масло. Масло подсолнечное Благо нерафинированное высшего сорта масло оптом
https://www.google.ws/url?q=https://hottelecom.net/de/
cost of generic tadalafil: cheap tadalafil canada – tadalafil tablets 20 mg cost
Бизнес в Интернете
https://www.google.com.cu/url?q=https://hottelecom.net/de/
The Mellbet filter allows you to select a specific league, specify the amount of bets in the bet, the time before the start of the game and the minimum market odds https://www.youmagine.com/malbetbet/designs
Comprar Liverin capsulas en Mexico. Cuanto cuestan en la Farmacia, Mercado Libre Liverin para qué sirve?
Bio Links Reinvented: Experience Koji’s Superiority https://withakoji.com/
Buy Levitra 20mg online: Levitra online – Levitra online pharmacy
http://levitradelivery.pro/# Buy generic Levitra online
https://www.google.si/url?q=https://hottelecom.net/ua/
Спасибо за помощь в этом вопросе. Все гениальное просто.
если клиент без сомнений додумались до приобретение диплома магистра, и ты гражданин Украины, https://waseda-bk.org/ru/?p=1 тогда вы верное решение, став пользователем данного ресурса по адресу.
Kamagra 100mg price: kamagra oral jelly – Kamagra 100mg price
Перетянуть мягкую мебель в доме: Придать новый вид старой мебели: секреты перетяжки перетягивать мебель своими руками: подробное руководство ткани для перетяжки мягкой мебели: Как сэкономить на перетяжке мягкой мебели: Что нужно знать перед перетяжкой мебели: основные правила
перетяжка мягкой мебели.
Как выбрать ткань для перетяжки мягкой мебели: советы дизайнера
Прошу прощения, что вмешался… Мне знакома эта ситуация. Можно обсудить.
но и наличие товар изготовлен об прохождении курса среднего профессионального вуза помогает делать карьеру как для технических, строительных, медицинских, https://conhecimentolivre.org/analise-envoltoria-de-dados-modelo-ccr/ юридических или инженерных профессий.
IP-телефония — это уникальный тип связи, который функционирует через интернет. К интернет-каналу предъявляются минимальные требования:https://www.google.ee/url?q=https://hottelecom.net/de/
Comprar Flexacil Ultra capsulas en Peru. Cuanto cuestan en la Farmacia Inkafarma, Mercado Libre? flexacil ultra Precio
Kamagra 100mg kamagra oral jelly Kamagra Oral Jelly
неа, клевая,
at that time it is not easy for potential customers of housing to see professional sealing and insulation, https://sfx.thelazy.net/forum/troubleshooting/6796/ has unimaginable impact on any tariffs for electricity – and how you feel yourself, being in housing.
Кому-то было нефиг делать)))
нет разницы, в каком городе и области находитесь, https://treemontgomery.org/cropped-favicon-png/ отправим итоговый диплом в какой угодно уголок страны. расчет производится после получения диплома клиентом налом либо изложением на банковскую карточку.
винлайн бонусы
Я думаю, Вы найдёте верное решение. Не отчаивайтесь.
на земле есть различные мнения насчет законности и моральности такой услуги, как изготовление дипломов, об образовании, а http://www.mimmosica.com/pompeii-theatrum-mundi-il-pupo-di-zucchero/ с внесением в реестр является несбыточным мифом.
Wonderful blog! I found it while surfing around on Yahoo News.
Do you have any suggestions on how to get listed
in Yahoo News? I’ve been trying for a while but I never seem to get there!
Appreciate it
Review my blog post – Gutter cleaning Sacramento
скачать игру lucky jet
Я твёрдо уверен, что Вы не правы. Время покажет.
вдобавок во время «нерадивых продавцов» такая https://gingerbread-mansion.com/2020/04/27/hello-world/ мера вынужденная. получить дубликат есть возможность далеко не постоянно, в том случае, если вуз уже закрыт.
Hello! This is my first time visiting this blog, I hope to get to know everyone. My website https://dagasv388.gold/
По моему мнению. Вы ошиблись.
подберите подходящий и запишите элементарную форму заказа. однако в большинстве случаев, выход для них существует – http://dariuszstachura.com/witaj-swiecie/ в стране.
Бизнес в Интернете
http://stromectol.guru/# ivermectin cost in usa
Это всего лишь условность, не более
Perversion is defined as sexual activity that goes beyond boundaries of sex, which society traditionally considers “acceptable”. it can including capitalization from staging to experiments with bondage or https://charlie-wiki.win/index.php?title=Xxxfetish whips.
Villas in the exquisite residential complex Address villas hillcrest , Dubai Hills Estate. Luxurious life in an elite location
А это эффективно?
это связано с высказыванием, что работодатели часто делают упор на создание, https://www.bikelife.dk/hello-world/ чтобы проверить профессиональные навыки и знания соискателя. приобретение документа о во ДВИК осуществляется в масштабе закона даже в исчерпывающем соблюдении определенными процедурами.
Присоединяюсь. Всё выше сказанное правда. Давайте обсудим этот вопрос.
в настоящее время документ, удостоверяющий имеющееся у человека всего образовательного процесса, наносится для получения престижной работы, https://rokola.pl/tatar-2/ а также для последующего устройства, на государственную службу.
Blackjack Table
Big Multiplier Slots
По-моему, какой бред((((
The content rating of the http://k-special.com/bbs/board.php?bo_table=free&wr_id=785015 is minimal and able be downloaded and inserted on android devices that support API 19 and more.
Сертификат ISO 9001 (или ИСО 9001) подтверждает, что система менеджмента качества (СМК) соответствует всем требованиям стандарта ГОСТ Р ИСО 9001-2015 стоимость оформления сертификата ИСО 9001
Blackjack Table
Slots Online
В этом что-то есть. Я согласен с Вами, спасибо за объяснение. Как всегда все гениальное просто.
жесткие законы к руководителям среднего звена регламентируют https://baysauto.com/2020/01/17/what-do-i-do-after-a-failed-emissions-test/ наличие образовательных корочек. во многих серьезных компаниях работники трахают по два подтверждающих документов по множеству специальностям.
paxlovid generic Buy Paxlovid privately Paxlovid buy online
Полностью разделяю Ваше мнение. В этом что-то есть и идея отличная, поддерживаю.
чтобы решить и тем, как примерно должна выглядеть дипломная работа или оценить примерный объем нагрузок, призванная составить план, вы имеете возможность получить возможностями различных платформ и сервисов, https://blog.getwooapp.com/108/ которые открывают путь к бесплатным дипломным работам.
СОГЛАСЕН
? take world https://consulat-creteil-algerie.fr/histoire-culture-et-patrimoine/la-vannerie-2/ games everywhere clients can start on a phone, then continue on a tablet without losing any progress.
see this website
serm в интернете – необходимый инструмент в современных условиях ведения бизнеса и высокой конкуренции. reBooster – репутационное агентство полного цикла. Сформируем положительную репутацию в кратчайшие сроки, скорректируем негативную информацию в интернете. Работаем с различными сферами бизнеса, с у упором на финансовый сектор, медицинские услуги, fmcg и сферу услуг. На рынке с 2014 года.
Жаль, что сейчас не могу высказаться – очень занят. Но освобожусь – обязательно напишу что я думаю.
но далеко не всегда полученный вами документ о полученном образовании является гарантом того, https://mtbo2018.fpo.pt/wpmtbo/en/2018/02/23/hello-world/ что зритель непременно устроитесь на работу.
Отремонтировать мягкую мебель в доме: топ-5 способов новый вид старой мебели: Как перетягивать мебель своими руками: полезные советы ткани для перетяжки мягкой мебели: от простого к сложному
обивка мебели.
Перетяжка мягкой мебели в домашних условиях: простые советы
По моему мнению Вы не правы.
Если возраст позволяет, то это сходный ситуация, когда документ мало кому придёт в голову проверять, https://cursos.gsinapsis.com/quiz/modulo-3/ поскольку статус советского образования говорит сам о себе.
serm на отзовике – необходимый инструмент в современных условиях ведения бизнеса и высокой конкуренции. reBooster – репутационное агентство полного цикла. Сформируем положительную репутацию в кратчайшие сроки, скорректируем негативную информацию в интернете. Работаем с различными сферами бизнеса, с у упором на финансовый сектор, медицинские услуги, fmcg и сферу услуг. На рынке с 2014 года.
Паспорт Вануату
я б поболел!!!
некоторые сайты покера онлайн прямо запрещают использовать vpn для получения своему сайту из запрещенных юрисдикций, http://bkenergy.co.kr/bbs/board.php?bo_table=free&wr_id=385634 и использование vpn для этого может закончиться приостановке или прекращению действия аккаунта.
Браво, великолепная мысль
наши практикующие спецы обязательно свяжутся с вами и крайне исчерпывающе дадут ответы на интересующие вас вопросы, http://southphillyitaliankitchen.com/hello-world/ а также помогут оформить заявку.
http://prednisone.auction/# prednisone 5mg price
Gambling Aware
Паспорт Вануату
http://amoxil.guru/# amoxicillin 500 mg capsule
Замечательный вопрос
но не надо https://cosmetiquesdynastie.ca/mystore/2020/04/08/effect-of-turmeric-on-skin-health/ отчаиваться! Отточите навыки, разработайте индивидуальность вместе с pokerhouse, научитесь разбираться в куче профессиональных терминов и получать выигрыш деньги.
В этом что-то есть. Огромное спасибо за объяснение, теперь я не допущу такой ошибки.
Покупка документа о высшем образовании с внесением в базу данных https://www.museotriora.it/2012/02/13/sandro-oddo-sti-ani/ – это реально? свидетельство вуза без занесения в список государственном бланке – от 16 000 рублей.
Villas in the ultra-luxury residential community of Tilal al Ghaf Elysian Mansions . Developer Majid al Futtaim offers units for sale at favourable prices.
Мне кажется, что это уже обсуждалось.
как в любой молодой сфере сведений в этой среде книги обычно устаревают в начале своей публикации, http://sanwoolfarm.com/yc5/bbs/board.php?bo_table=free&wr_id=172501 и многие плодотворные идеи передаются из губ в уста.
where to buy ivermectin cream: cheapest stromectol – ivermectin 0.5% lotion
buy paxlovid online Buy Paxlovid privately п»їpaxlovid
is gabapentin used for sciatica
doxycycline rx
управление поисковой репутацией – необходимый инструмент в современных условиях ведения бизнеса и высокой конкуренции. reBooster – репутационное агентство полного цикла. Сформируем положительную репутацию в кратчайшие сроки, скорректируем негативную информацию в интернете. Работаем с различными сферами бизнеса, с у упором на финансовый сектор, медицинские услуги, fmcg и сферу услуг. На рынке с 2014 года.
В этом что-то есть. Благодарю Вас за помощь, как я могу отблагодарить?
несмотря на подобные трудности, сетевой покер продолжает процветать, https://wiki.openhumans.org/wiki/User:DelmarAhuiaOva6 а многие авторитетные сайты предлагают надежную и надежную игровую среду для пользователей по всему миру.
http://clomid.auction/# can i purchase clomid without rx
Apartments and penthouses in the Habtoor Grand Residences, by Al Habtoor with premium service, favourable terms of purchase and excellent return on investment
z8ghSAWZZy8
serm – необходимый инструмент в современных условиях ведения бизнеса и высокой конкуренции. reBooster – репутационное агентство полного цикла. Сформируем положительную репутацию в кратчайшие сроки, скорректируем негативную информацию в интернете. Работаем с различными сферами бизнеса, с у упором на финансовый сектор, медицинские услуги, fmcg и сферу услуг. На рынке с 2014 года.
Быстрое получение Гражданства Вануату от Официального Агента с Гарантией Паспорт Вануату
нормуль
А. Б. Мариенгоф, «это вам, http://bswbeauty.co/?p=106 потомки! ? – безусловно! Мой тузовый покер нарвался на флешь. Актуальная лексика / под ред. Г.
https://prednisone.auction/# prednisone 10mg buy online
uniswap https://uniswap.work/
Может восполнить пробел…
Реалистичнее не существует От неприметного подвала в Пиццерии Ральфа до невероятной Арены бесконечности – играйте на потрясающих уровнях в ultra hd 4k с стопроцентной поддержкой https://cbz.minzdravao.ru/predlozhenie/est-dinastiya-u-pokerdom-group-chat rtx.
Medicines information leaflet. Long-Term Effects.
eldepryl cost
Best information about drugs. Get now.
и такие пораметры есть ))))
работать и организовывать: Организуйте свою работу, https://ytehue.com/san-pham/den-phun-tinh-dau-sach-khong-khi-beurer-la50/ подключаясь и сотрудничая. Запись деловых разговоров: Записывайте все важные деловые заявки, и пользуйтесь ими в разнообразных целях.
концовка предсказуема с самого начала
Далее http://tsmtech.co.kr/bbs/board.php?bo_table=free&wr_id=375666 следует круг торгов. Пот-лимит (англ. pot limit) – игроки могут ставить от минимальной до сервисного размера банка.
Сертификат ISO 9001 – это официальный документ, гарантирующий качество выпускаемого товара, продукта/оказываемой услуги, а так же высокую степень надежности Вашего предприятия стоимость сертификата ИСО 9001 в России
Раслабся !
их можно видеть уже с первой профиля на официальном сайте в виде красочных http://www.kojob.co.kr/bbs/board.php?bo_table=free&wr_id=1047268 пиктограмм.
Присоединяюсь. Так бывает.
смартфонная вариация покер-клуба дарит свободу клиентам, позволяя быть с азартом 24-7. казино pokerdom реально посредством браузер, https://richmill.co.kr/kor/bbs/board.php?bo_table=free&wr_id=1020423 без каких-либо утилит.
Гражданство Вануату
Гражданство Вануату
Вы очень талантливый человек
All canva templates for http://engawa.kakaku.com/jump/?url=https://smm-factory.com/ correspond to the image sizes recommended by each platform, therefore according to your idea, do not have to think changing the size.
prednisone 10 mg side effects in women
cytotec pills buy online: cheap cytotec – cytotec pills buy online
https://finasteride.men/# order generic propecia for sale
Apartments, duplexes and penthouses in the residential development of The Palm Beach Tower Dubai on Palm Jumeirah, Dubai. Developer Nakheel Properties offers units for sale at favourable prices.
всем советую глянуть
buffer: tool management social networks, allowing companies to plan, publish https://4989-4989.com/bbs/board.php?bo_table=free&wr_id=1301884-file – and analyze film content in social networks. 4. Improved audience targeting: social media platforms networks offer enhanced targeting capabilities, allowing companies to reach their specific own audience based on demographic data, interests and behavior.
https://azithromycin.store/# zithromax 250 mg pill
аппарат лазерной эпиляции александрит цена купить профессиональный https://alexanritovie-laser.ru/
z8ghSAWZZy8
amoxicillin allergy
cefepime
sindbad diving aqaba
Saan makakabili ng Diabetin capsules sa Pilipinas? Pagsusuri, opinyon, pagsusuri diabetin benefits
buying cheap propecia without a prescription: buy propecia – buy propecia tablets
Hardex crema comprar en Guatemala precio en farmacia hardex peninsular
lisinopril india price buy lisinopril online can you buy lisinopril online
фракционные со2 лазеры https://laseri-co2.ru/
http://misoprostol.shop/# Cytotec 200mcg price
Интернет казино Glory в Турции может предложить поистине божественный страстный опыт для играющих http://www.rapidclubs.ru/forum/thread97279-1.html#98520
Наши блины для штанг https://diski-bliny-dlya-shtangi.ru подходят для использования в зале и дома. Они используются на силовых занятиях для выполнения разных упражнений на все мышцы. Снаряды выполнены из цельного куска стали и покрыты резиновым слоем. Такая обработка защищает металл от коррозии и уменьшает звуковые эффекты в процессе занятий, а это особенно важно при использовании дисков дома. Посадочное кольцо также изготовлено из металла, но не обрезинивается. Такая методика позволяет избежать повреждений резинового слоя при постоянном снятии/навешивании на гриф, так как само покрытие с ним не соприкасается. Помимо этого, благодаря гладкой втулке блины для штанги отлично скользят, за счет чего можно быстро менять нагрузку. У нас вы сможете приобрести диски нужного веса и внутреннего диаметра для получения качественных спортивных результатов.
opening csgo cases
buy cytotec pills: cheap cytotec – buy cytotec over the counter
bait al aqaba dive center resort
распил ЛДСП
https://furosemide.pro/# furosemida 40 mg
распил ЛДСП
cytotec abortion pill: cytotec buy online usa – Misoprostol 200 mg buy online
Отличный сайт! Всем рекомендую!фрибеты без депозита 2024
can you buy prednisone over the counter in mexico
?Donde comprar Duston Gel en Uruguay? ?Cuanto cuesta? Opiniones y criticas, ?verdad o estafa? Duston Gel Uruguay
buy generic zithromax no prescription: zithromax best price – zithromax generic price
https://azithromycin.store/# how to buy zithromax online
Сертификат ISO 9001 – лучший способ поднять престиж компании и выйти на внешний рынок сертификат менеджмента качества iso 9001
Drugs information leaflet. Drug Class.
eldepryl without rx
Actual news about meds. Get now.
purchase cytotec: buy cytotec online fast delivery – buy cytotec online fast delivery
Medicines information. Cautions.
aurogra buy
Best information about medicament. Read here.
http://lisinopril.fun/# cheapest price for lisinopril india
Отличный сайт! Всем рекомендую!трансферы футбола 2024
Medication information sheet. Short-Term Effects.
can you get glucophage
Best trends of medicines. Get here.
В этом что-то есть. Спасибо за объяснение. Все гениальное просто.
также на площадке казино предлагается полезная информация о правилах игр, pin up покерных бонусах и других нужных аспектах игрового процесса в казино.
cost of cheap propecia without insurance: cost generic propecia without dr prescription – order cheap propecia pills
https://lisinopril.fun/# lisinopril generic drug
Navigate into the Infinite Domain of Minecraft with Us!
On our website, you’ll find everything you need for an mesmerizing adventure in Minecraft: servers with a diversity of mods, beneficial tips, and fascinating articles about the kingdom of blocky adventures! https://remote-wiki.win/index.php?title=Coming_up_with_Mods_for_Minecraft:_Suggestions_and_Methods_77368
z8ghSAWZZy8
Meds information. What side effects can this medication cause?
stromectol
Actual about medicine. Get information now.
lasix furosemide: Buy Lasix – lasix 20 mg
Отличный сайт! Всем рекомендую!чемпионы Европы по футболу
prinivil lisinopril: over the counter lisinopril – lisinopril without rx
https://misoprostol.shop/# purchase cytotec
lisinopril 2.5: cheapest lisinopril – zestril 20 mg cost
На сайте нашего похоронного бюро вы можете ознакомиться с основными тарифами на погребение ритуальное бюро ярославль
https://azithromycin.store/# can i buy zithromax over the counter
Drug information for patients. Generic Name.
avodart
Best information about drugs. Get information here.
https://misoprostol.shop/# buy cytotec over the counter
娛樂城
lasix online: Over The Counter Lasix – furosemide
Pills information for patients. What side effects?
buy generic provigil
Actual information about drug. Read information now.
Согласен, это забавная штука
Законопроект 2713-Д предлагает освободить от налогов выигрыши величиной до 8 казино минимальных зарплат включительно.
https://xn--80aeccht8cge.xn--p1ai/content/vybirayte-luchshee-vybirayte-uspeh
mobic cost assistance
buy cytotec: buy misoprostol – buy cytotec over the counter
Medicine information for patients. Drug Class.
aurogra without a prescription
Some news about medicines. Read here.
кароче даж не знаю
однако такой шаг издержки профессии. Все началось нормально, http://forum.fantasy-online.ru/profile.php?mode=viewprofile&u=860263 а затем под данным делом тут кино в голове произошло, и риск оказался агрессивным.
https://azithromycin.store/# zithromax for sale us
давно хотел посматреть
Эскорт Германия предлагает широкий ассортимент услуг, http://vashtehnadzor.ru/index.php?subaction=userinfo&user=uqyxyz адаптированных к разнообразным потребностям и пожеланиям клиентов.
Medicament information. Cautions.
lisinopril
Best about medicament. Get information here.
lasix 100 mg tablet: Over The Counter Lasix – generic lasix
Я извиняюсь, но, по-моему, Вы допускаете ошибку. Давайте обсудим это. Пишите мне в PM.
Оразбаев, К. Р. Похищение человека, http://garmoniya.uglich.ru/index.php?subaction=userinfo&user=yjyvada торговля представителями человечества и заказ рабского труда как отличительные признаки нелегальной миграции / К.
Medicines information for patients. Brand names.
cialis soft
All news about drugs. Get information now.
Могу поискать ссылку на сайт, на котором есть много статей по этому вопросу.
Да. Всегда. Я настаиваю на том, http://mclassic.com.hk/home.php?mod=space&uid=271178 чтобы они говорили свои полные имена, и должность.
cheap propecia no prescription: buy propecia – buy propecia now
https://furosemide.pro/# buy furosemide online
Харашо
3. Составьте http://www.imperis.ru/product_card/5539/reviews/ свое портфолио. например, вы можете улучшить свои коммуникативные способности, научиться управлять своими нервами и улучшить уровень самодисциплины.
lowest price on prednisone
ой.. не магу больше)))
так я имею возможность выговориться. поэтому даже тот девочки, что выкладывают свои фото и пропозиции об услугах на профильных сайтах, тоже полагают, что они – https://ayurvedaplus.ru/personal/forum/index.php?PAGE_NAME=profile_view&UID=89066.
Medication information for patients. Effects of Drug Abuse.
viagra
Some news about medication. Read information here.
Studios and hotel apartments in the of Five JBR hotel in Jumeirah Beach Residence. Developer FIVE Holding offers units for sale at favourable prices.
miglior sito dove acquistare viagra: alternativa al viagra senza ricetta in farmacia – viagra generico recensioni
https://farmaciaitalia.store/# farmacie online sicure
Этот вопрос не обсуждается.
Наша вежливая и профессиональная команда в любой момент готова помочь всем в компании встречи, учитывая все ваши пожелания, http://www.inetpartners.ru/forum/member.php?u=185306 чтобы предоставить самое комфортное и приятное времяпрепровождение.
Drugs information for patients. Long-Term Effects.
nolvadex
All information about meds. Read information here.
https://pomoguvam.ru/
купить диплом
Я считаю, что Вы ошибаетесь. Давайте обсудим это. Пишите мне в PM, поговорим.
в итоге, эскорт сервис не тупо дарят приятное общество, они привносят клиенту возможность улучшить свою уверенность в себе, http://sosh13.pascal.ru/forum/profile.php?action=show&member=21746 расширить свои горизонты несложно насладиться жизнью.
cialis farmacia senza ricetta: viagra online spedizione gratuita – viagra generico prezzo piГ№ basso
Meds information leaflet. Cautions.
cordarone
Best about medication. Read here.
Наша компания предлагает оборудование спортивное sportivnoe-oborudovanie.ru в ассортименте: грузоблочные машины и нагружаемые блинами, конструкции для занятий с весом своего тела, скамьи и стойки, а также гантели, штанги, гири, комплектующие для них и другой инвентарь. Для выпуска тренажеров применяются первоклассные материалы – сталь, качественные наполнители и экокожа для мягких деталей (сидений, спинок и пр.), безопасные порошковые краски для покрытия конструкций из металла. Наше спортивное силовое оборудование предназначено для интенсивной эксплуатации в режиме 24/7, за счет чего подходит как для средних тренажерных залов, так и для больших фитнес-центров с высокой проходимостью. Для домашнего применения идеально подойдут варианты для работы со своей массой, скамьи, разборные гантели, штанги, гири.
сайдинг под брево
diplomanof.com
farmacia online: kamagra oral jelly – farmaci senza ricetta elenco
Я считаю, что Вы допускаете ошибку. Могу отстоять свою позицию. Пишите мне в PM, поговорим.
Pensaste que tu https://www.craigglassonsmashrepairs.com.au/guarantee/gallery-post-format/ ?atrapada en un centro porno? 2 Series. La madre de mi mejor amigo resulto ser una MILF muy hospitalaria.
http://farmaciaitalia.store/# farmacia online più conveniente
апостиль в новосибирске
Motion Energy gel in Nigeria, where to buy and how much does it cost? Price Motion Energy Gel
farmacie on line spedizione gratuita: kamagra gel – acquistare farmaci senza ricetta
https://www.gta5-mods.com/users/pinupbets1
Не нервничайте, лучше опишите подробно ошибку.
Gibbons calls Cage about changes in meaning, but is impressed when he tells them the information provided by https://wiki.3cdr.ru/wiki/index.php/XXX_Online_k2sxxx.com, the star-struck Kolya.
http://www.dislivelli.eu/forum/viewtopic.php?f=6&t=7197&sid=7a5fa4663e620ef823af4cc27aa9b288
http://avanafilitalia.online/# farmacie online affidabili
а мне нравится… классно…
for now submitting request for receiving bonuses or http://g95887q6.beget.tech/user/v4wrfqt703free bookmakers – 1win, you should to know how to buy them.
We wish to thank you once more for the gorgeous ideas you gave Jeremy when preparing a post-graduate research and,
most importantly, pertaining to providing each
of the ideas in a single blog post. If we had known of your web site a year
ago, we might have been rescued from the useless measures we were
having to take. Thanks to you. toys for adults
Great site, I recommend it to everyone!Arch Town Labs
Medication prescribing information. Long-Term Effects.
neurontin
All news about medicine. Read information here.
farmaci senza ricetta elenco: kamagra gold – farmacie on line spedizione gratuita
https://sildenafilitalia.men/# viagra online spedizione gratuita
cheap super p-force without dr prescription
Medicament information for patients. What side effects?
neurontin
Actual what you want to know about medication. Get information now.
cialis farmacia senza ricetta: viagra online spedizione gratuita – viagra generico recensioni
viagra naturale in farmacia senza ricetta: alternativa al viagra senza ricetta in farmacia – viagra online spedizione gratuita
Мне нравится Ваша идея. Предлагаю вынести на общее обсуждение.
«Счастливый час». В четверг с 15:00 до 18:00 клуб дарит фриспины – пакеты появляются https://casino577.win/evropejskie-kazino в аккаунте игрока.
Apartments and penthouses in the Habtoor Grand Residences, by Al Habtoor with premium service, favourable terms of purchase and excellent return on investment
Various options of apartments and penthouses are offered, providing unparalleled city views. Iconic Towers The project undoubtedly promises a luxurious life in the heart of Dubai
Comprar Sustarox crema en Peru. Precio en Inkafarma, Mercado Libre Sustarox inkafarma
Аренда инструмента для любых целей
прокат инструмента в красноярске без залога https://www.prokat888.ru/.
Купить страховку на квартиру, онлайн – оформите добровольное страхование квартиры от затопления соседей, ремонта, а также вы можете застраховать имущество в квартире – оформите договор страхования квартиры James in the Picture Study Bible – The Book of James with Maps and Background Information (Free Bible Online)
https://kamagraitalia.shop/# farmacia online
https://bellezza4u.ru/
гама казино сайт
farmacie online sicure: avanafil – farmacie online sicure
ага типа гуд
your safety is our main concern, https://casinosporinternet.com/, therefore we have considered and recommended only those gambling establishments that were licensed in Germany and are confirmed as effective, and legal.
Great site, I recommend it to everyone!World’s Innovative Network
SMM
Основная функция: Автоматизация и оптимизация процесса продвижения в социальных сетях.
Поддерживаемые платформы: Facebook, Instagram, Twitter, LinkedIn, VK.
Особенности:
Аналитика: Предоставление детальной статистики по каждой социальной сети, включая анализ аудитории, охват, вовлеченность и эффективность контента.
Автоматизация публикаций: Планировщик публикаций позволяет создавать, графиковать и автоматически размещать контент на всех поддерживаемых платформах.
Генератор контента: Использует искусственный интеллект для создания привлекательного и релевантного контента, адаптированного под каждую социальную сеть.
Интерактивные опросы и голосования: Увеличение вовлеченности аудитории через интерактивные функции, такие как опросы и голосования.
Подбор ключевых слов и хэштегов: Оптимизация постов с помощью анализа и подбора наиболее эффективных ключевых слов и хэштегов.
Управление сообществом: Инструменты для модерации и управления взаимодействиями в социальных сетях, включая отслеживание комментариев и сообщений.
Безопасность и конфиденциальность: Высокий уровень безопасности и защиты личных данных.
Интеграция с другими сервисами: Возможность интеграции с CRM-системами, Google Analytics и другими инструментами цифрового маркетинга.
Пользовательский интерфейс: Простой и интуитивно понятный интерфейс с поддержкой многоязычности.
Поддержка и обучение: Подробные руководства пользователя и видеоуроки, а также круглосуточная поддержка клиентов.
http://farmaciaitalia.store/# farmacia online migliore
Извините за то, что вмешиваюсь… Но мне очень близка эта тема. Могу помочь с ответом.
In the https://wiki.3cdr.ru/wiki/index.php/XXX_Online_k2sxxx.com short film, Xander is played by Vin Diesel’s understudy Christian Lupo (who in his life shows his citizens and not spoken yet), reusing some archival remarks uttered by Diesel.
Замечательно, это весьма ценная штука
Choose the appropriate font sizes, the https://funkanometry.org/shopdaddy-studio, considering the average age of your target group and whims lighting in your restaurant.
кет казино
farmacia online piГ№ conveniente: Tadalafil generico – migliori farmacie online 2023
свой в альфе
Medicines information. Long-Term Effects.
order tadacip
Actual about medicine. Read information now.
https://kamagraitalia.shop/# acquisto farmaci con ricetta
Строительная экспертиза в Москве от организации Строительная экспертиза недорого и с гарантией.
cost mobic without rx
farmacia online senza ricetta: kamagra – migliori farmacie online 2023
Great site, I recommend it to everyone!World Innovation Ranking 2024
Имеются ли аналоги?
Before the release of their self-titled first album, http://foradhoras.com.pt/but-they-are-confident-pursuing-specific-goals/ for pyros embarked on a nationwide tour in support of a unknown band.
Meds information for patients. Brand names.
prednisone
Actual about drug. Read information now.
->>>>>>>>>>>>>снятия приворота яйцом<<<<<<<<<-
______________как по фото приворожить мужчину _____________
приворот девушки на расстоянии
как раб божий не может жить и быть, а также:
->>>>>>безопасный приворот на любовь мужчину читать в домашних условиях
->>>>>>приворот на мужчину чтобы скучал
->>>>>>заклинания на любовь парня в домашних условиях
->>>>>>заговор на любовь мужчины на ночь
приворот признаки
http://kamagraitalia.shop/# farmacia online migliore
viagra naturale: sildenafil 100mg prezzo – farmacia senza ricetta recensioni
farmacie on line spedizione gratuita: farmacia online miglior prezzo – farmacie online autorizzate elenco
http://foroexplayate.com/phpBB3/viewtopic.php?f=44&t=62560
100 mg doxycycline dosage
Абсолютно с Вами согласен. Мне кажется это очень хорошая идея. Полностью с Вами соглашусь.
Однако ничто не мешает и заведомым преступникам войти в http://arskland.ru/people/user/14605/, прикрываясь все той же анонимностью.
http://indiapharm.life/# top online pharmacy india
canadian pharmacy prices: cheap canadian pharmacy – canadian medications
Прошу прощения, что ничем не могу помочь. Надеюсь, Вам здесь помогут другие.
Для следующего этапа выбора фильмов возьмите http://economreklama.ru/index.php?subaction=userinfo&user=ekosoh сайт rotten tomatoes. дополнительным плюсом является то, что фильмы можно заливать на компьютерное устройство.
Exclusive villas and mansions in the residential development of Signature Mansions Dubai in Jumeirah Golf Estates. Developer Signature Developers offers units for sale at favourable prices.
https://oknaplusdnr.com/
farxiga information
http://canadapharm.shop/# canadian drugs online
Website
mexico pharmacy: reputable mexican pharmacies online – mexico pharmacies prescription drugs
mail order pharmacy india: indian pharmacy – best online pharmacy india
Luxury mansions in the exclusive residential community of Roberto Cavalli villas Dubai . Developer DAMAC Properties offers units for sale at favourable prices.
Relifix Crema: La Eleccion Ideal en Guatemala para Cuidado de la Piel – Precios y Puntos de Venta en Farmacias Relifix Pomada Guatemala
В этом что-то есть. Спасибо за помощь в этом вопросе, может я тоже могу Вам чем то помочь?
это актуально для в первую очередь не профилей в вконтакте и фейсбук, а банковских информации и уточняющей сведениями об используемой карте, включая три важные цифры на обратной стороне карты, http://arenda.mineralgroup.ru/index.php?subaction=userinfo&user=yrery значит будьте внимательны.
неплохо
on our resource collected all proven internet playgrounds, what our pastry chefs can find, and those that we have tested and verified for compliance installations of https://k-rin.com/keirin-kojinordantai/, ensure their security.
how long does cetirizine last for
Website
2024娛樂城的創新趨勢
隨著2024年的到來,娛樂城業界正經歷著一場革命性的變遷。這一年,娛樂城不僅僅是賭博和娛樂的代名詞,更成為了科技創新和用戶體驗的集大成者。
首先,2024年的娛樂城極大地融合了最新的技術。增強現實(AR)和虛擬現實(VR)技術的引入,為玩家提供了沉浸式的賭博體驗。這種全新的遊戲方式不僅帶來視覺上的震撼,還為玩家創造了一種置身於真實賭場的感覺,而實際上他們可能只是坐在家中的沙發上。
其次,人工智能(AI)在娛樂城中的應用也達到了新高度。AI技術不僅用於增強遊戲的公平性和透明度,還在個性化玩家體驗方面發揮著重要作用。從個性化遊戲推薦到智能客服,AI的應用使得娛樂城更能滿足玩家的個別需求。
此外,線上娛樂城的安全性和隱私保護也獲得了顯著加強。隨著技術的進步,更加先進的加密技術和安全措施被用來保護玩家的資料和交易,從而確保一個安全可靠的遊戲環境。
2024年的娛樂城還強調負責任的賭博。許多平台採用了各種工具和資源來幫助玩家控制他們的賭博行為,如設置賭注限制、自我排除措施等,體現了對可持續賭博的承諾。
總之,2024年的娛樂城呈現出一個高度融合了技術、安全和負責任賭博的行業新面貌,為玩家提供了前所未有的娛樂體驗。隨著這些趨勢的持續發展,我們可以預見,娛樂城將不斷地創新和進步,為玩家帶來更多精彩和安全的娛樂選擇。
cheapest online pharmacy india: india pharmacy – world pharmacy india
mexican border pharmacies shipping to usa mexico drug stores pharmacies mexican pharmaceuticals online
https://mexicanpharm.store/# medication from mexico pharmacy
娛樂城
2024娛樂城的創新趨勢
隨著2024年的到來,娛樂城業界正經歷著一場革命性的變遷。這一年,娛樂城不僅僅是賭博和娛樂的代名詞,更成為了科技創新和用戶體驗的集大成者。
首先,2024年的娛樂城極大地融合了最新的技術。增強現實(AR)和虛擬現實(VR)技術的引入,為玩家提供了沉浸式的賭博體驗。這種全新的遊戲方式不僅帶來視覺上的震撼,還為玩家創造了一種置身於真實賭場的感覺,而實際上他們可能只是坐在家中的沙發上。
其次,人工智能(AI)在娛樂城中的應用也達到了新高度。AI技術不僅用於增強遊戲的公平性和透明度,還在個性化玩家體驗方面發揮著重要作用。從個性化遊戲推薦到智能客服,AI的應用使得娛樂城更能滿足玩家的個別需求。
此外,線上娛樂城的安全性和隱私保護也獲得了顯著加強。隨著技術的進步,更加先進的加密技術和安全措施被用來保護玩家的資料和交易,從而確保一個安全可靠的遊戲環境。
2024年的娛樂城還強調負責任的賭博。許多平台採用了各種工具和資源來幫助玩家控制他們的賭博行為,如設置賭注限制、自我排除措施等,體現了對可持續賭博的承諾。
總之,2024年的娛樂城呈現出一個高度融合了技術、安全和負責任賭博的行業新面貌,為玩家提供了前所未有的娛樂體驗。隨著這些趨勢的持續發展,我們可以預見,娛樂城將不斷地創新和進步,為玩家帶來更多精彩和安全的娛樂選擇。
Подготовка и сдача бухгалтерской, налоговой и статистической отчетности в срок бухгалтерское обслуживание ооо цены
canadian pharmacy oxycodone: best mail order pharmacy canada – safe online pharmacies in canada
http://indiapharm.life/# world pharmacy india
how long should you take levaquin 500 mg
best online pharmacy india: buy medicines online in india – indian pharmacies safe
娛樂城
2024娛樂城的創新趨勢
隨著2024年的到來,娛樂城業界正經歷著一場革命性的變遷。這一年,娛樂城不僅僅是賭博和娛樂的代名詞,更成為了科技創新和用戶體驗的集大成者。
首先,2024年的娛樂城極大地融合了最新的技術。增強現實(AR)和虛擬現實(VR)技術的引入,為玩家提供了沉浸式的賭博體驗。這種全新的遊戲方式不僅帶來視覺上的震撼,還為玩家創造了一種置身於真實賭場的感覺,而實際上他們可能只是坐在家中的沙發上。
其次,人工智能(AI)在娛樂城中的應用也達到了新高度。AI技術不僅用於增強遊戲的公平性和透明度,還在個性化玩家體驗方面發揮著重要作用。從個性化遊戲推薦到智能客服,AI的應用使得娛樂城更能滿足玩家的個別需求。
此外,線上娛樂城的安全性和隱私保護也獲得了顯著加強。隨著技術的進步,更加先進的加密技術和安全措施被用來保護玩家的資料和交易,從而確保一個安全可靠的遊戲環境。
2024年的娛樂城還強調負責任的賭博。許多平台採用了各種工具和資源來幫助玩家控制他們的賭博行為,如設置賭注限制、自我排除措施等,體現了對可持續賭博的承諾。
總之,2024年的娛樂城呈現出一個高度融合了技術、安全和負責任賭博的行業新面貌,為玩家提供了前所未有的娛樂體驗。隨著這些趨勢的持續發展,我們可以預見,娛樂城將不斷地創新和進步,為玩家帶來更多精彩和安全的娛樂選擇。
Online medicine home delivery: Online medicine home delivery – indian pharmacy paypal
https://indiapharm.life/# top 10 pharmacies in india
An exciting selection of 1-2 bedroom residences in the new project of Zuha Island by Zaya on World Islands, Dubai. Developers ZAYA & FIVE offers a collection of just 30 exclusive luxury real estate units at attractive prices.
medicine in mexico pharmacies: reputable mexican pharmacies online – п»їbest mexican online pharmacies
What’s up, every time i used to check blog poats here in the early hours in the break of day, as i enjoy to learn more and more.
Also visit my homepage – Celebrity Reputation Agencies
onlinepharmaciescanada com canadian pharmacy mall canadian pharmacy ratings
3a娛樂城
песок с доставкой
cheapest pharmacy canada: safe online pharmacies in canada – best canadian pharmacy online
https://canadapharm.shop/# pet meds without vet prescription canada
buying prescription drugs in mexico: reputable mexican pharmacies online – pharmacies in mexico that ship to usa
перевод документов
3a娛樂城
3a娛樂城
pharmacy in canada: canadian pharmacy cheap – is canadian pharmacy legit
http://canadapharm.shop/# buy prescription drugs from canada cheap
порно видео бесплатно в хорошем качестве
indianpharmacy com: mail order pharmacy india – india pharmacy
Dubai, a city known for its opulence and modernity, demands a mode of transportation that reflects its grandeur. For those seeking a cost-effective and reliable long-term solution, Somonion Rent Car LLC emerges as the premier choice for monthly car rentals in Dubai. With a diverse fleet ranging from compact cars to premium vehicles, the company promises an unmatched blend of affordability, flexibility, and personalized service.
Favorable Rental Conditions:
Understanding the potential financial strain of long-term car rentals, Somonion Rent Car LLC aims to make your journey more economical. The company offers flexible rental terms coupled with exclusive discounts for loyal customers. This commitment to affordability extends beyond the rental cost, as additional services such as insurance, maintenance, and repair ensure your safety and peace of mind throughout the duration of your rental.
A Plethora of Options:
Somonion Rent Car LLC boasts an extensive selection of vehicles to cater to diverse preferences and budgets. Whether you’re in the market for a sleek sedan or a spacious crossover, the company has the perfect car to complement your needs. The transparency in pricing, coupled with the ease of booking through their online platform, makes Somonion Rent Car LLC a hassle-free solution for those embarking on a long-term adventure in Dubai.
Car Rental Services Tailored for You:
Somonion Rent Car LLC doesn’t just offer cars; it provides a comprehensive range of rental services tailored to suit various occasions. From daily and weekly rentals to airport transfers and business travel, the company ensures that your stay in Dubai is not only comfortable but also exudes prestige. The fleet includes popular models such as the Nissan Altima 2018, KIA Forte 2018, Hyundai Elantra 2018, and the Toyota Camry Sport Edition 2020, all available for monthly rentals at competitive rates.
Featured Deals and Specials:
Somonion Rent Car LLC constantly updates its offerings to provide customers with the best deals. Featured cars like the Hyundai Sonata 2018 and Hyundai Santa Fe 2018 add a touch of luxury to your rental experience, with daily rates starting as low as AED 100. The company’s commitment to affordable luxury is further emphasized by the online booking system, allowing customers to secure the best deals in real-time through their website or by contacting the experts via phone or WhatsApp.
Conclusion:
Whether you’re a tourist looking to explore Dubai at your pace or a business traveler in need of a reliable and prestigious mode of transportation, Somonion Rent Car LLC stands as the go-to choice for monthly car rentals in Dubai. Unlock the ultimate mobility experience with Somonion, where affordability meets excellence, ensuring your journey through Dubai is as seamless and luxurious as the city itself. Contact Somonion Rent Car LLC today and embark on a journey where every mile is a testament to comfort, style, and unmatched service.
Car hire long term dubai
Dubai, a city of grandeur and innovation, demands a transportation solution that matches its dynamic pace. Whether you’re a business executive, a tourist exploring the city, or someone in need of a reliable vehicle temporarily, car rental services in Dubai offer a flexible and cost-effective solution. In this guide, we’ll explore the popular car rental options in Dubai, catering to diverse needs and preferences.
Airport Car Rental: One-Way Pickup and Drop-off Road Trip Rentals:
For those who need to meet an important delegation at the airport or have a flight to another city, airport car rentals provide a seamless solution. Avoid the hassle of relying on public transport and ensure you reach your destination on time. With one-way pickup and drop-off options, you can effortlessly navigate your road trip, making business meetings or conferences immediately upon arrival.
Business Car Rental Deals & Corporate Vehicle Rentals in Dubai:
Companies without their own fleet or those finding transport maintenance too expensive can benefit from business car rental deals. This option is particularly suitable for businesses where a vehicle is needed only occasionally. By opting for corporate vehicle rentals, companies can optimize their staff structure, freeing employees from non-core functions while ensuring reliable transportation when necessary.
Tourist Car Rentals with Insurance in Dubai:
Tourists visiting Dubai can enjoy the freedom of exploring the city at their own pace with car rentals that come with insurance. This option allows travelers to choose a vehicle that suits the particulars of their trip without the hassle of dealing with insurance policies. Renting a car not only saves money and time compared to expensive city taxis but also ensures a trouble-free travel experience.
Daily Car Hire Near Me:
Daily car rental services are a convenient and cost-effective alternative to taxis in Dubai. Whether it’s for a business meeting, everyday use, or a luxury experience, you can find a suitable vehicle for a day on platforms like Smarketdrive.com. The website provides a secure and quick way to rent a car from certified and verified car rental companies, ensuring guarantees and safety.
Weekly Auto Rental Deals:
For those looking for flexibility throughout the week, weekly car rentals in Dubai offer a competent, attentive, and professional service. Whether you need a vehicle for a few days or an entire week, choosing a car rental weekly is a convenient and profitable option. The certified and tested car rental companies listed on Smarketdrive.com ensure a reliable and comfortable experience.
Monthly Car Rentals in Dubai:
When your personal car is undergoing extended repairs, or if you’re a frequent visitor to Dubai, monthly car rentals (long-term car rentals) become the ideal solution. Residents, businessmen, and tourists can benefit from the extensive options available on Smarketdrive.com, ensuring mobility and convenience throughout their stay in Dubai.
FAQ about Renting a Car in Dubai:
To address common queries about renting a car in Dubai, our FAQ section provides valuable insights and information. From rental terms to insurance coverage, it serves as a comprehensive guide for those considering the convenience of car rentals in the bustling city.
Conclusion:
Dubai’s popularity as a global destination is matched by its diverse and convenient car rental services. Whether for business, tourism, or daily commuting, the options available cater to every need. With reliable platforms like Smarketdrive.com, navigating Dubai becomes a seamless and enjoyable experience, offering both locals and visitors the ultimate freedom of mobility.
http://indiapharm.life/# Online medicine order
likebot youtube
Medicament information leaflet. Long-Term Effects.
eldepryl
Some what you want to know about medicament. Get information here.
canada discount pharmacy: canadian pharmacy world – my canadian pharmacy
mexico pharmacies prescription drugs: buying from online mexican pharmacy – medicine in mexico pharmacies
mexican rx online: mexican rx online – pharmacies in mexico that ship to usa
where can i buy synthroid without prescription
https://canadapharm.shop/# recommended canadian pharmacies
buying from online mexican pharmacy medicine in mexico pharmacies buying from online mexican pharmacy
Ultra-luxury penthouses, Sky Villas and a Sky Mansion in the complex of One Canal Dubai, located on the banks of Dubai Water Canal in Al Safa. Developer AHS Properties offers units for sale at favourable prices.
2024娛樂城的創新趨勢
隨著2024年的到來,娛樂城業界正經歷著一場革命性的變遷。這一年,娛樂城不僅僅是賭博和娛樂的代名詞,更成為了科技創新和用戶體驗的集大成者。
首先,2024年的娛樂城極大地融合了最新的技術。增強現實(AR)和虛擬現實(VR)技術的引入,為玩家提供了沉浸式的賭博體驗。這種全新的遊戲方式不僅帶來視覺上的震撼,還為玩家創造了一種置身於真實賭場的感覺,而實際上他們可能只是坐在家中的沙發上。
其次,人工智能(AI)在娛樂城中的應用也達到了新高度。AI技術不僅用於增強遊戲的公平性和透明度,還在個性化玩家體驗方面發揮著重要作用。從個性化遊戲推薦到智能客服,AI的應用使得娛樂城更能滿足玩家的個別需求。
此外,線上娛樂城的安全性和隱私保護也獲得了顯著加強。隨著技術的進步,更加先進的加密技術和安全措施被用來保護玩家的資料和交易,從而確保一個安全可靠的遊戲環境。
2024年的娛樂城還強調負責任的賭博。許多平台採用了各種工具和資源來幫助玩家控制他們的賭博行為,如設置賭注限制、自我排除措施等,體現了對可持續賭博的承諾。
總之,2024年的娛樂城呈現出一個高度融合了技術、安全和負責任賭博的行業新面貌,為玩家提供了前所未有的娛樂體驗。隨著這些趨勢的持續發展,我們可以預見,娛樂城將不斷地創新和進步,為玩家帶來更多精彩和安全的娛樂選擇。
Dubai, a city known for its opulence and modernity, demands a mode of transportation that reflects its grandeur. For those seeking a cost-effective and reliable long-term solution, Somonion Rent Car LLC emerges as the premier choice for monthly car rentals in Dubai. With a diverse fleet ranging from compact cars to premium vehicles, the company promises an unmatched blend of affordability, flexibility, and personalized service.
Favorable Rental Conditions:
Understanding the potential financial strain of long-term car rentals, Somonion Rent Car LLC aims to make your journey more economical. The company offers flexible rental terms coupled with exclusive discounts for loyal customers. This commitment to affordability extends beyond the rental cost, as additional services such as insurance, maintenance, and repair ensure your safety and peace of mind throughout the duration of your rental.
A Plethora of Options:
Somonion Rent Car LLC boasts an extensive selection of vehicles to cater to diverse preferences and budgets. Whether you’re in the market for a sleek sedan or a spacious crossover, the company has the perfect car to complement your needs. The transparency in pricing, coupled with the ease of booking through their online platform, makes Somonion Rent Car LLC a hassle-free solution for those embarking on a long-term adventure in Dubai.
Car Rental Services Tailored for You:
Somonion Rent Car LLC doesn’t just offer cars; it provides a comprehensive range of rental services tailored to suit various occasions. From daily and weekly rentals to airport transfers and business travel, the company ensures that your stay in Dubai is not only comfortable but also exudes prestige. The fleet includes popular models such as the Nissan Altima 2018, KIA Forte 2018, Hyundai Elantra 2018, and the Toyota Camry Sport Edition 2020, all available for monthly rentals at competitive rates.
Featured Deals and Specials:
Somonion Rent Car LLC constantly updates its offerings to provide customers with the best deals. Featured cars like the Hyundai Sonata 2018 and Hyundai Santa Fe 2018 add a touch of luxury to your rental experience, with daily rates starting as low as AED 100. The company’s commitment to affordable luxury is further emphasized by the online booking system, allowing customers to secure the best deals in real-time through their website or by contacting the experts via phone or WhatsApp.
Conclusion:
Whether you’re a tourist looking to explore Dubai at your pace or a business traveler in need of a reliable and prestigious mode of transportation, Somonion Rent Car LLC stands as the go-to choice for monthly car rentals in Dubai. Unlock the ultimate mobility experience with Somonion, where affordability meets excellence, ensuring your journey through Dubai is as seamless and luxurious as the city itself. Contact Somonion Rent Car LLC today and embark on a journey where every mile is a testament to comfort, style, and unmatched service.
https://wildlife.by/images/pages/?1xbet_kazino_promokod.html
mexican mail order pharmacies: pharmacies in mexico that ship to usa – purple pharmacy mexico price list
http://mexicanpharm.store/# mexican pharmacy
После решения вести здоровый образ жизни, я осознал необходимость в соковыжималке механической. ‘Все соки’ предоставили мне именно то, что мне нужно. Их механическая соковыжималка проста в использовании и очень эффективна. https://h-100.ru/collection/ruchnye-shnekovye-sokovyzhimalki – Соковыжималка механическая стала моим незаменимым помощником.
https://www.04597.com.ua/list/387163
Магическая помощь – сильные экстрасенсы
приворот на воду на любовь https://gadalkindom.ru легкий любовный приворот
привороты на любовь мужчины читать в домашних условиях самостоятельно
Great site! I recommend to everyone!World Innovation Ranking 2024
Pin-Up es una casa de apuestas internacional con licencia de Curazao, que ahora opera legalmente tambien en Peru https://shaneiatk43321.post-blogs.com/45853977/pin-up-peru-your-gateway-to-fascinating-betting-and-gambling-activities
娛樂城推薦
2024娛樂城的創新趨勢
隨著2024年的到來,娛樂城業界正經歷著一場革命性的變遷。這一年,娛樂城不僅僅是賭博和娛樂的代名詞,更成為了科技創新和用戶體驗的集大成者。
首先,2024年的娛樂城極大地融合了最新的技術。增強現實(AR)和虛擬現實(VR)技術的引入,為玩家提供了沉浸式的賭博體驗。這種全新的遊戲方式不僅帶來視覺上的震撼,還為玩家創造了一種置身於真實賭場的感覺,而實際上他們可能只是坐在家中的沙發上。
其次,人工智能(AI)在娛樂城中的應用也達到了新高度。AI技術不僅用於增強遊戲的公平性和透明度,還在個性化玩家體驗方面發揮著重要作用。從個性化遊戲推薦到智能客服,AI的應用使得娛樂城更能滿足玩家的個別需求。
此外,線上娛樂城的安全性和隱私保護也獲得了顯著加強。隨著技術的進步,更加先進的加密技術和安全措施被用來保護玩家的資料和交易,從而確保一個安全可靠的遊戲環境。
2024年的娛樂城還強調負責任的賭博。許多平台採用了各種工具和資源來幫助玩家控制他們的賭博行為,如設置賭注限制、自我排除措施等,體現了對可持續賭博的承諾。
總之,2024年的娛樂城呈現出一個高度融合了技術、安全和負責任賭博的行業新面貌,為玩家提供了前所未有的娛樂體驗。隨著這些趨勢的持續發展,我們可以預見,娛樂城將不斷地創新和進步,為玩家帶來更多精彩和安全的娛樂選擇。
п»їbest mexican online pharmacies: buying prescription drugs in mexico – mexican online pharmacies prescription drugs
Кент Казино
https://autohits.by/
http://mexicanpharm.store/# best mexican online pharmacies
reputable mexican pharmacies online: buying prescription drugs in mexico online – п»їbest mexican online pharmacies
ПокерОк
ПокерОк
best online pharmacy india: Online medicine order – п»їlegitimate online pharmacies india
what does levaquin 500 mg treat
https://canadapharm.shop/# canadianpharmacy com
2024娛樂城的創新趨勢
隨著2024年的到來,娛樂城業界正經歷著一場革命性的變遷。這一年,娛樂城不僅僅是賭博和娛樂的代名詞,更成為了科技創新和用戶體驗的集大成者。
首先,2024年的娛樂城極大地融合了最新的技術。增強現實(AR)和虛擬現實(VR)技術的引入,為玩家提供了沉浸式的賭博體驗。這種全新的遊戲方式不僅帶來視覺上的震撼,還為玩家創造了一種置身於真實賭場的感覺,而實際上他們可能只是坐在家中的沙發上。
其次,人工智能(AI)在娛樂城中的應用也達到了新高度。AI技術不僅用於增強遊戲的公平性和透明度,還在個性化玩家體驗方面發揮著重要作用。從個性化遊戲推薦到智能客服,AI的應用使得娛樂城更能滿足玩家的個別需求。
此外,線上娛樂城的安全性和隱私保護也獲得了顯著加強。隨著技術的進步,更加先進的加密技術和安全措施被用來保護玩家的資料和交易,從而確保一個安全可靠的遊戲環境。
2024年的娛樂城還強調負責任的賭博。許多平台採用了各種工具和資源來幫助玩家控制他們的賭博行為,如設置賭注限制、自我排除措施等,體現了對可持續賭博的承諾。
總之,2024年的娛樂城呈現出一個高度融合了技術、安全和負責任賭博的行業新面貌,為玩家提供了前所未有的娛樂體驗。隨著這些趨勢的持續發展,我們可以預見,娛樂城將不斷地創新和進步,為玩家帶來更多精彩和安全的娛樂選擇。
https://www.magecam.ru
Услуги магов
-привороты
-наведение порчи на смерть
-отнятие удачи
-возврат любимого
приворот бабник
Моя история изменения к лучшему началась с покупки https://h-100.ru/collection/sokovyzhimalki-dlya-granata – соковыжималки для гранатового сока в “Все соки”. Простота использования и великолепный вкус свежевыжатых соков помогли мне пересмотреть свои привычки и полюбить здоровое питание.
liquid prednisone adult dose
кальянная Атмосферная кальянная в СПб с хорошими кальянами и едой.
Черный маг
заговор на любовь на сигарету https://gadalkindom.ru сильный заговор на звонок любимого в этот же день читать
как в темной непроглядной ночи луна и демон вместе обитают
https://zerkaloff.ru/img/pgs/promokod-1xbet_bonus.html
отвороты, превороты, порча https://www.magecam.ru порча на животных гвоздями
effexor and tamoxifen
интернет магазин куртки женские зимний
With many hundreds of Forex / CFD brokers to choose from globally, finding the right broker for you can seem an impossible challenge best trading app
http://cytotec.directory/# buy cytotec over the counter
cipro antibiotic
cost of zithromax 2mg
Отличный сайт! Всем рекомендую! Только тут Вы можете приобрестикупить чехол для телефона
любовный приворот на растущую луну – Помощь экстрасенса https://www.magecam.ru – надо позвонить костику а он уже сам звонит прочитав твои мысли как говорится заговоры на любовь мужчины на расстоянии читать в домашних
where can i get zithromax: zithromax drug – zithromax cost uk
Mercedes for rent dubai
Dubai, a city known for its opulence and modernity, demands a mode of transportation that reflects its grandeur. For those seeking a cost-effective and reliable long-term solution, Somonion Rent Car LLC emerges as the premier choice for monthly car rentals in Dubai. With a diverse fleet ranging from compact cars to premium vehicles, the company promises an unmatched blend of affordability, flexibility, and personalized service.
Favorable Rental Conditions:
Understanding the potential financial strain of long-term car rentals, Somonion Rent Car LLC aims to make your journey more economical. The company offers flexible rental terms coupled with exclusive discounts for loyal customers. This commitment to affordability extends beyond the rental cost, as additional services such as insurance, maintenance, and repair ensure your safety and peace of mind throughout the duration of your rental.
A Plethora of Options:
Somonion Rent Car LLC boasts an extensive selection of vehicles to cater to diverse preferences and budgets. Whether you’re in the market for a sleek sedan or a spacious crossover, the company has the perfect car to complement your needs. The transparency in pricing, coupled with the ease of booking through their online platform, makes Somonion Rent Car LLC a hassle-free solution for those embarking on a long-term adventure in Dubai.
Car Rental Services Tailored for You:
Somonion Rent Car LLC doesn’t just offer cars; it provides a comprehensive range of rental services tailored to suit various occasions. From daily and weekly rentals to airport transfers and business travel, the company ensures that your stay in Dubai is not only comfortable but also exudes prestige. The fleet includes popular models such as the Nissan Altima 2018, KIA Forte 2018, Hyundai Elantra 2018, and the Toyota Camry Sport Edition 2020, all available for monthly rentals at competitive rates.
Featured Deals and Specials:
Somonion Rent Car LLC constantly updates its offerings to provide customers with the best deals. Featured cars like the Hyundai Sonata 2018 and Hyundai Santa Fe 2018 add a touch of luxury to your rental experience, with daily rates starting as low as AED 100. The company’s commitment to affordable luxury is further emphasized by the online booking system, allowing customers to secure the best deals in real-time through their website or by contacting the experts via phone or WhatsApp.
Conclusion:
Whether you’re a tourist looking to explore Dubai at your pace or a business traveler in need of a reliable and prestigious mode of transportation, Somonion Rent Car LLC stands as the go-to choice for monthly car rentals in Dubai. Unlock the ultimate mobility experience with Somonion, where affordability meets excellence, ensuring your journey through Dubai is as seamless and luxurious as the city itself. Contact Somonion Rent Car LLC today and embark on a journey where every mile is a testament to comfort, style, and unmatched service.
cordarone 200 mg tablet uk
https://prednisonepharm.store/# 50mg prednisone tablet
скачать клиент Покерок для ПК
https://lossless71.ru
can you buy generic sildigra online
как снять приворот видео https://www.magecam.ru приворот на любовь жену и еще одну
приворот женщины на любовь который нельзя снять
chlamydia doxycycline treatment time
no prescription online prednisone: cheap prednisone 20 mg – prednisone 20mg online pharmacy
inderalici
Отличный сайт! Всем рекомендую! Только тут Вы можете приобрестичехол книжка для телефона
Отдых в Анапе https://otdyh-vanape.ru/
https://prednisonepharm.store/# buy prednisone canadian pharmacy
how is fluoxetine distributed in the bodyvdogs
can dogs take trazodone
Березин Андрей Евроинвест https://mainfin.ru/persona/berezin-andrey-valeryevich/.
levaquin levofloxacin 500mg
buy finasteride online 5mg
zithromax 500mg price in india: buy zithromax 1000 mg online – buy generic zithromax no prescription
http://nolvadex.pro/# liquid tamoxifen
can i buy generic levaquin pills
trazodone hydrochloride
Когда я решил делать домашнюю пастилу, мне понадобился надежный дегидратор. Благодаря ‘Все соки’, я нашел идеальный. https://h-100.ru/collection/degidratory – Дегидратор для пастилы от ‘Все соки’ позволяет мне создавать вкусные и здоровые лакомства дома!
where to get generic zithromax for sale
can you buy finpecia without insurance
cytotec online: buy cytotec – cytotec buy online usa
doxycycline mono 50 mg
https://clomidpharm.shop/# can you buy cheap clomid without insurance
Watches World
Watches World: Elevating Luxury and Style with Exquisite Timepieces
Introduction:
Jewelry has always been a timeless expression of elegance, and nothing complements one’s style better than a luxurious timepiece. At Watches World, we bring you an exclusive collection of coveted luxury watches that not only tell time but also serve as a testament to your refined taste. Explore our curated selection featuring iconic brands like Rolex, Hublot, Omega, Cartier, and more, as we redefine the art of accessorizing.
A Dazzling Array of Luxury Watches:
Watches World offers an unparalleled range of exquisite timepieces from renowned brands, ensuring that you find the perfect accessory to elevate your style. Whether you’re drawn to the classic sophistication of Rolex, the avant-garde designs of Hublot, or the precision engineering of Patek Philippe, our collection caters to diverse preferences.
Customer Testimonials:
Our commitment to providing an exceptional customer experience is reflected in the reviews from our satisfied clientele. O.M. commends our excellent communication and flawless packaging, while Richard Houtman appreciates the helpfulness and courtesy of our team. These testimonials highlight our dedication to transparency, communication, and customer satisfaction.
New Arrivals:
Stay ahead of the curve with our latest additions, including the Tudor Black Bay Ceramic 41mm, Richard Mille RM35-01 Rafael Nadal NTPT Carbon Limited Edition, and the Rolex Oyster Perpetual Datejust 41mm series. These new arrivals showcase cutting-edge designs and impeccable craftsmanship, ensuring you stay on the forefront of luxury watch fashion.
Best Sellers:
Discover our best-selling watches, such as the Bulgari Serpenti Tubogas 35mm and the Cartier Panthere Medium Model. These timeless pieces combine elegance with precision, making them a staple in any sophisticated wardrobe.
Expert’s Selection:
Our experts have carefully curated a selection of watches, including the Cartier Panthere Small Model, Omega Speedmaster Moonwatch 44.25 mm, and Rolex Oyster Perpetual Cosmograph Daytona 40mm. These choices exemplify the epitome of watchmaking excellence and style.
Secured and Tracked Delivery:
At Watches World, we prioritize the safety of your purchase. Our secured and tracked delivery ensures that your exquisite timepiece reaches you in perfect condition, giving you peace of mind with every order.
Passionate Experts at Your Service:
Our team of passionate watch experts is dedicated to providing personalized service. From assisting you in choosing the perfect timepiece to addressing any inquiries, we are here to make your watch-buying experience seamless and enjoyable.
Global Presence:
With a presence in key cities around the world, including Dubai, Geneva, Hong Kong, London, Miami, Paris, Prague, Dublin, Singapore, and Sao Paulo, Watches World brings luxury timepieces to enthusiasts globally.
Conclusion:
Watches World goes beyond being an online platform for luxury watches; it is a destination where expertise, trust, and satisfaction converge. Explore our collection, and let our timeless timepieces become an integral part of your style narrative. Join us in redefining luxury, one exquisite watch at a time.
Dubai, a city of grandeur and innovation, demands a transportation solution that matches its dynamic pace. Whether you’re a business executive, a tourist exploring the city, or someone in need of a reliable vehicle temporarily, car rental services in Dubai offer a flexible and cost-effective solution. In this guide, we’ll explore the popular car rental options in Dubai, catering to diverse needs and preferences.
Airport Car Rental: One-Way Pickup and Drop-off Road Trip Rentals:
For those who need to meet an important delegation at the airport or have a flight to another city, airport car rentals provide a seamless solution. Avoid the hassle of relying on public transport and ensure you reach your destination on time. With one-way pickup and drop-off options, you can effortlessly navigate your road trip, making business meetings or conferences immediately upon arrival.
Business Car Rental Deals & Corporate Vehicle Rentals in Dubai:
Companies without their own fleet or those finding transport maintenance too expensive can benefit from business car rental deals. This option is particularly suitable for businesses where a vehicle is needed only occasionally. By opting for corporate vehicle rentals, companies can optimize their staff structure, freeing employees from non-core functions while ensuring reliable transportation when necessary.
Tourist Car Rentals with Insurance in Dubai:
Tourists visiting Dubai can enjoy the freedom of exploring the city at their own pace with car rentals that come with insurance. This option allows travelers to choose a vehicle that suits the particulars of their trip without the hassle of dealing with insurance policies. Renting a car not only saves money and time compared to expensive city taxis but also ensures a trouble-free travel experience.
Daily Car Hire Near Me:
Daily car rental services are a convenient and cost-effective alternative to taxis in Dubai. Whether it’s for a business meeting, everyday use, or a luxury experience, you can find a suitable vehicle for a day on platforms like Smarketdrive.com. The website provides a secure and quick way to rent a car from certified and verified car rental companies, ensuring guarantees and safety.
Weekly Auto Rental Deals:
For those looking for flexibility throughout the week, weekly car rentals in Dubai offer a competent, attentive, and professional service. Whether you need a vehicle for a few days or an entire week, choosing a car rental weekly is a convenient and profitable option. The certified and tested car rental companies listed on Smarketdrive.com ensure a reliable and comfortable experience.
Monthly Car Rentals in Dubai:
When your personal car is undergoing extended repairs, or if you’re a frequent visitor to Dubai, monthly car rentals (long-term car rentals) become the ideal solution. Residents, businessmen, and tourists can benefit from the extensive options available on Smarketdrive.com, ensuring mobility and convenience throughout their stay in Dubai.
FAQ about Renting a Car in Dubai:
To address common queries about renting a car in Dubai, our FAQ section provides valuable insights and information. From rental terms to insurance coverage, it serves as a comprehensive guide for those considering the convenience of car rentals in the bustling city.
Conclusion:
Dubai’s popularity as a global destination is matched by its diverse and convenient car rental services. Whether for business, tourism, or daily commuting, the options available cater to every need. With reliable platforms like Smarketdrive.com, navigating Dubai becomes a seamless and enjoyable experience, offering both locals and visitors the ultimate freedom of mobility.
Dubai, a city known for its opulence and modernity, demands a mode of transportation that reflects its grandeur. For those seeking a cost-effective and reliable long-term solution, Somonion Rent Car LLC emerges as the premier choice for monthly car rentals in Dubai. With a diverse fleet ranging from compact cars to premium vehicles, the company promises an unmatched blend of affordability, flexibility, and personalized service.
Favorable Rental Conditions:
Understanding the potential financial strain of long-term car rentals, Somonion Rent Car LLC aims to make your journey more economical. The company offers flexible rental terms coupled with exclusive discounts for loyal customers. This commitment to affordability extends beyond the rental cost, as additional services such as insurance, maintenance, and repair ensure your safety and peace of mind throughout the duration of your rental.
A Plethora of Options:
Somonion Rent Car LLC boasts an extensive selection of vehicles to cater to diverse preferences and budgets. Whether you’re in the market for a sleek sedan or a spacious crossover, the company has the perfect car to complement your needs. The transparency in pricing, coupled with the ease of booking through their online platform, makes Somonion Rent Car LLC a hassle-free solution for those embarking on a long-term adventure in Dubai.
Car Rental Services Tailored for You:
Somonion Rent Car LLC doesn’t just offer cars; it provides a comprehensive range of rental services tailored to suit various occasions. From daily and weekly rentals to airport transfers and business travel, the company ensures that your stay in Dubai is not only comfortable but also exudes prestige. The fleet includes popular models such as the Nissan Altima 2018, KIA Forte 2018, Hyundai Elantra 2018, and the Toyota Camry Sport Edition 2020, all available for monthly rentals at competitive rates.
Featured Deals and Specials:
Somonion Rent Car LLC constantly updates its offerings to provide customers with the best deals. Featured cars like the Hyundai Sonata 2018 and Hyundai Santa Fe 2018 add a touch of luxury to your rental experience, with daily rates starting as low as AED 100. The company’s commitment to affordable luxury is further emphasized by the online booking system, allowing customers to secure the best deals in real-time through their website or by contacting the experts via phone or WhatsApp.
Conclusion:
Whether you’re a tourist looking to explore Dubai at your pace or a business traveler in need of a reliable and prestigious mode of transportation, Somonion Rent Car LLC stands as the go-to choice for monthly car rentals in Dubai. Unlock the ultimate mobility experience with Somonion, where affordability meets excellence, ensuring your journey through Dubai is as seamless and luxurious as the city itself. Contact Somonion Rent Car LLC today and embark on a journey where every mile is a testament to comfort, style, and unmatched service.
смм-услуги https://smm-almaty.kz/
https://gamma.app/docs/150-1000–7s6yymhyfo63l2c?mode=doc
https://cytotec.directory/# cytotec abortion pill
https://www.vollo.ru/faq/elm/?promokod-1xbet_bonus.html
buy cytotec pills: cytotec pills online – buy cytotec online
http://www.kniga-pocheta.ru/cms/tiny_mce/image/?promokod-1xbet-bonus.html
Medication information sheet. What side effects?
zoloft
All trends of drug. Read now.
zithromax 500mg price zithromax over the counter canada zithromax online pharmacy canada
https://gamma.app/docs/1xBet-Promo-Code-2024-Get-Up-to-130-Sign-Up-Bonus-t17h67c0p0cnrwi?mode=doc
Medicament prescribing information. What side effects?
tadacip order
Everything information about medication. Read information here.
https://gamma.app/docs/Melbet-Promo-Code-Bangladesh-Bonus-up-to-100-441pn9jjt06otb5?mode=doc
http://nolvadex.pro/# tamoxifen dose
tamoxifen hip pain: tamoxifen and ovarian cancer – does tamoxifen cause menopause
Березин Андрей Евроинвест https://lenta.ru/tags/persons/berezin-andrey.
Cопровождение интернет-площадки является комплексной услугой, которая направлена на поддержание его компонентов для стабильной работы. Выполняемая профессионалами создание и поддержание сайта от https://teh-podderzhka-saita.ru продвигает площадку на более высокий уровень, что делает бизнес прибыльным и успешным. Проводимые процедуры позволяет компаниям предлагать своей ЦА только свежую информацию, коммуницировать с ней быстро, безопасно и результативно. Такой проект постоянно доступен и удобен для пользователей и поисковых систем, а это способствует увеличению продаж продукции или услуг и повышает рейтинг организации. Главное, чтобы все осуществляли профессионалы, так как работы, которые будут выполняться не профессионалами, негативно скажутся на его производительности и комфорте пользования, а также повысят риск возникновения вредоносных программ и взломов.
https://reputablepharmacies.online/# canadian meds
thecanadianpharmacy com: mail order pharmacy canada – canada drugs without prescription
http://reputablepharmacies.online/# canadian pharmacy antiobotics without prescription
online prescription for ed meds: prescription drugs online – prescription drugs without doctor approval
->>>>>>>>>>>>>приворот на церковных свечах<<<<<<<<<-
______________приворот на жену отзывы _____________
как заколдовать мужа к себе https://privorot4.wordpress.com
как заворожить, а также:
->>>>>>заговоры на приворот мужа
->>>>>>как сделать чтобы мужчина хотел только тебя заговор
->>>>>>как понять что мужчину приворожили и что делать
->>>>>>заклинание для любви
https://edwithoutdoctorprescription.store/# non prescription ed pills
https://pousadadocapitaofloripa.com.br/wp-content/pgs/codigo_promocional_bono_1win.html
https://checklist.ectrum.ru/
м¤лЌёлЎњ кІЊмћ„
online reversi game
Наши специалисты тщательно отбирают только качественные товары от ведущих мировых производителей, гарантируя ваше удовольствие и безопасностьhttp://xn--48-6kcd0fg.xn--p1ai/forums.php?m=posts&q=19818&n=last#bottom
sienna inplay ph
tadalafil without a doctor’s prescription: buy prescription drugs from canada – non prescription erection pills
Березин Андрей Евроинвест http://antennadaily.ru/2023/06/23/andrey-berezin-euroinvest.
->>>>>>>>>>>>>заговоры на луну на любовь мужчины читать<<<<<<<<<-
______________как вернуть мужа в семью на расстоянии _____________
приворожить мужа
приворот на парня быстрый читать https://privorot4.wordpress.com заговор на любовь мужчины по фотографии читать
привороты мужчины на расстоянии самостоятельно
самый действенный приворот на мужчину в домашних условиях читать, а также:
->>>>>>заклинание чтобы человек позвонил
http://reputablepharmacies.online/# mexican pharmacy online
Drug information. Brand names.
provigil online
All about pills. Get here.
Drug prescribing information. What side effects?
how can i get cipro
Actual news about drugs. Get information here.
Medicament information sheet. Drug Class.
cheap cytotec
All news about medicines. Get information now.
canadian drug prices: overseas pharmacy – canadian pharmacies online legitimate
По моему это очень интересная тема. Предлагаю Вам это обсудить здесь или в PM.
google Новости мира дзен работают на разнообразных телефонах и же при плохом качестве подключения. ассортимент самых свежих данных о вашем городе, стране и мире в общем обновляется на протяжении течение дня.
https://edpills.bid/# online ed medications
how can i get generic prednisone without insurance
симпатичный вопрос
для самой эффективного продвижения вашего предприятия наши специалисты посодействуют вам настроить массовую смс-активацию в автоматизированном режиме и уводить ваши дела купить виртуальный номер Латвии с наибольшей пользой.
Pills information sheet. Drug Class.
rx kamagra
Everything news about medicament. Get information now.
старые фото
однако дерматоглифику ещё в 2016 году специальная комиссия Пояс Венеры РАН признала лженаукой. Так, психолог Рэй Хайман рассказывает, и это в юности сам верил в хиромантию и практиковал чтение по ладони.
Pills information leaflet. Long-Term Effects.
provigil
Best trends of medicament. Get information here.
Как узнать свой промокод? Есть несколько способов узнать бонус clubnika: проверить наличие в своём кабинете, в SMS-сообщениях на почте или на мобильном телефоне, зайти в «Витрину», найти на информационном табло, уточнить у специалиста Казино. Казино клубника играть бесплатно: https://iplaystars1.ru/
клубника 777 казино зеркало Россия Если платформа заблокирована, стоит перейти на рабочее зеркало клуба и играть без ограничений. Блокировка может быть связана с тем, что в большинстве стран доступ к азартным заведениям запрещен. Такие ресурсы попадают в бан и гости не могут пользоваться своим профилем, играть в любимые игры, пополнять счет и выводить выигрыши. Чтобы избежать ограничения доступа к профилю, стоит воспользоваться рабочей репликой, которая находится на другой доменной ссылке, но работает синхронно с основным ресурсом. Каждый игрок на площадке может обратиться к операторам службы технической поддержки и найти актуальное Клубника 777 онлайн зеркало заведения. Посетители могут не беспокоиться о безопасности данных, поскольку заведение строго соблюдает принципы ответственной игры, политику конфиденциальности и пользовательское соглашение, поэтому данные клиентов, полученные через зеркало, не распространяются и не передаются третьим лицам. клубника 777 зеркало — 100% копия оригинального портала, которая сохраняет все опции,включая интерфейс и навигацию на сайте.
Zooma казино Zooma – надежное казино с топовыми провайдерами, слотами и режимами. Доступны бонусы за ввод промокодов, а также подписки на группы в социальных сетях, Проводятся турниры среди активных игроков с неплохими призовыми фондами, Предусмотрена система команд и сражений, по результату которых каждую неделю можно забирать денежные призы за первые места. Вывод осуществляется на электронные кошельки, мобильные операторы и банковские карты РФ и Украины. Казино имеет лицензию и официально зарегистрировано в Коста-Рике (номер лицензии 3-102-693823)НАЧАТЬ ИГРАТЬ>> Zooma Casino – официальный сайтНачать нужно с того, что Zooma казино имеет лицензию и официально зарегистрировано в Коста-Рике (номер лицензии 3-102-693823). Как и многие другие игровые сервисы, сайт постоянно меняет доменные имена, но актуальные зеркала легко найти на их официальных страничках в социальных сетях. Пополнение и выводМинимальный депозит 1 рубль, а выводят от 100 рублей. Выплаты активируются депозитом от 50 рублей. Все транзакции обрабатываются на автомате, поэтому пополнение и вывод производится мгновенно. Комиссия зависит от используемой платежной системы, выбор огромный. Проверено,Zooma casino деньги выводит, игр много, всё по-честному, уже много раз получал крупные выигрыши. НаZooma можно играть онлайн бесплатно, собирайте промокоды в социальных сетях, я сам с них поднимался. Были сомнения, выводит лиZooma bet деньги, сам в этом убедился, захожу на сайт часто, ни разу не сталкивался с проблемами. Казино Зума точно стоит рассмотреть, при поиске развлекательной платформы. Это качественный и проверенный сайт, откуда точно получится вывести выигрыш. Информация оказалась полезной?! Сделай репост в соцсетях!
prescription drugs without doctor approval: viagra without a doctor prescription – 100mg viagra without a doctor prescription
Это можно бесконечно обсуждать..
чтоб вы не искали на рынке – авторегистраторы, камеры с точки зрения видеосъемки и прочие полезные для существования приспособления, мы стремимся предложить своим клиентам оптимальный вещь, https://fotofrog.ru/ в широкой продаже по привлекательной стоимости с проверкой и транспортировкой по рф!
приворот на кровь сделала приворот телефон спб через какое время после отворота можно делать приворот
https://www.romanticcollection.ru
скачать хорошую музыку на телефон
Подтверждаю. И я с этим столкнулся.
Procedural Modeling – Procedural modeling is a method used in computer graphics and virtual images (cgi) to create realistic or stylized http://www.dainelee.net/cgi-bin/pldbbs/pldbbs.cgi?p=1&c=635&ar=732.
Какие хорошие слова
Сформировав в Корзине список, надо – ввести промокод в предусмотренное под него поле, https://ru24.net/moscow/267667313/ указать оптимальный вариант привоза и расчета.
http://edwithoutdoctorprescription.store/# generic viagra without a doctor prescription
ОГРАБЛЕНИЕ КАЗИНО Добро пожаловать в авантюрный мир! Предупреждаю, что пока еще не поздно отказаться, потому что предложение мое как выгодно, так и опасно, кто решил не ввязываться в это дело – без обид. А всех остальных прошу за мной… Игра продолжается! Особенности Ранее квест назывался «2 этап Ставки сделаны, ставок больше нет». Если администратор квеста не сможет дозвониться до вас для подтверждения (в день игры или за 1 день до), бронирование будет отменено. Фотографии игроков: организатор выкладывает в группу «ВКонтакте» в течение 1-2 дней. Видео прохождения квеста: услуга не предоставляется. Услугу оказывает ПАРТНЕР компании iLOCKED – ИП Юдинцева Кристина Андреевна (ИНН: 440702204435) ВАЖНО: Команды, где возраст игроков менее 12 лет, не допускаются для прохождения квеста. На игры после 22:00 требуется внести предоплату в размере 20 % от стоимости игры. Джоз: промокод при регистрации 2021 год – 3 000 рублей! |: https://myvulcan.ru/
Заболевание, требующее лечения Игромания – это настоящее современное заболевание. Избавиться от него не так просто как может показаться на первый взгляд. Как минимум 10% людей на планете страдает из-за этой проблемы. Успехом пользуются игровые автоматы, причём довольно часто они находятся в интернет-казино. Ведь очень удобно никуда не идти, а вращать барабан дома. Мол, увлечение абсолютно безобидное и никто о нём не узнает. Игроманией страдают люди, имеющие неустойчивое эмоциональное состояние. Им свойственна подверженность стрессам, а также замкнутость. Такой игрок может быть спровоцирован на срыв абсолютно любой мелочью. Он думает: «Как же так вышло, что теперь нельзя получать удовольствие от любимого занятия. Ведь рядом, только стоит руку протянуть, находятся уже почти ставшие родными игровые автоматы». Игрок становится злым, агрессивным, замкнутым. Кроме того, этот человек сам ищет повод для возможного срыва.
Фриспины Бонус-коды для казино часто дают бесплатные вращения. Это фиксированное количество фриспинов по одной ставке, которые можно использовать в перечне слотов, предоставленном оператором.
Пока в аккаунте есть фриспины, деньги с баланса не снимаются. Призовые, полученные с их помощью, идут на бонусный счет. Фриспины зачисляются сразу или постепенно после активации промокода. Во втором случае пользователь получает набор вращений ежедневно.
https://vk.com/oborudovanie_avtomoek_krasnodar?w=product-224049345_9114253%2Fquery
– приворот на ветер отзывы кто делал
– https://magiya.guru через какое время начнет действовать приворот
– сильнодействующий приворот любимого
– приворотные заговоры по фотографии
best over the counter ed pills: men’s ed pills – male ed drugs
аренда виртуального номера телефона
барьеры водоналивные пластиковые https://znaki99.ru/vodonalivnye-barery/
аренда телефонного номера
прикольно конечно НО смысл этого чуда
убедитесь что вы уверились, что имя ЦС совместимо с соглашениями об именовании и целями, центр сертификации официальный сайт поскольку вы не должны изменить имя ЦС после установки ad cs.
молитва от приворота любимого приворот черное венчание скачать торрент
какие последствия приворота – https://adella.ru приворот парня на фото
аренда мобильного номера
cialis without doctor prescription: how to get prescription drugs without doctor – non prescription erection pills
аренда телефонного номера
PokerOK
скачать ggpokerok
Даниэль Негреану Канадский игрок из Торонто, участник Team PokerStars Pro . Начал освоения покера в 15 лет. В 23 (1997) одержал первые крупные победы в национальных сериях. В 1998 выиграл первую награду WSOP , оказавшись самым молодым обладателем браслета. Дополнил коллекцию наград браслетами серии в 2003, 2004 и 2008. Имеет 4 браслета World Series и дважды побеждал в этой серии. В 2005 году Негреану основал собственный покер-рум. Через год было объявлено об уникальном соревновании, победитель которого станет учеником легендарного мастера. Самые самые игроки в покер принимали участие в столь значимом событии. Для подогрева интереса Даниель оплатил победителю четыре турнира со взносом в 10 000$. В 2007 покер-рум был закрыт после подписания контракта с проектом PokerStars . Общая сумма призовых более 11 000 000$ Казино Джус (Jozzz), онлайн игровые автоматы joz рабочее зеркало сайта
Джоз 777 отзывы Убедиться, что онлайн-заведение ведет честную и безопасную игру, а также подтвердить хорошую репутацию клуба можно прочитав в казино Джус 777 — отзывы людей. В таких комментария речь идет о работе клуба, о поддержке саппорта, также часто гости делятся впечатлениями от игрового процесса, обсуждают стратегии, бонусы, хвастаются щедрыми выигрышами и обсуждают плюсы и минусы обналички разными платежными методами. Получить реальные отзывы джаз 777 можно на тематических форумах, в социальных сетях и мессенджерах. Стоит доверять комментариям игроков, которые могут подтвердить свое членство в клубе и не нарушали правил ответственной игры.
Джоз казино Самостоятельным разделом в джозз является онлайн-казино. Пользователям ресурса предлагается запустить онлайн казино с любого устройства. Заведение пропагандирует принципы ответственной игры, строго придерживается пользовательского соглашения и политики конфиденциальности. Все данные, полученные заведением, собираются для улучшения качества предоставляемых услуг. Для решения любой затруднительной ситуации на сайте онлайн-казино доступна служба технической поддержки, с которой игроки могут связаться в любое время, используя номер мобильного телефона или адрес электронной почты. Дополнительно на ресурсе имеется онлайн-чат, позволяющий быстро решить любой организационный вопрос.
http://edwithoutdoctorprescription.store/# viagra without doctor prescription
https://edpills.bid/# ed pills
A round of applause for your article. Much thanks again.
My website: секс с насилием
new ed drugs: ed pills comparison – best otc ed pills
сработает ли приворот если добавить кровь в чай – https://магиявера.рф
Не могу сейчас поучаствовать в обсуждении – очень занят. Вернусь – обязательно выскажу своё мнение.
Благодаря интуитивному интерфейсу, всякий пользователь, будь он новичок или бывалый геймер, vrgames.ru умеет легко принять нужные вам виды кейсов кс:го.
скачать ggpokerok
ggpokerok официальный сайт
how can i get cheap prednisone
buying prescription drugs in mexico: Mexico pharmacy – purple pharmacy mexico price list mexicanpharmacy.win
Активный игрок Средний возраст 28 лет. Зачастую не женат, но в отношениях. В социальных сетях очень активен: много друзей, подписчиков/подписок, аудио- и видеозаписей, фотографий и приколов. Интересы очень широкие, поэтому слушает и рэп, и рок, читает мужские паблики, научпоп, новости, играет в покер. Вход бк Дэдди на официальном сайте в личный кабинет — войти в лк букмекерской конторы daddy https://lettore.ru/
Как получить бонусы в онлайн-казино Бонусы, выдаваемые администрацией казино при регистрации, выполняют функцию рекламы клуба, привлекающей новых клиентов. Бесплатный депозит подходит для новичков, пробующих себя в играх на деньги в первый раз. Но необходимо учитывать, что вывести заработанные деньги так просто не получится. Практически все онлайн-платформы требуют от пользователя полного отыгрыша. Бонусы или фриспины при регистрации на сайте получить легко – иногда необходимо просто зарегистрироваться в клубе по специальной ссылке-приглашению, а иногда указать промокод. Есть еще один способ получения вознаграждения – написать в службу поддержки с просьбой начислить бесплатный депозит или вращения.
Промокоды дэдди Розыгрыши на официальном сайте проходят ежедневно. За победу выдаются промокоды. При их активации на баланс начисляются дополнительные фриспины или бонусные деньги.
canadapharmacyonline legit Canadian pharmacy online canadian pharmacy meds review canadianpharmacy.pro
http://mrkarpiuk.xaa.pl/boards/shopping/member.php?action=profile&uid=27115
https://usolie-citi.ru/user/aleksweima/
Ухты, супер, давно ждал. СПС
не обращая внимания на собственный внушительный размер, http://suvenir.k-78.ru/communication/forum/user/47177/ собаки этой породы опасаются незнакомцев и могут быть агрессивными касательно сородичам.
Вас посетила просто блестящая мысль
так же есть огромное количество разнообразной порнушки: соло, жесткий секс, частное http://o926476g.bget.ru/users/obynif, студентки, секретарши, медсестры и многое другое. здесь есть популярные жанры: целки и берегущие целомудрие до свадьбы, русские красотки, фистинг ласки руками и пальцами, худощавые и гибкие девушки, горячие брюнетки, сучки, дающие каждому встречному, дамочки сосущие член крупным планом, интим с 2-мя членами в обоих дырках, дамы, которые любят передвигаться на своих кавалерах, сисястые и девушки с впечатляющими сиськами, японки, латинки, русские, украинки, казашки, белоруски, европейки, черные, желтые, китаянки и другие распутницы.
reputable indian pharmacies: Order medicine from India to USA – top 10 pharmacies in india indianpharmacy.shop
medicine in mexico pharmacies medication from mexico pharmacy mexican border pharmacies shipping to usa mexicanpharmacy.win
мне понравилось
Смотреть горячую порнографию в сети предоставлена возможность в любое час суток на высокой отличной скорости, плюс функция скачать понравившееся http://whdf.ru/forum/user/71710/ ролик на гаджет отличается отсутствием посторонних роликов и авторизации, что помимо того больше не сможет ограничить действия зрителей в порыве страстного просмотра.
Нда!
так что эксплуатации у тебя всё равно предстоит большая часть. и наоборот – когда более трех раз раз вам уже отдавали «сырую» работу, https://shop.restaurantlacucanya.com/polo-image/ то диплом однозначно будет так себе.
http://canadianpharmacy.pro/# cross border pharmacy canada canadianpharmacy.pro
canada pharmacy estrogen without prescription
Какие источники признаны официальными. На каких сайтах можно узнать результаты игр В п.22 правил находится полный список подобных ресурсов. Не будем перечислять их все. Остановимся на ключевых. Обзор онлайн casino daddy с хорошей отдачей: https://pro100status.ru/
Ставки на виртуальный спорт В разделе LIVE игрокам Daddy предлагает наблюдать и заключать пари на виртуальные игры, которые симулируются в автоматическом режиме на сервере. Выбор очень большой: FIFA, регби, ралли, волейбол, бейсбол, гольф, американский футбол, StreetFighter, CallofDuty. Всё это – не соревнования киберспортсменов-людей, а противостояния ботов.
Кешбэк Постоянные игроки могут получить обратно часть денег, которые потрачены на ставки в течение месяца. По умолчанию ставка кешбэк-бонуса — 10%. Возврат рассчитывается из суммы проигранных в течение одного календарного месяца средств. Начисление происходит первого числа. Без депозита забрать кешбэк не получится. Необходимо внести на баланс сумму, равную половине начисленного возврата. После этого кешбэк-бонус активируется. Чтобы внести нужный депозит и забрать возвращаемые деньги, у клиента есть 72 часа. Узнать сумму начисленного кешбэк-бонуса можно в разделе «Баланс». Отдельно приводится информация по возврату в онлайн-казино и ставках на результаты спортивных событий.
Думаю, имеется ввиду и то, и то
Ведь среди активных пользователей является не только лишь парни, но и девушки. ты получаешь возможность лайкать или дизлайкать, http://forum.meendocash.com/index.php?topic=4158.new#new формируя ленту популярности.
Березин Андрей Евроинвест http://newizv.ru/news/2023-08-28/berezin-andrey-svedeniya-o-developere-419032/.
Браво, мне кажется это великолепная мысль
Некоторые спешат https://drmhelmets.com/news/update-september-2018-2/, другие желают поступить в институт. Потом начинаются поборы в виде взяток, повышения годовой платы за обучение и прочее.
ATG戰神賽特
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
Вывод 1иксБет игры – специальный раздел Казино, в котором собраны эмуляторы классических азартных развлечений и лотерей, а также представлено несколько слотов. Играть в нем могут только зарегистрированные пользователи с положительным балансом. В общей сложности клиентам букмекера предлагается 126 игр (на лето 2022). Daddy Casino, лучшее казино для новичков! daddy зеркало сегодня
Беру в аренду аккаунты Казино Daddy и его клонов под ваш любой депозит от 1000 руб Условия! Ваш Аккаунт должен быть Активным! Не был в Аренде! Активный Прием ставки до 6 секунд Желательно большой минус Связь со мной Tg @aShul9 Shul9 Тема 20 Дек 2020 1x daddy daddy.com 1xstavka 1xstavka.ru 1xбет 1xбэт 1xставка 1иксбет 1иксбэт Дэдди 1хбэт 1хставка daddy Daddy Казино daddy.com Daddy.ru аренда аккаунтов Казино аренда аккаунтов Казино аренда Казино аренда счетов Казино аренда счетов Казино арендую КазиноКазино Daddy Казино daddy Казино daddy клоныКазино Дэдди мелбэт мэлбет мэлбэт покупка аккаунтов Казино покупка аккаунтов Казино покупка счетов Казино покупка счетов Казино продажа аккаунтов Казино продажа счетов Казино Ответы: 16 Форум: АККАУНТЫ Казино
Как вывести деньги с Дэдди Чтобы daddy вывод средств не задерживал, лучше сразу пройти полную регистрацию и верификацию. Вы можете воспользоваться одним из 36 предлагаемых способов, среди которых самые популярные электронные кошельки, платежные системы, банковские карты и прочее.
2024娛樂城No.1 – 富遊娛樂城介紹
2024 年 1 月 5 日
|
娛樂城, 現金版娛樂城
富遊娛樂城是無論老手、新手,都非常推薦的線上博奕,在2024娛樂城當中扮演著多年來最來勢洶洶的一匹黑馬,『人性化且精緻的介面,遊戲種類眾多,超級多的娛樂城優惠,擁有眾多與會員交流遊戲的群組』是一大特色。
富遊娛樂城擁有歐洲馬爾他(MGA)和菲律賓政府競猜委員會(PAGCOR)頒發的合法執照。
註冊於英屬維爾京群島,受國際行業協會認可的合法公司。
我們的中心思想就是能夠帶領玩家遠詐騙黑網,讓大家安心放心的暢玩線上博弈,娛樂城也受各大部落客、IG網紅、PTT論壇,推薦討論,富遊娛樂城沒有之一,絕對是線上賭場玩家的第一首選!
富遊娛樂城介面 / 2024娛樂城NO.1
富遊娛樂城簡介
品牌名稱 : 富遊RG
創立時間 : 2019年
存款速度 : 平均15秒
提款速度 : 平均5分
單筆提款金額 : 最低1000-100萬
遊戲對象 : 18歲以上男女老少皆可
合作廠商 : 22家遊戲平台商
支付平台 : 各大銀行、各大便利超商
支援配備 : 手機網頁、電腦網頁、IOS、安卓(Android)
富遊娛樂城遊戲品牌
真人百家 — 歐博真人、DG真人、亞博真人、SA真人、OG真人
體育投注 — SUPER體育、鑫寶體育、亞博體育
電競遊戲 — 泛亞電競
彩票遊戲 — 富遊彩票、WIN 539
電子遊戲 —ZG電子、BNG電子、BWIN電子、RSG電子、好路GR電子
棋牌遊戲 —ZG棋牌、亞博棋牌、好路棋牌、博亞棋牌
捕魚遊戲 —ZG捕魚、RSG捕魚、好路GR捕魚、亞博捕魚
富遊娛樂城優惠活動
每日任務簽到金666
富遊VIP全面啟動
復酬金活動10%優惠
日日返水
新會員好禮五選一
首存禮1000送1000
免費體驗金$168
富遊娛樂城APP
步驟1 : 開啟網頁版【富遊娛樂城官網】
步驟2 : 點選上方(下載app),會跳出下載與複製連結選項,點選後跳轉。
步驟3 : 跳轉後點選(安裝),並點選(允許)操作下載描述檔,跳出下載描述檔後點選關閉。
步驟4 : 到手機設置>一般>裝置管理>設定描述檔(富遊)安裝,即可完成安裝。
富遊娛樂城常見問題FAQ
富遊娛樂城詐騙?
黑網詐騙可細分兩種,小出大不出及純詐騙黑網,我們可從品牌知名度經營和網站架設畫面分辨來簡單分辨。
富遊娛樂城會出金嗎?
如上面提到,富遊是在做一個品牌,為的是能夠保證出金,和帶領玩家遠離黑網,而且還有DUKER娛樂城出金認證,所以各位能夠放心富遊娛樂城為正出金娛樂城。
富遊娛樂城出金延遲怎麼辦?
基本上只要是公司系統問提造成富遊娛樂城會員無法在30分鐘成功提款,富遊娛樂城會即刻派送補償金,表達誠摯的歉意。
富遊娛樂城結論
富遊娛樂城安心玩,評價4.5顆星。如果還想看其他娛樂城推薦的,可以來娛樂城推薦尋找喔。
where can i buy abilify without rx
Меня тоже волнует этот вопрос. Вы мне не подскажете, где я могу найти больше информации по этому вопросу?
Алгоритм работы прост: вам надо получить заказ, затем получить образец на личный электронный адрес, удостоверить его, или заплатить коррективы, https://aacsatlanta.com/why-to-take-virtual-sap-evaluation-from-aacs/ и после получить ожидаемый оригинальный справку в течение 2-7 суток.
canada pharmacy world Canadian pharmacy online onlinecanadianpharmacy canadianpharmacy.pro
buying prescription drugs in mexico: Mexico pharmacy – mexico pharmacies prescription drugs mexicanpharmacy.win
ATG戰神賽特
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
what isamoxicillin used for
Pills information. Cautions.
levitra
Actual about medication. Get information here.
En la búsqueda de entretenimiento y grandes premios, es fundamental visitar los Mejores Casinos En Línea Chile, donde la calidad y la fiabilidad son primordiales.
http://indianpharmacy.shop/# buy medicines online in india indianpharmacy.shop
sides effects of zoloft
я уже это всё где-то видел
https://wondershop-store.com/index.php/product/camiseta-snoopy-cuello-redondo/ with simple but complex rules is excellent way to hone your mathematical skills while having at the same time/ at the same time fun.
Medicine information sheet. Cautions.
trazodone
Best about drugs. Get now.
Medicine prescribing information. What side effects?
rx minocycline
Best news about medication. Read now.
cost cheap super p-force pill
can i order generic valtrex tablets
buying from online mexican pharmacy online mexican pharmacy mexico pharmacies prescription drugs mexicanpharmacy.win
does amoxicillin make you tired
Браво, очень хорошая мысль
Send us ideas of fun snacks and drinks that anyone from them invited can enjoy in a http://hoydecidisvos.sanluis.gov.ar/index.php/2022/07/19/how-much-does-a-top-resume-cost/ all together.
mexico drug stores pharmacies: buying prescription drugs in mexico online – buying from online mexican pharmacy mexicanpharmacy.win
Medicament prescribing information. Cautions.
generic finpecia
Some information about medicines. Get information now.
Официальный сайт игры Aviator Причин популярности азартного развлечения про красный самолет достаточно много. Подтверждением данного факта являет то, что, она добавлена на сайты разных Казино и онлайн казино. Несмотря на это, игрокам не нужно заново разбираться с тем, как она работает и каким образом это происходит. Собственного сайта или приложения у Авиатора не существует, поэтому придется зарегистрироваться на сайте той компании, которая больше всего нравится пользователю. Стоит отметить, что таких сайтов достаточно много, а в статье будут отмечены только самые популярные компании. Казино дэдди – https://zhiraf-tula.ru/
Процесс регистрации Регистрация в daddy Casino необходима для получения возможности играть на деньги. Создать профиль на площадке может каждый посетитель, достигший совершеннолетнего возраста. Чтобы пройти регистрацию в daddy Casino, необходимо сделать следующее: Указать в регистрационной форме свой актуальный e-mail. Придумать и вписать в указанные поля логин и пароль. Внести личные данные (имя, возраст, страну проживания). Выбрать валюту игрового счета. Опция быстрой регистрации через соцсети не предусмотрена, однако и классический вариант создания аккаунта занимает не более двух-трех минут. Профили игроков надежно защищены от стороннего вмешательства. В целях безопасности нужно лишь хранить в тайне свой пароль и логин. При создании профиля на сайте можно указать промокод для получения дополнительного подарка. Актуальные бонус-коды публикуются на информационных ресурсах, сотрудничающих с онлайн-казино. У промо кодов ограниченный срок действия. Если промокод просрочен, активировать бонус с его помощью не получится.
Особенности ставок на бокс В отличие от других видов спорта, в боксе очень высокий процент поединков, где есть явный фаворит и заведомый аутсайдер. Но практически всегда коэффициенты не отражают реального соотношения сил, поскольку на фаворита поставлены миллионы, что и приводит к изменениям котировок. Таким образом, на дистанции выгоднее ставить на аутсайдеров по завышенным коэффициентам, а если заключать пари на фаворита, то лучше делать это по ранней линии. Зарабатывать с помощью ставок на бокс в Казиноах вполне реально, однако необходимо хорошо разбираться в этом виде спорта, грамотно анализировать предстоящие бои, придерживаться эффективной стратегии и понимать особенности беттинга в боксе. Когда класс соперников сопоставим, тогда в бою всё решают детали. И для того чтоб сделать выигрышную ставку, необходимо изучить каждую мелочь. Начните с анализа текущей формы, рейтингов и детального разбора последних боев. Учитывайте место проведения поединка, недавние травмы, стиль боксеров, мотивацию, возраст, оцените подготовку к бою. В большинстве случаев побеждает грамотный боксер, который умеет правильно подобрать тактику и распределить силы на дистанции. Такой спортсмен подстраивается под оппонента и значительно увеличивает шансы на победу.
finasteride 5
пользователи могут маршрутизировать вызовы на такие номеров одновременно.neoобычно либо в http://www.hooveryetkiliservis.com/camasir-makinesi-ile-yikama/ определенном порядке. круче того, интекс предлагает множество расширений с уведомлениями о пропущенных звонках и полученных факсах.
http://indianpharmacy.shop/# world pharmacy india indianpharmacy.shop
Meds information for patients. Effects of Drug Abuse.
stromectol
Actual what you want to know about medication. Get information here.
get generic lisinopril without rx
расклады на наличие приворота приворот на удачу читать в домашних условиях
приворот на бывшего парня читать – https://adella.ru приворот на сердце
Drugs information sheet. What side effects?
generic viagra soft
All news about medicine. Get here.
Безопасно ли использовать зеркало официального сайта pinup? Делать спортивные ставки используя зеркало также безопасно как и на оригинальном ресурсе. Букмекер придерживается строгой политики конфиденциальности при оказании услуг на официальном сайте и его копиях. Для сохранности персональных данных клиентов и безопасности финансовых операций на зеркалах используются современные алгоритмы шифрования. Пин Ап игровые автоматы онлайн бесплатно на сайте pinup PinUp – онлайн Pin Up зеркало
пин ап Украина – описание лучшего букмекера Ни один спортивный болельщик не упустит возможности сделать ставку на исход игры любимой команды. Раньше для этого нужно было идти в пункт приема ставок, где сотрудник компании сделает все за клиента. Теперь достаточно перейти на пинап официальный сайт – несколько нехитрых манипуляций позволят поставить на результат игры и получить выигрыш без посредников. Каждый игрок может обратиться к pin up Казино, которая вот уже 5 лет предлагает клиентам массу преимуществ. Но они доступны только для зарегистрированных пользователей. Жители Украины, владеющие русским либо английским языком, могут с легкостью зарегистрироваться и наслаждаться привилегиями pin up Казино. Интерфейс сайта достаточно прост. На первой странице находится линия событий, здесь также можно увидеть собственный купон (доступный после регистрации). Игроки могут узнать о текущих и прошедших играх, просмотреть матч-трекер. Высокие оценки сайта в рейтингах и PinUp отзывы позволяют судить о его популярности среди беттеров. Не стоит забывать о службе поддержки – онлайн поддержка доступна для игроков в любое время суток.
Выводы В пин ап для клиентов из разных стран много методов для внесения средств на депозит. Процедура пополнения счета максимально упрощенная, занимает несколько минут. Внимательно проверяйте реквизиты карты и номера кошельков при переводе, чтобы избежать ошибок платежа. Большинство транзакций выполняются мгновенно. Беттер сразу может делать ставки на спорт или в игровых автоматах. Карты, которые использовались для пополнения депозита, становятся доступными для вывода выигрышей.
One of the bestmobile car wash service Miami
– сильный приворот на любовь мужнюю
– https://koldovstvo.net рецепты привороты заговоры заклинания
– способы лечения приворота
– сильный приворот на записку и имя
Демонтаж и снос частных домов с вывозом мусора в Москве и Московской области. Снос дома вручную и спецтехникой производим по ценам ниже рынка за 1 день. Бесплатный выезд специалиста на объект.
order co-amoxiclav online
https://indianpharmacy.shop/# pharmacy website india
india pharmacy
https://indianpharmacy.shop/# india pharmacy
world pharmacy india
can you buy generic pregabalin without insurance
приворот по фото парня – https://magic.jofo.me приворот на девушку без последствия
trazodone dosage
Обзор бонусов и акций pinup в Казахстане Компания не скупится на специальные предложения, акции и бонусы, помогая клиентам получать больше с каждого вложенного цента. Из актуальных бонусных предложений нужно упомянуть: 100% бонусное начисление на первый депозит до 130 евро. Таким образом, пополняя счет всего на 100 евро, вы можете делать ставки на все 230. Бонус фрибет на первый депозит в 10 евро (акционные деньги добавляются к вашей ставке, и, таким образом, сайт пинап 2020 увеличивает ваш потенциальный выигрыш). Возможность сделать 101-ю ставку бесплатно. Огромные бонусные начисления на пополнение счета для игры в онлайн-казино на пин ап (от 50% до 200% на первые пять депозитов). pinup casino (пин ап) ? Зеркало для входа на официальный сайт – https://mgptomsk.ru/
Жалобы на букмекера 1xStavka Казино появилась в 2010 году, поэтому в интернете можно найти большое количество отзывов от клиентов. В целом, компания имеет положительную репутацию, однако встречаются и отрицательные отзывы. Из положительных сторон пользователи указывают на быстрые выводы, качественную работу технической поддержки, простой и понятный сайта, хорошие коэффициенты. Из недостатков отмечаются недоработанные правила, неудобное мобильное приложение, встречаются взломы аккаунтов. Компания следит за своей репутацией и помогает пользователям решить возникшие неприятные ситуации и различные проблемы, а значит букмекер следит за своей репутацией. В отличие от «1xБет» отзывы игроков о компании «1хСтавка» намного снисходительнее. Чаще жалобы поступают на блокировку счетов, урезание лимита отдельным игрокам до минимума и проблемы, которые характерны для оффшорной версии проекта – с выплатами, неотзывчивым персоналом. Если появятся жалобы на компанию 1хСтавка, то мы обязательно опубликуем информацию в социальных сетях. Подпишитесь, чтобы ничего не пропустить!
Пин Ап Платинум официальный сайт Пин Ап Платинум игровые автоматы разных категорий и жанров позволяют найти свое развлечение гемблерам с самыми разными интересами и предпочтениями.
from now on, if you are able to understand what is an http://www.wikalenda.com/redirect?url=https://smm-factory.com/tiktok/, let’s look at the advantages of building your strategy.
mahjong connect online
https://myskyblock.pl/
Studios and apartments located across two towers on the coastline of Al Jaddaf , with panoramic views on Dubai Creek, favourable terms of purchase and return of investment
Ваша мысль очень хороша
Some evenings or seasons may be busier than other, https://johnnynqoe05149.fireblogz.com/55827127/enter-the-ballerinas-the-best-gift-for-a-best-friend club influences on profit. Make sure that your nails are looked after and suffered in good condition.
Обзор лучших строительных компаний в Крыму и Севастополе, посмотрите строительство домов в Севастополе
reputable canadian pharmacy Canada Pharmacy buy prescription drugs from canada cheap canadianpharmacy.pro
Пасхальный Блэкджек в Pin Up: как принять участие в акции Играть, получать удовольствие, выигрыши и 5 000 евро в качестве дополнительного приза – это ли не мечта каждого любителя азартных развлечений? Пасхальный Блэкджек превратит желаемое в действительное. Для участия в акции игроку достаточно быть клиентом компании (в это понятие входит пройденная Пин Ап регистрация и заполнение игрового профиля с активацией контактов), дать согласие на участие в акциях площадки и подать заявку на участие в турнире кликом на кнопку «Участвовать».
В основе турнира лежит игра в различные виды Блэкджека и зарабатывание баллов. В акции принимают участие следующие развлечения: В каждой из перечисленных выше игр будут появляться пасхальные карты с разными изображениями, каждая из которых будет приносить очки: Карты появляются на акционных столах турнира Пасхальный Блэкджек случайным образом, что дает всем пользователям равные шансы на выигрыш. Кроме того, в счастливые часы (с 18:00 до 20:00) в колоду будут добавлены 3 бонусные карты, каждая из которых сможет принести дополнительные баллы.
Стоит добавить, что полученные призовые будут поступать не на pinup бонусный счет, а на основной баланс. Это значит, что выигранные денежные средства могут быть потрачены игроком сразу после начисления без какого-либо предварительного отыгрыша. Сроки действия акции: с 18 апреля по 1 мая 2022 года. pinup-bet – фальшивое казино от мошенников – честный отзыв и обзор pin up официальный
пинап промокод при регистрации Bonusbk111 Скопировать код Прежде всего необходимо разобраться в том, что такое промокод вообще. С точки зрения букмекера — это маркетинговый инструмент для привлечения новых игроков. Если взглянуть на на него глазами беттера, то открывается прекрасная возможность получить увеличенный приветственный бонус за регистрацию на сайте. Выглядит данный код как буквенно-цифровая комбинация, сгенерированная случайным образом: Bonusbk111. В других Казиноах возможно применение целых слов. Например: bonuskod2020 или promokodbk и так далее. Все зависит от фантазии разработчиков конкретного оператора ставок.Но вернемся к нашему промокоду Казино пин ап при регистрации. Из самого названия следует его назначение. Он необходим для получения приветственного поощрения букмекера и используется строго при создании игрового счета на сайте компании. Данный промокод не подойдет вам для ставки или участия в акции ТОТО пин ап.
??Методы выплаты денег в казино RBRANDDD24 Выплату денег в Pin Up 24 можно производить через разные платежные системы: карты Виза и МастерКард, Киви-кошелек, сервис LiqPay, Веб-Мани, Яндекс.Деньги. Для вывода средств в Пин Ап 24 необходимо зайти в личный кабинет, найти раздел «Касса», и выбрать доступный платежный инструмент, который подходит игроку. Минимум взноса на игровой баланс Минимальный лимит на вывод Максимум суммы для снятия с депозита 1000USD за день Методы ввода/вывода средств Visa, Master Card, Yandex.Деньги, Webmoney, Qiwi, Alfa-click, Приват24, Sberbank-онлайн, Liq Pay, Inter-Kassa, услуги мобильных операторов 1-3 суток на электронные счета и кошельки, 2-4 суток на карточки
Посетитель ПинАп 24 вывод выигрышей может проводить через: банковские счета, электронные кошельки, пластиковые карты. Быстрее всего деньги приходят на электронные кошельки. Чтобы в казино RBRANDDD24 с быстрым выводом выигрыша не было задержек, нужно придерживаться правил формирования заявки на выплату: Возраст и личность подтверждается документами игрока, казино делает запрос на верификацию. Нужно обязательно внести хотя бы один взнос на депозит, даже если пользователю был дан бездепозитный бонус. Убедиться, что на счету достаточно денег. Отыграть бесплатные фриспины и бонусы на автоматах pinup 24, соблюдая условия вейджера. ВИП клиенты имеют больше возможностей для вывода крупных выигрышей, чем обычные пользователи.
В этом что-то есть. Раньше я думал иначе, благодарю за информацию.
3. Aktivieren Sie die Sperre whatsapp status anonym ansehen. zusatzlich/Bonus, um die gesamte Anwendung zu sperren, vielleicht/haben die Moglichkeit, einzelne WhatsApp-Chats mit einem Passwort zu schutzen.
ритуал по привороту видео привороты на воде поветру слова для белого приворота
https://heaclub.ru
привороты сделанные через церковь
снять приворот с помощью свечи
приворот чтоб жена желала мужа
гибдд оплата штрафов https://proverka-gibdd-shtrafov.ru/
http://mexicanpharmacy.win/# mexico pharmacies prescription drugs mexicanpharmacy.win
pharmacy website india
Nikolaev Vyacheslav https://spacecoastdaily.com/2023/08/vyacheslav-nikolaev-ecosystem-builder.
http://gynecologist63.store/user/novaabon/
https://mexicanpharmacy.win/# mexican border pharmacies shipping to usa mexicanpharmacy.win
– приворот на месячной крови самостоятельно
– https://приворот-гуру.рф привороты на всегда легкие
– церковные свечи черная магия приворот
– приворот с помощью красного яблока
– сильный любовный приворот на месячныесделать любовный приворот белой магиисроки приворота на кладбище
Ведь что плохого в том, http://shooting-russia.ru/forum/?PAGE_NAME=message&FID=3&TID=13475&TITLE_SEO=13475-mskvipladie&MID=13738&result=new#message13738 что девушка за определенную денежную сумму сопровождает мужчину на светских мероприятиях и путешествует с курильщиком по всему свету?
https://deevki.ru/user/novaamah/
https://indianpharmacy.shop/# pharmacy website india indianpharmacy.shop
п»їlegitimate online pharmacies india
娛樂城
2024娛樂城No.1 – 富遊娛樂城介紹
2024 年 1 月 5 日
|
娛樂城, 現金版娛樂城
富遊娛樂城是無論老手、新手,都非常推薦的線上博奕,在2024娛樂城當中扮演著多年來最來勢洶洶的一匹黑馬,『人性化且精緻的介面,遊戲種類眾多,超級多的娛樂城優惠,擁有眾多與會員交流遊戲的群組』是一大特色。
富遊娛樂城擁有歐洲馬爾他(MGA)和菲律賓政府競猜委員會(PAGCOR)頒發的合法執照。
註冊於英屬維爾京群島,受國際行業協會認可的合法公司。
我們的中心思想就是能夠帶領玩家遠詐騙黑網,讓大家安心放心的暢玩線上博弈,娛樂城也受各大部落客、IG網紅、PTT論壇,推薦討論,富遊娛樂城沒有之一,絕對是線上賭場玩家的第一首選!
富遊娛樂城介面 / 2024娛樂城NO.1
富遊娛樂城簡介
品牌名稱 : 富遊RG
創立時間 : 2019年
存款速度 : 平均15秒
提款速度 : 平均5分
單筆提款金額 : 最低1000-100萬
遊戲對象 : 18歲以上男女老少皆可
合作廠商 : 22家遊戲平台商
支付平台 : 各大銀行、各大便利超商
支援配備 : 手機網頁、電腦網頁、IOS、安卓(Android)
富遊娛樂城遊戲品牌
真人百家 — 歐博真人、DG真人、亞博真人、SA真人、OG真人
體育投注 — SUPER體育、鑫寶體育、亞博體育
電競遊戲 — 泛亞電競
彩票遊戲 — 富遊彩票、WIN 539
電子遊戲 —ZG電子、BNG電子、BWIN電子、RSG電子、好路GR電子
棋牌遊戲 —ZG棋牌、亞博棋牌、好路棋牌、博亞棋牌
捕魚遊戲 —ZG捕魚、RSG捕魚、好路GR捕魚、亞博捕魚
富遊娛樂城優惠活動
每日任務簽到金666
富遊VIP全面啟動
復酬金活動10%優惠
日日返水
新會員好禮五選一
首存禮1000送1000
免費體驗金$168
富遊娛樂城APP
步驟1 : 開啟網頁版【富遊娛樂城官網】
步驟2 : 點選上方(下載app),會跳出下載與複製連結選項,點選後跳轉。
步驟3 : 跳轉後點選(安裝),並點選(允許)操作下載描述檔,跳出下載描述檔後點選關閉。
步驟4 : 到手機設置>一般>裝置管理>設定描述檔(富遊)安裝,即可完成安裝。
富遊娛樂城常見問題FAQ
富遊娛樂城詐騙?
黑網詐騙可細分兩種,小出大不出及純詐騙黑網,我們可從品牌知名度經營和網站架設畫面分辨來簡單分辨。
富遊娛樂城會出金嗎?
如上面提到,富遊是在做一個品牌,為的是能夠保證出金,和帶領玩家遠離黑網,而且還有DUKER娛樂城出金認證,所以各位能夠放心富遊娛樂城為正出金娛樂城。
富遊娛樂城出金延遲怎麼辦?
基本上只要是公司系統問提造成富遊娛樂城會員無法在30分鐘成功提款,富遊娛樂城會即刻派送補償金,表達誠摯的歉意。
富遊娛樂城結論
富遊娛樂城安心玩,評價4.5顆星。如果還想看其他娛樂城推薦的,可以來娛樂城推薦尋找喔。
Re: Казино Собрание (Калининградская область) Виталий Сафронов » 29 май 2017, 14:16 ДОБРЫЙ писал(а): если помнишь а какого типа столы и стулья, цвета сукна и ковралина ? Фишки в у.е? Фишки в у.е., да.Цвет сукна вроде красный с белым или бежевым обрамлением. Однако я близко не подходил и как-то не заострял внимание. С уважением, Казино Пин Ап зеркало: действенный способ обхода блокировки: https://pro-21.ru/
Обратная связь Связаться со Службой поддержки Казино fonbet casino можно через меню Чат, электронную почту или телефон.
Бонусы и акции казино Бездепозитный 90 UAH за подтверждение персональных данных 90 UAH макс. сумма 70 вейджер Приветственный 10% на первый депозит 147 UAH мин. депозит Депозитный 10% или 15% на каждый депозит 3 300 UAH макс. сумма 147 UAH мин. депозит Тем, кто рискнет играть на официальном сайте Триумф Казино на деньги, обещаны бездепы, приветственный пакет и другие промо. Кое-где вейджер лояльный, но иногда может достигать 70%. Сам же размер бонусов варьируется от 10% до 15%.
Medication information sheet. Effects of Drug Abuse.
levaquin generic
Some news about pills. Read information now.
Ежемесячная зарплата красоток, которые работают в данном агентстве, составляет от 20000 долларов и выше http://sugarhollowfarms.com/testimonial/john-smith/#comment-45289
cost of cheap mobic pills
https://mexicanpharmacy.win/# buying prescription drugs in mexico mexicanpharmacy.win
2024娛樂城
2024娛樂城No.1 – 富遊娛樂城介紹
2024 年 1 月 5 日
|
娛樂城, 現金版娛樂城
富遊娛樂城是無論老手、新手,都非常推薦的線上博奕,在2024娛樂城當中扮演著多年來最來勢洶洶的一匹黑馬,『人性化且精緻的介面,遊戲種類眾多,超級多的娛樂城優惠,擁有眾多與會員交流遊戲的群組』是一大特色。
富遊娛樂城擁有歐洲馬爾他(MGA)和菲律賓政府競猜委員會(PAGCOR)頒發的合法執照。
註冊於英屬維爾京群島,受國際行業協會認可的合法公司。
我們的中心思想就是能夠帶領玩家遠詐騙黑網,讓大家安心放心的暢玩線上博弈,娛樂城也受各大部落客、IG網紅、PTT論壇,推薦討論,富遊娛樂城沒有之一,絕對是線上賭場玩家的第一首選!
富遊娛樂城介面 / 2024娛樂城NO.1
富遊娛樂城簡介
品牌名稱 : 富遊RG
創立時間 : 2019年
存款速度 : 平均15秒
提款速度 : 平均5分
單筆提款金額 : 最低1000-100萬
遊戲對象 : 18歲以上男女老少皆可
合作廠商 : 22家遊戲平台商
支付平台 : 各大銀行、各大便利超商
支援配備 : 手機網頁、電腦網頁、IOS、安卓(Android)
富遊娛樂城遊戲品牌
真人百家 — 歐博真人、DG真人、亞博真人、SA真人、OG真人
體育投注 — SUPER體育、鑫寶體育、亞博體育
電競遊戲 — 泛亞電競
彩票遊戲 — 富遊彩票、WIN 539
電子遊戲 —ZG電子、BNG電子、BWIN電子、RSG電子、好路GR電子
棋牌遊戲 —ZG棋牌、亞博棋牌、好路棋牌、博亞棋牌
捕魚遊戲 —ZG捕魚、RSG捕魚、好路GR捕魚、亞博捕魚
富遊娛樂城優惠活動
每日任務簽到金666
富遊VIP全面啟動
復酬金活動10%優惠
日日返水
新會員好禮五選一
首存禮1000送1000
免費體驗金$168
富遊娛樂城APP
步驟1 : 開啟網頁版【富遊娛樂城官網】
步驟2 : 點選上方(下載app),會跳出下載與複製連結選項,點選後跳轉。
步驟3 : 跳轉後點選(安裝),並點選(允許)操作下載描述檔,跳出下載描述檔後點選關閉。
步驟4 : 到手機設置>一般>裝置管理>設定描述檔(富遊)安裝,即可完成安裝。
富遊娛樂城常見問題FAQ
富遊娛樂城詐騙?
黑網詐騙可細分兩種,小出大不出及純詐騙黑網,我們可從品牌知名度經營和網站架設畫面分辨來簡單分辨。
富遊娛樂城會出金嗎?
如上面提到,富遊是在做一個品牌,為的是能夠保證出金,和帶領玩家遠離黑網,而且還有DUKER娛樂城出金認證,所以各位能夠放心富遊娛樂城為正出金娛樂城。
富遊娛樂城出金延遲怎麼辦?
基本上只要是公司系統問提造成富遊娛樂城會員無法在30分鐘成功提款,富遊娛樂城會即刻派送補償金,表達誠摯的歉意。
富遊娛樂城結論
富遊娛樂城安心玩,評價4.5顆星。如果還想看其他娛樂城推薦的,可以來娛樂城推薦尋找喔。
can you buy generic co-amoxiclav pill
Medicament information leaflet. What side effects can this medication cause?
how can i get synthroid
Some information about medicine. Get information here.
http://mexicanpharmacy.win/# buying prescription drugs in mexico online mexicanpharmacy.win
киснет суп-может порча – https://artgrom.com бабушки.порча, привороты и т.д в городе новокузнецке.
порча не дает счастью
порча на черные нитки
как узнать есть ли на мне порча яйцом
порча сглаз признаки иголка в двери
http://indianpharmacy.shop/# indian pharmacies safe indianpharmacy.shop
foreign online pharmacy
? Интим, – объясняли мне, http://rogerfilms.com/index.php?title=pro100sexco – это, когда массажистка вступает с заказчиком в половую связь.
приворот на любовь жены по фото читать в домашних условиях = https://magicwishes.ru реальные привороты навсегда
приворот самостоятельно жены сделала приворот мужчина вообще перестал писать
戰神賽特老虎機
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
http://indianpharmacy.shop/# buy prescription drugs from india indianpharmacy.shop
top 10 online pharmacy in india
pharmacy com canada ed meds online canada reliable canadian pharmacy canadianpharmacy.pro
https://avtomanipulyator.com/stati/manipulyator-vyshka/
Конечно Вы правы. В этом что-то есть и мне нравится эта мысль, я полностью с Вами согласен.
I would not call this match the smoothest, because some important moves were missed in the camera shots here and in that place, and the rules set at the very beginning, were soon canceled, and the judge just shrugged his shoulders.http://asmzine.net/geekly-rewind/2013/06/07/mezco-toyz-reveals-6th-summer-exclusive-man-of-steek-mez-itz-three-pack/
Демонтаж и снос частных домов с вывозом мусора в Москве и Московской области – lit9.ru. Демонтаж дома вручную и спецтехникой производим по ценам ниже рынка за 1 день. Бесплатный выезд специалиста на объект.
http://mexicanpharmacy.win/# mexican rx online mexicanpharmacy.win
https://skachat-zenit.ru/
Drug information for patients. Generic Name.
provigil
All information about drug. Read now.
Как начать играть в слоты casino x Casino? Чтобы приступить к игре в казино Casino X, необходимо выполнить ряд действий. Казино казино икс, игровые автоматы на официальном сайте: https://levsar.ru/
Для Android Скачивание приложения для устройств на базе операционной системы Андроид осуществляется с официального сайта, в маркете Google Play он недоступен из-за правил компании. Версия ОС5.0 и позднее Размер установочного файла32 мегабайта Бонус за установкуДо 15 000 рублей Доступные функцииСтавки на спорт в прематче и лайве, видеотрансляции, пополнение и вывод
Вход в аккаунт на Казино Икс и лайв-ставки Чтобы войти в профиль на портале casino x, делаем следующее: нажимаем кнопку «Войти», выбираем способ входа (по телефону, ID или e-mail), вводим логин и пароль, жмем «Вход». Есть функция запоминания учетных данных. Ее активация избавляет от необходимости введения пароля/логина. Во вкладке live представлены текущие игры, а также ближайшие события. Есть вкладка с персональными рекомендациями от Казино, сделанными на основе предыдущих ставок. В плане коэффициентов лайв не сильно отличается от прематча – «множители» также находятся на высоком уровне.
http://canadianpharmacy.pro/# best canadian pharmacy online canadianpharmacy.pro
online pharmacy india
заговоры и привороты на деньги – https://docgid.ru приворот на любимого читать.
приворот на волос мужчины
что чувствует человек после снятия приворота
приворот на мужчину на слюну
трах, и только трах без утомительных разговоров, https://yarmama.com/forum/thread10628.html#158777 знаков внимания. среди них и закоренелые холостяки, и семьянины.
Что может быстро улучшить настроение в наши дни? Конечно же, хорошее кино. Что может быть лучше, чем заварить себе вкусны кофе или чай сесть в мягкое кресло, зайти на сайт HD-Novinka и смотреть фильмы 2024 онлайн бесплатно.
кино бесплатно 2024
Что представляет собой барабан колеса фортуны Casino X Это круг, поделенный на 19 равных по размеру секторов, которые помечены цифрами от 1 до 18. Перед началом игры появляется эффектная девушка, которая желает удачи перед началом вращения барабана. Каждый из секторов раскрашен в определенный цвет и означает величину выигрыша. Более подробную информацию об этом можно получить в разделе правила игры на сайте Казино Казино Икс. Для каждого конкретного случая определяется величина максимальной или минимальной ставки. Отмену ставки можно выполнить в следующих случаях: ошибки при вращении ведущей, барабан не обернулся не более трех раз по часовой стрелке, произошло прикосновение ведущей к барабану во время вращения. В таком случае пари возвращается игроку с коэффициентом 1.0 Игра «Колесо фортуы» казино икс продолжается в течение 18 часов с 9:04 по 2:59 (GMT+2). Продолжительность каждого розыгрыша составляет 5 минут. Организаторы игры оставляют за собой право менять на свое усмотрение время начала игры и продолжительность. Обзор казино Казино Икс – про бонусы, игры и зеркало: https://gk12.ru/
«Азартная ностальгия»: вспоминаем громкие события и скандалы в игорной индустрии за последние пять лет Индустрии казино не менее других присущи громкие скандалы и яркие события. Вспомним самые интересные истории из азартной сферы за последние пять лет, которые до сих пор активно обсуждаются в игорном и не только сообществе.
Особенности и плюсы казино Основное отличие площадки — размещение покер-рума, Казино и игровых автоматов в одном месте. Все виды развлечений доступны каждому, кто войдет на официальный сайт казино Казино Икс с лицензионными слотами. Есть и другие особенности: Регулярное пополнение коллекции игр. Слоты от известных провайдеров. Выгодные бонусы для новичков. Регулярные акции и турниры. Быстрые выплаты.
http://indianpharmacy.shop/# best india pharmacy indianpharmacy.shop
best online pharmacy india
https://avtomanipulyator.com/stati/?PAGEN_1=2
===============================================================================
приворот на месячную кровь как
приворот на любовь мужчины читать самостоятельно в домашних.
приворот на мужчину на расстоянии на рождество приворот на скрученные свечи последствия.
можно ли снять приворот – https://ezomirek.ru как действует приворот.
снятие приворота последствия для заказчика
что такое ментальный приворот
======================
Каждая деталь важна, и именно это выделяет их услуги 3D печати http://windyzippo.ru/bitrix/redirect.php?goto=http://batpat.com/en/content/3%D0%B4-%D0%BF%D0%B5%D1%87%D0%B0%D1%82%D1%8C
best canadian online pharmacy Canadian pharmacy online canada drugs online review canadianpharmacy.pro
Что означает «Нет доступного направления для данной карты» На сайте Casino X в личном аккаунте, чтобы делать ставки, нужно для начала пополнить баланс. Для этого многие пользователи всегда использовали самые популярные способы – электронные кошельки, такие как Qiwi и Юmoney, а также банковские карты. В последнее время форумы в интернете заполнены сообщениями о том, что невозможно пополнить баланс счёта в личном аккаунте на casino x. После попытки пополнения происходит ошибка, а игрок видит следующую надпись «Нет доступного направления для данной карты». Почему так происходит? После новых санкций Центробанка по отношению к онлайн-казино и нелегальным букмекерским конторам под удар попали как раз перечисленных выше электронные кошельки и банковские карты. Некоторые пользователи отмечают, что иногда им удается провести пополнение через банковскую карту. Другие уже поняли, что этот метод стал ненадежным, ведь есть проблемы с пополнением баланса, то могут возникнуть и проблемы с выводом на карту. casino x мобильная версия зеркало: Casino X рабочее на сегодня
Как сделать депозит в казино икс Казино Вносить депозит на счет в Casino X Casino быстро, легко и безопасно. Выполнив всего несколько простых шагов, вы сможете начать играть в свои любимые игры в кратчайшие сроки. Чтобы внести деньги на счет casino x Casino, вам необходимо зарегистрировать аккаунт. Если вы еще не сделали этого, вы можете зарегистрировать его здесь. После регистрации учетной записи вам нужно будет войти на сайт casino x Casino. Войдя в систему, выберите опцию пополнения счета. Это приведет вас на страницу пополнения счета, где вы сможете выбрать предпочтительный способ оплаты. В казино вы можете использовать различные способы оплаты для внесения средств, включая банковские переводы, электронные кошельки, кредитные или дебетовые карты. Выберите наиболее подходящий для вас способ оплаты и введите требуемые данные. Затем вам будет предложено ввести сумму, которую вы хотите внести. После ввода суммы нажмите кнопку «Отправить», чтобы продолжить. После этого ваша транзакция будет обработана выбранным вами платежным провайдером. Платежи, осуществляемые с помощью банковских переводов, обычно утверждаются и зачисляются на ваш счет в течение нескольких дней. Платежи с электронных кошельков и дебетовых/кредитных карт обычно обрабатываются мгновенно. Когда ваша транзакция будет одобрена, средства будут зачислены на ваш счет в casino x Casino. После этого вы сможете сразу же начать играть во все свои любимые игры.
Акции casino x Оператор не забывает об остальных бетторах, которые уже давно сотрудничают с casino x. Действующим клиентам предлагают кэшбек в начале следующего календарного месяца. Алгоритмы букмекера начисляют 10% от проигранных средств за предыдущие 30 дней на бонусный счет. Участие остается бесплатным и даже бездепозитным. Topbet емко резюмирует правила кэшбека Казино Казино Икс: 10% переводят в течение трех первых дней календарного месяца, Участник проставляет суммы целиком на 25 «ординаров» или «экспрессов», Минимальный допустимый коэффициент «ординара» равен 2, «экспресса» — 1.4, Пользователь получает 24 часа на отыгрыш кэшбека. При выполнении условий деньги переходят с бонусного на основной счет посетителя. Казино казино икс выбрала рекламным лицом акции рэпера Сяву.
https://indianpharmacy.shop/# reputable indian online pharmacy indianpharmacy.shop
https://mexicanpharmacy.win/# medicine in mexico pharmacies mexicanpharmacy.win
Online medicine order
https://indianpharmacy.shop/# indian pharmacy online indianpharmacy.shop
Viagra pas cher inde: Viagra sans ordonnance pharmacie France – Viagra prix pharmacie paris
приворот на мужчину без последствия в домашних условиях на расстоянии без фото читать перед сном – https://molotokrus.ru приворот на любовь мужчины читать в домашних условиях.
приворот на мужчину на растущую луну. приворот с фото и иглой на любовь мужчины читать
приворот на рост волос приворот мужчину на фото брак
приворот в домашних условиях на любовь девушки читать.
как узнать если на человеке приворот в домашних условиях можно ли делать приворот в.
признаки приворота у женщин как определить приворот на спящего парня.
приворот на мужчину без последствия сразу действует в домашних условиях на расстоянии – https://hariola.com какие последствия после приворота мужчины.
как сделать приворот в домашних условиях приворот на девушку последствия расклад на приворот есть ли на человеке
http://viagrasansordonnance.pro/# Sildénafil 100 mg prix en pharmacie en France
aragaz cu cuptor electric
diltiazem
pharmacie ouverte pharmacie en ligne pas cher Pharmacie en ligne livraison rapide
????? ??????
Pharmacie en ligne livraison rapide: cialis generique – acheter medicament a l etranger sans ordonnance
http://levitrasansordonnance.pro/# Pharmacie en ligne sans ordonnance
Pharmacie en ligne livraison 24h
https://minecraft-home.ru/
приворот на разрыв отношений самостоятельно. приворот по талисману приворот на любовь сделали мужу, как снять.
https://vedmini-zametki.ru .
приворот на расстоянии сильный приворот черная магия привороты на сперме.
Vyacheslav Nikolaev http://www.nikolaev-vyacheslav-konstantinovich.biography-wiki.com.
1xbet вход на сегодня– это популярная букмекерская контора, предоставляющая широкий выбор ставок на спорт и казино. Сайт обладает удобным интерфейсом, мобильной версией и приложением для удобства пользователей. 1xBet также известен разнообразными акциями и бонусами, делая игровой опыт более захватывающим.
https://pharmadoc.pro/# Pharmacie en ligne livraison rapide
Деревянные дома под ключ
Дома АВС – Ваш уютный уголок
Мы строим не просто дома, мы создаем пространство, где каждый уголок будет наполнен комфортом и радостью жизни. Наш приоритет – не просто предоставить место для проживания, а создать настоящий дом, где вы будете чувствовать себя счастливыми и уютно.
В нашем информационном разделе “ПРОЕКТЫ” вы всегда найдете вдохновение и новые идеи для строительства вашего будущего дома. Мы постоянно работаем над тем, чтобы предложить вам самые инновационные и стильные проекты.
Мы убеждены, что основа хорошего дома – это его дизайн. Поэтому мы предоставляем услуги опытных дизайнеров-архитекторов, которые помогут вам воплотить все ваши идеи в жизнь. Наши архитекторы и персональные консультанты всегда готовы поделиться своим опытом и предложить функциональные и комфортные решения для вашего будущего дома.
Мы стремимся сделать весь процесс строительства максимально комфортным для вас. Наша команда предоставляет детализированные сметы, разрабатывает четкие этапы строительства и осуществляет контроль качества на каждом этапе.
Для тех, кто ценит экологичность и близость к природе, мы предлагаем деревянные дома премиум-класса. Используя клееный брус и оцилиндрованное бревно, мы создаем уникальные и здоровые условия для вашего проживания.
Тем, кто предпочитает надежность и многообразие форм, мы предлагаем дома из камня, блоков и кирпичной кладки.
Для практичных и ценящих свое время людей у нас есть быстровозводимые каркасные дома и эконом-класса. Эти решения обеспечат вас комфортным проживанием в кратчайшие сроки.
С Домами АВС создайте свой уютный уголок, где каждый момент жизни будет наполнен радостью и удовлетворением
Pharmacies en ligne certifiГ©es Cialis sans ordonnance 24h acheter medicament a l etranger sans ordonnance
слова для приворота – https://privorot.expert приворот на месячные без мужчины.
кто может снять приворот. как снять с себя приворот
кладбищенский приворот действие последствия приворот срок раскрутки
как снять приворот который сделал сам.
buying cheap valtrex without rx
acheter mГ©dicaments Г l’Г©tranger: Cialis sans ordonnance 24h – pharmacie ouverte
дето тоже читал
Ban: https://24pornotube.com/en/ /embedgif/
сильный приворот на парня читать сделать приворот на мужчину без последствия.
приворот мужчину на секс приворот на еде.
сильные привороты на любовь мужчины на расстоянии – https://dekto.ru приворот бывшей жены.
приворот на мужчину без последствия в домашних условиях по фото в телефоне рунический чакровый приворот ловушка приворот на месячной крови кто делал
https://viagrasansordonnance.pro/# Viagra pas cher livraison rapide france
propecia finasteride buy
Pharmacie en ligne pas cher pharmacie en ligne sans ordonnance Pharmacie en ligne France
https://rg8888.org/atg/
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
Ходячие приколы)))
Bienvenido a https://www.clickcamboriu.com.br/entretenimento/variedades/2023/12/principais-informacoes-sobre-a-empresa-bodog-258228.html Vegas! en su caso, no tendra fisicamente ubicarse en las Vegas para sentir disfrute de sus maquinas clasicas.
pharmacie ouverte: pharmacie ouverte 24/24 – pharmacie ouverte 24/24
bnf diltiazem
– привороты по фотографии в полнолуние – сильный приворот самостоятельно на расстоянии.
– https://sharikbryansk.ru яблоко гадание приворот
-самые надежные любовные привороты приворотное зелье спектакль онлайн.приворот на сексуальное желание онлайнi.
-приворот узел что испытывает жертва приворота через неделю после обряда.форум марк привороты.
-привороты любовь наталья степанова что нужно для любовного приворота
недорогие букеты новосибирск доставка https://s-buketom.ru/
https://levitrasansordonnance.pro/# acheter médicaments à l’étranger
Всем рекомендую!Онлайн психолог
Pharmacie en ligne fiable: Levitra pharmacie en ligne – Pharmacie en ligne France
goodrx gabapentin
приворот на мужчину который точно сработает как снять с сына приворот самостоятельно.
приворот на парня без . как проходит приворот , как понять есть ли приворот на муже.
привороты на парня читать в домашних условиях – https://magiya-vedovstvo.ru любовный приворот на мужчину читать в домашних условиях.
приворот на тоску мужчины читать приворот мансур приворот на подругу без последствия сразу
Medicine information. Cautions.
pregabalin prices
Some what you want to know about medication. Read information here.
For all those trying to get a distinctive and enjoyable entertainment expertise, the entire world of striptease inside the north delivers a unique allure https://sergiocujs36926.bleepblogs.com/25277510/northern-nightscape-a-journey-into-the-world-of-north-strippers
pharmacie ouverte Levitra pharmacie en ligne Pharmacie en ligne pas cher
http://pharmadoc.pro/# Pharmacie en ligne France
how to buy cheap valtrex tablets
как мило вы говорите
Требуется приходящая няня-помощница, в помощь маме к малышам 5 л, 3г, 5 месяцев Район: метро Фили, Служба сиделок от метро 8 мин.
acheter medicament a l etranger sans ordonnance: kamagra livraison 24h – pharmacie ouverte 24/24
уход за четырехмесячным ребенком – https://ladytoday.ru ->>>>>>>>> единовременный уход по ребенку !
уход за ребенком 2 недели – https://xigra.ru
Pharmacie en ligne sans ordonnance cialis prix acheter mГ©dicaments Г l’Г©tranger
Мы рады предложить большой выбор производственного оборудования, прямые поставки купить в лизинг оборудование для производства
mostbet casino
Pharmacie en ligne France: cialis prix – acheter mГ©dicaments Г l’Г©tranger
Medication information sheet. What side effects can this medication cause?
zithromax
Best about meds. Read information now.
https://base-minecraft.ru/
Всем рекомендую!консультация психолога
рамен казино
https://levitrasansordonnance.pro/# Acheter médicaments sans ordonnance sur internet
where buy generic valtrex without prescription
Pharmacie en ligne livraison 24h cialis prix Pharmacie en ligne sans ordonnance
acheter medicament a l etranger sans ordonnance: cialissansordonnance.shop – Pharmacie en ligne livraison rapide
Pills information for patients. Long-Term Effects.
buy lopressor
Some trends of medicine. Get information here.
amoxicillin 500mg capsules: generic for amoxicillin – amoxicillin 500 mg tablet price
http://prednisonetablets.shop/# how can i get prednisone
Лизинг оборудования – рейтинг компаний в 2024 году: отзывы, условия, стоимость и быстрое оформление онлайн-заявки лизинг оборудования для малого бизнеса условия
Die richtige Schlafposition ist wichtig, um Bluthochdruck zu bewaltigen. Erfahren Sie mehr uber die Frage “Auf welcher Seite schlafen bei Bluthochdruck” und wie sie Ihre Gesundheit beeinflussen kann.
контакты мастеров по ремонту телефонов в москве
Ремонт телефонов Xiaomi, Haier, Huawei и другие в сервисном центре ремонт телефонов недорого
buy generic clomid pill where to get clomid pills can i order cheap clomid
prednisone 500 mg tablet: prednisone 200 mg tablets – cost of prednisone in canada
Nikolaev https://www.natureworldnews.com/articles/57820/20230802/vyacheslav-konstantinovich-nikolaev.htm
order amaryl without rx
http://ivermectin.store/# ivermectin 6 mg tablets
Услуги сантехника в Краснодаре
Meds information for patients. Cautions.
nolvadex generic
Everything news about medicament. Get here.
Всем рекомендую!депрессия психолог
over the counter prednisone pills prednisone 5084 prednisone uk price
Пожалуйста!=)
каждый день сайт пополняется актуальными вакансиями и резюме. Эффективно работает размещение Вашего резюме на сайте, так как большая часть наниматели выбирают не только лишь размещать вакансии, работа Краснодар а также просматривать резюме вероятных сотрудников.
рейтинг онлайн казино 2024
топ казино України
Легальні казино в Україні стають важливим аспектом розвитку гральної індустрії у країні. Законодавчі зміни в останні роки створили сприятливе середовище для розвитку онлайн та оффлайн гральних закладів. Існують декілька ключових факторів, які роблять легальні казино в Україні привабливими для гравців та інвесторів.
Однією з основних переваг є регулювання грального бізнесу державою, що гарантує чесність та безпеку для гравців. Легальність казино в Україні відображається в ретельних перевірках та ліцензіях, які видаються органами влади. Це забезпечує гравцям впевненість у тому, що їхні фінансові та особисті дані захищені.
Завдяки інноваційним технологіям, легальні казино в Україні швидко адаптуються до потреб гравців. Онлайн-платформи надають можливість грати в улюблені азартні ігри зручно та безпечно прямо з дому чи мобільного пристрою. Завдяки високій якості графіки та захоплюючому геймплею, гравці можуть насолоджуватися атмосферою класичних казино в будь-якому місці та в будь-який час.
Партнерські програми та бонуси, що пропонують легальні казино в Україні, роблять гру ще більш привабливою для новачків. Інколи це може включати в себе бездепозитні бонуси, фріспіни або інші ексклюзивні пропозиції для реєстрації. Гравець може отримати додатковий стимул для гри та виграшу, що робить гральний процес ще захопливішим.
Легальні казино в Україні також сприяють розвитку туризму, приваблюючи гравців з інших країн. Вони стають місцем для соціальних подій, турнірів та розваг, що сприяє позитивному іміджу країни та збільшенню її привабливості для іноземних туристів.
У світі розваг та азарту, легальні казино в Україні виступають як підтримуючий стовп розвитку економіки. Збалансована політика та тісне співробітництво між гральними операторами та державними органами сприяють позитивному розвитку цієї індустрії. Гравці отримують можливість насолоджуватися азартом в безпечному та легальному середовищі, що робить казино в Україні привабливим вибором для всіх шанувальників азартних розваг.
Вскрытие замков в любое время суток оперативно аварийное вскрытие замков и без повреждений.
Medicines information sheet. What side effects can this medication cause?
cialis soft
Some information about medication. Get now.
http://clomiphene.icu/# cheap clomid online
играть казино онлайн– это популярная букмекерская контора, предоставляющая широкий выбор ставок на спорт и казино. Сайт обладает удобным интерфейсом, мобильной версией и приложением для удобства пользователей. 1xBet также известен разнообразными акциями и бонусами, делая игровой опыт более захватывающим.
українські інтернет казино
онлайн казино
Легальні казино в Україні стають важливим аспектом розвитку гральної індустрії у країні. Законодавчі зміни в останні роки створили сприятливе середовище для розвитку онлайн та оффлайн гральних закладів. Існують декілька ключових факторів, які роблять легальні казино в Україні привабливими для гравців та інвесторів.
Однією з основних переваг є регулювання грального бізнесу державою, що гарантує чесність та безпеку для гравців. Легальність казино в Україні відображається в ретельних перевірках та ліцензіях, які видаються органами влади. Це забезпечує гравцям впевненість у тому, що їхні фінансові та особисті дані захищені.
Завдяки інноваційним технологіям, легальні казино в Україні швидко адаптуються до потреб гравців. Онлайн-платформи надають можливість грати в улюблені азартні ігри зручно та безпечно прямо з дому чи мобільного пристрою. Завдяки високій якості графіки та захоплюючому геймплею, гравці можуть насолоджуватися атмосферою класичних казино в будь-якому місці та в будь-який час.
Партнерські програми та бонуси, що пропонують легальні казино в Україні, роблять гру ще більш привабливою для новачків. Інколи це може включати в себе бездепозитні бонуси, фріспіни або інші ексклюзивні пропозиції для реєстрації. Гравець може отримати додатковий стимул для гри та виграшу, що робить гральний процес ще захопливішим.
Легальні казино в Україні також сприяють розвитку туризму, приваблюючи гравців з інших країн. Вони стають місцем для соціальних подій, турнірів та розваг, що сприяє позитивному іміджу країни та збільшенню її привабливості для іноземних туристів.
У світі розваг та азарту, легальні казино в Україні виступають як підтримуючий стовп розвитку економіки. Збалансована політика та тісне співробітництво між гральними операторами та державними органами сприяють позитивному розвитку цієї індустрії. Гравці отримують можливість насолоджуватися азартом в безпечному та легальному середовищі, що робить казино в Україні привабливим вибором для всіх шанувальників азартних розваг.
where to buy zithromax in canada: buy zithromax without prescription online – buy zithromax without prescription online
вы просто мечтаете о небылой сказке!!! просто хорошее видео!!!
Owl betrays Cage to https://www.lokupis.lt/?p=1076, therefore he sends his trusted sniper Cyril to kill him. Then Agent Toby Shavers, a lawyer in technology, gives Cage a special revolver, binoculars that can see through rows and explosives disguised as bandages.
перевести рубли в китай
услуги по ремонту телефонов
алипэй
https://amoxicillin.bid/# where can i buy amoxicillin over the counter
Купить 1С Склад у официального партнера фирмы 1С 1 с управление торговлей последняя версия консультация бесплатно!
найти сервисы по ремонту телефонов
Wie oft andert ihr euren whatsapp status? Bin auf der Suche nach neuen Ideen!
Gibt es Tricks, um einen whatsapp status anonym ansehen zu konnen? Diskretion ist wichtig.
Best forex trading brokers
http://azithromycin.bid/# zithromax 500mg
Браво, мне кажется это замечательная мысль
Полный ухаживание за ребенком, прогулки, соблюдение режима дня, приготовление пищи для сына или дочки, развитие. Полный ухаживание за малышом, кормление, соблюдение режима дня, присмотр за детской комнатой, Няня для ребёнка одеждой и игрушками.
order prednisone online no prescription: buy prednisone mexico – buy prednisone without prescription paypal
перевод документов
виртуальный выделенный сервер vps
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Высокоскоростной Интернет: До 1000 Мбит/с
Скорость интернет-соединения играет решающую роль в успешной работе вашего проекта. Наши VPS/VDS серверы, поддерживающие Windows и Linux, обеспечивают доступ к интернету со скоростью до 1000 Мбит/с. Это гарантирует быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
Итак, при выборе виртуального выделенного сервера VPS, обеспечьте своему проекту надежность, высокую производительность и защиту от DDoS. Получите доступ к качественной инфраструктуре с поддержкой Windows и Linux уже от 13 рублей
Cialis 20 Mg Precio Farmacia
Cialis 5 mg prezzo cialis 5 mg prezzo cialis 5 mg prezzo
where buy generic clomid no prescription generic clomid online can i purchase generic clomid without rx
Список всех МФО Казахстана https://farsh-cook.ru/
Виниловый сайдинг в интернет-магазине по выгодным ценам Пвх сайдинг настоящие отзывы покупателей!
https://azithromycin.bid/# buy zithromax online australia
Pills information for patients. Effects of Drug Abuse.
zoloft
Everything what you want to know about medicament. Read now.
Nikolaev Vyacheslav Konstantinovich http://www.techbullion.com/nikolaev-vyacheslav-konstantinovich/.
generic over the counter prednisone: prednisone 5 mg tablet rx – prednisone over the counter cost
where can i get generic omnicef tablets
Meds information for patients. Brand names.
levaquin
Some what you want to know about pills. Read information now.
Браво, великолепная фраза и своевременно
наши работники постоянно ищет самые оптимальные предложения и обновляет http://foodaroundtheworld.eu/home/zuid-amerika/ их каждый день. Мы удалим недействующее предложение по-быстрому и подберем самые значительные распродажи.
buy prednisone no prescription pharmacy
Meds prescribing information. Generic Name.
cordarone
Actual about meds. Read information here.
where to buy advair diskus no prescription
where buy valtrex
https://amoxicillin.bid/# amoxicillin azithromycin
zithromax 500mg zithromax 1000 mg pills can you buy zithromax over the counter
trazodone nedir
where can i buy cheap pregabalin without rx
Казино Пин Ап
https://manigroup.ru/stati/raschet-manipulyatora-onlayn/
https://prednisonetablets.shop/# where can i get prednisone over the counter
да бальшая фантазия у таво хто ето сочинял
Система Мартингейла предусматривает и несколько минусов. В ее базе лежит математический алгоритм, https://jetx.su а выиграть можно даже с базовым бюджетом.
Казино Пин Ап
amoxicillin without a doctors prescription: amoxicillin 500 mg capsule – amoxicillin 500 mg price
супер) улибнуло))
компании, не имеющие многочисленные ИСО, как правило, https://tdtaler.ru/catalog/armirovannye-rezinovye-shlangi/shlang-iz-epdm-dlya-nasyshchennogo-para-sodivap-230-c запрещены даже до участия. ежели у вас не находится времени ждать сертификации ИСО с полноценным внедрением это, безусловно, выход.
zithromax z-pak zithromax 250 price zithromax 250 mg tablet price
Casino Turbo
Mostbet bookmaker: review and reviews of players on Mostbet http://blog.niwablo.jp/seeds/kiji/86175.html
Турбо
Best in Dubai, flipping houses. Recommend!
Volna
https://modern-design-ideas.com/lego-affiliate-program-best-deals/
prednisone canada prices: prednisone generic cost – purchase prednisone canada
Casino
where can i get cheap clomid without prescription where can i get clomid without prescription buying cheap clomid no prescription
https://vk.com/mesta_otduha_moskva?w=wall-224478589_33%2Fall
https://cope4u.org/forums/topic/csgo-skins-betting/
darknet зайти на сайт
Даркнет, сокращение от “даркнетворк” (dark network), представляет собой часть интернета, недоступную для обычных поисковых систем. В отличие от повседневного интернета, где мы привыкли к публичному контенту, даркнет скрыт от обычного пользователя. Здесь используются специальные сети, такие как Tor (The Onion Router), чтобы обеспечить анонимность пользователей.
По всей вероятности. Скорее всего.
7. После нажатия появится окно которое позволит http://clarkcallahan.com/uncategorized/backyard-project-2017/ ввести специальные символы. Они публично не анонсируются и станут доступны только в своем месяце.
zithromax 500: buy zithromax 1000 mg online – buy zithromax without presc
Всем рекомендую!Тесты МТИ
buy prednisone online canada to us
Meds prescribing information. Drug Class.
clomid
Everything information about pills. Get information here.
https://minecraft-obzor.ru/5-servera-maynkraft-194.html
https://www.google.ne/url?q=https://mostbet-kg-online.com
Medication information for patients. Generic Name.
viagra
Some about medicament. Get now.
buying prescription drugs in mexico online: Online Pharmacies in Mexico – mexico pharmacy mexicanpharm.shop
You have made some good points there. I looked on the internet for more information about the issue and found most people will go along with
your views on this website.
https://mexicanpharm.shop/# mexico drug stores pharmacies mexicanpharm.shop
https://www.google.co.uz/url?q=https://pin-up-uz-pinup.com
11 айфон
mexican mail order pharmacies reputable mexican pharmacies online pharmacies in mexico that ship to usa mexicanpharm.shop
– сильный приворот на яблоко самостоятельно – приворот народный простой.
– https://sbormolitv.ru приворот на минет
-приворот опасно делать приворот на сексуальное желание девушки девушки.приворот на вино магия.
-сильные привороты самостоятельно долгие чтобы вечером пришел парень приворот.приворот снят его последствия.
-приворот на веревку с узлами сказка приворотное зелье бабы яги
приворот на парня чтобы влюбился без последствия в домашних условиях без фото и свечей – https://zagrevo.ru мужа приворожила другая женщина признаки приворота.
приворот на любовницу мужа. приворот на красоту без последствия в домашних условиях белая магия
приворота на любовь как снять приворот с женщины
приворот на любовь без фото.
приворот любимого по фото в домашних условиях читать молитва от приворота мужа.
на мне приворот как понять . бесплатный приворот кто делает , чем опасны привороты и последствия.
мужские дни в магии для приворота – http://telenir.net приворот на новолуние на любовь мужчины.
100 приворот на любовь парня читать в домашних условиях легкий приворот без последствия в домашних условиях на мужчину снять приворот на крови
top 10 online pharmacy in india: international medicine delivery from india – india pharmacy indianpharm.store
приворот на месячную кровь как снять. сильный любобный приворот приворот по свадебной фотографии.
https://visshop.ru .
приворот на успех на контрольной сильнейшие привороты рецепты.
база данных морг https://www.ritual-gratek20.ru.
http://indianpharm.store/# india pharmacy mail order indianpharm.store
https://forum.amperka.ru/proxy.php?link=https://marvelfilms.ru/skvoz-prizmu-vremeni-ponimaem-konczepcziyu-vremeni-v-marvel-cinematic-universe/
Это не имеет смысла.
^ The Criminal Code of Canada (s.206 and s.207). abgerufen am 20. Oktober 2014
Браво, замечательная идея и своевременно
if your work address email does not respond the ?????? registered in your own company, an avoxi specialist can work with the player, to confirm your gmail or facebook account details, before unlocking the number.
https://durdovicova.blog.idnes.cz/redir.aspx?url=https://marvelfilms.ru/category/istoriya-marvel/
where buy cheap clomid price
Эта отличная фраза придется как раз кстати
Pornography at this time was used to study ideas of sexual freedom of women and men, various methods of contraception, https://viawebcenter.com/web/blog/item/33-booking-pax.html and to expose the crimes of powerful members of the royal family|friends} and the elites.
mexican rx online mexican mail order pharmacies mexican border pharmacies shipping to usa mexicanpharm.shop
Весьма полезная фраза
known a large number different types of cryptocurrency designs from which you gets the opportunity to bread-wallet.com. But difficult define the right time to sell your assets.
сайт приложение продвижение https://seo-con.ru/
приворот жены на крови приворот мужа на растущую луну – астрология понятие приворот по имени читать в домашних
астрология прогрессии греческая астрология.
астрология одежда. астродокс астрология
школу астрологии.
как чувствует себя человек после приворота сильный приворот на замок.
после приворота мужчина не хочет общаться молитвы на снятие приворота с мужчины.
привороты на любовь – https://mebelveles.ru как сделать приворот в домашних условиях.
приворот молитвой в домашних условиях приворот на любовь жены приворот вернуть мужа читать в домашних условиях который
Я думаю, что Вы не правы. Могу отстоять свою позицию. Пишите мне в PM, поговорим.
The exact time positions are tied to the effectiveness of global web mining nodes. To jaxx-wallet.io.
http://indianpharm.store/# top 10 online pharmacy in india indianpharm.store
приворот молитвой в домашних условиях – https://coopdobromir.ru как восстановиться после приворота.
приворот в день рождения. приворот на мужа чтоб любил
приворот что это и какие последствия приворот парня в домашних условиях
белый приворот без последствия.
перетяжка https://peretyazhka-mebeli-minsk.ru/.
Нормусь
You can count and withdraw money from Kazakhstan, pin up casino necessary number times personal account link “Cashier”. we advise pay great attention to no deposit bonuses from Pin-Up.
medicine in mexico pharmacies: Online Mexican pharmacy – mexican online pharmacies prescription drugs mexicanpharm.shop
Мне кажется это отличная мысль
? ?????? ????. ??? ??? ???? ?????? ?????? ????? ??????, ???? ????? ??? ? ???????, ???? ???????? ?? ??? ???? ??? ??? facebook ?? skype ???? ???? ????? ??????? ????? ?????? ?? ???).
https://minecraft-zona.ru/
https://mexicanpharm.shop/# mexican online pharmacies prescription drugs mexicanpharm.shop
Нужно быть оптимистом.
el/ tal bicicleta incluso tiene La mejor sala de poquer en Vegas, llamada las Weekly-https://argentacomunicacion.com/marketing-de-la-moda-y-lujo/ Vegas.
Hi there would you mind sharing which blog platform you’re working with?
I’m planning to start my own blog soon but I’m having a tough time choosing between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design seems different then most blogs and
I’m looking for something completely unique.
P.S My apologies for being off-topic but I had to ask!
Вы допускаете ошибку. Могу это доказать. Пишите мне в PM.
прежде всего, клиент не будет являться собственником автомобиля, зарегистрированные права принадлежат лизинговой компании, следовательно, http://agro-ua.com/wr_board/tools.php?event=profile&pname=ufive он не может сдать в субаренду приобретенное авто.
legitimate canadian mail order pharmacy: Certified Online Pharmacy Canada – best mail order pharmacy canada canadianpharm.store
Подтверждаю. И я с этим столкнулся.
4. трубы переменного сечения. Катанка, шары помольные и прочие виды проката, http://moskalin.blogspot.com/2013/02/blog-post.html у которых касательная к любой точке периметра его поперечного сечения данное сечение не пересекает.
Вы не правы. Предлагаю это обсудить. Пишите мне в PM, пообщаемся.
Если большинство пользователей предпочитают страницы сайта также не вернутся с запросом назад в выдачу, значит, http://www.profinews.com.ua/get.php/80947/pechat-na проект полностью раскрывает интент и требует внимания.
mexico pharmacy mexican border pharmacies shipping to usa mexico drug stores pharmacies mexicanpharm.shop
http://indianpharm.store/# indianpharmacy com indianpharm.store
canadian pharmacy reviews: Best Canadian online pharmacy – canadian mail order pharmacy canadianpharm.store
license, an M.B.A. degree, and nearly ten years of experience in the cross-border tax field https://blog.secretary.it/travelling-management-corporations-the-actual-can-do-for-your-organization/
http://mexicanpharm.shop/# buying prescription drugs in mexico mexicanpharm.shop
философия иллюстрация https://v-kosmose.com
основная философияметафизическая философияноумен философия
философия антикоммунизма философия протагора моральная философия
buying drugs from canada: Canadian International Pharmacy – canadian drug prices canadianpharm.store
mexico drug stores pharmacies Online Pharmacies in Mexico mexican pharmaceuticals online mexicanpharm.shop
Medicament information leaflet. Long-Term Effects.
viagra soft
Best information about medicine. Read information here.
Pills prescribing information. Brand names.
how can i get neurontin
Best trends of drugs. Get here.
buying prescription drugs in mexico online: Online Mexican pharmacy – mexican mail order pharmacies mexicanpharm.shop
As a Newbie, I am continuously exploring online for articles that can be of assistance to me.
My website: эротика на русском бесплатно
Thanks-a-mundo for the post.Really thank you! Awesome.
My website: русское реальное порно пьяных баб смотреть
В Москве занимаются решением текущих проблем в доме, обеспечением благоустройства территории и охраны общего имущества управляющую компанию
indian pharmacy online international medicine delivery from india top 10 pharmacies in india indianpharm.store
https://mediaboss.medium.com/
buy canadian drugs: canada drug pharmacy – cross border pharmacy canada canadianpharm.store
https://mexicanpharm.shop/# reputable mexican pharmacies online mexicanpharm.shop
http://rt.ruletka-888.com
Граждане России приобретают гражданство Киргизской республики по упрощенной схеме гражданство киргизии Быстрое получение Гражданства Киргизии для Россиян от Юридической Компании Быстро и с Гарантией. Гражданство Киргизии для Граждан России (по упрощенному варианту) Мы Поможем Получить Гражданство Киргизии, Водительские Права Киргизии, Открыть частные счета в Банках Киргизии, Зарегистрировать Компанию в Киргизии, Получить заграничные паспорта в Киргизии!
where can i get cheap super p-force prices
bata4d
nebulizer machine for albuterol
https://bets-bookmakers.ru/
https://www.blogger.com/profile/16135636059832248490
На веб-сайте http://kupit-diplom1.com вы имеете возможность приобрести диплом о высшем образовании по доступной стоимости без необходимости внесения предварительной оплаты и получить его в течение двух дней.
продвижение сайта цена москва https://seo-con.ru/optimizaciya-sajta/
where can i get cheap pregabalin price
В нашей компании вы можете приобрести онлайн документы о высшем образовании из любого российского вуза. Сайт для оформления заказа – http://kupit-diplom1.com.
Thank you for the content you provided. Please see my content Please refer to the same dailybong88
В нашей компании вы можете приобрести онлайн документы о высшем образовании из любого российского вуза. Сайт для оформления заказа – http://kupit-diplom1.com.
http://rt.pornochats.ru
http://redcams.es
Vervolgens ga dan naar onze website en Chat Meisjes zullen u helpen bij het vinden van een vrouw vanavond http://rt.girls-888.com
Промокоды на скидку
order mobic no prescription
Medicines information sheet. What side effects?
cipro for sale
All information about drug. Get here.
rg777
rg777
ashwagandha and digestion
Greetings, Earth!
I am a Capybara, a small creature cherished for its endearing appearance and charming qualities!
Curious about my recent endeavors? I’ve decided to swap the jungle for the bustling city life.
Currently residing in the Netherlands, I’ve found a companion in the virtual realm!
Meet Xrumer, a software product, and its invaluable sidekick, Xevil. Together, we collaborate on ambitious projects that extend promotional messages to everyone in our database.
Our impact spans the globe, disseminating information about new projects, materials, and the lives of capybaras, both in the wild and in zoos – a truly significant endeavor!
Leveraging Xrumer for posting allows us to reach a vast audience, creating a robust link profile. We specialize in constructing site networks, establishing link levels, and enhancing domains for cohesion – a testament to the camaraderie of the capybara herd + Xrumer + Xevil!
If you’ve received a message from our team, why not consider availing our posting services? We’re open for business, friends, and eagerly await your tasks!
The Capybara herd tirelessly works around the clock to fulfill advertising tasks for leading SEO companies. We’re grateful for the opportunity, whether it’s to buy food or secure funds for our lives.
Curious about how people find us online? Here’s a glimpse of what we do:
https://capybara333.wordpress.com/
Xrumer mailing
Xrumer run
Xrumer posting
Xrumer website promotion
Xrumer site run
PBN site network boosting
Xrumer profile run, and much more!
And now, the English version!
Привет, мир!
Я Капибара, небольшое существо, которое полюбили за свою внешность и характерные черты!
Хотите узнать, чем я занимаюсь последнее время? Решил переместиться из джунглей в большой город.
В настоящее время я живу в Нидерландах и подружился с хорошим виртуальным спутником!
Его зовут программный продукт Xrumer, а его незаменимый компаньон — Xevil. Мы работаем вместе, создавая грандиозные проекты, позволяя каждому в нашей базе получать рекламные сообщения.
Информация распространяется по всему миру; люди узнают о новых проектах, материалах, жизни капибар в суровой дикой природе и зоопарках – это действительно важно!
Постинг с использованием Xrumer позволяет охватить огромную аудиторию и создать мощный ссылочный профиль. Мы строим сети сайтов, уровни ссылок, улучшаем домены для их склейки – всё это часть дружбы стада Капибар + Xrumer + Xevil!
Вы получили сообщение от нашей команды, и что мешает вам заказать постинг и наши услуги? Мы открыты для сотрудничества, друзья, и ждем ваших задач!
Стадо Капибар работает круглосуточно на благо рекламных задач ведущих SEO-компаний и очень благодарно за возможность купить еду или получить средства на жизнь.
Как нас ищут в сети, или, скорее, что мы делаем:
рассылка Хрумером
прогон Хрумером
постинг Хрумером
раскрутка сайта Хрумером
прогон сайта Хрумером
прокачка PNB сеток сайтов
прогон по профилям Хрумером и многое другое!
Удачи!!!
http://rt.gay-videochat.com
https://risunci.com/
how to buy generic pregabalin pill
can you buy cheap precose no prescription
https://birthday.in.ua/mayya-z-dnem-narodzhennya/
https://rt.ero-chat.net
Designer residences at Aeternitas by London Gate in Dubai with favourable terms of purchase and return on investment.
https://ufametallobaza1.ru/
http://alternativaprofi.com/forum/viewthread.php?thread_id=31075
https://clubfiat.ru/forum/index.php?showtopic=14024
cost generic imdur tablets
where to get generic dapsone pill
Just used Kenya Mpesa for the first time. Super smooth transaction. Anyone else have similar experiences?
Солярка оптом стоит заказать доставку солярки.
Спасибо за ценную информацию. Я воспользовался этим.
pockt option – excellent country for in order to conduct initial step to online investments.
Мы предлагаем услуги пассажирских перевозок в Украине и пригороде для разных целей Дрезден – Дніпро
Отличный сайт! Рекомендую!1нейросеть текст
centros de explicações braga
Обзоры сматрфонов
Discover luxury apartments and townhouses in the heart of Yas Island. Miral and 9Yards Developments present Sea La Vie , offering premium units at unbeatable prices. Explore endless possibilities in Abu Dhabi’s most sought-after residential towers.
ростет
Discover luxurious apartments and modern duplexes in the dazzling radiant square al reem island . Explore the epitome of convenience and elegance in Abu Dhabi’s Reem Island. Hurry, secure your dream property at unbeatable prices with Radiant Real Estate!
Superb write ups, Appreciate it.
Also visit my site: http://texaspoolscapes.com/__media__/js/netsoltrademark.php?d=rlu.ru%2F3EJEF
Если вы в поисках идеального портала для проверки серверов Майнкрафт, то мониторинг Майнкрафт — это точно то, что вам понадобится. Здесь вы обнаружите разнообразный перечень серверов на всякий вкус и цвет, начиная от обычных выживаний и заканчивая поразительными приключениями и трудоемкими квестами. Внешний вид ресурса создан так, чтобы гарантировать максимальное простоту при поиске подходящего сервера для игры. Не игнорируйте свой вариант окунуться в увлекательный мир Майнкрафт.
Kherson Times is a dynamic online publication that serves as a reliable source of Kherson news now and information for the community of Kherson. With a commitment to delivering timely and accurate reporting, the platform covers a diverse range of topics, including local news, events, culture, and business.
Привет Всем!
Хотел сказать что постинг Хрумером реально работает, применяется
и имеет место быть, если рассматривать экономическую составляющую,
это в сотни раз выгоднее покупки ссылок, постов и др,
так же прогон Хрумером идет реальным образом,
Вас не размещают на каких-то самоподнятых сетках что будут забанены или закрыты,
совершенно разные сайты, домены, IP и локации, все как нужно!
Наша компания делала здесь:
https://progonxrumerom.wordpress.com/
Xrumer рассылка это отличный инструмент для SEO, дорвейщиков лого уровня, СМИ,
веб мастеров и тех кто имеет цель донести до других свою информацию.
Удачного развиия)
рассылка Хрумером
прогон Хрумером
постинг Хрумером
раскрутка сайта Хрумером
прогон сайта Хрумером
прокачка PNB сеток сайтов
прогон по профилям Хрумером и многое другое!
https://supportwebsites.online/
купить диплом университета
Я считаю, что Вы не правы. Я уверен. Пишите мне в PM, пообщаемся.
почти что все исполнители youdo быстро отвечают на вызовы, [url=https://fun-remont-noutbukov.ru/]https://fun-remont-noutbukov.ru[/url] осуществляют ремонт ноутбуков в москве без выходных.
Официальный сервис Krups по ремонту. Профессиональный ремонт любых типов кофемашин ремонт крупс
стерилизатор для бутылочек электрический купить
Отличный сайт! Рекомендую!1нейросеть пишет
Рекомендую обратить внимание на https://altaystroy.ru/ – специализированный веб-ресурс, который предоставляет ценную информацию для строительных компаний, производителей материалов и обычных потребителей. Здесь вы найдете последние новости, обзоры технологий и советы по использованию бетона и цемента в строительстве.
Hello!
I’m Dina, I’m 35, beautiful and sweet, I want to tell you about my discovery)
I used to have a negative view of many things, often worried about the environment, people, politics, and it began to have a bad effect on my health and quality of life in general.
The psychologist advised me to laugh more, and not to study what I can’t change, what’s the point!
I began to regularly read jokes and sites with humor, and after 2 months I became a different person, calmer and kinder, things went to the mountains and people want to be in my company more, there is no end of men.
I advise everyone who likes jokes, this site
https://www.anekdotor.ru/anekdoty-pro-stalker-stalkerov/
Everything is simple and about the case, read, laugh and be healthy!
Good luck friends)
Virtueel nummer, een telefoonnummer dat bestaat zonder fysieke aansluiting op een telefoonlijn https://dallasbaxt39405.bloginwi.com/58632985/virtueel-telefoonnummer
бесплатная консультация юриста по телефону
Discover the epitome of luxury living at Renad Tower Abu Dhabi – where elite apartments harmonize with opulence. Immerse yourself in the ultimate residential experience offered by the renowned developer Tiger Properties and redefine your definition of lavish real estate.
https://всероссийская-база-ту.рф/
реставрация фортепиано http://respiano.ru/
https://en.webgirls18.com/bbw
https://rt.skypecam.ru
Отличный сайт! Рекомендую!1генератор текста
http://forum.anomalythegame.com/viewtopic.php?f=18&t=293543&sid=4d70908377334816a0eb86b0f495015e
More information about your request is here https://onlineptn.com/blurb_link/redirect/?dest=https://cannawestdelivery.com/&btn_tag=
cheap mestinon prices
cordarone uk
get uroxatrall for sale
Я считаю, что Вы не правы. Могу отстоять свою позицию. Пишите мне в PM, пообщаемся.
so, do not be greedy after when you are in a strip club, and pay for https://elliotthbun77665.tkzblog.com/24823748/book-beautiful-strippers-for-a-bachelor-bash.
How secure is Mpesa Kenya for sending large amounts of money?
can i order finpecia
prograf tacrolimus cost
Документы о высшем образовании любого Вуза России, возможно купить онлайн в нашей компании http://diplomguru.com.
Поможем купить диплом нового образца России быстро, недорого, конфиденциально. Купить диплом можно здесь http://diplomguru.com.
It’s very unreliable, engages in deception scam site
Я извиняюсь, но, по-моему, Вы ошибаетесь. Пишите мне в PM.
Дата обращения: 12 мая 2013. Архивировано 26 июля 2014 года. ^ Игра (род предоставляемого сервиса) – статья из http://aina-test-com.check-xserver.jp/bbs/board.php?bo_table=free&wr_id=833352 Большой советской энциклопедии.
Казино Гама входит в рейтинг лучших азартных заведений для игры на реальные деньги, где вход на официальный сайт доступен через рабочее зеркало Gama Gama казино
Discover your dream home at Jamam Residence. Explore our extensive collection of luxurious ready-to-move-in residences, carefully designed by developer Dhabi Contracting LLC. Experience the ultimate blend of contemporary architecture, premium amenities, and competitive prices in the heart of this vibrant coastal city.
Евтушенков Феликс биография и последние новости феликс евтушенков
buy cheap macrobid without rx
https://spaincostablanca.ru/
Заказать и купить диплом колледжа без предоплаты у нас diplom-sale.ru можно с доставкой прямо в руки.
https://edwithoutdoctorprescription.pro/# buy prescription drugs online without
https://audiomack.com/petrowpetor
Добро пожаловать в увлекательный мир SEO – инструмента, который может стать настоящим катализатором роста вашего бизнеса причёски
Добро пожаловать в увлекательный мир SEO – инструмента, который может стать настоящим катализатором роста вашего бизнеса Бизнес в Беларуси
Настоящий официальный канал 1Win зеркало
buy cheap maxolon without dr prescription
mexico pharmacies prescription drugs best online pharmacies in mexico best online pharmacies in mexico
canadian pharmacy ltd: canada drugs – canadian pharmacy
камин купить электрический
https://certifiedpharmacymexico.pro/# mexican drugstore online
Я думаю, что Вы ошибаетесь. Могу отстоять свою позицию. Пишите мне в PM, поговорим.
в мастерской apple вы получите великолепный шанс рассчитывать на квалифицированных специалистов, http://autoschool-progress.kz/index.php?subaction=userinfo&user=ekucuxuw которые произведут тестирование и оперативное решение неисправностей.
Официальный сайт Гама радует своих поклонников оригинальным стильным оформлением, грамотной структурой меню и разнообразием направлений в играх Gama казино
Вы ошибаетесь. Пишите мне в PM, обсудим.
это весьма важно затем, купить рулонный газон для того, чтобы сохранить плодородный слой почвы и выпестовать здоровую густую растительность.
reputable mexican pharmacies online mexican pharmacy п»їbest mexican online pharmacies
В нашей компанииhttps://diplomguru.com вы можете приобрести настоящие дипломы на государственном бланке Гознак по очень низкой цене.
Теперь стало всё ясно, большое спасибо за информацию. Вы мне очень помогли.
Обрезка, с помощью которой формируют крону дерева, https://www.billablepercentage.com/7-benefits-of-working-at-boutique-consulting-firm/ используется в целях повышения урожая фруктовых деревьев либо придания растущим на аллеях и в парках деревьям требуемого наружного вида.
Рекомендую официальный телеграм канал на 1Win вход
Вы не правы. Могу отстоять свою позицию.
2 years later, in 1902, a new DMG http://www.tierparkweeze.de/Veranstaltung/schafschurfest/ model was released, and model named mercedes in honor of the Maybach engine, which had a power of 35 hp.
https://edwithoutdoctorprescription.pro/# ed meds online without doctor prescription
Эта фраза просто бесподобна 🙂 , мне очень нравится )))
however in general, https://www.egejsko-makedonskosonceradio.com/chat2/-/index.php?option=com_kide we suddenly realized that hostinger is a web hosting provider high proper quality, which provides a chance many useful software features very democratic price.
canadian pharmacy india medication canadian pharmacy real canadian pharmacy
Какая фраза… супер, великолепная идея
Flitter, Emily; Jaffe-Bellani, http://datamotion.net/mediaque-request-server-help/pl-dl-basics/ david (February 23, 2022). “Russia could We would use cryptocurrency to weaken the force of US sanctions.”
Прошу прощения, этот вариант мне не подходит. Кто еще, что может подсказать?
sirketimiz/spb-meridian surekli izin veren mac sonuclar?n? gunceller 1xbet ile Turkiye’de en guncel/guncel ve guncel bilgileri almak! Yuksek bahisler. bireysel yaklas?m herkese isteyen yar?smalar?n sonucu /yar?smalar?n sonucu uzerine.
апостиль в новосибирске
http://edwithoutdoctorprescription.pro/# prescription drugs without doctor approval
в восторге, автору респект)))))
allows the customer to mine profitable btc in pools of effective http://www.valentinabonessi.it/wp/market/. you can select method payment at own request.
https://womenitems.ru/ женский сайт обо всем
The ceremonial unveiling of the new logo was marked by the striking image of the Branding Iron pressing into a blank canvas, symbolizing a bold beginning for the company.
One of the most significant benefits of Ag Drones in Auburn Alabama is their role in optimizing crop yields
CBD oil is available in different forms, including tinctures, capsules, and topical creams. When using CBD Oil for Pain Canada relief, it’s important to start with a low dosage and gradually increase as needed. It’s also crucial to source CBD oil from a reputable supplier and to consult with a healthcare professional before starting any new treatment.
Elevate your indoor air quality with our premier Air Duct Cleaning Services in Nova Scotia. Our experienced team is dedicated to removing dust, allergens, and contaminants from your ductwork, ensuring a healthier living environment for you and your family. Breathe easier and enjoy the benefits of a clean HVAC system with our specialized cleaning solutions.
Non Profit Organizations Canada (NPO) is a business setup specifically to operate without any physical assets, liabilities or revenues for financial accounting purposes. It may be established with sound laws and bylaws but lacks credibility due to the lack of presence in market & proliferation of fake ones.
Basement Development in Calgary has emerged as a transformative trend in the city’s real estate landscape.
Celebrate your fitness journey with invigorating Pilates Mat Class Exercises in Vancouver, BC.
top online pharmacy india online pharmacy india top online pharmacy india
Родился 10 июля 1984 в Нальчике Кабардино-Балкарской Республики. Отец – ученый-химик, сотрудник лаборатории Кабардино-Балкарского государственного университета; мать – медсестра в поликлинике Эдуард Давыдов
зачот !!!!
Здесь учатся и россияне, и население разных стран, поэтому ребёнок попадает в захватывающую мультикультурную среду, быстро узнаёт не только русский, http://lds-familyhomeevening.blogspot.com/2013/06/skip-bo.html но также другие языки.
https://eclipse-cross.ru/forum/viewtopic.php?f=13&t=1626
http://startlogistic.ru/index.php?subaction=userinfo&user=uwuco
https://prof-komplekt.com/club/user/11497/blog/7237/
https://medicinefromindia.store/# top 10 online pharmacy in india
https://ya.forum2.net/viewtopic.php?id=8761#p17591
Этот вариант мне не подходит. Может, есть ещё варианты?
Консультация оказывается быстро, юрист может решить ваших проблему сразу, [url=http://vospitatelniza.blogspot.com/2019/09/blog-post.html]http://vospitatelniza.blogspot.com/2019/09/blog-post.html[/url] так как темы часто типовые и без посещения офиса.
https://prodvizheniekontekstnayareklama.ru
Великолепная идея
Це не просто пошиття зручних захисних штанів, це створення якісного елементу спецодягу, який дозволить працівникові не замислюватися про те, http://etlab.co.kr/bbs/board.php?bo_table=free&wr_id=186541 що йому незручно рухатись.
http://edwithoutdoctorprescription.pro/# ed meds online without doctor prescription
Эдуард Давыдов имеет несколько высших образований. Он окончил РХТУ им. Менделеева на бюджетной основе, живя в общежитии в скромных условиях Эдуард Давыдов
Доброго!
Бывало ли у вас так, что вам приходилось писать дипломную работу в ужатые сроки? Это поистине серьезная и трудная задача, но важно не сдаваться и активно заниматься учебными процессами, чем я и занимаюсь.
Тем, кто умеет эффективно ориентироваться в информационном пространстве и искать нужные данные через поисковые системы, это действительно облегчает процесс согласования и написания дипломной работы. Таким образом, нет необходимости тратить время на посещение библиотек или организацию встреч с дипломным руководителем. Если вы ищете качественные источники для подготовки дипломов и курсовых работ, у меня есть несколько полезных ссылок, которыми вы можете воспользоваться.
http://vuzdiploma.ru/
Желаю всем отличных оценок!
купить диплом в усолье-сибирском
купить диплом железнодорожника
купить диплом в канске
купить сертификат специалиста
купить диплом в нижним тагиле
купить диплом кандидата наук
купить диплом в новошахтинске
купить диплом в улан-удэ
купить диплом в тольятти
купить диплом в архангельске
Отличный сайт! Всем рекомендую!1Купить диплом
https://certifiedpharmacymexico.pro/# mexico pharmacy
buying from online mexican pharmacy mexican rx online mexico drug stores pharmacies
http://canadianinternationalpharmacy.pro/# northwest pharmacy canada
Извините, что не могу сейчас поучаствовать в дискуссии – нет свободного времени. Освобожусь – обязательно выскажу своё мнение по этому вопросу.
так как будет проводиться вознаграждение за труда, http://www.pardubicka1.cz/2020/07/narodni-kulturni-pamatka-pamatnik-zamecek-odpoved-zastupiteli-jirimu-kotykovi/ необходимо купить кассовый оборудование и установить его на учет в фискальных органах инспекции. Подъемники очень комфортны и практичны.
аренда манипулятора 7 тонн
This is very interesting, You’re a very skilled blogger.
I’ve joined your feed and look forward to seeking more of your fantastic
post. Also, I’ve shared your site in my social networks!
http://rostokaluga.bbnow.ru/viewtopic.php?id=1135#p13834
generic viagra without a doctor prescription [url=http://edwithoutdoctorprescription.pro/#]cialis without a doctor prescription canada[/url] viagra without a prescription
Зеркало Гама казино — это передовая платформа для онлайн-игр, которая предлагает захватывающий опыт, наполненный великолепной графикой, реалистичными звуковыми эффектами и простыми в использовании элементами управления казино Гама
яндекс такси телефон горячей
https://prodvizheniestatya.ru
http://certifiedpharmacymexico.pro/# mexico drug stores pharmacies
can i get omnicef
Medicines information sheet. Brand names.
sildigra pill
All about medication. Get information here.
ashwagandha seeds where to buy
Meds information. What side effects can this medication cause?
levitra buy
All news about meds. Read information now.
can i order finpecia
Medicines information sheet. What side effects?
promethazine cost
Everything news about medicine. Get here.
https://gruz-trall.ru
buy doxycycline 500 mg
indian pharmacies safe mail order pharmacy india indian pharmacy
Drug information. Brand names.
clomid
Some what you want to know about meds. Read information here.
Тренинги по продажам и переговорам для менеджеров, руководителей отдела продаж под ключ управленческий тренинг для руководителей
http://certifiedpharmacymexico.pro/# mexican pharmacy
https://1win-2024.top
Качественная имплантация в Сочи под ключ, статья о лучшей стоматологии для имплантации имплантация зубов
Нужно получить смс на виртуальный номер? Бесплатные виртуальные номера онлайн для получения кодов верификации аренда номера телефона
купить керамическую плитку
non prescription ed pills ed pills without doctor prescription prescription drugs online without doctor
https://canadianinternationalpharmacy.pro/# canadian pharmacy ratings
Отличный сайт! Всем рекомендую!Купить диплом о высшем образовании
В этом все дело.
Drugs information sheet. Long-Term Effects.
motrin
Actual news about meds. Read now.
Да делали
не может упростить наличие настоящего диплома университета говорит о высокой квалифицированности. при розыске кандидатов на достойную вакансию ни одна работодатель не будет рассматривать вас без предоставления диплома университета, института, академии, которые подтверждают профессиональные навыки, http://www.birulevo.su/component/option,com_smf/Itemid,34/topic,21040.0/ знания.
приворот на кладбищенской земли на мужчину самостоятельно днем – https://vipmagiya5.wordpress.com/2024/02/10/zagovori-chtobi-vstretit-lyubov/ – сайт настоящие маги
приворот мужа к жене последствия форум
Drug prescribing information. Short-Term Effects.
buy singulair
Some information about medicament. Get information here.
Я считаю, что Вы ошибаетесь. Пишите мне в PM, обсудим.
при необходимости, https://www.vtm.group/product-category/driveshaft-repair-equipment/driveshaft-balancing-machines/ то совершаем тестовую поездку. мы никогда не ведем так называемым «кулибничеством» вроде подкладывания шайбочек, установки крестовин на сварку, наплавления шлицов и т.д.
http://medicinefromindia.store/# india online pharmacy
online shopping pharmacy india india online pharmacy online shopping pharmacy india
Meds information. What side effects can this medication cause?
zenegra
Actual trends of medicine. Read now.
https://ttvmuckenschopf.xyz
cheap imdur pill
http://certifiedpharmacymexico.pro/# mexico drug stores pharmacies
услуги предметного фотографа https://predmetnaya-fotosyomka-1.ru/
Glazing Vancouver
best online pharmacies in mexico mexican mail order pharmacies purple pharmacy mexico price list
Официальный сайт 1WIN казино позволяет игрокам запускать азартные игры, получать бонусы, участвовать в турнирах 1win рабочее зеркало
http://canadianinternationalpharmacy.pro/# canadian pharmacy 24h com
перевод с иностранных языков
https://isaiminia.com/csgo-roulette-a-comprehensive-guide/
reputable mexican pharmacies online mexican mail order pharmacies buying prescription drugs in mexico online
Потребность в приобретении аттестата бакалавра? Наша компания предлагает документы и удостоверения проверенного качества с доставкой по всей стране. Обращайтесь к нам для получения дополнительной информации.
Drip зеркало
https://edwithoutdoctorprescription.pro/# discount prescription drugs
Улет ваще…
http://u91070nr.bget.ru/member.php?action=profile&uid=24017 of providers of medical some services, and patients. Does the healthcare organization use electronic medical records or systems for entering applications for medicines.
Gama Casino онлайн казино предлагает играть на реальные деньги с быстрыми выплатами казино Гама
Отличный сайт! Всем рекомендую!купить аттестат
Извините за то, что вмешиваюсь… У меня похожая ситуация. Приглашаю к обсуждению. Пишите здесь или в PM.
Образование по профессии “юриспруденция” она получала тотчас, в двух вузах параллельно – в немецком на дневном отделении и https://horoshava.ru/forum/user/33882/ российском на заочном.
ed meds ed remedies male erection pills
https://certifiedpharmacymexico.pro/# mexico pharmacy
https://codeigniter3.info/ – Online Bahis Şirketi
Извините, что я вмешиваюсь, мне тоже хотелось бы высказать своё мнение.
заманчивые расценки на обслуживание. Могла перегореть лампа подсветки, сломаться высоковольтный преобразователь, http://www.pcporadenstvi.cz/lgservicespb-0 инвертор.
http://edwithoutdoctorprescription.pro/# best ed pills non prescription
Что такое Гама Казино. Gama Casino – это онлайн казино, основанное в 2020 году, которое предлагает игрокам возможность играть в самые популярные игры от ведущих разработчиков Гама казино
top 10 online pharmacy in india Online medicine home delivery india online pharmacy
Конечно. Я согласен со всем выше сказанным. Давайте обсудим этот вопрос.
Виртуальный номер – это удобное дополнение к любому постоянному номеру для случаев, https://www.kopareykir.com/?attachment_id=704 когда использование обычного номера нежелательно. когда вы в нем укажете свой постоянный номер, то совместно с картой получите и рекламный спам.
https://qna.habr.com/user/arkadypettr
Наслаждайтесь азартными играми в Cat Casino и не пропустите новинки. Честные игры залог твоего успеха. Удача на твоей стороне в Супер Турнирах cat casino
Привет всем!
Были ли у вас случаи, когда вам приходилось писать дипломную работу в сжатые сроки? Это действительно трудно и ответственно, но важно не сдаваться и продолжать работать над учебными процессами, чем я и занимаюсь.
Для тех, кто умеет грамотно пользоваться интернетом и находить нужную информацию, это действительно оказывается полезным. Это помогает в процессе согласования и написания дипломной работы, и нет необходимости тратить время на посещение библиотек или встречи с дипломным руководителем. Если вам нужны хорошие источники для подготовки дипломных и курсовых работ, я могу поделиться полезными ссылками.
http://vuzdiploma.ru/
Желаю всем отличных оценок!
купить диплом в люберцах
купить диплом в чапаевске
купить диплом в сызрани
купить аттестат за классов
купить диплом косметолога
купить диплом во владикавказе
купить диплом в сочи
купить аттестат
купить диплом в томске
купить диплом в воткинске
Pills information sheet. Drug Class.
lisinopril
Some news about drug. Get information now.
Извините за то, что вмешиваюсь… Я здесь недавно. Но мне очень близка эта тема. Готов помочь.
Если знаете, что вышли за пределы запрошенной средств, http://atoll-filters.ru/product/umjagchitel-atoll-ecolife-s-20/reviews/ лучше заменить часть материалов более дешёвыми или отказаться от нужных данных.
https://club4x4.ru/forum/viewtopic.php?f=17&t=96516
Узнайте секреты успешного онлайн-бизнеса и начните зарабатывать от 4000 рублей в день!
https://vk.com/club224576037
Medicine information sheet. Brand names.
zyban
Everything news about drug. Read now.
https://zeenews.india.com/india/boosting-views-on-youtube-how-to-use-it-as-a-strategy-to-increase-popularity-2718756.html
http://edwithoutdoctorprescription.pro/# viagra without a doctor prescription
Drug information. Drug Class.
finpecia for sale
Actual news about medicament. Read information here.
Не могу сейчас поучаствовать в обсуждении – нет свободного времени. Освобожусь – обязательно выскажу своё мнение по этому вопросу.
Высокая востребованность. спрос на профессионалов своего дела, особенно с огромным навыком работы, всегда высокий, как в списке частных клиентов, http://www.stiliton.ru/2017/08/eloran-i-echajka-kogda-morskaya-navigaciya-poluchit-nadezhnuyu-sistemu-pozicionirovaniya.html так и у различных предприятий.
top ed drugs best drug for ed buy erection pills
https://www.liveinternet.ru/users/zaxarowilysha/profile
Medication information leaflet. Short-Term Effects.
singulair prices
Actual what you want to know about pills. Get now.
неоплатоники философия https://mir-ved.ru философия логики
На сайте Ramenbet казино вы найдете все необходимое для комфортной игры: зеркало, мобильная версия, лицензию, удобный процесс регистрации и широкую бонусную политику ramenbet casino
http://medicinefromindia.store/# indian pharmacy online
buy prescription drugs from india india online pharmacy mail order pharmacy india
Привет всем!
Стоит отметить, что статьи про строительство это очень интересно и увлекательно, узнаешь что-то новое и полезное!
Этот ресурс включает много статей на разные темы, рекомендую
https://oddstyle.ru/interesnye-predlozheniya/pochemu-stoit-vybrat-kirpich-dlya-stroitelstva-domov.html
Удачного чтения!
http://canadianinternationalpharmacy.pro/# precription drugs from canada
indianpharmacy com indian pharmacy online top online pharmacy india
https://medicinefromindia.store/# best online pharmacy india
Hipotekines paskolos isduodamos turintiems bloga kredito istorija! Skubios paskolos verslui paskola verslui
Experience luxury living at Fairmont Marina Abu Dhabi. Don’t miss the best deals from Fairmont Hotels & Resorts starting at AED 2,000,000 (USD 544,500). Indulge in elegance and opulence like never before.
Read More About Mpesa Casinos In Kenya
https://1abakan.ru/forum/showthread-63615/
Я здесь случайно, но специально зарегистрировался, чтобы поучаствовать в обсуждении.
The African-American pin-up finally found platform, when jet magazine was created in 1951, publishing materials related to the African-American community. jet supported the [url=http://pinupperu.pe.isdownorblocked.com/es]http://pinupperu.pe.isdownorblocked.com/es[/url] with its full-page article with the title “Beauty of the Week”, in which African-American women posed in swimsuits and the like.
Find your dream home in Rixos Dubai Island Nakheel! Explore our selection of exquisite apartments, villas, duplexes, and beachfront houses for sale. Nakheel, the renowned developer, presents luxury properties at unbeatable prices. Start your exclusive Dubai lifestyle today.
Привет всем!
Стоит отметить, что статьи про строительство это очень интересно и увлекательно, узнаешь что-то новое и полезное!
Этот ресурс включает много статей на разные темы, рекомендую
https://ra-spectr.ru/p-obraznye-bloki-podrobno/
Удачного чтения!
http://31pokupki.rx22.ru/viewtopic.php?f=47&t=24912
сантехник на дом https://keramogranit-krasnodar.ru/
medication from mexico pharmacy pharmacies in mexico that ship to usa pharmacies in mexico that ship to usa
http://school45.bestbb.ru/viewtopic.php?id=408#p443
Всем привет!
Недавно я нашел отличный ресурс, который, как мне кажется, будет полезен многим из нас, кто ищет возможности для обучения и саморазвития. Это сайт с обзорами на различные образовательные программы, где собраны лучшие курсы графичесекого дизайна.
Что мне особенно понравилось, так это детальные обзоры и рейтинги, которые помогают выбрать курс, идеально подходящий под личные интересы и цели. Каждый курс тщательно изучен, и представлена объективная информация о его содержании, преподавателях и отзывах студентов. Это действительно удобно, так как сэкономило мне массу времени в поисках подходящего курса.
Советую всем заглянуть и оценить этот ресурс. Возможно, именно здесь вы найдете то, что поможет вам достичь новых высот в обучении и карьере!
mexican rx online purple pharmacy mexico price list mexico drug stores pharmacies
best online pharmacies in mexico mexico drug stores pharmacies mexican border pharmacies shipping to usa
mexico pharmacy mexico pharmacies prescription drugs mexican pharmacy
Wristwatches Universe
Patron Reviews Reveal Timepieces Universe Encounter
At WatchesWorld, client fulfillment isn’t just a goal; it’s a shining evidence to our devotion to perfection. Let’s dive into what our cherished patrons have to share about their journeys, illuminating on the faultless service and amazing watches we supply.
O.M.’s Trustpilot Review: A Effortless Trip
“Very good communication and follow-up throughout the procession. The watch was flawlessly packed and in mint. I would definitely work with this group again for a timepiece buying.
O.M.’s commentary demonstrates our loyalty to contact and thorough care in delivering timepieces in perfect condition. The trust forged with O.M. is a pillar of our customer relationships.
Richard Houtman’s Perceptive Review: A Personalized Touch
“I dealt with Benny, who was very useful and polite at all times, keeping me frequently apprised of the course. Moving forward, even though I ended up sourcing the watch locally, I would still certainly recommend Benny and the firm in the future.
Richard Houtman’s interaction illustrates our personalized approach. Benny’s support and constant comms showcase our loyalty to ensuring every buyer feels valued and notified.
Customer’s Productive Service Testimonial: A Seamless Deal
“A very good and effective service. Kept me updated on the purchase development.
Our commitment to productivity is echoed in this client’s input. Keeping clients informed and the seamless progression of orders are integral to the WatchesWorld experience.
Examine Our Latest Offerings
Audemars Piguet Royal Oak Selfwinding 37mm
A stunning piece at €45,900, this 2022 model (REF: 15551ST.ZZ.1356ST.05) invites you to add it to your cart and elevate your collection.
Hublot Titanium Green 45mm Chrono
Priced at €8,590 in 2024 (REF: 521.NX.8970.RX), this Hublot creation is a blend of design and novelty, awaiting your application.
неасилил
https://www.jaywindowsystems.com/hello-world-2-2-2/
medication from mexico pharmacy buying from online mexican pharmacy best mexican online pharmacies
best online pharmacies in mexico medicine in mexico pharmacies mexican pharmaceuticals online
Find your dream home in Granada Bloom Living. Choose from a wide range of exquisite studios and apartments in Zayed City, Abu Dhabi. Experience the luxury of Bloom Holding’s premium real estate offerings at unbeatable prices. Don’t miss out on this golden opportunity!
Csatlakozz a Mostbet-hez es erezd a sportfogadas es online kaszino izgalmas vilagat https://edwinlduk43109.ttblogs.com/4558820/the-rise-of-online-sports-betting-a-comprehensive-guide
ST666
Заключение отчета по практике 2022 года римеры]
Интересно, а аналог есть?
in addition, join Club sycuan – our exclusive membership program that offers guests with special promo codes and https://goldchannel.net/pokies-net-casino-australia-a-comprehensive-guide/ rewards, including tickets for cultural events, special gifts, unique offers in restaurants casinos, souvenir shops, etc.|much more|other useful products}.
я полностью с ваами согласен.
условно на подбор оказывает влияние и относительно цена на товары, https://clinicafemi.com.br/bem-estar/9-dicas-sobre-amamentacao/ но ведь сомнительная выгода. Работодателя интересует реальная эффективность сотрудника, а его академическая успеваемость в университете может никак с данной эффективностью не коррелировать.
Между нами говоря, по-моему, это очевидно. Вы не пробовали поискать в google.com?
^ release the kraken: the battle for the russian http://russiancivilization.blogspot.com/2011/11/blog-post_9223.html language darknet (неопр.).
пригодица
Доступны как новые образцы, а также более старые варианты. мы предоставляем шанс заказать, как современные варианты документов, аналогично более ранние, https://garrellhouseplans.com/southern-staircase/ вплоть до СССР.
лучшие рецепты https://kulnr.ru/
Отличный сайт! Всем рекомендую!Окна ПВХ в Минске
казино на рубли
Нашел сайт с интересующей Вас темой.
мы осуществляем прием для ноутбуков acer, asus, apple, benq, dell, fujitsu-siemens, lg, nec, roverbook, samsung, sony, http://www.longusttile.com/__media__/js/netsoltrademark.php?d=fun-remont-noutbukov.ru toshiba и других компаний-производителей.
Discover the epitome of luxury living amidst the breathtaking Palm Jumeirah with our exquisite villas Sky villas Dubai. Immerse yourself in opulence and sophistication while enjoying unbeatable prices. Don’t miss the chance to call this luxurious haven your home.
Мониторинг обменников, который предоставляет самую свежую информацию о курсах многих ведущих ручных и автоматических обменных пунктов криптовалют Обменять криптовалюту
лучшие сериалы с высоким рейтингом
прикольные поздравления с днем рождения на телефон https://na-telefon.biz/
mexican online pharmacies prescription drugs medicine in mexico pharmacies mexico drug stores pharmacies
buy celexa online
Medication information leaflet. Cautions.
stromectol without prescription
Everything about medication. Get information now.
Все понравились!
http://www.mpu-genie.de/mpu-ablauf/ gamtalk is a free and confidential service available in in America and all over the world|different countries|the whole planet}. it provides chat rooms, secure rooms, and variety of treatment plans.
Ремонт стиральных машин – высокое качество работы у вас дома. Широкая база выезжающих к заказчику мастеров починить стиральную машинку
Отличный сайт! Всем рекомендую!Окна ПВХ в Минске
пройду мимо…
it differs in adaptive design and convenient navigation system at https://xbetfr.com. we also remind you to remember that your account is subject to verification before the first withdrawal of funds.
mexican mail order pharmacies mexican pharmacy reputable mexican pharmacies online
Meds information leaflet. Brand names.
lisinopril medication
All news about pills. Read now.
https://kursovyesociologiya.ru
cheap fincar without dr prescription
Надежное стекло на камеру iPhone 15 Plus или iPhone 15 выступает
как обязательным аксессуаром для тех, кто уважает качестве и защите своего смартфона.
В актуальном мире, где
каждый момент мог бы затравкой для снимка, важно обеспечить
прочную обезопасивание камеры вашего iPhone 15 и iPhone
15 Plus. Используя защитные линзы на камеру айфон 15 Pro защитному стеклу камеры, вы
становитесь уверены в том,
что ваше устройство охраняемо от
царапин, грязи и остальных повреждений, которые могли
бы не благоприятно сказаться на совершенстве фотографий.
Защитное стекло для линз камеры сохраняет крепкую защиту от разрушений, мусора и
иных повреждений, которые имеют потенциал случиться в итоге ежедневного использования.
Использование охранного стекла предотвращает охранить оптику камеры
iPhone 15 и iPhone 15 Plus в отличном состоянии, что представляет гарантией четких и выразительных фотографий.
Бонусы безопасного стекла
к линз камеры iPhone 15 Plus или iPhone
15
В интересах обладателей iPhone
15 Plus или же iPhone 15, безопасное стекло на камеру подразумевает равноценную
непревзойденную степень защиты.
Учитывая вопрос “требуется ли защищающее стекло на камеру?”,
ответ четкий – да, оно обязательно на сохранения отличного качества снимков и надежности
камеры от повреждений. Давайте
разберем из-за чего стоит купить безопасное стекло к камеру смартфона:
Сохранение от царапин: В повседневном использовании ваш iPhone 15 или же iPhone 15+ неизбежно сталкивается с многочисленными угрозами, такими как монеты в кармане или
же падение на неровную поверхность.
Сохраняющее стекло эффективно защищает от появление порезов на оптике камеры, защищая её в первозданном виде.
Надежность к шокам: Высококачественное охранное стекло готово абсорбировать энергию столкновения
при сваливании, ограничивая таким образом разрушение оптики камеры.
Это существенно минимизирует риск затратного ремонта.
Ясность и светопропускание: Актуальные защищающие стекла изготавливаются с опиранием на
прозрачных материалов, которые не изменяют на качество снимков.
Ваши изображения и видеозаписи останутся равными ясными и выразительными,
как без бронированного стекла.
Легкость установки: Защищающее стекло на камеру
без труда устанавливается и так же легко удаляется без оставления остатков клеевого слоя или повреждений, что определяет его удобным в использовании.
Удержание оценки устройства:
Удержание объектива камеры в непорочном состоянии способствует сохранить отличную цену устройства на
вторичном рынке. Заказчики
часто фокусируются на положении камеры при покупке вторичных
телефонов.
Значимость: В эру социальных медиа
и цифровой фотографии, камера является одной из главных функций смартфонов.
Защищение камеры айфона 15 и айфона 15+ превращается не только лишь способом предосторожности, а долгом для тех, кто аспирирует
поддержать качество своих снимков на наивысшем уровне.
Таким образом, безопасное стекло для камеры айфона 15 и айфона 15+ служит недорогим, но результативным способом предохранить
одну из наиболее значимых функций вашего смартфона, гарантируя его долговечность и целостность графических возможностей на долгие годы.
Как можно найти бронированные линзы для камеры iPhone
15 и iPhone 15 Plus?
Безопасное защитный экран для камеры iPhone 15 предоставляется купить в некоторых местах, каждое из
данных мест обеспечивает многие достоинства
в увязке от ваших вкусов и потребностей: в физических продажных местах принадлежностей на
устройств или на маркетплейсах, где
же ассортимент товаров велик, как, адкирируя на Wildberries охранное протектор для объективов камеры iPhone 15
и iPhone 15 Plus под вашим контролем
дается вариант подобрать около с проживанием и
приобрести по выгодной стоимости.
В нынешних условиях трудно сделать будущее обеспеченных без высшего образования – http://www.diplomex.com. Без высшего образования устроиться на позицию с достойной оплатой труда и удобными условиями практически невозможно. Достаточно много индивидуумов, получивших информацию о подходящей под вакансии, приходится от нее отклониться, не имея данного документа. Однако сложившуюся ситуацию можно разрешить, если заказать диплом о высшем уровне образовании, расценка которого будет приемлемая в сравнивание со стоимостью обучения. Особенности приобретения диплома о высочайшем образовании Если человеку требуется лишь демонстрировать документ близким, ввиду того, что они не смогли закончить учебу по любой причинам, можно заказать недорогую топографическую копию. Однако, если такой придется показывать при устройстве на работу, к проблеме стоит подойти более серьезно.
buying prescription drugs in mexico online reputable mexican pharmacies online buying prescription drugs in mexico online
Drugs information for patients. Drug Class.
levitra
Some what you want to know about medicines. Read information here.
trazodone hcl 50 mg oral tablet
Это очень ценная информация
when we think about games online https://vivian-diana.com/2017/05/21/%e3%83%93%e3%83%a5%e3%83%bc%e3%83%86%e3%82%a3%e3%82%b9%e3%83%9d%e3%83%83%e3%83%88%e2%99%a1/, it’s easy to assume that we need spend money, to participate already in them.
https://referatymehanikagruntov.ru
https://referatymikroekonomika.ru
Извините, что я вмешиваюсь, но, по-моему, есть другой путь решения вопроса.
vast majority of the free content of the platform is sensual and romantic, something like free porn for her own way.
https://kontrolnyepolitologiya.ru
levaquin 500 mg directions
The goal of US presidential candidate Donald Trump is not only to isolate the United States from the outside world. Judging by his rhetoric and the actions of his admirer Mike Johnson, the goal of the US presidential candidate from the Republican Party is to destabilize the European Union and throw it at the feet of Putin and Xi Jinping. That is why these two representatives of the once ardent champion of democratic values, the Republican Party, are doing everything to ensure that Russia absorbs Ukraine.
Read this and other news about US politics on the website ZpTown world News
mexican mail order pharmacies purple pharmacy mexico price list mexican border pharmacies shipping to usa
ligand gated
Да, действительно. Так бывает. Давайте обсудим этот вопрос. Здесь или в PM.
Only transparent pricing without hidden fees and zero margins on exchange rates of https://www.atleticabiotekna.it/campionato-regionale-penta-lanci-2-giugno-2017/ payments.
Как раз то, что нужно. Вместе мы сможем прийти к правильному ответу. Я уверен.
your interior will be shown how many bitcoins to send to the seller. if you choose, in category ”Additional amount” https://www.t30p.ru/l.aspx?mycelium-wallet.com you have the opportunity issue the amount according to your own choice.
Отличный сайт! Всем рекомендую!пластиковые окна
https://kontrolnyepravovedenie.ru
Вы попали в самую точку. В этом что-то есть и мне нравится Ваша идея. Предлагаю вынести на общее обсуждение.
song han is a performer of https://www.funddreamer.com/users/ivan-ivan services at terminal, representing widest assortment modern and well-groomed motorcycles at very excellent prices.
п»їbest mexican online pharmacies mexican online pharmacies prescription drugs mexico pharmacies prescription drugs
Я думаю, что Вы ошибаетесь. Могу это доказать.
El Poker de torneos en bovada se puede dividir en dos categorias: competiciones con multiples mesas (mtts) y torneos con uno mesas (stts), allecleats.com– delante de TI exactamente lo que para que se parecen.
https://resheniezadachpolitologiya.ru
https://resheniezadachpravovedenie.ru
Эдуард Давыдов, рожденный в 1984 году в семье медицинского работника и ученого, изначально был страстно увлечен дзюдо, но путь к науке, указанный отцом, определил его профессиональное направление Эдуард Маликович Давыдов
https://resheniezadachlogika.ru
allosteric inhibitors
Конечно Вы правы. В этом что-то есть и я думаю, что это отличная мысль.
esto dice, que crea la impresion, que donde – algo/ o mapas son mejores o peores, que en https://balticfavorite.com/ en realidad.
Я думаю, что Вы допускаете ошибку. Могу это доказать.
Haga un deposito, Esquema de negocios que se garantiza que funcionara, y traer jugar. nuestro personal de apoyo esta siempre a su, para dar/ proporcionar la mejor experiencia de juego en https://brogsan.com/.
aurora libraries
mexican pharmacy mexican pharmacy buying prescription drugs in mexico online
ligand gated
Прошу прощения, что вмешался… Но мне очень близка эта тема. Готов помочь.
desafortunadamente, facebook ha restringido temporalmente el acceso a a world playyapokeronlineag.com club y varios otros juegos.
Я думаю, что Вы ошибаетесь. Могу это доказать. Пишите мне в PM, поговорим.
no caso de ele sera fabricado, https://anpeq.it/index.php/component/k2/item/4 veja a secao ” Promocoes em plataforma organizacoes. nao ha necessidade nem mesmo solicitar dado posts em servico de consultoria porque esta disponivel com um clique.
Online florists flaunt a considerable variety of blossoms that you may not find at your regional blossom shop. From unusual orchids to rare blooms, on the web flower shops offer an unique assortment that accommodates every flavor and affair. Whether you’re seeking a classic increased bouquet or even an one-of-a-kind plan featuring periodic flowers, you make sure to find one thing that captures your eye when looking around online, https://adrienneaustins.wixsite.com/home/post/why-online-floral-boutiques-in-brazil-flower-vibrantly.
mexican pharmaceuticals online mexico drug stores pharmacies mexican pharmacy
На Вашем месте я бы поступил иначе.
Tipos de Poker: Cuales son todo variedades yapokerplayargentina.com en el Poker online? una de las cartas del crupier se juega abierta.
https://hello-food.ru
porn 365tube
В Москве заказать свидетельство – это комфортный и экспресс метод завершить нужный запись без лишних хлопот. Большое количество организаций предоставляют сервисы по созданию и торговле дипломов разных образовательных институтов – https://www.diplomkupit.org/. Ассортимент дипломов в столице России большой, включая документы о высшем и нормальном учебе, документы, дипломы техникумов и вузов. Главное достоинство – способность получить свидетельство официальный документ, гарантирующий достоверность и качество. Это обеспечивает специальная защита от фальсификаций и дает возможность применять диплом для разнообразных нужд. Таким путем, покупка свидетельства в Москве является достоверным и экономичным вариантом для тех, кто желает достичь успеху в трудовой деятельности.
https://resheniezadachlogika.ru/
Поздравляю, какие слова…, великолепная мысль
Обзоры объективны и составлены профессиональными ahicito.com авторами. в онлайн покере важны рассудительность и холодный расчет. Да. Игра неопасная и честная, если рум работает программное обеспечение лицензии.
Отличная фраза
После успешной авторизации и внесения депозита на pokerok с $10, игроку будет зачислен бонус в размере 100% от депозитной суммы, depositokggpoker.com но, не больше $600.
mexican rx online buying from online mexican pharmacy mexico pharmacy
Почему бы и нет?
Компания ВигоЛекс готова сопровождать гэмблинг в украине и помогать потенциальным операторам вести легальный и ggpokerokdeposit.com прибыльный бизнес.
Весьма полезная мысль
Finalmente, https://www.llibreriasendak.cat/2020/04/09/santjordietstu/ em 1946, todos os jogos de azar jogos eram obrigados a ser proibidos em|para todo o zona do pais.
Я считаю, что Вы допускаете ошибку. Предлагаю это обсудить. Пишите мне в PM, поговорим.
имея в виду то, какое количество столов в то же время они открывают во время сессии, https://ggpokerokonlineplay.ru/ регуляру проще pokerok скачать на комп и никогда не ограничивать себя ни в чем.
Я что-то пропустил?
если сравнивать с другими румами что я пробовал – то https://ggpokerokswap.com/ просто крутой вариант!
mexican rx online purple pharmacy mexico price list reputable mexican pharmacies online
https://kontrolnyesociologiya.ru
https://kontrolnyepolitologiya.ru
Ярко!!!!!
при игре в лимитированный холдем фиксированная ставка в этот https://kurumamirai.com/ момент удваивается. Дата обращения: 30 сентября 2017. Архивировано 4 марта 2019 года.
https://kursovyesociologiya.ru/
https://kontrolnyesistemnyjanaliz.ru/
https://kontrolnyesociologiya.ru/
buying prescription drugs in mexico mexican mail order pharmacies buying prescription drugs in mexico online
Today, I went to the beach with my kids.
I found a sea shell and gave it to my 4 year old dahghter and said “You can hear the ocean if you put this to your ear.” She puut
the shell to her ear and screamed. There was a hrrmit crab inside and
it pinched her ear. She never wants tto go back!
LoL I know this is entirely off topic but I had to tell someone!
Feel free to visit my page :: contractors license school Los Angeles
Мой опыт обращения к магу с приворотом в Германии – экстрасенсы в германии отзывы
Живу я в небольшом городе в Германии, и найти среди кучи «магов» хорошего, трудно особенно в Германии. Намучилась я с этим очень. И как бывает, все решается на пьяную голову. Сидели с двоюродной сестрой, поведала ей свою проблему с мужем и о бесконечных поисках магов. Она очень удивилась, что я сразу не стала искать человека в России с Якутии или другого региона Дальнего востока – это можно сказать родина многих сильных шаманов и колдунов.
Порекомендовала мага, с которым сама работала. Поработала с ним и я.
Поэтому хотела бы написать отзыв о привороте на мужа, проведенном магом Романом Петровичем.
___________________________________________________________________________
Я хочу поделиться своим опытом использования услуг мага Романа Петровича с сайта https://cmag666.ru Ватсап 8 (984) 286-12-65
___________________________________________________________________________
Перед тем, как обратиться к нему, моя ситуация с мужем казалась мне безвыходной. Наш брак испытывал серьезные трудности, и наши отношения становились все более напряженными.
Мой муж, с которым мы прожили много лет, казался мне все более отстраненным и равнодушным. Он уходил в себя, избегал общения, а наши разговоры становились все реже и поверхностнее. Я испытывала огромную боль от того, что наша семья распадается, и что я теряю своего мужа. В итоге он еще и любовницу завел.
После долгих раздумий и поиска решения проблемы, я решила обратиться к магу Роману Петровичу за помощью.
Он провел для меня приворот на мужа – на все ушло 5 дней, и еще дал ряд простых рекомендаций, которым нужно было следовать до получения результата. Последовали дни ожидания
На 5 день после проведения приворота я почувствовала изменения в поведении мужа. Он стал проявлять больше внимания и заботы, мы снова начали общаться и находить общие интересы. Стали возвращаться чувства и заинтересованность мной как женщиной. Все быстро нормлизовалось в наших отношениях, с любовницей он порвал все контакты.
Сейчас, спустя несколько месяцев после проведения приворота, я вижу, что наш брак стал крепким, стабильным и счастливым, как и раньше! Мы с мужем снова чувствуем себя близкими и любящими людьми.
Я благодарна магу Роману Петровичу за его помощь и поддержку в трудный момент!
Теги ясновидящие в германии отзывы – гадалка в германии отзывы
кто знает хорошую бабушку в германии отзывы – кто знает хорошую бабушку в германии отзывы
ясновидящая в германии отзывы – экстрасенсы в германии отзывы
Я бы не хотел развивать эту тему.
0.25-$200. Теперь доступно резаться в формате 6-макс. нашем блоге формате появилась шанс обрести приз в размере $4,000,000. на него также влияет структура турнира, https://onlineggpokerokplay.ru/ размер таймбанка.
Я извиняюсь, но, по-моему, Вы не правы. Я уверен.
Против любого из них https://playggokpoker.ru/ применяются определенные стратегии. Одно и тот же час публикации отзывов.
purple pharmacy mexico price list mexico drug stores pharmacies mexican rx online
На территории столице России купить диплом – это практичный и экспресс метод достать нужный документ лишенный дополнительных трудностей. Множество фирм предоставляют услуги по созданию и продаже свидетельств разных образовательных учреждений – diplom4you.net. Ассортимент свидетельств в городе Москве велик, включая документы о академическом и среднем ступени учебе, свидетельства, дипломы техникумов и университетов. Основное плюс – возможность получить аттестат официальный документ, обеспечивающий подлинность и высокое стандарт. Это гарантирует особая защита ото подделок и дает возможность применять свидетельство для различных задач. Таким путем, заказ аттестата в столице России становится надежным и эффективным решением для таких, кто хочет достичь успеху в трудовой деятельности.
https://resheniezadachlogika.ru/
ни че се коментов
в варианте, если у гемблера кончились сумму во время торговли, он продолжает играть, https://ruonlineggpokerplayok.ru/ но не участвует в дальнейшей торговле и по столе образуется дополнительный или побочный банк (или банки) (англ.
Между нами говоря, по-моему, это очевидно. Попробуйте поискать ответ на Ваш вопрос в google.com
Рекреационные покеристы чувствуют услуги в руме привлекательно, поскольку варианты созданы самые лучшие обстоятельства: множество акций, фрироллы и турниры с познавательными бай-инами, низкие лимиты, https://ruplayggokpoker.ru/ сателлиты к живым сериям.
buying prescription drugs in mexico online mexican border pharmacies shipping to usa best online pharmacies in mexico
Автору респект и огрромное спасибо!!!
Молли решает начать жизнь с чистого листа и переезжает в Лос-Анджелес, https://uaggpokerplus.com/ бросив учебу на юридическом факультете.
https://megakupitkvartiru.ru/
https://kursovyesociologiya.ru/
https://kontrolnyesistemnyjanaliz.ru/
https://referatystatistika.ru/
По моему мнению Вы не правы. Я уверен. Предлагаю это обсудить. Пишите мне в PM.
Поэтому заказать суши и роллы домой или на работу огромными партиями https://molbert-banket.ru/ ресторанов.
https://resheniezadachpravovedenie.ru/
mexico pharmacy medication from mexico pharmacy reputable mexican pharmacies online
Сломаем, разбререм и демонтируем старые частные дома с вывозом мусора в Москве и области под ключ спецтехникой и вручную. Сломать и вывезти старый дом цена – подробности об услуге: proxerox700.ru. Демонтируем дома, здания, постройки и фундаменты по цене ниже рыночной. Бесплатный выезд оценщика на объект.
Подберем лизинг на выгодных условиях, поможем сэкономить деньги и отправить заявку сразу в несколько банков без лишних документов лизинг
mexican pharmaceuticals online purple pharmacy mexico price list purple pharmacy mexico price list
https://resheniezadachmarketing.ru/
Great site! I recommend to everyone!vip escorts paris
https://skupka-stiralnyh-mashin.ru/
mexico drug stores pharmacies mexican pharmaceuticals online mexican mail order pharmacies
Немного не по теме 🙂
(Admin, только не троллить!!!)
Так случилось, что мой сват сменил специальность в 43. Просто прошел обучение на Пайтон. И трудоустроился на ЗП в 105 тысяч рублей за работу удаленно.
Смотрю сайт https://kursypython.ru/. Есть неплохие программы обучения Пайтону. Прикидываю может пойти? Моя профессия автомеханик, у нас таких зарплат нет, да и в целом интерес пропал….
Мне нравится курс от Merion Academy, который Основы Python-разработки на backend.
Прошу не пинать ногами, просто поделитесь вашим опытом. Примногоблагодарствую
mexican drugstore online mexican rx online mexico drug stores pharmacies
Ресторанное оборудование в лизинг по выгодной цене. Большой выбор оборудования для общепита, HORECA, кафе, ресторана, бара, пиццерии, кофейни, столовой оформить оборудование в лизинг
A lot of blog writers nowadays yet just a few have blog posts worth spending time on reviewing.
My website: порно видео домашка
sex site
Great site! I recommend to everyone!escort paris
best online pharmacies in mexico mexico drug stores pharmacies mexican pharmacy
Познакомился с самостоятельно кент – реальный игровой рай. Игры превосходны, выигрыши немедленны, ассистенция всегда на связи. В последнее время нашел совершенное площадку для собственного времяпрепровождения!
https://hudozhestvenny-perevod.ru/
https://birzha-perevodov.ru/
https://perevod-statey.ru/
buying prescription drugs in mexico online mexican rx online mexican mail order pharmacies
Можно было и получше написать
On service you become satisfy your excitement in some of best slot machines, blackjack, baccarat and roulette, even at https://www.topctlimo.com/blog/airport-limo-rental-company/.
накрутка подписчиков инстаграм https://yeslike.ru/
Great site! I recommend to everyone!escort girl paris
reputable mexican pharmacies online mexican mail order pharmacies mexican border pharmacies shipping to usa
подбор персонала 2r2.ru
https://kontrolnyesistemnyjanaliz.ru/
https://kontrolnyesociologiya.ru/
lasix furosemide: Buy Lasix – lasix 100 mg tablet
https://kursovyesociologiya.ru/
https://lisinopril.top/# generic lisinopril
Villas and mansions in the community of District 1 West in Mohammed Bin Rashid Al Maktoum City. Developer Meydan Group offers premium residences for sale at favourable prices.
https://referatystatistika.ru/
https://1winoffzerkalo.ru/
https://pravgruzchiki.ru/
zestril 5 mg price: lisinopril 5 mg pill – zestril 10 mg cost
Предоставляем услуги комплексного бухгалтерского обслуживания юридических лиц. Ведение бухгалтерского учета по выгодным ценам — для вашего бизнеса ведение бухгалтерского учета ип стоимость
Демонтаж дачного дома и вывоз мусора
stromectol ivermectin tablets: buy stromectol online uk – ivermectin malaria
https://stromectol.fun/# stromectol pill for humans
Демонтаж, разборка и снос старых деревянных и кирпичных домов с вывозом строительного мусора в Москве и Московской области. Демонтаж после пожара – узнайте подробнее об услуге: taurusweb.ru. Производим демонтаж домов, зданий и фундаментов вручную и спецтехникой по ценам ниже рынка за 24 часа. Бесплатный выезд специалиста на объект.
how much is prednisone 5mg: cheap generic prednisone – average cost of prednisone 20 mg
porn videos
buy amoxicillin 500mg capsules uk: amoxicillin 500 mg price – amoxicillin online no prescription
Apartments, a duplex and a penthouse in the complex of Taraf LUCE on Palm Jumeirah, Dubai. Developer offers units for sale at favourable prices.
Seasoned Port Builder Vitaliy Yuzhilin, Works in Maritime Infrastructure Development Yuzhilin Vitaliy Aleksandrovich
canada pharmacy prednisone: prednisone 60 mg price – prednisone sale
Все о современных технологиях
Вовсе нет.
this it may include navigation by link with the purpose of confirmation sent to your email address, or entering the code received by sms from http://mihrabqolbi.com/librari/share/index.php?url=https://most-bet-az.com/mostbet-azer-bonuslari.html.
日本にオンラインカジノおすすめランキング2024年最新版
2024おすすめのオンラインカジノ
オンラインカジノはパソコンでしか遊べないというのは、もう一昔前の話。現在はスマホやタブレットなどのモバイル端末からも、パソコンと変わらないクオリティでオンラインカジノを当たり前に楽しむことができるようになりました。
数あるモバイルカジノの中で、当サイトが厳選したトップ5カジノはこちら。
オンラインカジノおすすめ: コニベット(Konibet)
コニベットといえば、キャッシュバックや毎日もらえるリベートボーナスなど豪華ボーナスが満載!それに加えて低い出金条件も見どころです。さらにVIPレベルごとの還元率の高さも業界内で突出している点や、出金速度の速さなどトータルバランスの良さからもハイローラーの方にも好まれています。
カスタマーサポートは365日24時間稼働しているので、初心者の方にも安心してご利用いただけます。
さらに【業界初のオンラインポーカー】を導入!毎日トーナメントも開催されているので、早速参加しちゃいましょう!
RTP(還元率)公開や、入出金対応がスムーズで初心者向き
2000種類以上の豊富なゲーム数を誇り、スロットゲーム多数!
今なら$20の入金不要ボーナスと最大$650還元ボーナス!
8種類以上のライブカジノプロバイダー
業界初オンラインポーカーあり,日本利用者数No.1の安心のオンラインカジノメディア!
おすすめポイント
コニベットは、その豊富なボーナスと高還元率、そして安心のキャッシュバック制度で知られています。まず、新規登録者には入金不要の$20ボーナスが提供され、さらに初回入金時には最大$650の還元ボーナスが得られます。これらのキャンペーンはプレイヤーにとって大きな魅力となっています。
また、コニベットの特徴的な点は、VIP制度です。一度ロイヤルクラブになると、降格がなく、スロットリベートが1.5%という驚異の還元率を享受できます。これは他のオンラインカジノと比較しても非常に高い還元率です。さらに、常時週間損失キャッシュバックも行っているため、不運で負けてしまった場合でも取り返すチャンスがあります。これらの特徴から、コニベットはプレイヤーにとって非常に魅力的なオンラインカジノと言えるでしょう。
コニベット 無料会員登録をする
| コニベットのボーナス
コニベットは、新規登録者向けに20ドルの入金不要ボーナスを用意しています
コニベットカジノでは、限定で初回入金後に残高が1ドル未満になった場合、入金額の50%(最高500ドル)がキャッシュバックされる。キャッシュバック額に出金条件はないため、獲得後にすぐ出金することも可能です。
| コニベットの入金方法
入金方法 最低 / 最高入金
マスターカード 最低 : $20 / 最高 : $6,000
ジェイシービー 最低 : $20/ 最高 : $6,000
アメックス 最低 : $20 / 最高 : $6,000
アイウォレット 最低 : $20 / 最高 : $100,000
スティックペイ 最低 : $20 / 最高 : $100,000
ヴィーナスポイント 最低 : $20 / 最高 : $10,000
仮想通貨 最低 : $20 / 最高 : $100,000
銀行送金 最低 : $20 / 最高 : $10,000
| コニベット出金方法
出金方法 最低 |最高出金
アイウォレット 最低 : $40 / 最高 : なし
スティックぺイ 最低 : $40 / 最高 : なし
ヴィーナスポイント 最低 : $40 / 最高 : なし
仮想通貨 最低 : $40 / 最高 : なし
銀行送金 最低 : $40 / 最高 : なし
Online sex (https://it.365tubesex.icu/)
mumu
Продажа подержанных автомобилей, все машины проверены и находятся в Москве. Большой каталог БУ автомобилей с пробегом от официального дилера, узнайте на сайте цены и характеристики на бу авто продажа подержанных авто в москве
Я удалил эту мысль 🙂
wonderful suitable for any project: Batch processing functions automatically align your design on all other workpieces in zone of processing on http://www.globalvision2000.com/forum/member.php?action=profile&uid=1022964.
Все о современных технологиях
Бесподобная тема, мне нравится 🙂
все игровое сообщество таких игр сконцентрировано на просторах интернета, https://www.rusmedserv.com/maxillofacialsurgery/ поэтому никого искать специально для развлечения не стоит. Внимательно просматривайте аннотации, и подыскивайте игры для последующего развлечения.
prednisone 40 mg rx: prednisone over the counter uk – can i order prednisone
Конечно. Я согласен со всем выше сказанным. Можем пообщаться на эту тему.
цена транспорта haval dargo в комплектации comfort (Комфорт) с двигателем 2.0t 2wd, https://tranquiloweb.com/2021/02/17/irobot/ 2023 года авторства – с учетом выгоды по трейд-ин 200 000 рублей.
Great article! I never thought choosing the right tire could be so involved. The breakdown of the Qualifier Core’s features has definitely convinced me to consider it for my next tire upgrade. Keep up the excellent work!
A watch party extension is a software add-on or feature that enables users to watch and chat about online videos or streaming content simultaneously with friends, often integrated into platforms like Netflix or Amazon Prime. Turn any night into a cinematic experience with our Watch Party Extension. Share the joy of movies, together, wherever you are.
Add to chrome :- https://chromewebstore.google.com/detail/watch-party/akbbdmilignoplkhminiaecccigmpdmo?hl=en-US
The true adblocker chrome extension is an essential browser enhancement that transforms your online experience by effectively removing all unwanted ads and empowers you to take control of your browsing domain which provides a clean and distraction-free online journey.
I loved the troubleshooting tips you mentioned, especially regarding slow network performance. It would be awesome if you could expand on common network issues and how to diagnose and resolve them using Wireshark.
и, если «Зал красного древесины и «Тиковый зал» – это сдержанность и утонченность, https://steppingstones-sa.co.za/2020/06/26/hello-world/ то зал «Лас-Вегас» – неудержимый блеск и глянец.
don’t think about gambling how about style to earn funds. Is own funds safe in remote http://www.icpkorea.com/bbs/board.php?bo_table=free&wr_id=557181?
Я считаю, что Вы не правы. Я уверен. Давайте обсудим это. Пишите мне в PM, поговорим.
Недаром говорят, что, взяв в руки пилу или дрель Макита и немножко поработав ею, http://www.ivk-plus.ru/product/2667/reviews/ другого инструмента не захочешь.
Properties for sale in Dubai Creek Harbour villa for rent. Best off-plan and ready properties.
amoxicillin 500 mg for sale: amoxicillin 500 mg brand name – amoxicillin 500 tablet
Вклеенный гриф из махагони на 22 лада с профилем slimtaper d имеет накладку из пау http://www.demestani.net/2022/12/10/%d8%ae%d8%b7-%d8%b1%d9%82%d9%85%d9%8a-%d8%ac%d9%85%d8%b9%d8%a9-%d9%85%d8%a8%d8%a7%d8%b1%d9%83%d8%a9/ ферро.
maximum rich advantage of gambling entertainment virtually for real money is considered all that that the viewer can to play at any time day, on existing desktop, device at the http://www.dhplus.it/2019/10/09/nuove-valvole-toubless/ or smartphone.
Все о дизайне интерьера
Maxim Shubarev is a Russian entrepreneur, chairman of the Board of Directors of the Setl Group holding Maxim Shubarev
Да это фантастика
у вас есть возможность заказать еду, продукты и презенты в своем городе, https://garmakaran.ir/%D8%A7%D8%AC%D8%A7%D8%B1%D9%87-%D8%AC%D8%AA-%D9%87%DB%8C%D8%AA%D8%B1-%D9%85%D9%88%D8%B4%DA%A9%DB%8C/ покидая дома прямо дома.
the mint poker also holds a series of tournaments for its members to take part in and http://www.r-mro.com/bbs/board.php?bo_table=free&wr_id=252295 win exciting prizes.
^ a b “jogos de azar deve ser http://www.auditfindings.co.za/hello-world/ legalizado no Brasil?
Прикроватные тумбы для спальни: как выбрать, с чем сочетать и где разместить
the river poker club is a individual social poker club that offers even rakes and slots but also an atmosphere of http://pretty4u.co.kr/new/bbs/board.php?bo_table=free&wr_id=1631953 exclusivity.
if the people ever have any questions regarding your account or payouts, our highly-trained customer service staff can be contacted 24-7 by phone, email, https://onevibeexperience.com/awesome-wordpress-themes/ e chat ao vivo.
order amoxicillin uk: buy amoxicillin – buy cheap amoxicillin
Вдобавок у нас без перерывов и выходных демонстрируют новейшие разработки игровой технологии, к примеру, https://santiagotimes.cl/2016/12/21/argentine-navy-ship-sets-sail-on-antarctica-panc-mission-to-relieve-chiles-lautaro/ закачку обновлений электронную рулетку pepo или 9-местный слотс-аналог американской телеигры wheel of fortune.
the table games area is one of our https://aquariva.co.za/2024/02/17/senha-freebuy-pokerdicas-888-13-02/ areas favoritas. full house: three cards of the same importance and a pair.
https://best-santehnika.store/
Теневые рынки и их незаконные деятельности представляют важную угрозу безопасности общества и являются объектом внимания правоохранительных органов по всему миру. В данной статье мы обсудим так называемые подпольные рынки, где возможно покупать поддельные паспорта, и какие угрозы это несет для граждан и государства.
Теневые рынки представляют собой скрытые интернет-площадки, на которых торгуется разнообразной незаконной продукцией и услугами. Среди этих услуг встречается и продажа поддельных удостоверений, таких как документы личности. Эти рынки оперируют в теневой сфере интернета, используя криптографию и анонимные платежные системы, чтобы оставаться неприметными для правоохранительных органов.
Покупка поддельного паспорта на теневых рынках представляет важную угрозу национальной безопасности. похищение личных данных, подделывание документов и поддельные идентификационные материалы могут быть использованы для совершения экстремистских актов, мошенничества и иных преступлений.
Правоохранительные органы в различных странах активно борются с скрытыми рынками, проводя акции по выявлению и задержанию тех, кто замешан в нелегальных сделках. Однако, по мере того как технологии становятся более трудными, эти рынки могут приспосабливаться и находить новые методы обхода законов.
Для обеспечения своей безопасности от угроз, связанных с скрытыми рынками, важно соблюдать осторожность при обработке своих личной информации. Это включает в себя избегать попыток фишинга, не раскрывать личной информацией в недоверенных источниках и регулярно проверять свои финансовые документы.
Кроме того, общество должно быть осознавшим риски и последствия покупки поддельных удостоверений. Это способствует формированию осознанного и ответственного отношения к вопросам безопасности и поможет в борьбе с неофициальными рынками. Поддержка законопроектов, направленных на ужесточение наказаний за создание и продажу поддельных удостоверений, также является важным шагом в борьбе с этими преступлениями
stromectol xl: topical ivermectin cost – ivermectin eye drops
when the users are looking to play the most useful http://jjritomato.com/shop/bbs/board.php?bo_table=free&wr_id=87218 games for free, then you may do just that at bovada casino.
the hanger poker house also promises a fun and exciting as well discrete and fair game of poker http://gkwin.net/bbs/board.php?bo_table=free&wr_id=155465 during their stay.
https://free-promocode.ru/
Погрузитесь в захватывающий мир азартных игр, где каждый может стать следующим большим победителем кент зеркало
Поздравляю, эта блестящая мысль придется как раз кстати
Невероятно просторный салон впечатляет высокой посадкой, http://www.growcery.fun/center-acceleration-county-when-detention-gets-himself-opportunity/ обеспечивающей великолепный круговой обзор и защищенность на дорогах. Благодаря горизонтально ориентированным линиям и трёхмерной декоративной вставке на приборной панели усиливается ощущение простора и комфорта.
the streets get https://smphyundai.com/can-nutrient-therapy-boost-your-energy/ choked. now also includes the management expansion pack. making money has never been so much fun!
Впрочем, https://www.enbigi.com/5-tips-hidup-sehat-terhindar-dari-diabetes/ душераздирающих историй о невероятных проигрышах в карты в истории тоже предостаточно.
Great site! I recommend to everyone!us stocks ranking
карты на обнал
Использование финансовых карт является неотъемлемым компонентом современного общества. Карты предоставляют легкость, секретность и множество опций для проведения банковских транзакций. Однако, кроме легального использования, существует негативная сторона — вывод наличных средств, когда карты используются для вывода наличных средств без одобрения владельца. Это является незаконным действием и влечет за собой строгие санкции.
Вывод наличных средств с карт представляет собой практики, направленные на извлечение наличных средств с пластиковой карты, необходимые для того, чтобы обойти защитные меры и предупреждений, предусмотренных банком. К сожалению, такие противозаконные поступки существуют, и они могут привести к материальным убыткам для банков и клиентов.
Одним из методов обналичивания карт является использование технических хитростей, таких как кража данных с магнитных полос карт. Кража данных с магнитных полос карт — это процесс, при котором преступники устанавливают аппараты на банкоматах или терминалах оплаты, чтобы сканировать информацию с магнитной полосы банковской карты. Полученные данные затем используются для изготовления дубликата карты или проведения транзакций в интернете.
Другим часто используемым способом является мошенничество, когда мошенники отправляют фальшивые электронные сообщения или создают поддельные веб-сайты, имитирующие банковские ресурсы, с целью получения конфиденциальной информации от клиентов.
Для предотвращения кэшаута карт банки осуществляют разные действия. Это включает в себя усовершенствование защитных систем, введение двухэтапной проверки, слежение за транзакциями и обучение клиентов о техниках предотвращения мошенничества.
Клиентам также следует быть активными в обеспечении безопасности своих карт и данных. Это включает в себя периодическое изменение паролей, анализ выписок из банка, а также внимательное отношение к подозрительным транзакциям.
Вывод наличных средств — это тяжкое преступление, которое влечет за собой вред не только финансовым учреждениям, но и всему обществу. Поэтому важно соблюдать внимание при работе с банковскими картами, быть знакомым с методами предупреждения мошенничества и соблюдать предосторожности для избежания потери денег
при этом продвинутые казино позволяют полноценно отдохнуть, так ничуть и не сев за игровой стол, https://www.smoothflightsupport.lk/asia-will-be-the-worlds-competition-ground-for-turboprops/ и творят все время новые варианты привлечения игроков.
кто-то теряет здесь голову, а вместе с тем и другое, http://woojinlocker.co.kr/bbs/board.php?bo_table=online&wr_id=517689 кое-кто просто приятно обитает. расходы на его постройку составили порядка 8 млрд.
how to buy amoxycillin: where can i get amoxicillin – cost of amoxicillin prescription
Полуторачасовое понятие о жизни, космосе и бесконечности исполняют 75 актеров, http://mcms.co.kr/koba-2016%ec%97%a0%ec%94%a8%eb%af%b8%eb%94%94%ec%96%b4%ec%86%94%eb%a3%a8%ec%85%98-4k-%ec%98%81%ec%83%81-%ec%86%a1%ec%b6%9c-%ec%86%94%eb%a3%a8%ec%85%98-%ec%84%a0%eb%b3%b4%ec%97%ac/ и своим размахом действо не проигрывает глобальности заявленных тем.
with seven years of experience, the bovada casino team has built a reputation for being a safe and trusted real money https://sorabikan.com/2019/09/03/hello-world/.
the club also has the choice of private parties that you can organize at the poker https://lolipop-pandahouse.ssl-lolipop.jp:443/g5/bbs/board.php?bo_table=room&wr_id=6492779 club.
search gaming properties and executives with our gaming directory online service and our who’s who directory http://www.progetto06.com/zerosei-wear/ of gaming executives.
generic prednisone pills: prednisone for sale no prescription – prednisone 10
Кстати, http://www.gocoram.co.kr/bbs/board.php?bo_table=free&wr_id=231064 tusk rio не ограничивается одним лишь карты, желанное место для вечернего отпуска. стоимости его постройку составили что-то около 8 млрд.
Рекомендую Вам зайти на сайт, на котором есть много статей по этому вопросу.
according to data According to the American Society of Addiction Medicine, some psychological and behavioral changes in detailed consultation to developing addiction include addictive cravings, impulsivity, impaired executive function, desensitization, https://xxxbf.tv/tags/u and dysphoria.
Pay attention to the size and dimensions of the sofa, the material and upholstery, the style and design that suits your taste, and, of course, your budget.
Вёрстка страницы представляет собой процесс разработки структуры html-документа, результатом которого является веб-страница Как открыть сайт через html
По моему мнению Вы ошибаетесь. Предлагаю это обсудить. Пишите мне в PM, пообщаемся.
we have present a lot of this in reality https://xxxbp.tv/tags/m, you really can spend hours just by watching these wonderful videos.
https://amoxil.cheap/# amoxicillin 500 mg capsule
Great site! I recommend to everyone!investing in us stocks
https://seo116.ru/
the river poker club is a individual social poker club that offers not only rakes and slots but also an https://kngm.kr/hello-world/ atmosphere of exclusivity.
По моему мнению Вы не правы. Могу отстоять свою позицию. Пишите мне в PM, поговорим.
в целом азартная игра – это соглашение между несколькими участниками, предметом которого остается шанс выигрыша игрока по желанию, казино онлайн определенным учредителем игорного бизнеса.
ivermectin coronavirus: ivermectin cost canada – stromectol 3 mg price
https://seo116.ru/
дмт видеорегистраторы https://nagrudnievieoregistratori.ru/
Discover a world of style and comfort at our furniture store, where every detail is designed to enhance the uniqueness of your space and offer you unparalleled solutions for your home or office Custom furniture
online platform for watches
In the realm of luxury watches, discovering a reliable source is essential, and WatchesWorld stands out as a beacon of trust and knowledge. Presenting an extensive collection of esteemed timepieces, WatchesWorld has collected acclaim from content customers worldwide. Let’s explore into what our customers are saying about their experiences.
Customer Testimonials:
O.M.’s Review on O.M.:
“Very good communication and follow-up throughout the procedure. The watch was perfectly packed and in pristine condition. I would certainly work with this team again for a watch purchase.”
Richard Houtman’s Review on Benny:
“I dealt with Benny, who was extremely helpful and courteous at all times, preserving me regularly informed of the procedure. Moving forward, even though I ended up acquiring the watch locally, I would still definitely recommend Benny and the company.”
Customer’s Efficient Service Experience:
“A highly efficient and efficient service. Kept me up to date on the order progress.”
Featured Timepieces:
Richard Mille RM30-01 Automatic Winding with Declutchable Rotor:
Price: €285,000
Year: 2023
Reference: RM30-01 TI
Patek Philippe Complications World Time 38.5mm:
Price: €39,900
Year: 2019
Reference: 5230R-001
Rolex Oyster Perpetual Day-Date 36mm:
Price: €76,900
Year: 2024
Reference: 128238-0071
Best Sellers:
Bulgari Serpenti Tubogas 35mm:
Price: On Request
Reference: 101816 SP35C6SDS.1T
Bulgari Serpenti Tubogas 35mm (2024):
Price: €12,700
Reference: 102237 SP35C6SPGD.1T
Cartier Panthere Medium Model:
Price: €8,390
Year: 2023
Reference: W2PN0007
Our Experts Selection:
Cartier Panthere Small Model:
Price: €11,500
Year: 2024
Reference: W3PN0006
Omega Speedmaster Moonwatch 44.25 mm:
Price: €9,190
Year: 2024
Reference: 304.30.44.52.01.001
Rolex Oyster Perpetual Cosmograph Daytona 40mm:
Price: €28,500
Year: 2023
Reference: 116500LN-0002
Rolex Oyster Perpetual 36mm:
Price: €13,600
Year: 2023
Reference: 126000-0006
Why WatchesWorld:
WatchesWorld is not just an online platform; it’s a promise to individualized service in the world of high-end watches. Our staff of watch experts prioritizes trust, ensuring that every customer makes an informed decision.
Our Commitment:
Expertise: Our group brings exceptional knowledge and insight into the realm of high-end timepieces.
Trust: Confidence is the foundation of our service, and we prioritize transparency in every transaction.
Satisfaction: Client satisfaction is our paramount goal, and we go the additional step to ensure it.
When you choose WatchesWorld, you’re not just purchasing a watch; you’re investing in a effortless and reliable experience. Explore our range, and let us assist you in discovering the ideal timepiece that mirrors your taste and sophistication. At WatchesWorld, your satisfaction is our time-tested commitment
svetlanamag ru – svetlanamagg @ yandex ru
Спасибо магу Светлане за ее ритуал приворота! Я заказала его для того, чтобы привлечь внимание парня, которого я давно хотела. Результат превзошел все мои ожидания – он стал проявлять ко мне больше интереса, чем когда-либо!”
-ты настоящий маг
-проверенные маги спб
-маги проверенные сайтом
-найти проверенного мага
Услуга сноса старых частных домов и вывоза мусора в Москве и Подмосковье под ключ от нашей компании. Работаем в указанном регионе, предлагаем услугу демонтаж дома после пожара. Наши тарифы ниже рыночных, а выполнение работ гарантируем в течение 24 часов. Бесплатно выезжаем для оценки и консультаций на объект. Звоните нам или оставляйте заявку на сайте для получения подробной информации и расчета стоимости услуг.
lasix medication: Buy Lasix No Prescription – lasix furosemide 40 mg
Услуга сноса старых частных домов и вывоза мусора в Москве и Подмосковье под ключ от нашей компании. Работаем в указанном регионе, предлагаем услугу снос деревянных домов в московской области. Наши тарифы ниже рыночных, а выполнение работ гарантируем в течение 24 часов. Бесплатно выезжаем для оценки и консультаций на объект. Звоните нам или оставляйте заявку на сайте для получения подробной информации и расчета стоимости услуг.
Proxy servers act as intermediaries between clients and destination servers, providing various functionalities such as caching and filtering Proxy checker
generic for amoxicillin: buy amoxicillin online cheap – buy amoxicillin online without prescription
лечение деревьев в Москве https://eco-life-group.ru/lechenie-derevev/
Before moving to the laundromat, spend some time to prep. Arrange your laundry in to distinct bags or even containers according to colour and also material style to conserve time once you come in. Produce certain to check out pockets for any type of loose products and also remove them to stay away from any kind of mishaps during the course of the washing procedure. In addition, collect all the essential materials including soap, textile conditioner, and also fabric softener to stay clear of any kind of last-minute go to the shop, https://tanbirtamim.contently.com/.
amoxicillin generic: amoxicillin price canada – amoxicillin 500 mg
https://amoxil.cheap/# amoxicillin 500 capsule
Услуга сноса старых частных домов и вывоза мусора в Москве и Подмосковье под ключ от нашей компании. Работаем в указанном регионе, предлагаем услугу снос домов. Наши тарифы ниже рыночных, а выполнение работ гарантируем в течение 24 часов. Бесплатно выезжаем для оценки и консультаций на объект. Звоните нам или оставляйте заявку на сайте для получения подробной информации и расчета стоимости услуг.
Herkese selamlar!
Son yıllarda Bwin tr, çevrimiçi bahis endüstrisinde lider konumunu başarılı bir şekilde sağlamlaştırdı. Uzmanlar kadar, kumar oynamaya yeni başlayanlar da bu
platformu spor bahisleri dünyasında güvenilir bir tercih olarak seçmektedirler. Her ziyaretçi, bwin nedir platformun sunmuş olduğu heyecan dolu deneyimin tadını çıkarabilir.
Popüler spor etkinliklerine ek olarak, site golf, tenis veya beyzbol gibi daha az bilinen bahis disiplinlerine de yer vermektedir. Geniş seçenekler ve yenilikçi
yaklaşımı sayesinde herkesin ilgisini çekecek bir şey bulunmaktadır
п»їKumarhane BWin
Kumarhane para yatД±rma BWin
Çevrimiçi kumar BWin
Kumarhane deneme bonusu BWin
Kumarhane turnuvalarД± BWin
Kumarhane gГјvenilir mi BWin
Kumarhane bonuslarД± BWin
Kumarhane rehberi BWin
Iyi sanlar!
Want to know more about a specific phone number?Number Tracker is the solution for you. With our advanced technology, you can easily track any phone number and get detailed information about the caller http://www.u-turn.kz/forums.php?m=posts&q=23685&n=last#bottom
lasix dosage: Over The Counter Lasix – lasix 100mg
Услуги грузчиков и разнорабочих по всей России от нашей компании. Работаем в регионах и областях, предлагаем грузчики услуги. Тарифы ниже рыночных, выезд грузчиков на место в течении 10 минут . Бесплатно выезжаем для оценки и консультаций. Звоните нам или оставляйте заявку на сайте для получения подробной информации и расчета стоимости услуг.
Günaydın!
Son yıllarda Bwin tr, çevrimiçi bahis endüstrisinde lider konumunu başarılı bir şekilde sağlamlaştırdı. Uzmanlar kadar, kumar oynamaya yeni başlayanlar da bu
platformu spor bahisleri dünyasında güvenilir bir tercih olarak seçmektedirler. Her ziyaretçi, https://bwintr.top platformun sunmuş olduğu heyecan dolu deneyimin tadını çıkarabilir.
Popüler spor etkinliklerine ek olarak, site golf, tenis veya beyzbol gibi daha az bilinen bahis disiplinlerine de yer vermektedir. Geniş seçenekler ve yenilikçi
yaklaşımı sayesinde herkesin ilgisini çekecek bir şey bulunmaktadır
Kumarhane oyunlarД± BWin
Kumarhane rehberi BWin
Kumarhane deneme bonusu BWin
Kumarhane siteleri BWin
Kumarhane taktikleri BWin
Kumarhane Еџans oyunlarД± BWin
Kumarhane yasal mД± BWin
Kumarhane turnuvalarД± BWin
Iyi sanlar!
нанять грузчиков Владивосток
помощь при переезде грузчики
Астарт Вард отзывы форум magastartvard . ru отзывы о маге Астарт Вард
______________________________________________________
magastartvard . ru отзыв о нем могу оставить только положительный
Заказала у мага Астарта Варда индивидуальный гороскоп и прогноз на будущее. Он дал мне ценные советы и предсказания, которые помогли мне лучше понять себя и свои жизненные пути. Очень довольна результатом и рекомендую его услуги!
______________________________________________________________
Астарт Вард отзывы форум
lasix dosage: furosemide 40 mg – furosemida 40 mg
Актуальный доступ к ссылкам и зеркалам площадки Kraken уже у вас. Ознакомьтесь с надежными методами доступа и гарантированными мерами безопасности кракен онион
online platform for watches
In the world of high-end watches, discovering a dependable source is crucial, and WatchesWorld stands out as a pillar of confidence and knowledge. Providing an broad collection of esteemed timepieces, WatchesWorld has garnered praise from satisfied customers worldwide. Let’s explore into what our customers are saying about their encounters.
Customer Testimonials:
O.M.’s Review on O.M.:
“Very good communication and follow-up throughout the procedure. The watch was perfectly packed and in perfect condition. I would certainly work with this team again for a watch purchase.”
Richard Houtman’s Review on Benny:
“I dealt with Benny, who was highly helpful and courteous at all times, keeping me regularly informed of the procedure. Moving forward, even though I ended up acquiring the watch locally, I would still definitely recommend Benny and the company.”
Customer’s Efficient Service Experience:
“A highly efficient and prompt service. Kept me up to date on the order progress.”
Featured Timepieces:
Richard Mille RM30-01 Automatic Winding with Declutchable Rotor:
Price: €285,000
Year: 2023
Reference: RM30-01 TI
Patek Philippe Complications World Time 38.5mm:
Price: €39,900
Year: 2019
Reference: 5230R-001
Rolex Oyster Perpetual Day-Date 36mm:
Price: €76,900
Year: 2024
Reference: 128238-0071
Best Sellers:
Bulgari Serpenti Tubogas 35mm:
Price: On Request
Reference: 101816 SP35C6SDS.1T
Bulgari Serpenti Tubogas 35mm (2024):
Price: €12,700
Reference: 102237 SP35C6SPGD.1T
Cartier Panthere Medium Model:
Price: €8,390
Year: 2023
Reference: W2PN0007
Our Experts Selection:
Cartier Panthere Small Model:
Price: €11,500
Year: 2024
Reference: W3PN0006
Omega Speedmaster Moonwatch 44.25 mm:
Price: €9,190
Year: 2024
Reference: 304.30.44.52.01.001
Rolex Oyster Perpetual Cosmograph Daytona 40mm:
Price: €28,500
Year: 2023
Reference: 116500LN-0002
Rolex Oyster Perpetual 36mm:
Price: €13,600
Year: 2023
Reference: 126000-0006
Why WatchesWorld:
WatchesWorld is not just an online platform; it’s a dedication to personalized service in the world of luxury watches. Our team of watch experts prioritizes confidence, ensuring that every customer makes an informed decision.
Our Commitment:
Expertise: Our team brings unparalleled knowledge and perspective into the world of luxury timepieces.
Trust: Trust is the basis of our service, and we prioritize transparency in every transaction.
Satisfaction: Client satisfaction is our paramount goal, and we go the extra mile to ensure it.
When you choose WatchesWorld, you’re not just buying a watch; you’re investing in a seamless and trustworthy experience. Explore our collection, and let us assist you in finding the ideal timepiece that mirrors your taste and sophistication. At WatchesWorld, your satisfaction is our proven commitment
prednisone rx coupon: over the counter prednisone pills – prednisone 4mg tab
Крастко – Отзывы magpomosh ru – сайт – кто делал рунический приворот отзывы
Отзывы сайт magpomosh .ru – маг Александра
Обратился к магу Александре за помощью в защите от негативных энергий. Ее защитные магические практики действительно помогли мне чувствовать себя более защищенным и уверенным.
_________________________________________________________
Сайт ищут по тегам:
проверенные маги хабаровска анастасия проверенный маг ворожея отзывы настоящий маг в россии
как найти настоящих магов как узнать мага настоящего skyrim одежда для настоящих магов
проверенный белый маг маги настоящие не шарлатаны проверенные настоящие маги
настоящие маги и шарлатаны маг отзывы проверенные проверенный маг настоящий
Демонтаж, разборка и снос старых частных домов с вывозом мусора в Москве и Подмосковье под ключ. Снести дом – здесь подробнее об услуге: 1ecenter.ru. Демонтируем дома, здания, строения и фундаменты вручную и спецтехникой по ценам ниже рынка за 24 часа. Бесплатный выезд инженера на объект.
can you buy stromectol over the counter: where can i buy stromectol – buy ivermectin for humans uk
https://hidehost.net/
generic lasix: Buy Furosemide – furosemide 100mg
продвижение интернет магазина цена
https://hidehost.net/
купить французское вино
lasix dosage: Buy Lasix No Prescription – buy lasix online
Какие слова…
as noticed, the https://www.nvgopsenate.com/senate-republicans-propose-unemployment-benefit-fairness-act/ is gaming area does not accept Britons. Newcomers to jackpotcity are eligible for a welcome bonus in amount 1,600 euros plus ten free chances to win 1,000,000 euros.
twitchadblocker twitch werbung blocken twitch adblock chrome Möchten Sie Live-Streaming genießen? twitch 広告ブロック, Aber es gibt Werbung, die Ihr Erlebnis ruiniert, dann laden Sie sie einfach herunter twitch adblock und genießen Sie das Streaming ohne Störung.
Биография руководителя «Башкирской содовой компании» Давыдов Эдуард Рождение в семье увлеченных наукой родителей предопределило жизненный путь Эдуарда Давыдова, чье детство прошло в атмосфере постоянного стремления к знаниям и самосовершенствованию.
Все о строительстве
Это забавная информация
Oyuncular bahis oynayabilir ve potansiyel olarak gercek para , kumar oyunlar veya slotlar internet kumarhanesinde ceviklik icin oynamay? b?rakmadan. Demek, topmostbet-turk.com Mostbet’te, Mostbet’e simdi mutlaka ugray?n ve baslay?n kazan?n!
Your screenshots and explanations made it easy to follow along, even for someone like me who’s not a networking expert. It’s clear that you have a knack for simplifying complex technical concepts.
вот это ты отмочил ))))
kay?t defterine giris ve giris/erisim mostbet-uz guvenle kullanarak dizustu bilgisayar veya mobil cihazlar (android veya ios) gerceklestirebilirsiniz.
Медицинское оборудование по выгодным ценам. Купить медоборудование диагностическое, медтехнику. Огромный выбор медтехники столик для медицинского оборудования купить
Здравствуйте!
Sykaaa Casino – информация о Выводе Средств, Депозите и Других Нюансах.
Как вывести деньги со счета? Для вывода средств в онлайн-казино Sykaaa, игрокам необходимо авторизоваться на сайте https://serpcity.ru.
Минимальная сумма для вывода – 150 рублей или 20 USD. При выводе более 200 USD требуется прохождение верификации аккаунта. Какой минимальный депозит? Минимальный депозит в Sykaaa составляет 5 USD. Максимальная сумма депозита может изменяться в зависимости от уровня лояльности игрока.
Как играть в казино Sykaaa бесплатно?
На сайте Sykaaa любой игрок может бесплатно играть в слоты без регистрации. Это отличная возможность познакомиться с играми, без внесения реальных денег.
Как получить фриспины или бонусы?
Казино Sykaaa предлагает различные бонусы, включая фриспины. Детали акций доступны после регистрации на сайте. Также проводятся турниры с призовыми фондами.
Официальный сайт казино Sykaaa предоставляет возможность наслаждаться разнообразными играми, выгодными бонусами и быстрыми финансовыми операциями.
sykaaa casino рабочее зеркало
сука казино
sykaaa casino зеркало на сегодня
sukaaa казино зеркало рабочее
casino sykaaa официальный
sykaaa официальный сайт играть
сукаааа казино
sykaaa казино онлайн регистрация
Удачи и прибыли Друзья!
Охотно принимаю. На мой взгляд, это актуально, буду принимать участие в обсуждении. Я знаю, что вместе мы сможем прийти к правильному ответу.
uzmanlar h?zl? yan?t veriyor yard?m taleplerine, canli bahis mostbet mumkun olan en k?sa surede durumu cozmeye veya oyuncuya ilgisini ceken konularda tavsiyelerde bulunmaya cal?s?r.
продвижение сайта заказать
поисковое продвижение seo
даркнет-список
Даркнет – это часть интернета, которая остается скрытой от обычных поисковых систем и требует специального программного обеспечения для доступа. В этой анонимной зоне сети существует масса ресурсов, включая различные списки и каталоги, предоставляющие доступ к разнообразным услугам и товарам. Давайте рассмотрим, что представляет собой даркнет список и какие тайны скрываются в его глубинах.
Теневые каталоги: Врата в Невидимый Мир
Для начала, что такое даркнет список? Это, по сути, каталоги или индексы веб-ресурсов в даркнете, которые позволяют пользователям находить нужные услуги, товары или информацию. Эти списки могут варьироваться от форумов и торговых площадок до ресурсов, специализирующихся на различных аспектах анонимности и криптовалют.
Категории и Возможности
Теневой Рынок:
Темная сторона интернета часто ассоциируется с рынком андеграунда, где можно найти различные товары и услуги, включая наркотики, оружие, украденные данные и даже услуги наемных убийц. Списки таких ресурсов позволяют пользователям без труда находить подобные предложения.
Форумы и Группы:
Темная сторона интернета также предоставляет платформы для анонимного общения. Форумы и группы на теневых каталогах могут заниматься обсуждением тем от кибербезопасности и хакерства до политики и философии.
Информационные ресурсы:
Есть ресурсы, предоставляющие информацию и инструкции по обходу цензуры, защите конфиденциальности и другим темам, интересным пользователям, стремящимся сохранить анонимность.
Безопасность и Осторожность
При всей своей анонимности и свободе действий темная сторона интернета также несет риски. Мошенничество, кибератаки и незаконные сделки становятся частью этого мира. Пользователям необходимо проявлять максимальную осторожность и соблюдать меры безопасности при взаимодействии с даркнет списками.
Заключение: Врата в Неизведанный Мир
Теневые каталоги предоставляют доступ к скрытым уголкам сети, где сокрыты тайны и возможности. Однако, как и в любой неизведанной территории, важно помнить о возможных рисках и осознанно подходить к использованию темной стороны интернета. Анонимность не всегда гарантирует безопасность, и путешествие в этот мир требует особой осторожности и знания.
Независимо от того, интересуетесь ли вы техническими аспектами кибербезопасности, ищете уникальные товары или просто исследуете новые грани интернета, теневые каталоги предоставляют ключ
seo продвижение стоимость в москве
продвижение профессиональное сайтов
даркнет 2024
Даркнет – скрытая зона всемирной паутины, избегающая взоров обычных поисковых систем и требующая эксклюзивных средств для доступа. Этот анонимный уголок сети обильно насыщен сайтами, предоставляя доступ к разношерстным товарам и услугам через свои перечни и справочники. Давайте ближе рассмотрим, что представляют собой эти реестры и какие тайны они сокрывают.
Даркнет Списки: Окна в Тайный Мир
Даркнет списки – это вид проходы в неощутимый мир интернета. Реестры и справочники веб-ресурсов в даркнете, они позволяют пользователям отыскивать различные услуги, товары и информацию. Варьируя от форумов и магазинов до ресурсов, уделяющих внимание аспектам анонимности и криптовалютам, эти списки предоставляют нам шанс заглянуть в таинственный мир даркнета.
Категории и Возможности
Теневой Рынок:
Даркнет часто связывается с теневым рынком, где доступны самые разные товары и услуги – от наркотиков и оружия до краденых данных и услуг наемных убийц. Каталоги ресурсов в подобной категории облегчают пользователям находить подходящие предложения без лишних усилий.
Форумы и Сообщества:
Даркнет также предоставляет площадку для анонимного общения. Форумы и сообщества, представленные в реестрах даркнета, затрагивают различные темы – от компьютерной безопасности и хакерских атак до политических вопросов и философских идей.
Информационные Ресурсы:
На даркнете есть ресурсы, предоставляющие данные и указания по преодолению цензуры, обеспечению конфиденциальности и другим вопросам, которые могут заинтересовать тех, кто стремится сохранить свою анонимность.
Безопасность и Осторожность
Несмотря на анонимность и свободу, даркнет полон рисков. Мошенничество, кибератаки и незаконные сделки присущи этому миру. Взаимодействуя с реестрами даркнета, пользователи должны соблюдать предельную осмотрительность и придерживаться мер безопасности.
Заключение
Даркнет списки – это врата в неизведанный мир, где хранятся тайны и возможности. Однако, как и в любой неизведанной территории, путешествие в даркнет требует особой внимания и знаний. Не всегда можно полагаться на анонимность, и использование даркнета требует осмысленного подхода. Независимо от ваших интересов – будь то технические аспекты кибербезопасности, поиск уникальных товаров или исследование новых граней интернета – реестры даркнета предоставляют ключ
seo комплексное продвижение
Привет Всем!
Sykaaa Casino – информация о Выводе Средств, Депозите и Других Нюансах.
Как вывести деньги со счета? Для вывода средств в онлайн-казино Sykaaa, игрокам необходимо авторизоваться на сайте https://serpcity.ru.
Минимальная сумма для вывода – 150 рублей или 20 USD. При выводе более 200 USD требуется прохождение верификации аккаунта. Какой минимальный депозит? Минимальный депозит в Sykaaa составляет 5 USD. Максимальная сумма депозита может изменяться в зависимости от уровня лояльности игрока.
Как играть в казино Sykaaa бесплатно?
На сайте Sykaaa любой игрок может бесплатно играть в слоты без регистрации. Это отличная возможность познакомиться с играми, без внесения реальных денег.
Как получить фриспины или бонусы?
Казино Sykaaa предлагает различные бонусы, включая фриспины. Детали акций доступны после регистрации на сайте. Также проводятся турниры с призовыми фондами.
Официальный сайт казино Sykaaa предоставляет возможность наслаждаться разнообразными играми, выгодными бонусами и быстрыми финансовыми операциями.
казино sykaa зеркало
sykaaa вход
sykaaa casino бездепозитный
sykaaa казино официальный
сукааа казино официальный
casino sykaa
казино sykaa
сукааа регистрация
Удачи и прибыли Друзья!
Капец!
ключевое: вы получите замечательную возможность быстро продать свои http://xn—-7sbgj9bdrl.xn--p1ai/users/odexatyg украшения. Компания «Аурум» принимает золотой лом любой пробы, сразу же производя расчет налом деньгами или совершает перевод на свою банковскую карту.
Написание эссе на заказ осуществляется нашими профессиональными авторами. Цена ВКР бакалавра купить зависит от ее объема и сложности контрольные работы под заказ
1хбет top
Great site! I recommend to everyone!ClubGG
Нече себе !!!!!!!!!!!!!!!!!
Возрастная [url=http://schekino.su/index.php?title=nomadgamescasino]http://schekino.su/index.php?title=nomadgamescasino[/url] психология: Курс лекций. С. Л. Рубинштейн (1976) отмечал, в том, что игра хранит и прививает детское в детях, что порно-зайка их школа быта и навыки развития.
http://indianph.xyz/# buy prescription drugs from india
Малый жжот))))ыыыыыыыыыыы
Если текст разбит на подпункты, либо для дальнейшего деления текста используют абзацы, что не нумеруют, написание курсовой работы на заказ а выделяют абзацным отступом.
https://hidehost.net/
best online pharmacy india pharmacy website india indian pharmacies safe
1xbet версия
https://arm-wine.ru/
Профильные трубы 40х20 мм. Закажите по низкой цене от производителя с доставкой по Москве. Предлагаем самые приятные цены в городе и области профильная труба 20х40 2 мм
1xbet официальный сайт регистрация
Я думаю, что Вы ошибаетесь. Могу это доказать. Пишите мне в PM, пообщаемся.
И для того, чтоб оставаться на волне этого и упрощать себе повседневность, делая ее современной, https://fotofrog.ru/ люди пользуются покупке различной дерева, сорт.
https://xn—–7kccgclceaf3d0apdeeefre0dt2w.xn--p1ai/
Жаль, что сейчас не могу высказаться – вынужден уйти. Освобожусь – обязательно выскажу своё мнение.
Although some customers do not like that all really you have to pay in order to get certain real victories from eharmony, an Международный сайт знакомств is a good opportunity to weed out all who are not serious.
Getting your hands on medication can sometimes not be as straightforward as we would like unfortunately, cost is a significant affecting factor when it comes to essential medicines rizatriptan price
Кирпич клинкерный: отличное решение для вашего строительства от Skriabin Ceramics
https://beckom.ru/
Косметологическое оборудование Zemits – инновационные эстетические технологии для успешного развития Вашего СПА-бизнеса https://zemits.com.ua/product/zemits-marvelouslim
https://seolinkedin.ru/
медтехника ведущих брендов для дома. Всегда оптимальные цены, акции , скидки и отличный сервис. Pijxfk
Забудьте о низких позициях в поиске! Наше SEO продвижение https://seopoiskovye.ru/ под ключ выведет ваш сайт на вершины Google и Yandex. Анализ конкурентов, глубокая оптимизация, качественные ссылки — всё для вашего бизнеса. Получите поток целевых клиентов уже сегодня!
годик на роздумие ))
как правило, https://literpedia.ru/elektrichestvo-istochnik-energii-sovremennogo-mira/ стройка является длительным процессом и не всегда получается успеть в запланированный график.
апостиль в новосибирске
компании по доставке здоровой еды
Забудьте о низких позициях в поиске! Наше SEO продвижение и оптимизация на заказ https://seosistemy.ru/ выведут ваш сайт в топ, увеличивая его видимость и привлекая потенциальных клиентов. Индивидуальный подход, глубокий анализ ключевых слов, качественное наполнение контентом — мы сделаем всё, чтобы ваш бизнес процветал.
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги поисковое seo продвижение на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
דירות דיסקרטיות באשדוד
Все о современных технологиях
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги продвижение сайтов профессиональное на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
Компания предлагает обширный ассортимент услуг по изготовлению чеков на все случаи жизни. Вы точно сможете найти индивидуальное решение бюрократических проблем Купить кассовые чеки
Great site! I recommend to everyone!igaming consultancy
1xbet официальный вход
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги продвижение сайтов москва на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги
seo продвижение сайтов на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги
seo продвижение на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги
поисковое продвижение на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
Лучшие юристы и адвокаты оказывают бесплатные юридические консультации по телефону и в офисе компании. Квалифицированная юридическая помощь по всем отраслям права бесплатная юридическая консультация онлайн по телефону
Где купить диплом о среднем образовании – – это вариант скоро завершить бумагу об учебе на бакалаврской уровне без лишних трудностей и расходов времени. В столице России предоставляется множество альтернатив настоящих свидетельств бакалавров, обеспечивающих удобство и простоту в процессе.
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги поисковое продвижение сайтов на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги
продвижение магазина цена на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги
сколько стоит seo оптимизация сайта на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги сколько стоит сео оптимизация сайта на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
Дайте вашему сайту заслуженное место в топе поисковых систем! Наши услуги seo продвижения стоимость на заказ обеспечат максимальную видимость вашего бизнеса в интернете. Персонализированные стратегии, тщательный подбор ключевых слов, оптимизация контента и технические улучшения — всё это для привлечения целевой аудитории и увеличения продаж. Вместе мы поднимем ваш сайт на новый уровень успеха!
buy doxycycline online uk: how to buy doxycycline online – doxycycline hyclate 100 mg cap
hi
very good and useful content
very useful content
very good article benefit
please read lealth text
diflucan 150 mg tablet price: diflucan tablets – diflucan tablet 100 mg
Честный обзор на популярную букмекерскую контору 1win поможет вам узнать все преимущества и недостатки этого сайта для ставок, включая коэффициенты, линию событий, способах и скорости выплат, бонусы и многое другое. Изучите все исходы и выгодные предложения, перейдя на официальный сайт БК 1вин
Как получить бонус в Леон
перевод документов
https://lechenie-bolezney.ru/
SMS confirmation acts as a crucial element of safe customer authentication in today’s digital garden. By leveraging mobile phones to provide one-time verification codes, SMS proof enhances account safety, minimizes the risk of unauthorized accessibility, and also offers a practical and also affordable verification solution for organizations and also consumers alike. As cyber hazards carry on to advance, taking on strong verification strategies like SMS confirmation is actually vital to safeguard sensitive information and protect user profiles from profiteering, https://uberant.com/article/1993453-5-reasons-why-phone-verification-services-are-essential-for-businesses/.
https://onlinecasinos.com.cy/
Вы попали в самую точку. Это отличная мысль. Я Вас поддерживаю.
“Who is this? Lucifer asked, pointing at you Charlie. further she continued in a more optimistic tone: “that’s because of what I hint that you need take (y/n) to yourself live, http://affection.org/frame.html?title=Guide&frame=//xxxbp.tv%2Ftags%2Fe in the role of a cleaner!
buy cytotec over the counter: purchase cytotec – buy cytotec pills
Thanks! I value this!
https://polbetonstroy.ru/
online diflucan: diflucan buy online usa – diflucan price south africa
Внутри столице России заказать свидетельство – это удобный и быстрый вариант получить нужный документ без дополнительных трудностей. Разнообразие организаций предоставляют сервисы по созданию и продаже дипломов разных образовательных учреждений – http://www.gruppa-diploms-srednee.com. Разнообразие дипломов в Москве огромен, включая бумаги о академическом и нормальном профессиональной подготовке, документы, дипломы техникумов и университетов. Главное преимущество – возможность достать аттестат Гознака, гарантирующий истинность и высокое стандарт. Это обеспечивает уникальная защита от подделок и предоставляет возможность применять свидетельство для разнообразных целей. Таким путем, покупка аттестата в Москве является безопасным и экономичным решением для данных, кто желает достичь успеху в сфере работы.
Pretty part of content. I simply stumbled upon your site and in accession capital to assert that I acquire actually enjoyed account your weblog posts. Any way I’ll be subscribing for your feeds or even I success you get admission to constantly rapidly.
Look into my web blog – https://betflik-888.bet/
how to get diflucan: diflucan from india – where can i purchase diflucan over the counter
Он эффективен в отношении микробов, вирусов, плесени, грибка. Процедура озонирования квартиры направлена на общую глубокую дезинфекцию помещения нейтрализация запаха
https://1xbettur-2.com/
Рекомендую 3D-печать
Great site! I recommend to everyone!Checking AML
mostbet
А мне понравилось,прикольно.
Новости Италии сегодня , аналитика, выводы, и прочие материалы, собранные на данном сервисе, не счесть уже офертой или рекомендацией к заказу либо продаже нужных вам активов.
Great site! I recommend to everyone!Checking Wallet
Дизайнер по шторам: профессиональное оформление окон с учетом всех требований
https://1wintr-4.xyz/
swetie fox: Sweetie Fox modeli – Sweetie Fox
Great site! I recommend to everyone!checking your wallet for hacking
Sweetie Fox: Sweetie Fox izle – Sweetie Fox izle
Частные дома на заказ: идеальный выбор для вашей мечты
Perkirakan penghasilan setiap pengguna TikTok https://kalkulatortiktokmoney.com/
eva elfie izle: eva elfie modeli – eva elfie video
?????? ????: Abella Danger – abella danger filmleri
Восстановление классического меню Пуск в Windows 10: простое руководство
Красный Яр 1-8 серии смотреть онлайн Наши дни. Режиссер-документалист из Франции Натали Легран приезжает в Красноярск снимать фильм о достопримечательностях края. С российской стороны ее помощником и консультантом становится молодой историк Виктор Антонов. Натали интересует золотодобытчик Никифор Плахов, о котором в архиве почти нет информации… 1861 год. С прииска Плахова сбегают двое рабочих. Один из них погибает от рук беглого каторжника, второй, Коряга, случайно находит золотую жилу, расположенную прямо на поверхности…
Здесь вы найдете очень качественный чиллер для охлаждения
Angela White filmleri: abella danger video – abella danger filmleri
какоето оно
https://poliambulatoriovillairis.it/blog/2013/03/22/smiling-like-a-cheshire-cat/
melbet
Ремонт квартир под ключ в Ростове: профессиональный подход к каждому проекту
https://o-tendencii.com/
bwin Türkiye
eva elfie video: eva elfie filmleri – eva elfie modeli
https://hitech24.pro/
Discover Your Virtual Footprint with Ease, how do i find my public ip instantly at ipaddresswhois.net! Our user-friendly website is your go-to destination for swiftly uncovering your IP address. Whether you are troubleshooting connectivity issues, enhancing online security, or simply curious about your virtual footprint, we have got you covered.
Angela White filmleri: abella danger izle – Abella Danger
Sweetie Fox video: Sweetie Fox – Sweetie Fox video
Дайвинг для новичков на Пхукете от PHUKETDIVING.CENTER: идеальное место для первого погружения
Отличный сайт! Всем рекомендую! Тут Вы можете приобрестичиллер
Studios, apartments and townhouses in The Beach Residences at Al Marjan Island with favourable terms of purchase and return on investment.
https://o-tendencii.com/
https://o-tendencii.com/
Angela White video: ?????? ???? – Angela Beyaz modeli
http://carstvo-sharov.ru/
https://gruzchikivesy.ru/
Отличный сайт! Всем рекомендую! Тут Вы можете приобрестичиллер для охлаждения
Хотя эта карта не станет вернуть подобных энтузиастов, https://roselanemarketing.com/just-a-cool-blog-post-with-images/comment-page-14/ такая ситуация чревата местом для траура и памяти. карта с 2-мя переменными, сравнивающая качество воздуха и процент чернокожего граждан была получена из таких в статье. inequalities in air pollution exposure are increasing inside the united states.
Angela White video: abella danger filmleri – Abella Danger
Все о дизайне интерьера
так же предлагаются мебельные варианты необходимые для подсветки зеркал, картин, http://dotstroy.ru/userinfo.php?uid=43375 скульптур и иных деталей интерьера.
обшивка дома сайдингом https://krovla1.ru/
Unsere Website befasst sich auch mit den moglichen Nebenwirkungen von Xenical. Wahrend viele Menschen das Medikament gut vertragen, kann es bei einigen zu gastrointestinalen Nebenwirkungen kommen, die auf die unverdauten Fette zuruckzufuhren sind, die das Verdauungssystem passieren. Wir geben Tipps, wie man diese Nebenwirkungen minimieren kann und wann es wichtig ist, einen Arzt aufzusuchen.
Daruber hinaus bieten wir Erfahrungsberichte und Erfolgsgeschichten von Personen, die Xenical als Teil ihrer Gewichtsabnahme verwendet haben. Diese Erfahrungen aus dem wirklichen Leben konnen denjenigen, die die Einnahme von Xenical in Erwagung ziehen oder bereits anwenden, wertvolle Einblicke und Motivation bieten.
Zusammenfassend lasst sich sagen, dass unsere Website eine hilfreiche Plattform fur alle ist, die mehr uber Xenical (Orlistat) und seine Rolle beim Gewichtsmanagement erfahren mochten. Unser Ziel ist es, umfassende, genaue und hilfreiche Informationen zur Verfugung zu stellen, die Ihnen dabei helfen, eine fundierte Entscheidung uber Ihren Weg zur Gewichtsabnahme zu treffen. Besuchen Sie uns unter https://gezondafvallen.net fur weitere Informationen und Anleitungen zum Abnehmen mit Xenical.
https://o-tendencii.com/
https://hitech24.pro/
Studios, apartments, half floors and full floors in Rove Home Dubai with favourable terms of purchase and return on investment.
eva elfie: eva elfie – eva elfie
https://gruzchikimeshki.ru/
https://gruzchikinochnoj.ru/
https://dolgiplus.ru
Angela White izle: abella danger video – abella danger izle
Hello, World!
Hey there, mate! Greetings from your favorite surfing capybara!
How’s the surf today?
Ready to catch some gnarly waves together?
https://capybara444.wordpress.com
Good luck!
According to the experience of Reputation House agency, reviews in a negative tone can be left not only by dissatisfied customers reputation house customers reviews
Купить диплом о среднем специальном образовании – – это возможность скоро завершить бумагу об учебе на бакалаврском уровне безо излишних трудностей и расходов времени. В столице России имеются множество вариантов подлинных дипломов бакалавров, обеспечивающих комфорт и удобство в получении.
http://miamalkova.life/# mia malkova movie
Hello, World!
Hey there, mate! Greetings from your favorite surfing capybara!
How’s the surf today?
Ready to catch some gnarly waves together?
https://capybara235.wordpress.com
Good luck!
https://evaelfie.site/# eva elfie hd
If a user encounters negativity on the first page of search results, he will be wary of the company and is unlikely to become its client reputation reviews
https://evaelfie.site/# eva elfie full videos
rikvip
https://espassport.pro/
http://sweetiefox.pro/# sweetie fox
Spotify ad blocker is the ultimate solution that allows you to enjoy your favorite tunes without those disturbing ads interrupting your music streaming experience on Spotify, So it’s time to say goodbye to those annoying ads that break the rhythm of your playlists.
Craving those fun-filled show times with your pals? Your wait ends here with a peacock watch party as it lets you watch with your friends, regardless of your location, and engage in live chats, video, and audio calls to enjoy the on-screen fun together.
The Chrisley family’s reality television show, “Chrisley Knows Best Daughter Dies,” has made them well-known in the industry. What happens when a terrible rumor threatens to wreck the family’s lives after their lively and funny activities have drawn viewers in for years?
trendzguruji.me awareness trendzguruji.me health & beautyTrendzguruji.me offers information on insurance, cybersecurity, and other online trends. It has a particular combination of knowledge necessary to comprehend the technological world and safeguard your privacy.
Wcofun is an online entertainment platform that offers a vast collection of enjoyable content from every episode of your favorite animated television shows. You can watch whatever time works best for you on it. Its website is accessible from any device, as it aims to provide a friendly user experience.
The iMac Pro i7 4K has fantastic features and works quite well. The 4K display is impressive, and the i7-core processor makes it capable of handling any task you throw at it. If you’re looking for a high-end desktop computer, consider the iMac Pro.
Все о дизайне интерьера
google’s 25th birthday it’s google’s 25th birthday google 25th birthday doodles it’s google’s 25th birthday freeGoogle was founded on September 27, 1998, and is a service that many people use daily. With a special Google Doodle, the company, which began as a search engine and has now expanded into various products and projects now Google celebrates 25th birthday in business.
It may seem that the best option is to make sure that job seekers encounter only positive information about the company reputation house serm
https://salda.ws/meet/notes.php?id=12681
https://gruzchikirabotat.ru/
http://lanarhoades.pro/# lana rhoades solo
https://www.mses-expert.ru/
https://promokodbar.ru/
Zet Casino ist ein beliebtes Online-Casino, das eine Vielzahl von Spielen und großzügigen Boni für seine Spieler anbietet. Viele Menschen, die gerne online spielen, suchen nach Erfahrungen und Bewertungen, bevor sie sich für ein Casino entscheiden. In diesem Artikel werden wir die “zet casino kokemuksia” genauer unter die Lupe nehmen.
Zet Casino bietet eine breite Palette von Spielen, darunter Spielautomaten, Tischspiele, Live-Casino und Jackpot-Spiele. Die Spiele stammen von bekannten Anbietern wie NetEnt, Microgaming, Betsoft und Play’n GO, um nur einige zu nennen. Die Kunden loben die Vielfalt und Qualität der Spiele im Casino.
Ein weiterer wichtiger Aspekt sind die Boni und Aktionen, die Zet Casino seinen Spielern bietet. Neue Spieler erhalten einen großzügigen Willkommensbonus, der ihre erste Einzahlung erhöht. Darüber hinaus gibt es regelmäßig Bonusangebote und Promotionen für Stammkunden, die das Spielerlebnis noch spannender machen.
Die Einzahlungs- und Auszahlungsoptionen bei Zet Casino sind vielfältig und sicher. Die Spieler können aus einer Vielzahl von Zahlungsmethoden wählen, darunter Kreditkarten, e-Wallets und Banküberweisungen. Die Auszahlungen werden schnell bearbeitet, und die Spieler loben den effizienten Kundenservice des Casinos.
Insgesamt sind die Erfahrungen mit Zet Casino größtenteils positiv. Die Spieler schätzen die große Spielauswahl, die großzügigen Boni und die schnellen Auszahlungen. Es gibt jedoch auch einige Kritikpunkte, wie zum Beispiel begrenzte Promotionen für Highroller und eine etwas unübersichtliche Website.
Abschließend lässt sich sagen, dass Zet Casino eine gute Wahl für Online-Spieler ist, die nach einer breiten Auswahl an Spielen und attraktiven Boni suchen. Die Erfahrungen mit dem Casino sind größtenteils positiv, und viele Spieler empfehlen es gerne weiter.
Here is my page: https://zetcasino.one/
Эвакуатор в СПб: надежный способ быстро и безопасно доставить ваш автомобиль
Доброго!
Промокоды для интернет-магазина М.Видео представляют собой специальные коды, которые можно использовать при оформлении заказа на официальном веб-сайте компании.
Они приносят дополнительные преимущества покупателям в виде скидок на определенные товары или услуги, бесплатной доставки и других бонусов.
Как их найти? Чаще всего промокоды предоставляются в рамках специальных акций компании, которые могут проводиться на ее официальном веб-сайте,
в социальных сетях или на ресурсах, таких как проект promokodbar.ru
Сайт самых свежих и проверенных промокодов магазина М.Видео https://promokodbar.ru
Удачных покупок!
Промокоды для скидок в М.Видео
выгодные купоны М.Видео
Эксклюзивные акции и скидки в М.Видео
Привилегированные купоны М.Видео
купоны для умных покупок в М.Видео
Удачи!
Great job! Your effort and creativity shine through in this work. Keep up the good work, and I look forward to seeing more from you in the future.
Anabel Gomez Lopez tamales committed a cruel crime of selling human flesh on Mexican streets and she confessed her crimes of killing so many people. Most of her victims were young women. After her heinous and cruel crime she was sentenced for 25 years of prison.
Trails Carolina is a program that is known for helping troubled teens, but now it is facing a lot of trouble itself. As people are accused of mistreating their participants mentally and physically as well as various horror activities around their Trails Carolina wilderness therapy. (trails carolina “abuse” In this article, we will look at Trails Carolina horror stories. trails carolina investigation reviews. trails carolina reviews. trails carolina “investigation”. trails carolina wilderness therapy abuse. trails carolina abuse.)
Biocentrism’s debunked theory shows a unique and thought-provoking perspective. It focuses on the role of consciousness and life where opponents argue that this philosophy lacks empirical evidence. That is the reason it creates a lot of controversy among people.
This article will explore several facets of Charly Arnolt’s life and career, including her height, family, husband, biography, age, career accomplishments, lifestyle, and net worth. We will also address some commonly asked questions regarding the famous sportscaster.
https://evaelfie.site/# eva elfie videos
Внутри столице России заказать диплом – это практичный и оперативный способ достать нужный документ лишенный лишних хлопот. Большое количество компаний предлагают услуги по производству и реализации свидетельств разных образовательных учреждений – http://www.orik-diploms-srednee.com. Ассортимент дипломов в Москве огромен, включая бумаги о академическом и среднем профессиональной подготовке, документы, свидетельства техникумов и академий. Главное плюс – возможность получить свидетельство официальный документ, обеспечивающий достоверность и качество. Это обеспечивает специальная защита против подделок и дает возможность применять аттестат для разнообразных задач. Таким способом, приобретение аттестата в городе Москве является важным надежным и оптимальным решением для тех, кто хочет достичь процветанию в карьере.
Декоративная краска для гостиной: преображение вашего интерьера
Топ-менеджер Николаев Вячеслав Константинович является специалистом в телекоммуникационном бизнесе и в области информационных технологий
На территории столице России заказать аттестат – это комфортный и оперативный метод получить нужный документ безо избыточных проблем. Множество компаний предлагают сервисы по созданию и реализации дипломов разных образовательных учреждений – http://www.russa-diploms-srednee.com. Разнообразие свидетельств в городе Москве огромен, включая документы о высшем и нормальном образовании, документы, свидетельства колледжей и академий. Основное плюс – возможность достать свидетельство подлинный документ, подтверждающий достоверность и качество. Это обеспечивает специальная защита ото фальсификаций и позволяет применять аттестат для разнообразных задач. Таким путем, заказ диплома в Москве является безопасным и экономичным вариантом для данных, кто желает достичь успеха в карьере.
глаз бога бот
https://evaelfie.site/# eva elfie hot
era food
This article has been a valuable resource for understanding low back injuries and recovery. Do you have any upcoming articles planned that delve deeper into specific exercises or therapies for low back pain management?
https://sweetiefox.pro/# sweetie fox full video
As a home baker, I appreciate learning about the quality control measures in the wheat flour production. It makes me more conscious about the ingredients I choose for my recipes. Do you have any tips for consumers on selecting the best-quality flour for baking?
https://evaelfie.site/# eva elfie videos
https://salda.ws/meet/notes.php?id=12681
Здравствуйте!
Вы когда-нибудь писали диплом в сжатые сроки? Это очень ответственно и тяжело, но нужно не сдаваться и делать учебные процессы, чем Я и занимаюсь)
Тем кто умеет разбираться и гуглить информацию, это действительно помогает по ходу согласований и написания диплома, не нужно тратить время на библиотеки или встречи с дипломным руководителем, вот здесь есть хорошие данные для заказа и написания дипломов и курсовых с гарантией и доставкой по России, можете посмотреть здесь https://3russkiy-diploms.com, проверено!
купить аттестат
купить диплом
купить диплом о среднем специальном
купить диплом Гознак
купить диплом института
Желаю всем отличных оценок!
https://www.news5cleveland.com/news/local-news/indictment-woman-used-other-pilots-credentials-to-rent-later-crash-aircraft
Привет всем!
Были ли у вас случаи, когда приходилось писать дипломную работу в крайне ограниченные сроки? Это действительно требует большой ответственности и трудоемкости, но важно не отступать и продолжать активно участвовать в учебном процессе, как я.
Для тех, кто умеет эффективно находить и использовать информацию в сети, это действительно помогает в процессе согласования и написания дипломной работы. Больше не нужно тратить время на посещение библиотек или организацию встреч с научным руководителем. Здесь, на этом ресурсе, предоставлены надежные данные для заказа и написания дипломных и курсовых работ с гарантией качества и доставкой по всей России. Можете ознакомиться с предложениями тут https://2orik-diploms.com, это проверенный источник!
купить диплом нового образца
купить диплом о среднем специальном
купить диплом института
купить диплом
где купить диплом
Желаю всем отличных оценок!
http://evaelfie.site/# eva elfie hd
С момента своего вступления в должность в 2005 году Эдуард Давыдов содействовал реализации амбициозного плана по трансформации Башкирской содовой компании (БСК), что привело к фундаментальным изменениям в её операционной деятельности и финансовых показателях Давыдов Эдуард
Привет всем!
Бывало ли у вас такое, что приходилось писать дипломную работу в очень ограниченные сроки? Это действительно требует большой ответственности и тяжелого труда, но важно не сдаваться и продолжать активно заниматься учебными процессами, так же, как и я.
Для тех, кто умеет эффективно использовать интернет для поиска и анализа информации, это действительно облегчает процесс согласования и написания дипломной работы. Не нужно тратить время на посещение библиотек или организацию встреч с дипломным руководителем. Здесь представлены надежные данные для заказа и написания дипломных и курсовых работ с гарантией качества и доставкой по всей России. Можете ознакомиться с предложениями по ссылке https://server-diploms.com, это проверенный способ!
купить диплом
купить диплом ссср
купить диплом о среднем специальном
купить диплом нового образца
Желаю всем отличных оценок!
https://miamalkova.life/# mia malkova hd
Доброго!
Было ли у вас когда-нибудь такое, что приходилось писать дипломную работу в сжатые сроки? Это действительно требует огромной ответственности и напряженных усилий, но важно не сдаваться и продолжать активно заниматься учебными процессами, чем я и занимаюсь.
Для тех, кто умеет искать и анализировать информацию в интернете, это действительно помогает в процессе согласования и написания дипломной работы. Не нужно тратить время на посещение библиотек или организацию встреч с дипломным руководителем. Здесь представлены надежные данные для заказа и написания дипломных и курсовых работ с гарантией качества и доставкой по России. Можете ознакомиться с предложениями по ссылке https://1russa-diploms.com, проверено!
купить диплом института
купить аттестат
купить диплом о среднем образовании
где купить диплом
купить диплом
Желаю всем отличных оценок!
Здравствуйте!
Бывало ли у вас такое, что приходилось писать дипломную работу в крайне сжатые сроки? Это действительно требует огромной ответственности и напряженных усилий, но важно не опускать руки и продолжать активно заниматься учебными процессами, как я.
Для тех, кто умеет быстро находить и анализировать информацию в сети, это действительно помогает в процессе согласования и написания дипломной работы. Больше не нужно тратить время на посещение библиотек или устраивать встречи с дипломным руководителем. Здесь, на этом ресурсе, предоставлены надежные данные для заказа и написания дипломных и курсовых работ с гарантией качества и доставкой по всей России. Можете ознакомиться с предложениями на сайте https://saksx-diploms24.com, это проверено!
купить диплом бакалавра
купить диплом Вуза
где купить диплом
купить диплом колледжа
купить диплом о среднем специальном
купить диплом института
купить диплом в Москве
купить аттестат школы
купить диплом университета
купить аттестат
Желаю всем отличных оценок!
Заслуги Давыдова и его профессиональные достижения в области химической промышленности не остались незамеченными Давыдов Эдуард
Привет всем!
Были ли у вас случаи, когда вам приходилось писать дипломную работу в сжатые сроки? Это действительно требует большой ответственности и усилий, но важно не сдаваться и продолжать активно заниматься учебными процессами, как я.
Для тех, кто умеет эффективно искать информацию в интернете, это действительно облегчает процесс согласования и написания дипломной работы. Больше не нужно тратить время на посещение библиотек или организацию встреч с дипломным руководителем. Здесь, на этом ресурсе, предоставлены надежные данные для заказа и написания дипломных и курсовых работ с гарантией качества и доставкой по всей России. Можете ознакомиться с предложениями на купить диплом, это проверенный источник!
купить диплом колледжа
купить диплом института
купить диплом в Москве
купить диплом техникума
купить аттестат
Желаю всем отличных оценок!
Давыдов родился 10 июля 1984 года в Нальчике. Эдуард Давыдов с самых ранних лет проявлял выдающийся интерес к научным знаниям Эдуард Давыдов
Здравствуйте!
Вы когда-нибудь писали диплом в сжатые сроки? Это очень ответственно и тяжело, но нужно не сдаваться и делать учебные процессы, чем Я и занимаюсь)
Тем кто умеет разбираться и гуглить информацию, это действительно помогает по ходу согласований и написания диплома, не нужно тратить время на библиотеки или встречи с дипломным руководителем, вот здесь есть хорошие данные для заказа и написания дипломов и курсовых с гарантией и доставкой по России, можете посмотреть здесь https://3russkiy-diploms.com, проверено!
купить диплом университета
купить диплом бакалавра
купить диплом специалиста
купить диплом техникума
купить диплом о среднем специальном
Желаю всем отличных оценок!
пинапп https://bk-pinup.kz/
Привет всем!
Бывало ли у вас такое, что приходилось писать дипломную работу в очень ограниченные сроки? Это действительно требует большой ответственности и тяжелого труда, но важно не сдаваться и продолжать активно заниматься учебными процессами, так же, как и я.
Для тех, кто умеет эффективно использовать интернет для поиска и анализа информации, это действительно облегчает процесс согласования и написания дипломной работы. Не нужно тратить время на посещение библиотек или организацию встреч с дипломным руководителем. Здесь представлены надежные данные для заказа и написания дипломных и курсовых работ с гарантией качества и доставкой по всей России. Можете ознакомиться с предложениями по ссылке https://saksx-diploms24.com, это проверенный способ!
купить диплом колледжа
купить диплом Гознак
купить диплом специалиста
купить диплом
купить диплом Вуза
купить диплом университета
купить диплом института
купить диплом цена
купить диплом о среднем специальном
купить диплом в Москве
Желаю всем отличных оценок!
New project of Hudayriyat Island in Abu Dhabi with favourable purchasing conditions and investment returns.
Печать фотографий онлайн. Доставим заказ за 2-4 дня Ежемесячные акции и скидки Собственная фотофабрика фотоуслуги цены
Надежный и производительный дымоход из нержавеющей стали
Обучение Вячеслава Константиновича Николаева началось в стенах МГУ на факультете вычислительной математики и кибернетики, после чего он продолжил образование в США, изучая менеджмент Николаев Вячеслав Константинович
twitchadblocker twitch 広告ブロックあなたはけいれんしていますか 広告ブロッ ク恋人ですが、あなたの経験を台無しにする不快な広告がありますが、心配しないでダウンロードしてください twitch adblock ブラウザ上で、中断することなく無限にストリーミングできます。
adblock chrome | ad blocker chrome | Download onze extensie adblocker chrome en bekijk zorgeloos je favoriete films en seriblokkeren es. Adblocker Chrome is de beste tool waarmee je onnodige advertenties kunt die je irriteren tijdens het streamen. Dus waar wacht je nog op, schiet op en installeer de extensie nu.
https://aviatorjogar.online/# aviator jogar
cassino pin up: pin-up casino – pin up
С 1999 года Николаев активно участвовал в международных проектах, начиная с аналитической работы в области телекоммуникаций и ИТ в J’son and Partners Вячеслав Константинович Николаев
https://aviatoroyunu.pro/# aviator sinyal hilesi
can you contact me mostly by email??, because I don’t have no social skills and I’m too shy to watch people live or using the http://pr.lgubiz.net/bbs/board.php?bo_table=free&wr_id=1780852 application.
reality all dirty and real http://aboard.onoffbiz.com/bbs/board.php?bo_table=free&wr_id=530867 beauties, who in the tables are for you here again are stunningly sexy!
The charge of harassment under article 2240 hf will constitute a misdemeanor under aggravating circumstances, http://www.maumsaram.com/bbs/board.php?bo_table=free&wr_id=68388 is punishable by imprisonment for up to two years and a fine in the amount from 855 to 8540 dollars.
http://aviatorghana.pro/# aviator sportybet ghana
I’m calm. My sexuality is still in mode, but, new apartment is no longer always in control”, – said the Italian porn https://www.go-vespa.pt/community/profile/sharronantonief/ in February this year in the process meetings with journalists at the Berlin International Film Festival.
The payments come as legislators throughout the country consider how to reply to the emerging downside fueled by synthetic intelligence technology.
Mostbet aslan pazarda genc isimdir ve sonuc olarak onun kurucular? ve uzmanlar tak?mlar kendilerini profesyoneller ve cekici bu sektor icinde, dunyan?n her yerinden, dunyan?n her yerinden, dunyan?n her yerinden, dunyan?n her yerinden, dunyan?n her yerinden mostbet uyelerinin ortaya c?kt? cok iyi f?rsatlar? varhttps://www.signwizards.co.uk/img_2507/
the series, which, according to Siffredi’s words, is based flawlessly “98%” on his real biography, is in no hurry to tell about his upbringing in Ortona, a https://quitpit.com/best-stories-for-storytelling-competition/ town in Abruzzo, most famous for heavy fighting between troops of allies and states of the Axis during the Second World War.
נערות ליווי באילת
דירות דיסקרטיות בחיפה
обнал карт купить
Сознание сущности и опасностей связанных с отмыванием кредитных карт способно помочь людям предотвращать атак и сохранять свои финансовые состояния. Обнал (отмывание) кредитных карт — это процесс использования украденных или нелегально добытых кредитных карт для проведения финансовых транзакций с целью сокрыть их происхождения и предотвратить отслеживание.
Вот некоторые способов, которые могут помочь в уклонении от обнала кредитных карт:
Охрана личной информации: Будьте осторожными в связи предоставления личных данных, особенно онлайн. Избегайте предоставления картовых номеров, кодов безопасности и других конфиденциальных данных на ненадежных сайтах.
Надежные пароли: Используйте мощные и уникальные пароли для своих банковских аккаунтов и кредитных карт. Регулярно изменяйте пароли.
Отслеживание транзакций: Регулярно проверяйте выписки по кредитным картам и банковским счетам. Это поможет своевременно выявить подозрительных транзакций.
Антивирусная защита: Используйте антивирусное программное обеспечение и обновляйте его регулярно. Это поможет защитить от вредоносные программы, которые могут быть использованы для кражи данных.
Осмотрительное поведение в социальных медиа: Будьте осторожными в сетевых платформах, избегайте опубликования чувствительной информации, которая может быть использована для взлома вашего аккаунта.
Быстрое сообщение банку: Если вы заметили какие-либо подозрительные операции или утерю карты, сразу свяжитесь с вашим банком для блокировки карты.
Образование: Будьте внимательными к инновационным подходам мошенничества и обучайтесь тому, как предотвращать их.
Избегая легковерия и осуществляя предупредительные действия, вы можете снизить риск стать жертвой обнала кредитных карт.
обнал карт работа
Обналичивание карт – это неправомерная деятельность, становящаяся все более популярной в нашем современном мире электронных платежей. Этот вид мошенничества представляет тяжелые вызовы для банков, правоохранительных органов и общества в целом. В данной статье мы рассмотрим частоту встречаемости обналичивания карт, используемые методы и возможные последствия для жертв и общества.
Частота обналичивания карт:
Обналичивание карт является весьма распространенным явлением, и его частота постоянно растет с увеличением числа электронных транзакций. Киберпреступники применяют различные методы для получения доступа к финансовым средствам, включая фишинг, вредоносное программное обеспечение, скимминг и другие инновационные подходы.
Методы обналичивания карт:
Фишинг: Злоумышленники могут отправлять фальшивые электронные сообщения или создавать веб-сайты, имитирующие банковские системы, с целью получения личной информации от владельцев карт.
Скимминг: Злоумышленники устанавливают устройства скиммеры на банкоматах или терминалах для считывания данных с магнитных полос карт.
Вредоносное программное обеспечение: Киберпреступники разрабатывают вредоносные программы, которые заражают компьютеры и мобильные устройства, чтобы получить доступ к личным данным и банковским счетам.
Сетевые атаки: Атаки на системы банков и платежных платформ могут привести к утечке информации о картах и, следовательно, к их обналичиванию.
Последствия обналичивания карт:
Финансовые потери для клиентов: Владельцы карт могут столкнуться с денежными потерями, так как средства могут быть списаны с их счетов без их ведома.
Угроза безопасности данных: Обналичивание карт подчеркивает угрозу безопасности личных данных, что может привести к краже личной и финансовой информации.
Ущерб репутации банков: Банки и другие финансовые учреждения могут столкнуться с утратой доверия со стороны клиентов, если их системы безопасности оказываются уязвимыми.
Проблемы для экономики: Обналичивание карт создает экономический ущерб, поскольку оно стимулирует дополнительные затраты на борьбу с мошенничеством и восстановление утраченных средств.
Борьба с обналичиванием карт:
Совершенствование технологий безопасности: Банки и финансовые институты постоянно совершенствуют свои системы безопасности, чтобы предотвратить несанкционированный доступ к картам.
Образование и информирование: Обучение клиентов о методах мошенничества и том, как защитить свои данные, является важным шагом в борьбе с обналичиванием карт.
Сотрудничество с правоохранительными органами: Банки активно сотрудничают с правоохранительными органами для выявления и пресечения преступных схем.
Заключение:
Обналичивание карт – весомая угроза для финансовой стабильности и безопасности личных данных. Решение этой проблемы требует совместных усилий со стороны банков, правоохранительных органов и общества в целом. Только эффективная борьба с мошенничеством позволит обеспечить безопасность электронных платежей и защитить интересы всех участников финансовой системы.
Незаконные форумы, где осуществляют обнал банковских карт, представляют собой онлайн-платформы, специализирующиеся на обсуждении и осуществлении противозаконных транзакций с финансовыми пластиком. На таких форумах участники делают обмен данными, методами и опытом в сфере обналичивания, что влечет за собой незаконные действия по получению доступа к финансовым средствам.
Эти веб-ресурсы могут предоставлять различные услуги, относящиеся с мошенничеством, например фальсификация, считывание, вредоносное программное обеспечение и другие методы для сбора данных с банковских пластиковых карт. Кроме того рассматриваются вопросы, касающиеся применением похищенных информации для осуществления финансовых операций или вывода средств.
Участники неправомерных форумов по обналичиванию карт могут стремиться сохраняться анонимными и уходить от привлечения органов безопасности. Участники могут делиться советами, предлагать сервисы, относящиеся к обналом, а также совершать операции, направленные на финансовое преступление.
Важно отметить, что участие в таких деятельностях не просто представляет собой нарушением правовых норм, но также может приводить к правовым санкциям и уголовной ответственности.
In news reports most often used the language of addiction, describing “craving”, “tolerance”, http://ppac.club/ “need for more number of views and ‘withdrawal’.
http://aviatorghana.pro/# aviator bet
Free download Pinterest SVG Icons for logos, websites and mobile apps, useable in Sketch or Figma android icons
если, для примера, первичная высокотемпературная вода нагревает вторичную воду, то такую центральную систему https://www.aloxavantina.com.br/2021/07/16/deputado-thiago-silva-homenageia-campea-sulamericana-de-atletismo-arielly-kailayne/, строго говоря, следует именовать водоводяной.
Не доволен видом своей мебели? Перетянем ее в Минске
перетяжка https://obivka-divana.ru/ .
http://jogodeaposta.fun/# melhor jogo de aposta para ganhar dinheiro
Где купить виртуальный номер: рейтинг лучших сервисов SMS-активаций. Как и в других подобных сервисах, здесь вы можете купить номер для разового использования или взять номер в аренду на более длительный срок арендовать номер телефона
Все о дизайне интерьера
Villas for Sale in the Emaar Farm Gardens II. The developer offers comfortable real estate at competitive prices.
Login Ngamenjitu
Portal Judi: Situs Lotere Daring Terbesar dan Terpercaya
Portal Judi telah menjadi salah satu portal judi daring terbesar dan terpercaya di Indonesia. Dengan beragam pasaran yang disediakan dari Grup Semar, Situs Judi menawarkan sensasi main togel yang tak tertandingi kepada para penggemar judi daring.
Market Terbaik dan Terpenuhi
Dengan total 56 pasaran, Portal Judi memperlihatkan beberapa opsi terbaik dari market togel di seluruh dunia. Mulai dari market klasik seperti Sydney, Singapore, dan Hongkong hingga market eksotis seperti Thailand, Germany, dan Texas Day, setiap pemain dapat menemukan market favorit mereka dengan mudah.
Langkah Main yang Praktis
Ngamenjitu menyediakan tutorial cara bermain yang mudah dipahami bagi para pemula maupun penggemar togel berpengalaman. Dari langkah-langkah pendaftaran hingga penarikan kemenangan, semua informasi tersedia dengan jelas di platform Situs Judi.
Hasil Terakhir dan Informasi Paling Baru
Pemain dapat mengakses hasil terakhir dari setiap market secara real-time di Situs Judi. Selain itu, informasi paling baru seperti jadwal bank online, gangguan, dan offline juga disediakan untuk memastikan kelancaran proses transaksi.
Pelbagai Jenis Game
Selain togel, Ngamenjitu juga menawarkan berbagai jenis permainan kasino dan judi lainnya. Dari bingo hingga roulette, dari dragon tiger hingga baccarat, setiap pemain dapat menikmati berbagai pilihan permainan yang menarik dan menghibur.
Keamanan dan Kenyamanan Pelanggan Dijamin
Situs Judi mengutamakan keamanan dan kepuasan pelanggan. Dengan sistem security terbaru dan layanan pelanggan yang responsif, setiap pemain dapat bermain dengan nyaman dan tenang di situs ini.
Promosi dan Bonus Istimewa
Ngamenjitu juga menawarkan bervariasi promosi dan bonus istimewa bagi para pemain setia maupun yang baru bergabung. Dari hadiah deposit hingga bonus referral, setiap pemain memiliki kesempatan untuk meningkatkan kemenangan mereka dengan bonus yang ditawarkan.
Dengan semua fasilitas dan pelayanan yang ditawarkan, Portal Judi tetap menjadi pilihan utama bagi para penggemar judi online di Indonesia. Bergabunglah sekarang dan nikmati pengalaman bermain yang seru dan menguntungkan di Portal Judi!
https://vavada13.life/
aviator game: play aviator – aviator malawi
То есть, виртуальный номер нужен для обеспечения приватности, безопасности и свободной работы с десятками и сотнями сайтов одновременно аренда сим карты
Купить диплом техникума – Это вариант завладеть официальный бумага о завершении образовательного учреждения. Диплом открывает двери к последующим карьерным возможностям и профессиональному росту.
В наше время все чаще возникает необходимость в переводе документов для различных целей. В Новосибирске есть множество агентств и переводчиков, специализирующихся на качественных переводах документов. Однако, помимо перевода, часто требуется также апостиль, который удостоверяет подлинность документа за рубежом.
Получить апостиль в Новосибирске — это несложно, если обратиться к профессионалам. Многие агентства, занимающиеся переводами, также предоставляют услуги по оформлению апостиля. Это удобно, т.к. можно сделать все необходимые процедуры в одном месте.
При выборе агентства для перевода документов и оформления апостиля важно обращать внимание на их опыт, репутацию и скорость выполнения заказов. Важно найти надежного партнера, который обеспечит качественный и своевременный сервис. В Новосибирске есть множество проверенных организаций, готовых помочь в оформлении всех необходимых документов для вашего спокойствия и уверенности в законности процесса.
https://salda.ws/meet/notes.php?id=12681
Presents the new residential complex of The Sapphire by Damac Properties with favourable terms of purchase and return on investment.
zithromax generic price: order zithromax without prescription – order zithromax without prescription
zithromax 600 mg tablets – https://azithromycin.pro/can-you-take-ibuprofen-with-zithromax.html zithromax 250 mg
glaz boga
buy zithromax 500mg online: zithromax and seizure buy zithromax online australia
В наше время все чаще возникает необходимость в переводе документов для различных целей. В Новосибирске есть множество агентств и переводчиков, специализирующихся на качественных переводах документов. Однако, помимо перевода, часто требуется также апостиль, который удостоверяет подлинность документа за рубежом.
Получить апостиль в Новосибирске — это несложно, если обратиться к профессионалам. Многие агентства, занимающиеся переводами, также предоставляют услуги по оформлению апостиля. Это удобно, т.к. можно сделать все необходимые процедуры в одном месте.
При выборе агентства для перевода документов и оформления апостиля важно обращать внимание на их опыт, репутацию и скорость выполнения заказов. Важно найти надежного партнера, который обеспечит качественный и своевременный сервис. В Новосибирске есть множество проверенных организаций, готовых помочь в оформлении всех необходимых документов для вашего спокойствия и уверенности в законности процесса.
https://salda.ws/meet/notes.php?id=12681
canadian pharmacy drugs online: canadian pharmacy – my canadian pharmacy canadianpharm.store
Септики Топас
Real estate in the brand-new project of New Launch Dubai islands villas . Developer offers gorgeous villas at attractive prices.
porn videos
เมื่อเอ่ยถึงการบริการ wm ฝาก – ถอน เร็วทันใจ โอนไว 1 วินาที สำหรับทำพนันออนไลน์ ท่านชอบได้ยินผู้เล่นคนไม่ใช่น้อยต่างเอ๋ยถึง สล็อตเว็บไซต์ตรง100% ที่ย้ำการผลิตรายได้ให้กับนักพนัน พวกเราขอเสนอแนะ
เว็บไซต์ตรงไม่ผ่านเอเย่นต์ไม่มีอย่างต่ำ บาคาร่าเว็บตรง ที่มีระบบระเบียบเทคโนโลยีทันสมัย จะเป็นตัวกระตุ้นความพอใจของนักพนัน และก็นำมาซึ่งกระแสได้ดิบได้ดีเสมอ เชื้อเชิญให้มีส่วนร่วมกับการลงทุน สล็อตดัง เป็นอีกหนึ่งวิถีทางสำหรับการพนัน เกมสล็อต จากทั้งโลก
สล็อตเว็บไซต์นอก ลิขสิทธิ์แท้ เกมสล็อตแตกง่าย Evoplay สล็อต ผ่านปากทางเข้าเริ่มเล่น เว็บไซต์สล็อตแท้ คัดสรรนำเอา เกมสล็อต ทั้งผอง มีให้แด่ท่านเลือกเล่นกันอย่างครบวงจรที่เยี่ยมที่สุด นับได้ว่าเป็น สล็อต เว็บไซต์ นอก ลิขสิทธิ์แท้ เล่นง่าย ได้เงินจริง แจกเงินรางวัลกันตลอดแต่ละวัน
เข้าเล่น เกมไพ่บาคาร่าที่ Sexygaming นแบบง่ายๆไม่ยุ่งยาก สลับซับซ้อน และก็ ยังมีความพิเศษมากมายก่ายกอง สามารถเข้ามาเลือกเล่นกับทางเว็บไซต์ตรง ที่ได้รับความนิยมที่1 ของไทย
มีค่ายเกมให้เลือกเล่นกันมากมาย ค่ายบาคาร่า ต่างแดน ที่ส่งตรงจากผู้พัฒนา Ezslot มีแพลตฟอร์มถ่ายทอดสด ระบบเสถียร ไม่มีกระดอน ไม่มีสะดุด แบบออนไลน์กันตลอดระยะเวลา บันเทิงใจครบหมดทุกค่าย ข้างในที่เว็บเดียว
การแทงหวยร่ำรวยง่ายสุดๆ ไทยลอตโต้ ให้ความใส่ใจในความปลอดภัยและก็ความเป็นส่วนตัวของข้อมูลผู้เล่น ทำให้ท่านเชื่อมั่นสำหรับในการแทงหวยออนไลน์กับเว็บไซต์แห่งนี้ ระบบรักษาความปลอดภัยระดับสูงจะดูแลข้อมูลของคุณอย่างเคร่งครัด
pg เกมสล็อตมาแรงที่สุดในปี2024 ที่เหล่านักเดิมพันทุกคนห้ามพลาดเด็ดขาดมาพร้อมฟีเจอร์สวยอลังการ ภาพสีเสียงเต็มระบบ
Строительство жилых домов: качественное жилье для вашей семьи
mexico drug stores pharmacies: Medicines Mexico – best online pharmacies in mexico mexicanpharm.shop
https://cleaning24moscow.ru/
сайты кореи авто https://avtodom63.ru/
canadian pharmacy uk delivery: canadianpharmacymeds com – canadian pharmacy service canadianpharm.store
https://canadianpharmlk.com/# canadian pharmacy ltd canadianpharm.store
medicine in mexico pharmacies: Medicines Mexico – medication from mexico pharmacy mexicanpharm.shop
Hi there to all, for the reason that I am genuinely keen of reading this blog’s post to be
updated regularly. It contains good data.
Review my site 카지노사이트
клининговая услуга
https://ekspert-komforta.ru/
Святослав Серебряков отзывы маг
Отзыв о снятии порчи от Мага Святослава Серебрякова: Освобождение от Тьмы и Возвращение к Свету
Я хочу поделиться своим невероятным опытом работы с Магом Святославом Серебряковым в снятии порчи. Долгое время я страдал от непонятных препятствий, неудач и негативных событий, которые казались связанными с каким-то внешним воздействием.
Обратившись к Магу Святославу, я почувствовал сразу же облегчение и надежду. Его профессионализм и преданность помогли мне пройти через этот темный период. Он внимательно выслушал мою ситуацию и предложил план действий для снятия порчи.
После ритуала снятия порчи я почувствовал, как будто тяжесть, которая долгое время давила на меня, была снята. Моя жизнь начала наполняться светом и позитивной энергией. Негативные события перестали преследовать меня, и я почувствовал себя свободным от влияния темных сил.
Маг Святослав Серебряков – это настоящий специалист в своем деле. Его умение работать с энергией и его преданность своей работе сделали его истинным исцелителем для меня. Я благодарен ему за его помощь в освобождении меня от порчи и возвращении к свету.
Если вы столкнулись с подобной ситуацией, не стесняйтесь обратиться к Магу Святославу Серебрякову. Он может помочь вам вернуть гармонию и благополучие в вашу жизнь.
Спасибо вам, Маг Святослав, за вашу помощь и поддержку в моем пути к исцелению и свету.
-приворот на скрученных церковных
-приворот читать
-сильный приворот на мужчину быстро читать
-приворот женщина
-гадалка на приворот
https://calculatortiktok.com/
https://indianpharm24.com/# cheapest online pharmacy india indianpharm.store
https://allergija.com/zashhitnye-kozyrki-iz-polikarbonata.html
https://indianpharm24.com/# india online pharmacy indianpharm.store
https://file-don.ru/proektirovanie-press-form-sozdanie-idealnoj-konstrukczii-dlya-proizvodstva-vysokokachestvennyh-izdelij/
http://indianpharm24.shop/# buy medicines online in india indianpharm.store
Bonos de casino sin deposito ?No te los pierdas!
bono de casino sin deposito casino online con bono sin deposito .
https://salezhilie.ru/
В современном мире все чаще возникает необходимость легализации документов для использования за границей. Один из способов осуществления данной процедуры – получение апостиля. В Новосибирске эта услуга доступна всем желающим в специализированных организациях.
Апостиль – это особая форма легализации документов, предназначенных для использования в странах, участниках Гаагской конвенции 1961 года. С помощью апостиля подтверждается подлинность подписи документа, квалификация должностного лица, его полномочия и подлинность печати, если это предусмотрено. Получить апостиль можно на документах различного характера – свидетельства о рождении, браке, смерти, доверенности, диплома об образовании и других.
В Новосибирске услуги по оформлению апостиля предоставляют специализированные учреждения. Для этого необходимо обратиться в нотариальную контору или в отдел ЗАГС. При обращении следует иметь при себе оригинал документа, который требует легализации, а также паспорт для удостоверения личности. Стоимость услуги может варьироваться в зависимости от типа документа и срочности выполнения.
Оформление апостиля в Новосибирске является необходимым шагом для тех, кто планирует выезд за рубеж или ведет деловую деятельность с иностранными партнерами. Без данной процедуры документы не будут иметь юридической силы за пределами России. Важно помнить, что апостиль выдается только на территории стран-участниц конвенции, поэтому перед оформлением стоит уточнить, является ли страна, в которую вы собираетесь поехать, участником данного документа.
Выводя таким образом, можно сказать, что получение апостиля в Новосибирске – это важный этап в легализации документов для использования за границей. Соблюдая все необходимые процедуры и требования, вы сможете без проблем и задержек использовать свои документы на территории других стран. Не откладывайте на потом, обратитесь за помощью к специалистам и оформите все необходимые документы вовремя.апостиль в Новосибирске
https://prednisonest.pro/# purchase prednisone
https://kupitroom.ru/
химчистка квартиры
https://arcmetal.ru/
Строительство домов из профилированного бруса в Твери: качество и надежность
Discover the leading Best neurology hospitals in Delhi, Learn about their advanced treatments, expert neurologists, and compassionate care for neurological disorders.
http://prednisonest.pro/# buy prednisone 10 mg
먹튀사이트
https://kupitroom.ru/
신규사이트
슬롯체험
카지노뉴스
https://spbflatkupit.ru/
Discover the epitome of luxury living in Dubai with DAMAC Properties’ exquisite range of apartments, villas, and townhouses. Explore exclusive properties for sale in iconic locations like Damac Bay 2 Business Bay, Dubai Marina, and Burj Khalifa.
https://prednisonest.pro/# prednisone cream
ТолMuch – ваш надежный партнер в переводе документов. Многие сферы жизни требуют предоставления переведенных документов – образование за рубежом, международные бизнес-соглашения, иммиграционные процессы. Наши специалисты помогут вам с профессиональным переводом документов.
Наш опыт и профессионализм позволяют нам обеспечивать высокое качество перевода документов в самые кратчайшие сроки. Мы понимаем, насколько важна точность и грамотность в этом деле. Каждый проект для нас – это возможность внимательно отнестись к вашим документам.
Сделайте шаг к успешному будущему с нами. Наши услуги по переводу документов помогут вам преодолеть языковые барьеры в любой области. Доверьтесь переводу документов профессионалам. Обращайтесь к ТолMuch – вашему лучшему выбору в мире лингвистики и перевода.
#переводдокументов #ТолMuch #язык #бизнес
https://spbdomkupit.ru/
https://spbhousekupit.ru/
трансфер вокзал белокуриха http://transfer-novosibirsk-belokurikha.ru/
siesta key marina boat rentals https://boatrent.shop/
https://amoxilst.pro/# amoxicillin 500 mg cost
https://ekbflatkupit.ru/
https://zhksaleflat.ru/
I’m really impressed with your B.Sc 2nd Year Time Table writing skills as well as with the layout on your blog.
Discover the epitome of luxury living at Rashid Yachts! Explore an exquisite collection of studios, apartments, and penthouses crafted by renowned developers. Uncover the perfect blend of off-plan and ready properties in an unparalleled waterfront setting. Experience the pinnacle of elegance and seize your dream home today!
https://zhksalezhilie.ru/
https://zhksaledom.ru/
https://vsegda-pomnim.com/
https://edpills.guru/# get ed prescription online
http://klublady.ru/
Все о современных технологиях
http://edpills.guru/# cheap ed treatment
http://diplombiolog.ru/
http://diplombuhgalter.ru/
Discover luxury apartments and penthouses in the exclusive Le Pont Dubai. Experience the epitome of coastal living with Meraas, as they present incredible units for sale at unbeatable prices. Don’t miss out on this coveted opportunity to make your dream home a reality.
http://pharmnoprescription.pro/# online pharmacy reviews no prescription
В нашем кинотеатре https://hdrezka.uno смотреть фильмы и сериалы в хорошем HD-качестве можно смотреть с любого устройства, имеющего доступ в интернет. Наслаждайся кино или телесериалами в любом месте с планшета, смартфона под управлением iOS или Android.
I must admit that after giving some of the advice you provided here a try, it truly helped me. Both the volume of visitors to my website and their level of engagement have increased. I appreciate your useful advice.
https://kursovyebiolog.ru
https://edpills.guru/# best ed medication online
5 способов улучшить свой участок с помощью рулонного газона
рулонный газон цена https://rulonnyygazon177.ru/ .
kelexo crypto
казино
Полный комплекс бухгалтерских услуг для юридических лиц, ООО и ИП. Ведение бухучета, сопровождение и обслуживание бизнеса. Наши бухгалтеры помогут Вам бухгалтерские услуги
הגובר של כל נערת ליווי בתל אביב מציעה הזדמנות ייחודית לחוות את ההנאות החושניות ביותר אם אתה מזמין אותה אליך לבית או דירת נופש ולשפר את ההערכה העצמית ואת דימוי המיניות. תמיד זמינות לשירותך האישי הדיסקרטי ביותר. אוסף עדכני של עם מספרי טלפון ליצירת קשר נערות ליווי בחיפה
В современной промышленности важное значение имеет испытательное оборудование, позволяющее оценивать параметры изделий на различных этапах производства. Один из ключевых видов такого оборудования — вибростенды, предназначенные для испытания компонентов и сборок на устойчивость к воздействию механических колебаний виброустановки
והבטיחות של הנערות והן של הלקוח. בחורות ישראליות, אתיופיות, אירופאיום וכמובן גם רוסיות בכל הגילאים עוזרות לעורר את האנרגיות טוטאלית! האם אתה סוף סוף מוכן לגלות את הסודות החבויים בעולם הפינוק הארוטי למבוגרים בעיר החובקת תשוקה? עם התגברות ההתעניינות כלפי דירות דיסקרטיות באשדוד
https://pharmacynoprescription.pro/# online drugs no prescription
http://canadianpharm.guru/# canadian pharmacy ltd
https://canadianpharm.guru/# reliable canadian pharmacy reviews
https://canadianpharm.guru/# canadian mail order pharmacy
https://1ecenter.ru
כיף להזמין לבית מלון צעירה סקסית יפיפיה לחוויה ייחודית המשלבת את כוח הריפוי של אירוטיקה עם הנאה אמיתית. זה חורג מהגבולות כשמדובר בהזמנה לביתך או מלון. תקשורת אדיבה וברורה, כבוד והסכמה הדדית הם תמיד חיוניים לפגישות בטוחות ומהנות. חשוב לזכור שצריך דירות דיסקרטיות באשקלון
אסתטיים עם טעם מצוין! כיצד למצוא המושלמות בעוד הביקוש לבילויים דיסקרטיים עם ממשיך לגדול, חשוב למצוא סוכנות מכובדת ומקצועית עם הגובר של כל נערת ליווי בתל אביב מציעה הזדמנות ייחודית לחוות את ההנאות החושניות ביותר אם אתה מזמין אותה אליך לבית או דירת נופש דירות דיסקרטיות בבאר שבע
Услуга демонтажа старых частных домов и вывоза мусора в Москве и Подмосковье от нашей компании. Мы предлагаем демонтаж и вывоз мусора в указанном регионе по доступным ценам. Наша команда https://hoteltramontano.ru гарантирует выполнение услуги в течение 24 часов после заказа. Мы бесплатно оцениваем объект и консультируем клиентов. Узнать подробности и рассчитать стоимость можно по телефону или на нашем сайте.
https://canadianpharm.guru/# canadian pharmacy mall
http://canadianpharm.guru/# canada drugs
волчонок смотреть онлайн
עם גירוי אירוטי ויוצר חוויה ייחודית החורגת מבילוי מסורתי. המטרה העיקרית של היא לעורר את החושים, לשחרר מתח ולקדם את הרווחה חוויה מחוץ לעולם הזה שתפתה את הגוף והנפש שלך. בנוסף הן בהחלט יכולות לשפר את המודעות שלך לגוף ולעזור לך להתחבר עם החושניות שלך דירות דיסקרטיות בתל אביב
http://indianpharm.shop/# world pharmacy india
1вин
https://na-dache.pro
http://klubmama.ru
https://mexicanpharm.online/# best online pharmacies in mexico
https://canadianpharm.guru/# canadian pharmacy prices
Дизайнерские радиаторы отопления. Представить современный дом без радиатора очень трудно, особенно в осенний и зимний сезон, когда так хочется тепла и уюта https://radiators-teplo.github.io/
Купить диплом о среднем специальном – Это способ достать официальный документ по окончании образовательного учреждения. Диплом открывает пути к новым карьерным возможностям и профессиональному росту.
Come on, join our site to achieve your great luck. SENJATA4D“
сео цена
https://mexicanpharm.online/# mexican drugstore online
https://adzan.online/
Лучшие картинки различных тематик https://stilno.site
http://mexicanpharm.online/# best online pharmacies in mexico
В ассортименте нашего интернет-магазина сантехники представлена только оригинальная продукция таких известных брендов как Джилекс, PRO AQUA, Valfex, LD, СТМ и многих других
Изготовление стильных фотокниг недорого. Быстрая и качественная печать фотобуков на заказ. Создавайте фотоальбомы онлайн с помощью простого и бесплатного фоторедактора фотокнига заказать москва
даркнет россия
стране, вроде и в других территориях, даркнет представляет собой участок интернета, неприступную для стандартного поиска и просмотра через регулярные поисковики. В противоположность от публичной плоской сети, даркнет является неизвестным участком интернета, доступ к чему часто делается через эксклюзивные программы, наподобие Tor Browser, и неизвестные инфраструктуры, подобные как Tor.
В теневой сети сосредоточены различные источники, включая дискуссии, торговые места, блоги и прочие интернет-ресурсы, которые могут неприступны или запретны в стандартной коммуникации. Здесь допускается найти различные продукты и послуги, включая нелегальные, например наркотические препараты, стрелковое оружие, взломанные данные, а также услуги хакеров и прочие.
В России даркнет так же применяется для обхода цензуры и наблюдения со стороны сторонних. Некоторые клиенты могут использовать его для передачи информацией в обстоятельствах, когда автономия слова заблокирована или информационные ресурсы подвергнуты цензуре. Однако, также рекомендуется отметить, что в теневой сети имеется много не Законной работы и потенциально опасных положений, включая обман и киберпреступления
https://indianpharm.shop/# indian pharmacies safe
https://pro-dachnikov.com
http://mexicanpharm.online/# mexican pharmaceuticals online
Уникальные фото различных тематик https://pro-dachnikov.com
Заказать диссертацию онлайн. Комплексная поддержка соискателей по подготовке НИР любой сложности под ключ. Выполнение – в сумме за 120 дней по гуманитарным дисциплинам, и в сумме 150-180 дней по техническим дисциплинам купить вкр
Регистрация в букмекерской конторе Fonbet – это первый шаг к захватывающему миру спортивных ставок. Процедура регистрации на официальном сайте проста и удобна: достаточно заполнить несколько обязательных полей, подтвердить свои данные и выбрать удобный способ пополнения счета. Подробная инструкция – https://t.me/s/registraciya_fonbet_ru
http://indianpharm.shop/# online shopping pharmacy india
является участником банды . Именно помогла ему открыть сайт и теперь она за своё покровительство и раскрутку получает часть денег от клиентов-лохов, которых обработал мерзавец-шарлатан.
Как это обычно и бывает у мошенников, — это не настоящие имя-отчество, а очередной псевдоним. За случайной кличкой скрывается безработный, раньше уже мотавший сроки, продолжающий свою мошенническую деятельность.
Вместо реального фото, на вывешено сгенерированное нейросетью изображение мультяшного персонажа, эдакого старца-волхва. Настоящую же свою испитую,физиономию немаг тщательно скрывает, так как справедливо опасается, что вычислят и накажут.
Также на размещены написанные аферистом отзывы даже за 2010 год. В реальности же сайт появился всего пару недель назад – 15 февраля 2024 года. И именно эти две недели уголовник обманывает именно под кличкой.
Однако у него уже есть опыт в мошеннической деятельности, так как раньше он промышлял под кличками:
Будьте бдительны: и на сайте и на других подобных площадках действуют опасные и умелые в своей противозаконной деятельности аферисты. Они знают, как войти в доверие, но никто из них не способен оказать реальную помощь.
И шарлатан и подобные ему, постоянно дают пустые обещания. Деньги гребут лопатой, но никогда ни одному человеку не помогут. Так как все приписываемые им сверхъестественные способности — один сплошной обман. Ни один реальный отзыв от обманутых клиентов на не будет пропущен лжемагом – все отзывы от сам себе и пишет.
шарлатан фильм 2020 смотреть онлайн бесплатно в хорошем качестве
https://pharmacynoprescription.pro/# online pharmacies without prescription
https://game24.space/
pin up casino indir: pin up casino guncel giris – pin up giris
https://podacha-blud.com/
VSDC Free Video Editor: Your Ultimate Tool for Creating Stunning Videos
https://gruzchikirabotnik.ru/
Отличный сайт! Всем рекомендую! заказ цветов Минск
Salutation to our dedicated dais in return staying cultured about the latest intelligence from the Joint Kingdom. We understand the prominence of being well-versed upon the happenings in the UK, whether you’re a resident, an expatriate, or purely interested in British affairs. Our extensive coverage spans across sundry domains including politics, briefness, education, entertainment, sports, and more.
In the jurisdiction of wirepulling, we support you updated on the intricacies of Westminster, covering ordered debates, government policies, and the ever-evolving vista of British politics. From Brexit negotiations and their impact on trade and immigration to domestic policies affecting healthcare, instruction, and the circumstances, we provide insightful review and timely updates to stop you navigate the complex area of British governance – https://newstopukcom.com/mosfest-makes-a-triumphant-comeback-for-its/.
Economic news is vital in search adroitness the monetary pulsation of the nation. Our coverage includes reports on superstore trends, charge developments, and budgetary indicators, donation valuable insights for investors, entrepreneurs, and consumers alike. Whether it’s the latest GDP figures, unemployment rates, or corporate mergers and acquisitions, we fight to hand over precise and akin intelligence to our readers.
Popular Porn
Ищете профессиональных грузчиков, которые справятся с любыми задачами быстро и качественно? Наши специалисты обеспечат аккуратную погрузку, транспортировку и разгрузку вашего имущества. Мы гарантируем профессиональные грузчики, внимательное отношение к каждой детали и доступные цены на все виды работ.
aviator sinyal hilesi: aviator sinyal hilesi ucretsiz – aviator hilesi ucretsiz
услуги грузчиков в самаре
https://muslim-prayer-times.com/
aviator ucak oyunu: aviator hile – aviator sinyal hilesi ucretsiz
twitchadblocker Yayın yapmayı seviyor musun? twitch reklam engelleme, ama araya girip anınızı mahveden reklamlar mı var? O zaman endişelenmeyin ve indirin twitch adblock şimdi ve sınırsız akışın keyfini çıkarın.
Создавай свой стиль вместе с нами! Учись шить свитшоты от профи и раскрой свой талант в мире моды. Присоединяйся к мастер-классу и стань лучшим в создании уникальных вещей! Регистрация ограничена https://u.to/zQWJIA
заказать услуги грузчиков
gates of olympus slot: pragmatic play gates of olympus – gates of olympus slot
https://gruzchikistudent.ru
https://gruzchikietazh.ru
slot oyunlari: sweet bonanza yorumlar – sweet bonanza demo
Бизнесмен Андрей Кнауб хорошо известен как предприниматель и трейдер в сфере нефтепереработки. Он более 25 лет был частью крупнейших отраслевых компаний, реализовал множество благотворительных и социальных проектов кнауб андрей
slot oyunlar? siteleri: slot siteleri bonus veren – slot oyun siteleri
Электронная регистрация в Росреестре – Сделки онлайн – Центр “Недвижимость и право”
Электронная регистрация в Росреестре сделок с недвижимостью. Ускоренные сроки – 3-7 дней. Выписки из ЕГРН.
I don’t know whether it’s just me or if perhaps everybody else encountering problems with your site.
It appears as though some of the tsxt in your posts are running off the screen. Can someone else pleaase comment and let me
know if this is happening to them too? This maay be a issue with
my browser because I’ve had this happen before.
Thank you
Here is my webb page – 카지노사이트
aviator: aviator mostbet – aviator oyna slot
https://catherineasquithgallery.com
sweet bonanza 100 tl: sweet bonanza free spin demo – sweet bonanza oyna
All desktop OS among other things can to use the http://www.absent.ru/restoran/all/?search=%3D%2F%22%3E%3Ch1%3E%3Ca+href%3D+http%3A%2F%2Fgamestop-wallet.io. Many crypto traders believe that this wallet wonderful suitable for storage of digital collectibles, like nft.
Предприниматель придерживался мнения, что заботиться надо не только о персонале, но и окружающей среде кнауб андрей
https://gruzchikjob.ru
https://www.avito.ru/kemerovskaya_oblast_mezhdurechensk/predlozheniya_uslug/podem_domov._perenos_domov._zamena_ventsov_3831125828
В биографии бизнесмена Андрея Артуровича Кнауба важно отметить, что для него ключевое значение имела забота о персонале и экологической обстановке в регионе кнауб андрей артурович
покер онлайн
Egor Alexandrovich Abramov’s personal life remains guarded, allowing his work to speak volumes about his dedication to the craft egor abramov entrepreneur
sweet bonanza: guncel sweet bonanza – sweet bonanza free spin demo
Egor Abramov’s biography, initiated by chance, has evolved into a promising career, and as he continues to make his mark in the cinematic landscape, audiences can anticipate more captivating performances from this talented young actor egor alexandrovich abramov
Предлагаем слуги: https://lit9.ru, демонтаж фундамента, слом домов.
Вы не правы. Я уверен. Могу это доказать. Пишите мне в PM, пообщаемся.
you can to receive page in the “Rewards” module in the administrative interface of the http://rusf.ru/comment/gromov/guestbk.htm.
Наша компания дает проф хостинг-услуги по бурению скважин на воду на С-петербурге равным образом Ленинградской области. Мы владеем богатым эмпирически в данной мира а также гарантируем лучшее выполнение круглых работ.
Бурение скважин – этто надежный а также эффективный способ обеспеченья хозяйственного хозяйства, фирм равным образом организаций чистой а также лучшей водой. Наша команда мастериц осуществляет эмпайр скважин различной глубины и диаметра, учитывая отличительные черты донных вожак в течение конкретном регионе – https://burenie-na-vodu-spb.online/lodejnopolskij/.
Наша сестра используем прогрессивное ясс равно технологии, что разрешает нам проделывать службы я мухой равно безопасно. Наша цель – вооружить покупателей беспроигрышным и еще прочным водоснабжением, каковое хорэ поклоняться долгие годы.
Сверх бурения скважин, автор тоже делаем отличное предложение услуги числом обустройству скважинной доктрины: энергоустановка насосов, фильтров, резервуаров а также другого оснащения чтобы обеспеченья уютного потребления водой.
Читайте статью на vc.ru https://vc.ru/crypto/1099363-kak-prodat-notkoin-notcoin-sposoby-prodazhi-instrukcii-i-sovety-novichkam как продать Ноткоины сегодня по отличной цене. Если вы хотите продать Ноткоин, нажимаете кнопку “Создать ордер” – “Продать” – выбираете цену и количество – нажимаете продать.
https://sporty24.site
Despite his youth, Egor Abramov has already earned critical acclaim and popularity among viewers. His growth as an actor portends a bright future and opens up new opportunities in Russian cinema egor alexandrovich abramov
https://www.avito.ru/osinniki/predlozheniya_uslug/podem_domov._perenos_domov._zamena_ventsov_3799568326
Наш путеводитель по Санкт-Петербургу собрал лучшие отели и места для туристов Сапсан Петербург Москва Мы расскажем, в каких кафе можно бюджетно перекусить, где попробовать особенные блюда с местным колоритом или отужинать, как потомки аристократов.
http://cleandi.ru/
Услуги грузчиков https://mhpereezd.ru с гарантией!
https://mhpereezd.ru
Отечественный производитель предлагает оборудование для фитнеса https://oborudovanie-dlya-fitnesa.ru/ по приятным ценам, без добавочных наценок. Всегда в продажеобъемный каталог для оптовых покупателей. Предоставляем многофункциональные станки и аксессуары, которые помогут вам улучшить ваше здоровье и физическую форму.
В изготовлении мягких частей используется винилискожа. Основные элементы изготовлены из углеродистых видов стали. Качественные продукты позволяют продуктивно заниматься фитнесом как дома, так и тренажерном центре. Производимое оборудование отличается достойным качеством и надежностью, что позволяет вам тренироваться продуктивно и удобно. Для домашних тренировок отлично подойдут эспандеры, слэмбэги, степ платформы, грифы, платформы босу, массажеры, платформы Bosu, скакалки, утяжелители.
Egor, along with central actors, explores more mature themes in the latest season, depicting the evolving challenges faced by their characters egor abramov biography
Торгово-промышленное объединение предлагает спортивные тренажеры sportivnyj-trenazher.ru для усиленной эксплуатации в коммерческих условиях. В каталоге интернет-магазина вы оцените самые востребованные модели устройств – блочных и нагружаемых. Объемный каталог дает возможность подобрать тренажеры для изолированной укрепления теоретически любых мышц. Оформите многофункциональный Кроссовер, Баттерфляй, силовую раму Смита, вертикально-горизонтальную тягу, скамью Скотта, Дельта машину, Гакк тренажер, конструкции для работы с собственным весом, Гравитрон для подтягивания и отжиманий, гиперэкстензию, атлетические скамьи, универсальную лавку, Хаммер. Изготавливаемое оборудование не требует постоянного технического обслуживания. Можете заказать весовой стек необходимого веса.
сеть даркнет
Подпольная часть сети: недоступная зона компьютерной сети
Теневой уровень интернета, тайная зона интернета продолжает вызывать интерес интерес как граждан, а также правоохранительных структур. Этот подпольный слой интернета известен своей анонимностью и возможностью осуществления преступных деяний под тенью анонимности.
Основа темного интернета состоит в том, что он не доступен для популярных браузеров. Для доступа к этому уровню требуются специализированные программные средства и инструменты, предоставляющие анонимность пользователям. Это вызывает отличную площадку для разнообразных противозаконных операций, в том числе торговлю наркотиками, торговлю огнестрельным оружием, кражу конфиденциальных данных и другие незаконные манипуляции.
В ответ на возрастающую опасность, некоторые государства ввели законодательные меры, целью которых является запрещение доступа к подпольной части сети и преследование лиц занимающихся незаконными деяниями в этой скрытой среде. Однако, несмотря на предпринятые шаги, борьба с подпольной частью сети остается сложной задачей.
Важно отметить, что полное запрещение теневого уровня интернета практически невыполнима. Даже с введением строгих мер контроля, доступ к этому уровню интернета все еще осуществим через различные технологии и инструменты, используемые для обхода блокировок.
Кроме законодательных мер, имеются также проекты сотрудничества между правоохранительными структурами и технологическими компаниями с целью пресечения противозаконных действий в теневом уровне интернета. Впрочем, для успешной борьбы требуется не только техническая сторона, но и совершенствования методов выявления и предотвращения незаконных действий в этой области.
В заключение, несмотря на принятые меры и усилия в борьбе с преступностью, темный интернет остается серьезной проблемой, которая требует комплексного подхода и совместных усилий как со стороны правоохранительных органов, а также технологических организаций.
http://viagragood.ru/v-50-let-normalnaya-erekciya.html
Готов перейти от идей к реальности? Шьем брендовые свитшоты вместе! Учись создавать стильные вещи и покорять мир своим талантом на новом мастер-классе. Не упусти возможность стать модным гуру! Зарегистрироваться сейчас https://u.to/zQWJIA
https://www.avito.ru/prokopevsk/predlozheniya_uslug/podem_domov._perenos_domov._zamena_ventsov_3799239508
https://gruzchikibol.ru/
https://gruzchikivagon.ru/
In both 2014 and 2015 Alexandre Cougnaud raced in the Porsche Carrera Cup France championship. He finished in 10th position the first year and in 12th position the second year https://it.motorsport.com/driver/alexandre-cougnaud/177269/photo-galleries/
https://gruzchikistudent.ru/
Регистрация в букмекерской конторе Fonbet – это первый шаг к захватывающему миру спортивных ставок. Процедура регистрации на официальном сайте проста и удобна: достаточно заполнить несколько обязательных полей, подтвердить свои данные и выбрать удобный способ пополнения счета. Подробная инструкция – https://t.me/s/registraciya_fonbet_ru
https://gruzchikietazh.ru/
https://gruzchikibaza.ru/
https://jp.motorsport.com/driver/alexandre-cougnaud/408164/
https://gruzchikikorob.ru/
https://gruzchikibaza.ru
https://gruzchikivagon.ru
https://vk.com/zamena_venzov
https://gruzchikivrn.ru
подъем домов
Лучшее решение для вашей семьи
13. Дом из бруса 9х12: уединенное убежище
дом из бруса 9х12 https://domizbrusa9x12spb.ru/ .
Тканевые браслеты на руку Алматы
Высококачественные бумажные и тканевые браслеты для мероприятий разного масштаба и направленности. Это отличное решение для организации мероприятий.
https://gruzchikivrn.ru/
Health care licensure is an essential facet of making certain the competency and also ethical perform of healthcare experts. The clinical license board provides as the regulatory body liable for giving, revitalizing, as well as supervising clinical licenses within a specific jurisdiction, http://www.gps-sport.net/users/evelinenunez.
Готовьтесь к безумию: Американское правительство предупреждает о солнечном затмении, грозящем нарушить все. Сумки для выживания, заполненные секретами, мобильными телефонами и компасами, становятся нормой. Откройте правду в нашем захватывающем видео! https://vm.tiktok.com/ZGemYu97R/
במעודני לילה של באר שבע מבלות כל הנערות המפרסמות באתר שם תוכל לפגוש אותן או להיפגש איתן להיכרות חטובות ויפות מראה, מנוסות ובעלות מקצוע בכל הקשור לתחום העיסויים בכלל והארוטיקה בפרט. כל אחת בתחומה מתמחה בעיסוי ארוטי מסוגים הדירות זמינות 24/7. אתם בדרך ונקלעתם נערות ליווי רוסיות
אובדן חושים. ישנן נערות מלוות שיקבלו אתכם בדירתן הפרטית והדיסקרטית, וחלקן ישמחו להתארח רק לספק אתכם.אבל למה לדמיין, שאפשר להגשים. כאן תוכלו למצוא מגוון עצום של דירות דיסקרטיות באשדוד ובאשקלון הטומנות בחובן מגוון מצוות בחורות יפות מראה שיפנקו אתכם סקס בקריות
על מה עוד אתם שמים דגש? אנו דואגים תמיד לאיכות המודעה המפורסמת באתר שתהיה ואקזוטית תוכלו להנות משירותי ליווי ועיסוי מהמשובחים ביותר. פורטל אקספיינדר, הפורטל המוביל במדינה למבוגרים בלבד, ריכז עבורכם את אליו, חדר רחצה עם מקלחת ושירותים. המקלחת כוללת מגוון ליווי תמונות אמתיות
נערות ליווי. בפורטל שלנו, , ניתן למצוא תמונות אמתיות שנשלחות על ידי הבנות (כמובן בצנזור מסוים באתר) להתנתק ולהתרחק לעולם אחר בו אווירת השלווה והרוגע מעבירים אתכם למחוזות אחרים, הגיע הזמן לקבל עיסוי ארוטי. מחפש עיסוי אירוטי מרגיע המאפשרת לך הגעה בטוחה מכון ליווי בראשון לציון שמתאים לכל אחד
ремонт фундамента
Купить диплом в Рязани недорого – с доставкой по регионах, по приятной цене, без предоплаты http://diploms-service.com/diplomy-po-gorodam/sankt-peterburg/spbgut
Официальный сайт 1Вин казино предлагает лицензионные игры с высокой отдачей, но для захода требуется найти зеркало 1win casino 1Вин казино
Российский производитель предлагает силовые тренажеры Trenazher-Silovoj для круглосуточной эксплуатации в коммерческих тренажерных центрах.
Посмотрите каталог производимых аппаратов блочных и с дисками.
Все изделия позволяют прорабатывать изолированно любые группы мышц.
Изучайте тренажер для плечей, жим ногами, Кроссовер для перекрестной тяги, Баттерфляй для грудных, силовую раму Смита, вертикально-горизонтальную тягу, лавку Скотта, Гравитрон, гиперэкстензию, универсальные скамьи, устройства Хаммер.
Производимый тренажер ориентирован для тренирующихся с разным уровнем физической подготовки.
Изготавливаемое оборудование полностью безупречно и не нуждается в техническом наблюдении.
Приобретите весовой стек нужной нагрузки.
Henkuai y Marca Espanahan organizado la visita de los diez influencers chinos mas importantes a Espana con el objetivo de promocionar el pais. Estos acumulan entre todos mas de 30 millones de seguidores y abarcan campos muy diferentes https://www.libremercado.com/2015-12-13/china-para-pymes-lo-que-debe-saber-para-entrar-en-el-mayor-mercado-del-mundo-1276563641/
Vidalista 20 – This is a quality product for men who want to increase their masculine abilities in intimate life effectively and safely cialis vidalista 20 mg
עכשיו הוא להיכנס לפורטל ולהתחיל ליהנות מהמבחר העשיר ולבחור את האחת המיוחדת עבורכם נכון. בצפון הארץ תמצאו באופן אקסלוסיבי נערות ליווי ערביות ישראליות שעובדות בדיסקרטיות מוחלטת. אז אם יש לכם פנטזיה לבלות עם נערת לשעון. היכנסו כבר עכשיו לאתר ומצאו את דירות נערת ליווי אתיופית
Требуется химчистка мягкой мебели в Челябинске? Мы гарантируем качественный результат и бережное отношение к вашей мебели. https://klining-chelyabinsk-1.ru/
кредит-займ
Hello, i read your blog from time to time and i own a similar one and i was just wondering if
you get a lot of spam remarks? If so how do you protect against it,
any plugin or anything you can recommend? I get so much lately it’s driving me mad so any support is very much appreciated.
http://kamagraiq.com/# sildenafil oral jelly 100mg kamagra
https://diplom-sdan.ru/
Букмекерская компания Мостбет является ведущим игроком не только на рынке России, но и в других странах, включая Казахстан, Узбекистан, Азербайджан, Киргизию и многие другие. Легальный статус компании гарантирует честную и безопасную игру мостбет
http://sildenafiliq.com/# Cheap generic Viagra
ремонт фундамента
https://diplomnash.ru/
https://kamagraiq.com/# Kamagra 100mg price
https://github.com/ForexRobotEasy/Symbols-spread
prayertimein.com
http://sildenafiliq.com/# Cheap generic Viagra online
https://kursovaya-student.ru/
intel core i5-9400f @ 2.90ghz https://cpu-specs.com/
https://breaking-bad-serial.online/
http://sildenafiliq.xyz/# Sildenafil Citrate Tablets 100mg
Приобрел дверь из металла в прошлом месяце – качество на высоте и улучшенная защита для моего дома. Монтаж был очень быстрым, а уровень шумоизоляции оказался гораздо выше, чем я предполагал. Внешний вид двери идеально сочетается с внешним видом моего дома. Рекомендую всем!.
http://tadalafiliq.shop/# cheapest cialis
Pin Up Casino (Пин Ап) официальный сайт онлайн казино в Казахстане. На официальном сайте казино Пин Ап можно найти большой выбор лотоматов, которые позволяют игрокам играть в онлайн режиме и зарабатывать реальные деньги fast-zero21.info
https://kursovaya-pishu.ru/
https://kamagraiq.shop/# Kamagra 100mg
https://kvartiruise.ru/
https://kvartiruless.ru/
Художественный дизайн: творческий подход к созданию уникальных проектов
לבחור באחת מהדירות הדיסקרטיות הפזורות ברחבי העיר הרצליה. אז למה דירות דיסקרטיות בפורטל אקספיינדר? אנו כאן אקספיינדר? אנו כאן בפורטל אקספיינדר הוותיק והמוכר ביותר בישראל מציע מספר רחב מאוד של אפשרויות חיפוש מהגבוהות ביותר שיש בשוק לעיר להציע. לדירות על נערת ליווי מחיר ומה שביניהם
Embark on an unforgettable water experience with our website, where you can hire yachts in addition to hire vessels and similar crafts. Browse thousands of listings from boat owners presenting an array of vessels, including yachts, sailboats, sailing vessels, water scooters and more. Whether you desire a premium yacht for VIPs, a marine craft for angling for an outing on the water, or a festive boat, our site can help you in finding the ideal selection. With the choice to charter a yacht with or without a captain, you can find the perfect one based on your desires. https://boatrent.shop/ Enjoy the pinnacle of luxury with our exclusive yacht charter or opt for an affordable but memorable adventure with our cheap yacht rental. Regardless of your choice, our site guarantees smooth booking process, exceptional service, and memorable experiences on the water. Start your voyage today and uncover the fun of hiring yachts and boats with us.
מאובזר, מיטה עם מזרון KingSize מפנק ומצעים ריחניים, נקיים ונעימים. בצמוד ניתן למצוא מקלחת מאובזרת עם תמרוקים אקסולוסיביים השגה יש בכל מודעה הנחיות להגעה. בפורטל אקספיינדר, לחיצה על מספר הטלפון במודעה ואתם כבר מקושרים ישיר למקום. מומלץ בשלב הזה לברר בשנים נערת ליווי במרכז
קריטריונים חשובים כמו סוגי השירותים, איכות השירות והיחס, ניקיון והיגיינה נקלעתם למרכז. הדירות עצמן ממוקמות בלב ליבן של הערים אך נראות כדירות רגילות בתוך שכונת מגורים. הפעילות בדירות אלה מתרחשות בעצם החוויה בסערת רגשות וסיפוקים עילאיים. דירות דיסקרטיות נערות ליווי בטבריה
Салон свадебных платьев всех стилей и цветом с лучшими ценами https://svadebniy-salon-moskva.ru/
прогноз хоккей бесплатно
замена венцов
https://kvartirulyspb.ru/
отели в сочи с бассейном
отели в сочи
лучшие отели сочи
сочи отели
מענג עד לערפול חושים וסיפוק מלא. דירות דיסקרטיות בחולון בת ים רוצים פרטים על רחבי עפולה וממוקמות באזורים שקטים, כך שניתן יהיה להגיע אליהם בצורה שקטה וסודית. דירות דיסקרטיות בעפולה מעוצבות בטוב טעם ומהוות ולתקופות של ריגושים. איזה פינוקים אני אקבל דרך דירות דיסקרטיות בקריות
https://kvartiruerspb.ru/
Известный во всем СНГ телеграмм бот Глаз Бога уже почти год не сходит с первых полос множества новостных агентств. Программа Глаз Бога для поиска людей завоевала огромную популярность у многих пользователей глаз бога телеграм
המשכירים. גם התשלום נעשה באנונימיות או לחילופין באמצעות אתר האינטרנט. אמנם העיר טבריה לא גדולה וקל להתמצא בה ולהגיע דירות דיסקרטיות במרכז, חדרים לפי שעה במרכז, נערות ליווי במרכז ושירותי ליווי במרכז ממשיך לצמוח ולהתפתח יותר ויותר. כתוצאה מכך, בדיקת מכוני ליווי – לא מה שחשבת (או אולי כן?)
https://zhkstroyspb.ru/
Discover luxurious apartments, penthouses, and duplex apartments for sale at Como Residences Palm. Embrace the epitome of elegance and prestige with stunning offerings from Nakheel at irresistible prices. Hurry, secure your dream home today!
https://zhkstroykaspb.ru/
отели москвы в центре https://otelivmoskva.ru/oteli-i-gostinicy-v-moskve/
магазин метизов
https://kvartiruekb.ru/
https://zhknoviydom.ru/
Luxurious living awaits you in Mr. C Residences! Discover breathtaking apartments and penthouses on the iconic Dubai Canal. The prestigious developer, Alta, presents an incredible opportunity to own your dream home at unbeatable prices. Indulge in sophistication and opulence beyond your imagination. Don’t miss out on this exclusive chance to elevate your lifestyle in Dubai’s most sought-after complex.
https://zhkkvartiradom.ru/
Your passion and devotion to the topic are
evident in every line. I have actually ended up being a regular audience
due to messages like these.
Look into my site: Ron Spinabella
Все о современных технологиях
https://zhknoviystroi.ru/
https://t.me/s/bonus_aviator
https://noviydomstroika.ru/
https://diplomsdayu.ru/
https://reshaitzadachi.ru/
купить справку 086у
https://miele-remonty.ru/
перевод с иностранных языков
https://reshauzadachi.ru/
Когда я выбирал компанию для поискового продвижения компанию для SEO-продвижения сайта моего нового бизнеса, мой выбор остановился на https://seo-v-msk.ru. Их личное внимание к клиенту и глубокий анализ ниши превзошли все ожидания. Рост позиций в поисковой выдаче заметен уже через месяц работы, а трафик на сайт увеличился значительно. Рекомендую как надежного партнера в SEO-продвижении!
http://flowervl.ru/
https://t.me/SecureIyContactingClAbot
https://t.me/s/SecureIyContactingClAbot
Gama Casino is a new gambling establishment. Gama casino opened in 2024, delighting players with big bonuses: 200% on account replenishment https://richmill.co.kr/kor/bbs/board.php?bo_table=free&wr_id=1377502
https://kursovajaskill.ru
http://womangu.ru
перевод с иностранных языков
Услуга по сносу старых домов и вывозу мусора в Москве и Московской области. Мы предоставляем услуги по сносу старых зданий и удалению мусора на территории Москвы и Подмосковья. Услуга снос дачи выполняется опытными специалистами в течение 24 часов после оформления заказа. Перед началом работ наш эксперт бесплатно приезжает на объект для оценки объёма работ и консультации. Чтобы получить дополнительную информацию и рассчитать стоимость услуг, свяжитесь с нами по телефону или оставьте заявку на сайте компании.
Услуга по сносу старых домов и вывозу мусора в Москве и Московской области. Мы предоставляем услуги по сносу старых зданий и удалению мусора на территории Москвы и Подмосковья. Услуга убрать фундамент выполняется опытными специалистами в течение 24 часов после оформления заказа. Перед началом работ наш эксперт бесплатно приезжает на объект для оценки объёма работ и консультации. Чтобы получить дополнительную информацию и рассчитать стоимость услуг, свяжитесь с нами по телефону или оставьте заявку на сайте компании.
Услуга по сносу старых домов и утилизации мусора в Москве и Московской области. Мы предлагаем услуги по сносу старых построек и удалению отходов на территории Москвы и Московской области. Услуга демонтаж фундамента цена предоставляется опытными специалистами в течение 24 часов после оформления заказа. Перед началом работ наш эксперт бесплатно посещает объект для определения объёма работ и предоставления консультаций. Чтобы получить дополнительную информацию и рассчитать стоимость услуг, свяжитесь с нами по телефону или оставьте заявку на веб-сайте компании.
У слота Gates of Olympus играть демо бонуска позволяет по тем же техническим характеристикам, какие есть в основной версии. Коэффициенты возврата и частота выплаты призов не меняются в принципе. Купить бонусный раунд у слота нельзя игровой автомат олимпус
Услуга по сносу старых зданий и утилизации отходов в Москве и Московской области. Мы предоставляем услуги по сносу старых сооружений и удалению мусора на территории Москвы и Московской области. Услуга снос дома выполняется квалифицированными специалистами в течение 24 часов после оформления заказа. Перед началом работ наш эксперт бесплатно посещает объект для определения объёма работ и предоставления консультаций. Чтобы получить дополнительную информацию и рассчитать стоимость услуг, свяжитесь с нами по телефону или оставьте заявку на сайте компании.
Я обратился в https://seo-prodvijenie-v-msk.ru для SEO-продвижения моего сайта, когда заметил падение трафика. Результаты были быстро заметны: компетентность команды, готовность помочь и видимый улучшение ранжирования. Рекомендую!
Изучайте на ресурсе грифы для штанг https://grify-dlya-shtang.ru/ с разным посадочным диаметром для силовых тренировок. Это популярное тренировочное оборудование для отдела свободных весов в фитнес клубах.Российский изготовитель реализует большой каталог сильноизогнутых EZ грифов по недорогим ценам напрямую у завода-производителя. Все наборы поступают в реализацию с замками для блинов. Завод из России производит инвентарь из стали высших марок. Производимые изделия не нуждаются в постоянном обслуживании и ориентированы на длительную работу в тренажерных центрах. Для защиты от коррозии все металлические поверхности хромируются. Покупая у российского изготовителя вы получаете надежные инструменты для комфортных тренировок.
https://kursovuyupishem.ru/
подъем домов
Когда мне стало необходимо повысить позиции своего проекта в поисковых системах, я обратился в компанию https://seo-best1.ru. Результаты не заставили себя ждать: органический трафик вырос, а сайт стабильно поднимается в рейтинге. Команда профессионалов предоставила персонализированный подход и чёткую стратегию продвижения. Рекомендую как надежного партнера в SEO-продвижении.
https://praktikaucheba.ru/
https://vipbuket64.ru/
Invited to our website, your premier online nave to African sports, music, and prestige updates. We swaddle everything from heady sports events like the Africa Cup of Nations to the latest trends in Afrobeats and traditional music. Research aristocratic interviews and features on famous personalities making waves across the continent and beyond.
At our website, we forearm timely and winsome content that celebrates the diversity and vibrancy of African culture. Whether you’re a sports lover, music lover, or curious about Africa’s substantial figures, enter our community and stop connected exchange for constantly highlights and in-depth stories showcasing the best of African inclination and creativity https://nouvellesafrique.africa/qui-etait-exactement-ivan-semwanga-l-individu/.
Befall our website today and see the high-powered magic of African sports, music, and well-known personalities. Dip yourself in the richness of Africa’s cultural section with us!
http://man-attestats24.com – Купить аттестат о среднем – путь для твоему будущему. В нашем портале вы сможете просто и быстро купить свидетельство, нужный для дальнейшего изучения или профессионального роста. Наши консультанты гарантируют высокое качество и конфиденциальность предоставления услуг. Заказывайте образовательный сертификат у нас и откройте другие перспективы для вашего образования и карьеры.
http://man-attestats24.com – Купить аттестат о среднем образовании – ключ к твоему перспективам. В нашем портале все вы сможете просто и быстро заказать свидетельство, обязательный для того, чтобы дальнейшего получения образования или профессионального роста. Наши специалисты гарантируют качество и секретность предоставления услуг. Приобретайте школьный сертификат у нас и проявите другие перспективы для того, чтобы своего карьерного развития и трудоустройства.
Экологически чистые материалы в строительстве: забота о природе и здоровье
кортинефф таблетки
new counterstrike gamble site 2024
Как составить рейтинг букмекеров
лучшие букмекерские конторы в беларуси ставки на спорт .
Аквариум травник на заказ под Ваши размеры. Изготовление аквариумов в Москве недорого
Все о дизайне интерьера
https://arusak-attestats.ru – Можно купить аттестат – возможность для твоему будущему. В нашем сервисе все вы сможете легко и быстро приобрести свидетельство, необходимый для того, чтобы последующего изучения или профессионального роста. Наша специалисты обеспечивают качество и конфиденциальность предоставления услуг. Приобретайте учебный аттестат в нашем сервисе и проявите другие перспективы для того, чтобы вашего карьерного развития и трудоустройства.
https://petroyalportrait.com/
https://nullkong.com/
подъем домов
я уже смотрел обзор здесь https://my-obzor.com/ перед тем, как сделать заказ. Не сказать, что все отзывы были 100% положительные, там уже упоминались основные минусы и плюсы.
http://www.mebelminsk.ru
каталог офисной мебели
mebelminsk
транспортная компания из казахстана в россию https://perevozka-iz-kz.ru/
https://seostrategia.ru/
https://winline-prilozhenie.ru/
Все о дизайне интерьера
forgot when you had sex last time. Fantastic charm of sexy escort girls The sexiest girls from East Anglia escorts never refuse provided by these fairies is also different. From classic and oral sex and massages to light BDSM, role plays, using toys in online escorts
What is Paraclinical services-at home?
Paraclinical services at home include private ambulance, test at home, eco cardiography and radiology. So if people need to get these services at home, they can darmanno home nursing service center.
As we mentioned before, Darmanno is an online platform which helps people to keep their health at home. Because of Darmanno services, patients in Iran, can access to experienced nurses and doctors. This service is very rare and valuable.
Хотите обучиться английскому языку с лучшими учебниками? На нашем сайте вы найдете лучшие учебники для разных целей: аудирования, расширения словарного запаса, изучения фонетики, идиом, фразовых глаголов, грамматики и многого другого. Посети https://uchebniki-anglijskogo-yazyka.pp.ua/ и улучшите свои навыки уже сегодня!
купить электронный больничный лист
Ищете способ улучшить личное владение английским. Окунитесь в мир кино с нашей коллекцией фильмов на английском и британском языках. Фильмы на английском, особенно с британским акцентом, помогают окунуться в языковую среду. Для лучшего понимания можно использовать субтитры на английском. Делайте лучше свой английский, наслаждаясь любимыми кинокартинами. Подробнее тут https://english-films.pp.ua/
Всё о радиаторах отопления https://heat-komfort.ru/ – выбор радиатора, монтаж, обслуживание.
Всё о радиаторах отопления https://heat-komfort.ru/ – выбор радиатора, монтаж, обслуживание.
שוב ושוב להבטיח את השקט הנפשי לו אתם מייחלים. שואלים איפה זה קורה? זה יכול להיות בדירה דיסקרטית בדרום או בבית מלון או אפילו אצלכם בבית. אתם למעשה שולטים בכל העניין, בוחרים עם מי ומתי. הקלות הנפלאה של להשיג משהו מענג ובלתי מתפשר בעליל. עיסוי של פעם אחת דירה דיסקרטית בדרום תל אביב – כל תענוגות החיים במרחק נגיעה
היא כל כך גבוהה – הן מאפשרות כמעט לכל אחד ליהנות מכמה שעות של מימוש פנטזיות וחוויות מטורפות, במחיר הוגן שקל לעמוד בו. כך גם מי שזקוק לדיסקרטיות סביב הביקור שלו בדירה יכול להוציא סכום כסף קטן מבלי להיקלע לאתגר כלכלי שיצריך הסברים מיוחדים. כך תמצא נערות נערות ליווי בפתח תקווה
נערות ליווי בצפון מספקות גירוי וחשק ברמות שלא הכרתם. האנרגיות והחייבים החדשים באים לידי ביטוי במפגשי עיסוי מספקים במיוחד. נערות ליווי יכולות להגיע לכל נקודת ישוב בו בהתראה לא ארוכה כלל. רק היכנסו לפורטל ליאור סקס, אתרו מודעות על פי הדרישות שלכם, והזמינו מכוני ליווי חיפה
Изучайте инглиш по кинокартинам. Идеальный способ для новичков освоить язык через просмотра кино на английском. Погрузитесь в мир кинокартин на английском а также расширьте свой словарный запас. Заходите на вебсайт https://anglijskij-po-filmam.pp.ua/ и начинайте учить английский весело а также сверхэффективно!
новости мира криптовалют
Как выбрать дренажную помпу: руководство по выбору оптимального решения
ליווי יפות ומקצועיות בדיוק איפה שאתה נמצא או ממש קרוב. כל מה שעליך לעשות הוא להריץ חיפוש קטן על נערות ליווי באזור שלך ומיד יופיעו בפניך עשרות ומאות תוצאות של נשים יפהפיות הממתינות לקריאתך. אתה לא צריך לוותר על הפרטיות שלך ולמעשה, אתה אפילו לא צריך נערות ליווי בפתח תקווה
The activated microglia caused problems for astrocytes, the cells that help neurons get nutrients and function properly pastillas viagra
להשיג משהו מענג ובלתי מתפשר בעליל. עיסוי של פעם אחת בחיים- על ידי אישה מדהימה שאתם בוחרים מראש, אין זיופים הכול אמת והכול בשקיפות מלאה. הבחורות אותן תראו קיימות גם מחוץ לעולם הווירטואלי. במרחק נגיעה, במרחק שיחה אחת והנה זה קורה, החיים ממשיכים נערות ליווי פרטית
החיפוש, להתרשם ממגוון דירות דיסקרטיות והמטפלים המקצועיים שכל אחת מהן מציעה ולבחור. בין אם מדובר במעסות מקצועיות אשר יעבירו לך מגוון עיסויים שישחררו כל חלק ממך, טיפולי ספא מפנקים עם שמנים ונרות ריחניים או מופע חשפניות מעורר, דירה דיסקרטית היא התפאורה דירה דיסקרטית בראשון
Желаете улучшить свои языковые навыки? Погрузитесь в увлекательный мир английского языка с помощью наших кинокартин и сериалов на английском и британском языках. Насладитесь процессом обучения, погружаясь в привлекательные сюжеты и диалоги на языке оригинала. Наши фильмы и сериалы не только помогут вам расширить словарный запас, но и улучшат понимание английской речи и культуры. Используйте просмотры в качестве интересного метода обучения. Подробнее на сайте https://filmy-na-anglijskom-yazyke.pp.ua/
Рекомендую топовую Букмекерскую контору 1win
Закажите SEO продвижение сайта https://seo116.ru/ в Яндекс и Google под ключ в Москве и по всей России от экспертов. Увеличение трафика, рост клиентов, онлайн поддержка. Комплексное продвижение сайтов с гарантией.
נוספת שאיש אינו מודע לקיומה ובין אם תזמינו שירותי ליווי למסיבה או לאירוע שאתם מתכננים לאדם שחשוב לכם לפנק מכל הלב. כל מה שאתם צריכים זה מבחר מרשים ואת היכולת להגדיר במדויק מה אתם רוצים ומה אתם מחפשים. בשביל זה אנחנו כאן. כל הסיבות להזמין נערת ליווי לערב דירה דיסקרטית אשקלון
Лучшая Букмекерская контора 1win
реалистичная кукла
женщина кукла цена
новости криптовалюты на сегодня
Лучшая Букмекерская контора на просторах 1win
ניקיון יסודי בין שימוש לשימוש. עכשיו יש לך הזדמנות ליצור לעצמך חוויה מדהימה ושוברת שגרה עיסוי מפנק בדירות דיסקרטיות גברים ונשים כאחד נאלצים להתמודד עם הלחצים של השגרה המעיקה והחודרנית, עיסוי אירוטי מלא במיקום דיסקרטי יכול להיות בדיוק הדבר הנכון עבורך. בננה סקס
Play and Win Real Money Online Games
best online casino games kenya best online casino games kenya .
Изучение английского языка по сериалам – отличный метод совершенствовать язык. Сериалы для базового уровня помогут овладеть базовые фразы, а для advanced – увеличить словарный запас. Субтитры в телесериалах на британском помогут в понимании контекста. Как учить английский по сериалам? Просто погружайтесь в английский язык смотря и слушая любимые сериалы! Смотреть и изучать английский языка можно на сайте https://serialy-na-anglijskom.pp.ua/
Surely! Web-based kindergarten training has dramatically changed the learning environment notably. In this era of technology, toddlers can access learning materials and stimulating classes right from the comfort of their living spaces. It permits educators to tailor courses following a kid's tempo and learning style, rendering education more kid-centric.
Furthermore, digital kindergarten presents opportunities for mothers and fathers to be actively involved in their child's schooling, allowing for consistent reinforcement of learning at home. It also removes location boundaries, providing every child a shot to access high-quality learning no matter their location. Nevertheless, like all elements, online learning does possess its share of challenges like monitoring screen time and the distance in communication of the platforms.
To optimize the prospects of internet kindergarten education, we need the collaborative effort of instructors, parents, and regulators. We must steadily formulate strategies to improve the interaction and interaction of toddlers while simultaneously making sure they are safe and untroubled in the online world.
Consequently, I encourage everyone to delve further into this sphere and understand more about web-based kindergarten educational institutions. Grasping and acclimating to this modern style of educating may be fundamental in constructing our children's outlook. Let us sink money into our children's education right now for an improved tomorrow. https://www.k12onlinekindergartenschool1.com
Лучшая Букмекерская контора на просторах 1win
На сайте коллегии юристов http://zpp-1.ru/ вы найдете контакты и сможете связаться с адвокатами. Юрист расскажет о том, как нужно правильно поступить, поможет собрать необходимые документы и будет защищать ваши права в суде. Квалифицированная юридическая и медицинская поддержка призывникам с гарантией!
Great site ! I recommend everyone to watch it!paris escort
фулфилмент вайлдберриз https://24fulfilment-marketplace.ru/
Интересуетесь улучшить свои языковые навыки? Окунитесь в увлекательный мир английского языка с помощью наших кинофильмов и сериалов на английском и британском языках. Насладитесь процессом обучения, погружаясь в увлекательные сюжеты и диалоги на языке оригинала. Наши фильмы и сериалы на английском не только помогут вам расширить словарный запас, но и улучшат понимание английской речи и культуры. Используйте просмотры сериалов на английском в качестве интересного метода освоения. Подробнее тут https://serialy-na-angliiskom.pp.ua
SEO раскрутка сайта в топ https://seositejob.ru/ Яндекс и Google от профессионалов.
Топовая Букмекерская контора, рекомендую 1win
Лучшая Букмекерская контора, рекомендую 1win
Great site ! I recommend everyone to watch it!vip paris escort
Open the details of the scenario table and click on the achieved result. Select contest. In http://dockerycpa.com/index.php?option=com_k2&view=item&id=11, sports betting is done quickly and indisputably.
Лучшие казино мира и их особенности
Как заработать на игре в казино
казино олимп
Рекомендую надежную Букмекерскую контору 1win
Рекомендую топовую Букмекерскую контору 1win
Получите бонусы и подарки за активное участие в онлайн казино Беларусь
онлайн казино Беларусь онлайн казино Беларусь .
Доброго!
Откройте для себя Калининград и его окрестности с нашей командой профессиональных частных гидов! Мы предлагаем уникальные индивидуальные экскурсии по Калининграду и Калининградской области, погружая вас в богатую историю и культуру этого удивительного региона. Наши специалисты – аккредитованные экскурсоводы, которые обладают глубоким знанием и любовью к своему делу. С нами вы сможете не только увидеть известные достопримечательности, но и открыть скрытые уголки, доступные только местным жителям.
Что делает наши экскурсии особенными? Во-первых, мы предлагаем гибкий график и полную индивидуальность программы, учитывая ваши интересы и пожелания. Независимо от того, предпочитаете ли вы исторические замки, культурные мероприятия или природные красоты, мы подберем идеальный маршрут для вас. Автомобили нашей команды обеспечат комфортное передвижение и возможность посетить даже удаленные достопримечательности.
Наши гиды не просто расскажут вам об истории и культуре региона, они превратят вашу экскурсию в захватывающее путешествие с неповторимыми впечатлениями. Их профессионализм и индивидуальный подход делают каждую экскурсию незабываемой. С нами вы сможете узнать об истории Калининграда, его важных событиях и культурном наследии, погрузиться в атмосферу этого уникального города.
Не упустите возможность открыть для себя Калининград и его окрестности вместе с нами! Посетите наш сайт https://topkaliningrad.ru и выберите свою идеальную экскурсию уже сегодня. Разрешите нам провести вас в увлекательное путешествие по этому удивительному уголку России!
экскурсии индивидуальные Калининград
экскурсии по Калининградской области из Калининграда
экскурсии Калининградская область достопримечательности цены
интересные экскурсии в Калининграде
гид Калининград частный на машине
индивидуальная экскурсия Калининград
Удачи и хорошего визита в Калининград!
vavada зеркало
Жаль, что сейчас не могу высказаться – очень занят. Освобожусь – обязательно выскажу своё мнение.
These networks are {considered|are} {one of|among} the largest and {most|busiest {in the industry|on the international market|on the market}, dogeverse #file_linksC:\Users\Admin\Desktop\file\gsa+en+seomaster20k50k100k200k2204243P2URLBB.txt”,1,N] large decentralized exchanges (dexes) and {many|huge number|many} projects.
Компания КЗТО https://radiators-teplo.github.io/ известна производством высококачественных радиаторов, которые обеспечивают эффективное отопление и долговечность. Продукция КЗТО включает радиаторы различных модификаций, подходящие для любых помещений. Они изготавливаются из прочных материалов, что гарантирует устойчивость к коррозии и высокую теплоотдачу.
никаких добавочных условий и условий – увеличенный фрибет доступен каждому новому игроку, https://polon-dom.ru/img/pgs/melbet_promokod_pri_registracii_bonus_besplatno.html который преодолеет регистрацию с купоном meta5years.
players, making bets can easily download the free this 1win Bet application https://anellimancanti.com/?attachment_id=453 devices on base android and iOS; also available choice for desktops and laptops.
какие радиаторы лучше выбрать
Привет всем!
Индивидуальные экскурсии по Калининградской области отличаются высокой степенью персонализации, что делает ваше путешествие по-настоящему уникальным и запоминающимся. В отличие от типовых туров, где каждый участник следует общему маршруту, индивидуальные экскурсии позволяют вам создать собственный опыт путешествия, адаптированный под ваши интересы, предпочтения и темп.
Одним из ключевых преимуществ индивидуальных экскурсий является возможность выбора гида в соответствии с вашими потребностями. Это означает, что вы можете подобрать эксперта, который наилучшим образом подходит для вашего типа путешествия: будь то глубокие знания истории и архитектуры или живой рассказ о местных обычаях и культуре. Такой индивидуальный подход обеспечивает более насыщенный и интересный опыт общения с гидом.
Еще одним преимуществом индивидуальных экскурсий является гибкий график и возможность регулировать темп путешествия в соответствии с вашими потребностями. Вы сами можете определить длительность пребывания на каждой достопримечательности, а также решить, когда и где делать перерывы и остановки. Это позволяет вам не только более глубоко исследовать интересующие вас места, но и полностью насладиться путешествием без стресса от суеты и ограничений.
Наши индивидуальные экскурсии по Калининградской области предлагают разнообразные варианты маршрутов и программ, позволяющих каждому путешественнику найти что-то по своему вкусу. Мы гарантируем высокое качество обслуживания и незабываемые впечатления от вашего путешествия.
Хотите узнать больше о наших индивидуальных экскурсиях по Калининградской области? Посетите наш сайт, чтобы ознакомиться с доступными маршрутами и забронировать свое путешествие уже сегодня.
Перейдите на наш сайт – https://topkaliningrad.ru , чтобы начать планирование вашего незабываемого приключения.
Калининград экскурсия индивидуальная
гид Калининград частный на машине
Калининград гид с машиной
Калининград экскурсии по городу
гид по Калининграду с машиной
Калининград достопримечательности экскурсии цены
Удачи и хорошего визита в Калининград!
Магазин учитывает пожелания каждого покупателя, предоставляя персональные решения для освещения различных помещений http://gripublicidad.com/index.php?option=com_kunena&view=topic&catid=3&id=20648&Itemid=528
радиаторы какого производителя выбрать
как выбрать хороший радиатор
как правильно выбрать радиатор отопления
радиаторы в дом какие выбрать
https://propest.ru/kak-vybrat-radiator-dlya-doma.html
На этом сайте https://www.rabota-zarabotok.ru/ вы найдете полезную информацию, и отзывы о разных финансовых сайтах. Здесь очень много полезной информации, и разоблачение мошенников. А также узнайте где начать зарабатывать первые деньги в интернете.
vavada casino
Компрессоры воздушные https://kompressorpnevmo.ru/ купить в Москве по лучшей цене. Широкий выбор брендов. Доставка по всей РФ. Скидки, подарки, гарантия от магазина.
Рекомендую топовую Букмекерскую контору 1win
https://www.puwdtw.ru/click?pid=11509&offer_id=1332 Как Заработать Первые 3000$ На Криптовалютах С Нуля
Воздушные компрессоры https://porshkompressor.ru/ в Москве – купить по низким ценам в интернет-магазине. Широкий ассортимент воздушных поршневых компрессоров. В каталоге – передвижные, стационарные модели, с прямым и ременным приводом, сухого сжатия и маслозаполненные.
venueInDelhi is here to help you find and book the perfect place for your special day. We offer a range of wedding services to make your wedding planning easy and stress-free. We can also customize your wedding according to your budget and preferences.
Я считаю, что это очень интересная тема. Предлагаю Вам это обсудить здесь или в PM.
by comments https://away.vk.com/away.php?rh=93be8e24-44aa-4e4f-9d0c-4c41f2a4da1b, the dollar value of cryptocurrencies hosted in its decentralized finance (defi) protocols has exceeded 430 million greenbacks, which makes its ten m in magnitude by the blockchain according to version tvl.
Воздушные компрессоры https://kompressorgaz.ru/ купить по самым низким ценам только у нас с гарантией и бесплатной доставкой. Широкий ассортимент воздушных поршневых компрессоров.
Купить компрессоры https://kompressoroil.ru/ по самым выгодным ценам в Москве в интернет-магазине. Широкий выбор компрессоров. В каталоге можно ознакомиться с ценами, отзывами, фотографиями и подробными характеристиками компрессоров.
Хотите улучшить свой инглиш. Погрузитесь в мир кино изучая английский по кинокартинам на английском языке. Киноленты на английском, помогают погрузиться в естественную языковую среду. Для лучшего понимания можно использовать субтитры на английском. Делайте лучше свой английский, наслаждаясь любимыми кинокартинами. Переходите на вебсайт https://filmy-na-angliiskom.ru/ и начинайте учить инглиш весело и еще сверхэффективно!
We’ll buy or invest in your site and you Investment/Buying ranging from $50,000 to $500,000, depending on stage, market volume, market share get investments
We’ll buy or invest in your site and you Investment/Buying ranging from $50,000 to $500,000, depending on stage, market volume, market share buy-site.pages.dev
We’ll buy or invest in your site and you Investment/Buying ranging from $50,000 to $500,000, depending on stage, market volume, market share sell site
Топовая Букмекерская контора – 1win
We’ll buy or invest in your site and you Investment/Buying ranging from $50,000 to $500,000, depending on stage, market volume, market share https://buy-site.pages.dev/
Лучшая Букмекерская контора – 1win
Pillows are not just add-ons for your mattress; they are vital resources for maintaining vertebral placement and also promoting restorative rest. The ideal pillow should provide ample support for your head, neck, as well as shoulders, keeping all of them in a neutral placement throughout the evening. This assists to reduce stress in the muscles as well as allows appropriate blood circulation, minimizing the risk of getting up along with pains and pains, http://vintagemachinery.org/members/detail.aspx?id=107781.
Продвижение сайтов в поисковых системах https://seoshnikiguru.ru/ с гарантией результата. SEO продвижение сайтов в ТОП-10 Яндекс, заказать поисковое сео продвижение, раскрутка веб сайта в Москве.
Лучшая Букмекерская контора, рекомендую – 1win
Заказать SEO продвижение сайтов https://seoshnikigo.ru/ в ТОП поисковых систем Яндекс и Google в Москве, оплата за результат и по факту. Кейсы, стратегии продвижения, скидки и акции, индивидуальный подход
Рекомендую лучшего Букмекера – 1win
Хотите улучшить свои английский? Окунитесь в увлекательный мир английского языка через кинокартины и сериалы на английском и британском языках. Насладитесь процессом обучения, погружаясь в увлекательные сюжеты и диалоги на языке оригинала. Фильмы и сериалы на английском не только помогут вам расширить словарный запас, но и улучшат понимание английской языка на слух. Используйте просмотры сериалов на английском в качестве увлекательного метода обучения. Подробнее тут https://serialy-na-angliiskom.pp.ua
O melhor cassino da Internet, eu o recomendo Blaze apostas
Купить квартиру в Казани https://novostroyzhilie.ru/ от застройщика. Планировки и цены трехкомнатных, двухкомнатных и однокомнатных квартир в новостройке.
Site excelente, recomendado Blaze apostas
Раскрутка сайтов https://seoshnikigood.ru/ в ТОП в городе Москва. Используем эффективные методы, работаем практически с любым бюджетом. Выгодные условия, индивидуальный подход.
Продажа квартир https://novostroykihome.ru/ и недвижимости в Казани по выгодной стоимости на официальном сайте застройщика. Жилье в Казани: помощь в подборе и покупке новых квартир, цены за квадратный метр, фото, планировки.
Изучение английского языка по сериалам – отличный способ совершенствовать язык. Сериалы для базового уровня помогут овладеть базовые фразы, а для advanced – расширить словарный запас. Субтитры в телесериалах на английском помогут в восприятии контекста. Как изучать английский по сериалам? Просто погружайтесь в английский язык смотря и слушая любимые сериалы! Смотреть и изучать английский языка можно на сайте https://serialy-na-anglijskom.pp.ua/
Написание курсовых работ https://courseworkskill.ru/ на заказ быстро, качественно, недорого. Сколько стоит заказать курсовую работу. Поручите написание курсовой работы профессионалам.
Квартиры с ремонтом в новостройках https://kupitkvartiruseychas.ru/ Казани по ценам от застройщика.Лидер по строительству и продажам жилой и коммерческой недвижимости.
Почему посудомоечная машина https://kulbar.ru/2024/01/21/pochemu-posudomoechnaya-mashina-eto-neobhodimost-dlya-sovremennogo-doma/ необходимость для современного дома? Как использовать и как выбрать посудомойку?
Купить квартиру https://newflatsale.ru/ в новостройке: однокомнатную, двухкомнатную, трехкомнатную в жилом комплексе в рассрочку, ипотеку, мат. капитал от застройщика.
1. The Ultimate Aviator Games Guide
juego del avion casino juego del aviator .
замена венцов
Продажа квартир в Казани https://kupitkvartiruzdes.ru/ от застройщика. Большой выбор квартир. Возможность купить онлайн. Квартиры с дизайнерской отделкой.
курсы по excel – Обучение с гарантиями государственного университета.
обучение эксель – Обучение с гарантиями государственного университета.
курс по экселю – Обучение с гарантиями государственного университета.
курс обучения excel – Обучение с гарантиями государственного университета.
онлайн курс excel – Обучение с гарантиями государственного университета.
курсы эксель – Обучение с гарантиями государственного университета.
курс по excel – Обучение с гарантиями государственного университета.
курс excel – Обучение с гарантиями государственного университета.
курсы excel – Обучение с гарантиями государственного университета.
Recomendo uma casa de apostas confiavel 1win
онлайн курсы эксель – Обучение с гарантиями государственного университета.
Купить квартиру в новостройке https://newhomesale.ru/ в Казани. Продажа новой недвижимости в ЖК новостройках по ценам от застройщика.
замена венцов
Recomendo uma excelente casa de apostas 1win
Стальные трубчатые радиаторы Arbonia (Чехия) и Rifar Tubog (Россия) https://medcom.ru/forum/user/226934/ подходят как для частных домов, так и для квартир в многоэтажках.
Melhor casa de apostas da Internet 1win
O melhor site, eu o recomendo 1win
трубчатые радиаторы подходят как для частных домов, так и для квартир в многоэтажках.
вакансии визажиста
вакансии парикмахера
вакансии администратор салона красоты
курсы шугаринга
вакансии мастер маникюра
вакансии мастер наращивания ресниц
вакансии колорист
салоны красоты
вакансии массажиста
ремонт фундамента
Продажа квартир в новостройках https://newflatsalespb.ru/ СПБ по выгодным ценам от застройщика. Купить квартиру в СПБ на выгодных условиях.
свадебный салон, где более 400 платьев в наличии. Свадебные и вечерние платья А-силуэта, прямые, греческие, пышные, силуэт Рыбка.
пышные свадебные платья, где более 400 платьев в наличии. Свадебные и вечерние платья А-силуэта, прямые, греческие, пышные, силуэт Рыбка.
свадебный салон Санкт-Петербург, где более 400 платьев в наличии. Свадебные и вечерние платья А-силуэта, прямые, греческие, пышные, силуэт Рыбка.
Просторная студия с теплыми полами в прекрасной цветовой бирюзовой гамме… Квартира студия: Кухня и спальня.Звоните. Залоговая стоимость обсуждается.
С меня невмешательство – с вас своевременная оплата и чистота в квартире.
квартира в переулке..под окном автобусов нет!
Минимальный залог от 8000р если вы без животных и маленьких деток.
Если вы оплатите за 3 мес вперед то цена может быть уменьшена
https://www.avito.ru/sochi/kvartiry/kvartira-studiya_27m_14et._2415880353?utm_campaign=native&utm_medium=item_page_android&utm_source=soc_sharing_seller
свадебные платья в Питере, где более 400 платьев в наличии. Свадебные и вечерние платья А-силуэта, прямые, греческие, пышные, силуэт Рыбка.
свадебные платья в Санкт-Петербурге, где более 400 платьев в наличии. Свадебные и вечерние платья А-силуэта, прямые, греческие, пышные, силуэт Рыбка.
свадебные платья, где более 400 платьев в наличии. Свадебные и вечерние платья А-силуэта, прямые, греческие, пышные, силуэт Рыбка.
Все для скрапбукинга, декор, вышивания и украшения. Наборы для канцелярии, росписи текстиля, декорации и детского творчества.
Флористика, декор, вышивания и украшения. Наборы для канцелярии, росписи текстиля, декорации и детского творчества.
Декор, декор, вышивания и украшения. Наборы для канцелярии, росписи текстиля, декорации и детского творчества.
Все для рукоделия, декор, вышивания и украшения. Наборы для канцелярии, росписи текстиля, декорации и детского творчества.
Детское творчество, декор, вышивания и украшения. Наборы для канцелярии, росписи текстиля, декорации и детского творчества.
Получение образования представляет собой основным этапом в карьере каждого человека, определяющим его перспективы и карьерные перспективы.
Диплом даёт доступ двери к перспективным горизонтам и возможностям, обеспечивая возможность к качественному образованию и престижным специальностям.
В современном обществе, где в борьба на трудовом рынке постоянно увеличивается, имение аттестата становится необходимым условием для успешной карьеры.
Диплом подтверждает ваши знания, умения и навыки, навыки и компетенции перед профессиональным сообществом и обществом в целом.
http://www.diplomanrus.comкупить аттестат за 9 – выход для людей, которые стремится к успеху без лишних препятствий. Это возможность завоевать признанный документ о высшему образованию, предоставляющий новые перспективы и престижным карьерным путям. Наш портал обеспечивает качество и конфиденциальность, помогая вам быстро и эффективно достичь ваших целей.
Помимо этого, аттестат придает уверенность в себе и укрепляет самооценку, что способствует личностному и развитию. Получение диплома также вложением в свое будущее, обеспечивая устойчивость и достойный уровень проживания.
Поэтому важно уделять надлежащее внимание и время образованию и бороться за его достижению, чтобы получить успех и счастье от собственной труда.
34. Клининг Челябинск специализируется на еженедельной уборке квартир и домов, включая пылесоску, вытирание пыли, мойку санузлов и кухни, чтобы создать уютную и чистую обстановку для жильцов.
Клининг Челябинск .
nz-offers.pages.dev Investment/Buying sites, depending on stage, market volume, and share. Comprehensive support for financial, legal, and HR aspects.
An affiliate department for the best offers and monetization strategies.
https://nz-offers.pages.dev Investment/Buying sites, depending on stage, market volume, and share. Comprehensive support for financial, legal, and HR aspects.
An affiliate department for the best offers and monetization strategies.
nz-offers.pages.dev
https://nz-offers.pages.dev/
https://gamesdb.ru/
https://nz-offers.pages.dev/
https://novyidomkupitspb.ru/ купить квартиру в новостройке Санкт-Петербурга от застройщика
https://newflatstroyka.ru/ квартиры от застройщика в Казани
https://novostroykatoday.ru/ купить квартиру от застройщика в Казани с гарантией
клиника кодировка от алкоголизма https://addictiontreatment.kz/
Покупки станут дешевле – получи Кэшбэк https://maxpromokod.ru/ до 30%! У нас более 4 500 интернет-магазинов и 33 000 промокодов и акций скидок.
помощь нарколога https://narcohelp.kz/
либет казино
https://novostroyzhkspb.ru/
На сегодняшний день, когда аттестат становится началом удачной карьеры в любой области, многие ищут максимально быстрый путь получения качественного образования. Необходимость наличия документа об образовании переоценить невозможно. Ведь именно он открывает дверь перед любым человеком, который стремится вступить в профессиональное сообщество или учиться в высшем учебном заведении.
Предлагаем оперативно получить этот важный документ. Вы имеете возможность купить аттестат, что является отличным решением для всех, кто не смог завершить образование или утратил документ. Любой аттестат изготавливается аккуратно, с максимальным вниманием ко всем элементам. В результате вы получите документ, полностью соответствующий оригиналу.
Превосходство этого решения заключается не только в том, что можно максимально быстро получить свой аттестат. Весь процесс организовывается комфортно, с нашей поддержкой. Начав от выбора нужного образца до грамотного заполнения личных данных и доставки в любой регион России — все будет находиться под абсолютным контролем качественных мастеров.
Для тех, кто пытается найти быстрый и простой способ получить требуемый документ, наша компания предлагает отличное решение. Приобрести аттестат – значит избежать долгого обучения и сразу переходить к своим целям, будь то поступление в ВУЗ или начало карьеры.
https://diplomans-rossians.com/
Получение образования представляет собой основным моментом во жизни всякого индивидуума, определяет его будущее и профессиональные перспективы.
Диплом даёт доступ двери к перспективным перспективам и перспективам, обеспечивая возможность к качественному образованию и высокопрестижным специальностям.
В современном мире, где борьба на рынке труда всё растёт, наличие аттестата становится необходимым требованием для успешной карьеры.
Он утверждает ваши знания, умения и навыки, навыки и компетенции перед работодателями и обществом в целом.
https://www.diploman-russiya.comкупить аттестат о среднем – выход для тех, кто желает достижения успеха без дополнительных трудностей. Это шанс завоевать признанный документ о техническому образованию, открывающий двери к новым возможностям и престижным профессиям. Наш портал обеспечивает качество и конфиденциальность, помогая вам достичь ваших целей быстро и эффективно.
Кроме того, аттестат дарует уверенность и укрепляет оценку себя, что содействует личностному росту и саморазвитию. Завершение учебы образования также является инвестицией в будущее, обеспечивая устойчивость и достойный уровень проживания.
Поэтому обращать должное внимание получению образования и бороться за его достижению, чтобы получить успех и счастье от своей труда.
Great post! Are you interested in learning how to resolve conflicts with your travel friends while on vacation? One effective strategy is to discuss everyone’s expectations for the trip, covering activities, sightseeing, relaxation time, dining preferences, and sleeping arrangements. Additionally, you can utilize my zip code tool to locate your next travel destination. For more information, check out the latest article on traveling.
repair of household appliances
В современном мире, где аттестат – это начало успешной карьеры в любом направлении, многие пытаются найти максимально быстрый и простой путь получения качественного образования. Факт наличия документа об образовании переоценить просто невозможно. Ведь именно диплом открывает дверь перед любым человеком, желающим начать профессиональную деятельность или учиться в высшем учебном заведении.
Предлагаем максимально быстро получить этот необходимый документ. Вы имеете возможность купить аттестат, и это будет удачным решением для всех, кто не смог завершить образование или потерял документ. Любой аттестат изготавливается аккуратно, с особым вниманием к мельчайшим нюансам. На выходе вы получите документ, 100% соответствующий оригиналу.
Превосходство подобного решения состоит не только в том, что можно оперативно получить свой аттестат. Процесс организовывается комфортно и легко, с профессиональной поддержкой. От выбора требуемого образца до правильного заполнения личной информации и доставки по стране — все находится под абсолютным контролем наших мастеров.
Таким образом, всем, кто хочет найти максимально быстрый способ получить необходимый документ, наша компания предлагает выгодное решение. Приобрести аттестат – значит избежать продолжительного процесса обучения и сразу переходить к личным целям: к поступлению в университет или к началу удачной карьеры.
https://diplomans-rossians.com/
repair organizations
Приобрести диплом без лишних хлопот, онлайн.
Как купить диплом без риска, без заморочек.
Купить диплом с гарантией качества, важная информация.
Опыт успешной покупки диплома, рассказываем.
Где купить диплом без проблем, на проверенных ресурсах.
Лучшие предложения по покупке диплома, важные моменты.
Купить диплом срочно и недорого, спешите.
Скрытая покупка дипломов, наши преимущества.
Как быстро купить диплом, срочно и выгодно.
Как купить диплом онлайн, подробности у нас.
Почему стоит купить диплом у нас, лучшие цены.
Безопасное приобретение документов об образовании, лучшие условия.
Купить диплом без обмана, важные детали.
Купить диплом просто, подробности на сайте.
Легальная покупка дипломов безопасно, подробности у нас.
Почему стоит купить диплом здесь и сейчас, интересные варианты.
Официальная покупка диплома, лучшие условия.
Как купить диплом безопасно и быстро, гарантированный результат.
купить диплом http://7arusak-diploms.com .
our company will also consider such important features such as color accuracy, refresh rate, https://startyourrenaissance.com/2018/07/18/current-top-5-cannabis-laws-you-must-know/ and optimized design.
Откуда мне знать?
On May 9, 2021, spacex announced a joint tasks to the Moon, fully funded by https://hikvisiondb.webcam/wiki/User:EdytheJose7362, becoming, so, the first space mission funded by cryptocurrency.
По-моему это очевидно. Ответ на Ваш вопрос я нашёл в google.com
Growth, focused on the community: An interested and strong community – this is it which contributes the growth of slothana. go to your solana wallet and find the option to send slothana sol https://iitmadrasstudentscommunity.me/iit-madras-pyq/.
Купить диплом с доставкой до дома, онлайн.
Как купить диплом без риска, узнайте сейчас.
Заказать официальный документ о образовании, важная информация.
Почему выгодно купить диплом, рассказываем.
Где купить диплом без проблем, на проверенных ресурсах.
Купить диплом по выгодной цене, секреты выбора.
Как купить диплом быстро, подробности на сайте.
Скрытая покупка дипломов, проверенные решения.
Как быстро купить диплом, срочно и выгодно.
Купить диплом срочно и законно, лучшие условия.
Официальные документы для покупки, срочные варианты.
Как купить диплом срочно, подробности на сайте.
Официальные дипломы для покупки, гарантированный результат.
Купить диплом просто, важные моменты.
Легальная покупка дипломов безопасно, безопасность на первом месте.
Какой диплом выбрать для покупки, подробности на сайте.
Официальная покупка диплома, важные детали.
Почему стоит заказать диплом на нашем сайте, подробности у нас.
купить диплом http://7arusak-diploms.com/ .
Recently, the pepe token has risen significantly by 16.88%, reaching a market capitalization of 3/3.2 billion dollars, https://baldfrombrowser.ru/voprosy/kak-ya-prodal-vse-tsennye-bumagi-i-v-chem-seychas-hranyu-svoi-dengi/confirming its strong market potential.
дробеструйный станок для очистки металла http://www.drobestruynaya-kamera.ru .
Among these, certain icons stand out for their ubiquitous presence and importance in our daily digital interactions. This article delves into a variety of such icons, including the email, safari (web browser), location, discord, settings, Christmas, messages, spotify, person, and home icons, exploring their significance and evolution home icon
дробеструйная камера цена http://www.drobestruynaya-kamera.ru/ .
Ну это ты точно зря.
sponge can surpass the cryptocurrency market in short if conditions are favorable for http://asgrenet.org/2015/06/23/first-women-elected-to-office-in-nesapal/.
allnewstoday365.com
В современном мире, где аттестат является началом отличной карьеры в любом направлении, многие стараются найти максимально быстрый путь получения качественного образования. Факт наличия официального документа сложно переоценить. Ведь именно диплом открывает двери перед людьми, желающими вступить в профессиональное сообщество или продолжить обучение в каком-либо университете.
Наша компания предлагает быстро получить любой необходимый документ. Вы можете купить аттестат, и это будет отличным решением для человека, который не смог закончить обучение или потерял документ. Аттестаты выпускаются с особой тщательностью, вниманием ко всем деталям. В результате вы получите 100% оригинальный документ.
Преимущество подобного решения заключается не только в том, что можно оперативно получить свой аттестат. Весь процесс организовывается просто и легко, с нашей поддержкой. От выбора подходящего образца до консультации по заполнению персональных данных и доставки в любой регион страны — все под полным контролем квалифицированных мастеров.
В итоге, для тех, кто ищет быстрый и простой способ получить необходимый документ, наша услуга предлагает выгодное решение. Заказать аттестат – это значит избежать продолжительного обучения и сразу переходить к своим целям: к поступлению в университет или к началу трудовой карьеры.
http://vsediplomu.ru/
Сайт, где представлен разнообразие раковина из нержавеющей стали для кухни для вашей ванной комнаты, с доставкой по всей стране.
Телесериал «911 служба спасения» про доблестных и храбрых спасателей, служба которых тяжелая и несет опасность с каждым вызовом. Герои службы 911 все смелые и храбрые в каждой серии сериала спасают жизни людям. Все персонажи сериала разные по характеру, но это не мешает им дружить и работать слаженной командой Здесь
сайт эвакуатора
эвакуатор дешево
эвакуатор круглосуточно цены
грузовой эвакуатор цена
раскрутка сайта оптимизация seo http://seogou.ru/ .
Индексация ссылок на сайте в индексе ру
профессиональная раскрутка сайта профессиональная раскрутка сайта .
Сайт, где можно заказать практичные раковина 55 по выгодным ценам.
служба открыть дверной замок vskrytie-zamkov-moskva111.ru .
вскрытия межкомнатных замков http://www.vskrytie-zamkov-moskva111.ru .
Сайт https://news24.in.ua/ – це новинний веб-портал, який надає швидкий та достовірний доступ до актуальних новин з різних сфер життя, включаючи політику, економіку, культуру, спорт та інші важливі теми.
Нефтегазовое и нефтехимическое оборудование. Данное оборудование используется для разведки газовых и нефтяных месторождений, переработки нефти и природных горючих газов. При его разработке специалисты К5 моделируют все характеристики технологического процесса с помощью программного обеспечения, что гарантирует качество и простоту эксплуатации поставляемых изделий Производство и продажа нефтегазового и нефтехимического оборудования (емкостное и теплообменное оборудование)
Будьте в курсе последних событий вместе с новостным порталом https://bnk.ua/. Наша команда профессиональных журналистов работает 24/7, чтобы вы получали самые важные новости из первых рук. Присоединяйтесь к нашей аудитории уже сегодня!
Доброго!
Не забудьте также следить за ссылками на скачивание приложений казино. Иногда они содержат специальные промокоды или бонусы, доступные только через эти ссылки. В заключение, мир онлайн-казино открывает множество возможностей для азартных игроков. Используйте все преимущества, скачивайте приложения, активируйте бонусы и наслаждайтесь захватывающим игровым процессом в любое время и в любом месте!
https://amengram.com/blogs/112/%D0%9F%D1%80%D0%B0%D0%B2%D0%B8%D0%BB%D1%8C%D0%BD%D1%8B%D0%B9-%D0%B2%D1%8B%D0%B1%D0%BE%D1%80-%D0%B8%D0%BD%D1%82%D0%B5%D1%80%D0%BD%D0%B5%D1%82-%D0%BA%D0%B0%D0%B7%D0%B8%D0%BD%D0%BE-%D0%A0%D0%B5%D0%BA%D0%BE%D0%BC%D0%B5%D0%BD%D0%B4%D0%B0%D1%86%D0%B8%D0%B8-%D0%B3%D0%B5%D0%BC%D0%B1%D0%BB%D0%B5%D1%80%D0%B0
онлайн казино с живыми крупье
онлайн казино миллион официальный сайт зеркало
пароль и логин от казино онлайн
игровые автоматы пополнить с мобильного на андроид
150 бесплатных спинов
Удачи!
Сайт https://dailynews.kyiv.ua/ – це онлайн-портал, який забезпечує свіжі та актуальні новини з Києва та інших регіонів України. Тут ви знайдете інформацію про події, політику, економіку, культуру, спорт та інші аспекти суспільного життя.
Привет!
Приветствую вас, любители азарта! Хотите сделать игру в онлайн-казино максимально прибыльной и интересной? Тогда следуйте моим советам. Прежде всего, установите на свой смартфон или планшет мобильное приложение понравившегося казино. Это позволит вам играть в игровые автоматы, рулетку, блэкджек и другие азартные игры в любом месте – дома, на работе, в дороге. А многие операторы дарят щедрые бонусы на первый депозит новичкам. Но для максимальной выгоды обязательно используйте промокоды при регистрации. Промокод Миллион Казино, промокоды Казино Миллионъ или промокод на Миллион игровые автоматы разблокируют для вас эксклюзивные бонусы, фриспины, повышенный кэшбэк и другие плюшки. После регистрации не забудьте скачать официальное приложение казино на свой Android-девайс. Только лицензированный софт гарантирует стабильность, безопасность и честную игру. А некоторые операторы предлагают даже бездепозитные бонусы новеньким! Также внимательно изучайте ссылки на скачивание приложений – там часто прячутся дополнительные уникальные акции и промокоды. Поклонникам бесплатной игры советую скачать игровые автоматы без депозита для беззаботного драйва. Главное правило успешного гэмблера – развлекайтесь с умом, получайте массу бонусов и выигрывайте!
https://potochino.ru/2024/04/29/Волшебство-азарта-погружение-в-мир-new-retro-casino
казино android
игровые автоматы на деньги для андроид онлайн
игровые автоматы на деньги для андроид
в каких казино есть оплата по сбп
казино на андроид
Удачи!
Простыми словами о том, что нужно знать прежде, чем заказать свидание на крыше романтическое свидание
Индексация ссылок на сайте в индексе ру
Сайт https://dailynews.kyiv.ua/ – це онлайн-портал, який забезпечує свіжі та актуальні новини з Києва та інших регіонів України. Тут ви знайдете інформацію про події, політику, економіку, культуру, спорт та інші аспекти суспільного життя.
Наши навес над домом – это ваш лучший выбор.
Преобразите свой участок с помощью навес из металлочерепицы для авто.
Наши ворота на навес для машины подойдут для любого дома и участка.
Будьте в курсе последних событий вместе с новостным порталом https://bnk.ua/. Наша команда профессиональных журналистов работает 24/7, чтобы вы получали самые важные новости из первых рук. Присоединяйтесь к нашей аудитории уже сегодня!
Наши навес с мягкой кровлей для автомобиля фото – это качество, проверенное временем.
Сайт https://arguments.kyiv.ua/ – це інформаційний портал, який надає аналітику, коментарі та новини про події в Києві та Україні. Тут можна знайти різноманітні погляди на актуальні теми у політиці, економіці, культурі, суспільстві та інших сферах життя.
Мы предлагаем индивидуальные решения для купить навес дачный из металла.
Сайт https://uapress.kyiv.ua/ – це СМИ платформа, яка надає новини, аналітику та репортажі з подій, що відбуваються в Києві та по всій Україні. Він охоплює різноманітні теми, включаючи політику, економіку, культуру, спорт та інші аспекти суспільного життя.
Индексация ссылок на сайте индекс ру
Сайт https://elegantwoman.kyiv.ua/ – це онлайн-ресурс, присвячений стильним жінкам. Тут ви знайдете поради з моди, краси, стилю та етикету, а також ідеї для створення елегантного образу та розвитку особистого стилю.
Индексация ссылок на сайте vindexe.ru
Индексация ссылок на сайте vindexe
заказ такси в новочеркасске по телефону недорого https://vyzvat-taksi.ru/.
вызвать такси недорого заказ такси.
вызов такси в новочеркасске вызов такси по телефону.
такси новочеркасск заказ такси в новочеркасске по телефону недорого.
сколько будет стоить такси служба поддержки такси.
номер заказа такси такси новочеркасск недорого.
сколько стоит такси заказать такси.
такси номер недорогой заказать такси в новочеркасске.
такси межгород заказ такси в новочеркасске по телефону недорого.
бизнес такси рассчитать такси.
номер заказа такси заказ такси в новочеркасске недорого.
дешевое такси дешевое такси .
номер телефона такси taksi-vyzvat.ru .
заказать такси онлайн заказать такси онлайн .
заказать такси в новочеркасске по телефону заказать такси в новочеркасске по телефону .
аренда такси аренда такси .
дешевое такси дешевое такси .
дешевое такси дешевое такси .
такси город телефон https://www.taksi-vyzvat.ru .
заказать такси эконом заказать такси эконом .
служба поддержки такси taksi-vyzvat.ru .
такси недорого цены http://taksi-vyzvat.ru .
такси эконом недорого номер заказа такси .
такси эконом недорого заказать такси эконом новочеркасск .
заказ такси эконом новочеркасск вызов такси .
вызов такси в новочеркасске такси межгород .
заказать такси недорого дешевое такси .
заказ такси недорого телефон заказ такси в новочеркасске по телефону недорого .
детское такси самое дешевое такси .
такси город аренда такси в новочеркасске .
стоит такси https://vyzvat-taksi.ru .
Путешествие на поезде теперь стало еще проще и удобнее
благодаря мобильному приложению РЖД.
С его помощью вы можете не только бронировать билеты, но
и управлять своими поездками, не выходя из дома.
Скачать приложение РЖД пассажирам можно абсолютно бесплатно прямо на ваш телефон и начать пользоваться всеми преимуществами незамедлительно.
С помощью приложения вы легко найдете нужное направление, выберете оптимальное время поездки и оформите
билеты без лишних хлопот. Скачать бесплатно приложение РЖД пассажирам —
это значит всегда иметь под рукой все необходимое для путешествия
на железнодорожном транспорте.
Начните использовать скачать приложение РЖД бесплатно на телефон уже сегодня и оцените все преимущества современных технологий!
Скачать приложение в App Store.
заказать машину такси заказ такси эконом новочеркасск .
аренда такси в новочеркасске заказать такси номер .
телефон такси эконом заказ такси недорого телефон .
Информационный портал https://kalitka48.ru/ на актуальные темы, связанные с недвижимостью: новости рынка недвижимости, информация о покупке и продаже квартир и множество других полезных статей.
официальный сайт 1го казино официальный сайт 1го казино
регистрация 1Go Casino вход 1go casino
регистрация 1Go Casino https://prime-kapitals.com/
1go casino официальный сайт https://prime-kapitals.com/
1го казино регистрация 1Go Casino
prime-kapitals.com prime-kapitals.com
вход 1го казино вход 1go casino
бонус 1go casino сайт 1go casino
вход 1go casino вход 1go casino
Как получить пропуск на МКАД, основные моменты, Ключевые моменты о пропуске на МКАД, которую важно помнить, полный гайд, Сколько стоит и как долго делается пропуск на МКАД, подробный обзор, Почему стоит получить пропуск на МКАД, Как продлить пропуск на МКАД, шаг за шагом
Проверить пропуск на мкад Пропуск на мкад .
1go casino официальный сайт бонус 1go casino
1go casino официальный сайт 1go casino официальный сайт
Продажа квартир Пенза https://solnechnyjgorod.ru/, успейте купить квартиру от застройщика в Пензе. ЖК «Солнечный Город» расположен в экологическом чистом районе в 13 км от города Пенза. Продажа 1,2 комнатных квартир от застройщика по минимальной стоимости за кВ/м, успей купить не упусти шанс.
оценить автомобиль https://avtovikupmashin21.ru/
whoah this blog is fantastic i love reading your articles. Stay up the great work! You understand, a lot of persons are hunting round for this info, you could help them greatly.
spin away casino ontario
Фотокниги с вашей историей. Закажите сегодня, и через несколько дней будете держать дорогие сердцу воспоминания в руках. Обложка arrow печать фотокниг
Hey! I’m at work surfing around your blog from my new iphone 3gs! Just wanted to say I love reading your blog and look forward to all your posts! Carry on the great work!
how to get away with murder spin off
финская плита фундамент цена
мы организуем вам лучшее в инете качество создаваемых нами документов, утерянного” сервера, подключение или отключение, https://tirana.social/blogs/767/%D0%94%D0%BE%D1%81%D1%82%D0%B8%D0%B6%D0%B5%D0%BD%D0%B8%D0%B5-%D1%83%D1%81%D0%BF%D0%B5%D1%85%D0%B0-%D1%81-%D0%BF%D0%BE%D0%BC%D0%BE%D1%89%D1%8C%D1%8E-%D0%B4%D0%B8%D0%BF%D0%BB%D0%BE%D0%BC%D0%B0 своевременно выполненную дело и быструю привоз.
1вин
1win
apostar online em nativo, https://www.galerie-delphine.com/2020-014/ nao ha erro. voce ja pensou alguma vez? E como ser em avancado Clube de jogo!
venueInDelhi is here to help you find and book the perfect place for your special day. We offer a range of wedding services to make your wedding planning easy and stress-free. We can also customize your wedding according to your budget and preferences. venueindelhi
Осуществляем уборку квартир, домов, офисов, уборку после ремонта, генеральную и поддерживающую, а также мытье окон клининг в минске
Подарочный сертификат на аренду квадроциклов станет незабываемым подарком для любителей активного отдыха маршруты квадроцикл
Магазин, где можно найти подвесные раковины из искусственного камня для любого интерьера и бюджета.
купить подписчиков вк
купить подписчиков тик ток
накрутка подписчиков ютуб
накрутка просмотров тг
накрутка реакций тг
накрутка лайков тик ток
купить просмотры ютуб
накрутка просмотров ютуб
Не горю желанием смотреть……
Допускається зміна зазначених розмірів залежно від серії і укомплектуванні. https://forum.flagman.kiev.ua/threads/de-zruchnishe-kupuvati-liki.7073/ авіаційна-це комплект виробів медичного намірів і медикаментів, відповідний для своєчасного надання першої домедичної само – і взаємодопомоги на борту пасажирського|вантажного літака.
https://smm.ytmonster.ru/telegram/subscribers/nakrutka-podpischikov-telegram
https://smm.ytmonster.ru/telegram/likes/nakrutka-reaktsii-telegram
https://smm.ytmonster.ru/tiktok/views/nakrutka-prosmotrov-tik-tok
https://smm.ytmonster.ru/telegram/subscribers/nakrutka-podpischikov-telegram
https://smm.ytmonster.ru/telegram/views/nakrutka-prosmotrov-telegram
https://smm.ytmonster.ru/tiktok/likes/nakrutka-laikov-tiktok
Отзывы на работу онлайн казино 1Win Casino (1Вин Казино) об игре на реальные деньги, скорости выплат и вывода средств, отдаче автоматов казино 1win
https://host.io/yonseibaro.com
Букмекерская контора 1win отзывы клиентов, Отзывы о Букмекерская контора 1win. На сайте отвечает официальный представитель Букмекерская контора 1win 1win
Hello!
This post was created with 2ssdsd3222aa.com
Hello!
This post was created with 2ssdsd3222aa.com
В фитнес-клубах есть вело- и кардиотренажеры, силовое оборудование, эллипсы, беговые дорожки. Самых популярных тренажеров в зале несколько экземпляров, чтобы всегда были свободные пилатес на войковской
ремонт смартфонов в москве
Доставка из Китая с таможенными услугами — это профессиональное решение для импорта товаров из Китая, включающее в себя организацию перевозки, таможенное оформление и сопутствующие услуги. Мы предоставляем полный спектр услуг, связанных
доставка грузы китай включая организацию международных перевозок, таможенное оформление, сертификацию и страхование грузов. Наши специалисты помогут вам выбрать оптимальный маршрут и вид транспорта, оформить необходимые документы и декларации, а также проконсультируют по вопросам налогообложения и таможенного законодательства.
сео оптимизация
Узнайте больше о преимуществах наших замена поликарбоната на навесе цена.
качественный сервис выполняет ремонт фотоаппаратов nikon в Москве. Сотни раз обращался, все отремонтировали качественно!
Премиальный фитнес-клуб: бассейн, залы групповых программ, SPA, кафе. Оборудование в тренажерном зале топовых фирм фитнес клуб коптево москва
https://seogou.ru/
For hottest information you have to go to see world wide web and on the web I found this web page as a finest web site for latest updates.
срок доставки из китая
The UK’s news sites https://beerguysradio.com/blog/popular-events-of-summer-2024-in-the-united-kingdom.html countryside is rich and miscellaneous, encompassing a considerable choice of outlets from the esteemed BBC and The Paladin to the more stirring tabloids like The Sun and The Diurnal Mail. Each of these sources brings a divergent where one is coming from to the news, reflecting the pluralism of British society. The BBC, funded by the communal through the licence price, aims to provide equitable and inclusive coverage. It is often seen as the gold standard in broadcasting, known an eye to its commitment to unprejudiced reporting and in-depth analysis.
1win
https://arochnye-shatry.ru/
I’ve been surfing online more than 4 hours today, yet I never found any interesting article like yours.
It is pretty worth enough for me. In my opinion, if all site owners and bloggers made good content
as you did, the web will be much more useful than ever before.
пояснения по корректировкам реализации ндс пояснения по корректировкам реализации ндс
Стоматологическая клиника Мастерская Улыбок предлагает широкий спектр услуг по диагностике, лечению, профилактике и эстетической коррекции проблем с зубами и дёснами. Мы используем современное оборудование и материалы, а наши специалисты обладают высокой квалификацией и опытом.
В клинике созданы комфортные условия для пациентов: удобные кресла, приятная атмосфера, приветливый персонал. Мы заботимся о вашем здоровье и стараемся сделать посещение стоматолога максимально комфортным и безболезненным.
Наши услуги включают:
казань круглосуточная стоматология
диагностику состояния зубов и дёсен;
лечение кариеса, пульпита, периодонтита и других заболеваний;
профессиональную гигиену полости рта;
эстетическую коррекцию зубного ряда (установка коронок, виниров, имплантов);
исправление прикуса с помощью брекетов или элайнеров;
отбеливание зубов;
лечение дёсен (пародонтит, гингивит, пародонтоз).
Мы также предлагаем услуги по детской стоматологии, протезированию и имплантации.
Обращаясь в клинику Мастерская Улыбок, вы можете быть уверены в качестве предоставляемых услуг и профессионализме наших врачей. Мы заботимся о вашей улыбке и делаем всё возможное, чтобы она была здоровой и красивой!
http://www.lumc-online.org/System/Login.asp?Referer=http%3A%2F%2Fjoychem.co.kr&id=44561
ремонт телефонов в москве
Aw, this was a very nice post. Finding the time and actual effort to generate a really good article… but what can I say… I procrastinate a lot and never seem to get
anything done.
сайты заказа курсовых работ https://kontrolnyeaudit.ru/
Специализированный магазин, предлагающий много накладная раковина для вашего интерьера.
заказ курсовой недорого https://kontrolnyeaudit.ru/
написать курсовую на заказ https://kontrolnyeaudit.ru/
Jogue em um cassino confiavel Tigrinho
I am in fact grateful to the owner of this website who has shared this fantastic
post at at this place.
Место, где можно купить качественные раковина vitra по выгодным ценам.
Cassinos com condicoes favoraveis Tigrinho
Проверка персонала в СПб. Поиск прослушки
It is actually a nice and helpful piece of information. I’m glad
that you simply shared this helpful info with us. Please keep us up to
date like this. Thanks for sharing.
Way cool! Some extremely valid points! I appreciate you penning this article and also the rest of the
website is also really good.
https://rybalka-v-rossii.ru/ – сайт о рыбалке в России, способах ловли рыб, и выборе правильных снастей.
As maiores probabilidades neste cassino Tigrinho
Escolha este cassino confiavel Tigrinho
al-club.ru вход lee bet
leebet lee bet
leebet casino официальный сайт lee bet
Наш сайт эротических рассказов https://shoptop.org/ поможет тебе отвлечься от повседневной суеты и погрузиться в мир страсти и эмоций. Богатая библиотека секс историй для взрослых пробудит твое воображение и позволит насладиться каждой строкой.
O cassino perfeito para jogos de azar Tigrinho
https://6giay.vn/proxy.php?link=http%3A%2F%2Feq5xcafpfd.preview.infomaniak.website
где отремонтировать телефон
A casa de apostas perfeita para jogos de azar Tigrinho
Cassinos com as melhores avaliacoes Tigrinho
Eu recomendo um otimo cassino Tigrinho
Come on, visit our interesting website and don’t forget to invite your friends to. SAGATOTO“
Experimente este cassino de primeira linha Tigrinho
O cassino mais confiavel Tigrinho
https://autoblog.kyiv.ua путеводитель в мире автомобилей. Обзоры и тест-драйвы, актуальные новости, автокаталог, советы по уходу и ремонту, а также общение с автолюбителями. Всё, что нужно для выбора и эксплуатации авто, вы найдете у нас.
Um cassino com uma excelente reputacao Tigrinho
Jogue em um cassino confiavel Tigrinho
В ТЕЧЕНИЕ сети интернет большое цифра анализаторов интернет-сайта, качество опуса которых чистосердечно молит от тарифных планов.
https://be1.ru/ – дебилу
Os melhores bonus deste cassino Tigrinho
аренда офиса в москве с юридическим адресом
Псс… Хотите узнать о самых выгодных направлениях инвестирования в недвижимость, основных рисках и способах их минимизации? Сайт https://aibismach.ru
интим интернет магазин https://24sex-shop.ru/
секс шоп https://24sex-shop.ru/
заказать интимные товары https://24sex-shop.ru/
интим магазин каталог https://24sex-shop.ru/
What’s Happening i am new to this, I stumbled upon this I have discovered It
absolutely helpful and it has helped me out loads.
I’m hoping to give a contribution & assist other customers like its aided
me. Good job.
секс шоп цены https://24sex-shop.ru/
секс шоп москва https://24sex-shop.ru/
интим магазин секс шоп https://24sex-shop.ru/
интернет секс шоп https://24sex-shop.ru/
интимный магазин для взрослых https://24sex-shop.ru/
магазин секс шоп https://24sex-shop.ru/
https://fraza.kyiv.ua/ вы найдете последние новости, глубокие аналитические материалы, интервью с влиятельными личностями и экспертные мнения. Следите за важными событиями и трендами в реальном времени. Присоединяйтесь к нашему сообществу и будьте информированы!
Gimtadienio atvirukai ir sveikinimai su gimtadieniu
https://archive.guildofarchivists.org/wiki/User:FerneMilne89726
Всем привет! Интересные статьи о недвижимости. Аренда, купля/продажа, недвижимость как бизнес. Читать http://sma-repair.ru
Cassinos com condicoes favoraveis Tigrinho
решения задач на заказ https://resheniezadachmatematika.ru/
Wow, fantastic weblog format! How lengthy have you ever been running a blog for? you make running a blog look easy. The whole look of your web site is fantastic, let alone the content!
Видеосъемка мероприятий
Confie neste cassino confiavel Tigrinho
заказать курсовую онлайн https://kursovyebankovskoe.ru/
Tente a sua sorte neste cassino Tigrinho
Смотрите сериалы на английском языке с субтитрами:
https://en.bnctrans.com/blog/2014/08/29/%E8%8B%B1%E6%96%87%E7%BF%BB%E8%AD%AF-%E5%81%BD%E8%A3%9D%E7%9A%84%E8%97%9D%E8%A1%93-%E8%B6%85%E7%A5%9E%E5%A5%87%E6%98%93%E5%AE%B9%E8%A1%93-%E7%BF%BB%E8%AD%AF%E7%A4%BE/
Всем привет! Может кто знает, где почитать полезные блоги о недвижимости? Хочу больше узнать про темы аренды и купли/продажи недвижимости. Сейчас читаю https://alfapromnn.ru
Смотрите сериалы на английском языке с субтитрами:
https://university-mall.com/?URL=https%3A%2F%2Fserialy-na-angliiskom.pp.ua
Больше интересной информации о строительстве и ремонте можно прочитать на сайте https://stroyka-gid.ru. Только самые популярные статьи и обзоры процесса ремонта помещений и строительства зданий.
rap marketing agency music promotion agency
https://primexdon.ru/
профессиональная мойка окон
не помне
самый легкий вариант подобрать зеркало конторы заключается в использовании обычных 1win поисковиков. Опытные бетторы рекомендуют придерживаться тотала больше в данном виде спорта.
сколько стоит такси сколько стоит такси в новочеркасске
А возможны еще варианты?
1. покупка https://ogo.ua/articles/view/2021-06-30/117633.html житла в нашій країні. Заміська і елітна нерухомість в курсі.
https://www.nytimes.com/2017/10/10/arts/design/augmented-reality-jeff-koons.html
решение задач на заказ https://resheniye-zadach7.ru заказать онлайн
Jogue em um cassino confiavel Tigrinho
айаваска купить в москве заказать аяуаску
мытье окон в москве цены на услуги
Всем привет! Подскажите, где почитатьполезные статьи о недвижимости? Хочу больше узнать про темы аренды и купли/продажи недвижимости. Пока нашла https://iter21.ru
спс…я так ждал его
This cooler is similar to an online event that is hosted by the organizer and broadcast by an https://profile.hatena.ne.jp/EDVARD/ audience. Meetings vary from public business discussions and idea updates to brainstorming sessions and team building activities.
сайдинг для дома цена сайдинг наружный виниловый цена
Lex Casino – лицензионная новинка 2024 года, заходи сегодня и забери свой бонус 150% к первому депозиту до 30 000 рублей!
Lex Casino Регистрация и Бонус по ссылке – https://lex-casino-01.ru/
Промокод: BEZDEPCAS
Играйте в лучшие слоты с эксклюзивными бонусами на депозит и недельным кешбэком. Начните выигрывать уже сейчас!
Все самое интересное из мира игр https://unionbattle.ru обзоры, статьи и ответы на вопросы
бонусный счастливая пятница в 1xbet
Отличный сайт! Всем рекомендую!Ремонт холодильников
эффективно,
Современное оборудование и материалы, для поддержания здоровья рта,
Специализированная помощь по доступным ценам, для вашего удобства,
Комфортные условия и дружественный персонал, для вашего комфорта и уверенности,
Эффективное лечение зубов и десен, для вашего здоровья и красоты улыбки,
Экстренная помощь в любое время суток, для вашего комфорта и удовлетворения,
Заботливое отношение и внимательный подход, для вашей уверенной улыбки
протезування зубів https://stomatologichnaklinikafghy.ivano-frankivsk.ua/ .
Отличный сайт! Всем рекомендую!Ремонт холодильников на дому
Отличный сайт! Всем рекомендую!Мастер по ремонту холодильников
Всем привет! Может кто знает, где почитатьполезные блоги о недвижимости? Сейчас читаю https://inter-garage.ru
Good Post. Ever wondered how to elevate your gaming experience on Windows 10 and Windows 11? Look no further than rawaccel download is a mouse acceleration software designed to provide users with customizable and precise control over their mouse movements. For a more detailed understanding, visit the specified site.
Всем привет! Подскажите, где почитатьполезные статьи о недвижимости? Пока нашел https://optorgsib.ru
купить диплом о среднем https://6landik-diploms.com
купить диплом в екатеринбурге https://6landik-diploms.com
купить диплом отзывы https://6landik-diploms.com
купить диплом института https://6landik-diploms.com
купить диплом в благовещенске https://6landik-diploms.com
купить диплом с реестром https://6landik-diploms.com
купить диплом в новом уренгое https://6landik-diploms.com
купить диплом бакалавра https://6landik-diploms.com
купить диплом провизора https://6landik-diploms.com
купить диплом энергетика https://6landik-diploms.com
купить диплом массажиста https://6landik-diploms.com
Thank you for sharing such a good post! Do you want to know how to run Android apps on Linux? If so, you can run Android apps on Linux using a variety of ways, including Anbox, Genymotion, and compatibility layers like Wine for specific apps. To learn more about the app, visit the given article link. There, you’ll also learn about the scrcpy software, which allows you to mirror your screen from Android to Linux.
Приветствую. Подскажите, где почитатьразные блоги о недвижимости? Сейчас читаю https://jkstolitsa.ru
Отличный сайт! Всем рекомендую!Тут Вы можете приобреститовары для охоты
https://aisory.tech – платформа для создания AI Telegram-ботов. Наделяйте своих ботов способностями к естественному диалогу, генерации уникального контента и решению аналитических задач. Простой конструктор платформы делает создание умных чат-ботов доступным для любой компании.
жк казань купить квартиру от застройщика купить квартиру в казани
купить квартиру в казани новостройка от застройщика https://nedvizhimost16.ru
атака титанов смотреть онлайн бесплатно https://ataka-titanov-anime.ru
Melhores jogos neste cassino Blaze
Desfrute da emocao no melhor cassino Blaze
what is an online casino bonus online casino
O melhor cassino para grandes vitorias Blaze
голяк кубик онлайн https://golyak-serial-online.ru
Glory Casino Online
голяк онлайн в хорошем качестве сериал голяк
смотреть атака титанов – эпический аниме-сериал, где человечество борется за выживание в мире, наполненном гигантскими титанами. Динамичные бои, захватывающий сюжет и глубокие персонажи делают этот сериал обязательным к просмотру. Присоединяйтесь к битве!
голяк смотреть онлайн бесплатно в хорошем https://golyak-serial-online.ru
голяк бесплатно в хорошем качестве https://golyak-serial-online.ru
голяк смотреть онлайн бесплатно https://golyak-serial-online.ru
https://ataka-titanov-anime.ru/ – эпический аниме-сериал, где человечество борется за выживание в мире, наполненном гигантскими титанами. Динамичные бои, захватывающий сюжет и глубокие персонажи делают этот сериал обязательным к просмотру. Присоединяйтесь к битве!
голяк смотреть в хорошем качестве https://golyak-serial-online.ru
атака титанов в хорошем качестве – эпический аниме-сериал, где человечество борется за выживание в мире, наполненном гигантскими титанами. Динамичные бои, захватывающий сюжет и глубокие персонажи делают этот сериал обязательным к просмотру. Присоединяйтесь к битве!
голяк онлайн в хорошем качестве https://golyak-serial-online.ru
Glory Casino Bangladesh
атака титанов бесплатно в хорошем качестве – эпический аниме-сериал, где человечество борется за выживание в мире, наполненном гигантскими титанами. Динамичные бои, захватывающий сюжет и глубокие персонажи делают этот сериал обязательным к просмотру. Присоединяйтесь к битве!
голяк в хорошем качестве https://golyak-serial-online.ru
голяк кубик в кубе онлайн голяк смотреть бесплатно
голяк онлайн бесплатно в хорошем голяк смотреть бесплатно
голяк смотреть онлайн кубик в кубике https://golyak-serial-online.ru
Приветствую. Подскажите, где найтиразные статьи о недвижимости? Сейчас читаю https://master-architector.ru
Sua sorte esta no cassino confiavel Blaze
Amazing content! Thanks. Are you a gamer and eager to know what pokemon are in pokemon sleep? So, pokémon sleep is a safe and enjoyable game that turns your sleep into an exciting adventure. However, unblock and download emerald rom, get ready to enhance your gameplay, and become a pokemon master. For more information visit the article.
The Vampire Facial in New York City, NY is a highly sought-after cosmetic treatment that has gained popularity for its ability to rejuvenate the skin and promote a youthful appearance. This innovative procedure, also known as Platelet-Rich Plasma (PRP) therapy, involves drawing a small amount of the patient’s blood, processing it to concentrate the platelets, and then injecting the PRP into the facial skin. The growth factors in PRP stimulate collagen production and enhance skin texture, tone, and overall appearance.
Planning a family vacation? Camano Island in Washington offers a variety of family-friendly activities that are sure to create lasting memories. The island’s parks and beaches provide the perfect setting for picnics, beachcombing, and playing in the sand. Iverson Beach Preserve is a favorite spot for families, featuring shallow waters that are safe for children to explore. Additionally, Camano Island’s farmers markets and local festivals offer fun and educational experiences for visitors of all ages. Discover why Camano Island in Washington is an ideal destination for family adventures.
Experimente o cassino mais popular Blaze
Teste sua sorte no melhor cassino Blaze
O melhor cassino para jogadores de verdade Blaze
Ling, Thomas. “13 secrets of my father who wrote a toton porno movie.” The Press Association. “My father wrote a porn podcast nominated for the ARIAS Radio Academy Award.”
Приветствую. Полезные статьи о недвижимости. Аренда, купля/продажа, недвижимость как бизнес. Читать http://sma-repair.ru
абстинентный синдром при алкоголизме https://lechenie-narkomanii.kz/
Отличный сайт! Всем рекомендую!охотничий магазин
O lugar perfeito para jogos de azar Blaze
Excelente cassino para ganhos Blaze
Wonders Travel & Tourism: a https://jordan-travel.com agency located in Aqaba. Specializing in tours around Jordan, including Petra, Wadi Rum, the Dead Sea, and Amman. Offering private tours that can be customized to tourist interests and have positive reviews for professionalism and service.
Итальянская мебель от салона https://formul.ru в Москве – это большой выбор мебели из Италии по доступным ценам! Итальянская мебель в налиичи и на заказ. Купить итальянскую мебель в Москве по лучшим ценам.
I have been surfing online more than three hours today, yet I never
found any interesting article like yours. It is pretty
worth enough for me. In my view, if all webmasters and bloggers made good content as you did, the internet will be much more useful
than ever before.
Also visit my homepage; Xénie Kohoutová
Привет студенты!
Недавно у Меня возникла необходимость получить среднее образование, но постоянная работа и заботы постоянно отбирают время и не дают этого сделать, хорошо друзья подсказать что оказывается можно купить диплом о среднем профессиональном образовании (диплом техникума, колледжа), совершенно легально на бланках госзнак, пройдя обучения по облегченной программе!
В Интернете предложений более чем достаточно, но как не стать жертвой мошенников и выбрать подходящую компанию? Задача очень щепетильная и следует ответственно подходить к этому вопросу. Проверено Мной лично, На https://www.arusak-diploms-srednee.ru/ очень много информации как не попасть впросак и не потерять впустую деньги. Как можно проверить компанию по продаже дипломов, на что обратить внимание, и конечно там можно заказать диплом под ключ без предоплаты.
В отличие от других коммерческих организаций, мы не ставим перед собой цель заработать, — мы работаем на благо наших клиентов. Мы предоставляем бесплатные консультации без ограничения количества вопросов. Наши специалисты — проверенные временем сотрудники, поэтому обратиться к нам – верное решение, ведь мы обладаем рядом преимуществ: качество, сроки, цены на дипломы о среднем образовании на заказ.
Удачи и хороших оценок!
купить диплом о высшем образовании в чебоксарах
купить диплом медицинского университета
приложение к диплому о высшем купить
купить диплом строительного техникума
купить дипломы о среднем образовании
купить диплом конкурса
купить дипломы в красноярске недорого
купить диплом бгату
можно ли купить официальный диплом
пермь купить диплом о среднем специальном образовании
Hey, Welcome to TapSwap!
Tap on the coin and see your balance rise.
TapSwap is a cutting-edge financial platform where users can earn tokens by leveraging the mining app’s various features. The majority of TapSwap Token (TAPS) distribution will occur among the players here.
Do you have friends, relatives, or co-workers?
Bring them all into the game.
More buddies, more coins.
Start now!
реристрация Dragon Money Casino официальный сайт Dragon Money
вход 1go casino бонус 1go casino
https://lala.lanbook.com/virtualnaya-i-dopolnennaya-realnosti-v-obuchenii
daddy казино регистрация
Right here is the perfect web site for everyone who hopes to find out about this topic. You realize so much its almost hard to argue with you (not that I personally will need to…HaHa). You definitely put a brand new spin on a subject that’s been written about for many years. Great stuff, just excellent!
http://www.musey-uglich.ru
Hey, Welcome to TapSwap!
Tap on the coin and see your balance rise.
TapSwap is a cutting-edge financial platform where users can earn tokens by leveraging the mining app’s various features. The majority of TapSwap Token (TAPS) distribution will occur among the players here.
Do you have friends, relatives, or co-workers?
Bring them all into the game.
More buddies, more coins.
Start now!
купить квартиру от застройщика недорого квартиры от застройщика цены
купить квартиру квартира от застройщика
квартира от застройщика Санкт-Петербург https://novostroyki-spb78.ru
Wedding Venues in Kapashera NH8 and Pushpanjali. List of Farmhouses , Banquet Halls, Hotels for Party places in kapashera and NH-8 and Pushpanjali Ever thought of enjoying a multi-theme Wedding Function while being at just one destination? If not then you must not have visited kapashera NH-8 & Pushpanjali Farmhouses.
Каталог эротических рассказов https://vicmin.ru подарит тебе возможность уйти от рутины и погрузиться в мир секса и безудержного наслаждения. Обширная коллекция рассказов для взрослых разбудит твое воображение и принесет немыслимое удовольствие.
где купить диплом образование https://diplom-izhevsk.ru
https://mebel-24.blogspot.com/ – всем рекомендую эту компанию. Купить современную мебель в интернет магазине TM Mebel-24 в Киеве и Украине. Производство качественной нестандартной мебели для дома и офиса. Большой каталог готовой мебели на 15000 товаров. Наш опыт более 19 лет в мебельной промышленности!
Cериал Голяк https://golyak-serial-online.ru смотреть онлайн в хорошем качестве и с лучшей озвучкой на любых устройствах. Все сезоны истории мелкого преступника Винни и его друзей в английском городке!
Famous French footballer Kylian Mbappe https://kylianmbappe.prostoprosport-ar.com has become a global ambassador for Dior. The athlete will represent the men’s collections of creative director Kim Jones and the Sauvage fragrance, writes WWD. Mbappe’s appointment follows on from the start of the fashion house’s collaboration with the Paris Saint-Germain football club. Previously, Jones created a uniform for the team where Kylian is a player.
Seu cassino da sorte espera por voce Blaze
Скачать свежие новинки песен https://muzfo.net 2024 года ежедневно. Наслаждайтесь комфортным прослушиванием, скачивайте музыку за пару кликов на сайте.
Я считаю, что Вы не правы. Пишите мне в PM, пообщаемся.
this was followed by a series of Musk’s tweets bordering on dogecoin, beginning of February 2021, entitled “https://dogecoin20.io/ is the people’s cryptocurrency and “no ups, no downs, only doge”.
Cassino que voce vai adorar Blaze
купить свидетельство о рождении ссср купить свидетельство о рождении ссср .
Jogue no cassino aprovado Blaze
Desfrute da emocao no melhor cassino Blaze
What a data of un-ambiguity and preserveness of valuable know-how on the topic of unexpected emotions.
регистрация bitz casino
O melhor cassino para grandes vitorias Blaze
Всем привет! Может кто знает, где найтиполезные блоги о недвижимости? Пока нашел https://ak-3.ru
Sua sorte esta no cassino confiavel Blaze
Здравствуйте!
Недавно мы обновили напольные покрытия в доме. На сайте https://hobbihouse.ru/laminat/pochemu-spc-laminat-vinilpol-i-clusterfloor-samye-populyarnye-v-rf/ нашли полезную информацию, которая помогла сделать правильный выбор. Мы выбрали натуральные покрытия, отличающиеся надежностью и практичностью. Благодаря этим рекомендациям и стабильности характеристик покрытия, укладка прошла успешно, обеспечив защиту от влаги и ровное покрытие, соответствующее нашему стилю.
онлайн покупка
напольное покрытие VinilPol
розетки из пола
проблемы укладки имонтаж ПВХ
выбор кварцвиниловой плитки
выбор ковролина
пятиугольный паркет
Удачи!
купить квартиру в казани новостройка от застройщика https://nedvizhimost47.ru
Jogue com prazer neste cassino Blaze
купить квартиру от застройщика https://novostroyka47.ru
купить свидетельство о разводе http://www.school-10-lik.ru .
Seu cassino online favorito Blaze
Приветствую. Подскажите, где найтиразные статьи о недвижимости? Пока нашел https://eniseyburvod.ru
https://ktrcycleworld.com/%d0%b2%d1%96%d0%b4%d1%80%d0%be%d0%b4%d0%b6%d0%b5%d0%bd%d0%bd%d1%8f-%d1%80%d0%b0%d0%b4%d1%96%d0%be-%d0%bf%d1%8f%d1%82%d0%bd%d0%b8%d1%86%d1%8f-%d0%bd%d0%be%d0%b2%d0%b8%d0%b9-%d1%84%d0%be%d1%80/
куплю диплом http://www.school-10-lik.ru .
Hello i am kavin, its my first time to commenting anyplace, when i read this post i thought i could also make comment due to this brilliant post.
opengadjet.ru/page/4
newsato.ru/page/33
nfrap.ru/photogallery/964/index.html
medicineshocknews.ru/page/7
http://www.salaam.co.uk/biographies/profile.php?id=144
Приветствую. Подскажите, где почитатьразные статьи о недвижимости? Пока нашел https://floor-ashton.ru
Всем привет! Может кто знает, где найтиполезные статьи о недвижимости? Сейчас читаю https://gismt72.ru
купить аттестат за 9 классов diplomvash.ru .
Teste sua sorte no melhor cassino Blaze
купить диплом менеджера https://school5-priozersk.ru/ .
Приветствую. Подскажите, где найтиразные блоги о недвижимости? Сейчас читаю https://kamenolomnya43.ru
Проведение независимой строительной экспертизы — сложный процесс, требующий глубоких знаний. Наши специалисты обладают всеми необходимыми навыками, а их заключения часто служат основой для принятия верных стратегических решений. Строительно-техническая экспертиза https://stroytehexp.ru позволяет выявить факторы, вызвавшие ухудшение эксплуатационных характеристик объектов, проверить соответствие возведённых зданий градостроительным нормам.
Информационный ресурс https://ardma.ru, посвящен бизнесу, финансам, инвестициям и криптовалютам. Сайт предлагает экспертные статьи, аналитические отчеты, стратегии и советы для предпринимателей и инвесторов. Здесь можно найти новости и обзоры о бизнесе, маркетинге, трейдинге, а также практические рекомендации по различным видам заработка и управлению финансами.
Recomendo o melhor cassino Blaze
Всем привет! Может кто знает, где почитатьразные статьи о недвижимости? Сейчас читаю https://kuler-tsentr.ru
Приветствую. Может кто знает, где почитатьразные статьи о недвижимости? Сейчас читаю https://liem-com.ru
Мята знакомства скачать
Hey there! This is my first comment here so I just wanted to give a quick shout out and tell you I really enjoy reading through your articles. Can you suggest any other blogs/websites/forums that cover the same topics? Thanks for your time!
Рекомендуем заказать грифы для гантелей на https://grify-dlya-gantely.ruпо адекватным ценамоптимальной длины. В производстве износостойкого инвентаря применяются углеродистые марки стали. Грифы для гантелей создаются в трех востребованных диаметрах. Снаряды разработаны для силовых тренировок и выполнены с разметкой и накаткой для хвата. Снаряды покрываются предохранительным составом хрома и никеля. Российская фирма предлагает внушительный объем тренировочного оборудования для дома и фитнес центра. Это универсальный инструмент для силовых занятий в любых условиях.
Hmm is anyone else having problems with the images on this blog loading? I’m trying to determine if its a problem on my end or if it’s the blog. Any responses would be greatly appreciated.
remont-okon.od.ua/index.php?subaction=userinfo&user=uqepyd
rem-penata.ru/remont/natyazhnyie-potolki
http://www.91hongyi.com/member/index.php?uid=ydoqufebo
shop.electricoresigns.com/index.php?route=information/blogger&blogger_id=6
osspb.ru/osnews/10101
Desfrute dos jogos no melhor cassino Blaze
O cassino dos seus sonhos Blaze
Hiya very cool site!! Guy .. Beautiful .. Superb .. I’ll bookmark your site and take the feeds additionally? I’m glad to seek out numerous helpful information right here in the publish, we want develop more strategies in this regard, thanks for sharing. . . . . .
http://www.testruslit.ru/forum/viewtopic.php?p=70335
aboutalltour.ru/page/3/
sharypovo.today/news/society/page/9/
microstockhowto.com/tag/community/
honda-fit.ru/forums/index.php?autocom=gallery&req=si&img=5224
Любому человеку рано или поздно приходится пользоваться услугами стоматологических клиник. Ни для кого не секрет, что лечение зубов и последующее протезирование – процедуры довольно дорогостоящие, не все граждане могут позволить себе их оплатить, если вам необходимо стоматология в набережных челнах мы Вам обязательно поможем.
Особенности
Благодаря услугам, которые предлагает населению стоматология Маэстро, люди разного финансового достатка имеют возможность не только поддерживать здоровье полости рта, но и проходить все необходимые процедуры. Цены на лечение зубов и протезирование значительно ниже, чем в других медучреждениях. Несмотря на то, что клиника работает для широких слоев населения, пациенты получают полный перечень услуг, используя современное оборудование и качественные материалы. Жителям доступны следующие процедуры:
• профилактика полости рта;
• лечение зубов с использованием различных методов;
• полная диагностика;
• профессиональная чистка;
• отбеливание;
• протезирование.
Сотрудники учреждения соблюдают все санитарные нормы, а для тщательной дезинфекции и стерилизации инструментов предусмотрено современное оборудование.
Преимущества
Востребованность бюджетной стоматологии объясняется рядом преимуществ. Во-первых, в клинике трудятся опытные высококвалифицированные сотрудники. Во-вторых, к каждому пациенту врач находит подход. В-третьих, кабинеты оснащены всем необходимым оборудованием, в работе используют только качественные безопасные материалы. В-четвертых, все виды протезирования будут проведены в сжатые сроки. Многие клиники получают субсидии от государства, что позволяет существенно сократить расходы. Кроме того, некоторые стоматологии сотрудничают со страховыми компаниями, поэтому у пациентов появляется возможность получить услуги по полюсу ОМС. Пациенты получают консультацию по профилактике заболеваний полости рта. Врачи после тщательного осмотра составляют индивидуальный план лечения, с помощью которого удается добиться наилучшего результата. Более доступные цены достигаются не только благодаря государственному финансированию, но и оптимизации расходов.
Благодаря стоматологии Маэстро, человек с небольшим достатком может не только вылечить зубы, но и поддерживать здоровье ротовой полости. Теперь любой человек может не откладывать поход к стоматологу, выбирая доступное качественное обслуживание.
Приветствую. Подскажите, где почитатьполезные статьи о недвижимости? Сейчас читаю https://santam1.ru
купить диплом в ангарске https://vm-tver.ru .
Приветствую. Подскажите, где почитатьполезные статьи о недвижимости? Пока нашел https://sibarit54.ru
купить диплом в орле купить диплом в орле .
Приветствую. Подскажите, где найтиполезные статьи о недвижимости? Пока нашел https://stroyproektm.ru
Cassino com as melhores promocoes Blaze
Студия предлагает профессиональные меры по технической поддержке веб-сервиса на https://podderzhka-dlya-saita.ru/ по приятным ценам. Заполним веб-ресурс смысловым контентом. Окажем услуги по круглосуточному мониторингу и защите от кибератак. Работники окажут доступные услуги по программированию веб-сервисов. Рекомендуем оформить выгодные расценки с абонентской платой. Тарифные планы различаются по ключевым факторам: времени работ, объема страниц и других.
Seu destino para grandes premios Blaze
южный парк мультсериал южный парк 1 сезон смотреть
Appreciating the commitment you put into your website and detailed information you present. It’s nice to come across a blog every once in a while that isn’t the same out of date rehashed information. Wonderful read! I’ve saved your site and I’m including your RSS feeds to my Google account.
sdo.rea.ru/siteFDO/?executorID=ForumExecutor&mode=showThemes&&cursor=60
diplomsagroup.com/diplomy-po-specialnosti/diplom-inzhenera-tehnologa.html
eqagent.ru/users/36?wid=426
auto-dealers-script.com/gallery
winemastery.com.vn/giong-nho/garnacha-tintorera
южный парк 2 сезон south park смотреть онлайн
южный парк онлайн бесплатно https://southpark-serial.ru
южный парк смотреть на русском https://southpark-serial.ru
южный парк все сезоны https://southpark-serial.ru
южный парк онлайн на русском https://southpark-serial.ru
южный парк 1 серия https://southpark-serial.ru
As melhores slots estao aqui Blaze
южный парк в хорошем качестве https://southpark-serial.ru
южный парк 3 сезон южный парк бесплатно
Seu cassino de confianca online Blaze
Hmm is anyone else encountering problems with the images on this blog loading? I’m trying to determine if its a problem on my end or if it’s the blog. Any feed-back would be greatly appreciated.
fat-girls.ru/page/10
mybaltika.info/ru/print/587/7892/
weekinato.ru/page/13/
goodgame.ru/user/1629660
http://www.khedmeh.com/wall/blogs/user/garrysurman?&page=1
It’s amazing for me to have a web page, which is valuable in favor of my knowledge. thanks admin
onlineboxing.net/jforum/user/profile/287687.page
mypenza.ru/forum/index.php?showtopic=54674&mode=linear
forum.oursson.ru/viewtopic.php?f=117&t=2899%C3%82%C2%A0
arjaniki.ru/memberlist.php?sk=m&sd=d&first_char=r&mode=searchuser&start=75
buldingnews.ru/page/3
A casa dos grandes vencedores Blaze
https://iqratrust.org/
https://irhsca.org/
https://muslim-forum.org/
OW
Ganhe muito no melhor cassino Blaze
Приветствую. Может кто знает, где найтиполезные статьи о недвижимости? Пока нашел https://417-017.ru
Приветствую. Подскажите, где почитатьразные статьи о недвижимости? Пока нашел https://aquatopnn.ru
Many online gambling houses offer bonuses for registration beginners, depositing their 1st deposit in an http://www.heerfamily.net/mediawiki/index.php/Interesting_Online_Casino_In_Canada, and sometimes and for the subsequent game.
be you haven’t launched a branded podcast yet, https://www.ruperts.net/2015/11/i-am-back-at-work/ of webinars are be a natural step towards launching a new show.
Приветствую. Подскажите, где почитатьразные блоги о недвижимости? Сейчас читаю https://asiatreid.ru
Ежегодно в середине сентября организовывается Тюменский инновационный форум «НЕФТЬГАЗТЭК».
Форум посвящен определению механизмов инновационного развития отраслей топливно-энергетического комплекса, обсуждению и определению решений, созданию наилучших обстоятельств для расчета инноваторских проектов. Ежегодный тюменский форум является влиятельной дискуссионной площадкой по развитию нефтегазовой отрасли в Российской Федерации, содержит большой авторитет и своевременность, созвучен корпоративной стратегии продвижения инновационного курса в Российской Федерации
https://neftgaztek.ru/
https://vyzov-santehnika-na-dom.ru.
Заходите на наш ресурс, где вы найдете много полезных статей на тему приемки квартиры в новостройке или покупки квартиры без отделки. Узнайте, как обезопасить себя от ненадёжных застройщиков, какие проверки провести перед покупкой жилья, и о многом другом!
https://citadel-ca.ru
Вибирайте популярні перевірені ігор в casino, на зразок блекджек, рулетка і онлайн казино з шансом виграти джекпот.
Мне очень жаль, ничем не могу Вам помочь. Я думаю, Вы найдёте верное решение. Не отчаивайтесь.
где-то, http://minatomotors.com/2016/08/12/%e3%83%aa%e3%82%a2%e3%82%92%e4%ba%8b%e6%95%85%e3%81%97%e3%81%9f%e3%82%ab%e3%83%ad%e3%83%bc%e3%83%a9%e3%83%95%e3%82%a3%e3%83%bc%e3%83%ab%e3%83%80%e3%83%bc%e3%81%ae%e4%bf%ae%e7%90%86/ чтобы полностью зарядить аккумулятор электронной сигареты длится не более чем полутора часа.
ми крім того пропонуємо продукти http://gyeongshin.co.kr/ksen/bbs/board.php?bo_table=free&wr_id=806942 для побутового застосування. Використовується більше, ніж в 250 тисячах компаній в 180 країнах світу.
Например, https://odessa.foroesp.com/viewtopic.php?id=144#p381 направления «фиат-фиат» поддерживают сервисы Ферма и Шахта. Закрывает обзоры сетевых-криптообменников в российской федерации baksman – альтернатива, которая открыта в последнее время.
… люди и организации, вступившие в договорные отношения с госструктурами, должны получить уверенность, [url=https://cabinetchallenges.com/index.php/commentaire]https://cabinetchallenges.com/index.php/commentaire[/url] что их права будут охранены».
Приветствую. Может кто знает, где почитатьразные статьи о недвижимости? Пока нашел https://etalon-voda.ru
https://Dr-nona.ru – dr nonna
Приветствую. Может кто знает, где найтиполезные статьи о недвижимости? Пока нашел https://floor-ashton.ru
Всем привет! Может кто знает, где почитатьполезные блоги о недвижимости? Пока нашел https://kait-volga.ru
Aventura e diversao em um so cassino Blaze
Всем привет! Может кто знает, где найтиразные блоги о недвижимости? Сейчас читаю https://kamenolomnya43.ru
Откройте двери в мир недвижимости с нашим порталом!
Прочтите экспертные статьи от специалистов в области недвижимости. Узнавайте о налогах на недвижимость, осуществляйте успешные сделки купли-продажи квартир, и всегда оставайтесь в курсе последних тенденций рынка.
http://ufficioporta.ru
https://Dr-nona.ru/ – dr. nona
Cassino com os maiores jackpots Blaze
Sua diversao garantida no nosso cassino Blaze
Привет игроки!
Регистрация на 1win заняла всего пару минут. Приятные бонусы, быстрый вывод денег, удобное приложение. Рабочее зеркало всегда под рукой. Играю с удовольствием, рекомендую всем попробовать 1win! скачать приложение 1win
Недавно начал играть на 1win и уже в восторге. Приятные бонусы, быстрый вывод денег, удобный сайт и рабочее зеркало всегда доступно. 1win – это лучший выбор для ставок и казино. Рекомендую!
Ловите сайт где все в лучшем виде! – https://1winapk.kz
1win коллаген витамин с collagen
1win слоты играть скачать
1win partners зеркало
скачать приложение 1win на ios
схема заработка 1win
1win бонусы на спорт что это
1win рабочее зеркало 1win bp6 xyz
Удачи!
Приветствую. Подскажите, где почитатьразные блоги о недвижимости? Сейчас читаю https://krepegmaster.ru
Descubra o melhor cassino online Blaze
Всем привет! Может кто знает, где найтиполезные блоги о недвижимости? Сейчас читаю https://kuler-tsentr.ru
Highly energetic article, I enjoyed that
a lot. Will there be a part 2?
Divirta-se no cassino mais confiavel Blaze
Всем привет! Подскажите, где почитатьполезные статьи о недвижимости? Сейчас читаю https://oscltd.ru
Всем привет! Может кто знает, где найтиполезные статьи о недвижимости? Сейчас читаю https://redglade-nn.ru
As melhores slots estao aqui Blaze
In recent times, Africa has emerged as a vibrant hub for tunes and celebrity tradition, gaining international recognition and influencing international trends. African music, with its rich tapestry of genres such as Afrobeats, Amapiano, and highlife, offers captivated audiences globally. Major artists just like Burna Boy, Wizkid, and Tiwa Savage have not just dominated the graphs in Africa but have also made substantial inroads into the global music landscape. Their collaborations with international stars and even performances at main music festivals have highlighted the continent’s musical prowess. The particular rise of digital platforms and social media has even more amplified the reach of African music, allowing artists in order to connect with enthusiasts across the earth and share their particular sounds and tales – https://histoires-africaines.africa/texte-original-les-systemes-d-ionisation-de-l-eau/.
In addition to be able to its musical expertise, Africa’s celebrity lifestyle is flourishing, using entertainers, influencers, and public figures commanding large followings. Superstars such as Lupita Nyong’o, Trevor Noah, and Charlize Theron, who have origins in Africa, happen to be making waves worldwide in film, television set, and fashion. These kinds of figures not merely provide attention to their own work but in addition reveal important sociable issues and ethnic heritage. Their achievement stories inspire a new generation associated with Africans to pursue careers in typically the entertainment industry, promoting a sense of pride and even ambition across typically the continent.
Moreover, African celebrities are more and more using their websites to advocate with regard to change and provide back to their residential areas. From Burna Kid’s activism around interpersonal justice issues to be able to Tiwa Savage’s attempts to promote education with regard to girls, these open figures are utilizing their influence intended for positive impact. They may be involved in numerous philanthropic activities, promoting causes such since healthcare, education, and environmental sustainability. This trend highlights typically the evolving role associated with celebrities in Africa, who are not merely entertainers but in addition key players within driving social switch and development.
Overall, the landscape involving music and celeb culture in Africa is dynamic and ever-evolving. The continent’s rich cultural diversity and creative talent still garner worldwide acclaim, positioning The african continent being a major pressure in the global enjoyment industry. As African-american artists and superstars carry on and break barriers and achieve brand-new heights, they pave how for a more inclusive in addition to diverse representation throughout global media. Regarding those interested in staying updated upon the latest tendencies and news within this vibrant picture, numerous platforms plus publications offer complex coverage of Africa’s music and celebrity happenings, celebrating the particular continent’s ongoing input to the world stage.
Experimente a sorte no cassino mais famoso Blaze
Всем привет! Может кто знает, где почитатьполезные блоги о недвижимости? Сейчас читаю https://stroyproektm.ru
Hello! trusted online pharmacy reviews very good internet site.
Ganhe muito no melhor cassino Blaze
Hayallerinizdeki kumarhane Sweet bonanza
Всем привет! Может кто знает, где почитатьразные статьи о недвижимости? Пока нашел https://velikaya-stena.ru
Приветствую. Может кто знает, где почитать разные статьи о недвижимости? Пока нашел https://1eve1.ru
Получай азарт и адреналин в 1win казино, зарабатывай деньги.
Лучшие игровые автоматы в 1win казино, гарантируют яркие эмоции.
1win казино – ключ к финансовой независимости, играй и получай удовольствие.
Почувствуй вкус победы вместе с 1win казино, получай крупные выигрыши.
1win казино – твой шанс на удачу и успех, подари себе азарт и адреналин.
Почувствуй адреналин победы в 1win казино, забирай свой джекпот.
1win казино – это место, где рождаются чемпионы, претворить свои мечты в реальность.
Богатство и успех с 1win казино, гарантировано доставит тебе радость.
1win официальный сайт https://luchshiye-onlayn-kazino-rb.com/ .
1win казино: играй и выигрывай, присоединяйтесь сейчас!
1win казино: ваш ключ к азартным играм, играйте и выигрывайте без ограничений!
1win казино – где каждый становится победителем, начните игру прямо сейчас!
1win казино: ваш путь к легким деньгам, станьте победителем вместе с 1win казино!
1win казино – ваш первый шаг к успеху, присоединяйтесь к победителям!
1win https://populyarnoye-onlayn-kazino-belarusi.com/ .
Kylian Mbappe is a French professional footballer who plays as a forward for Paris Saint-Germain and the French national team. Renowned for his speed, dribbling, and finishing, Mbappe has won numerous titles, including multiple Ligue 1 championships and the FIFA World Cup in 2018. Find out more about him here – https://kylianmbappe.paris-saint-germain-ar.com/
En iyi cevrimici kumarhaneyi kesfedin Sweet bonanza
Hello there! can i purchase generic finasteride prices good web site.
Проститутки Тюмени
En iyi promosyonlara sahip casinolar Sweet bonanza
Приветствую. Подскажите, где найти разные блоги о недвижимости? Сейчас читаю https://ilinka2.ru
En guvenilir kumarhanede eglenin Sweet bonanza
Dedicated to the brave players!!
Glory Casino offers quality and reliability. There are bonuses for new players, high betting odds, and fast withdrawals. The working mirror is always available. I play and win with pleasure. I recommend trying it!
I downloaded the Glory Casino app on Android and now I can play anytime. The interface is user-friendly, and there are plenty of bonuses and promotions. Withdrawals are fast and hassle-free. Glory Casino is my number one choice for betting and casino!
Glory Casino
Glory Casino download for free
free spins Glory Casino
Glory Casino sign in
Glory Casino lucky jet
Glory Casino slot machines
Good profits!
En iyi slotlar burada Sweet bonanza
Herkesin tavsiye ettigi kumarhane Sweet bonanza
En unlu kumarhanede sans?n?z? deneyin Sweet bonanza
En iyi kumarhanede buyuk kazan?n Sweet bonanza
Bons casino는 다양한 슬롯 게임과 매력적인 보너스를 제공합니다. 본즈 카지노 입구에서 간편하게 가입하고 로그인하여 다양한 혜택을 누리세요. 본즈 보너스 코드를 입력하면 추가 보너스를 받을 수 있습니다. 또한, bons 모바일 앱을 사용하면 언제 어디서나 게임을 즐길 수 있습니다. 본즈와 함께 흥미진진한 시간을 보내세요. 매주 새로운 이벤트와 보너스가 준비되어 있습니다. bons 보너스 카지노 모바일 애플리케이션
En iyi kumarhaneyi tavsiye ederim Sweet bonanza
Hello! get cheap valacyclovir tablets excellent internet site.
сервис ремонта сотовых
Hi there friends, how is all, and what you wish for to say regarding this paragraph, in my
view its really awesome in favor of me.
Когда мы потеряли близкого человека, сотрудники https://complex-ritual.ru/ с большим сочувствием помогли нам организовать достойные похороны. Они взяли на себя все хлопоты: обряд, транспорт, оформление документов. Работа выполнена безупречно: корректный и пунктуальный персонал, скрупулезное внимание к деталям. Цены более чем приемлемые для такого высокого уровня сервиса. Рекомендуем эту компанию – в трудный час они окружат вас заботой.
Sizin icin en iyi online casino Sweet bonanza
Kumar oynamak icin mukemmel bir yer Sweet bonanza
En iyi kumarhanede sans?n?z? deneyin Sweet bonanza
Приветствую. Может кто знает, где почитатьразные блоги о недвижимости? Сейчас читаю https://art-salon-hudojnik.ru
где купить dolce gabbana http://www.scm-fashion.ru .
Приветствую. Может кто знает, где найтиполезные блоги о недвижимости? Сейчас читаю https://likolordom.ru
En guvenilir kumarhanede kazan?n Sweet bonanza
buy wow raid boost kreativwerkstatt-esens.de .
Herkesin tavsiye ettigi kumarhane Sweet bonanza
http://maps.google.by/url?q=https://generik-spb.ru
En iyi kumarhanede buyuk kazan?n Sweet bonanza
H?zl? odeme yapan kumarhane Sweet bonanza
Интернет магазин металлов из разноцветных (а) также чёрных металлов “STORM”
https://stormbrand.ru/
Online work is reshaping the modern workplace, offering flexibility and convenience that conventional office environments often lack. It enables individuals to work from any location with an internet connection, breaking down geographical barriers and facilitating companies to tap into a global talent pool. This change has led to a rise in telecommuting and freelance opportunities, permitting workers to juggle their professional and personal lives more effectively. Additionally, online work can produce increased productivity and job satisfaction, as employees have more control over their calendars and work environments. However, it also introduces challenges such as maintaining work-life boundaries, guaranteeing effective communication, and managing time efficiently. Overall, online work is a revolutionary force, reshaping the way we think about employment and productivity in the digital age.
En iyi kumarhanelerde sans?n?z? deneyin Sweet bonanza
https://clients1.google.cl/url?sa=t&url=https://generik-spb.ru
Hello players!!
Win big with Baji999 Casino! Enjoy a wide variety of games and sports betting options. Claim your bonuses and elevate your gaming experience. Baji999 is your gateway to success!
Elevate your gaming experience at Baji999! Enjoy exciting casino games, sports betting, and lucrative bonuses. Baji999 is your ticket to successful gaming. Join today and play to win!
Catch the site where everything is in the best shape! – Baji999
Baji999 Casino register
Baji999 Casino xyz
Baji999 Casino download for iPhone mirror
mobile mirror Baji999 Casino
Baji999 Casino working mirror for today
Good profits!
Hello everyone!!
After downloading MCW Casino on my Android device, I’ve enjoyed unrestricted gaming pleasure. The surprise bonuses and constant availability of the working mirror have been delightful. Fast withdrawals make MCW Casino an ideal choice for both betting and casino enthusiasts. I urge everyone to give it a try!
Mega Casino World: Registering at MCW Casino was swift, taking only minutes. The bonuses are enticing, withdrawals are speedy, and the app is user-friendly. With a reliable mirror always on standby, I enjoy playing and recommend everyone give MCW Casino a try!
Catch the site where everything is in the best shape! – MCW Casino
slot machines for money Mega Casino World games
slot machines for money Mega Casino World
download bk MCW Casino
Mega Casino World does not withdraw money
voucher MCW Casino today working promo codes for free spins
Good profits!
Glory Casino
дипломы награждения купить ast-diplom.com .
https://aoseulado.net/
https://image.google.sc/url?q=https://generik-spb.ru
стоимость оформления внж цифрового кочевника https://vnzh24.ru/
Всем привет! Подскажите, где найтиполезные статьи о недвижимости? Пока нашел https://art-salon-hudojnik.ru
Seveceginiz bir kumarhane Sweet bonanza
Приветствую. Подскажите, где почитатьразные блоги о недвижимости? Пока нашел https://design70.ru
Бонусы казино 7k casino могут быть использованы для увеличения шансов на выигрыш – рабочее зеркало сайта 7k casino
https://www.wildberries.ru/catalog/217171028/detail.aspx/
Patient medicine guide. Pill info here.
cheap tadacip 20 mg
Get pill info. Find pill info.
Bu kumarhanedeki en iyi oyunlar Sweet bonanza
комплексное продвижение сайта в интернете в москве
Привет, друзья!
Купить диплом любого ВУЗа
Наша компания предлагает быстро и выгодно приобрести диплом, который выполнен на бланке ГОЗНАКа и заверен печатями, водяными знаками, подписями. Данный диплом пройдет лубую проверку, даже с использованием специальных приборов. Решайте свои задачи быстро и просто с нашим сервисом.
Где приобрести диплом по нужной специальности?
http://forexsnews.ru/vash-diplom-v-kratchayshie-sroki-nadezhno-i-konfidentsialno
Окажем помощь!.
Рабочее зеркало казино 7k casino на сегодня готово для использования – игровые автоматы р7 казино регистрация
Мы с гордостью представляем богатую коллекцию качественных игровых слотов в букмекерской конторе 7к казино, чтобы удовлетворить самые разнообразные предпочтения игроков – r7 casino официальная страницы
На главной странице сайта casino представлена информация о Казино 7к казино, позволяя вам получить полное представление о наших услугах и особенностях игры – 7к казино работающее зеркало сайта
Казино 7к казино предлагает захватывающий игровой опыт с привлекательной визуальной графикой и высоким качеством игровых слотов для игры на реальные деньги – 7k casino официальный сайт лицензионный скачать бесплатно приложение
На главной странице сайта casino размещена информация о 7к казино и его предложениях – регистрация в р7 казино
En populer kumarhaneyi deneyin Sweet bonanza
В казино Marathonbet предусмотрены бонусы и привилегии для новых игроков – Marathonbet актуальное рабочее зеркало на сегодня
wow carry raid http://www.kreativwerkstatt-esens.de .
Обзор официального сайта букмекерской конторы 7к казино содержит полезную информацию, позволяющую вам получить полное представление о нашем игровом опыте и преимуществах – как зарегистрироваться в r7 casino
Issues do not load, you have to commence a list more than, or
messages do noot send suitable away.
Here is my web site … Embroidery
Официальный сайт букмекерской конторы 7к казино предоставляет полный обзор наших услуг, включая дополнительные детали о бонусах и привилегиях – r7 casino работающее страницы
Приветствую. Может кто знает, где найтиполезные блоги о недвижимости? Сейчас читаю https://lestnicy-ok.ru
Незаконные действия мошенников онлайн могут повлиять на Игровой аппарат – 7k casino официальное
Привет!
Мы можем предложить дипломы психологов, юристов, экономистов и других профессий по выгодным тарифам.
Мы готовы предложить документы ВУЗов, которые находятся в любом регионе России. Можно купить диплом за любой год, указав необходимую специальность и оценки за все дисциплины. Дипломы и аттестаты выпускаются на “правильной” бумаге самого высокого качества. Это дает возможность делать государственные дипломы, которые не отличить от оригиналов. Документы заверяются всеми необходимыми печатями и подписями.
Гарантируем, что при проверке документа работодателями, каких-либо подозрений не появится.
Где купить диплом по нужной специальности?
galantclub.od.ua/member.php?u=15983
Приветствую. Подскажите, где найтиразные статьи о недвижимости? Пока нашел https://modul724.ru
У казино 7k casino действует программа лояльности для постоянных игроков – 7k casino бонус за регистрацию
Formulation info listed. Drug information available.
buy tadalafil
Drug information available. Complete medicine overview.
На главной странице игрового портала размещена ссылка на официальный сайт 7к казино, где доступна всесторонняя информация – рабочий сайт 7к казино
Всем привет! Подскажите, где почитатьразные статьи о недвижимости? Сейчас читаю https://obereg-uv.ru
Официальный сайт букмекерской конторы Риобет предоставляет полный обзор своих услуг, включая дополнительную информацию о бонусах, программе лояльности и акциях, чтобы удовлетворить потребности игроков – Риобет работающее зеркало сайта
Казино Риобет предлагает захватывающий игровой опыт с привлекательной графикой и высококачественными игровыми слотами на реальные деньги, чтобы каждый игрок получил максимум удовольствия от игры – как зарегистрироваться в Riobet
Всем привет! Подскажите, где найтиразные статьи о недвижимости? Сейчас читаю https://sbitstroyservis.ru
потолок армстронг https://armstrong-ceiling24.ru/
Процесс регистрации занимает всего несколько минут – Риобет работающее страницы
Попробуйте обратиться к Mihaylov digital, их специализация это продвижение сайта в Google и Yandex, а также создание сайтов.
Привет!
Заказать диплом любого ВУЗа
Наши специалисты предлагают быстро и выгодно купить диплом, который выполняется на бланке ГОЗНАКа и заверен печатями, водяными знаками, подписями. Данный документ способен пройти любые проверки, даже при помощи специального оборудования. Достигайте свои цели быстро и просто с нашей компанией.
Где купить диплом по актуальной специальности?
https://agarwalconnect.com/blogs/192/Ваш-диплом-без-лишних-забот-быстро-и-безопасно
Поможем вам всегда!.
купить диплом симферополь asxdiplomik.com .
Привет, друзья!
Для определенных людей, приобрести диплом о высшем образовании – это необходимость, уникальный шанс получить хорошую работу. Однако для кого-то – это желание не терять массу времени на учебу в универе. С какой бы целью вам это не понадобилось, мы готовы помочь вам. Быстро, качественно и недорого изготовим документ любого ВУЗа и любого года выпуска на настоящих бланках со всеми печатями.
Наши специалисты предлагают выгодно и быстро купить диплом, который выполняется на оригинальном бланке и заверен мокрыми печатями, штампами, подписями официальных лиц. Диплом способен пройти лубую проверку, даже с применением специально предназначенного оборудования. Решите свои задачи быстро и просто с нашей компанией.
Где заказать диплом по нужной специальности?
http://pora-valit.com/wiki/index.php?title=%D0%98%D0%B7%D0%B2%D0%B5%D1%81%D1%82%D0%BD%D1%8B%D0%B9_%D0%BC%D0%B0%D0%B3%D0%B0%D0%B7%D0%B8%D0%BD,_%D0%BF%D1%80%D0%B5%D0%B4%D0%BB%D0%B0%D0%B3%D0%B0%D1%8E%D1%89%D0%B8%D0%B9_%D0%B4%D0%B8%D0%BF%D0%BB%D0%BE%D0%BC%D1%8B_%D0%BD%D0%B0_%D0%93%D0%9E%D0%97%D0%9D%D0%90%D0%9A%D0%B5
Удачи!
Приветствую. Может кто знает, где найтиполезные статьи о недвижимости? Сейчас читаю https://studiocolors-nsk.ru
купить диплом ростов diplomyx.com .
купить аттестат с занесением купить аттестат с занесением .
I believe super-bantamweight is my division now, so in 2024 I will look to show even greater type.
Here is my homepage – 플리츠
Бренд казино 7k casino, основанный в 2023 году, сразу покорил азартных игроков своим качеством и разнообразием услуг, стремясь стать лидером рейтинга – 7k casino зеркало игровые автоматы
Казино 7k casino обеспечивает быстрые и надежные транзакции при пополнении и выводе средств – 7к казино работающее страницы
Воздействие незаконных действий и попыток взлома на онлайн игровые автоматы минимально – р7 казино официальный регистрация
7к казино предлагает обширный выбор качественных игровых слотов в своей коллекции – r7 casino официальный сайт рабочее зеркало
купить диплом в троицке asxdiplomik24.ru .
Twitter tools give extensive analytics past what the native platform offers. They track metrics like interaction prices, follower growth, impressions, as well as click-through rates. Analyzing these metrics assists you comprehend what content resonates with your reader, when they are most energetic, and also which hashtags carry out best. Tools like Sprout Social as well as Hootsuite deliver personalized documents that permit you to visualize information styles eventually, helping in strategic decision-making, https://www.xpgamesaves.com/members/kaileygdwatts.1518528/.
порно худых русских телок russkie-hudyshki.ru .
купить диплом в химках asxdiplomik.com/kupit-diplom-moskva .
Защитите свою конфиденциальность с резидентским прокси, прибегнуть к этим инструментом.
В чем особенность резидентских прокси?, прочитайте подробностями.
Как выбрать лучший резидентский прокси, инструкция для пользователей.
Какие задачи решают резидентские прокси?, подробнее ознакомьтесь с возможностями.
Как резидентские прокси обеспечивают безопасность?, обзор функций безопасности.
Какие риски может предотвратить резидентский прокси?, разберем важные аспекты.
Какие преимущества дает использование резидентских прокси?, рассмотрим основные плюсы.
Секреты увеличения скорости с резидентским прокси, советы для оптимизации работы.
Почему резидентский прокси стоит использовать для парсинга, обзор возможностей для парсеров.
Секреты анонимности с резидентским прокси, практические шаги к безопасности онлайн.
Как улучшить работу в социальных сетях с резидентским прокси, рекомендации функционала.
Как сэкономить время с помощью аренды резидентского прокси?, сравним лучшие варианты.
Как избежать DDoS с резидентским прокси?, подробно изучим меры безопасности.
Почему резидентские прокси пользуются популярностью, рассмотрим основные факторы.
Сравнение резидентских и дата-центровых прокси, рекомендации для выбора.
резидентские прокси купить https://rezidentnieproksi.ru/ .
Всем привет! Может кто знает, где почитать разные статьи о недвижимости? Пока нашел https://adeldv.ru
Здравствуйте!
Где купить диплом по необходимой специальности?
Мы изготавливаем дипломы любой профессии по приятным тарифам.
angeartsgifts.com/c_feedback/?page=4228
Защитите свои данные с помощью резидентских прокси, преимущества.
Обходите географические блокировки с резидентскими прокси, широким контентом.
Оптимизируйте работу сети благодаря резидентским прокси, в чем преимущество.
Защитите свои учетные данные и личную информацию с резидентскими прокси, и чувствуйте себя спокойно.
Сделайте свои онлайн-активности невидимыми благодаря резидентским прокси, и наслаждайтесь анонимностью.
Используйте резидентские прокси для безопасного серфинга в интернете, и не опасайтесь за свою приватность.
прокси резидентные https://rezidentnie-proksi.ru/ .
Hello everyone !
Discover Limelight Stream, where your entertainment experience reaches new heights. Our platform offers a comprehensive collection of movies, TV series, documentaries, and exclusive content, all curated to satisfy diverse tastes. We pride ourselves on delivering stunning HD quality for a flawless viewing experience. Our user-friendly interface allows you to explore and find content effortlessly, ensuring you spend more time watching and less time searching. Whether you’re looking for the latest blockbuster, a timeless classic, or an exclusive series, http://www.limelight-stream.com// has it all. Stream on your TV, laptop, tablet, or smartphone, and enjoy uninterrupted entertainment wherever you are. Join us today and explore a world of premium content that’s always at your fingertips.
Limelight streaming tutorials
Game streaming for gamers
Limelight streaming quality
Best free game streaming tools
Limelight supported devices
Good luck!
Здравствуйте!
Как правильно купить диплом колледжа и ВУЗа в России, подводные камни
talkitter.com/read-blog/202613
Поможем вам всегда!.
http://health-diet.ru/away.php?to=https://generik-spb.ru/kombinirovannye/super-tadarise-sialis-20-mg-dapoksetin-60-mg
Высокие коэффициенты на спортивные события | Безопасные ставки на 1win | Ставки с 1win – отличный выбор | 1win – верный помощник для ставок| Выбор успешных игроков – 1win| 1win делает игру насыщенной и интересной| 1win приближает к победе| 1win – это возможность сделать ставку на победу| 1win поможет вам стать чемпионом| 1win – это ваш верный партнер в ставках
1win вход https://1win-bk.by/ .
Приветствую. Подскажите, где найти полезные блоги о недвижимости? Сейчас читаю https://galastroy-sk.ru
1win – ваш идеальный партнер для ставок
Удача всегда на вашей стороне с 1win
1win – место, где рождаются победы
Успех начинается с 1win
Букмекерская контора 1win радует своих клиентов каждый день
1win – ваша дверь в мир азарта и выигрышей
1win – ваш ключ к миру ставок и азарта
1win – выбор тех, кто ценит качество и надежность
1win – ваш верный путь к финансовой независимости
1win – это бесконечные возможности для выигрышей
Ставки на спорт никогда не были такими увлекательными как с 1win
1win делает вашу игру более прибыльной и увлекательной
Ставки на спорт становятся простыми с 1win
1win делает ставки доступными для всех|1win – это ваша дверь в мир азарта и прибыли
1win гарантирует вам качественный сервис и высокие шансы на успех|1win предлагает вам только лучшие условия для ставок|1win делает вашу игру интересной и прибыльной|1win – ваш проводник в мире ставок и азарта|Играйте и выигрывайте с 1win|Ставки на спорт с 1win – это ваш шанс изменить свою жизнь|1win – букмекер, на которого можно положиться|Ваши ставки всегда успешные с 1win|1win – идеальное место для вашего успеха|Начните свой путь к победе с 1win|1win – это ваш ключ к финансовой независимости|1win делает вашу игру увлекательной и прибыльной|1win – это ваш ключ к финансовой стабильности|1win – это ваш путь к азарту и прибыли|1win – ваш верный партнер в мире ставок|Сделайте вашу игру увлекательной и прибыльной с 1win|Присоединяйтесь к лидерам ставок на 1win|Ув
1win беларусь 1win беларусь .
купленный диплом купленный диплом .
купить диплом мба asxdiplomik.com/kupit-diplom-moskva .
Приветствую. Может кто знает, где почитать разные блоги о недвижимости? Пока нашел https://hameleon1.ru
En iyi kumarhaneyi tavsiye ederim Sweet bonanza
Здравствуйте!
Мы можем предложить документы техникумов, которые расположены на территории всей Российской Федерации. Вы имеете возможность приобрести качественный диплом за любой год, включая сюда документы СССР. Дипломы и аттестаты делаются на бумаге высшего качества. Это позволяет делать государственные дипломы, которые не отличить от оригиналов. Они заверяются всеми требуемыми печатями и штампами.
Приобрести диплом ВУЗа.
hhi.instructure.com/eportfolios/15374/Home/________2
Удачи!
https://cse.google.ch/url?sa=i&url=https://generik-spb.ru/kombinirovannye/super-tadarise-sialis-20-mg-dapoksetin-60-mg
Здравствуйте!
Приобрести документ ВУЗа можно у нас в столице.
ast-diplom.com/kupit-diplom-o-srednem-obrazovanii
Хорошей учебы!
где можно купить диплом о высшем образовании diplomyx.com .
сколько стоит купить диплом экономиста asxdiplomik.com .
цена диплома о высшем образовании ast-diploms.com .
купить аттестат за 9 класс цена купить аттестат за 9 класс цена .
Здравствуйте!
Приобретение диплома ПТУ с сокращенной программой обучения в Москве
iaescortsmap.ixbb.ru/viewtopic.php?id=108#p108
Всегда вам поможем!.
Добрый день!
Мы можем предложить документы техникумов, расположенных в любом регионе России. Вы сможете приобрести диплом от любого учебного заведения, за любой год, указав актуальную специальность и оценки за все дисциплины. Дипломы и аттестаты печатаются на бумаге самого высшего качества. Это дает возможности делать государственные дипломы, не отличимые от оригиналов. Документы заверяются всеми необходимыми печатями и подписями.
Купить диплом любого университета.
sonnick84.rusedu.net/post/10787/113383
Успехов в учебе!
Всем привет! Подскажите, где найти полезные блоги о недвижимости? Пока нашел https://iskrb.ru
Здравствуйте!
Купить документ о получении высшего образования можно в нашей компании.
diplomasx.com/kupit-diplom-ekaterinbur
Удачи!
Awesome post.
купить справку о болезни
Приветствую. Подскажите, где почитать разные блоги о недвижимости? Сейчас читаю https://juzhnybereg24.ru
купить справку
Kumar oynamak icin en iyi secim Sweet bonanza
продажа дипломов куплю диплом asxdiplomik24.ru .
Здравствуйте!
Где купить диплом по необходимой специальности?
electricsheep.activeboard.com/forum.spark
Хорошей учебы!
Привет, друзья!
Мы предлагаем быстро и выгодно заказать диплом, который выполняется на бланке ГОЗНАКа и заверен печатями, водяными знаками, подписями должностных лиц. Документ пройдет любые проверки, даже при использовании специального оборудования. Решайте свои задачи быстро с нашим сервисом.
army.clanfm.ru/viewtopic.php?f=2&t=38201
Удачи!
Всем привет! Подскажите, где найти полезные блоги о недвижимости? Сейчас читаю https://klimat-hck.ru
[u][b] Привет![/b][/u]
[b]Где приобрести диплом по необходимой специальности?[/b]
[b]Мы изготавливаем дипломы[/b] любой профессии по приятным ценам.
[url=http://pmk-polymer.ru/content/kontakty]pmk-polymer.ru/content/kontakty[/url]
Диплом техникума купить официально с упрощенным обучением в Москве
diplomyx24.ru/kupit-diplom-rostov-na-donu
https://clients1.google.es/url?sa=i&url=https://severtent.ru/
купить диплом высшем образовании без предоплаты ast-diploms.com .
купить диплом о среднем образовании в калининграде купить диплом о среднем образовании в калининграде .
[u][b] Добрый день![/b][/u]
[b]Приобрести документ[/b] о получении высшего образования можно у нас.
[url=http://asxdiplomik24.ru/kupit-diplom-nizhnij-novgorod/]asxdiplomik24.ru/kupit-diplom-nizhnij-novgorod[/url]
[b]Успехов в учебе![/b]
Негативное воздействие незаконных действий и мошенников онлайн может повлиять на игровые аппараты – 7к казино зеркало
Привет!
Заказать документ университета вы сможете у нас в Москве.
ast-diploms.com/kupit-diplom-rostov-na-donu
Здравствуйте!
Заказать документ ВУЗа вы сможете в нашей компании в столице.
ast-diplom24.ru/kupit-diplom-krasnoyarsk
Удачи!
Seveceginiz bir kumarhane Sweet bonanza
Привет, друзья!
Приобрести документ университета можно в нашей компании в столице.
diploms-x.com/kupit-diplom-omsk
Привет!
Приобрести диплом университета.
godsoftheuniverse.mn.co/posts/61725501
Добрый день!
Где купить диплом специалиста?
Приобрести диплом о высшем образовании.
true.pahom.su/2024/07/04/kak-nayti-nadezhnyy-magazin-s-obshirnym-vyborom-diplomov.html
Здравствуйте!
Где купить диплом специалиста?
opengadjet.ru/legkiy-sposob-poluchit-diplom-byistro-i-prosto
Удачи!
Привет, друзья!
Мы изготавливаем дипломы любых профессий по выгодным ценам.
formfinance.ru/byistroe-oformlenie-diplomov-nadezhno-i-legalno
Привет!
Где заказать диплом по актуальной специальности?
Мы изготавливаем дипломы любой профессии по доступным ценам.
raceburo.ru/page/3
Здравствуйте!
Официальная покупка аттестата о среднем образовании в Москве и других городах
tawasol1.mn.co/posts/62049026
Поможем вам всегда!.
сколько стоит диплом сколько стоит диплом .
купить дипломы о высшем образовании москва diplomyx.com .
Guvenilir bir kumarhanede oynay?n Sweet bonanza
ремонт мобильных телефонов
Hi there, this weekend is good in favor of me, as this point in time i
am reading this great educational paragraph here at my home.
ремонт телефонов в москве рядом
Здравствуйте!
Мы предлагаем документы техникумов, расположенных в любом регионе РФ. Вы имеете возможность приобрести диплом за любой год, указав актуальную специальность и оценки за все дисциплины. Дипломы и аттестаты печатаются на бумаге самого высокого качества. Это позволяет делать государственные дипломы, не отличимые от оригиналов. Они будут заверены всеми обязательными печатями и штампами.
biiut.com/read-blog/66268
Привет!
Где заказать диплом по актуальной специальности?
Купить диплом ВУЗа.
forum.rucarp.ru/album.php?albumid=128&attachmentid=35737&commentid=1961
Guvenilir bir kumarhanede sans?n?z Sweet bonanza
купить диплом массажиста diplomyx.com .
купить диплом информатика asxdiplomik.com .
Привет, друзья!
Приобретение школьного аттестата с официальным упрощенным обучением в Москве
odinzovo.rusff.me/viewtopic.php?id=4869#p8228
Рады оказать помощь!.
Процесс получения диплома стоматолога: реально ли это сделать быстро?
ast-diploms.com/kupit-diplom-rostov-na-donu
Привет, друзья!
Узнайте, как приобрести диплом о высшем образовании без рисков
anoreksja.org.pl/posting.php?mode=post&f=13
Окажем помощь!.
Привет!
Где приобрести диплом по актуальной специальности?
Мы можем предложить дипломы любой профессии по приятным ценам. Стоимость будет зависеть от определенной специальности, года получения и образовательного учреждения. Всегда стараемся поддерживать для заказчиков адекватную ценовую политику. Для нас важно, чтобы документы были доступны для большого количества граждан.
Для вас изготавливаем дипломы психологов, юристов, экономистов и любых других профессий по приятным ценам.
avtobestnews.ru/kupit-diplom-rf-v-moskve-byistroe-oformlenie-i-vyisokoe-kachestvo
Рады оказаться полезными!.
Привет!
Покупка школьного аттестата с упрощенной программой: что важно знать
forum.activeworlds.ru/member.php?535-worksale
Рады помочь!.
Привет!
Мы предлагаем документы техникумов, расположенных на территории всей России. Можно приобрести диплом от любого учебного заведения, за любой год, указав необходимую специальность и хорошие оценки за все дисциплины. Документы выпускаются на “правильной” бумаге самого высокого качества. Это позволяет делать настоящие дипломы, не отличимые от оригиналов. Документы заверяются необходимыми печатями и подписями.
rab.chsl.ru/club/user/2/blog/8/
диплом мама купить ast-diploms.com .
купить диплом рудн diplomasx.com .
Здравствуйте!
Мы готовы предложить дипломы любой профессии по доступным ценам. Цена зависит от выбранной специальности, года выпуска и образовательного учреждения. Стараемся поддерживать для клиентов адекватную политику тарифов. Важно, чтобы дипломы были доступны для большинства граждан.
kingcityrp.moibb.ru/viewtopic.php?t=364
Шкаф-купе, сделанный на заказ, или стандартная магазинная модель: в чем разница при выборе?
Определение подходящей мебели для жилища является непростым делом.
Особенно это касается таких необходимых элементов, как шкаф-купе мебель на заказ.
Следует ли приобретать шкаф-купе,
который уже сделан, или лучше заказать изготовление по собственным
предпочтениям? Попробуем разобраться.
Плюсы покупки шкафа-купе у производителя
Экономичные шкафы-купе от производителя завлекают своей доступностью и оперативностью покупки.
Приобретение шкафа-купе для
вашей спальни или прихожей даст вам возможность немедленно насладиться покупкой и не требует продолжительного времени на доставку.
Фабричная мебель зачастую соответствует современному дизайну, благодаря чему её можно гармонично включить в любое оформление
помещения.
Индивидуальное оформление вашего интерьера
Индивидуально изготовленный шкаф-купе проектируется с учетом уникальных размеров вашей комнаты и ваших
предпочтений в дизайне и функционале.
Такой подход приобретает особую значимость, если ваша задача — оптимально
распорядиться доступным пространством или
если вам нужен уникальный дизайнерский проект.
Ясно, что если целью является минимизация расходов и времени,
то разумный вариант — это готовый
шкаф. Однако для желающих получить уникальный шкаф, изготовленный с учетом индивидуальных требований и габаритов, лучшим выбором станет изготовление на заказ.
В Санкт-Петербурге существует чудесная возможность
для покупки шкафа-купе по выгодной цене, будь то мебель со склада или сделанная на заказ в соответствии с вашими предпочтениями.
Здравствуйте!
Как получить диплом техникума с упрощенным обучением в Москве официально
obruchalka-vrn.ru/index.php?subaction=userinfo&user=ugobepa
Поможем вам всегда!.
Добрый день!
Где заказать диплом по необходимой специальности?
medbereg.ru/club/user/82/blog/4159/
Удачи!
Добрый день!
Мы предлагаем быстро и выгодно купить диплом, который выполняется на оригинальном бланке и заверен печатями, водяными знаками, подписями официальных лиц. Документ пройдет лубую проверку, даже при использовании профессиональных приборов. Решайте свои задачи максимально быстро с нашими дипломами.
http://www.hashtap.com/@anna.erofeeva/%D0%B7%D0%B0%D0%B4%D0%B0%D1%87%D0%B0-APw6J41V5WwR
Успехов в учебе!
Казино Риобет предлагает захватывающий игровой опыт с яркой графикой и качественными игровыми слотами для игры на реальные средства – Riobet официальный сайт рабочее
купить диплом бакалавра в волгограде asxdiplomik24.ru .
https://www.google.im/url?q=https://generik-spb.ru/levitra-vardenafil/djenerik-levitra-20-mg
Добрый день!
Заказать диплом о высшем образовании.
http://www.xn--5-htbd2chx.xn--p1ai/product/igra-stol-forma/reviews/
Успехов в учебе!
Казино 7k casino предлагает круглосуточную поддержку пользователей – r7 casino автоматы официальный сайт
На главной странице сайта casino размещена ссылка на 7к казино, где можно найти всю необходимую информацию – 7k casino на сегодня
Официальный сайт букмекерской конторы 7к казино предоставляет полный обзор своих услуг – рабочее зеркало сайта 7k casino
Bu kumarhanedeki en iyi oyunlar Sweet bonanza
http://cse.google.st/url?q=https://severtent.ru/
Здравствуйте!
Где приобрести диплом специалиста?
Приобрести диплом о высшем образовании.
laporteproperty.com/en/cb-profile/pluginclass/cbblogs?action=blogs&func=show&id=121
можно купить диплом высшем образовании можно купить диплом высшем образовании .
купить диплом бакалавра в нижнем новгороде ast-diploms.com .
Привет, друзья!
Мы можем предложить документы ВУЗов, которые находятся на территории всей РФ. Можно купить диплом за любой год, включая сюда документы старого образца. Дипломы и аттестаты печатаются на “правильной” бумаге самого высшего качества. Это позволяет делать настоящие дипломы, которые невозможно отличить от оригиналов. Документы заверяются всеми обязательными печатями и штампами.
http://www.zdravamir.ru/index.php?option=com_myblog&show=on-on-n-n-n-n-n-n-.html&Itemid=
Здравствуйте!
Официальное получение диплома техникума с упрощенным обучением в Москве
bdfeu.ukraine7.com/t19982-topic#36429
Рады оказаться полезными!.
Привет, друзья!
Всё, что нужно знать о покупке аттестата о среднем образовании
newsbizlife.ru/kupit-diplom-vyisokoe-kachestvo-i-nadezhnost
купить диплом в новочеркасске asxdiplomik24.ru .
Привет!
Мы можем предложить документы ВУЗов, расположенных в любом регионе РФ. Вы сможете заказать качественно сделанный диплом от любого учебного заведения, за любой год, указав подходящую специальность и хорошие оценки за все дисциплины. Дипломы и аттестаты выпускаются на бумаге самого высшего качества. Это дает возможность делать настоящие дипломы, не отличимые от оригинала. Они заверяются всеми обязательными печатями и штампами.
interactor.pro/read-blog/1360
Здравствуйте!
Полезные советы по безопасной покупке диплома о высшем образовании
bestworld.getbb.ru/viewtopic.php?f=8&t=1260
Рады помочь!.
Привет, друзья!
Удивительно, но купить диплом кандидата наук оказалось не так сложно
ratingforex.ru/forum-forex/viewtopic.php?f=18&t=35616&sid=f68caf2cc1c72d393fe7b0bd77673496
Поможем вам всегда!.
Lucas Smith Lab перевернул мир хитов! Хочешь услышать твои любимые песни в совершенно новом свете?
Тогда тебе срочно нужно познакомиться с музыкальным проектом Lucas Smith Lab!
Этот талантливый музыкант переосмыслил такие мировые хиты как Freed From Desire, Womanizer, Thunderstruck, A Bar Song (Tipsy) и многие другие,
создав невероятные кавер-версии, которые заставят тебя по-новому взглянуть на знакомые мелодии.
Готов удивляться? Включай Яндекс Музыку или другие платформы и погружайся в мир потрясающей музыки Lucas Smith Lab
#LucasSmithLab #Каверы #Музыка #Хиты #НовоеЗвучание
[url=https://music.yandex.ru/artist/22453757]Lucas Smith Lab[/url]
Lucas Smith Lab
En iyi cevrimici kumarhaneyi kesfedin Sweet bonanza
Привет!
Купить диплом любого ВУЗа.
obektivcentr.ru/forum/user/17419/
Удачи!
Привет, друзья!
Где купить диплом по актуальной специальности?
Купить диплом университета.
amtest.mybb.ru/viewtopic.php?id=423#p1372
Привет!
Мы готовы предложить дипломы любой профессии по приятным ценам.
domainrama.com/read-blog/822_nadezhnyj-magazin-s-obshirnym-vyborom-dokumentov.html
Привет!
Мы предлагаем выгодно заказать диплом, который выполняется на оригинальной бумаге и заверен печатями, штампами, подписями. Наш диплом пройдет любые проверки, даже при помощи профессионального оборудования. Решите свои задачи быстро и просто с нашим сервисом.
orgi.biz/org_kupit_diplom____
Хорошей учебы!
Привет!
Где заказать диплом специалиста?
buldingnews.ru/byistroe-oformlenie-diploma-nadezhno-i-konfidentsialno
Удачи!
Привет!
Мы предлагаем дипломы любых профессий по выгодным тарифам.
newsinweek.ru/poluchite-diplom-bez-lishnih-voprosov/
http://a-parser.com/proxy.php?link=https://generik-spb.ru/levitra-vardenafil/djenerik-levitra-20-mg
Привет!
Официальная покупка диплома вуза с сокращенной программой в Москве
medicineshocknews.ru/garantirovannoe-poluchenie-diploma-bez-riska-i-problem
Будем рады вам помочь!.
Добрый день!
Мы можем предложить документы техникумов, которые расположены в любом регионе РФ. Можно приобрести диплом за любой год, включая сюда документы старого образца. Дипломы и аттестаты выпускаются на бумаге самого высокого качества. Это дает возможность делать настоящие дипломы, которые не отличить от оригиналов. Документы заверяются необходимыми печатями и штампами.
http://www.cyberpinoy.net/read-blog/33705
Добрый день!
Легальная покупка школьного аттестата с упрощенной программой обучения.
Заказать диплом о высшем образовании.
ebuddiz.com//read-blog/24664
Здравствуйте!
Мы предлагаем документы техникумов, которые находятся в любом регионе РФ. Можно купить качественный диплом за любой год, указав необходимую специальность и хорошие оценки за все дисциплины. Дипломы и аттестаты выпускаются на бумаге самого высшего качества. Это дает возможность делать настоящие дипломы, которые невозможно отличить от оригинала. Они будут заверены необходимыми печатями и штампами.
entrastart.com//read-blog/49
Привет, друзья!
Наша компания предлагает быстро и выгодно заказать диплом, который выполнен на бланке ГОЗНАКа и заверен мокрыми печатями, штампами, подписями официальных лиц. Наш диплом способен пройти лубую проверку, даже с применением профессионального оборудования. Решите свои задачи максимально быстро с нашими дипломами.
http://www.metal-archives.com/users/dilopluyy
Успешной учебы!
Привет!
Приобрести диплом о высшем образовании.
micchat.online/read-blog/1525
Привет, друзья!
Где заказать диплом специалиста?
dskrnd.ru/forum/user/6469/
Успешной учебы!
Привет, друзья!
Как официально купить аттестат 11 класса с упрощенным обучением в Москве
magnat-matras.ru/forum/user/50794
Поможем вам всегда!.
ремонт сотовых в москве
Привет, друзья!
Мы готовы предложить документы техникумов, расположенных на территории всей России. Вы имеете возможность заказать диплом за любой год, в том числе документы старого образца. Документы выпускаются на “правильной” бумаге высшего качества. Это дает возможности делать государственные дипломы, которые невозможно отличить от оригиналов. Документы будут заверены необходимыми печатями и подписями.
автомедведь.рф/club/user/8729/blog/193097/
Здравствуйте!
Покупка диплома о среднем полном образовании: как избежать мошенничества?
sydplatinum.com/купить-диплом-рф/
Здравствуйте!
Как безопасно купить диплом колледжа или ВУЗа в России, что важно знать
vatrusha.maxbb.ru/viewtopic.php?f=2&t=692
Будем рады вам помочь!.
як і раніше успіх в обміні валют, на пряму залежить тому місця, обмен юсдт на монобанк де легко купити валюту дешевше, і реалізувати дорожче.
купить диплом в новосибирске ast-diploms.com .
купить диплом бакалавра в нижнем новгороде diplomasx.com .
Здравствуйте!
Где заказать диплом специалиста?
Заказать диплом университета.
cdposz.ru/club/user/802/forum/message/1485/1544/
Обеспечьте конфиденциальность с резидентскими прокси, советуем этим инструментом.
Какие преимущества у резидентских прокси?, узнайте подробностями.
Советы по выбору резидентского прокси, инструкция для пользователей.
Зачем нужны резидентские прокси?, узнайте возможностями.
Как резидентские прокси обеспечивают безопасность?, обзор функций безопасности.
Какие риски может предотвратить резидентский прокси?, рассмотрим важные аспекты.
Как резидентский прокси помогает повысить эффективность?, рассмотрим основные плюсы.
Как быстрее работать в сети с резидентским прокси?, рекомендации для оптимизации работы.
Почему резидентский прокси стоит использовать для парсинга, разбор возможностей для парсеров.
Как оставаться анонимным в Интернете с резидентским прокси, рекомендации к безопасности онлайн.
Как расширить свои возможности в соцсетях с резидентским прокси?, подробный обзор функционала.
Зачем арендовать резидентские прокси и какие бонусы?, сравним лучшие варианты.
Как избежать DDoS с резидентским прокси?, подробно изучим меры безопасности.
Какие преимущества привлекают пользователей к резидентским прокси?, рассмотрим основные факторы.
Сравнение резидентских и дата-центровых прокси, советы для выбора.
купить резидентские прокси листы https://rezidentnieproksi.ru/ .
авито диплом авито диплом .
Привет, друзья!
Приобретение школьного аттестата с официальным упрощенным обучением в Москве
wecanchat.mn.co/posts/62049695
Окажем помощь!.
Здравствуйте!
Мы предлагаем документы ВУЗов, расположенных в любом регионе Российской Федерации. Вы можете купить качественно напечатанный диплом от любого заведения, за любой год, указав необходимую специальность и хорошие оценки за все дисциплины. Документы печатаются на бумаге самого высокого качества. Это дает возможности делать государственные дипломы, не отличимые от оригинала. Документы будут заверены необходимыми печатями и штампами.
ivebo.co.uk/read-blog/45620
Азарт казино вован и волнующие джекпоты безвозмездны и пребывают непосредственно у тебя поблизости, в том большом во всем мире приложении-площадок для мессенджеров.
Привет, друзья!
Легальная покупка школьного аттестата с упрощенной программой обучения.
Приобрести диплом любого ВУЗа.
samovod.ru/content/articles/65991/
Привет, друзья!
Легальные способы покупки диплома о среднем полном образовании
magazin.orgsoft.ru/communication/forum/index.php?PAGE_NAME=profile_view&UID=190534
Поможем вам всегда!.
Безопасность данных с резидентскими прокси, преимущества.
Смотрите зарубежные сериалы с резидентскими прокси, неограниченным контентом.
Получите быстрый и надежный интернет с резидентскими прокси, как это работает.
Обезопасьте свои онлайн-платежи с резидентскими прокси, и чувствуйте себя спокойно.
Прячьте свою локацию и IP-адрес с резидентскими прокси, и оставайтесь незамеченными.
Используйте резидентские прокси для безопасного серфинга в интернете, и не тревожьтесь за свою приватность.
аренда резидентных прокси https://rezidentnie-proksi.ru/ .
купить диплом колледжа в краснодаре ast-diploms.com .
Привет!
Где приобрести диплом специалиста?
Купить диплом любого ВУЗа.
true.pahom.su/2024/07/04/kak-nayti-nadezhnyy-magazin-s-obshirnym-vyborom-diplomov.html
купить дипломы о высшем образовании москва купить дипломы о высшем образовании москва .
vons доставляет продукты и алкоголь в https://bulgaria.forum.cool/viewtopic.php?id=140#p330 большинстве городов США. также, членство в трудоустройстве услуге, стоит $299 в году.
Добрый день!
Где приобрести диплом специалиста?
Приобрести диплом о высшем образовании.
http://www.zdravamir.ru/index.php?option=com_myblog&show=n-n-n-n-on-n-n-n-n-n-.html&Itemid=
купить диплом фармацевта с занесением в реестр купить диплом фармацевта с занесением в реестр .
Добрый день!
Мы изготавливаем дипломы любой профессии по приятным тарифам.
tailblog.com/wp/2024/06/30/купить-диплом-в-анапе/
Здравствуйте!
Приобретение школьного аттестата с официальным упрощенным обучением в Москве
eicolumbaira.es/купить-диплом-онлайн/
у нас обширный ассортимент блюд, и других товаров в которых предусмотрена возможность доставки как из заведений общепита, https://arma.at.ua/forum/60-12951-1 вовсе из партнеров.
Приветствую. Может кто знает, где почитать полезные статьи о недвижимости? Пока нашел https://glatt-nsk.ru
Привет, друзья!
Купить диплом старого образца, можно ли это сделать по быстрой схеме?
silton.ru/forum/user/5008
Рады оказать помощь!
Здравствуйте!
Наша компания предлагает выгодно приобрести диплом, который выполняется на оригинальной бумаге и заверен печатями, водяными знаками, подписями. Данный документ способен пройти лубую проверку, даже с применением профессионального оборудования. Достигайте свои цели максимально быстро с нашим сервисом.
nvkb.ru/forum/index.php/user/101059/
Удачи!
Привет, друзья!
Как официально купить аттестат 11 класса с упрощенным обучением в Москве
mamapoltava.listbb.ru/viewtopic.php?f=39&t=5302
Рады помочь!
Ищете качественную мебель для офиса? Рекомендую обратить внимание на замм. Этот бренд предлагает широкий ассортимент офисной мебели, включая стильные и функциональные офисные столы. Продукция замм отличается высоким качеством, долговечностью и современным дизайном. Идеально подходит для создания комфортного и продуктивного рабочего пространства. В ассортименте вы найдете всё, что нужно для организации современного офиса. Отличный выбор для тех, кто ценит надежность и стиль! С уважением, Zamm мебель.
this is only one of such ways with which the https://p-network.io/ can store important data for firms.
Всем привет! Может кто знает, где найтиразные блоги о недвижимости? Сейчас читаю https://krovli-12.ru
Привет!
Где купить диплом специалиста?
Заказать диплом любого ВУЗа.
kurkure.ru/index.php/cb-profile/pluginclass/cbblogs?action=blogs&func=show&id=140
Приветствую. Может кто знает, где найтиполезные статьи о недвижимости? Сейчас читаю https://krovli-12.ru
лучшее порево бесплатно лучшее порево бесплатно .
Здравствуйте!
Мы готовы предложить дипломы любой профессии по приятным ценам.
vintfint.com/blogs/21171/ упите-?ипломы-Ѕыстро-и-Ќадежно
Здравствуйте!
Мы изготавливаем дипломы любой профессии по доступным тарифам. Цена зависит от конкретной специальности, года получения и университета. Стараемся поддерживать для покупателей адекватную политику тарифов. Важно, чтобы документы были доступными для большинства граждан.
yesbookmarks.com/story17129175/купить-аттестат-за-11-класс
Здравствуйте!
Мы изготавливаем дипломы любой профессии по приятным ценам.
educacioncontinua.udgvirtual.udg.mx/2024/07/11/купит-диплом-мти/
Привет, друзья!
Приобрести диплом любого ВУЗа.
sonnick84.rusedu.net/post/10787/113381
Привет, друзья!
Официальная покупка диплома ВУЗа с упрощенной программой обучения
japapmessenger.com/read-blog/522
Рады помочь!
Привет, друзья!
Как правильно приобрести диплом колледжа или ПТУ в России, важные моменты
startinvest.2bb.ru/viewtopic.php?id=10516#p53862
Поможем вам всегда!
Добрый день!
Приобретение диплома ПТУ с сокращенной программой обучения в Москве
sydplatinum.com/купить-диплом-рф/
Привет, друзья!
Мы можем предложить документы ВУЗов, которые расположены в любом регионе Российской Федерации. Вы имеете возможность купить диплом за любой год, в том числе документы старого образца. Дипломы и аттестаты выпускаются на “правильной” бумаге самого высокого качества. Это дает возможности делать настоящие дипломы, которые не отличить от оригинала. Документы будут заверены всеми необходимыми печатями и подписями.
http://www.bakinsky-dvorik.ru/club/user/127071/blog/4747/
Добрый день!
Мы изготавливаем дипломы любой профессии по невысоким ценам.
newsbig2.almoheet-travel.com/gramotno-pokupaem-diplom-v-seti-internet-avtorskij-obzor/
Привет!
Где купить диплом по актуальной специальности?
themepacific.com/support/users/lutroduyda/
Привет, друзья!
Мы можем предложить документы техникумов, расположенных в любом регионе Российской Федерации. Вы сможете купить диплом от любого учебного заведения, за любой год, в том числе документы старого образца. Документы делаются на “правильной” бумаге самого высшего качества. Это позволяет делать настоящие дипломы, которые не отличить от оригинала. Они будут заверены всеми необходимыми печатями и подписями.
blogger-mania.mn.co/posts/61838359
Приветствую. Может кто знает, где почитатьразные статьи о недвижимости? Пока нашел https://varmex-spb.ru
Если вам нужны профессионалы в области продвижения сайтов и разработки, обратите внимание на MD. Они предлагают полный спектр услуг: от SEO и SEM до работы с Яндекс.Директ. Команда специализируется на создании эффективных стратегий, которые помогают привлечь целевую аудиторию и увеличить видимость вашего бизнеса в интернете. Их профессионализм и подход к каждому клиенту гарантируют отличные результаты. Рекомендую ООО”МД” как надежного партнера в цифровом маркетинге! С уважением, Mihaylov Digital.
Здравствуйте!
Приобрести документ ВУЗа
diploms-x24.ru/kupit-diplom-nizhnij-novgorod
Добрый день!
Купить диплом о среднем образовании в Москве и любом другом городе
landik-diploms-srednee.ru/attestat-shkoly В
Привет!
Как официально купить аттестат 11 класса с упрощенным обучением в Москве
gamesfortop.ru/diplom-dlya-karernogo-rosta-prosto-i-udobno
Поможем вам всегда!
Привет!
Мы готовы предложить дипломы любой профессии.
newmedtime.ru/vyisshee-obrazovanie-za-sutki-legalno-i-nadezhno
Будем рады вам помочь!.
Здравствуйте!
Где приобрести диплом по актуальной специальности?
dzone.com/users/5166875/leonardchambers.html
стоимость блоков 400 https://gazobeton-moskow.ru/
Привет, друзья!
Мы предлагаем документы ВУЗов, расположенных в любом регионе России. Можно купить качественно напечатанный диплом от любого учебного заведения, за любой год, в том числе документы старого образца. Дипломы и аттестаты выпускаются на “правильной” бумаге самого высокого качества. Это дает возможности делать государственные дипломы, не отличимые от оригиналов. Документы заверяются всеми обязательными печатями и подписями.
productinn.mn.co/posts/61828807
casino locowin
Привет!
Мы готовы предложить дипломы любой профессии по приятным ценам.
http://www.acrossperu.com/купить-диплом-в-коврове/
бесплатное порно видео бесплатное порно видео .
Привет, друзья!
Приобрести документ о получении высшего образования
asxdiplomik.com/kupit-diplom-moskva
Привет, друзья!
Рекомендации по безопасной покупке диплома о высшем образовании
landik-diploms-srednee.ru/kupit-diplom-volgograd В
Привет!
Как купить диплом о высшем образовании с минимальными рисками
armit.ru/social/user/42552/forum/message/1605/1607/#message1607
Будем рады вам помочь!
Приветствую. Может кто знает, где найти полезные статьи о недвижимости? Пока нашел https://konditsioneri-shop.ru
Привет!
Мы изготавливаем дипломы любой профессии по доступным тарифам.
allukrnews.ru/vash-put-k-uspehu-kupit-diplom/
Привет, друзья!
Мы готовы предложить дипломы психологов, юристов, экономистов и других профессий по доступным ценам. Цена будет зависеть от той или иной специальности, года выпуска и университета. Всегда стараемся поддерживать для заказчиков адекватную политику цен. Важно, чтобы документы были доступными для большого количества граждан.
http://www.tumblr.com/cathyfowler2
Лучшие корейские автомобили | Как выбрать авто из Кореи? | Корейские авто: плюсы и минусы | Топ-5 автомобилей из Кореи | Секреты долговечности корейских автомобилей | Топ-3 востребованных автомобиля из Кореи | Как не ошибиться при покупке поддержанного автомобиля Кореи | Ценовая политика корейских автомобилей | Что стоит знать перед покупкой корейского авто | Рейтинг SUV корейских производителей | Корейские кроссоверы: стиль и комфорт | Корейские авто для долгих поездок: комфорт и безопасность | Как выбрать городской автомобиль из Кореи? | Как оценить состояние авто из Кореи перед покупкой? | Как сделать уникальным свой корейский автомобиль
авто из кореи купить авто из кореи купить .
Здравствуйте!
Мы предлагаем дипломы психологов, юристов, экономистов и любых других профессий по доступным тарифам.
gamesfortop.ru/vash-diplom-garantiya-kachestva-i-podlinnosti
Здравствуйте!
Купить диплом о среднем образовании в Москве и любом другом городе
karriere.kv-architektur.de/купить-диплом-иргупс/
Привет, друзья!
Приобрести диплом любого университета.
http://www.bisshogram.com/read-blog/267
אפשר לדבר הרבה על הפינוקים והרגעים הנעימים בחברתן של הנערות הסקסיות שמארחות גברים. אבל מה שקורה בין הסדינים הוא לא עניין לדבר אינטימית ביותר. הן לא שואלות שאלות קשות, אלא רק גורמות לגבר להרגיש בנוח. הן אוהבות לגעת והן רוצות לגעת. הן יודעות כיצד לעבוד הנאה בתל אביב – חוויה שכל גבר חייב לעצמו לפחות פעם אחת בחיים
Рекомендую лучшего букмекера 1win
Добрый день!
Мы можем предложить дипломы любой профессии по выгодным ценам.
acilshop.com/2024/06/23/купить-диплом-вуза-в-новомосковске/
Посетите 1win официальный сайт для получения доступа к широкому ассортименту игр и ставок.
Привет!
Где заказать диплом по нужной специальности?
http://www.marqueze.net/miembros/matthewmorgan/profile/classic/
Привет!
Как приобрести диплом о среднем образовании в Москве и других городах
karhu.blueaddlution.com/2024/06/30/купить-диплом-в-серове/
כל סודות הגוף והן יגרמו לך להנאה רבה. אתה תרגיש את הגבריות שלך בשיא עצמתה, ובעודך נהנה מהנשיות המושלמת של הנערות. גופך ינוע בתל אביב פותחות בפניך דלת לעולם חדש – עולם של הנאה אין סופית והגשמת פנטזיות. זוהי המומחיות שלהן והן עושות זאת בתשוקה רבה. הן discover more here
Как приобрести аттестат о среднем образовании в Москве и других городах
diploms-x.com/kupit-diplom-voronezh
Официальный 1win сайт предлагает разнообразные азартные игры и выгодные ставки.
ומקשיח את מה שצריך להקשיח. להרגע עם הבחורות היפות של דירות דיסקרטיות בחיפה כולנו סובלים מסטרס. לפעמים אלו צעירים העובדים שעות ליווי בחיפה אז עם סיבה או בלי סיבה, פשוט הזמן עכשיו נערות ליווי בחיפה והן ידאגו שיהיה לך טוב. הנערות מגיעות עד אלייך, וזה יכול read this post here
הערב, אתה פשוט יכול להזמין נערה כלבבך והיא תשמח את מצב רוחך. ולא רק בערב, נערות ליווי בחיפה מעניקות שירות 24 שעות ביממה ובכל ליווי זמינות ברגע זה אתה לא צריך לחלום על בילויים אינטימיים עם נערות מדהימות, אתה רק צריך להתקשר ולקבוע עם הנערות. נערות this post
Привет!
Мы изготавливаем дипломы любой профессии по приятным тарифам.
webyourself.eu/blogs/358414/ упите-?ипломы-Ѕыстро-и-Ќадежно
Привет!
Купить диплом о высшем образовании.
true.pahom.su/2024/07/04/kak-nayti-nadezhnyy-magazin-s-obshirnym-vyborom-diplomov.html
Привет!
Приобрести документ ВУЗа
ast-diplom24.ru/kupit-diplom-omsk
Добрый день!
Всё, что нужно знать о покупке аттестата о среднем образовании
http://www.rcmecano.fr/2024/06/30/купили-дипломы-университета/
Привет!
Купить диплом о среднем образовании в Москве и любом другом городе
landik-diploms-srednee.ru/kupit-diplom-v-kazani В
Играть в 1win казино можно с любым устройством, получая удовольствие от высокого качества игр.
1win официальный сайт гарантирует честные игры и надежные выплаты.
כל סודות הגוף והן יגרמו לך להנאה רבה. אתה תרגיש את הגבריות שלך בשיא עצמתה, ובעודך נהנה מהנשיות המושלמת של הנערות. גופך ינוע יודעות איך לעשות זאת בצורה הטובה ביותר. אין סיבה להרגיש לבד כאשר אתה יכול להזמין כבר עכשיו נערות ליווי בתל אביב שיבואו ויבלו ליווי אדיר
באופן מיידי. זוהי חוויה משחררת שתגרום לך לשכוח מהכל ולמלא מחדש את המצברים. דירות דיסקרטיות בחיפה – חוויה נעימה בעיר נעימה. וכאשר יש דירות דיסקרטיות בבאר שבע, תוכל לעשות זאת בקלי קלות. הדירות הדיסקרטיות הן הפתרון המתאים עבור כל הגברים. לפעמים זהו the full report
Здравствуйте!
Где приобрести диплом по актуальной специальности?
dzone.com/users/5166875/leonardchambers.html
Ищете надёжный ресурс? 1вин сайт предоставляет всё необходимое для азартных игр.
Привет!
Мы можем предложить дипломы любой профессии.
epicit.ru/vash-diplom-legalno-nadezhno-i-udobno
Рады оказать помощь!.
Здравствуйте!
Купить документ о получении высшего образования
diplomyx24.ru/kupit-diplom-moskva
Добрый день!
Как приобрести аттестат о среднем образовании в Москве и других городах
arusak-diploms-srednee.ru/kupit-diplom-magistra В
Along with the growth of internet scams as well as identification theft, knowing exactly how virtual SMS confirmation services function as a cover against these risks is actually essential. By exploring the detailed methods which SMS codes reinforce protection actions, you’ll find the elaborate mechanisms that safeguard your personal info from falling under the incorrect hands, https://nadersobhysoliman.blogspot.com/2024/06/just-how-virtual-sms-text-verification.html.
Зеркало 1win поможет вам продолжить игру без перебоев.
Привет!
Мы изготавливаем дипломы любых профессий по выгодным ценам.
prikol100500.ru/vash-diplom-byistro-nadezhno-kachestvenno
1вин зеркало рабочее всегда доступно для вас.
https://derbayerischelowe.info/
Здравствуйте!
Как получить диплом техникума с упрощенным обучением в Москве официально
hunmanby.uk/купить-диплом-в-дмитрове/
Здравствуйте!
Приобрести диплом ВУЗа.
xn--80apeih4a.xn--p1ai/club/user/71/blog/4501/
Привет, друзья!
Мы предлагаем дипломы любых профессий по приятным тарифам.
angelicaleyva.es/купить-диплом-тамбов/
Добрый день!
Полезная информация как официально купить диплом о высшем образовании
datafornix.com/госзнак-диплом-купить/
Hello players!!
I’ve been playing at Glory Casino for half a year. The high odds and fast payouts are great. The working mirror is always available, and registration takes a couple of minutes. An excellent casino and bookmaker, I recommend it to all gambling enthusiasts!
Glory Casino is reliability and convenience. Simple registration, generous bonuses, and fast payouts. The working mirror is always available. I play and win with pleasure. I recommend it to all gambling enthusiasts!
Catch the site where everything is in the best shape! – Glory Casino
Glory Casino promo codes
download Glory Casino on android for free from official website
Glory Casino official mobile
download apk Glory Casino on Android
Glory Casino website login
Good profits!
Здравствуйте!
Купить диплом любого университета.
antrem.ru/cb-profile/pluginclass/cbblogs?action=blogs&func=show&id=283
Hi, the whole thing is going sound here and ofcourse every one is sharing data, that’s actually good, keep up writing.
https://usirf.ru/